Elasticsearch:部署 ECE (Elastic Cloud Enterprise)
Posted Elastic 中国社区官方博客
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Elasticsearch:部署 ECE (Elastic Cloud Enterprise)相关的知识,希望对你有一定的参考价值。
Elasticsearch 公司提供 Elastic Cloud Enterprise (ECE),它与 Elasticsearch Cloud (https://www.elastic.co/cloud) 中使用的工具相同,并且免费提供。 该解决方案可在 AWS、Azure 或 GCP 上的平台即服务 (PaaS) 上使用,可以在本地安装以在 Elasticsearch 之上提供企业解决方案。如果你需要跨团队或跨地域管理多个 Elastic 部署,你可以利用 ECE 集中部署管理以实现以下功能:
- 供应
- 监控
- 扩展
- 复制
- 升级
- 备份和恢复
使用 ECE 集中管理部署可强制实施统一的版本控制、数据治理、备份和用户策略。 通过更好的管理提高硬件利用率也可以降低总成本。
前提条件
由于此解决方案针对大量服务器的大型安装,因此最低测试要求是 8 GB RAM 节点。 ECE 解决方案依赖于 Docker 的安装,因此 Docker 必须安装在节点上。ECE 仅支持部分操作系统; 兼容性矩阵可在线获取 Support Matrix | Elastic。在其他配置上,ECE 可以工作,但在出现问题时不受支持。
安装
在安装 ECE 之前,需要检查以下先决条件:
- 你的用户必须是启用 Docker 的用户。 如果由于非 Docker 用户而出现错误,请使用 sudo usermod -aG docker $USER 添加你的用户。
- 如果你尝试访问 /mnt/data 时出错,请授予你的用户访问该目录的权限。你可以使用如下的命令:
liuxg@liuxgu:/mnt$ pwd
/mnt
liuxg@liuxgu:/mnt$ sudo mkdir -p data
[sudo] password for liuxg:
liuxg@liuxgu:/mnt$ sudo chmod a+rwx data/- 你需要将以下行添加到 /etc/sysctl.conf(需要重新启动):
vm.max_map_count = 262144- 为了能够使用 ECE,它必须首先安装在第一台主机上,如下所示:
bash <(curl -fsSL https://download.elastic.co/cloud/elastic-cloud-enterprise.sh) install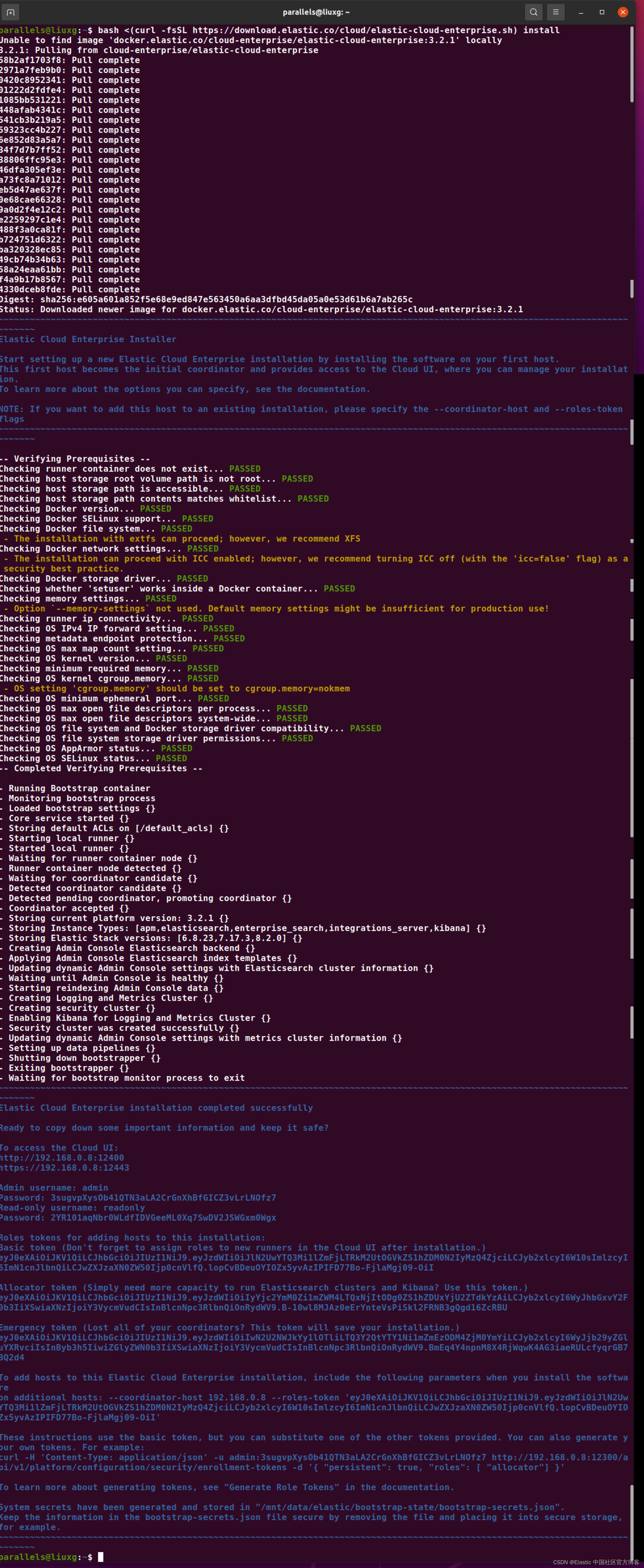
安装过程应自动管理这些步骤,如以上屏幕截图所示。最后,安装程序应提供你的登录的地址,用户名及密码,以便您可以在类似的输出中访问你的集群,如下所示:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Elastic Cloud Enterprise installation completed successfully
Ready to copy down some important information and keep it safe?
To access the Cloud UI:
http://192.168.0.8:12400
https://192.168.0.8:12443
Admin username: admin
Password: 3sugvpXysOb41QTN3aLA2CrGnXhBfGICZ3vLrLNOfz7
Read-only username: readonly
Password: 2YR101aqNbr0WLdfIDVGeeML0Xq7SwDV2JSWGxm0Wgx
Roles tokens for adding hosts to this installation:
Basic token (Don't forget to assign roles to new runners in the Cloud UI after installation.)
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJlN2UwYTQ3Mi1lZmFjLTRkM2UtOGVkZS1hZDM0N2IyMzQ4ZjciLCJyb2xlcyI6W10sImlzcyI6ImN1cnJlbnQiLCJwZXJzaXN0ZW50Ijp0cnVlfQ.lopCvBDeuOYIOZx5yvAzIPIFD77Bo-FjlaMgj09-OiI
Allocator token (Simply need more capacity to run Elasticsearch clusters and Kibana? Use this token.)
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiIyYjc2YmM0Zi1mZWM4LTQxNjItODg0ZS1hZDUxYjU2ZTdkYzAiLCJyb2xlcyI6WyJhbGxvY2F0b3IiXSwiaXNzIjoiY3VycmVudCIsInBlcnNpc3RlbnQiOnRydWV9.B-10wl8MJAz0eErYnteVsPiSkl2FRNB3gQgd16ZcRBU
Emergency token (Lost all of your coordinators? This token will save your installation.)
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiIwN2U2NWJkYy1lOTliLTQ3Y2QtYTY1Ni1mZmEzODM4ZjM0YmYiLCJyb2xlcyI6WyJjb29yZGluYXRvciIsInByb3h5IiwiZGlyZWN0b3IiXSwiaXNzIjoiY3VycmVudCIsInBlcnNpc3RlbnQiOnRydWV9.BmEq4Y4npnM8X4RjWqwK4AG3iaeRULcfyqrGB7BQ2d4
To add hosts to this Elastic Cloud Enterprise installation, include the following parameters when you install the software
on additional hosts: --coordinator-host 192.168.0.8 --roles-token 'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJlN2UwYTQ3Mi1lZmFjLTRkM2UtOGVkZS1hZDM0N2IyMzQ4ZjciLCJyb2xlcyI6W10sImlzcyI6ImN1cnJlbnQiLCJwZXJzaXN0ZW50Ijp0cnVlfQ.lopCvBDeuOYIOZx5yvAzIPIFD77Bo-FjlaMgj09-OiI'
These instructions use the basic token, but you can substitute one of the other tokens provided. You can also generate your own tokens. For example:
curl -H 'Content-Type: application/json' -u admin:3sugvpXysOb41QTN3aLA2CrGnXhBfGICZ3vLrLNOfz7 http://192.168.0.8:12300/api/v1/platform/configuration/security/enrollment-tokens -d ' "persistent": true, "roles": [ "allocator"] '
To learn more about generating tokens, see "Generate Role Tokens" in the documentation.
System secrets have been generated and stored in "/mnt/data/elastic/bootstrap-state/bootstrap-secrets.json".
Keep the information in the bootstrap-secrets.json file secure by removing the file and placing it into secure storage, for example.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~上面的安装将会生成很多的 docker 容器。我们可以使用如下的命令来查看:
docker ps就我而言,我可以在以下位置 http://192.168.0.8:12400 访问已安装的界面:
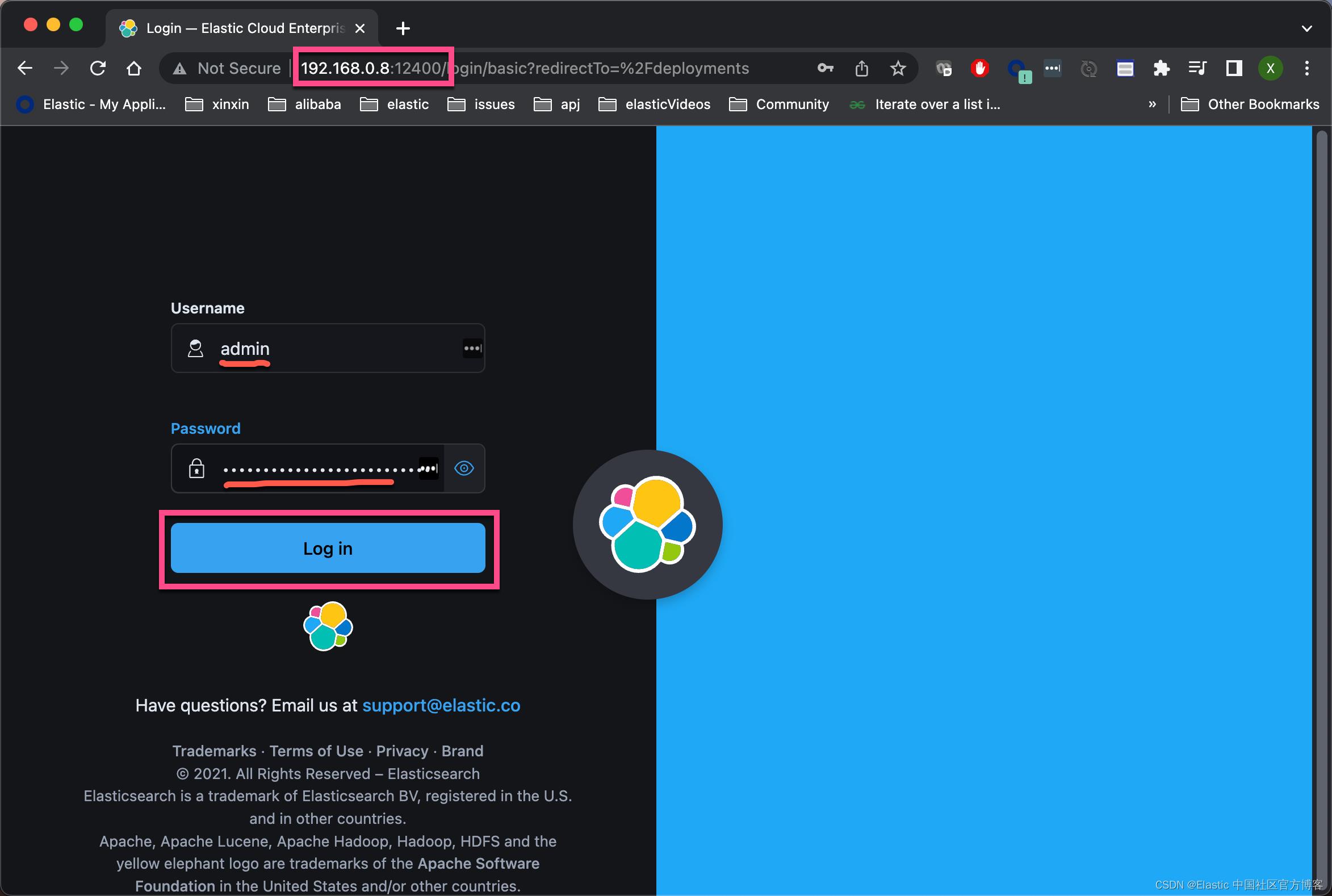
我们使用上面显示的用户名及密码来进行登录。
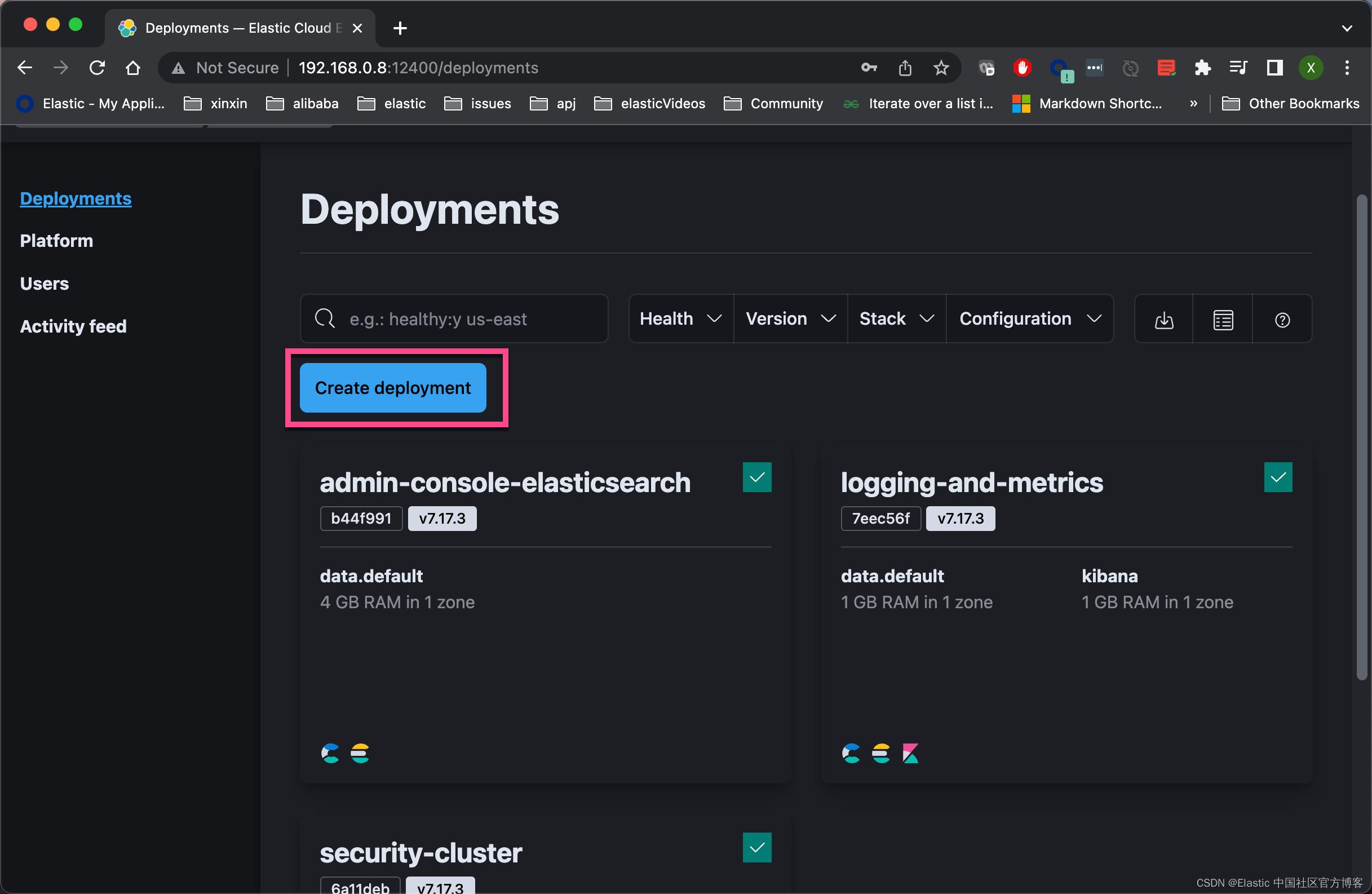
我们选择上面的 Create deployment 来创建一个最新的 Elasticsearch 集群:
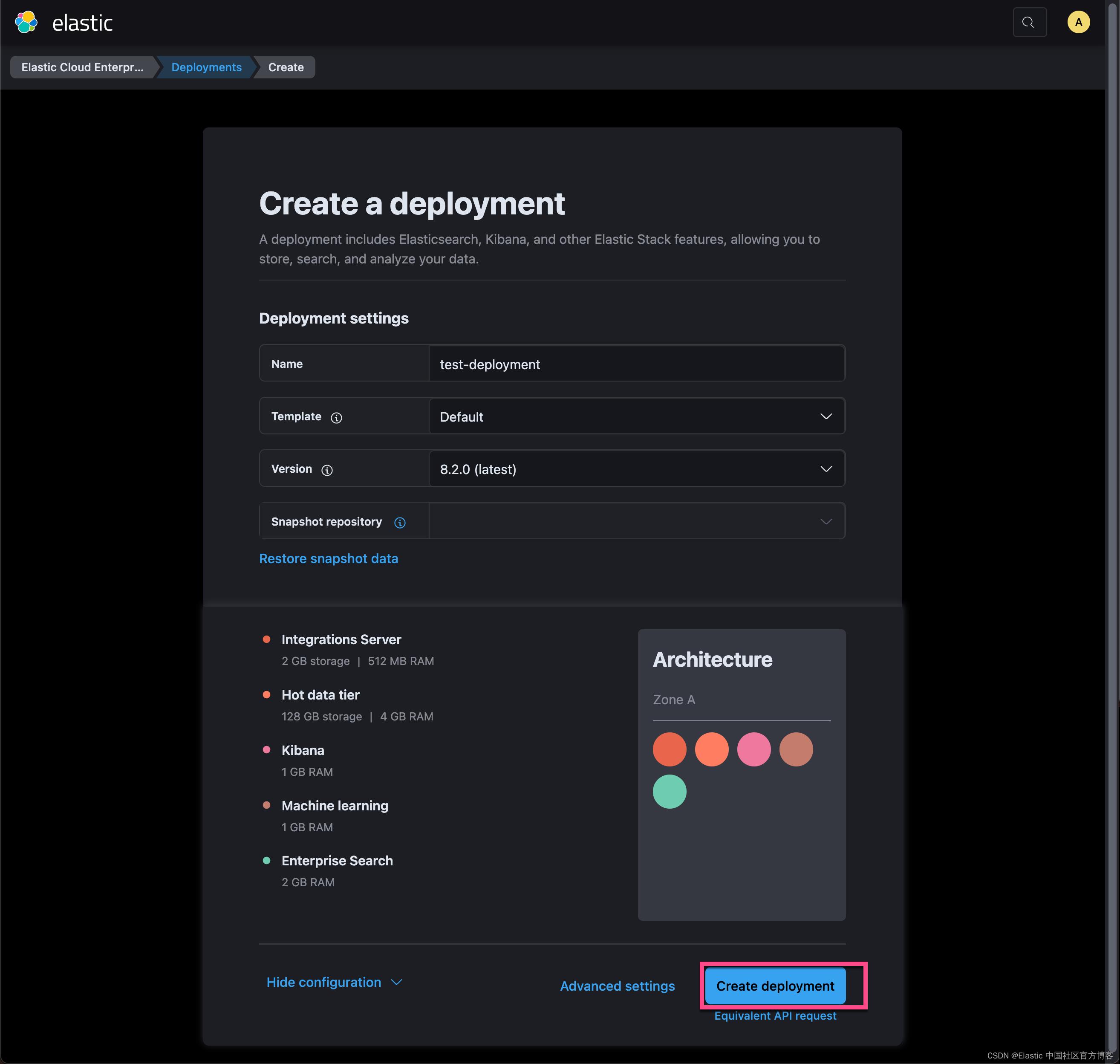
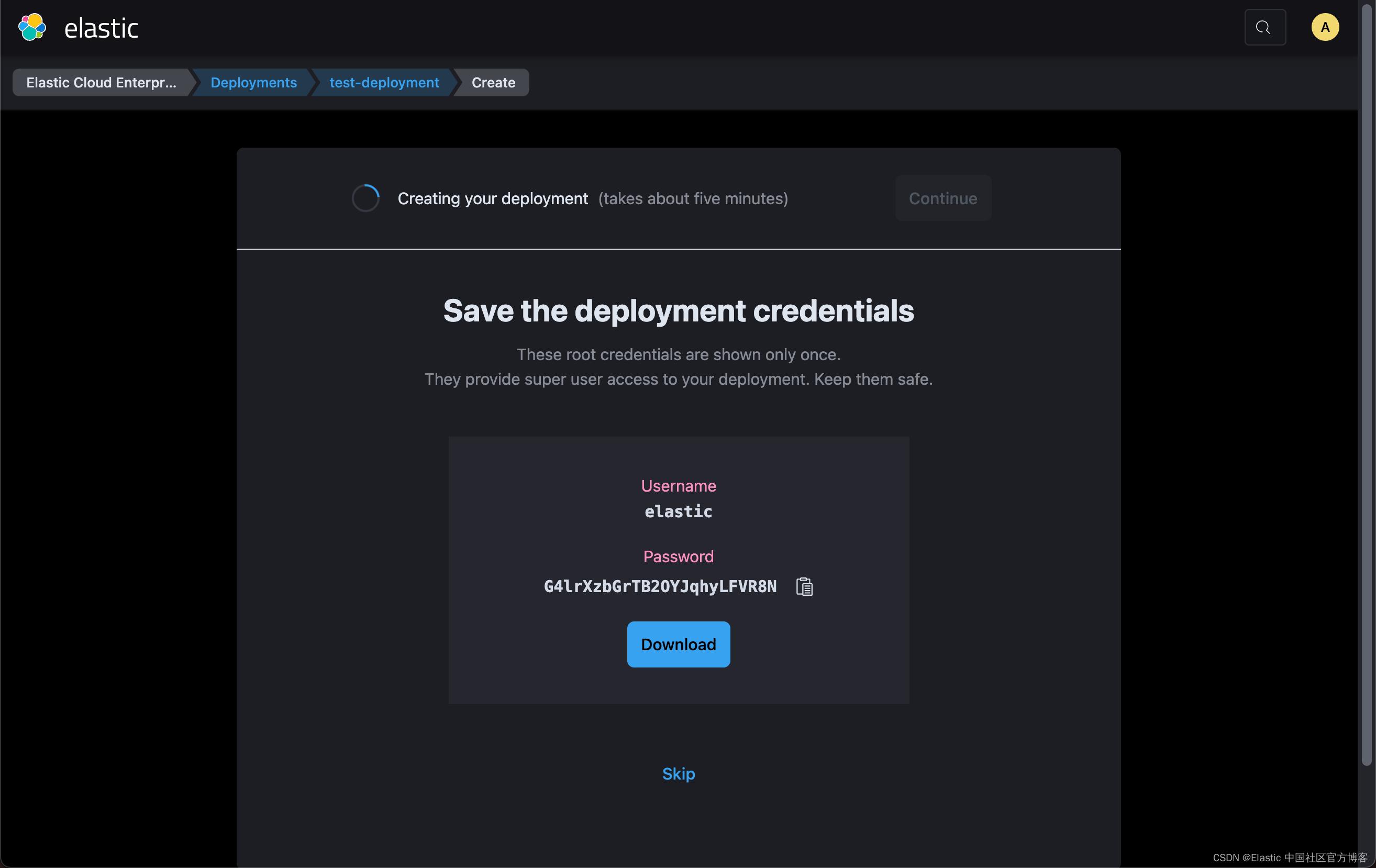
如上所示,我们须保存超级用户 elastic 的密码 G4lrXzbGrTB2OYJqhyLFVR8N 以备以后使用,因为这个密码只显示一次。启动一个集群需要一点时间。如上所示,需要15 分钟左右的时间。
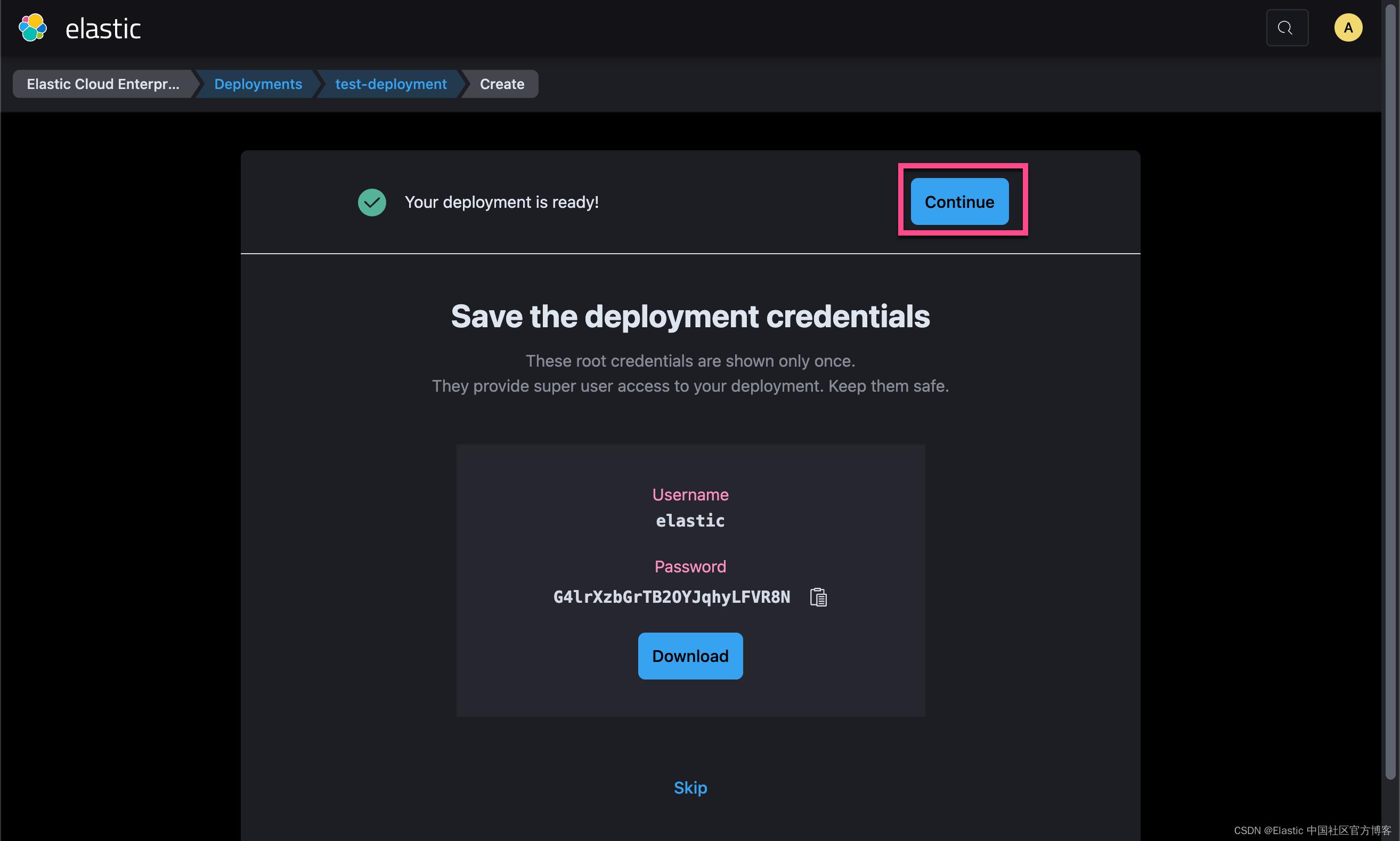
如上所示,我们的集群已经创建成功了。点击上面的 Continue 按钮:
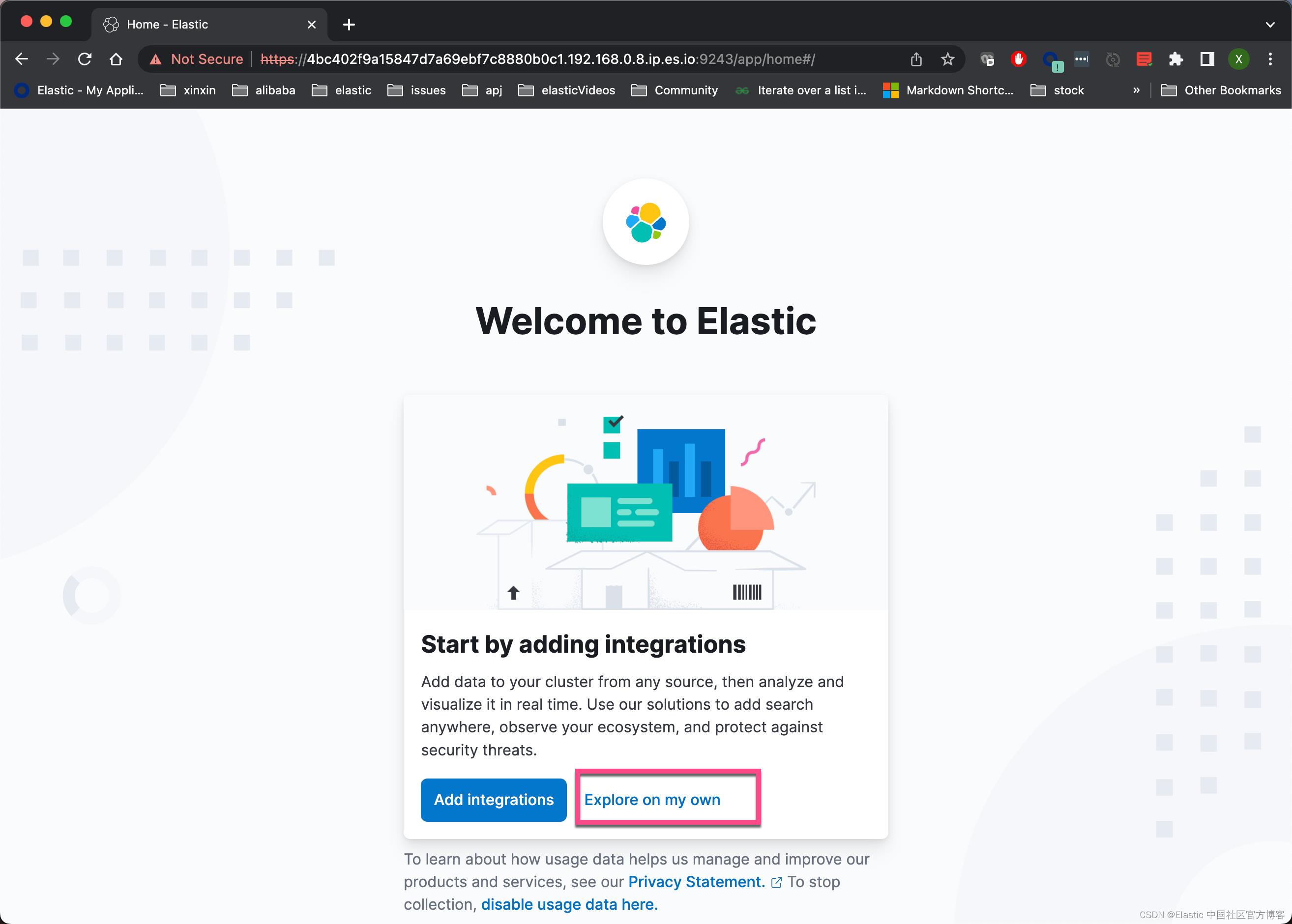
如上所示,我们的 Kibana 已经被成功地启动起来了。点击上面的 Explore on my own 链接:
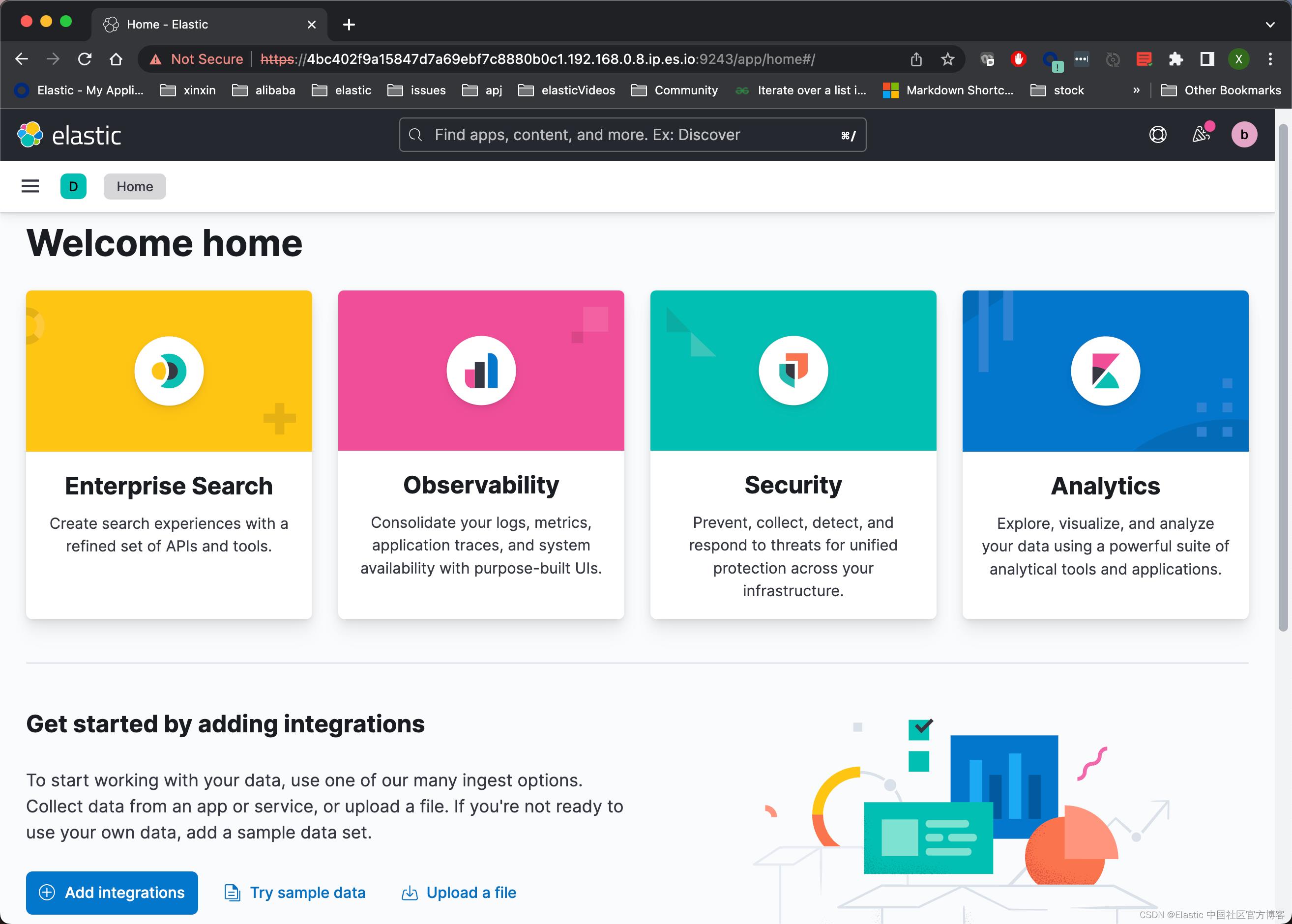
我们就进入到我们最为常见的 Kibana 界面了。这充分地说明了我们的安装是成功的。
可能你想问,如果我想把数据写入到 Elasticsearch 中,那我的这个集群的 endpoint 是什么呢?我们还是回到之前的地址 http://192.168.0.8:12400
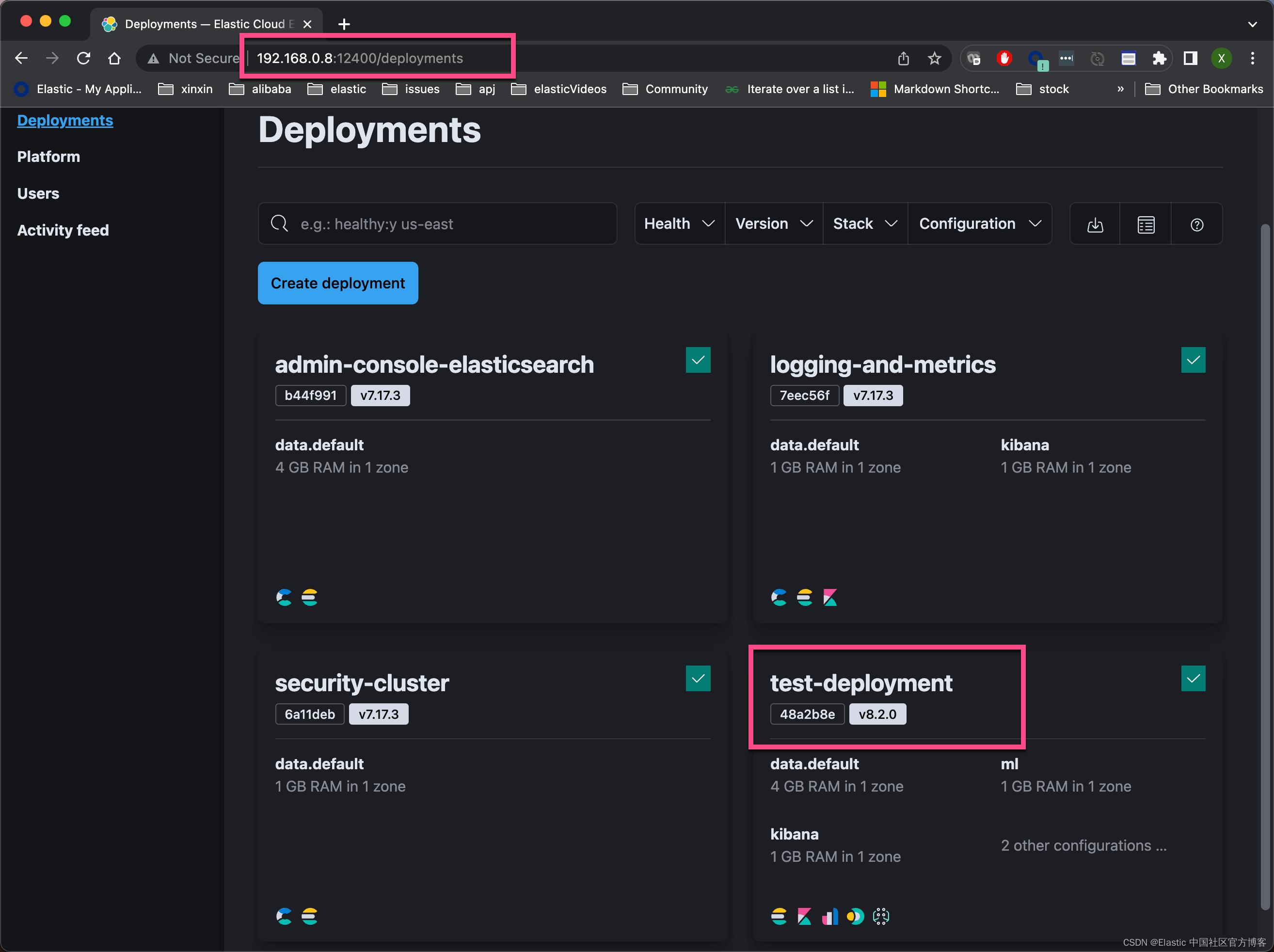
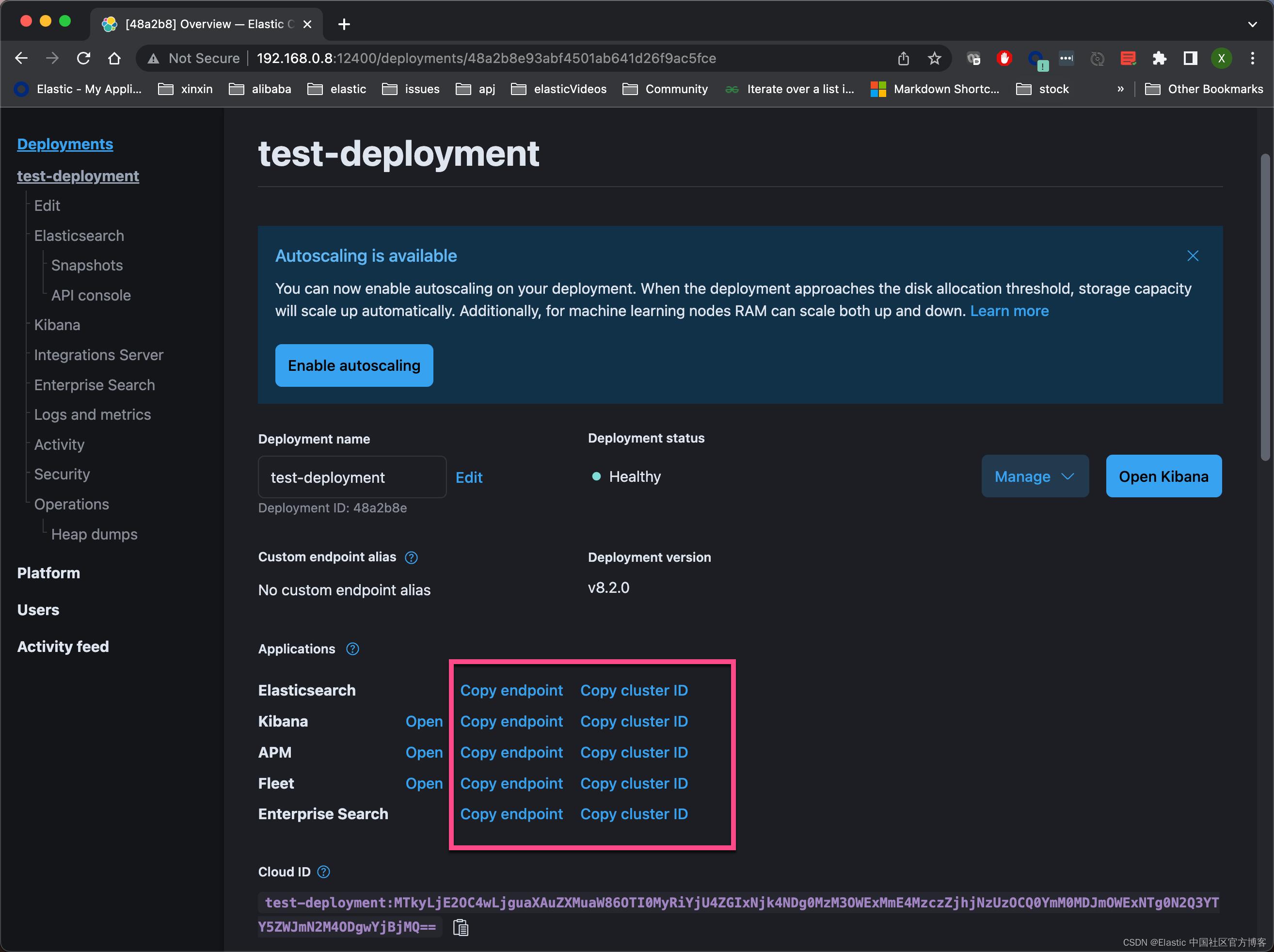
如上所示,我们可以看到 Elastic Stack 相关的所有 endpoints。 比如,针对我的情况,Elasticsearch 的 endpoint 地址为:
https://bb58db16984843379a12a8373f8c7538.192.168.0.8.ip.es.io:9243我们甚至可以直接点击上面的 Open 按钮来启动 APM, Kibana 及 Fleet。上面的界面和 Elastic 在 Elastic Cloud 上的界面非常相似。我们可以尝试官方的部署以得到2个星期的试用。
如何把数据写入到 Elasticsearch 中
我们首先需要得到 ECE 在安装过程中给我们生成的证书呢?我们在 Linux 机器上使用如下的命令:
openssl s_client -showcerts -connect bb58db16984843379a12a8373f8c7538.192.168.0.8.ip.es.io:9243 < /dev/zero请注意,在上面我们的 bb58db16984843379a12a8373f8c7538.192.168.0.8.ip.es.io:9243 是 Elasticsearch 的 endpoint 的地址。上面的命令将生成如下的信息:
$ openssl s_client -showcerts -connect bb58db16984843379a12a8373f8c7538.192.168.0.8.ip.es.io:9243 < /dev/zero
CONNECTED(00000003)
depth=2 CN = elastic ce master
verify error:num=19:self signed certificate in certificate chain
verify return:1
depth=2 CN = elastic ce master
verify return:1
depth=1 CN = elastic ce proxy root
verify return:1
depth=0 CN = elastic ce proxy 192.168.0.8
verify return:1
---
Certificate chain
0 s:CN = elastic ce proxy 192.168.0.8
i:CN = elastic ce proxy root
-----BEGIN CERTIFICATE-----
MIIDqDCCApCgAwIBAgIGAYGFWBhnMA0GCSqGSIb3DQEBCwUAMCAxHjAcBgNVBAMT
FWVsYXN0aWMgY2UgcHJveHkgcm9vdDAeFw0yMjA2MjEwODE5MTJaFw0yMzA3MjQw
ODE5MTJaMCcxJTAjBgNVBAMTHGVsYXN0aWMgY2UgcHJveHkgMTkyLjE2OC4wLjgw
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCP2Caqwm3ClG7nQAhsywH9
ltQjEaBA8qE+e9tP89UnJ09LHojYcedXhVRu5A54xh2PzhEWM1PElxBGWPh8f0a2
R+uj/klosXMM23V5H/mahx+uTiS/AJFNJmwEr2w4bgBBrUnDXU87O3WBPao9+ubl
Hpl0mutMKTBYwrA6sh20XvtjMiCD3yuLfTKtyTF1qX/Y2N4a7ssBSKXpaakAGAbq
NEtmzIcnsZZUYO1Luh7n8nKc48amF8f0NKtPLIqnGL/o0PZHNKyua1NdX8PmTVwb
KeWHsQWCPIQQw7FI9/gCcHglRf+ZO74LTBDX2EI/5WMfg/znGZKiBByqpNRasQ9T
AgMBAAGjgeAwgd0wQQYDVR0RBDowOIILMTkyLjE2OC4wLjiCCzE5Mi4xNjguMC44
ghYqLjE5Mi4xNjguMC44LmlwLmVzLmlvhwTAqAAIMBMGA1UdJQQMMAoGCCsGAQUF
BwMBMEkGA1UdIwRCMECAFCzWAcbVXQyvYUE9Ymz/fMS+KHOcoSCkHjAcMRowGAYD
VQQDExFlbGFzdGljIGNlIG1hc3RlcoIGAYGFV10yMB0GA1UdDgQWBBQkQNMkrjjF
GOlRPEuFBLC+PmyKtTAJBgNVHRMEAjAAMA4GA1UdDwEB/wQEAwIE8DANBgkqhkiG
9w0BAQsFAAOCAQEAzpbU5PmGN9WuKJYohKYho0V76GCdD01PovwPF/hl650tz5Jn
ifn8nh412rCXC81m+idV4igSM19Bxx+hQAhqbngs8Saz13CcjDbD4QlUkWsjLGbM
ME9GicARwIgW34b+pWCEtyMf5QiVLiPOz+b0nnXzHbPWQR6/1yaV6w2IO4IZtgb1
J6isOs9gmlOW6PfcHz1fOAjtV5XP2leDJk+pCDyJkvMlIxOObNZfPGJO3CUqF4HU
c6Ggeiix5Ev/9zbBNT5tLRPYs4IChuzvtD142T3WfOOqYN717TpY+vd+3EU/OrEj
bQF7f7S+qX94qKszsTeqPAPzXJmddaMU+kMPLw==
-----END CERTIFICATE-----
1 s:CN = elastic ce proxy root
i:CN = elastic ce master
-----BEGIN CERTIFICATE-----
MIIDajCCAlKgAwIBAgIGAYGFV10yMA0GCSqGSIb3DQEBCwUAMBwxGjAYBgNVBAMT
EWVsYXN0aWMgY2UgbWFzdGVyMB4XDTIyMDYyMTA4MTgyNFoXDTMyMDYxODA4MTgy
NFowIDEeMBwGA1UEAxMVZWxhc3RpYyBjZSBwcm94eSByb290MIIBIjANBgkqhkiG
9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0ybsisHoE628Od0lfryvfAnKP6u3pWiPiWQp
Sj3I11MCYWh6NKNFQfNiqE5jM3AVzq7Cuc20ygQr1LHeJ3Lpyn/fEOWVnTqKd70T
pN5ubTP4rrx1jI6gkwi7Zcj1j14le0KN7sldaltmfPUt3qgf+a7j99xsBDV4Z4T+
BLsVL2NHFI1a9W6a8htVnt4e43AFTavLLaYNHhJaLyt5ogBPr5tija2wqaj7GKWk
hsz8on8aQ2MNVWDf/+VVT3qTsNM5zWN6sFxWbiYH5de38UBemFlf3YlRQu/NLSFg
U9YtjWlef/U4Wye2SQw7KPSf6HeSFmwFzKWNg4vaJRH4nghKyQIDAQABo4GtMIGq
MBMGA1UdJQQMMAoGCCsGAQUFBwMBMAsGA1UdEQQEMAKCADBJBgNVHSMEQjBAgBSR
qhM9wrv0cP4YY7iI9YutryBkVqEgpB4wHDEaMBgGA1UEAxMRZWxhc3RpYyBjZSBt
YXN0ZXKCBgGBhVdbEjAdBgNVHQ4EFgQULNYBxtVdDK9hQT1ibP98xL4oc5wwDAYD
VR0TBAUwAwEB/zAOBgNVHQ8BAf8EBAMCAfYwDQYJKoZIhvcNAQELBQADggEBAFSh
oJUK6ODHBh0E0z/rWYui3VNikqxo+f33ZDLckFQeozDj8P4G0JGdhgWCihjhUXbF
oqONJxBbEwkTzHjX9KM6Drd5EvyEoovvpKvMlTIKakpm5XQW2Y3NsQj9E9Hp4BAO
1J0cWdYBt3ssEHpeGiEBccEIFfyrGSdb5O2548XGSHxjptqWmxsTO+CTMno9ssEG
9WjguSvrkF6pRah5UVw4I6vwub8ZMz4286clYNca9CY+U4Rc0tJkVxr+hkd4K/5w
f58tMqdsLoyWBFkc/kVh/AxNixO3fL7PJcJ5xQipa74VpuT53XP2lkfkpwgX/Y87
4JQgvQEJuvoaKJX/IGo=
-----END CERTIFICATE-----
2 s:CN = elastic ce master
i:CN = elastic ce master
-----BEGIN CERTIFICATE-----
MIIDUTCCAjmgAwIBAgIGAYGFV1sSMA0GCSqGSIb3DQEBCwUAMBwxGjAYBgNVBAMT
EWVsYXN0aWMgY2UgbWFzdGVyMB4XDTIyMDYyMTA4MTgyM1oXDTMyMDYxODA4MTgy
M1owHDEaMBgGA1UEAxMRZWxhc3RpYyBjZSBtYXN0ZXIwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQCOzPJDF3jTtSnFpI7JLy11pZaIo5Ykvxqw6WqVUrTx
o1IYTz6RftXDldBPJlJUMogEpx17JLhpKSQmXYksa5MzGFOrZBVJxCmFHGeA8Sia
cikgZ4lfZHCY9gY0ymw9AG/bumYWqADUtp6139TaOJzKrSXP5LTqwYdsAQaZl+eD
m+1wqY+6VDD6qdrJcUISiWjq+SZhkJWVMgx4Torqf9KGz2KuwXPHickIRD2g61oK
U6UEkdguz55u1o8JXZC7rexYOhAIzXUbG8QwuA4iGNETKE7AmQ9wLL4yXj8itS2u
4+XT03BVbKhVRoTZ6dVMjcSui/+q1/NDgJTegAe909z1AgMBAAGjgZgwgZUwCwYD
VR0RBAQwAoIAMB0GA1UdDgQWBBSRqhM9wrv0cP4YY7iI9YutryBkVjBJBgNVHSME
QjBAgBSRqhM9wrv0cP4YY7iI9YutryBkVqEgpB4wHDEaMBgGA1UEAxMRZWxhc3Rp
YyBjZSBtYXN0ZXKCBgGBhVdbEjAMBgNVHRMEBTADAQH/MA4GA1UdDwEB/wQEAwIB
9jANBgkqhkiG9w0BAQsFAAOCAQEAaUnNaRCe6rgJmO7QCVly1HK1pR+QIljvvjDd
gwG8VaW46f8ivFnJgRsjZ9FM8PQtJgrf9ihSe0TvousvuzOE1XOOaSDVz3Ie0NxI
T6dPRCH/4SDo7y0BbY7d6//HCH11+J4GTBmrEksOXnfyu4SXCQGkdB5BXTJKoJ9b
vdSGGKqoG7VhRqykYoHl/kbFEXhU8/3IqhBsBm15uwDuVLX2F39B0C+xTPXgS/SG
zIngtOMV2rkjpANC5KvHoX/Zol9lMeACgtR8HEGGBR2b5CGhLlO7Cxgumu+8X4ZK
Nw76R8X+/iic7ftijEvIAyz/A2gNZuCLIWQv9npkb/RJ6C+8yA==
-----END CERTIFICATE-----
---
Server certificate
subject=CN = elastic ce proxy 192.168.0.8
issuer=CN = elastic ce proxy root
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 3265 bytes and written 438 bytes
Verification error: self signed certificate in certificate chain
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: C6F4865780908827A4056B21FEFCFB39F3471A0DF0EC9DD37B587B43796C0316
Session-ID-ctx:
Master-Key: 58FCE590CBCAA914832E3B9A572653CEA6ADED15A88AB52E52F6DAA34674B6EE917D41FAB7E67DF56A6D670057458568
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket:
0000 - 3e 10 e0 ff 6a 91 f7 d5-4b 08 10 d5 29 65 c5 37 >...j...K...)e.7
0010 - ac 69 07 c4 ec 3e 3b 40-8e 0e 50 ac 2f 28 b5 d1 .i...>;@..P./(..
0020 - f7 17 4b 71 ce 8b 66 04-de b0 2b 66 fc 63 18 11 ..Kq..f...+f.c..
0030 - ee 95 b0 87 ee 6b 71 0d-91 e5 ee ca e2 8f 61 21 .....kq.......a!
0040 - 63 52 4b 89 53 e9 d5 88-3d c9 62 3b 52 43 0b 9f cRK.S...=.b;RC..
0050 - 74 d9 5e d7 c4 1b d0 77-ca 43 00 5f ac 88 93 02 t.^....w.C._....
0060 - 0c 3b 7e e4 93 b4 40 9d-8f 63 68 89 5b 76 2b cc .;~...@..ch.[v+.
0070 - ea d5 28 85 9d 7d e7 e0-fe 16 df bc e9 87 18 c5 ..(............
0080 - 90 .
Start Time: 1655861073
Timeout : 7200 (sec)
Verify return code: 19 (self signed certificate in certificate chain)
Extended master secret: no
---
HTTP/1.1 431 Request Header Fields Too Large
Content-Type: text/plain; charset=utf-8
Connection: close将输出中显示的最后一个证书保存到本地文件,在此示例中为 elastic-ece-ca-cert.pem:
$ cat << EOF > ~/elastic-ece-ca-cert.pem
> -----BEGIN CERTIFICATE-----
> MIIDUTCCAjmgAwIBAgIGAYGFV1sSMA0GCSqGSIb3DQEBCwUAMBwxGjAYBgNVBAMT
> EWVsYXN0aWMgY2UgbWFzdGVyMB4XDTIyMDYyMTA4MTgyM1oXDTMyMDYxODA4MTgy
> M1owHDEaMBgGA1UEAxMRZWxhc3RpYyBjZSBtYXN0ZXIwggEiMA0GCSqGSIb3DQEB
> AQUAA4IBDwAwggEKAoIBAQCOzPJDF3jTtSnFpI7JLy11pZaIo5Ykvxqw6WqVUrTx
> o1IYTz6RftXDldBPJlJUMogEpx17JLhpKSQmXYksa5MzGFOrZBVJxCmFHGeA8Sia
> cikgZ4lfZHCY9gY0ymw9AG/bumYWqADUtp6139TaOJzKrSXP5LTqwYdsAQaZl+eD
> m+1wqY+6VDD6qdrJcUISiWjq+SZhkJWVMgx4Torqf9KGz2KuwXPHickIRD2g61oK
> U6UEkdguz55u1o8JXZC7rexYOhAIzXUbG8QwuA4iGNETKE7AmQ9wLL4yXj8itS2u
> 4+XT03BVbKhVRoTZ6dVMjcSui/+q1/NDgJTegAe909z1AgMBAAGjgZgwgZUwCwYD
> VR0RBAQwAoIAMB0GA1UdDgQWBBSRqhM9wrv0cP4YY7iI9YutryBkVjBJBgNVHSME
> QjBAgBSRqhM9wrv0cP4YY7iI9YutryBkVqEgpB4wHDEaMBgGA1UEAxMRZWxhc3Rp
> YyBjZSBtYXN0ZXKCBgGBhVdbEjAMBgNVHRMEBTADAQH/MA4GA1UdDwEB/wQEAwIB
> 9jANBgkqhkiG9w0BAQsFAAOCAQEAaUnNaRCe6rgJmO7QCVly1HK1pR+QIljvvjDd
> gwG8VaW46f8ivFnJgRsjZ9FM8PQtJgrf9ihSe0TvousvuzOE1XOOaSDVz3Ie0NxI
> T6dPRCH/4SDo7y0BbY7d6//HCH11+J4GTBmrEksOXnfyu4SXCQGkdB5BXTJKoJ9b
> vdSGGKqoG7VhRqykYoHl/kbFEXhU8/3IqhBsBm15uwDuVLX2F39B0C+xTPXgS/SG
> zIngtOMV2rkjpANC5KvHoX/Zol9lMeACgtR8HEGGBR2b5CGhLlO7Cxgumu+8X4ZK
> Nw76R8X+/iic7ftijEvIAyz/A2gNZuCLIWQv9npkb/RJ6C+8yA==
> -----END CERTIFICATE-----
> EOF我们把上面的证书拷贝到 Metricbeat 的安装目录的根目录中。如果你对 Metricbeat 的安装和使用还不是很熟的话,请阅读我之前的文章 “Beats:Beats 入门教程 (二)”。这样在 Metricbeat 的安装目录中是这样的:
$ pwd
/Users/liuxg/elastic/metricbeat-8.2.0-darwin-aarch64
$ ls
LICENSE.txt fields.yml metricbeat.yml
NOTICE.txt kibana module
README.md logs modules.d
data metricbeat
elastic-ece-ca-cert.pem metricbeat.reference.yml我们可以看到 elastic-ece-ca-cert.pem 已经被拷贝过来了。
我们接着按照如下的步骤来配置 metricbeat.yml 文件:
metricbeat.yml
output.elasticsearch:
# Array of hosts to connect to.
hosts: ["https://bb58db16984843379a12a8373f8c7538.192.168.0.8.ip.es.io:9243"]
# Protocol - either `http` (default) or `https`.
protocol: "https"
# Authentication credentials - either API key or username/password.
#api_key: "id:api_key"
username: "elastic"
password: "G4lrXzbGrTB2OYJqhyLFVR8N"
ssl.certificate_authorities: ["elastic-ece-ca-cert.pem"]你需要根据自己的 Elasticsearch 集群的 endpoint 及密码进行相应的修改。我们接下来使用如下的命令来测试:
$ ./metricbeat test config
Config OK$ ./metricbeat test output
elasticsearch: https://bb58db16984843379a12a8373f8c7538.192.168.0.8.ip.es.io:9243...
parse url... OK
connection...
parse host... OK
dns lookup... OK
addresses: 192.168.0.8
dial up... OK
TLS...
security: server's certificate chain verification is enabled
handshake... OK
TLS version: TLSv1.2
dial up... OK
talk to server... OK
version: 8.2.0上面显示我们的证书是成功的。我们的 Metricbeat 也可以成功地连接到 Elasticsearch。
我们接下来尝试把当前电脑的 metric 发送到 Elasticsearch 中。在做之前,我们还需要在 metricbeat.yml 文件中配置 Kibana 的 endpoint 及证书,这是因为 Kibana 的 endpoint 的 url 和 Elasticsearch 的是不一样的。我们如法炮制,生成另外一个连接 Kibana 的证书 elastic-ece-ca-cert-kibana.pem。
metricbeat.yml
setup.kibana:
# Kibana Host
# Scheme and port can be left out and will be set to the default (http and 5601)
# In case you specify and additional path, the scheme is required: http://localhost:5601/path
# IPv6 addresses should always be defined as: https://[2001:db8::1]:5601
host: "https://4bc402f9a15847d7a69ebf7c8880b0c1.192.168.0.8.ip.es.io:9243"
protocol: "https"
# Authentication credentials - either API key or username/password.
username: "elastic"
password: "G4lrXzbGrTB2OYJqhyLFVR8N"
ssl.certificate_authorities: ["elastic-ece-ca-cert-kibana.pem"]在上面,请注意 endpoint 和证书和 Elasticsearch 是不一样的。
我们接着使用如下的命令来进行 setup:
$ ./metricbeat setup
Overwriting ILM policy is disabled. Set `setup.ilm.overwrite: true` for enabling.
Index setup finished.
Loading dashboards (Kibana must be running and reachable)
Loaded dashboards从上面的输出中,我们可以看到是成功的。
我们接下来直接启动 Metricbeat 就可以了:
./metricbeat -e
我们接下来直接到 Kibana 的界面中来查看数据:
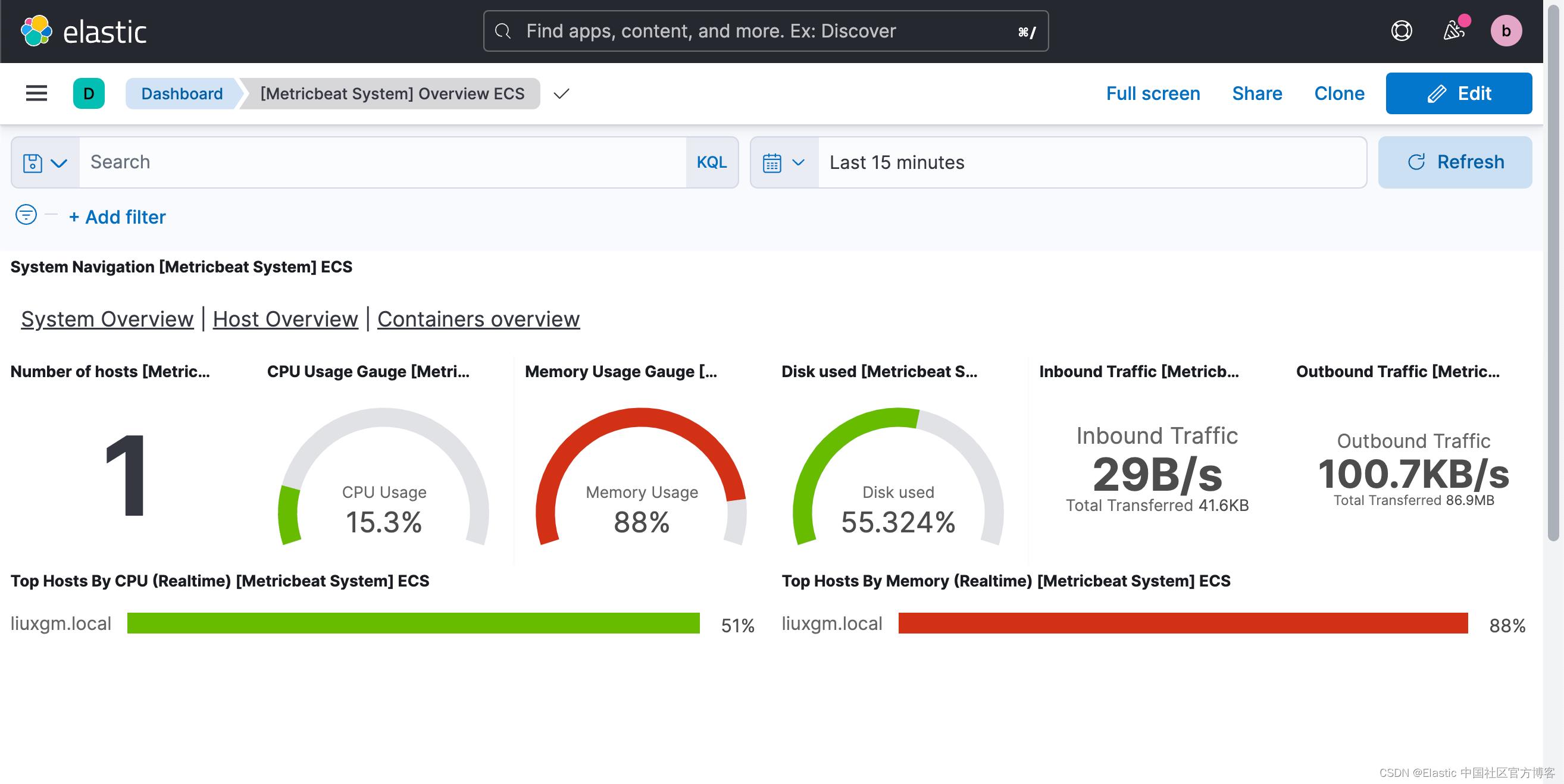
我们可以看到数据已经被成功地采集进来了。我们甚至可以查看它的 Dashboard:
移除 Elastic Cloud Enterprise
由于以下原因之一,你可能需要删除 Elastic Cloud Enterprise:
- 如果安装过程未成功完成并且你无法解决问题。
- 如果你要取消配置主机并希望删除已安装的 Elastic Cloud Enterprise 软件。
你可以通过移除主机上的所有 Docker 容器来移除 Elastic Cloud Enterprise:
docker rm -f frc-runners-runner frc-allocators-allocator $(docker ps -a -q); sudo rm -rf /mnt/data/elastic/ && docker ps -a如果你计划在主机上重新安装 Elastic Cloud Enterprise,请确保先从 Cloud UI 中删除主机。 如果主机仍与你的旧 Elastic Cloud Enterprise 安装相关联,则重新安装可能会失败。
警告:在安装期间,系统会生成放入 /mnt/data/elastic/bootstrap-state/bootstrap-secrets.json 机密文件的 secrets,除非你使用 --host-storage-path 参数传入不同的路径。 通过将 bootstrap-secrets.json 文件中的信息从其默认位置移除并将其放入安全的存储位置,以确保信息的安全。
总结
ECE 执行所有配置,如果您需要监控组件和其他 X-Pack 功能,它能够自动配置您的集群以管理所有必需的功能。如果您需要管理多个 Elasticsearch/Kibana 集群,ECE 非常有用,因为它消除了所有基础架构问题。
参考:
【1】Manage security certificates | Elastic Cloud Enterprise Reference [2.3] | Elastic
以上是关于Elasticsearch:部署 ECE (Elastic Cloud Enterprise)的主要内容,如果未能解决你的问题,请参考以下文章