Security ❀ Windows系统下如何使用sqlmap
Posted 国家级干饭型选手°
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Security ❀ Windows系统下如何使用sqlmap相关的知识,希望对你有一定的参考价值。
1、下载sqlmap
sqlmap下载链接:https://sqlmap.org/
点击此处自动跳转下载sqlmap网页
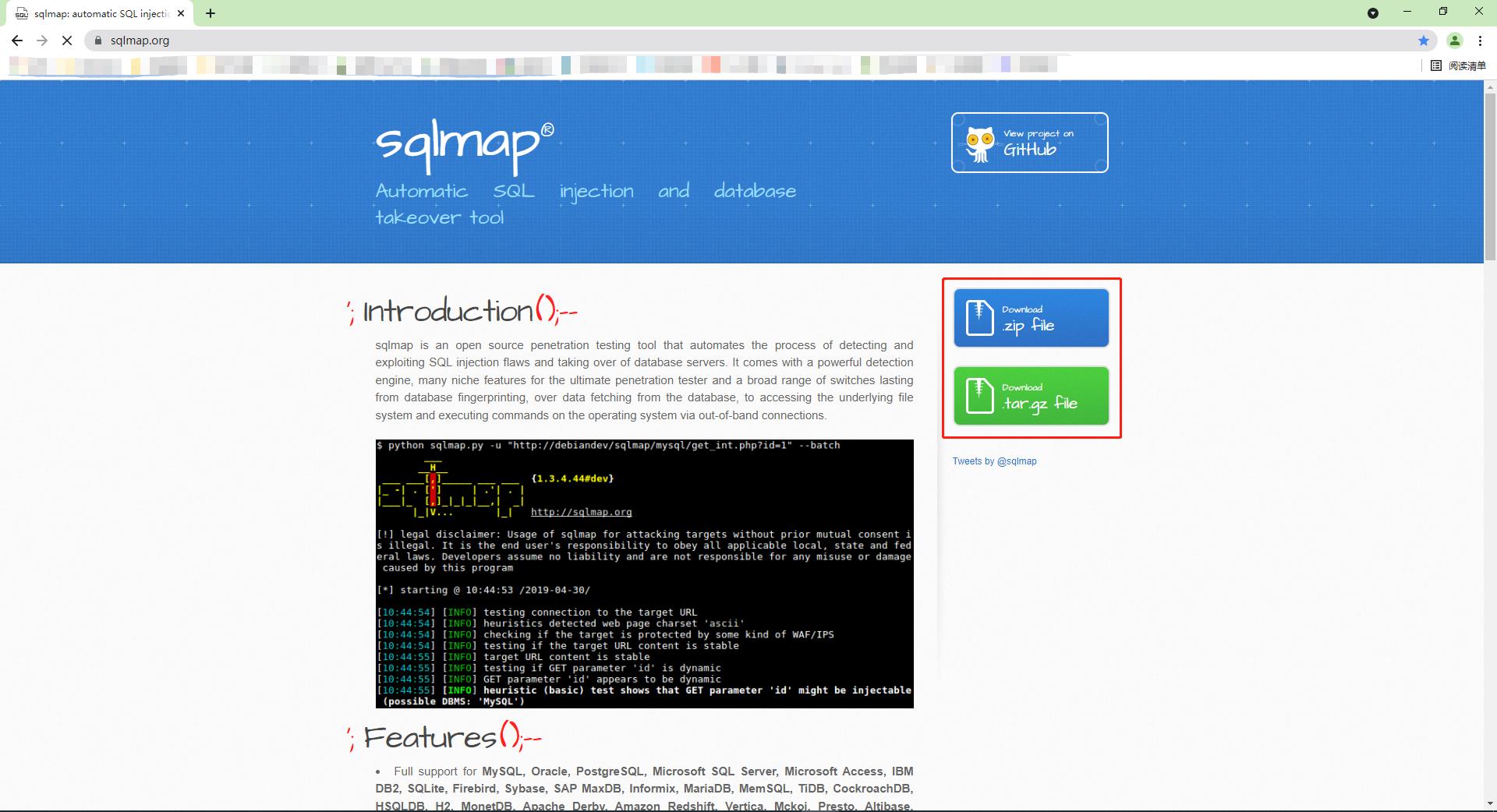
点击红框内图标进行下载sqlmap,sqlmap为python编译,需要运行在python环境下;
2、安装python
Python下链接:https://www.python.org/getit/
点击此处自动跳转下载python网页
可以在一些软件安装的APP中进行下载,安装过程较为简单,若是已经安装python却不知道对应路径的情况可以使用PATH进行查询;
# 使用CMD查询是否安装python
C:\\Users\\Administrator>python --version
Python 3.8.5
环境变量中查询对应的python安装路径;

3、将sqlmap放入python目录下
解压sqlmap文件,并改名为sqlmap(可以不进行修改)
将改名的sqlmap目录文件放入python运行目录下;

4、建立快捷方式
点击桌面,新建快捷方式;

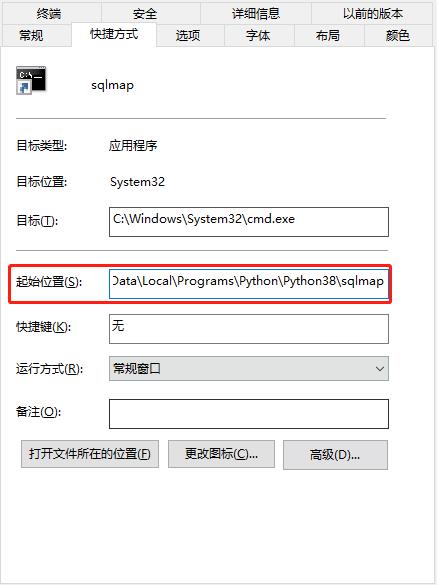
路径为python运行目录下sqlmap的文件路径;

快捷方式如下所示:
框内填入python运行目录下sqlmap的文件路径;
结果验证:
5、sqlmap帮助手册
C:\\Users\\Administrator\\AppData\\Local\\Programs\\Python\\Python38\\sqlmap>sqlmap.py --help
___
__H__
___ ___[,]_____ ___ ___ {1.5.8#stable}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
Usage: python3 sqlmap [options]
Options:
-h, --help Show basic help message and exit
-hh Show advanced help message and exit
--version Show program's version number and exit
-v VERBOSE Verbosity level: 0-6 (default 1)
Target:
At least one of these options has to be provided to define the
target(s)
-u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1")
-g GOOGLEDORK Process Google dork results as target URLs
Request:
These options can be used to specify how to connect to the target URL
--data=DATA Data string to be sent through POST (e.g. "id=1")
--cookie=COOKIE HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..")
--random-agent Use randomly selected HTTP User-Agent header value
--proxy=PROXY Use a proxy to connect to the target URL
--tor Use Tor anonymity network
--check-tor Check to see if Tor is used properly
Injection:
These options can be used to specify which parameters to test for,
provide custom injection payloads and optional tampering scripts
-p TESTPARAMETER Testable parameter(s)
--dbms=DBMS Force back-end DBMS to provided value
Detection:
These options can be used to customize the detection phase
--level=LEVEL Level of tests to perform (1-5, default 1)
--risk=RISK Risk of tests to perform (1-3, default 1)
Techniques:
These options can be used to tweak testing of specific SQL injection
techniques
--technique=TECH.. SQL injection techniques to use (default "BEUSTQ")
Enumeration:
These options can be used to enumerate the back-end database
management system information, structure and data contained in the
tables
-a, --all Retrieve everything
-b, --banner Retrieve DBMS banner
--current-user Retrieve DBMS current user
--current-db Retrieve DBMS current database
--passwords Enumerate DBMS users password hashes 列举DBMS数据库密码hash值
--tables Enumerate DBMS database tables 列举DBMS数据库表名
--columns Enumerate DBMS database table columns 列举DBMS数据库列名
--schema Enumerate DBMS schema 列举DBMS数据库模式
--dump Dump DBMS database table entries 下载数据库DBMS表项
--dump-all Dump all DBMS databases tables entries 下载数据库DBMS所有表项
-D DB DBMS database to enumerate 指定DBMS数据库
-T TBL DBMS database table(s) to enumerate
-C COL DBMS database table column(s) to enumerate
Operating system access:
These options can be used to access the back-end database management
system underlying operating system
--os-shell Prompt for an interactive operating system shell
--os-pwn Prompt for an OOB shell, Meterpreter or VNC
General:
These options can be used to set some general working parameters
--batch Never ask for user input, use the default behavior
--flush-session Flush session files for current target
Miscellaneous:
These options do not fit into any other category
--wizard Simple wizard interface for beginner users
以上是关于Security ❀ Windows系统下如何使用sqlmap的主要内容,如果未能解决你的问题,请参考以下文章
如何将 Windows.Security.Credentials.UI 命名空间包含到 C# 项目中
Spring3,Security3:系统可以在 Windows 上运行,但不能在 Linux 上运行 java.lang.IllegalArgumentException
windows下CTS测试android.cts.security.SELinuxHostTest-- testAllEnforcing fail