rsa题目
Posted Nullan
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了rsa题目相关的知识,希望对你有一定的参考价值。
easyrsa
还记得veryeasy RSA吗?是不是不难?那继续来看看这题吧,这题也不难。
已知一段RSA加密的信息为:0xdc2eeeb2782c且已知加密所用的公钥:
(N=322831561921859 e = 23)
请解密出明文,提交时请将数字转化为ascii码提交
比如你解出的明文是0x6162,那么请提交字符串ab
提交格式:PCTF{明文字符串}
factorord分解n
http://factordb.com/
分解链接
#!/usr/bin/python
#coding:utf-8
import libnum
from Crypto.Util.number import*
c = 0xdc2eeeb2782c
n = 322831561921859
e = 23
q = 13574881
p = 23781539
d = libnum.invmod(e, (p - 1) *(q - 1))
m = pow(c, d, n)
print "m的值为:"
print long_to_bytes(m)
meduimRSA
#!/usr/bin/python
#coding:utf-8
import libnum
from Crypto.Util.number import*
n = 87924348264132406875276140514499937145050893665602592992418171647042491658461
p = 275127860351348928173285174381581152299
q = 319576316814478949870590164193048041239
e = 65537
phi = (p-1)*(q-1)
d = libnum.invmod(e,phi)
with open('./flag.enc') as f:
c = f.read().encode('hex')
c = int(c,16)
m = pow(c,d,n)
print long_to_bytes(m)
meduimRSa
利用命令 openssl rsa -pubin -in pubkey.pem -text -modulus
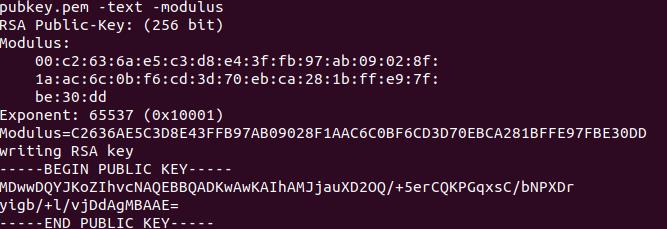 EXponent那一处是e
EXponent那一处是e
Modulus那一处是n
利用网站分解n
得到p和q
脚本
#!/usr/bin/python
#coding:utf-8
import libnum
from Crypto.Util.number import*
n = 87924348264132406875276140514499937145050893665602592992418171647042491658461
p = 275127860351348928173285174381581152299
q = 319576316814478949870590164193048041239
e = 65537
phi = (p-1)*(q-1)
d = libnum.invmod(e,phi)
with open('./flag.enc') as f:
c = f.read().encode('hex')
c = int(c,16)
m = pow(c,d,n)
print long_to_bytes(m)
以上是关于rsa题目的主要内容,如果未能解决你的问题,请参考以下文章