安卓逆向 -- 实战某峰窝APP(动态分析)
Posted web安全工具库
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了安卓逆向 -- 实战某峰窝APP(动态分析)相关的知识,希望对你有一定的参考价值。
往期文章
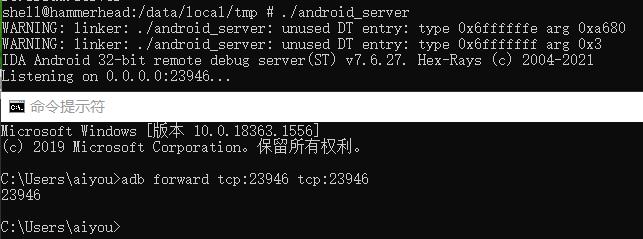
一、启动调试环境
1、启动android-server
./as
2、转发端口
adb forward tcp:23946 tcp:23946
二、启动IDA,加载要调试的SO文件
三、在上节课分析的关键处下断,然后查看相关参数

四、运行起来,触发断点,查看参数
1、setkey:
asfsaADDJF55b262d99cff7cac7459e8&
2、update:
PUT&https%3A%2F%2Fmapi.mafengwo.cn%2Frest%2Fapp%2Fuser%2Flogin%2F&after_style%3Ddefault%26app_code%3Dcom.mfw.roadbook%26app_ver%3D8.1.6%26app_version_code%3D535%26brand%3DAndroid%26channel_id%3DGROWTH-WAP-LC-3%26device_id%3D8c%253A3a%253Ae3%253A97%253A1b%253A8a%26device_type%3Dandroid%26hardware_model%3DAOSP%2520on%2520HammerHead%26mfwsdk_ver%3D20140507%26o_lat%3D36.142714%26o_lng%3D113.761059%26oauth_consumer_key%3D5%26oauth_nonce%3Df061b558-d0c4-446c-b91c-7688d9219be1%26oauth_signature_method%3DHMAC-SHA1%26oauth_timestamp%3D1635414450%26oauth_version%3D1.0%26open_udid%3D8c%253A3a%253Ae3%253A97%253A1b%253A8a%26put_style%3Ddefault%26screen_height%3D1776%26screen_scale%3D3.0%26screen_width%3D1080%26sys_ver%3D5.1.1%26time_offset%3D480%26x_auth_mode%3Dclient_auth%26x_auth_password%3D223456%26x_auth_username%3D15836353612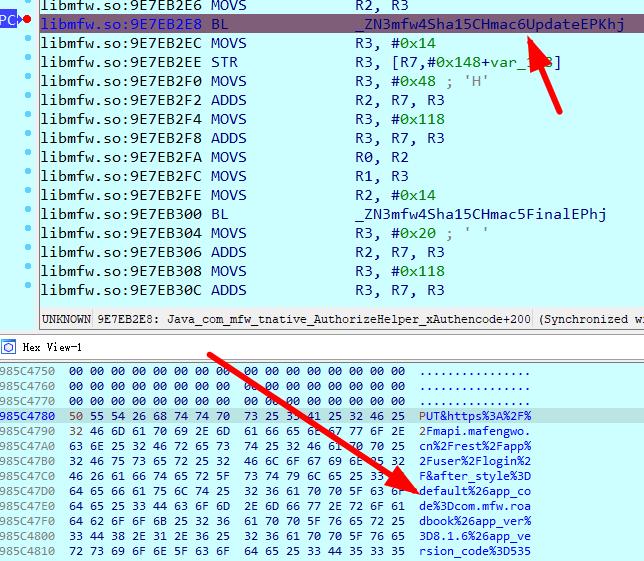
3、base64:
YQRRJRfQbVXBzDA06EKXXvd6lmI=
五、算法验证
var key="asfsaADDJF55b262d99cff7cac7459e8&"var s="PUT&https%3A%2F%2Fmapi.mafengwo.cn%2Frest%2Fapp%2Fuser%2Flogin%2F&after_style%3Ddefault%26app_code%3Dcom.mfw.roadbook%26app_ver%3D8.1.6%26app_version_code%3D535%26brand%3DAndroid%26channel_id%3DGROWTH-WAP-LC-3%26device_id%3D8c%253A3a%253Ae3%253A97%253A1b%253A8a%26device_type%3Dandroid%26hardware_model%3DAOSP%2520on%2520HammerHead%26mfwsdk_ver%3D20140507%26o_lat%3D36.142714%26o_lng%3D113.761059%26oauth_consumer_key%3D5%26oauth_nonce%3Df061b558-d0c4-446c-b91c-7688d9219be1%26oauth_signature_method%3DHMAC-SHA1%26oauth_timestamp%3D1635414450%26oauth_version%3D1.0%26open_udid%3D8c%253A3a%253Ae3%253A97%253A1b%253A8a%26put_style%3Ddefault%26screen_height%3D1776%26screen_scale%3D3.0%26screen_width%3D1080%26sys_ver%3D5.1.1%26time_offset%3D480%26x_auth_mode%3Dclient_auth%26x_auth_password%3D223456%26x_auth_username%3D15836353612"console.log(CryptoJS.HmacSHA1(s,key).toString())console.log(CryptoJS.HmacSHA1(s,key).toString(CryptoJS.enc.Base64))运行结果:YQRRJRfQbVXBzDA06EKXXvd6lmI=
禁止非法,后果自负
欢迎关注公众号:逆向有你
欢迎关注视频号:之乎者也吧


以上是关于安卓逆向 -- 实战某峰窝APP(动态分析)的主要内容,如果未能解决你的问题,请参考以下文章
Android编程实战源码级免杀_Dex动态加载技术_Metasploit安卓载荷傀儡机代码复现
Android 逆向Android 进程注入工具开发 ( 注入代码分析 | 远程调用 目标进程中 libc.so 动态库中的 mmap 函数 二 | 准备参数 | 远程调用 mmap 函数 )(代码片