2021 陇原抗疫 WriteUp
Posted 是Mumuzi
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了2021 陇原抗疫 WriteUp相关的知识,希望对你有一定的参考价值。
希望疫情早日结束
注:打*的是赛后出的
总WP:https://wp.n03tack.top/posts/14620/
Misc
soEasyCheckin
base32,但有问题,倒数出现了0$,0–>O,$—>S,得到一串hex。
结果hex那里又有问题,具体是出在83¥6988ee这里
根据规律,每6个字节的第1个字节为e,然后把¥替换成e
得到社会主义核心价值观编码,但是还是有个地方是错误的,中间有一段为:和谐斃明平
然后把他那个斃随便改一下,我改的“富强”
解码得到的SET{Qi2Xin1Xie2Li4-Long3Yuan0Zhan4Yi4}
根据拼音,可以知道是Yuan2
所以最终flag为:
SET{Qi2Xin1Xie2Li4-Long3Yuan2Zhan4Yi4}
打败病毒
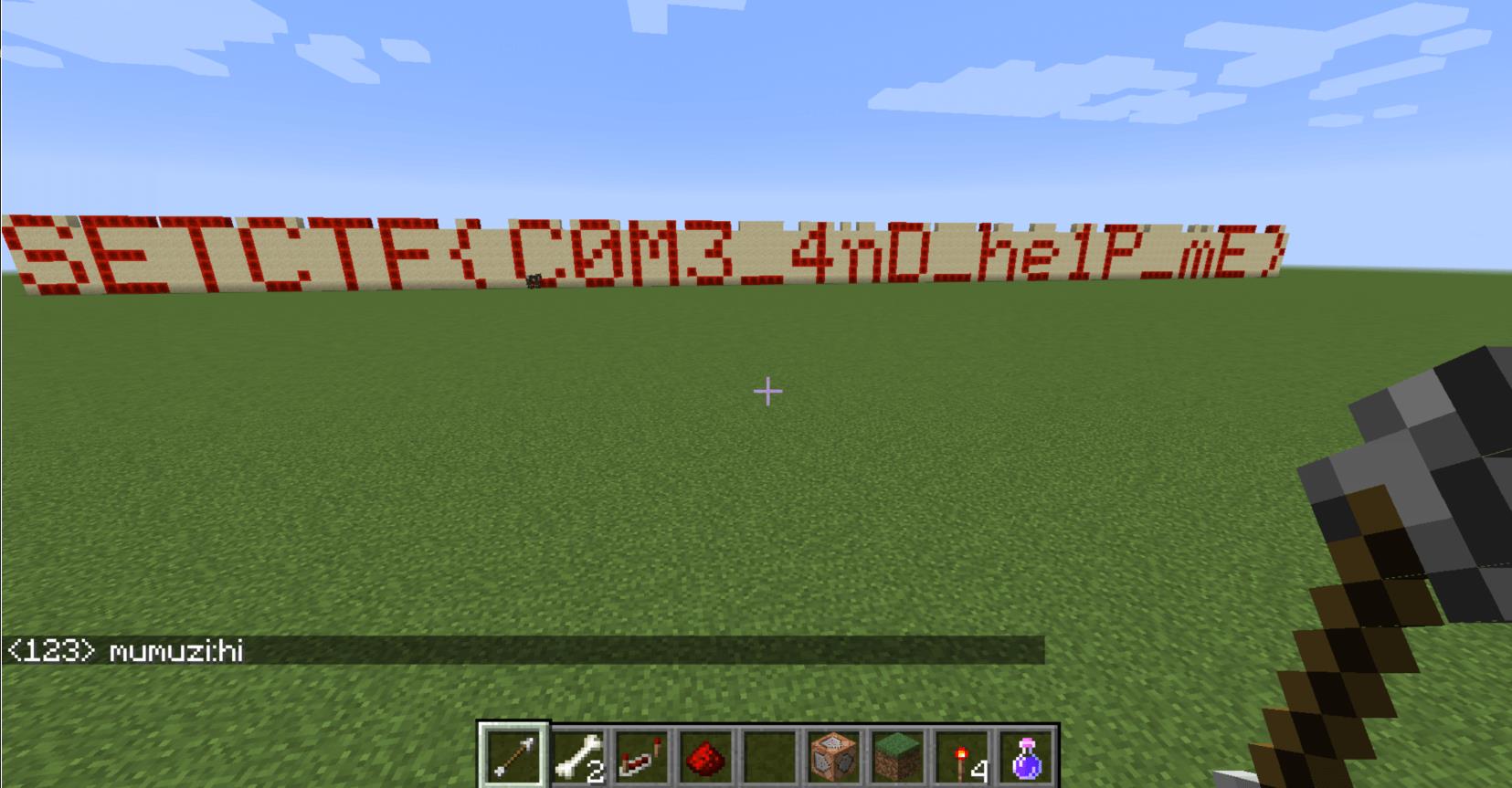
游戏打开之后发现在末地,打完末影龙后没有反应,flag藏在终末之诗里,于是直接去找文本
在.minecraft/version/陇原战“疫”.jar下
将其改为zip,找到assets/minecraft/texts/end.txt,得到11F9sACbBBBWKTiClYDtNF2yIEfThXdfIGPxF
base62解码即可
SETCTF{Fi9ht1ng_3ItH_V1rUs}
SOS
拨号音,踩正确的来组合出flag
用手机录音,然后m4a格式转wav格式,之后DTMF,因为录的总有问题,所以一共录了三次

前面都没出现8,这次终于出现了8,所以应该是6830AB1C75,得到flag
EasySteg
哥哥球球了别套了再套下去套神都哭了呜呜呜
JK为单图盲水印(java),用imagein也行的

然后在flag.rar的注释里面有一串tab和space组成的密文,转space转0,tab转1
然后解压,在flag.png的末尾有另一个png,那个png明显有flag字样,用stegsolve反一下色即可看清

flag{156cca8e
然后还在这个图片后面发现了明显的oursecret的特征,结合上面的base64(-b81b-)
得到oursecret的密码为LWI4MWIt

除了数字以外,没有重复字符,里面还有{},结合01串,得出为哈夫曼编码,利用红明谷的脚本即可解码
对应关系看脚本即可理解
import copy
import re
def dfs(c, d):
if len(c.keys()) == 1:
# g = {'j':29,'z':31,'7':25,'e':31,'l':23,'6':37,'4':32,'p':38,'h':27,'g':26,'x':28,'i':25,'u':27,'n':25,'8':36,'0':24,'o':23,'c':28,'y':24,'1':29,'b':26,'m':27,'2':28,'v':25,'d':33,'f':28,'9':33,'t':21,'w':22,'a':31,'r':24,'s':16,'k':32,'5':25,'q':23,'3':32,'{':1,'-':4,'}':1,}
# num = 0
# for k in g.keys():
# num += g[k] * len(d[k])
# print(num)
# print(c, d)
g = {}
for k in d.keys():
g[d[k]] = k
a = '1110111111000100001111000011010001101111100110100011110111100010100111110111001101111100011000111111111101011100011111100111000011010001111010011011111001110111100010000111001110011110111000111111100111011111011011101011110111110101101101101000110101011101011111111011110111101101110101111010011010110100011100100011010101111010111110110110111100011010111010111110110110111001001011011110100111010111111010111111011110111101001111010111110111101011100100111100101011011101110111111001010110100100110111110011111001101000111110111001011001110000111000011110000110111110011000011100001101100110100011100001111110011110000110110011010001110011101100001110110001001111111110010110011010001111011110110010011011111000001111100010010001001111101110110111111101101001001001011011101111101101101111001101001011011111100111110110110110110111110111010110111011110011111011011011010000110111111001111110111100111010111110011010011011110101001101110111100110110111101001101011101011111001101111011101101010111010111111001111110111010110110110101001101011111101001101000111010010111000010011001110111110111101101111101101110111010110100101101101101011010111111101111001110111111110011010110100101101111011011101100111001000001111001100100101011000000111100101011001000101100100000011001011001001000001111001100100101011000000111100101011001011111111001010001010001010010000011110011001001010110000001111001010110010001011001010001010000111100100000111100110010010101100000011110010101100101010010101100101010010000011110011001001010110000001111001010110010011001001010110000011011111001000001111001100100101011000000111100101000101000110111110010000001100101010010000011110011001001010010101100000011110010101100100010001001000011111110001010010000011110011001001010110000001111001010110010111111110010100010110001000100100000111100110010010101100000011110010100010100011011111001000000110010101001000001111001100100101011000000111100101011001001100100101011000001101111100100000111100110010010101100000011110010101100100010110010000001100101100100100000111100110010010101100000011110010100010100010100101011000001101111100100000111100110010010101100000011110010100101011001000101100100000011001011001001000001111001100100101011000000111100101011001011111111001010001010001010010000011110011001001010110000001111001010110010001000100100001111111000101001000001111001100100101011000000111100101011001000101100100000011001011001001000001111001100100101011000000111100101011001010100100000011001011111111001000001111001100100101011000000111100101011001000101100100000011001011001001000001111001100100101011000000111100101011001000100010010100100001111111000101001000001111001100100101011000000111100101011001010100100000011001011111111001000001111001100100101011000000111100101000101000101001010110000011011111001000001111001100100101011000000111100101000101000110111110010000001100000011110010000011110011001001010110000001111001010001010000001001010001010000111111011010011110011101011111011100001011010110101111010001111100110111110101111110110101010011101111101100100000101111011010111101101101110011001110001100011111001110010000010111100010111101111111101101101110000111010000101111110001100000110001110010100100000110000101110000100010110111100000101110011111110000111011010111101001101001101111101000100101111101101011111100111111001110001100001000011011111000001111100010011001110111101111111011111001000111000011101101110000111011011110011101111111011011010110100011111000100101111111011100000100000101110010111100011010110100011111101111001110101111010111011011100100110011101111100111101111100000001001001101001101111111101101011110111011110011101001101111010100110111011101011110011100000011010010111111000100110011101111101011110111110111'
m = ''
st = 0
while st < len(a):
ed = st + 1
while ed <= len(a):
if a[st:ed] in g.keys():
m += g[a[st:ed]]
break
else:
ed += 1
st = ed
print(m)
else:
k0 = list(c.keys())[0]
k1 = list(c.keys())[1]
if c[k0] > c[k1]:
k0, k1 = k1, k0
for k in list(c.keys())[2:]:
if c[k] < c[k1]:
if c[k] < c[k0]:
k0, k1 = k, k0
else:
k1 = k
for a in k0:
d[a] = '0' + d[a]
for a in k1:
d[a] = '1' + d[a]
c[k0+k1] = c[k0]+c[k1]
del c[k0]
del c[k1]
dfs(copy.deepcopy(c), copy.deepcopy(d))
c = {'n':9,'S':2,'B':3,'I':6,'U':6,'L':1,'O':3,'R':2,'F':3,'Y':1,'G':2,'H':3,'v':9,'N':2,'M':1,'Z':1,'D':6,'T':1,'h':18,'o':16,'u':17,'b':9,'s':7,'r':4,'g':8,'f':10,'a':14,'m':2,'i':20,'p':2,'e':14,'w':7,'q':2,'y':8,'P':1,'J':2,'E':2,'C':1,'V':1,'A':1,'j':4,'k':5,'x':5,'t':3,'c':6,'8':24,'9':56,'{':1,'3':217,'d':97,'4':83,'6':54,'0':25,'1':12,'2':10,'5':8,'7':10,'}':1,'l':4,'Q':1,'W':1,'z':1}
d = {}
for k in c.keys():
d[k] = ''
dfs(copy.deepcopy(c), copy.deepcopy(d))
#nSBIULORFYGHvNMIOUZSDTNhnoubuosrgfbouvasmruiohauiopewgvfbwuivpqynqwUPIFJDDBUEDUIDHBUIDCVHJIOAejikxneiwkyiohwehiooiuyhiosehfhuiaetyhovauieyrghfuotgvac89xcboiyuweagihniaweo{3d46303d39463d39383d41393d46303d39463d39323d38433d46303d39463d39383d38463d46303d39463d39333d39333d46303d39463d39303d39453d46303d39463d38453d41333d46303d3d39463d39373d42433d46303d39463d39323d38373d46303d39463d38453d41333d46303d39463d39303d39453d46303d39463d39383d41393d46303d39463d38433d39453d46303d39463d3d39383d41393d46303d39463d39323d38433d46303d39463d39373d42433d46303d39463d39383d41393d46303d39463d39333d41323d46303d39463d39383d41393d46303d39463d39373d3d42433d46303d39463d39333d41323d46303d39463d38433d39453d46303d39463d38453d41463d46303d39463d38443d3846}huilagsieufrcb78QWEGF678Rniolsdf149687189735489246avaeukighf6497ejixcnbmlolohnbasik2647893hasfhuvzxchbjkaefgyhuetyuhjadfxcvbn
{}里面的内容拿去hex,发现是Quoted Printable,但是有些地方出现了两次==,于是将其重复的删掉,得到
😩💌😏📓🐞🎣🗼💇🎣🐞😩🌞😩💌🗼😩📢😩🗼📢🌞🎯🍏
不是base100,所以拿去试试国外的一种,以前做la佬的ctfshow月饼杯_共婵娟用到的
https://github.com/pavelvodrazka/ctf-writeups/tree/master/hackyeaster2018/challenges/egg17

拼接起来,得到flag
flag{156cca8e-b81b-4157-9f39-4c41f4a4facb}
*ez_misc
hint是零宽,说的是和piet很像的一种esolang,然后结合ctfshow6月赛八神的babyLSBwithHelicopter
可以知道是brainloller
然后010打开,提示解出来是后面steghide的密码,并且CRC报错,用爆CRC的脚本一爆就发现正确宽度为14,高为12
用bftools解,bftools.exe decode brainloller bf.png,得到的bf再去解码得到密码Hello Worl
但是解不出来,于是用我6月赛写的脚本去解https://blog.csdn.net/qq_42880719/article/details/117479024
解出来是Hello Worle!,我猜是Hello World!
结合题目新上的hint,得到的密码我试过有
Hello Worl
Hello_Worl
Hello Worle!
Hello_Worle!
Hello World!
Hello_World!
Hello World
Hello_World
可惜都不对,通过出题人的朋友问了下出题人,他朋友也表示解不出来,但是出题人是能解出来的(好像用的是本地的附件)
所以我总感觉是比赛题目附件的问题?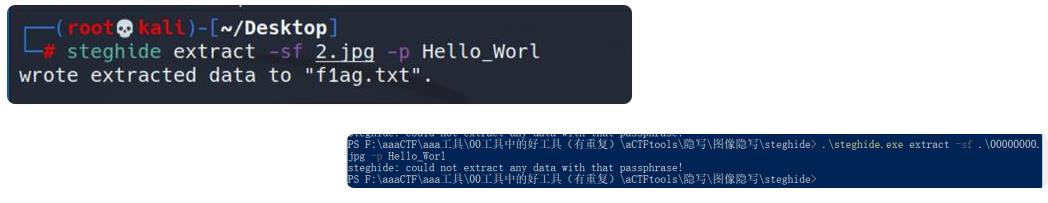
—17:02—:经过一个半小时的积极反馈



就bftools.exe解出来的把空格替换为下划线Hello_Worl解steghide,得到个文本
后面是一个熊曰,然后就完事
Re
EasyRe
flag就在常量里面。。
flag{fc5e038d38a57032085441e7fe7010b0}
以上是关于2021 陇原抗疫 WriteUp的主要内容,如果未能解决你的问题,请参考以下文章