Linux入侵检测
Posted xiaotanggao
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Linux入侵检测相关的知识,希望对你有一定的参考价值。
入侵检测
查看日志
系统日志/var/log/messages
- 记录服务启动,服务停止,身份切换,系统运行状态信息,网络错误,IO错误等等
- 动态查看
[root@server5 ~]# tail -f /var/log/messages
Dec 15 11:53:07 server1 avahi-daemon[732]: Withdrawing address record for fd15:4ba5:5a2b:1008:4da0:9d6a:40a1:1e34 on ens33.
Dec 15 11:53:07 server1 avahi-daemon[732]: Registering new address record for fe80::d88e:564d:cf7b:13ef on ens33.*.
Dec 15 11:53:07 server1 NetworkManager[800]: <info> [1639540387.4543] device (ens33): ipv6: duplicate address check failed for the fd15:4ba5:5a2b:1008:4da0:9d6a:40a1:1e34/64 lft 86400sec pref 14400sec lifetime 276-276[14400,86400] dev 2 flags noprefixroute,tentative src kernel address
Dec 15 11:53:07 server1 avahi-daemon[732]: Registering new address record for fd15:4ba5:5a2b:1008:b574:ef81:d29e:3c75 on ens33.*.
Dec 15 11:53:07 server1 avahi-daemon[732]: Withdrawing address record for fe80::d88e:564d:cf7b:13ef on ens33.
Dec 15 11:53:31 server1 systemd-logind: New session 3 of user root.
Dec 15 11:53:31 server1 systemd: Started Session 3 of user root.
Dec 15 11:54:15 server1 journal: shell-extensions did not set error for gs_plugin_refresh
Dec 15 11:55:16 server1 chronyd[763]: Selected source 202.118.1.130
Dec 15 11:56:21 server1 chronyd[763]: Source 162.159.200.123 replaced with 119.28.206.193
安全日志/var/log/secure
- 记录了安全信息,系统登录,网络连接等信息
- 查看远程登录失败日志
[root@server5 ~]# cat /var/log/secure |grep Failed
Dec 15 12:14:51 server1 sshd[4917]: Failed password for root from 192.168.139.10 port 43456 ssh2
Dec 15 12:14:59 server1 sshd[4917]: Failed password for root from 192.168.139.10 port 43456 ssh2
- 查看远程登录成功日志
[root@server5 ~]# cat /var/log/secure |grep Accepted
Dec 15 13:38:18 server5 sshd[47938]: Accepted password for root from 192.168.139.10 port 43458 ssh2
- 统计次数
[root@server5 ~]# grep -i Accepted /var/log/secure |awk 'print $(NF-3)' |sort |uniq -c
3 192.168.139.10
1 192.168.139.20
# 确保统计不出错
[root@server5 ~]# grep -i Accepted /var/log/secure |awk 'print $(NF-3)' |grep '^[0-9]' |sort |uniq -c |sort -rn
3 192.168.139.10
1 192.168.139.20
last用户登录信息
- last
[root@server5 ~]# last
zhangsan pts/2 192.168.139.10 Wed Dec 15 13:52 still logged in
root pts/2 192.168.139.20 Wed Dec 15 13:44 - 13:44 (00:00)
root pts/2 192.168.139.10 Wed Dec 15 13:41 - 13:41 (00:00)
root pts/2 192.168.139.10 Wed Dec 15 13:40 - 13:40 (00:00)
root pts/2 192.168.139.10 Wed Dec 15 13:38 - 13:38 (00:00)
- 踢除用户
[root@server5 ~]# w
13:54:03 up 2:05, 4 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root :0 :0 一16 ?xdm? 1:43 0.52s /usr/libexec/gnome-session-binary --session gnome-cla
root pts/0 :0 一16 19:47 0.17s 0.07s bash
root pts/1 192.168.139.1 11:53 3.00s 0.14s 0.00s w
zhangsan pts/2 192.168.139.10 13:52 1:09 0.01s 0.01s -bash
[root@server5 ~]# pkill -t pts/2
[zhangsan@server5 ~]$ Connection to 192.168.139.50 closed by remote host.
Connection to 192.168.139.50 closed.
[root@server5 ~]# cat /var/log/messages|grep zhangsan
Dec 15 13:52:54 server5 systemd: Created slice User Slice of zhangsan.
Dec 15 13:52:54 server5 systemd: Started Session 23 of user zhangsan.
Dec 15 13:52:54 server5 systemd-logind: New session 23 of user zhangsan.
Dec 15 13:58:49 server5 systemd: Removed slice User Slice of zhangsan.
- 查看最后5条
[root@server5 ~]# last -a -5
zhangsan pts/2 Wed Dec 15 13:52 - 13:58 (00:05) 192.168.139.10
root pts/2 Wed Dec 15 13:44 - 13:44 (00:00) 192.168.139.20
root pts/2 Wed Dec 15 13:41 - 13:41 (00:00) 192.168.139.10
root pts/2 Wed Dec 15 13:40 - 13:40 (00:00) 192.168.139.10
root pts/2 Wed Dec 15 13:38 - 13:38 (00:00) 192.168.139.10
wtmp begins Sat Jul 24 17:36:07 2021
- 查看指定时间
查看2021-12-15 14:00:00之前的信息
[root@server5 ~]# last -a -t 20211215140000
zhangsan pts/2 Wed Dec 15 13:52 - 13:58 (00:05) 192.168.139.10
root pts/2 Wed Dec 15 13:44 - 13:44 (00:00) 192.168.139.20
root pts/2 Wed Dec 15 13:41 - 13:41 (00:00) 192.168.139.10
root pts/2 Wed Dec 15 13:40 - 13:40 (00:00) 192.168.139.10
root pts/2 Wed Dec 15 13:38 - 13:38 (00:00) 192.168.139.10
root pts/2 Wed Dec 15 12:15 - 13:36 (01:21) 192.168.139.10
- 查看登录系统的用户的信息
[root@server5 ~]# last -a -f /var/log/btmp
zhagsan ssh:notty Wed Dec 15 13:52 gone - no logout 192.168.139.10
btmp begins Wed Dec 15 13:52:46 2021
- 查看登录日志
[root@server5 ~]# lastlog
用户名 端口 来自 最后登陆时间
root pts/2 192.168.139.20 三 12月 15 13:44:35 +0800 2021
bin **从未登录过**
daemon **从未登录过**
nfsnobody **从未登录过**
gdm :0 一 12月 13 16:50:55 +0800 2021
gnome-initial-setup **从未登录过**
tcpdump **从未登录过**
avahi **从未登录过**
zhangsan pts/2 192.168.139.10 三 12月 15 13:52:54 +0800 2021
- 统计当前在线状态
[root@server5 ~]# w
14:12:18 up 2:23, 3 users, load average: 0.12, 0.06, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root :0 :0 一16 ?xdm? 1:52 0.52s /usr/libexec/gnome-session-binary --session gnome-cla
root pts/0 :0 一16 38:02 0.17s 0.07s bash
root pts/1 192.168.139.1 11:53 2.00s 0.20s 0.00s w
- 踢除用户
[root@server5 ~]# w
13:54:03 up 2:05, 4 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root :0 :0 一16 ?xdm? 1:43 0.52s /usr/libexec/gnome-session-binary --session gnome-cla
root pts/0 :0 一16 19:47 0.17s 0.07s bash
root pts/1 192.168.139.1 11:53 3.00s 0.14s 0.00s w
zhangsan pts/2 192.168.139.10 13:52 1:09 0.01s 0.01s -bash
[root@server5 ~]# pkill -t pts/2
[zhangsan@server5 ~]$ Connection to 192.168.139.50 closed by remote host.
Connection to 192.168.139.50 closed.
[root@server5 ~]# cat /var/log/messages|grep zhangsan
Dec 15 13:52:54 server5 systemd: Created slice User Slice of zhangsan.
Dec 15 13:52:54 server5 systemd: Started Session 23 of user zhangsan.
Dec 15 13:52:54 server5 systemd-logind: New session 23 of user zhangsan.
Dec 15 13:58:49 server5 systemd: Removed slice User Slice of zhangsan.
计划任务
- 注意查看是否被恶意改动
[root@server5 ~]# crontab -l
* * * * * echo hello >> /root/1.txt
[root@server5 ~]# cat /var/spool/cron/root
* * * * * echo hello >> /root/1.txt
查看计划任务日志
[root@server5 ~]# tail -5 /var/log/cron
Dec 15 14:01:01 server5 CROND[48405]: (root) CMD (run-parts /etc/cron.hourly)
Dec 15 14:01:01 server5 run-parts(/etc/cron.hourly)[48405]: starting 0anacron
Dec 15 14:01:01 server5 run-parts(/etc/cron.hourly)[48414]: finished 0anacron
Dec 15 14:10:01 server5 CROND[48511]: (root) CMD (/usr/lib64/sa/sa1 1 1)
Dec 15 14:14:53 server5 crontab[48557]: (root) LIST (root)
防止日志被恶意删除
- chattr +a 只能追加
[root@server5 ~]# chattr +a /var/log/secure
[root@server5 ~]# lsattr /var/log/secure
-----a---------- /var/log/secure
查看启动时默认加载文件
-
注意查看是否被恶意改动
-
/etc/rc.local
[root@server5 ~]# cat /etc/rc.local
#!/bin/bash
# THIS FILE IS ADDED FOR COMPATIBILITY PURPOSES
#
# It is highly advisable to create own systemd services or udev rules
# to run scripts during boot instead of using this file.
#
# In contrast to previous versions due to parallel execution during boot
# this script will NOT be run after all other services.
#
# Please note that you must run 'chmod +x /etc/rc.d/rc.local' to ensure
# that this script will be executed during boot.
touch /var/lock/subsys/local
查看异常流量
iftop动态查看网卡接口流量
[root@server1 ~]# yum install -y epel-release.noarch
[root@server1 ~]# yum install -y iftop
[root@server1 ~]# iftop -i ens33
interface: ens33
IP address is: 192.168.139.10
MAC address is: 00:0c:29:17:9d:b3
# 键入q退出
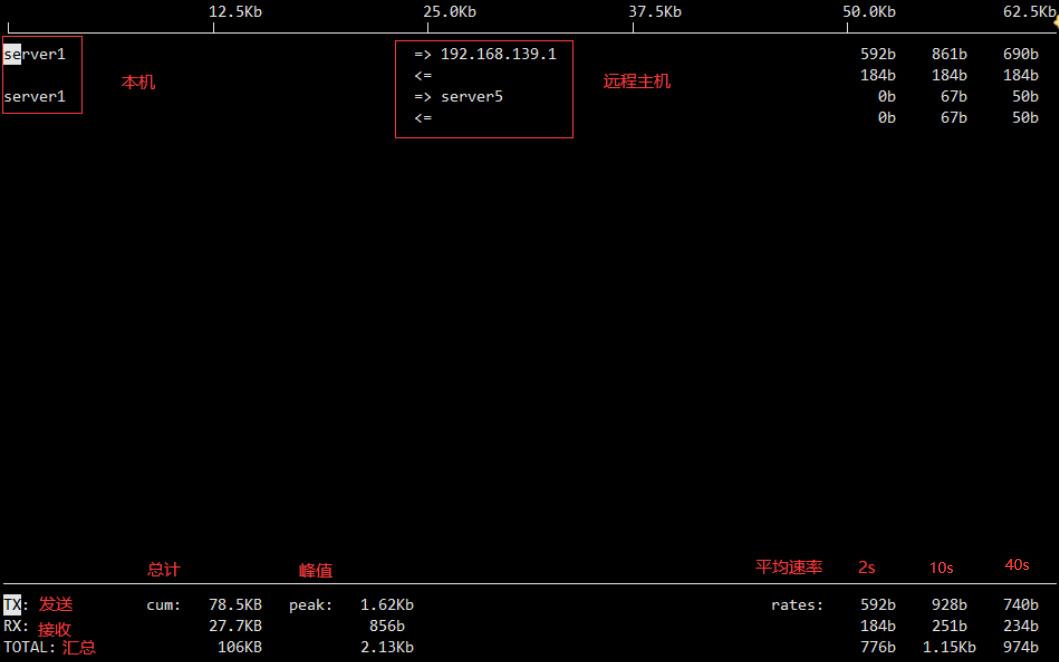
流量监控
- 常用监控软件zabbix,Prometheus等
数据包抓取
- 常用抓包工具:wireshark,tcpdump,sniffer
- 这里重点介绍tcpdump(不需要图形化界面,常用于生产环境抓包,但抓取的包不便于分析,常将tcpdump抓取的包导入到wireshark中分析)
- tcpdump安装
[root@server1 ~]# yum install -y tcpdump.x86_64
- 帮助信息
[root@server1 ~]# tcpdump --help
tcpdump version 4.9.2
libpcap version 1.5.3
OpenSSL 1.0.2k-fips 26 Jan 2017
Usage: tcpdump [-aAbdDefhHIJKlLnNOpqStuUvxX#] [ -B size ] [ -c count ]
[ -C file_size ] [ -E algo:secret ] [ -F file ] [ -G seconds ]
[ -i interface ] [ -j tstamptype ] [ -M secret ] [ --number ]
[ -Q|-P in|out|inout ]
[ -r file ] [ -s snaplen ] [ --time-stamp-precision precision ]
[ --immediate-mode ] [ -T type ] [ --version ] [ -V file ]
[ -w file ] [ -W filecount ] [ -y datalinktype ] [ -z postrotate-command ]
[ -Z user ] [ expression ]
[root@server1 ~]# man tcpdump
- 常用选项汇总
| 选项 | 说明 | 用法 |
|---|---|---|
| -i | 指定网络接口 | -i any 所有网卡接口 |
| -nn | 直接以IP和端口号显示 | |
| -v | 输出详细信息 | -nnv 可连用 |
| -c | 指定抓包数 | -c 100 |
| -w | 指定保存文件 | -w file1.tcpdump |
| -r | 指定读取文件 | -r file1.tcpdump |
| port | 指定端口 | port 22 |
| net | 指定网段 | net 192.168.139.0/24 |
| host | 指定主机 | host 192.168.139.10 |
| 指定协议 | arp | icmp | udp | tcp | ip | vrrp | |
| and|or|not | 指定逻辑关系 | host 192.168.139.10 and port 22 |
| tcp[13] | 指定TCP的标志位 | tcp[13]==18 |
- 抓取指定数量的包
[root@server1 ~]# tcpdump -i ens33 -nnv -c 3
tcpdump: listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes
01:31:59.425640 IP (tos 0x10, ttl 64, id 20374, offset 0, flags [DF], proto TCP (6), length 164)
192.168.139.10.22 > 192.168.139.1.50180: Flags [P.], cksum 0x97f3 (incorrect -> 0xa671), seq 2409031745:2409031869, ack 3240402273, win 257, length 124
01:31:59.426051 IP (tos 0x10, ttl 64, id 20375, offset 0, flags [DF], proto TCP (6), length 332)
192.168.139.10.22 > 192.168.139.1.50180: Flags [P.], cksum 0x989b (incorrect -> 0xd4ee), seq 124:416, ack 1, win 257, length 292
01:31:59.426336 IP (tos 0x0, ttl 128, id 20424, offset 0, flags [DF], proto TCP (6), length 40)
192.168.139.1.50180 > 192.168.139.10.22: Flags [.], cksum 0x6c54 (correct), ack 416, win 4106, length 0
3 packets captured
3 packets received by filter
0 packets dropped by kernel
- 保存抓取的包
保存
[root@server1 ~]# tcpdump -i ens33 -nnv -w ./file1.tcpdump
tcpdump: listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes
^C105 packets captured
109 packets received by filter
0 packets dropped by kernel
读取文件(建议导出到wireshark中)
[root@server1 ~]# tcpdump -i ens33 -nnv -r ./file1.tcpdump
- 抓取指定端口数据包
[root@server1 ~]# tcpdump -i ens33 -nnv port 22
- 抓取指定网段的包
[root@server1 ~]# tcpdump -i ens33 -nnv net 192.168.139.0/24
- 抓取指定主机的包
[root@server1 ~]# tcpdump -i ens33 -nnv host 192.168.139.50
- 指定协议
[root@server1 ~]# tcpdump -i ens33 -nnv arp
- 多条件(and|or|not)
[root@server1 ~]# tcpdump -i ens33 -nnv host 192.168.139.50 and port 22
[root@server1 ~]# tcpdump -i ens33 -nnv port 22 or 80
[root@server1 ~]# tcpdump -i ens33 -nnv not port 22
括号需要进行转义
[root@server1 ~]# tcpdump -i ens33 -nnv host 192.168.139.50 and \\( port 22 or 80\\)
- 按照TCP的标志位来抓包
仅抓取SYN=1的包
|C|E|U|A|P|R|S|F|
|--------------- |
|0 0 0 0 0 0 1 0 |
|--------------- |
|7 6 5 4 3 2 1 0|
tcp[13] == 2^1
[root@server1 ~]# tcpdump -i ens33 -nnv tcp[13]==2
tcpdump: listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes
02:27:09.131125 IP (tos 0x0, ttl 64, id 3847, offset 0, flags [DF], proto TCP (6), length 60)
192.168.139.50.54412 > 192.168.139.10.22: Flags [S], cksum 0x4710 (correct), seq 2439561938, win 29200, options [mss 1460,sackOK,TS val 10407381 ecr 0,nop,wscale 7], length 0
抓取SYN=1且Ack=1的包
|C|E|U|A|P|R|S|F|
|--------------- |
|0 0 0 1 0 0 1 0 |
|--------------- |
|7 6 5 4 3 2 1 0|
tcp[13] == 2^1 + 2^4 = 18
[root@server1 ~]# tcpdump -i ens33 -nnv tcp[13]==18
tcpdump: listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes
02:30:17.991000 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
192.168.139.10.22 > 192.168.139.50.54414: Flags [S.], cksum 0x97bc (incorrect -> 0x8e2a), seq 1084900368, ack 3292405268, win 28960, options [mss 1460,sackOK,TS val 26330013 ecr 10596245,nop,wscale 7], length 0
查看可疑进程
PS
[root@server1 ~]# ps
PID TTY TIME CMD
1732 pts/1 00:00:00 bash
2104 pts/1 00:00:00 ps
[root@server1 ~]# pstree
systemd─┬─NetworkManager───2*[NetworkManager]
├─atd
├─auditd───auditd
├─crond
├─dbus-daemon
├─irqbalance
├─login───bash
├─lvmetad
├─master─┬─pickup
│ └─qmgr
├─polkitd───6*[polkitd]
├─rsyslogd───2*[rsyslogd]
├─sshd─┬─sshd───bash───pstree
│ └─sshd───bash
├─systemd-journal
├─systemd-logind
├─systemd-udevd
└─tuned───4*[tuned]
[root@server1 ~]# pstree -p
systemd(1)─┬─NetworkManager(672)─┬─NetworkManager(685)
│ └─NetworkManager(688)
├─atd(677)
├─auditd(640)───auditd(641)
├─crond(675)
├─dbus-daemon(664)
├─irqbalance(669)
├─login(679)───bash(1398)
├─lvmetad(514)
├─master(1096)─┬─pickup(1969)
│ └─qmgr(1106)
├─polkitd(671)─┬─polkitd(682)
│ ├─polkitd(683)
│ ├─polkitd(684)
│ ├─polkitd(686)
│ ├─polkitd(692)
│ └─polkitd(700)
├─rsyslogd(898)─┬─rsyslogd(912)
│ └─rsyslogd(921)
├─sshd(895)─┬─sshd(1730)───bash(1732)───pstree(2107)
│ └─sshd(1986)───bash(1988)
├─systemd-journal(495)
├─systemd-logind(668)
├─systemd-udevd(520)
└─tuned(897)─┬─tuned(1303)
├─tuned(1304)
├─tuned(1306)
└─tuned(1308)
top
[root@server1 ~]# top
top - 02:37:54 up 7:31, 3 users, load average: 0.00, 0.01, 0.05
Tasks: 109 total, 1 running, 108 sleeping, 0 stopped, 0 zombie
%Cpu(s): 0.0 us, 0.0 sy, 0.0 ni,100.0 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
KiB Mem : 1863016 total, 1313968 free, 139552 used, 409496 buff/cache
KiB Swap: 2097148 total, 2097148 free, 0 used. 1568588 avail Mem
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
1 root 20 0 125396 3864 2580 S 0.0 0.2 0:02.82 systemd
2 root 20 0 0 0 0 S 0.0 0.0 0:00.04 kthreadd
4 root 0 -20 0 0 0 S 0.0 0.0 0:00.00 kworker/0:0H
6 root 20 0 0 0 0 S 0.0 0.0 0:00.60 ksoftirqd/0
7 root rt 0 0 0 0 S 0.0 0.0 0:00.11 migration/0
netstat | ss
[root@server1 ~]# ss -tnalp
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:* users:(("sshd",pid=895,fd=3))
LISTEN 0 100 127.0.0.1:25 *:* users:(("master",pid=1096,fd=13))
LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=895,fd=4))
LISTEN 0 100 [::1]:25 [::]:* users:(("master",pid=1096,fd=14))
lsof
查看文件正在被哪个进程使用
[root@server1 ~]# yum install -y lsof.x86_64
[root@server1 ~]# lsof /usr/sbin/vsftpd
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
vsftpd 2305 root txt REG 253,0 175440 34598 /usr/sbin/vsftpd
查看端口对应的进程
[root@server1 ~]# lsof -i:21
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
vsftpd 2305 root 4u IPv6 28498 0t0 TCP *:ftp (LISTEN)
[root@server1 ~]# lsof -i:80
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
httpd 2207 root 4u IPv6 28161 0t0 TCP *:http (以上是关于Linux入侵检测的主要内容,如果未能解决你的问题,请参考以下文章