uplload 通关纪实 pass5
Posted 安全界 的彭于晏
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了uplload 通关纪实 pass5相关的知识,希望对你有一定的参考价值。
php.ini 是 php的配置文件,.user.ini 中的字段也会被 php 视为配置文件来处理,从而导致 php 的文件解析漏洞。
但是想要引发 .user.ini 解析漏洞需要三个前提条件:
服务器脚本语言为PHP;
服务器使用CGI/FastCGI模式;
上传目录下要有可执行的php文件。
源代码如下:
$is_upload = false;
$msg = null;
if (isset($_POST['submit']))
if (file_exists(UPLOAD_PATH))
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext))
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path))
$is_upload = true;
else
$msg = '上传出错!';
else
$msg = '此文件类型不允许上传!';
else
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
先上传一个.user.ini文件,文件内容为auto_prepend_file=1.jpg。
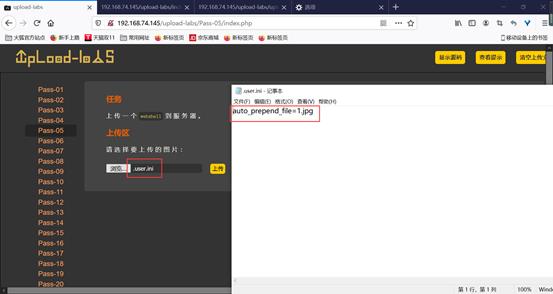
之后再上传一个1.jpg文件:
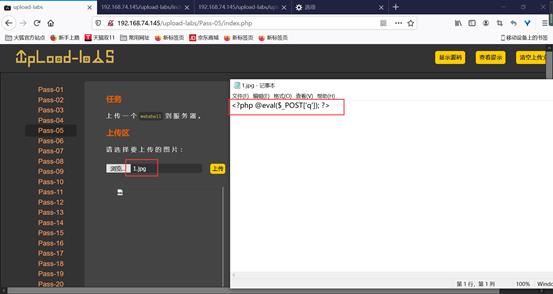
接着输入以下网址连接菜刀:
http://192.168.74.145/upload-labs/include.php?file=upload/1.jpg
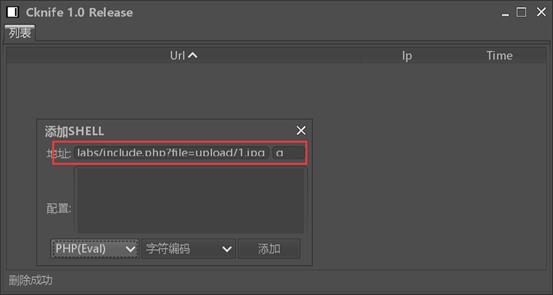
成功访问到:
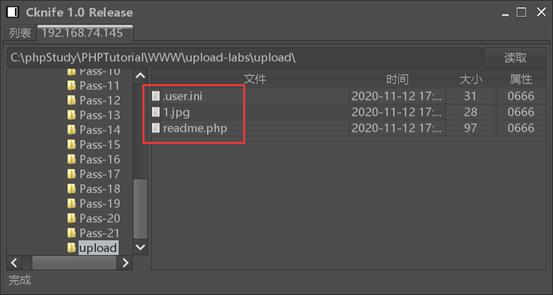
以上是关于uplload 通关纪实 pass5的主要内容,如果未能解决你的问题,请参考以下文章