buuoj re逆向前32题writeup(截图+c++源码+过程)
Posted weixin_51275728
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了buuoj re逆向前32题writeup(截图+c++源码+过程)相关的知识,希望对你有一定的参考价值。
萌新第一次写这玩意,如有错误,请多指教。
RE
1、easyre 明码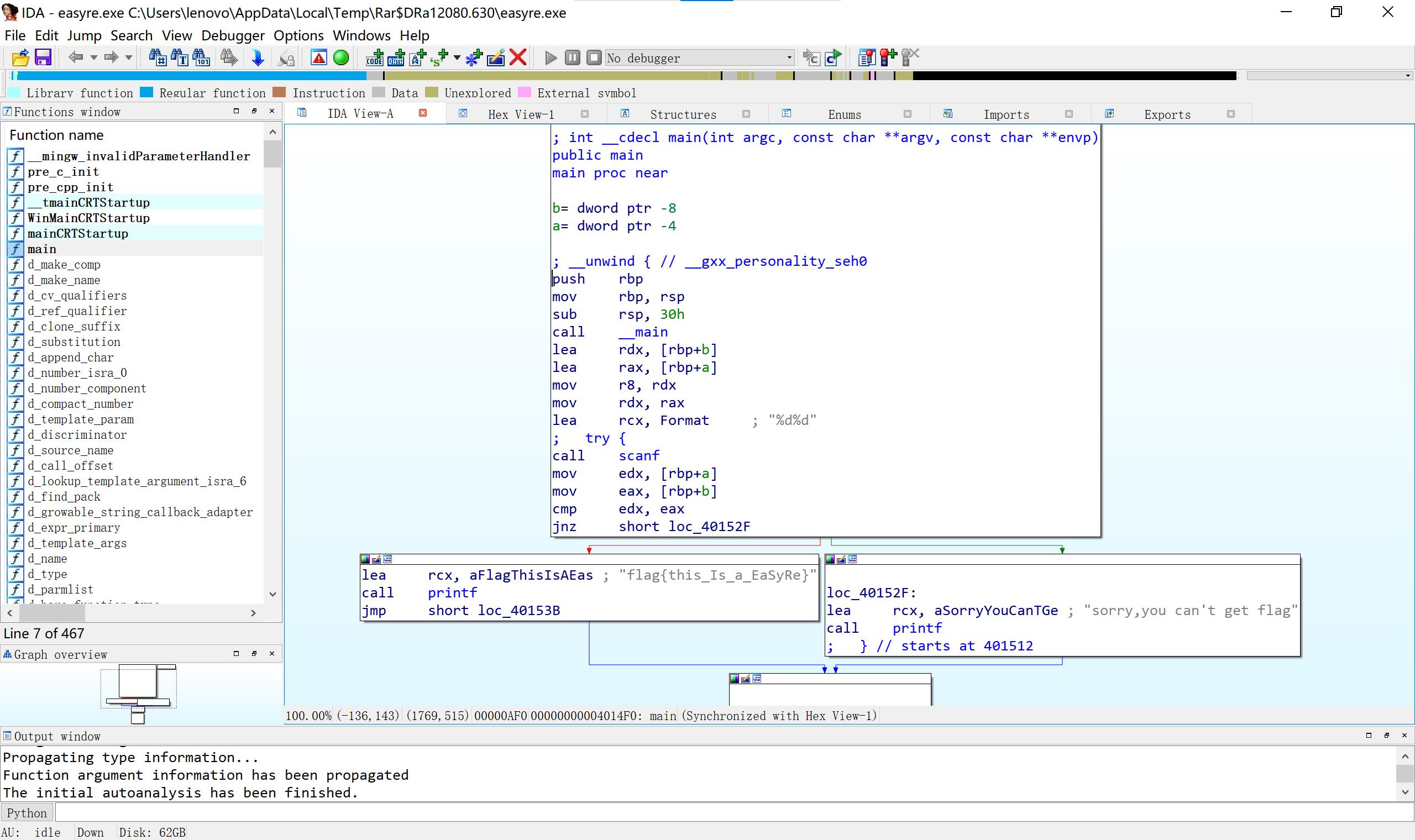
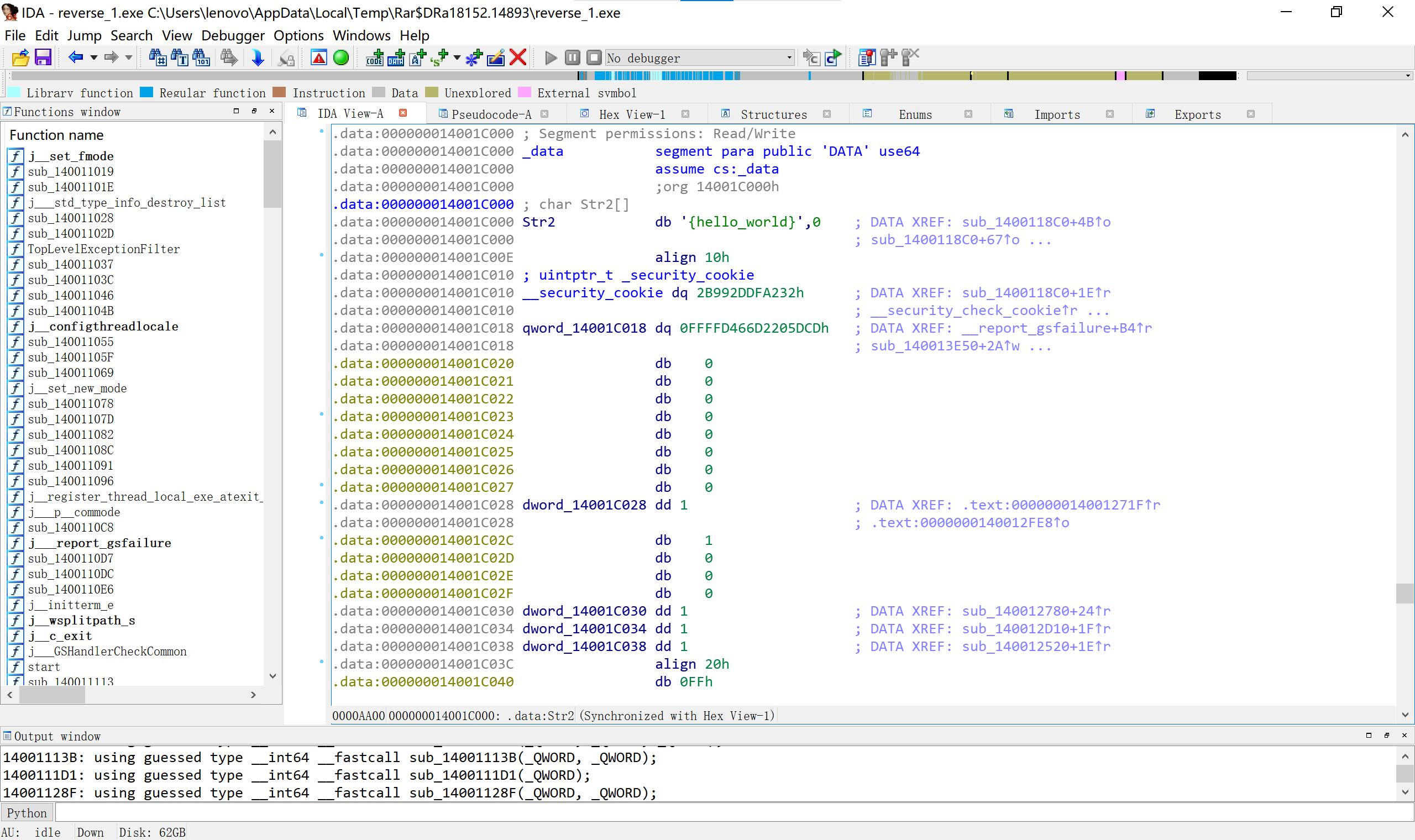
2、Reverse1明码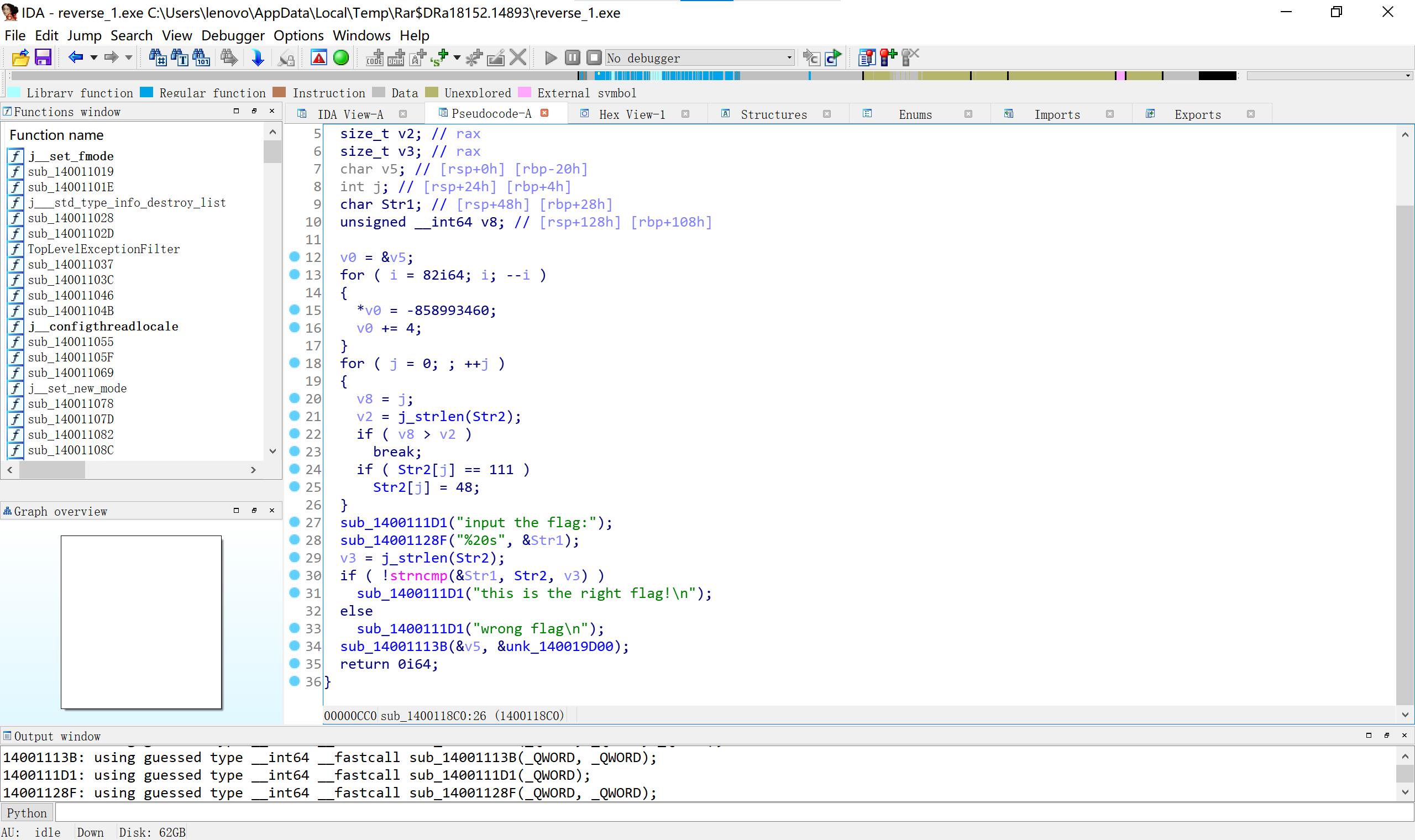
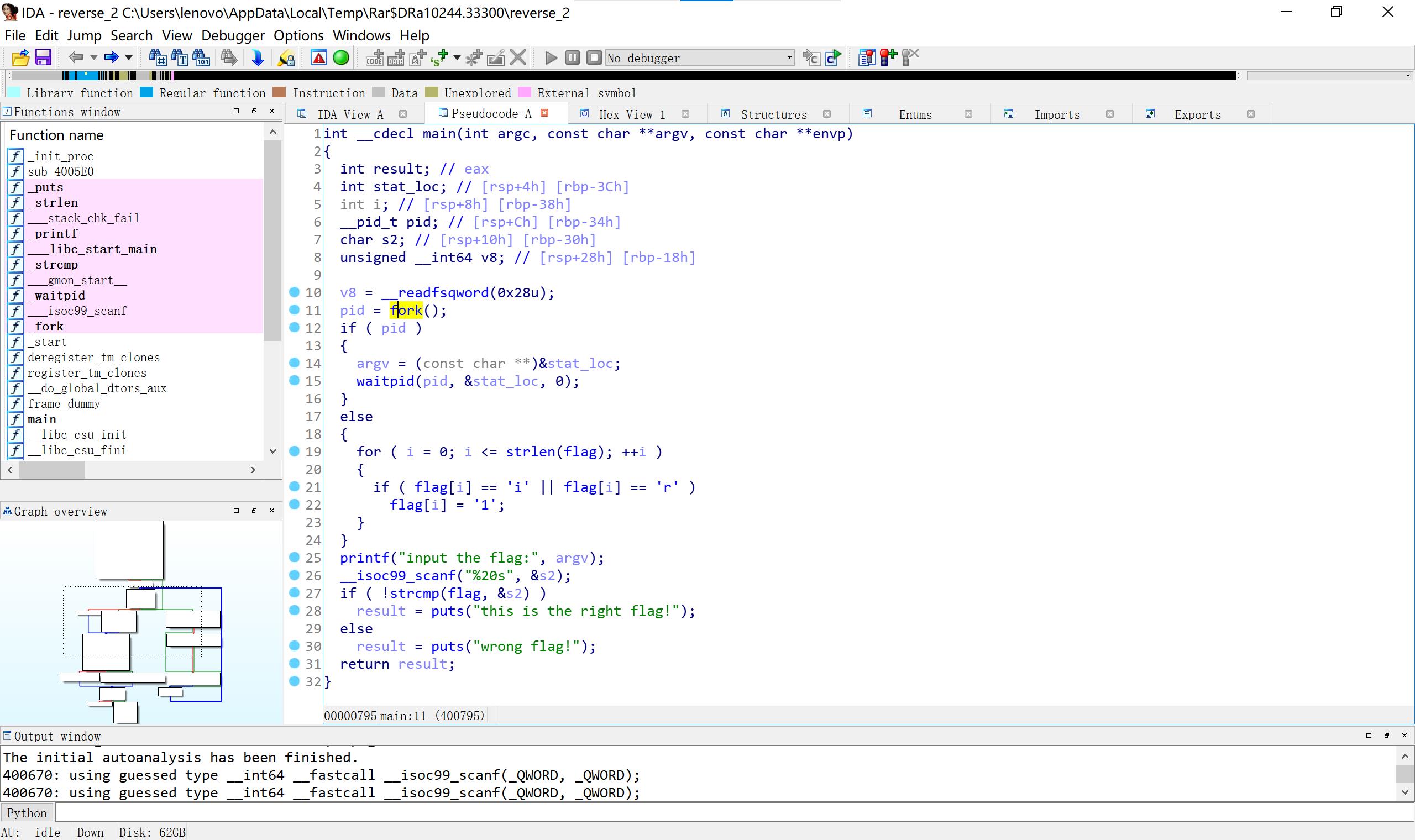
3、Reverse2 几乎明码
4、内涵的软件 明码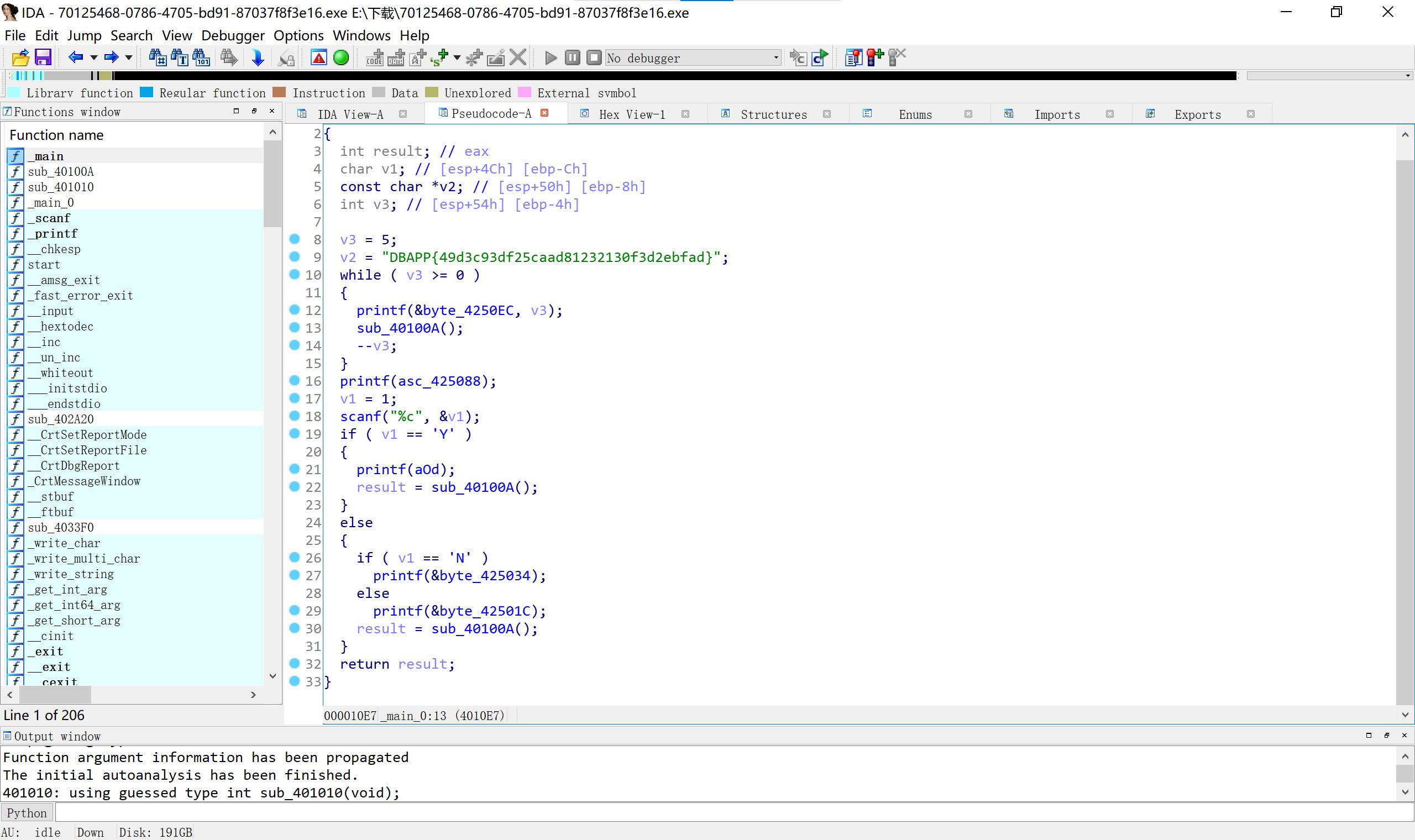
5、新年快乐 有壳先脱壳,之后是明码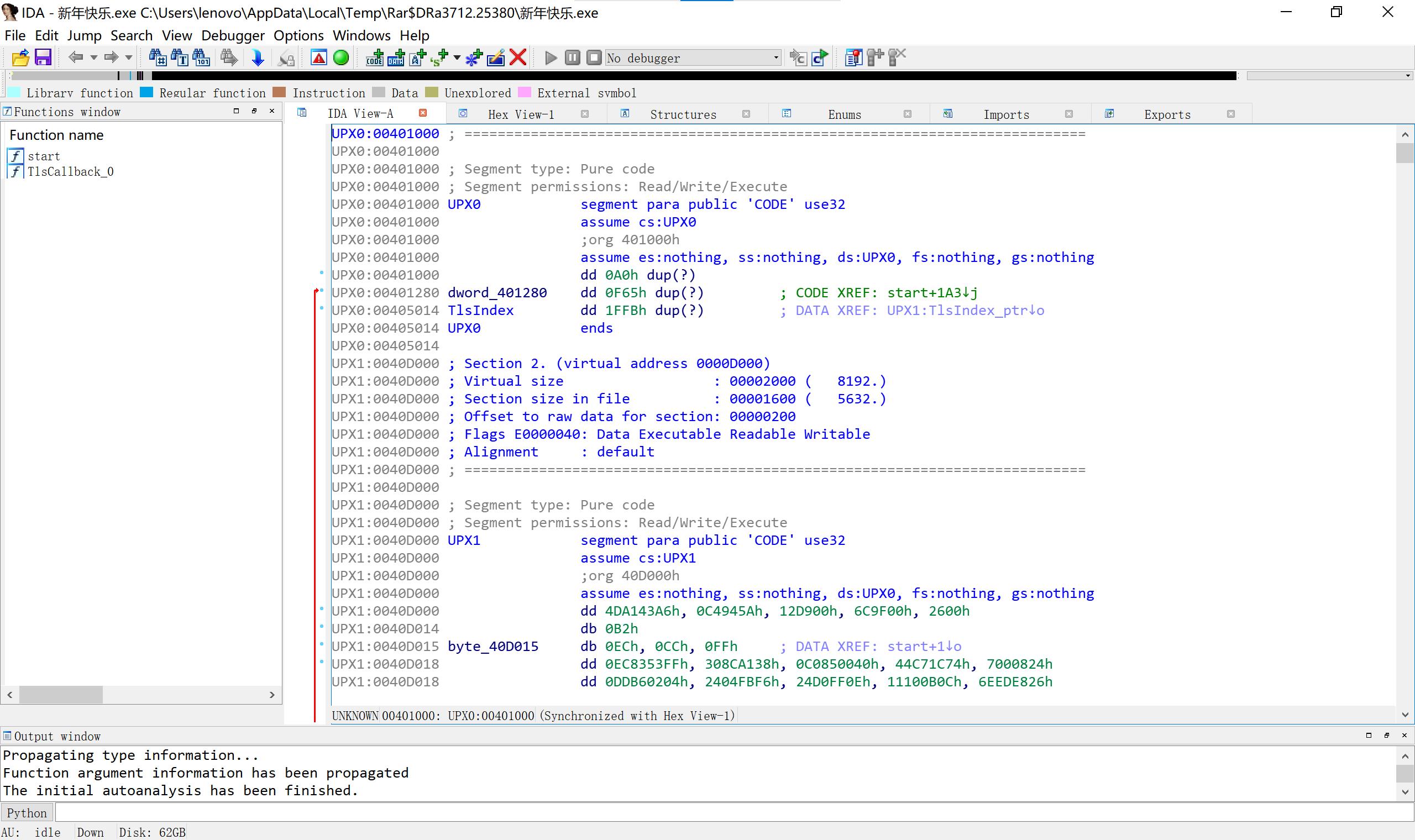
6、Xor 就是简单的异或
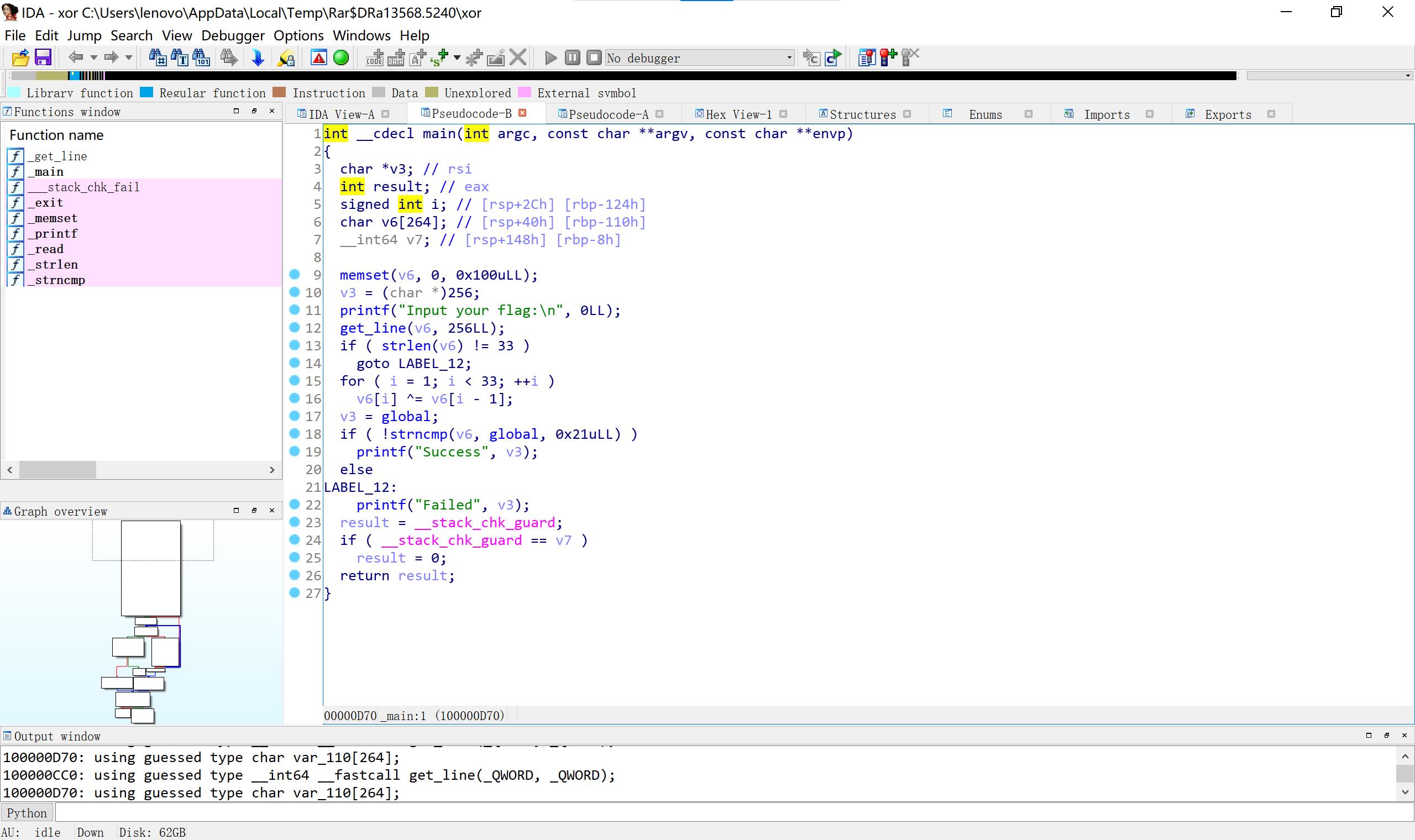
#include < iostream>
using namespace std;
int main()
char miwen[34] =
0x66, 0x0A, 0x6B, 0x0C, 0x77, 0x26, 0x4F, 0x2E, 0x40, 0x11,
0x78, 0x0D, 0x5A, 0x3B, 0x55, 0x11, 0x70, 0x19, 0x46, 0x1F,
0x76, 0x22, 0x4D, 0x23, 0x44, 0x0E, 0x67, 0x06, 0x68, 0x0F,
0x47, 0x32, 0x4F, 0x00
;
for(int i=0;i<33;i++)
char p=miwen[i]^miwen[i+1];
cout<<p;
7、helloworld 明码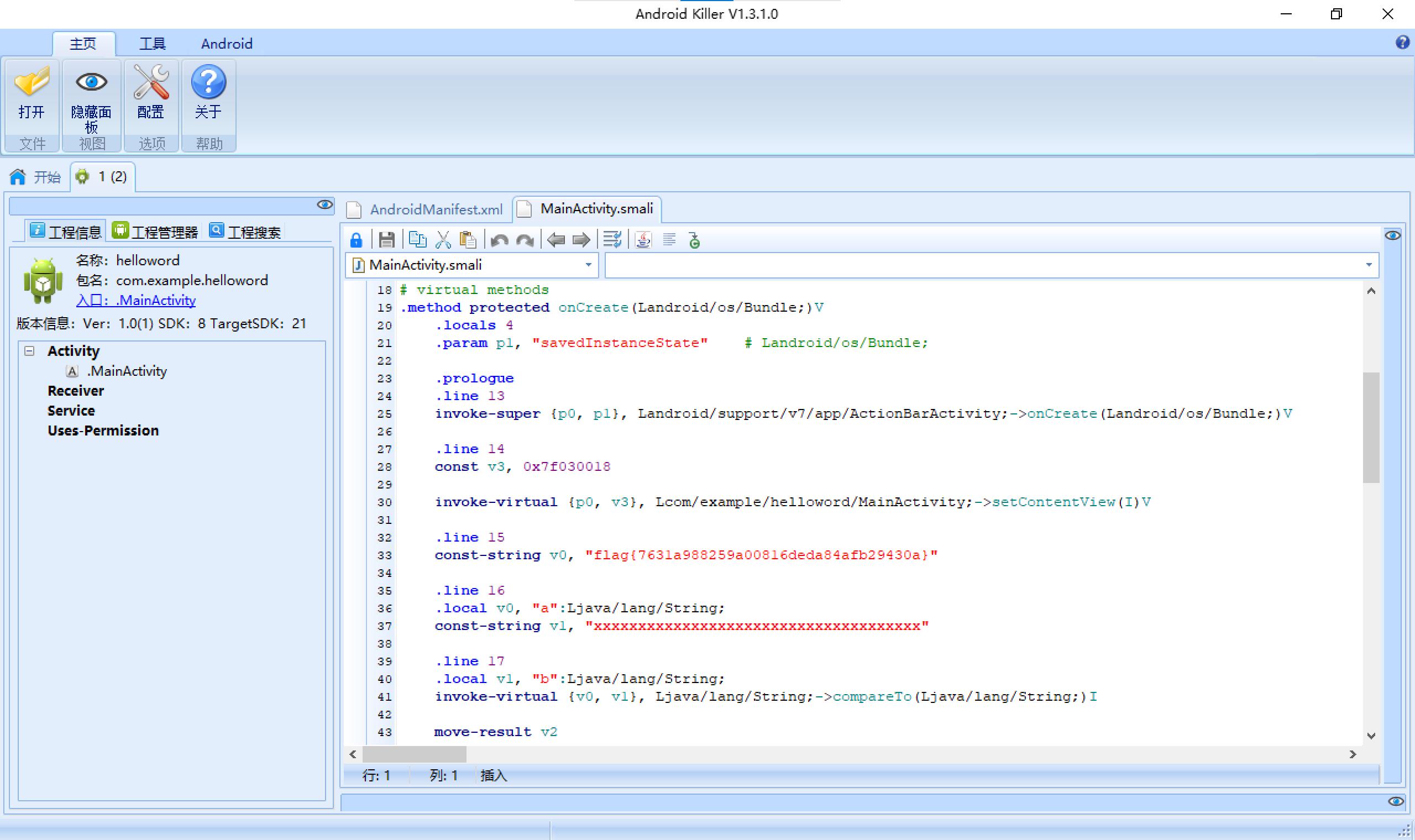
9不一样的flag 迷宫
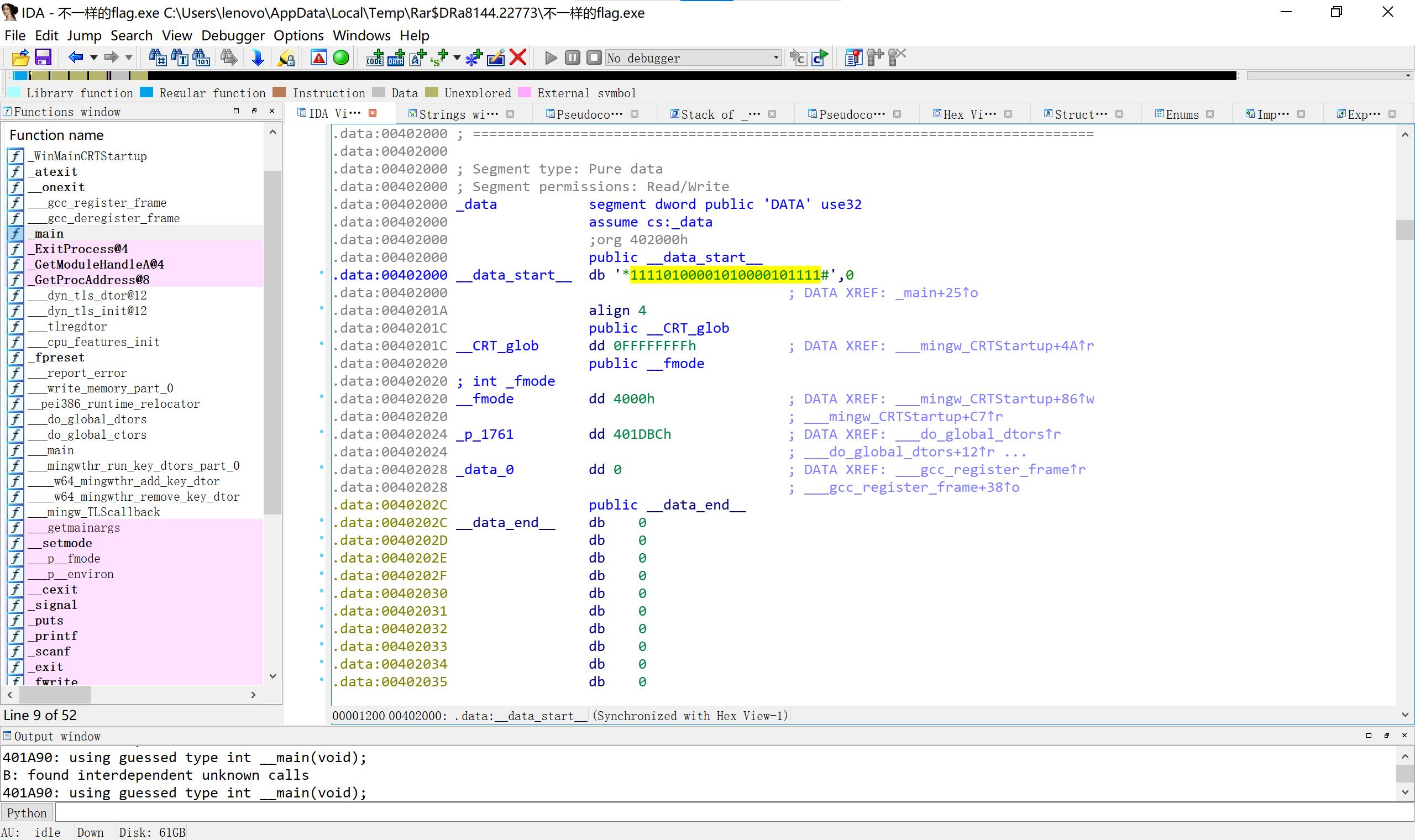
1 上 2 下 3 左 4 右
*1111
01000
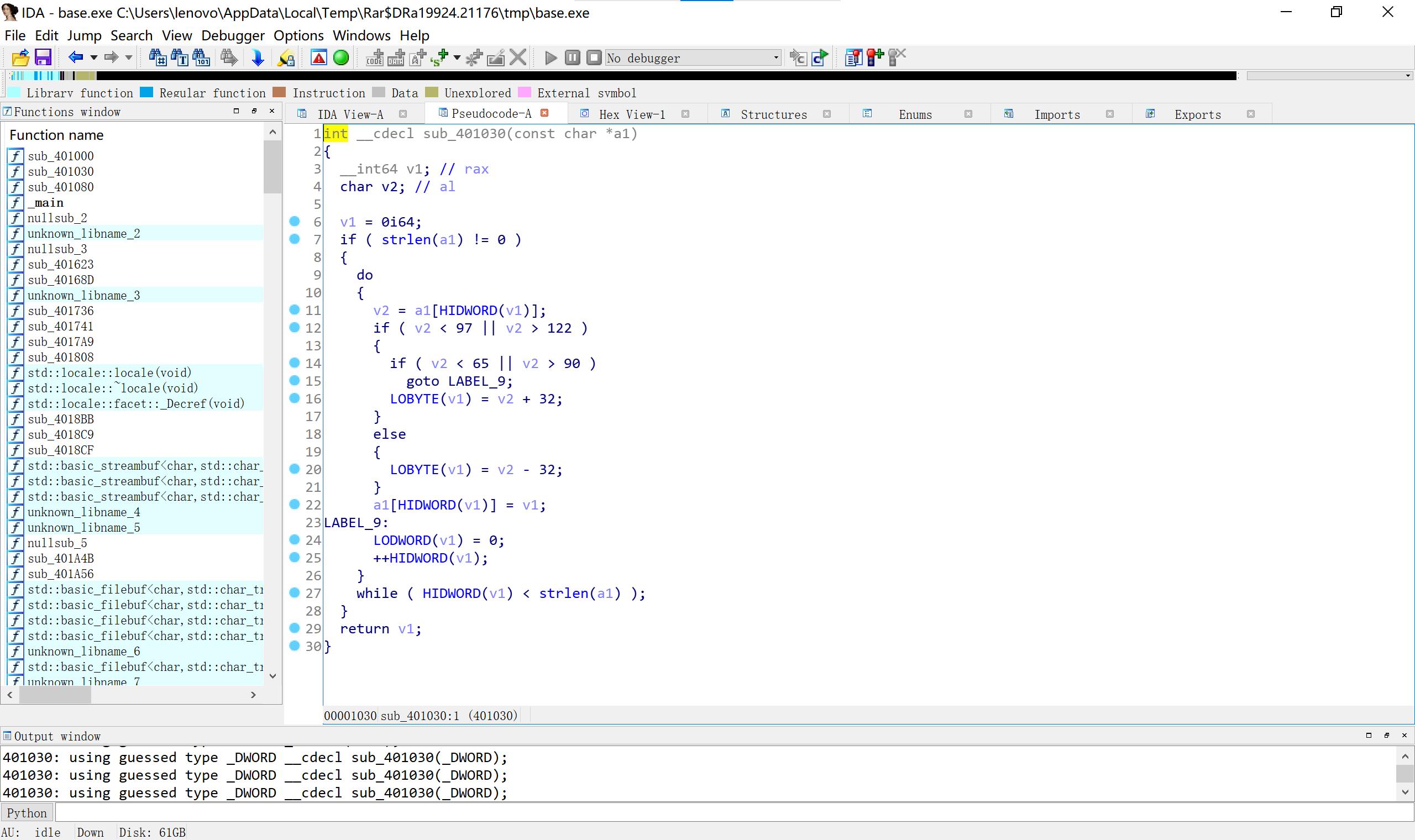
01010
00010
1111#
222441144222
10SimpleRev 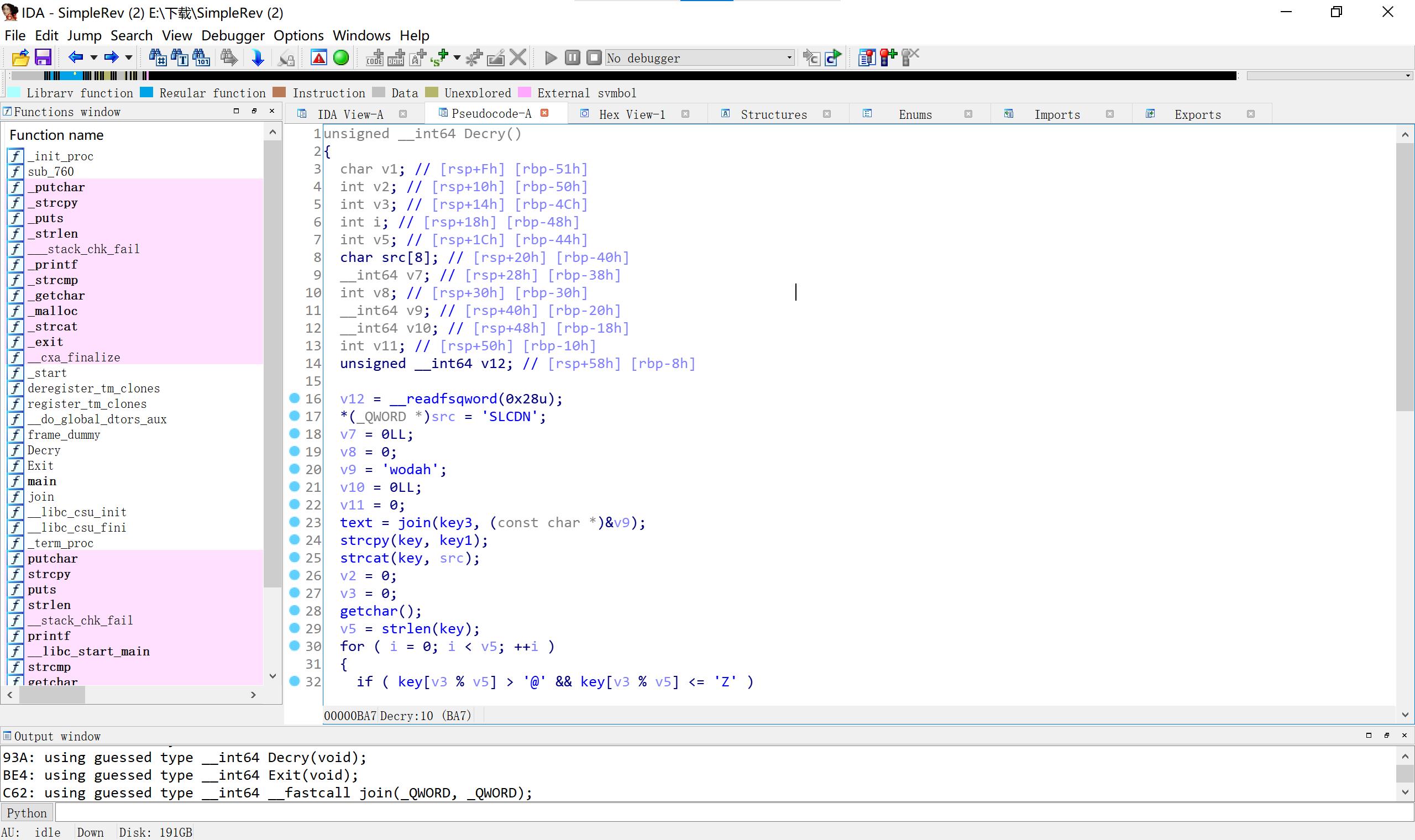
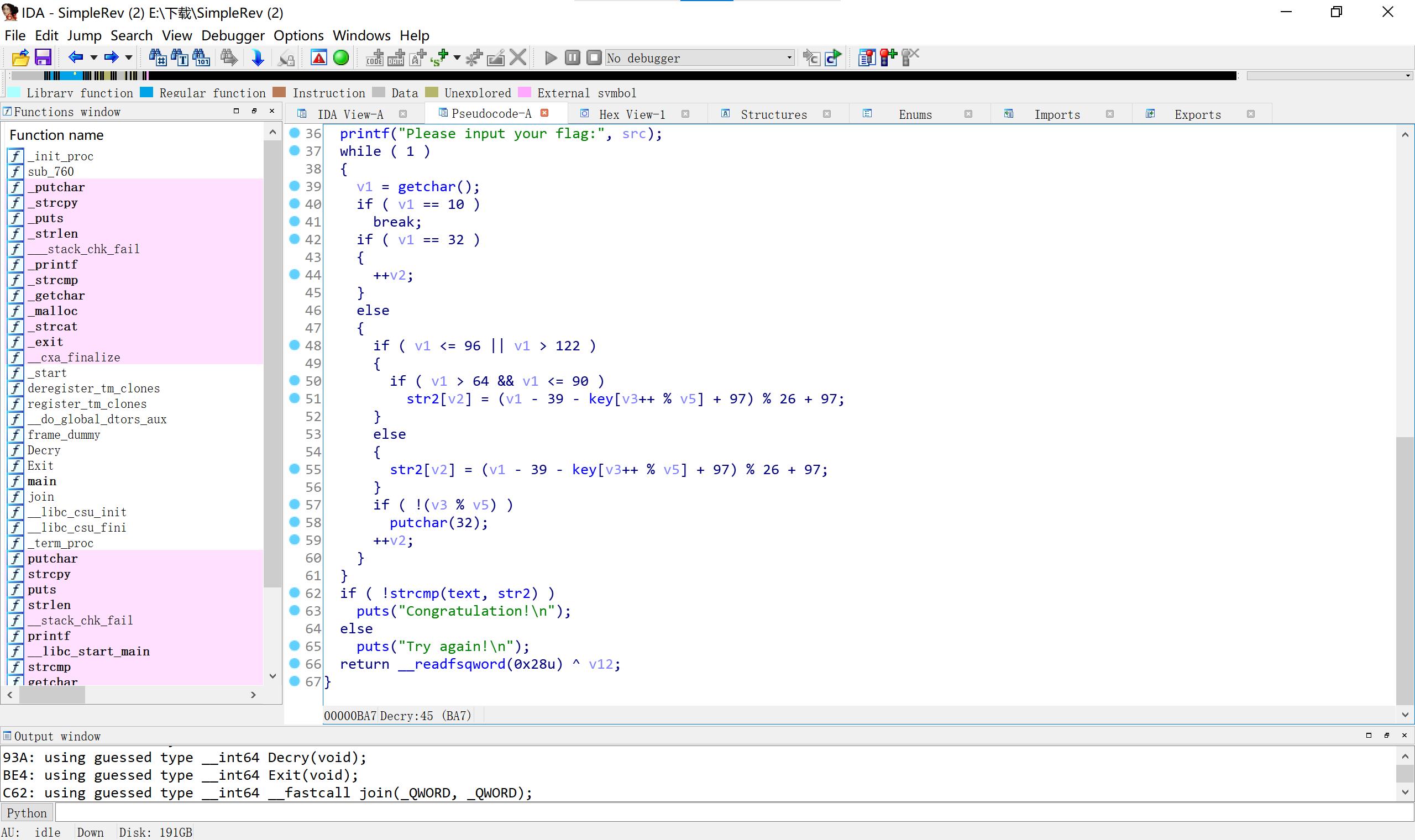
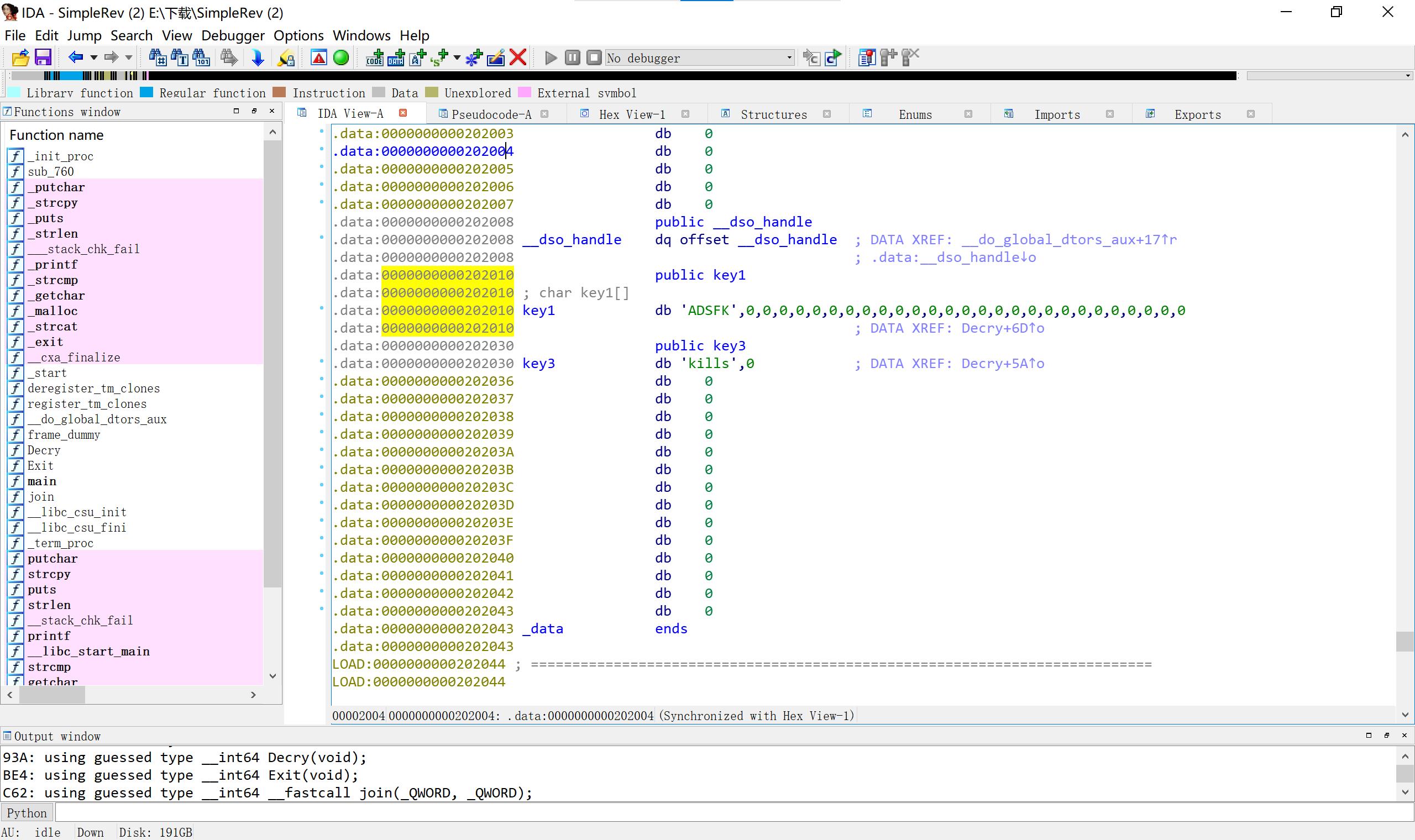
key拼接src ADSFKNDCLS text也是 killshadow(小端) 然后key转小写
#include
using namespace std;
int main()
string p=“killshadow”;
string key=“adsfkndcls”;
for(int i=0;i<10;i++)
for(int j=1;j<128;j++)
if((j>‘a’&&j<‘z’)||(j>‘A’&&j<‘Z’))
if(p[i]==(j-39-key[i]+97)%26+97)
char pp=j;
cout<<pp;
break;
8 reverse3 先base64 再每位数加上自己的位数
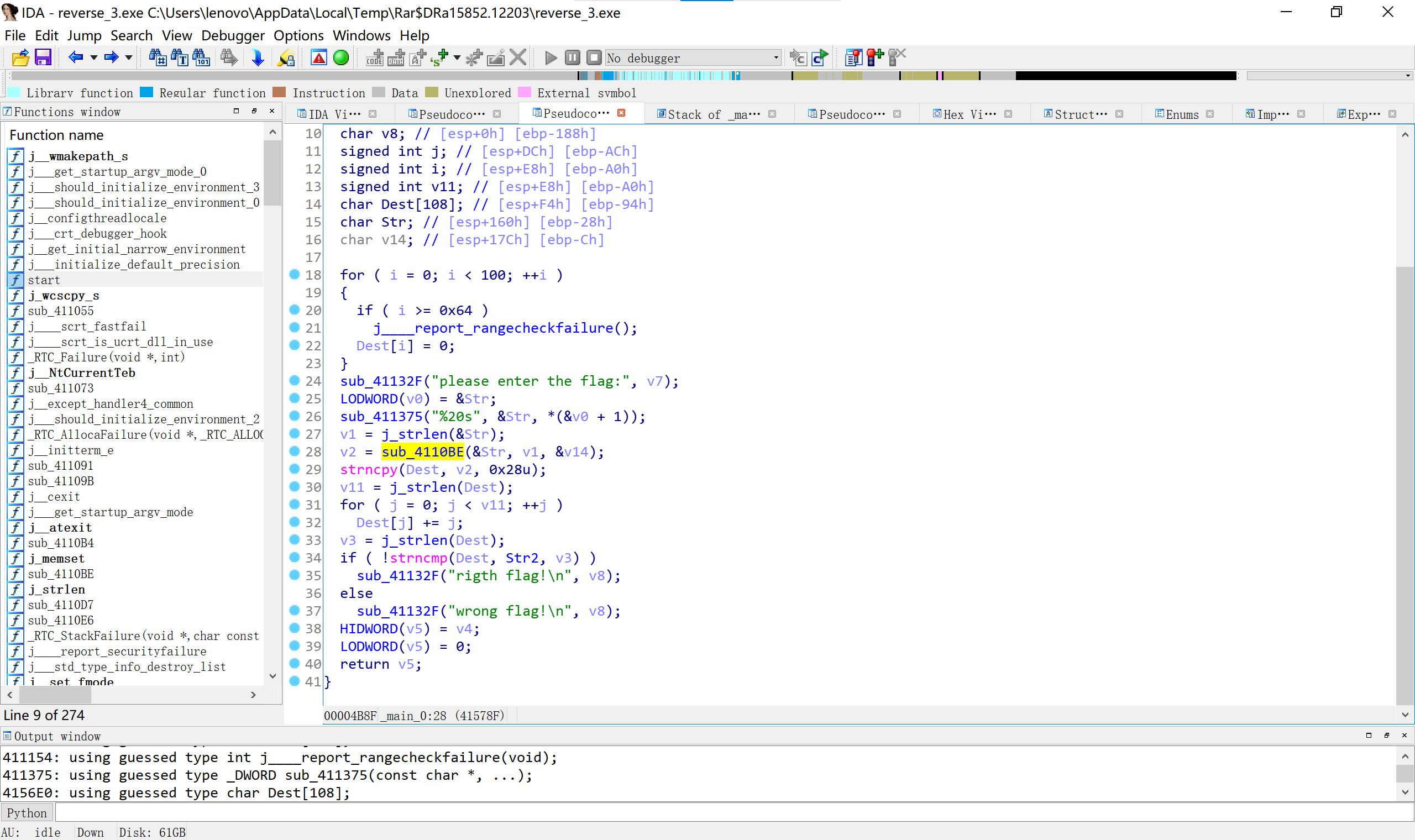
#include
using namespace std;
int main()
string p=“e3nifIH9b_C@n@dH”;
for(int i=0;i<p.length();i++)
p[i]-=i;
cout<<p;
再base64 解码即可
11 java 逆向解密密,用gui 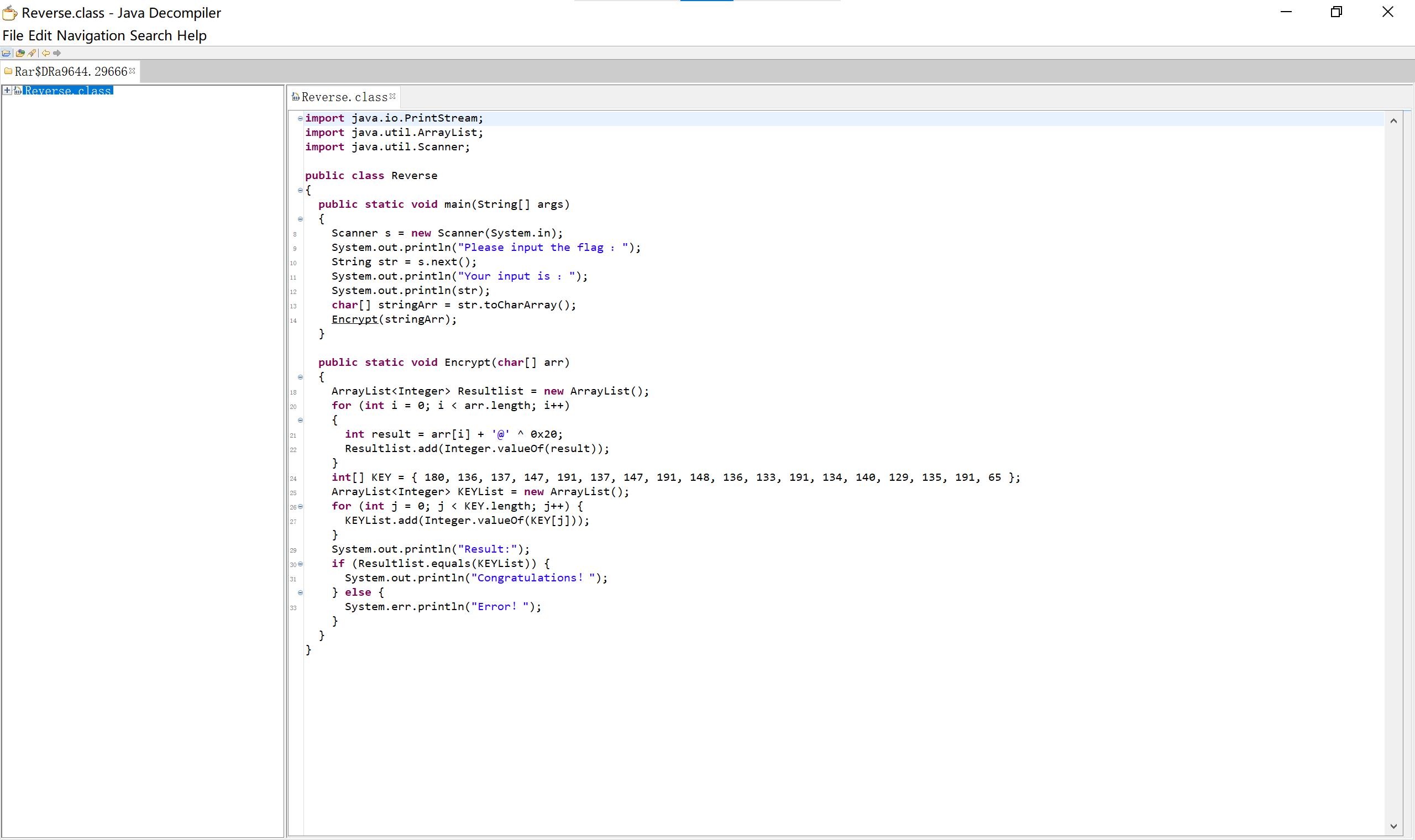
#include < iostream>
using namespace std;
int main()
int key[] = 180, 136, 137, 147, 191, 137, 147, 191, 148, 136, 133, 191, 134, 140, 129, 135, 191, 65 ;
for(int i=0;i<18;i++)
char p=key[i]-’@’^0x20;
cout<<p;
12luckgay
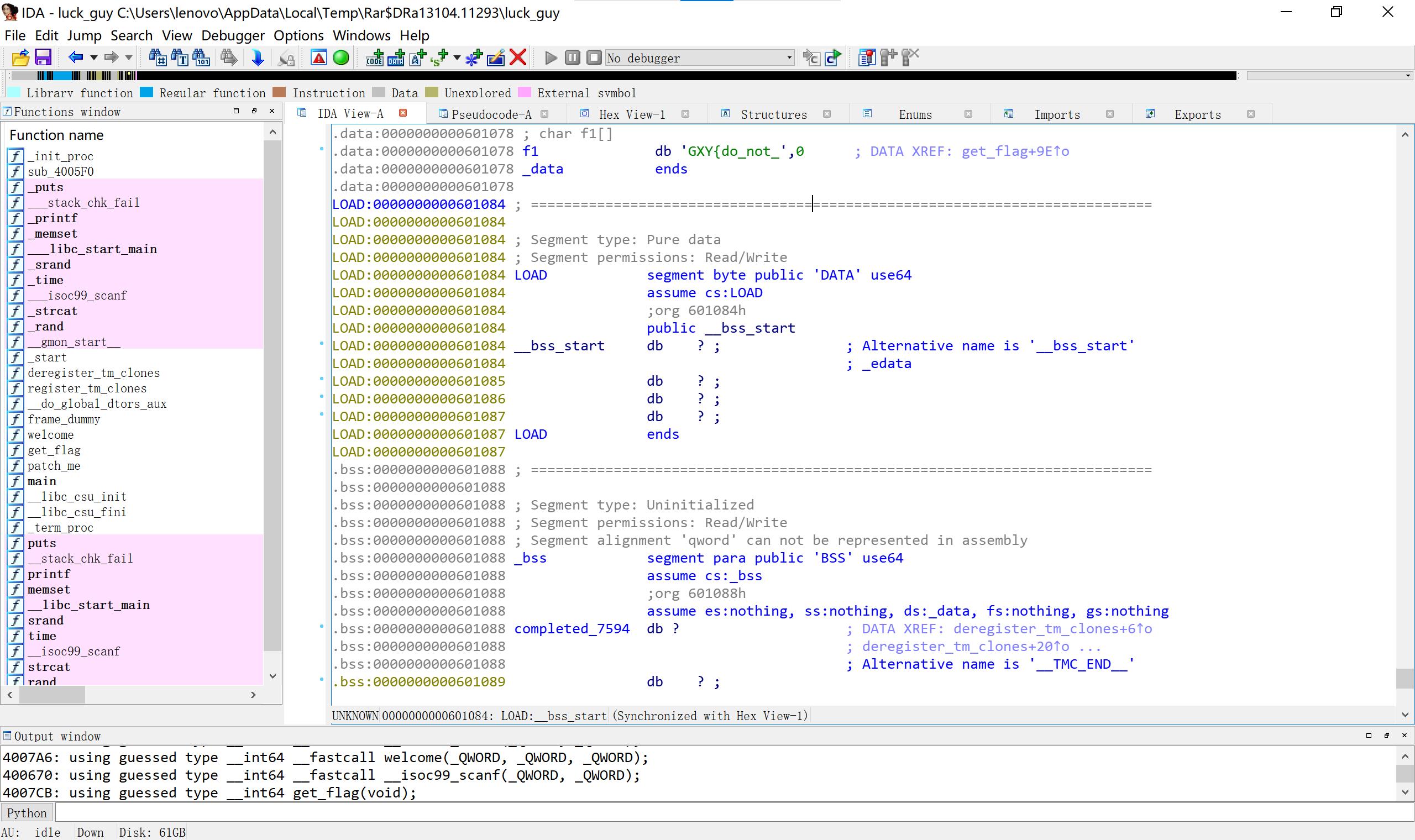
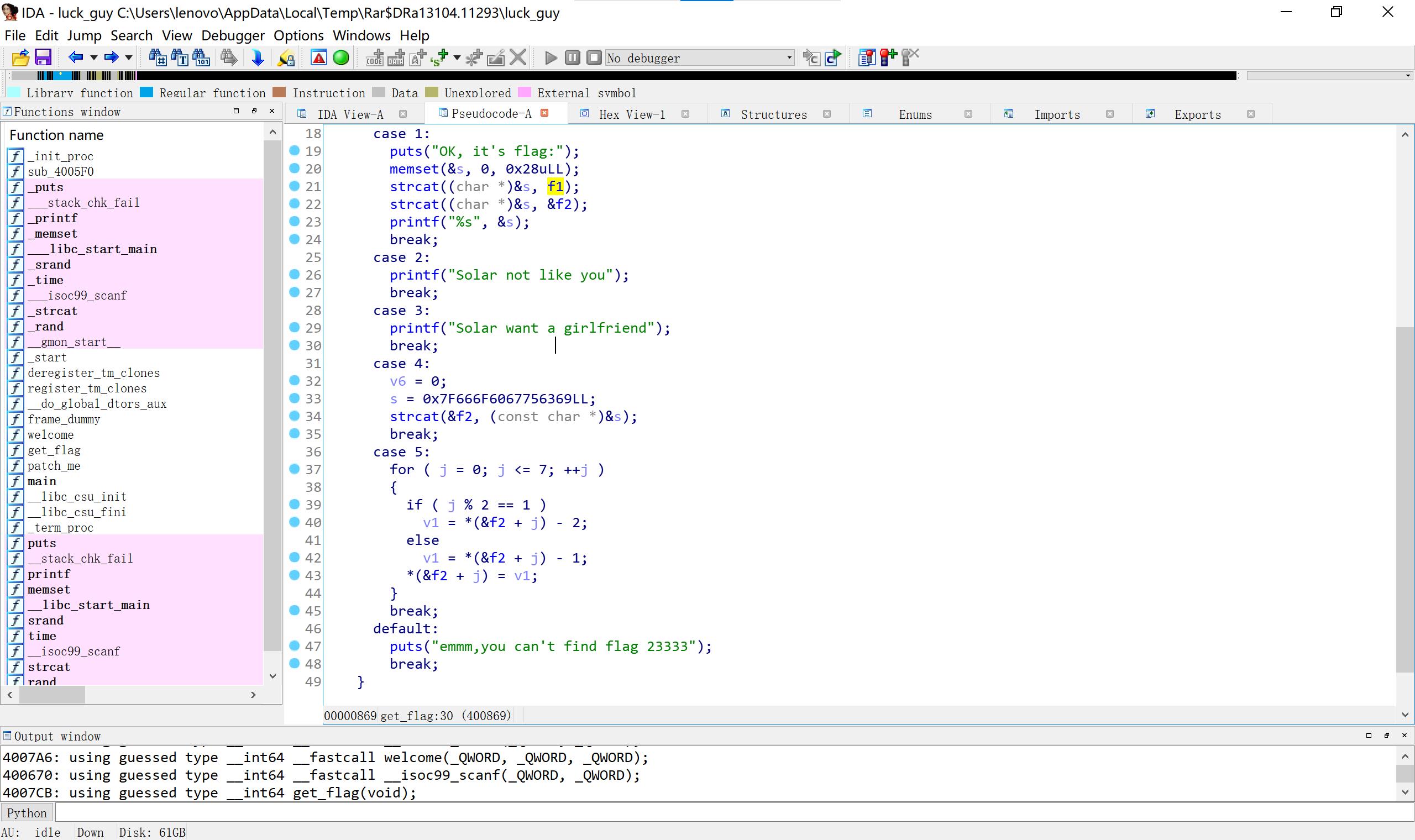
#include < iostream>
using namespace std;
int main()
int p[]=0x69,0x63,0x75,0x67,0x60,0x6f,0x66,0x7f;
for(int i=0;i<8;i++)
if(i%2==1)
p[i]-=2;
else p[i]-=1;
char x=p[i];
cout<<x;
13 刮开有奖 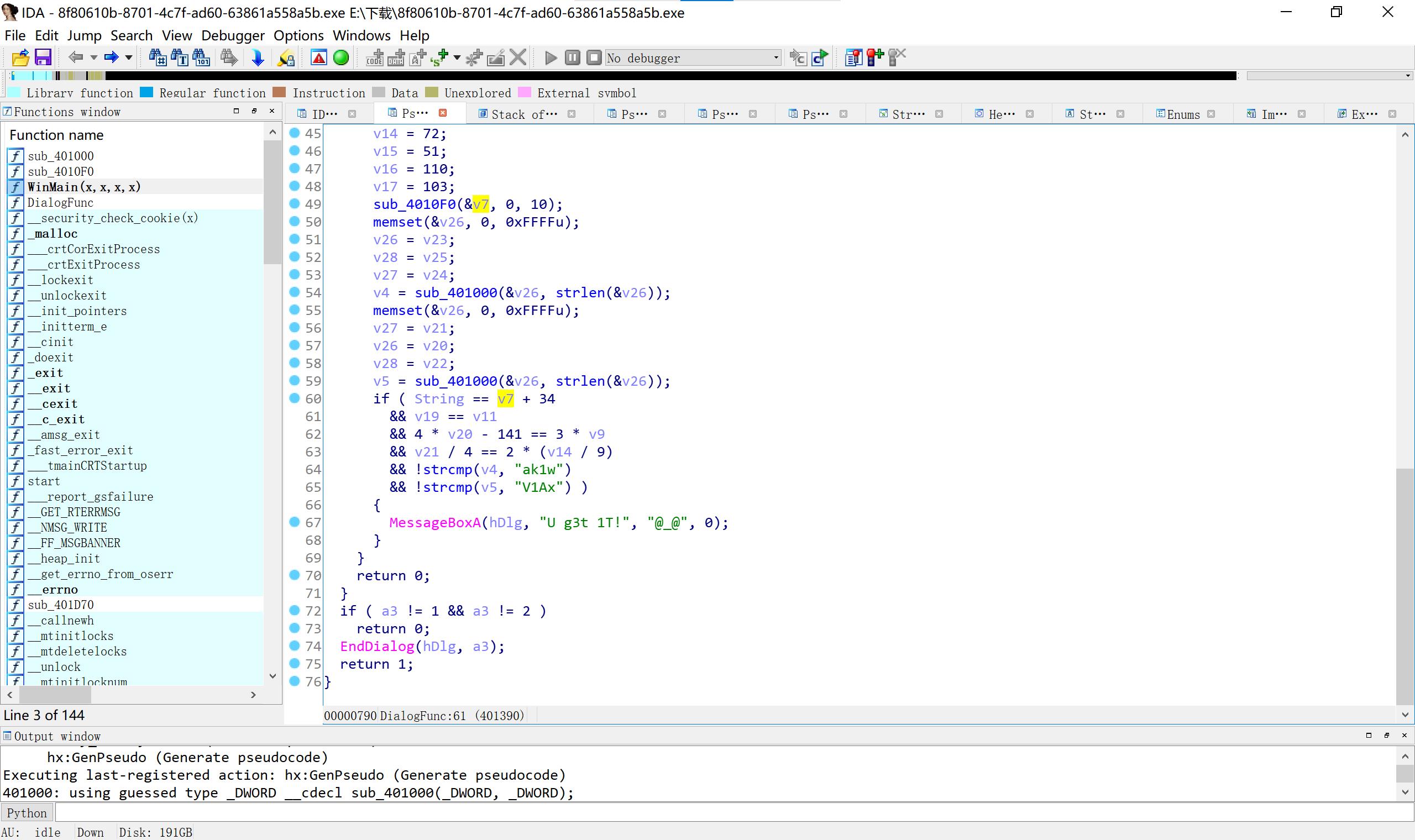
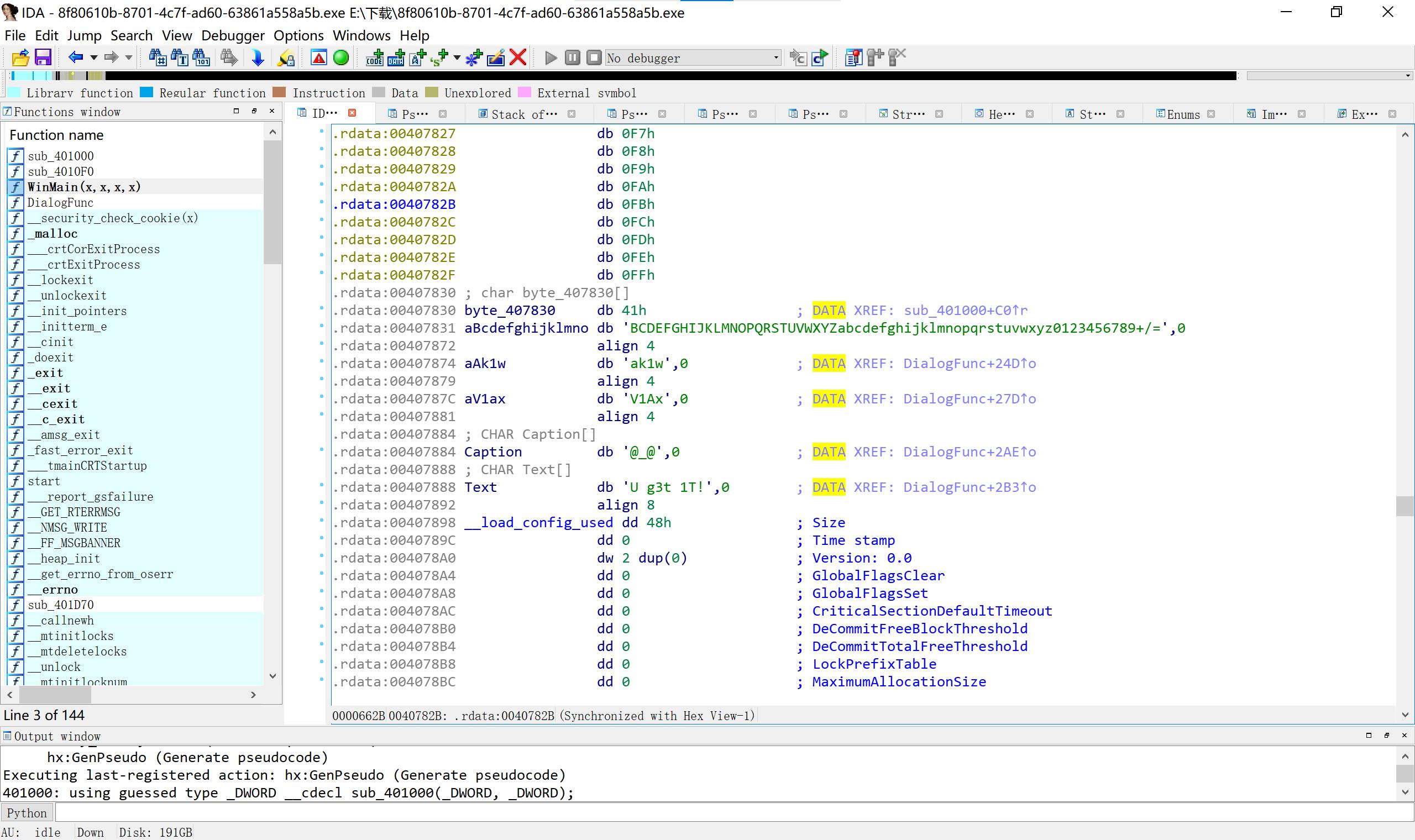
程序处理+base64
Sub_4010c0
#include<stdio.h>
#include
using namespace std;
int sub(char a1[], int a2, int a3)
int result; // eax
int i; // esi
int v5; // ecx
int v6; // edx
result = a3;
for ( i = a2; i <= a3; a2 = i )
v5 = i;
//v6 = *(DWORD *)(4 * i + a1);
v6 = a1[i];
if ( a2 < result && i < result )
do
//if ( v6 > *(DWORD )(a1 + 4 * result) )
if ( v6 > a1[result] )
if ( i >= result )
break;
++i;
//(DWORD *)(v5 + a1) = *(DWORD *)(a1 + 4 * result);
a1[v5] = a1[result];
if ( i >= result )
break;
//while ( *(DWORD )(a1 + 4 * i) <= v6 )
while ( a1[i] <= v6 )
if ( ++i >= result )
goto LABEL_13;
if ( i >= result )
break;
v5 = i;
//(DWORD *)(a1 + 4 * result) = *(DWORD )(4 * i + a1);
a1[result] = a1[i];
–result;
while ( i < result );
LABEL_13:
//(DWORD *)(a1 + 4 * result) = v6;
a1[result]= v6;
sub(a1, a2, i - 1);
result = a3;
++i;
return result;
int main()
char a[11]=90,74,83,69,67,97,78,72,51,110,103;
cout<<">>>>sub"<<endl;
sub(a,0,10);
for (int i=0;i<11;i++)
cout<<“a[”<<i+7<<"]"<<a[i]<<" “<<int(a[i])<<endl;
//cout<<a[i]<<” ";
14 JustRE先开始以为是直接的明码,发现不是,动调爆破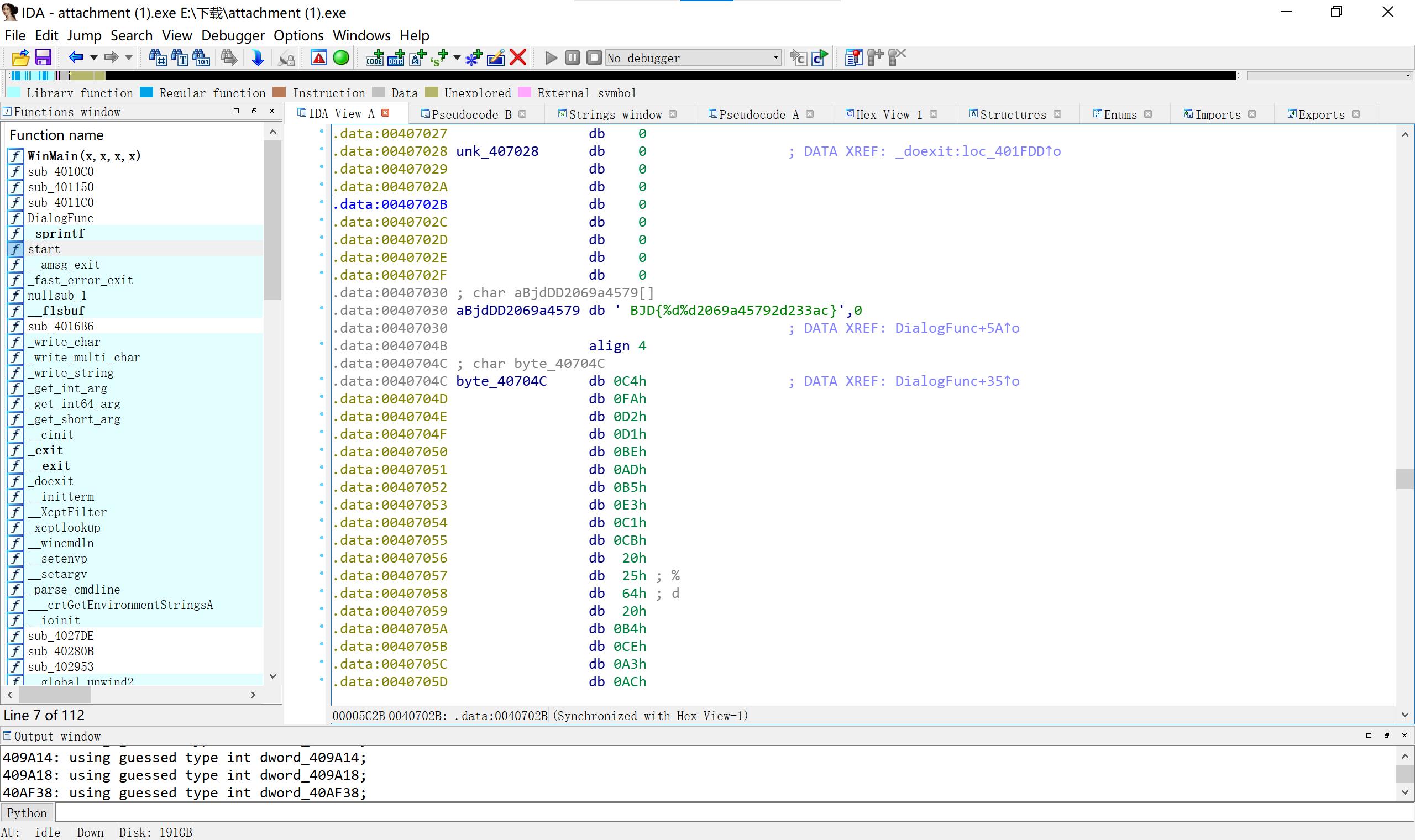
(不爆破按19999下也行)打开即可
15 findit
#include < iostream>
using namespace std;
int main()
char a[]=0x70,0x76,0x6b,0x71, 0x7b, 0x6d, 0x31,0x36,0x34, 0x36,0x37,0x35,0x32,0x36,0x32,0x30, 0x33,0x33,0x6c,0x34,0x6d,0x34,0x39,0x6c,0x6e,0x70,0x37,0x70,0x39,0x6d,0x6e,0x6b,0x32,0x38,0x6b,0x37,0x35,0x7d;
for(int i=0;i<38;i++)
cout<<a[i];
然后凯撒(看1第一个字符与第四个字符是否相邻,是则基本上就是凯撒)
16 简单注册器
#include < iostream>
using namespace std;
int main()
string p=“dd2940c04462b4dd7c450528835cca15”;
p[2]=p[2]+p[3]-50;
p[4]=p[2]+p[5]-48;
p[30]=p[31]+p[9]-48;
p[14]=p[27]+p[28]-97;
cout<<p;
17 pyre python反编译 - 在线工具 (tool.lu)
#!/usr/bin/env python
visit https://tool.lu/pyc/ for more information
print ‘Welcome to Re World!’
print ‘Your input1 is your flag~’
l = len(input1)
for i in range(l):
num = ((input1[i] + i) % 128 + 128) % 128
code += num
for i in range(l - 1):
code[i] = code[i] ^ code[i + 1]
print code
code = [
‘\\x1f’,
‘\\x12’,
‘\\x1d’,
‘(’,
‘0’,
‘4’,
‘\\x01’,
‘\\x06’,
‘\\x14’,
‘4’,
‘,’,
‘\\x1b’,
‘U’,
‘?’,
‘o’,
‘6’,
‘’,
‘:’,
‘\\x01’,
‘D’,
‘;’,
‘%’,’0x13’]
#include
using namespace std;
int main()
char coder[]=0x13,’%’,’;’,‘D’,0x01,’:’,’’,‘6’,‘o’,’?’,‘U’,0x1b,’,’,‘4’,0x14,0x06,0x01,‘4’,‘0’,’(’,0x1d,0x12,0x1f;
char code[23];
for(int i=0;i<23;i++)
code[i]=coder[22-i];
for(int i=22;i>0;i–)
code[i-1]^=code[i];
for(int i=0;i<23;i++)
code[i]=(code[i]-i)&0xff;
cout<<code[i];
18.easyre 有壳,脱壳,壳没有完美脱出,但够看了。
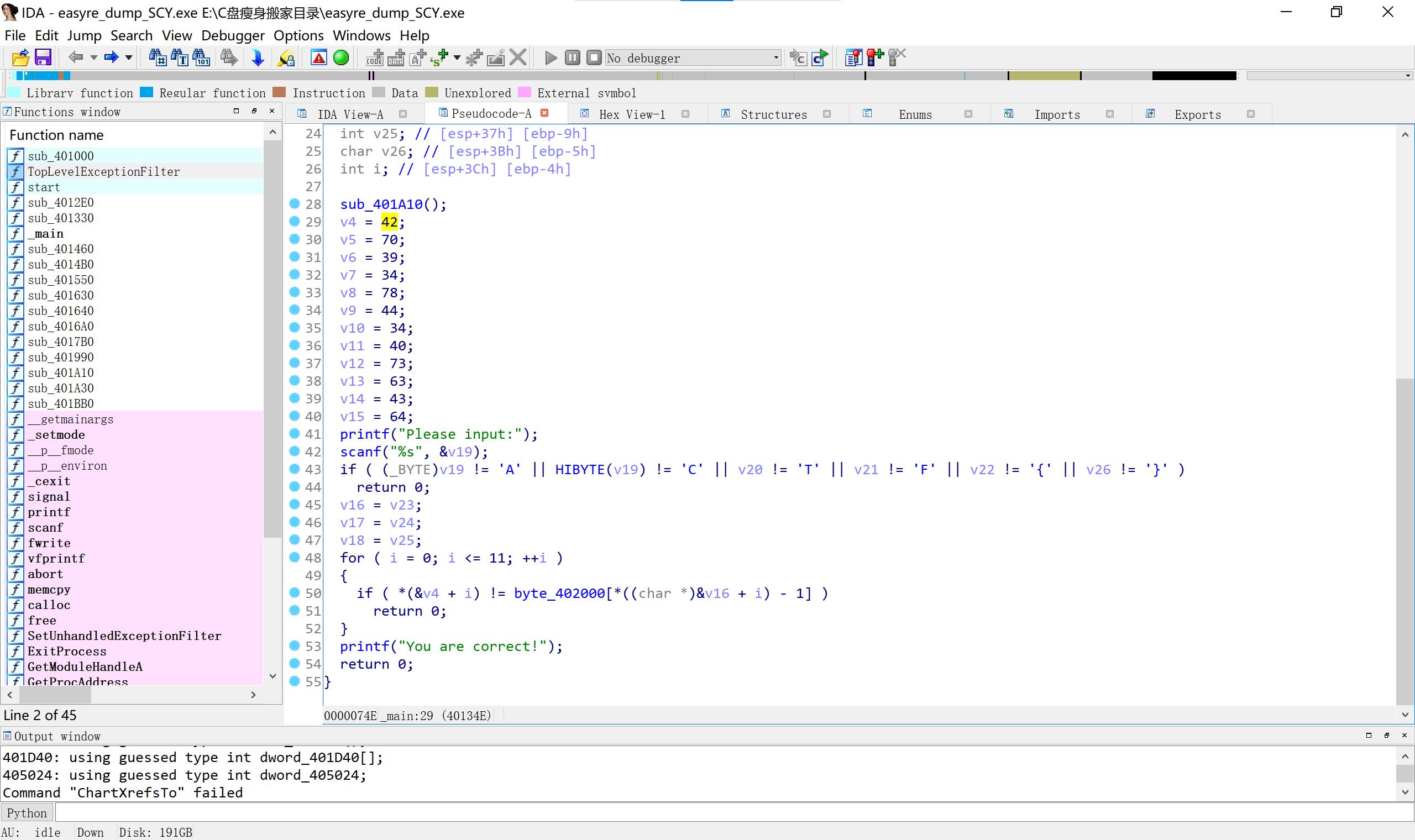
#include < iostream>
using namespace std;
int main()
string p="~|zyxwvutsrqponmlkjihgfedcba`_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)(’&%$# !"";
int v4 [12]= 42,70,39,34,78,44,34,40,73,63,43,64;
for(int i=0;i<12;i++)
for(int j=0;j<p.length();j++)
if(p[j]==v4[i])
char pp=j+2;
cout<<pp;
break;
19.Rsa算法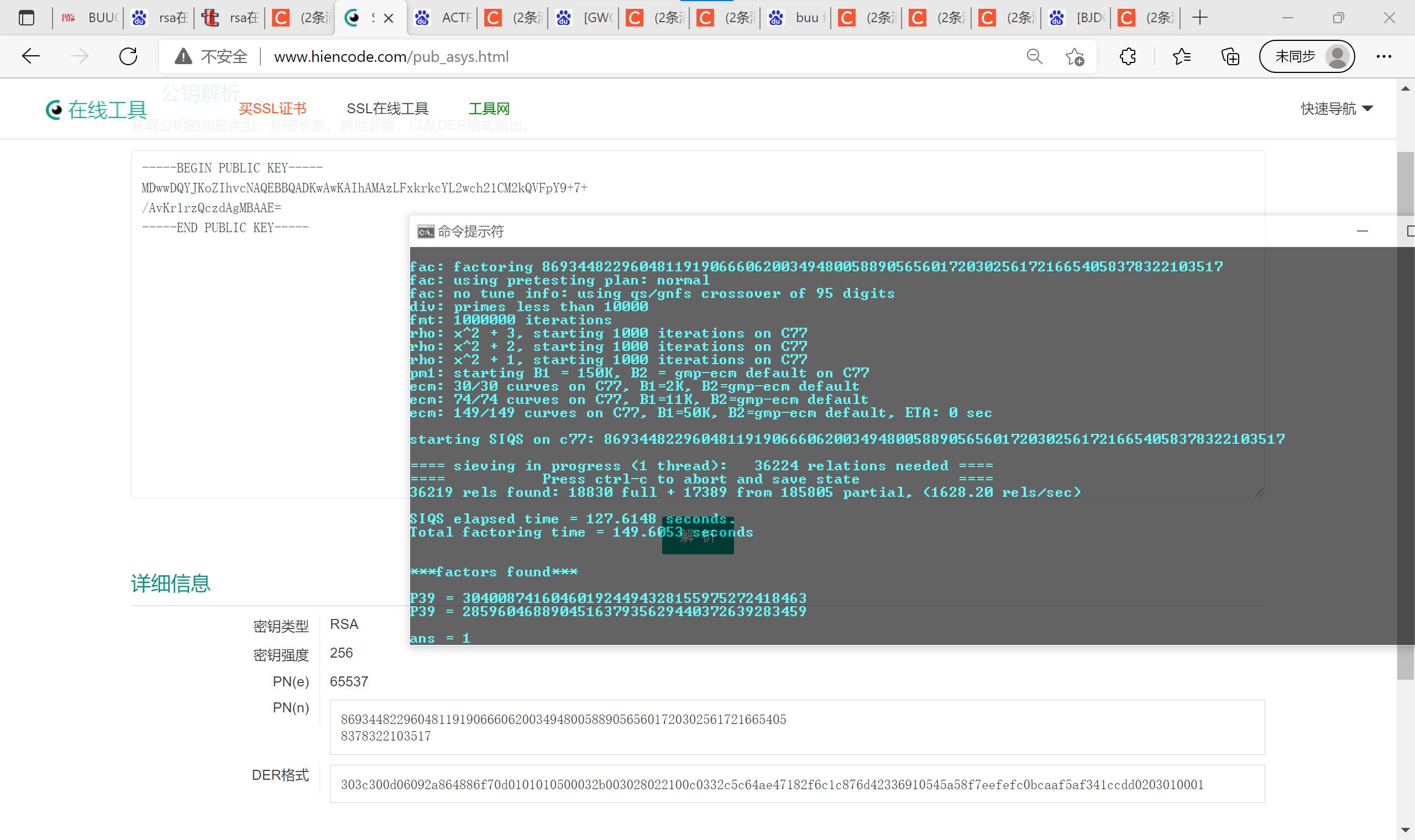
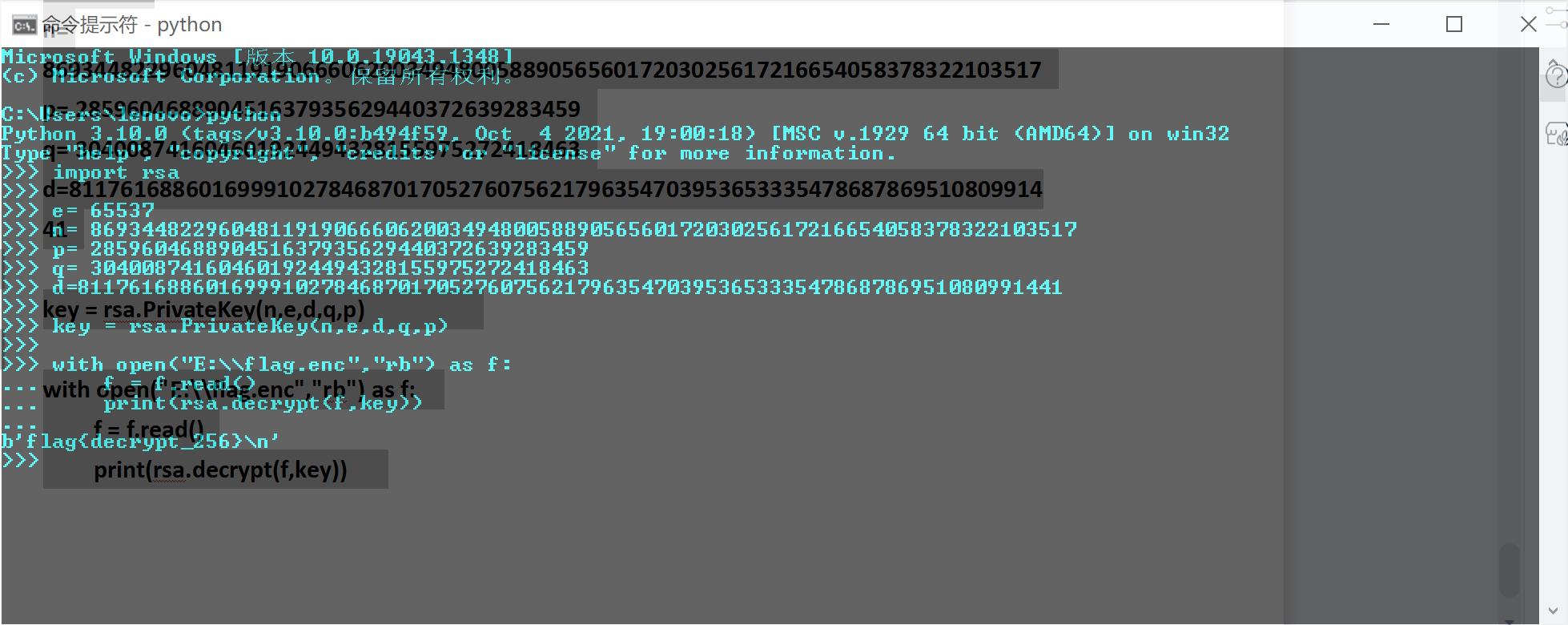
import rsa
e= 65537
n= 86934482296048119190666062003494800588905656017203025617216654058378322103517
p= 285960468890451637935629440372639283459
q= 304008741604601924494328155975272418463
d=81176168860169991027846870170527607562179635470395365333547868786951080991441
key = rsa.PrivateKey(n,e,d,q,p)
with open(“E:\\flag.enc”,“rb”) as f:
f = f.read()
print(rsa.decrypt(f,key))
20 rome 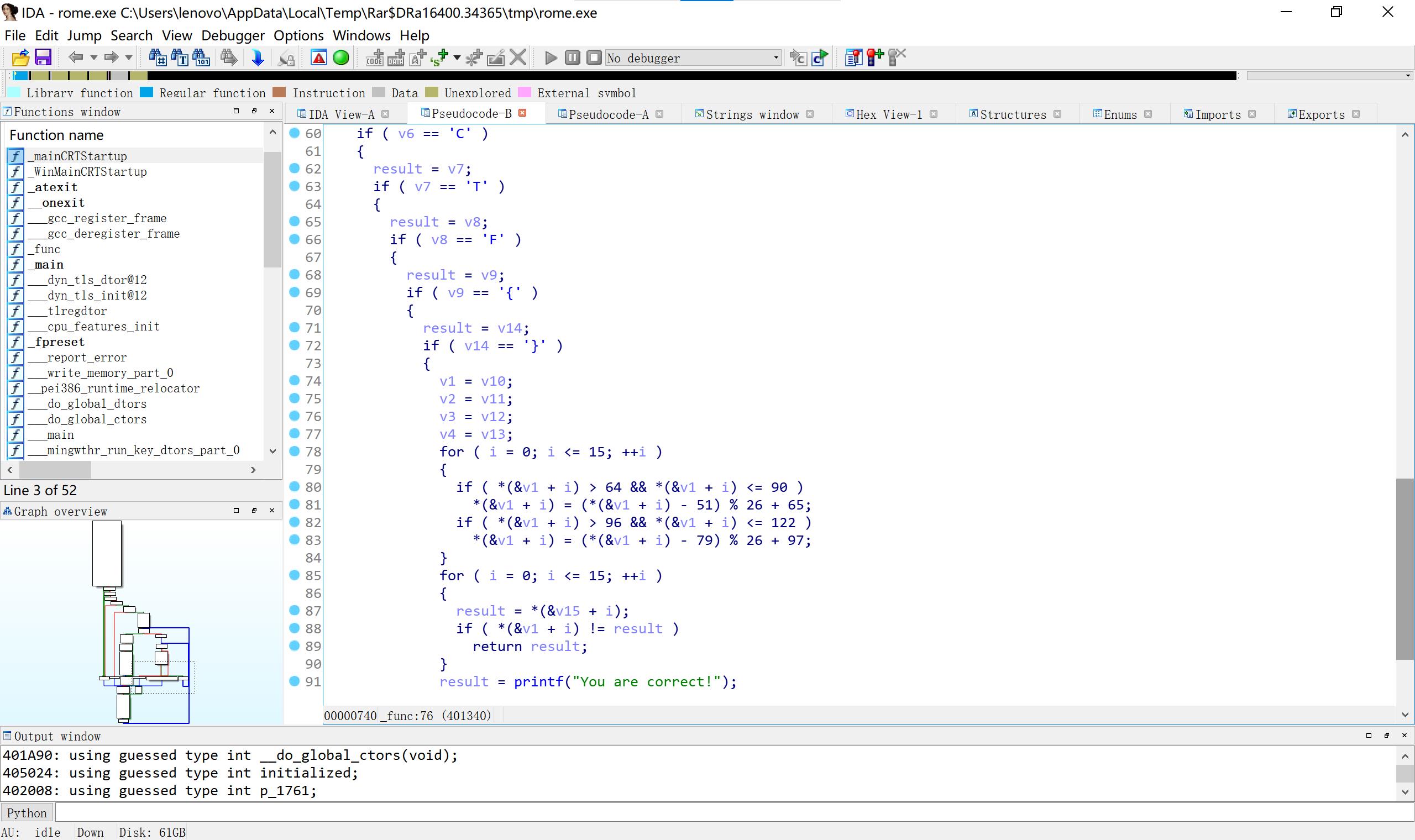
#include < iostream>
using namespace std;
int main()
int v15[16]=81,115,119,51,115,106,95,108,122,52,95,85,106,119,64,108;
for(int i=0;i<=15;i++)
for(int j=1;j<128;j++)
int k=j;
if ( j> 64 && j <= 90 )
k = (k - 51) % 26 + 65;
if ( j > 96 && j <= 122 )
k = (k - 79) % 26 + 97;
if(k==v15[i])
char p=j;
cout<<p;
break;
21 crackrtf cryptcreatehash 上网查其参数的含义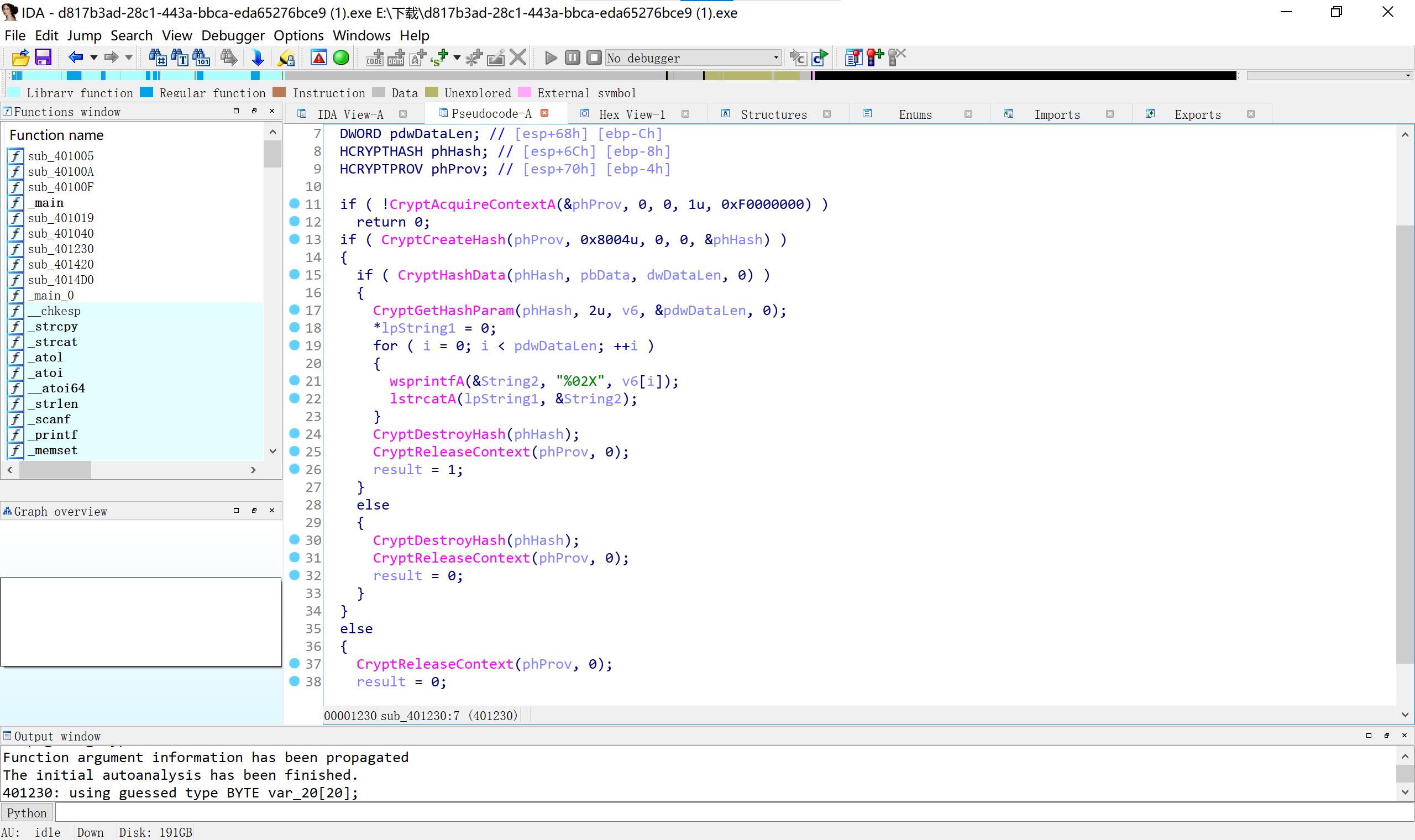
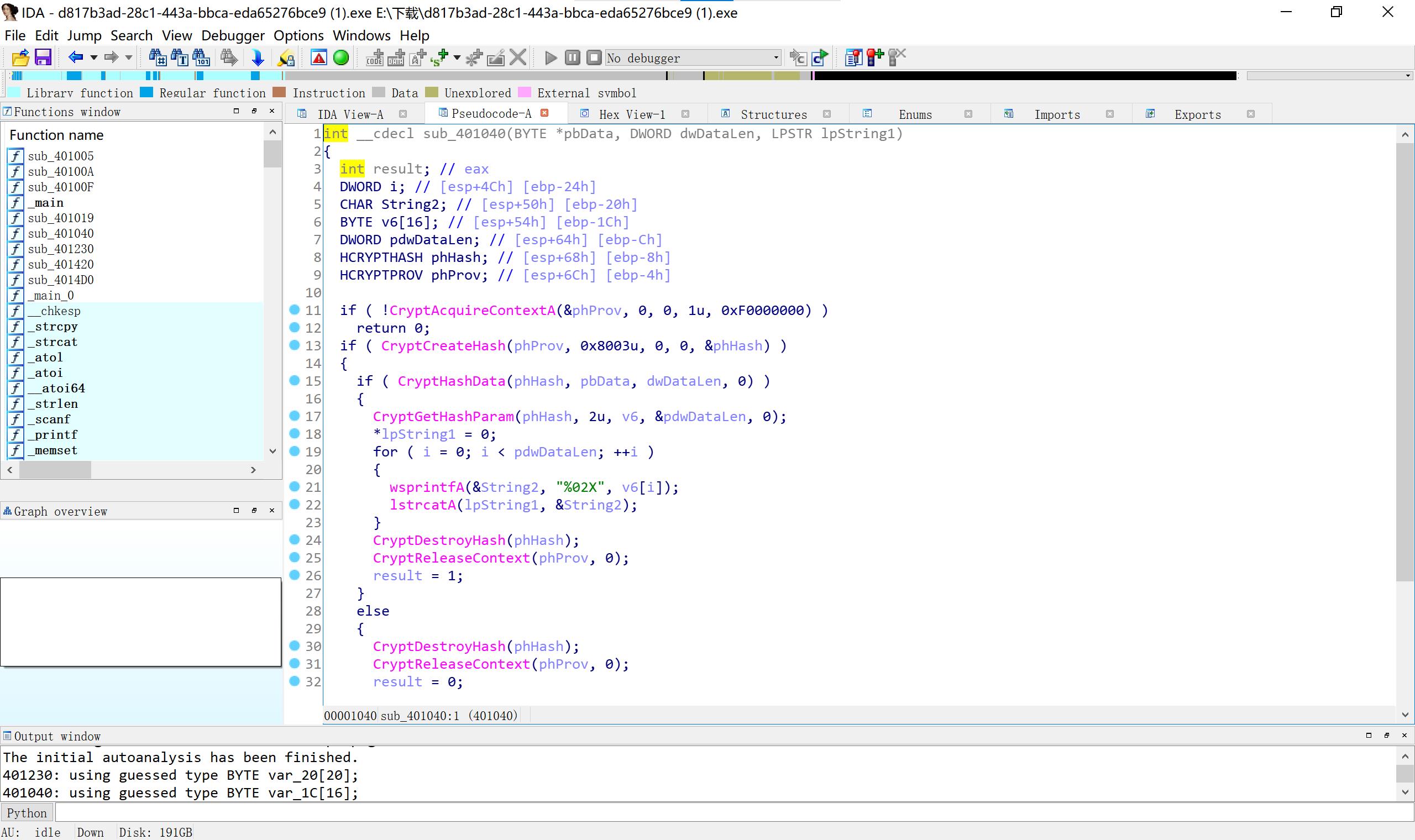
这个代码在网上找的,有点问题
import hashlib
flags = “@DBApp”
h2=""
for i in range(100000,999999):
h2 = hashlib.sha1((str(i)+flags).encode())
flags = h2.hexdigest()
if “6e32d0943418c2c33385bc35a1470250dd8923a9” == flags:
print (str(i)+flags)
print (i)
也可以在网上找sha1破解
就算不行也没关系的,看,直接就出两步的结果 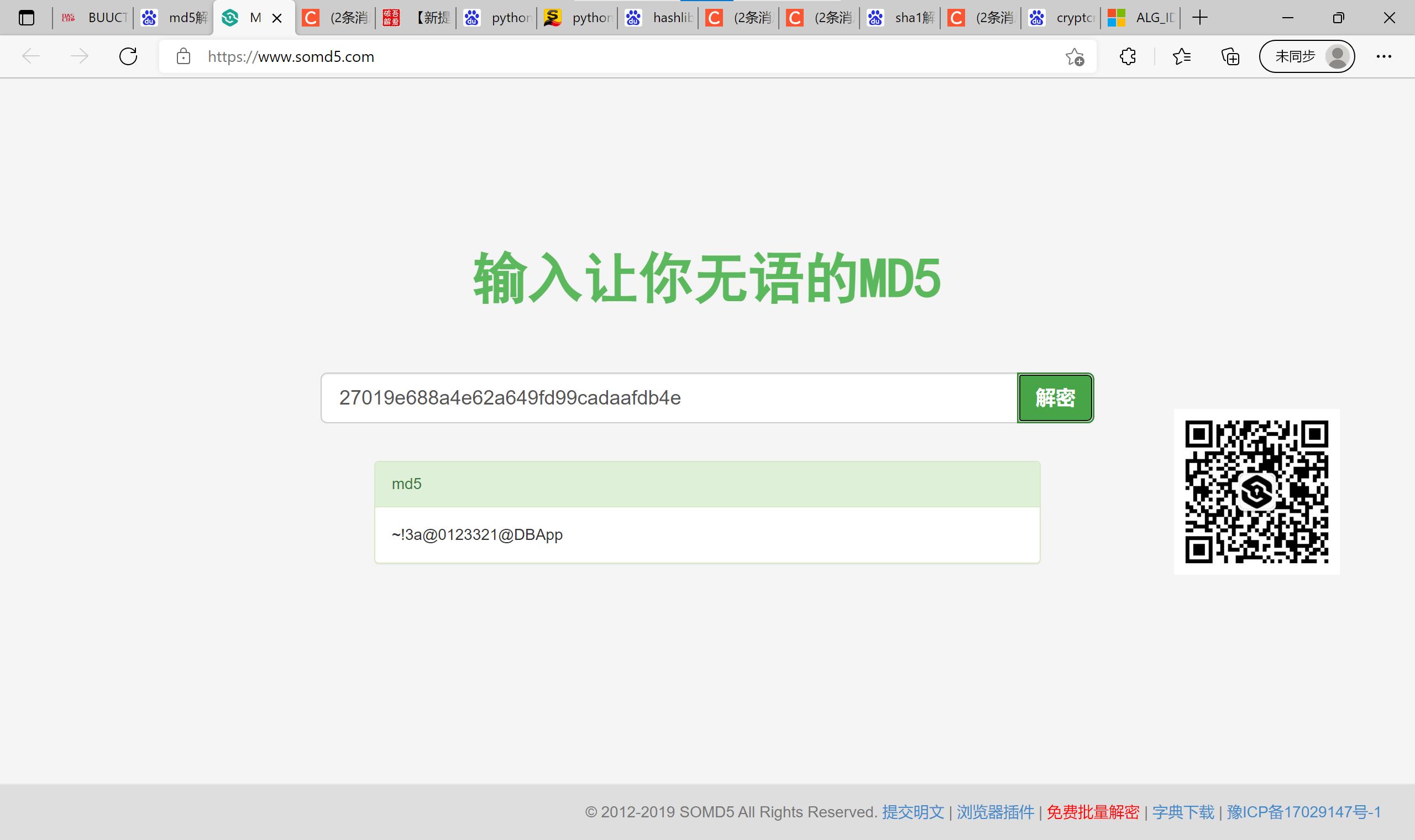
有个AAA文件,并且要进行异或操作,但不知道怎么异或
但是一看自己目录,有rtf文件了,打开就有flag ,感情是白忙了一小时!淦!看别人writeup
这里是文件前五个字符与头部指针\\rtfl异或,答案与第二个字符串相同。
22 easyre base64 10次 发现被坑了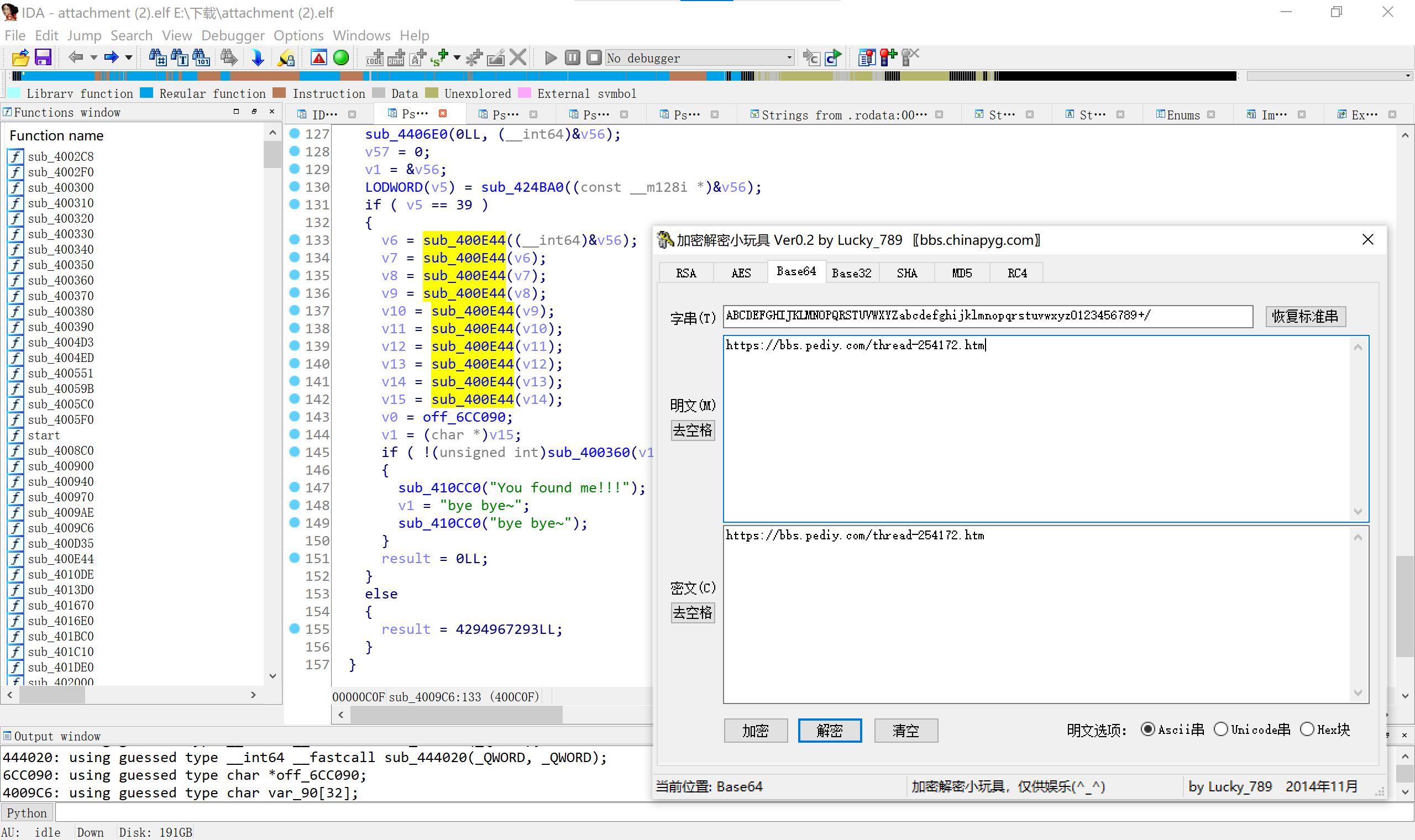
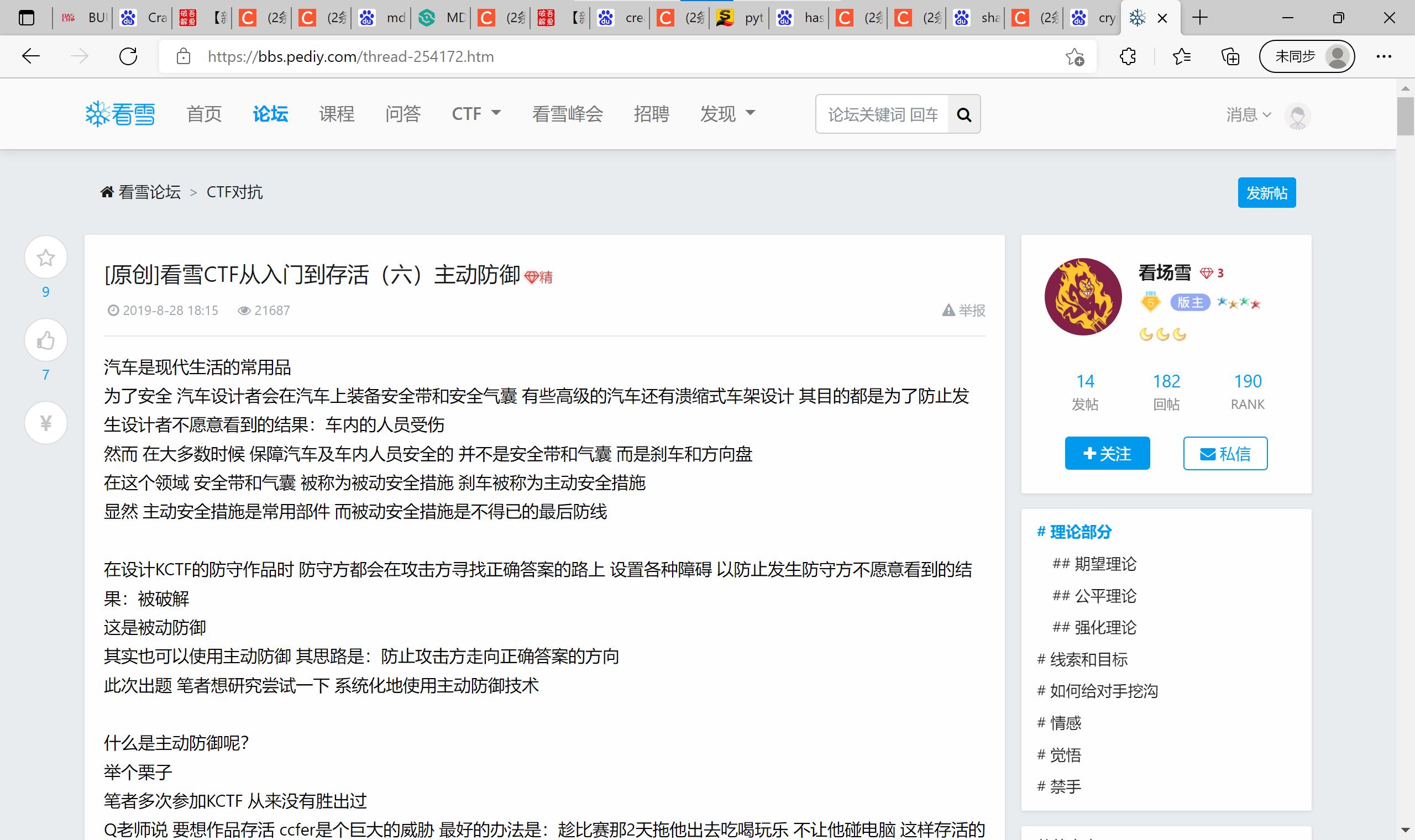
一般你做题得到看到这篇帖子的网址时候,你就被坑了,你看那清一色的评论
下面也什么都没有了,看fini_array,指向三个函数,第二个有价值。
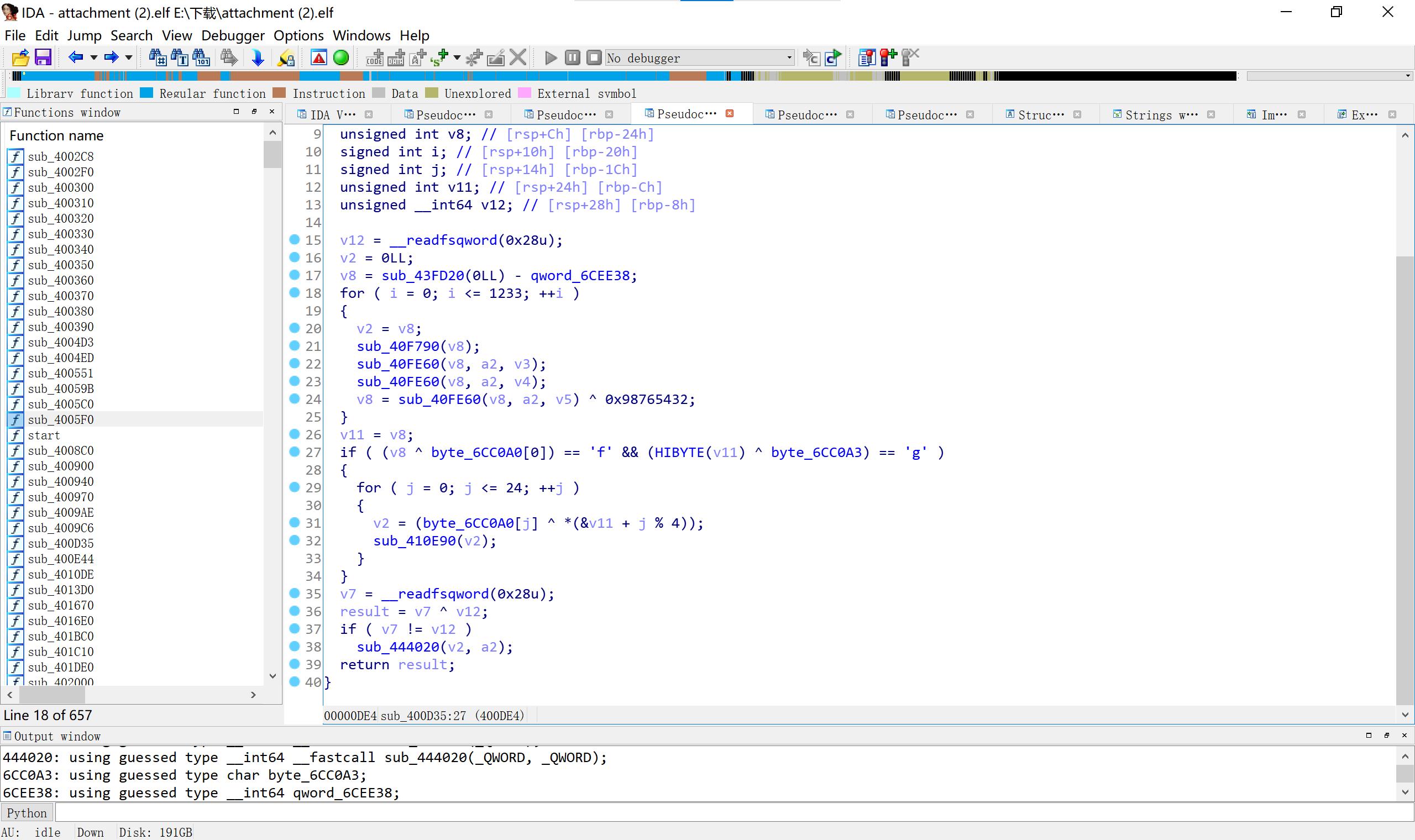
#include < iostream>
using namespace std;
int main()
int v17[]=73,111,100,108,62,81,110,98,40,111,99,121,127,121,46,105,127,100,96,51,119,125,119,101,107,57,123,105,121,61,126,121,76,64,69,67;
for(int i=0;i<=35;i++)
v17[i]^=i;
char p=v17[i];
cout<<p;
cout<<endl;
unsigned char ida_chars[] =
0x40, 0x35, 0x20, 0x56, 0x5D, 0x18, 0x22, 0x45, 0x17, 0x2F,
0x24, 0x6E, 0x62, 0x3C, 0x27, 0x54, 0x48, 0x6C, 0x24, 0x6E,
0x72, 0x3C, 0x32, 0x45, 0x5B
; string f=“flag”;
for(int i=0;i<4;i++)
f[i]^=ida_chars[i];
for(int i=0;i<25;i++)
ida_chars[i]^=f[i%4];
cout<<ida_chars[i];
23 login 感觉是web题,结果是披着web外套的re
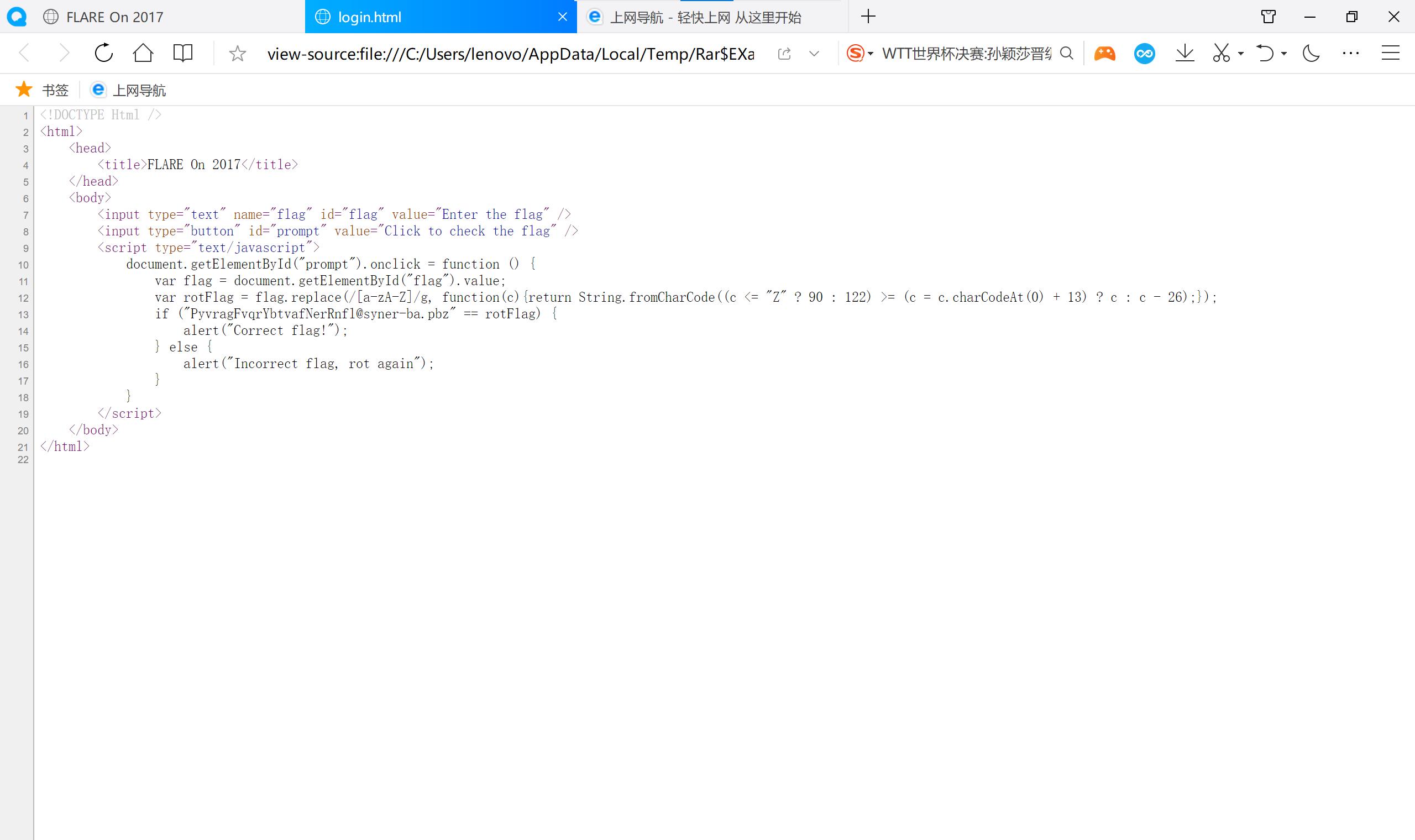
#include < iostream>
using namespace std;
int main()
string p=“PyvragFvqrYbtvafNerRnfl@syner-ba.pbz”;
for(int i=0;i<p.length();i++)
if(p[i]>=‘a’&&p[i]<=‘z’)
if(p[i]-13<97)
p[i]+=13;
else p[i]-=13;
else if(p[i]>=‘A’&&p[i]<=‘Z’)
if(p[i]-13<65)
p[i]+=13;
else p[i]-=13;
cout<<p[i];
24 re 在kali虚拟机中脱壳,upx -d 文件名 然后进ida(不知道怎么把虚拟机中的文件传到电脑上,就用在虚拟机上用qq小号以邮箱途径发给大号,正确用法是用ubantu,但有点复杂,不想搞)
解密
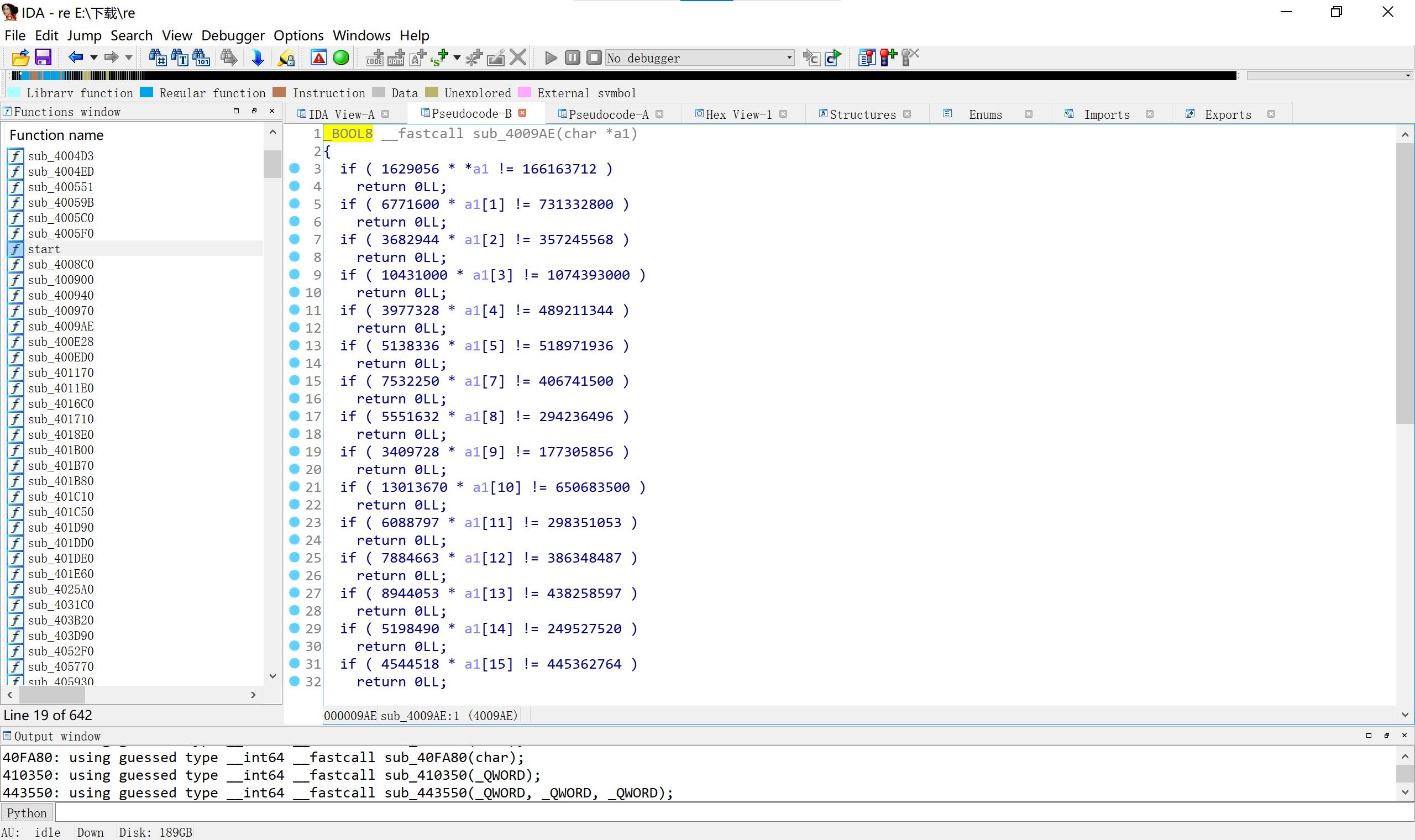
#include < iostream>
using namespace std;
int main()
char a1[32];
a1[0] = 166163712/ 1629056 ;
a1[1] = 731332800 / 6771600;
a1[2] = 357245568 / 3682944 ;
a1[3] = 1074393000/ 10431000 ;
a1[4] = 489211344/3977328 ;
a1[5] = 518971936/5138336 ;
a1[6]=‘0’;
a1[7] = 406741500/7532250 ;
a1[8] = 294236496/ 5551632 ;
a1[9] = 177305856/ 3409728 ;
a1[10] = 650683500/ 13013670 ;
a1[11] = 298351053 / 6088797 ;
a1[12] = 386348487 /7884663;
a1[13] = 438258597/8944053 ;
a1[14] = 249527520/5198490 ;
a1[15] = 445362764 / 4544518;
a1[17] = 174988800/3645600 ;
a1[16] = 981182160 /10115280 ;
a1[18] = 493042704 / 9667504;
a1[19] = 257493600/5364450 ;
a1[20] = 767478780/13464540 ;
a1[21] = 312840624/5488432 ;
a1[22] = 1404511500/14479500 ;
a1[23] = 316139670/ 6451830 ;
a1[24] = 619005024/6252576 ;
a1[25] = 372641472/7763364 ;
a1[26] = 373693320/7327320 ;
a1[27] = 498266640 / 8741520;
a1[28] = 452465676/8871876 ;
a1[29] = 208422720/ 4086720 ;
a1[30] = 515592000/9374400 ;
a1[31] = 719890500/5759124 ;
cout<<a1;
//a1[6]不知道,爆破的。
25signin,rsa 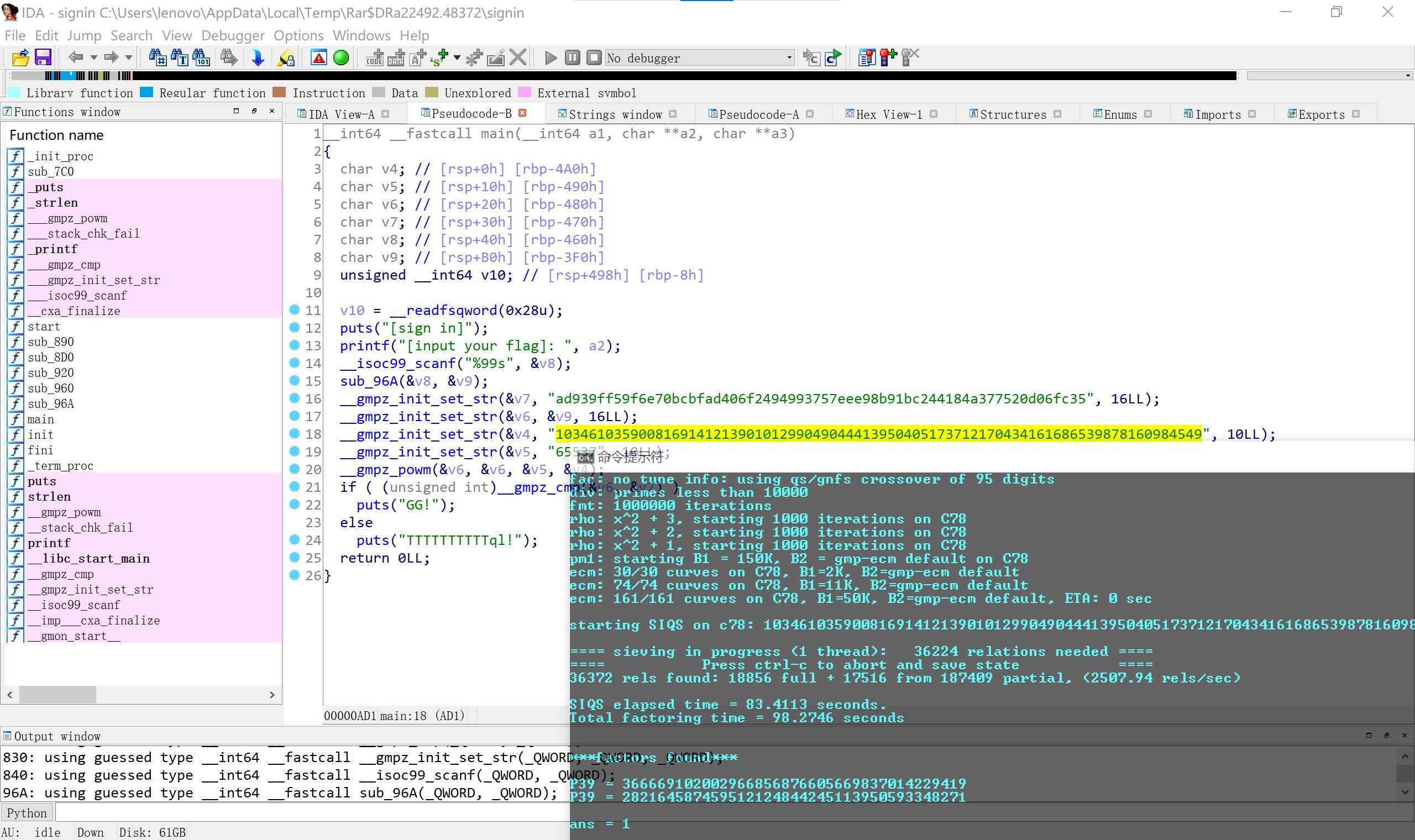
借网上的代码。。。 在自己做的过程中发现,Python3.10 没有gmpy2的库。。。
import gmpy2
import binascii
p = 282164587459512124844245113950593348271
q = 366669102002966856876605669837014229419
e = 65537
c = 0xad939ff59f6e70bcbfad406f2494993757eee98b91bc244184a377520d06fc35
n = 103461035900816914121390101299049044413950405173712170434161686539878160984549
d = gmpy2.invert(e, (p-1) * (q-1))
//48FFDA96436D1CC92E4415DE8C4D14FA4B6FD5D36D94B390D2308ADC1234CCCFBE38B158D8087
m = gmpy2.powmod(c, d, n)
print(binascii.unhexlify(hex(m)[2:]).decode(encoding=“utf-8”))
26level1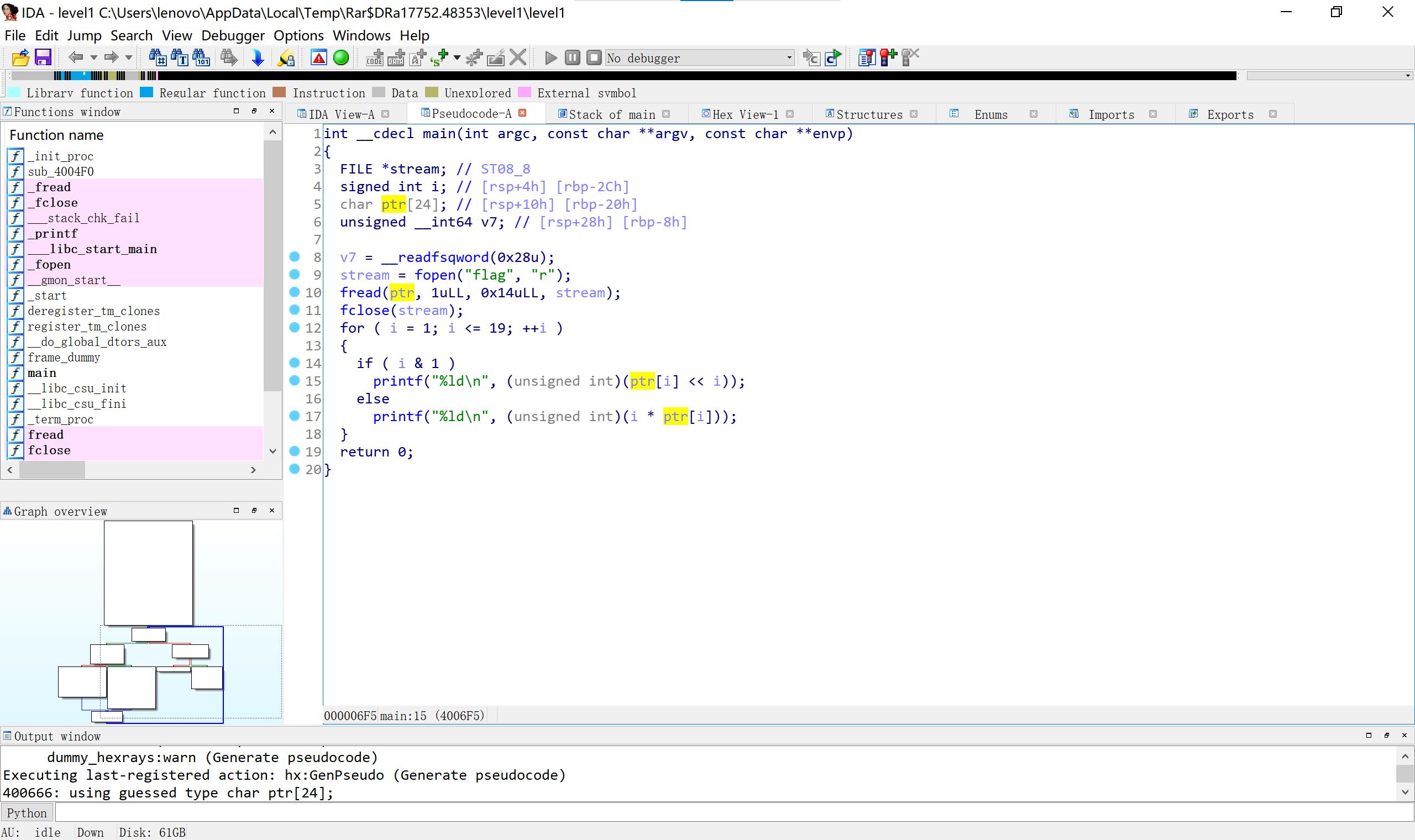
#include < iostream>
using namespace std;
int main()
long long int a[20]=0,198,232,816,200,1536,300,6144,984,51200,570,92160,1200,565248,756,1474560,800,6291456,1782,65536000;
for(int i=1;i<20;i++)
if(i&1)
a[i]=a[i]>>i;
else a[i]/=i;
for(int i=0;i<20;i++)
char p=a[i];
cout<<p;
27youghterdriver 有壳,脱壳,还是说一下,脱壳不一定要脱的很好,只要ida能识别其中的函数及数据就行。但我这次脱的太差了,函数都识别错了,一个反面教材。
创建了两个线程,得依次分析
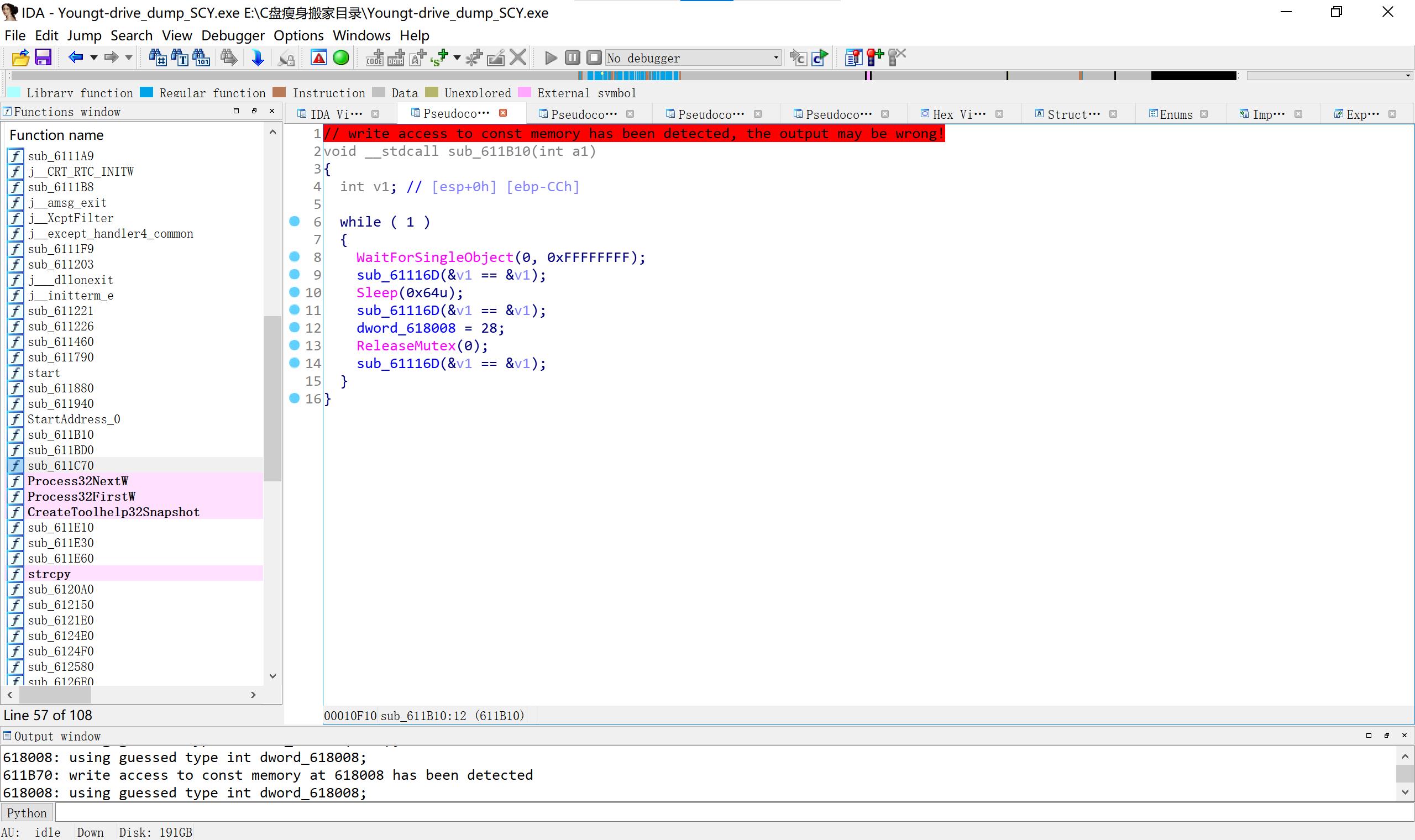
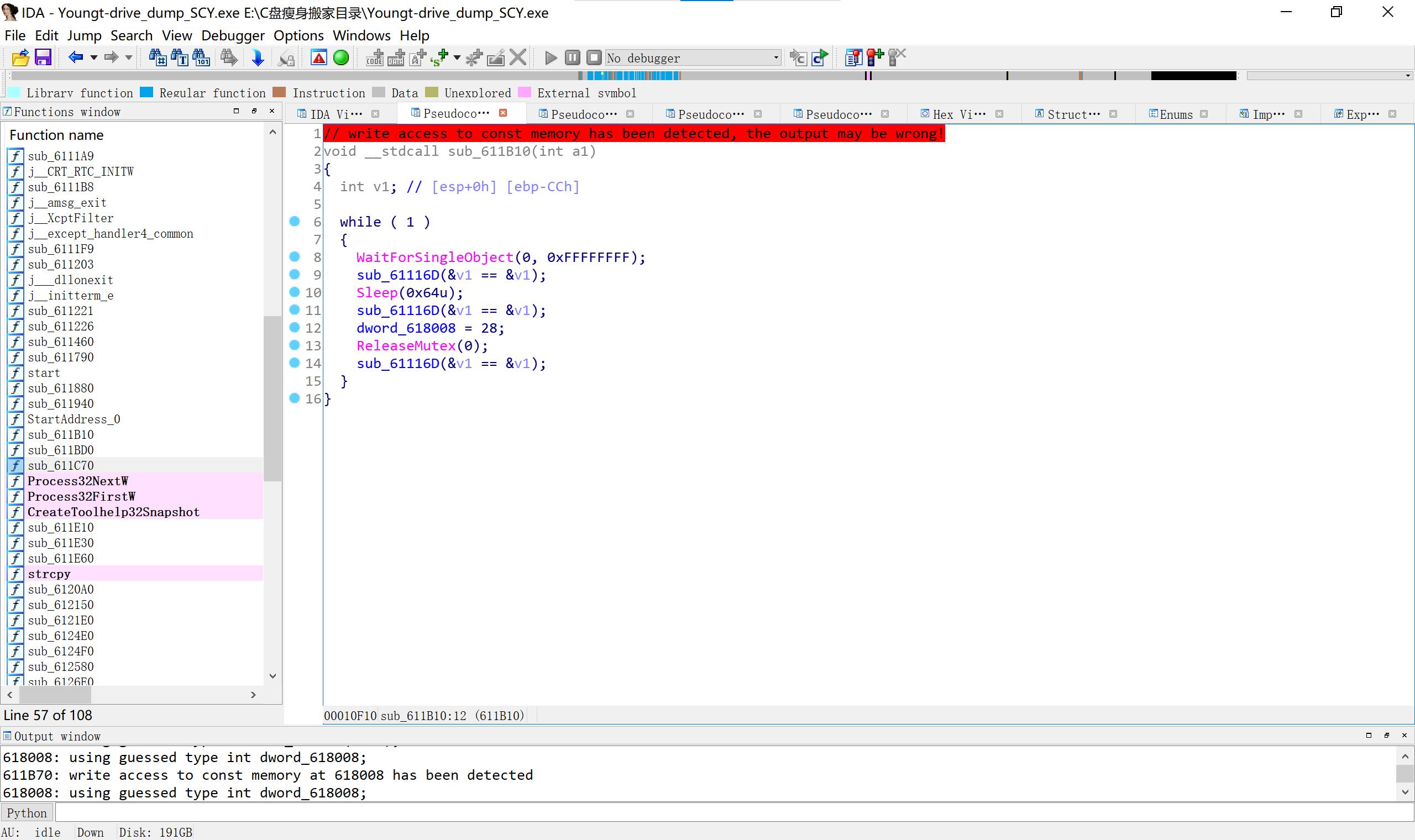
第二个感觉不对劲(1是上面的红字,2是这离谱的函数)
看汇编才知道dword_618008 -1不是数值减一,而是指针位置往前一格。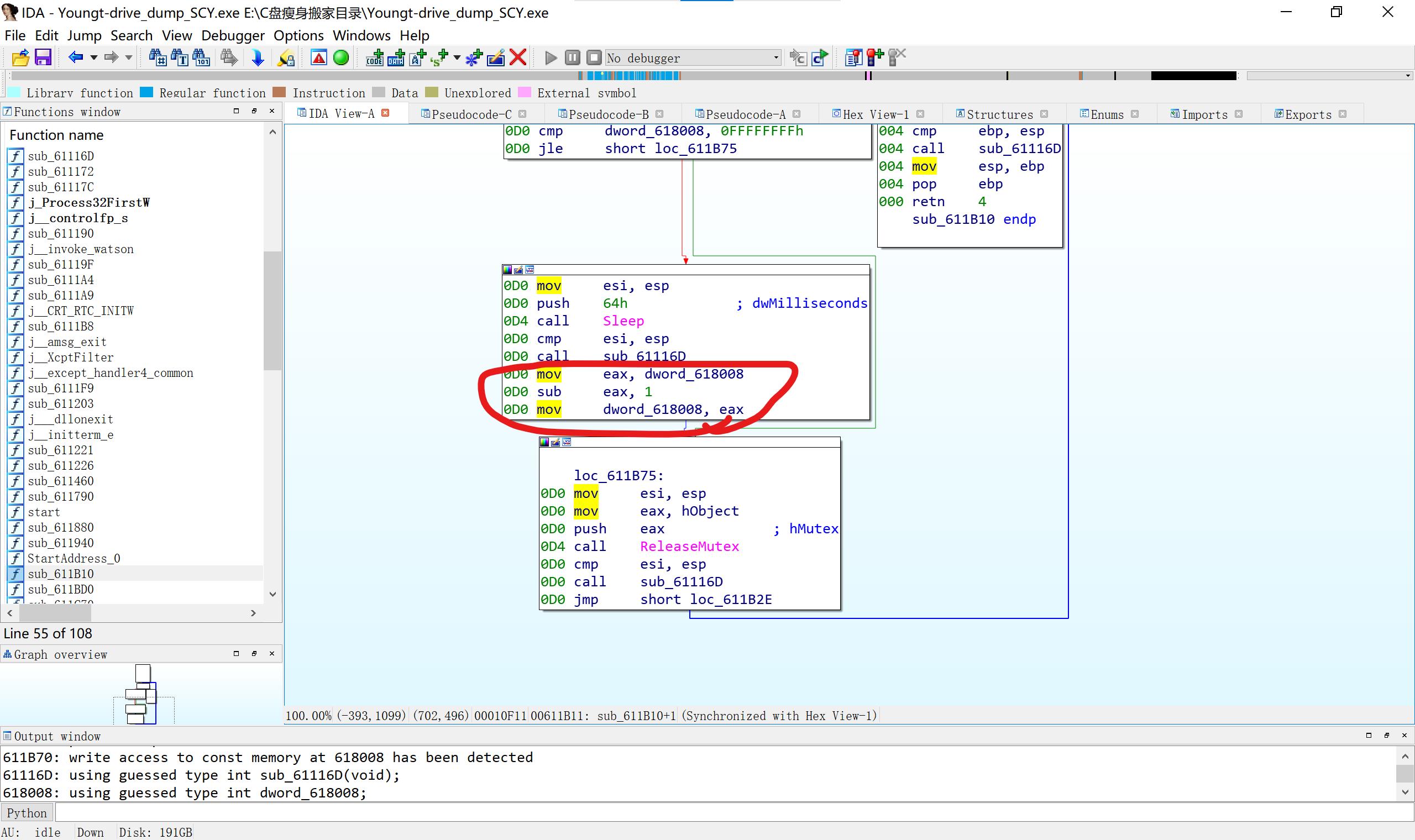
然后就不会了,双线程???看别人的writeup才知道是交替进行的意思
附代码(有点问题)
#include < iostream>
using namespace std;
int main()
string str=“0abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ”;//0来占个位
string k1=“TOiZiZtOrYaToUwPnToBsOaOapsyS”;
string k2=“QWERTYUIOPASDFGHJKLZXCVBNMqwertyuiopasdfghjklzxcvbnm”;
for(int i=0;i<k1.length();i++)
if(i%2==0)
cout<<k1[i];
else
for(int j=0;j<k1.length();j++)
if(k2[j]==k1[i])
cout<<str[j];
28 transform 交换表后异或
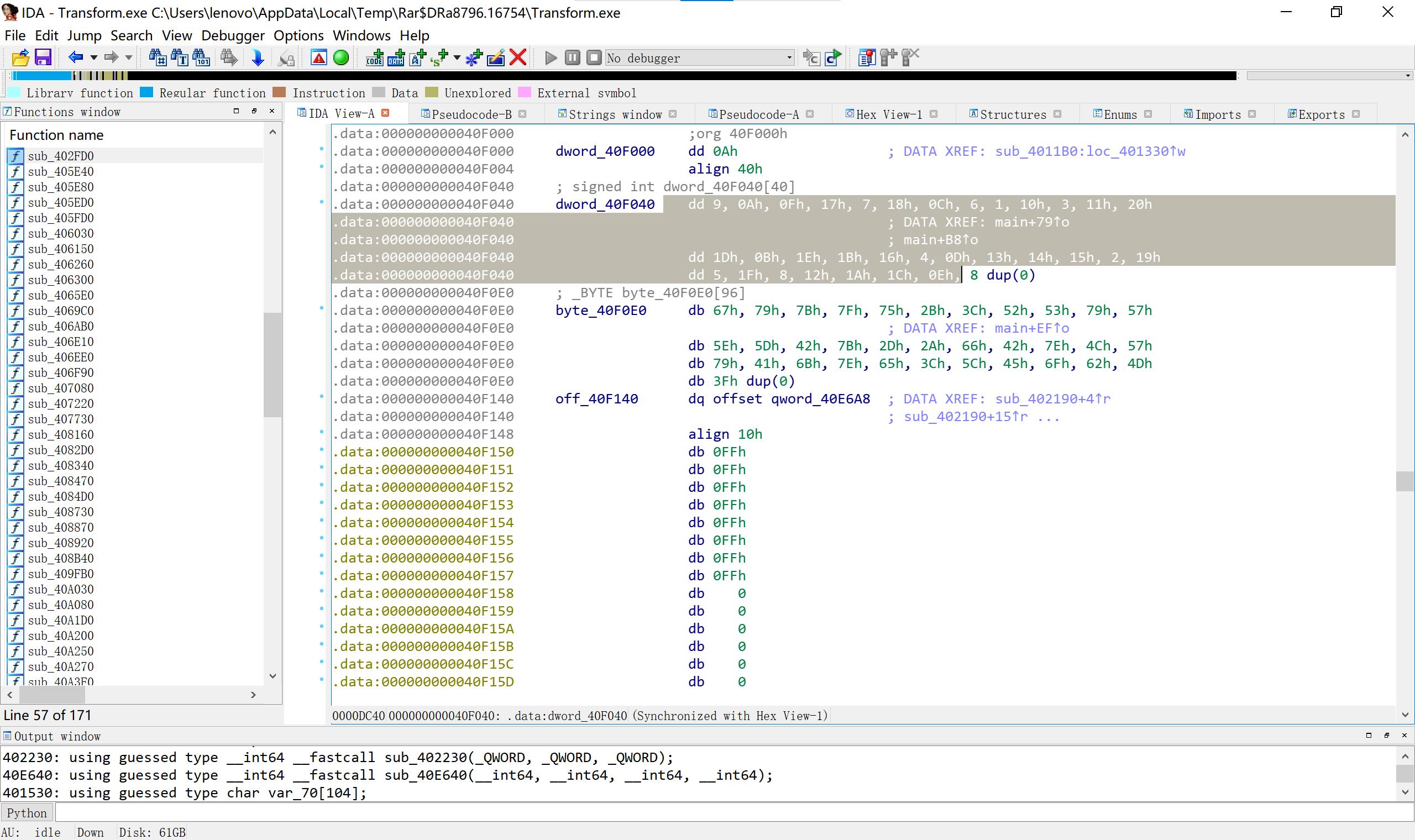
#include < iostream>
using namespace std;
int main()
unsigned char ida_chars[]=0x09,0x0A,0x0F,0x17,0x07,0x18,0x0C,0x06,0x01,0x10,0x03,0x11,0x20,0x1D,0x0B,0x1E,0x1B,0x16,0x04,0x0D,0x13,0x14,0x15,0x02,0x19,0x05,0x1F,0x08,0x12,0x1A,0x1C,0x0E;
unsigned char ida_char[] =
0x67, 0x79, 0x7B, 0x7F, 0x75, 0x2B, 0x3C, 0x52, 0x53, 0x79,
0x57, 0x5E, 0x5D, 0x42, 0x7B, 0x2D, 0x2A, 0x66, 0x42, 0x7E,
0x4C, 0x57, 0x79, 0x41, 0x6B, 0x7E, 0x65, 0x3C, 0x5C, 0x45,
0x6F, 0x62, 0x4D;
for(int i=0;i<33;i++)
ida_char[i]^=ida_chars[i];
for(int i=1;i<33;i++)
for(int j=0;j<33;j++)
if(ida_chars[j]==i)
cout<<ida_char[j];
29 usualcrypt base64 变表,先开始我没看到变表
#include < iostream>
using namespace std;
int main()
int i=6;
char v1;
string a=“ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/”;
dov1=a[10+i];
a[10+i]=a[i];
a[i]=v1;
i++;
while(i<15);
cout<<a;
然后我发现不行,仔细看函数,发现还有大小写转换。
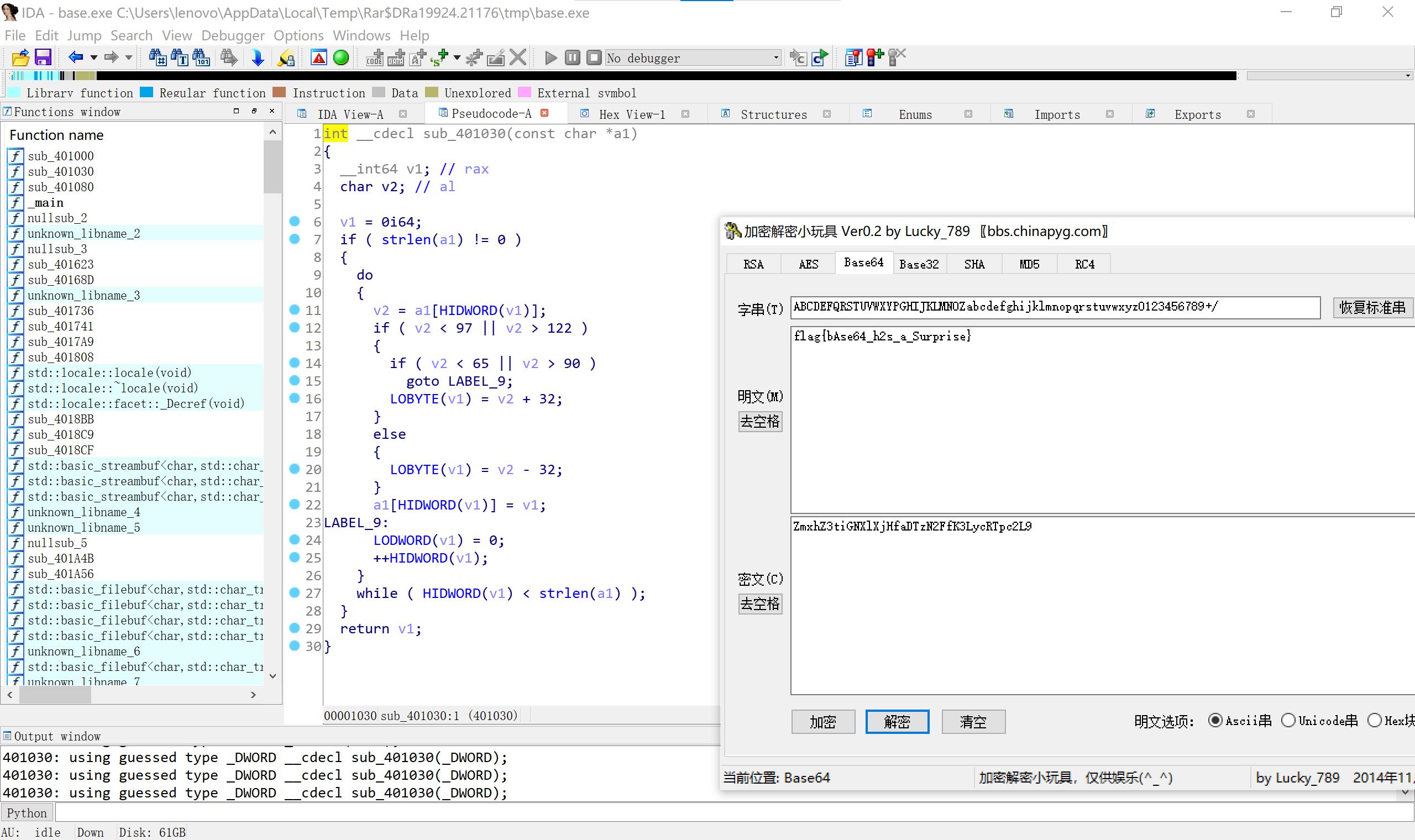
30level2 upx脱壳 明码
31 相册 base64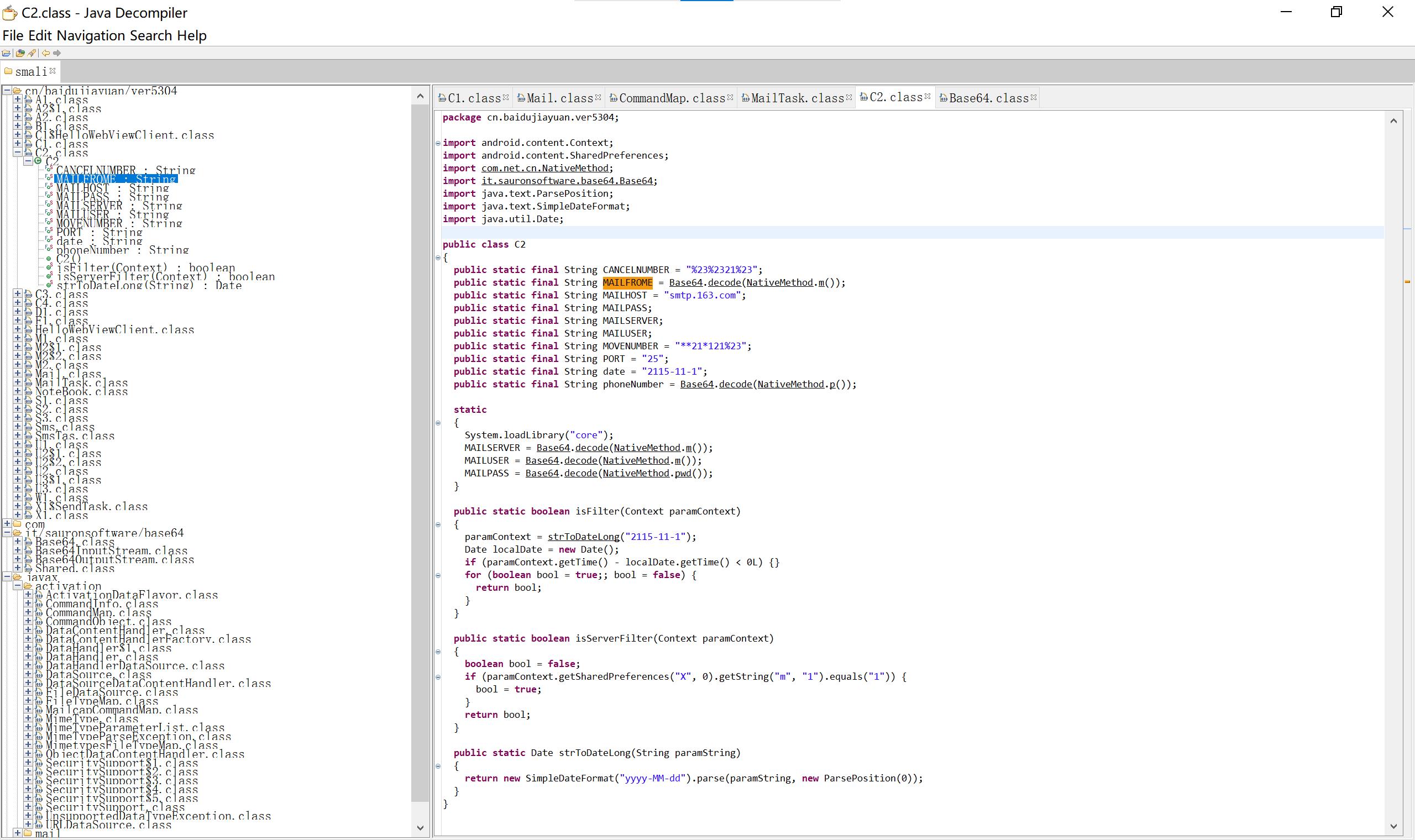
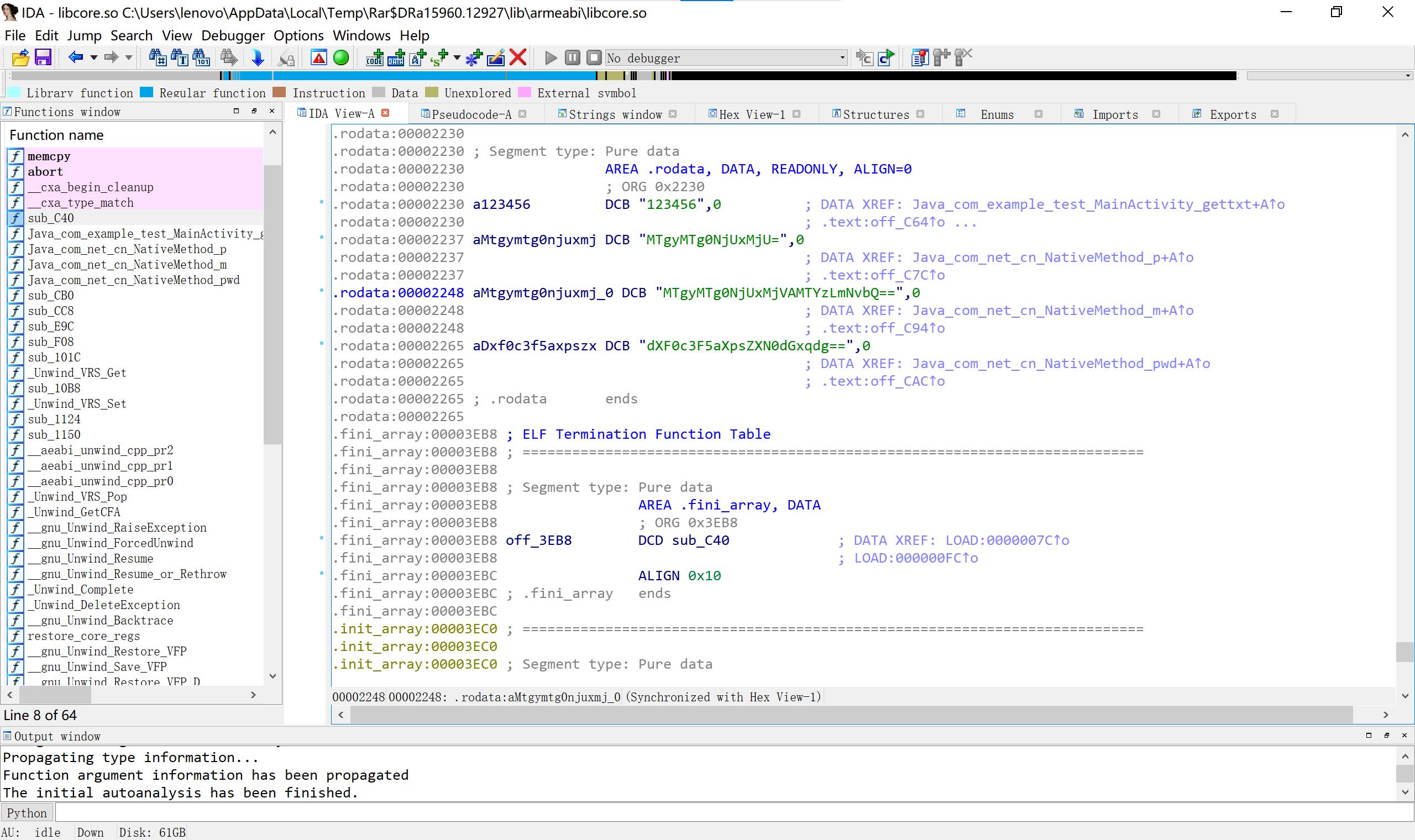
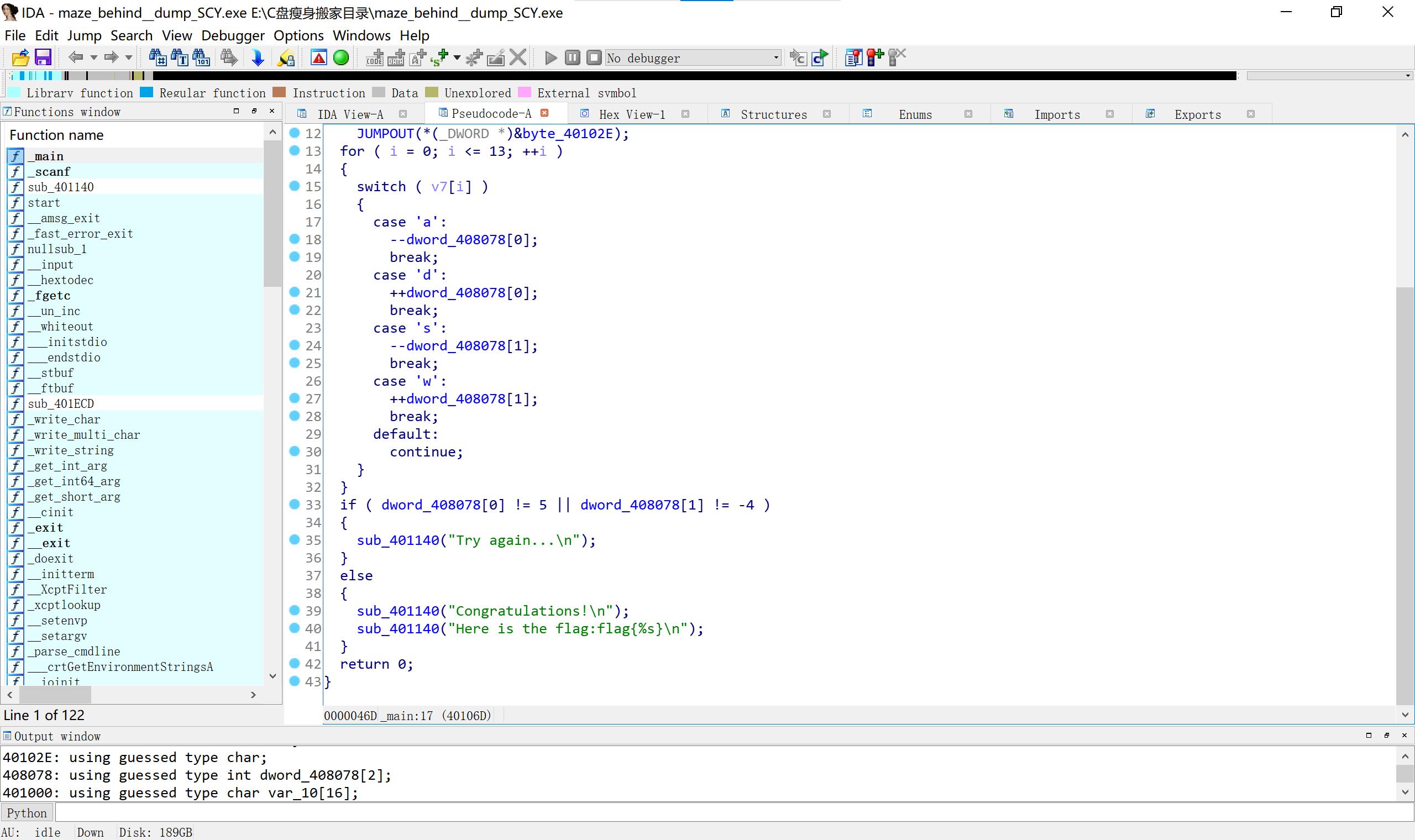
32 maze upx脱壳但我脱不好系列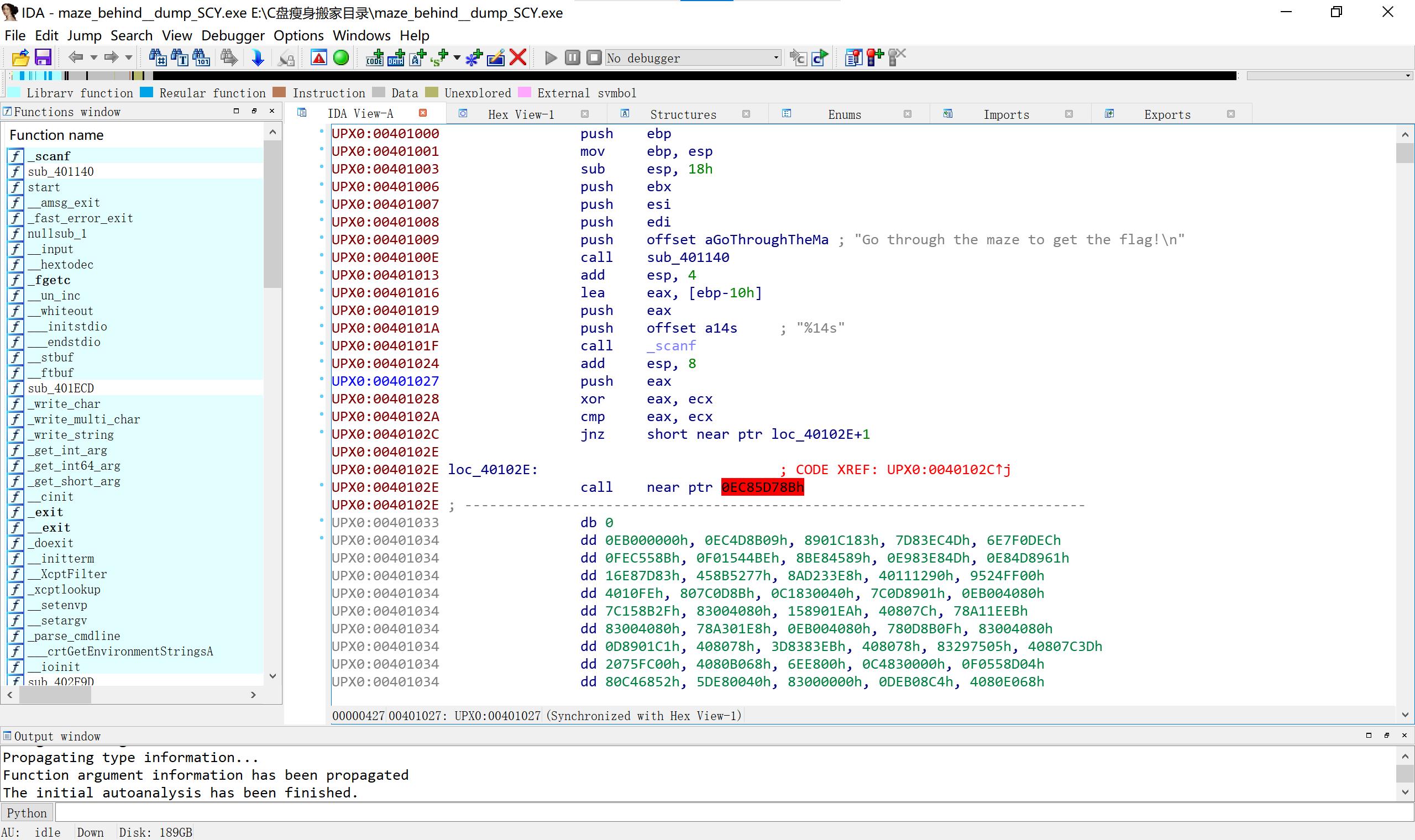
…+…
… …
… …
… …
… …F…
… …
…
70个字符710 不行,107可以
它还有花指令,对 call near ptr 0ecb5d7800h先按d 再把除dbe8h的部分按c 去除花指令。
按p,按f5即可
以上是关于buuoj re逆向前32题writeup(截图+c++源码+过程)的主要内容,如果未能解决你的问题,请参考以下文章