2021年津门杯国际网络安全创新大赛 - Misc
Posted H3rmesk1t
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了2021年津门杯国际网络安全创新大赛 - Misc相关的知识,希望对你有一定的参考价值。
m0usb
- 查看流量包,发现是 USB 的流量,USB 协议的数据部分在
Leftover Capture Data域中,先用tshark将流量提取出来
tshark -r usb.pcapng -T fields -e usb.capdata > usbdata.txt
如果提取出来的数据有空行可以将命令改为如下形式
tshark -r usb.pcapng -T fields -e usb.capdata | sed '/^\\s*$/d' > usbdata.txt
击键信息对照表可以参考:https://max.book118.com/html/2017/0407/99227972.shtm
提取出来的数据可能会带冒号,也可能不带(有可能和wireshark的版本相关),但是一般的脚本都会按照有冒号的数据来识别,这里参考一个添加冒号的脚本
f=open('usbdata.txt','r')
fi=open('out.txt','w')
while 1:
a=f.readline().strip()
if a:
if len(a)==16: # 鼠标流量的话len改为8
out=''
for i in range(0,len(a),2):
if i+2 != len(a):
out+=a[i]+a[i+1]+":"
else:
out+=a[i]+a[i+1]
fi.write(out)
fi.write('\\n')
else:
break
fi.close()
- 鼠标流量转换数据
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e",
"09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j",
"0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o",
"13":"p", "14":"q", "15":"r", "16":"s", "17":"t",
"18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y",
"1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4",
"22":"5", "23":"6","24":"7","25":"8","26":"9",
"27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\\t",
"2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\\\",
"32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".",
"38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>",
"3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>",
"44":"<F11>","45":"<F12>"}
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E",
"09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J",
"0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O",
"13":"P", "14":"Q", "15":"R", "16":"S", "17":"T",
"18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y",
"1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$",
"22":"%", "23":"^","24":"&","25":"*","26":"(","27":")",
"28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\\t","2c":"<SPACE>",
"2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\\"",
"34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>",
"3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>",
"41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
output = []
keys = open('out.txt')
for line in keys:
try:
if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00":
continue
if line[6:8] in normalKeys.keys():
output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag=0
print("".join(output))
for i in range(len(output)):
try:
a=output.index('<DEL>')
del output[a]
del output[a-1]
except:
pass
for i in range(len(output)):
try:
if output[i]=="<CAP>":
flag+=1
output.pop(i)
if flag==2:
flag=0
if flag!=0:
output[i]=output[i].upper()
except:
pass
print ('output: ' + "".join(output))
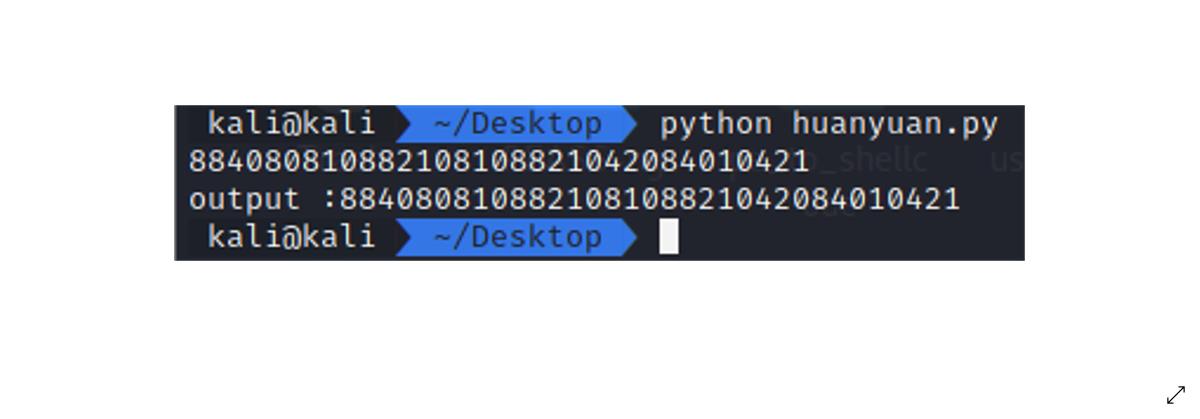
- 得到一串字符串:
884080810882108108821042084010421,发现只有01248几个数字,推测是云影密码,解密得到 Flag:flag{THISFLAG}
#!/usr/bin/python
# -*- coding=utf8 -*-
def de_code(c):
dic = [chr(i) for i in range(ord("A"), ord("Z") + 1)]
flag = []
c2 = [i for i in c.split("0")]
for i in c2:
c3 = 0
for j in i:
c3 += int(j)
flag.append(dic[c3 - 1])
return flag
def encode(plaintext):
dic = [chr(i) for i in range(ord("A"), ord("Z") + 1)]
m = [i for i in plaintext]
tmp = [];flag = []
for i in range(len(m)):
for j in range(len(dic)):
if m[i] == dic[j]:
tmp.append(j + 1)
for i in tmp:
res = ""
if i >= 8:
res += int(i/8)*"8"
if i%8 >=4:
res += int(i%8/4)*"4"
if i%4 >=2:
res += int(i%4/2)*"2"
if i%2 >= 1:
res += int(i%2/1)*"1"
flag.append(res + "0")
print ("".join(flag)[:-1])
if __name__ == '__main__':
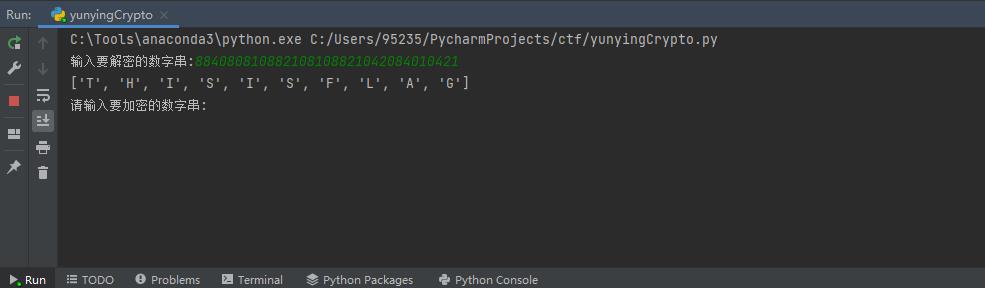
c = input("输入要解密的数字串:")
print (de_code(c))
m_code = input("请输入要加密的数字串:")
encode (m_code)
m1bmp
- 用
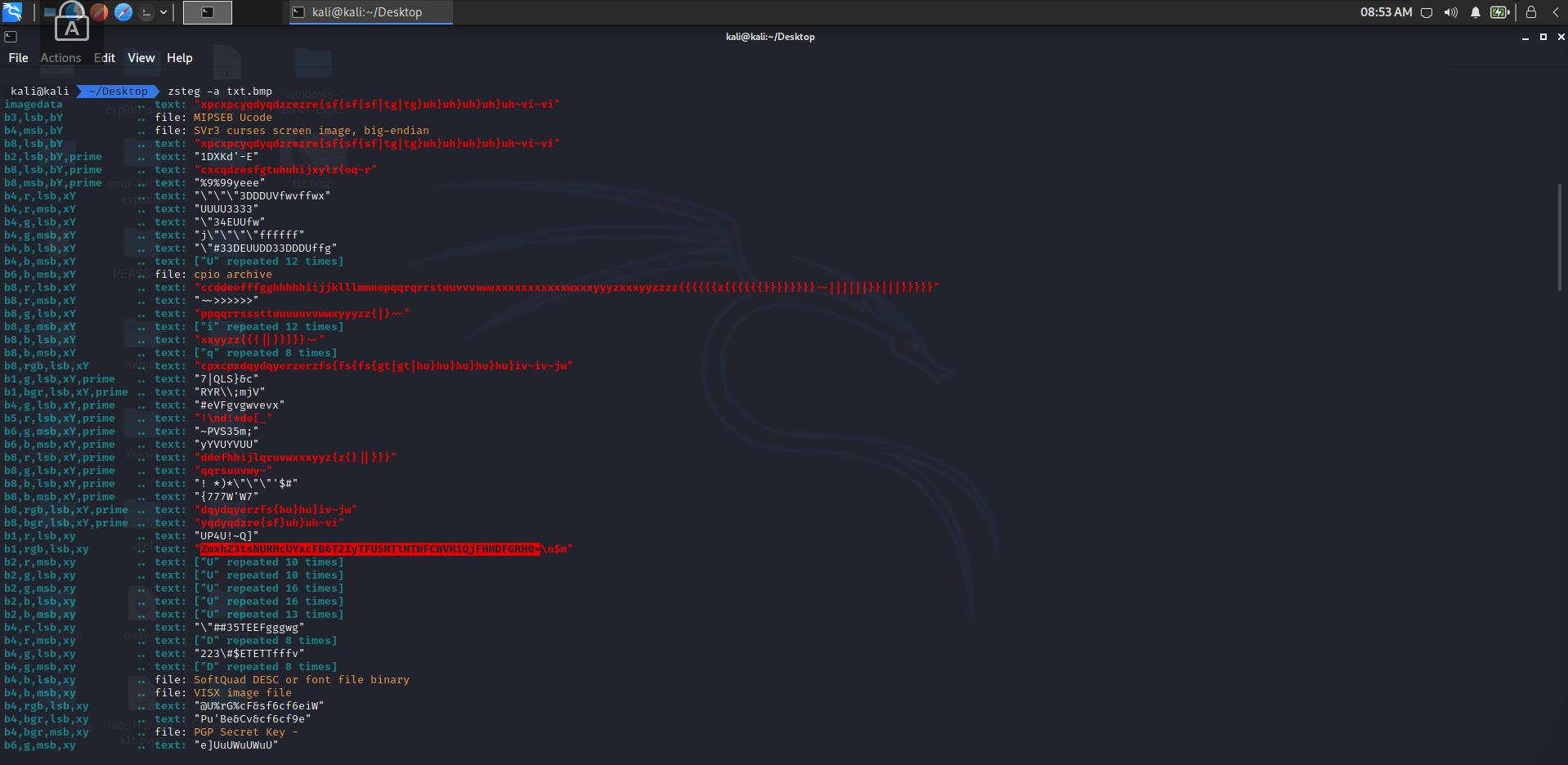
binwalk先查看一下图片,但是没有发现什么东西- 考虑到是 BMP 图片,猜测存在隐写,用
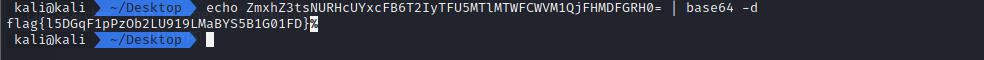
zsteg查看一下图片,发现 base64 字符串,解码得到 Flag:flag{l5DGqF1pPzOb2LU919LMaBYS5B1G01FD}
tunnel
- 打开数据包,发现全是有 base64 的 dns 域名请求,使用
tshark提取 A 记录的域名
tshark -r tunnel.pcap -Y "dns" -T fields -e dns.qry.name > out.txt
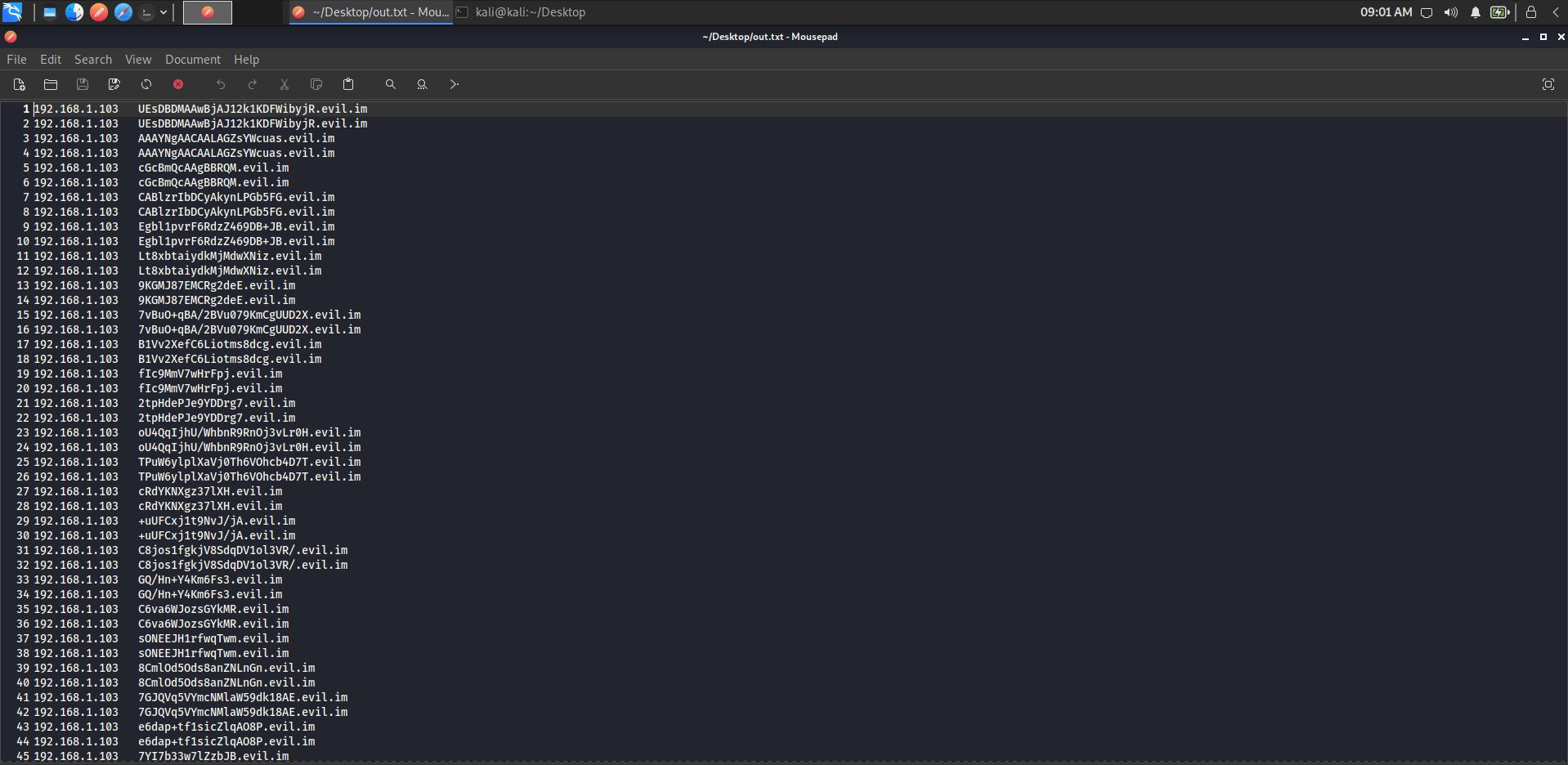
- 将 base64 字符串数据提取出来,
CyberChef解密一下,发现是一个 zip 文件
f=open('out.txt','r')
fp=open('zip.txt','w')
tmp=f.readline().strip('\\n')
s=''
while tmp[-8:]!='.evil.im':
tmp=f.readline().strip('\\n')
s=tmp[:-8]
while len(s)%4!=0:
s+='='
fp.write(s)
fp.write('\\n')
while 1:
a=f.readline().strip('\\n')
if a:
if a[-8:]=='.evil.im':
if a!=tmp:
s=a[:-8]
while len(s)%4!=0:
s+='='
fp.write(s)
fp.write('\\n')
tmp=a
else:
break
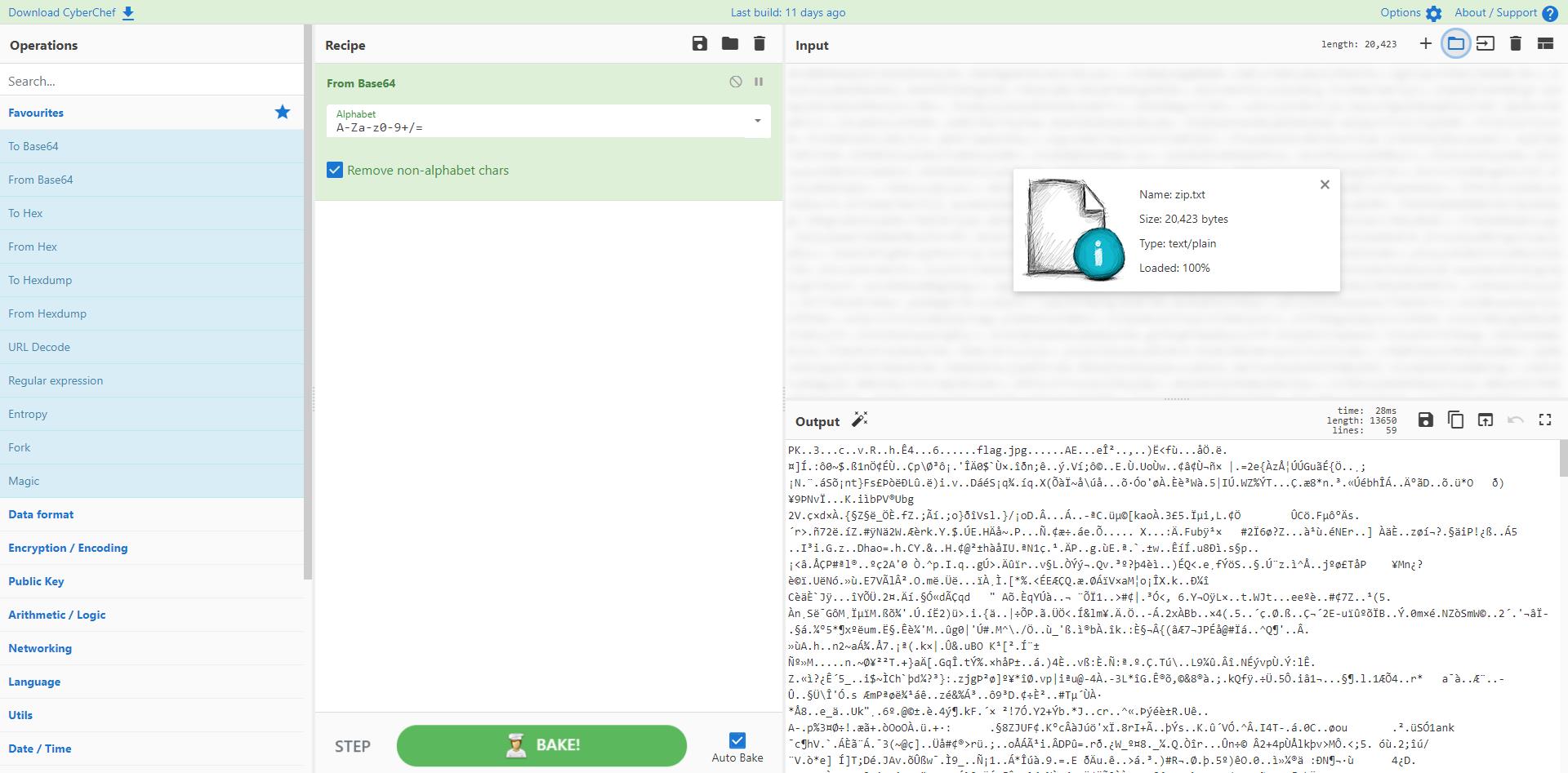
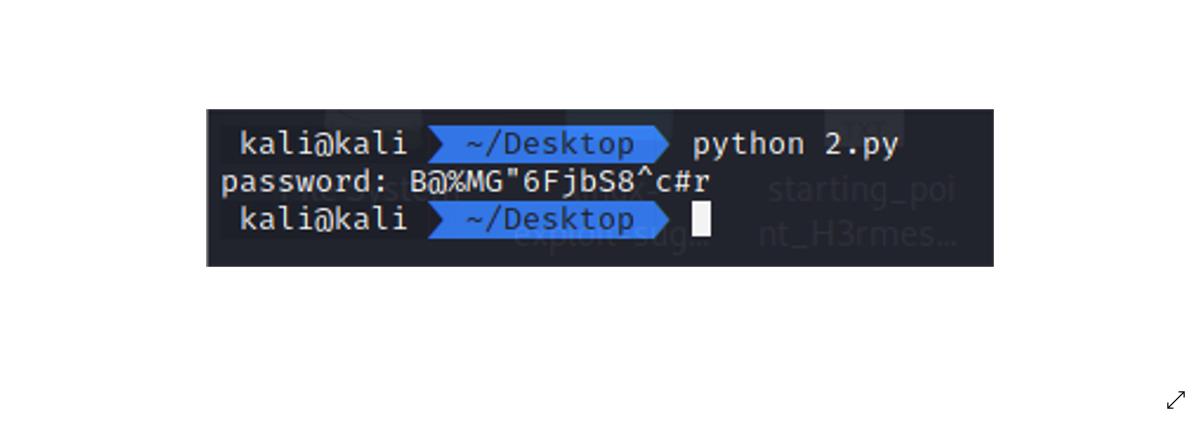
- 发现压缩包是加密的,由于前面提取出来了很多 base64 字符串,猜测存在 base64 隐写,解密得到压缩包的密码:
password: B@%MG"6FjbS8^c#r,打开压缩包在图片上发现 Flag:flag{D01nt_5py_0nmE}
#!/usr/bin/env python
import re
path = './zip.txt'
b64char = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
with open(path, 'r')as f:
cipher = [i.strip() for i in f.readlines()]
plaintext = ''
for i in cipher:
if i[-2] == '=': # There are 4-bit hidden info while end with two '='
bin_message = bin(b64char.index(i[-3]))[2:].zfill(4)
plaintext += bin_message[-4:]
elif i[-1] == '=': # There are 2-bit hidden info while end with one '='
bin_message = bin(b64char.index(i[-2]))[2:].zfill(2)
plaintext += bin_message[-2:]
plaintext = re.findall('.{8}', plaintext) # 8bits/group
plaintext = ''.join([chr(int(i,2)) for i in plaintext])
print(plaintext)

以上是关于2021年津门杯国际网络安全创新大赛 - Misc的主要内容,如果未能解决你的问题,请参考以下文章