XCTF-攻防世界CTF平台-Reverse逆向类——52handcrafted-pyc
Posted 大灬白
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了XCTF-攻防世界CTF平台-Reverse逆向类——52handcrafted-pyc相关的知识,希望对你有一定的参考价值。
下载题目附件之后,查看附件52:
发现它就是一个Python代码文件

#!/usr/bin/env python
# -*- coding: utf-8 -*-
import marshal, zlib, base64
exec(marshal.loads(zlib.decompress(base64.b64decode('eJyNVktv00AQXm/eL0igiaFA01IO4cIVCUGFBBJwqRAckLhEIQmtRfPwI0QIeio/hRO/hJ/CiStH2M/prj07diGRP43Hs9+MZ2fWMxbnP6mux+oK9xVMHPFViLdCTB0xkeKDFEFfTIU4E8KZq8dCvB4UlN3hGEsdddXU9QTLv1eFiGKGM4cKUgsFCNLFH7dFrS9poayFYmIZm1b0gyqxMOwJaU3r6xs9sW1ooakXuRv+un7Q0sIlLVzOCZq/XtsK2oTSYaZlStogXi1HV0iazoN2CV2HZeXqRQ54TlJRb7FUlKyUatISsdzo+P7UU1Gb1POdMruckepGwk9tIXQTftz2yBaT5JQovWvpSa6poJPuqgao+b9l5Aj/R+mLQIP4f6Q8Vb3g/5TB/TJxWGdZr9EQrmn99fwKtTvAZGU7wzS7GNpZpDm2JgCrr8wrmPoo54UqGampFIeS9ojXjc4E2yI06bq/4DRoUAc0nVnng4k6p7Ks0+j/S8z9V+NZ5dhmrJUM/y7JTJeRtnJ2TSYJvsFq3CQt/vnfqmQXt5KlpuRcIvDAmhnn2E0t9BJ3SvB/SfLWhuOWNiNVZ+h28g4wlwUp00w95si43rZ3r6+fUIEdgOZbQAsyFRRvBR6dla8KCzRdslar7WS+a5HFb39peIAmG7uZTHVm17Czxju4m6bayz8e7J40DzqM0jr0bmv9PmPvk6y5z57HU8wdTDHeiUJvBMAM4+0CpoAZ4BPgJeAYEAHmgAUgAHiAj4AVAGORtwd4AVgC3gEmgBBwCPgMWANOAQ8AbwBHgHuAp4D3gLuARwoGmNUizF/j4yDC5BWM1kNvvlxFA8xikRrBxHIUhutFMBlgQoshhPphGAXe/OggKqqb2cibxwuEXjUcQjccxi5eFRL1fDSbKrUhy2CMb2aLyepkegDWsBwPlrVC0/kLHmeCBQ=='))))
运行52.py

它只能用python2运行,Python3执行会报错
上面的代码中:
base64.b64decode()函数的作用是将Base64加密的字符串解码;
zlib.decompress()函数的作用是将压缩的字符串解压缩;
marshal模块主要用于支持读取和编写.pyc文件的Python模块的“伪编译”代码,marshal.loads(bytes)函数的作用是将pyc文件二进制流反序列化为Python对象;
最后exec()执行Python代码。
所以我们接下来就是要先获得执行的Python代码
import zlib,base64
pyc=zlib.decompress(base64.b64decode('eJyNVktv00AQXm/eL0igiaFA01IO4cIVCUGFBBJwqRAckLhEIQmtRfPwI0QIeio/hRO/hJ/CiStH2M/prj07diGRP43Hs9+MZ2fWMxbnP6mux+oK9xVMHPFViLdCTB0xkeKDFEFfTIU4E8KZq8dCvB4UlN3hGEsdddXU9QTLv1eFiGKGM4cKUgsFCNLFH7dFrS9poayFYmIZm1b0gyqxMOwJaU3r6xs9sW1ooakXuRv+un7Q0sIlLVzOCZq/XtsK2oTSYaZlStogXi1HV0iazoN2CV2HZeXqRQ54TlJRb7FUlKyUatISsdzo+P7UU1Gb1POdMruckepGwk9tIXQTftz2yBaT5JQovWvpSa6poJPuqgao+b9l5Aj/R+mLQIP4f6Q8Vb3g/5TB/TJxWGdZr9EQrmn99fwKtTvAZGU7wzS7GNpZpDm2JgCrr8wrmPoo54UqGampFIeS9ojXjc4E2yI06bq/4DRoUAc0nVnng4k6p7Ks0+j/S8z9V+NZ5dhmrJUM/y7JTJeRtnJ2TSYJvsFq3CQt/vnfqmQXt5KlpuRcIvDAmhnn2E0t9BJ3SvB/SfLWhuOWNiNVZ+h28g4wlwUp00w95si43rZ3r6+fUIEdgOZbQAsyFRRvBR6dla8KCzRdslar7WS+a5HFb39peIAmG7uZTHVm17Czxju4m6bayz8e7J40DzqM0jr0bmv9PmPvk6y5z57HU8wdTDHeiUJvBMAM4+0CpoAZ4BPgJeAYEAHmgAUgAHiAj4AVAGORtwd4AVgC3gEmgBBwCPgMWANOAQ8AbwBHgHuAp4D3gLuARwoGmNUizF/j4yDC5BWM1kNvvlxFA8xikRrBxHIUhutFMBlgQoshhPphGAXe/OggKqqb2cibxwuEXjUcQjccxi5eFRL1fDSbKrUhy2CMb2aLyepkegDWsBwPlrVC0/kLHmeCBQ=='))
f=open('52pyc.pyc','wb')
f.write(pyc)
f.close()
把pyc文件的二进制流写入文件52pyc.pyc
想把52pyc.pyc文件反编译一下,结果报错文件头的Magic值错误:
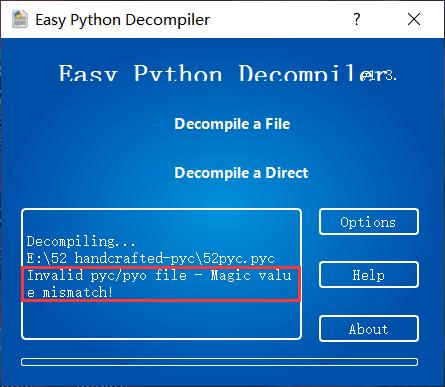
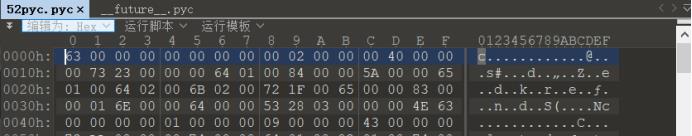
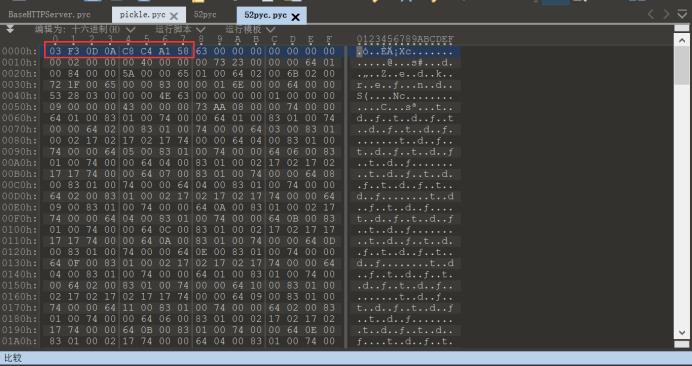
打开52pyc.pyc文件查看:
对比正常Python2的pyc文件:
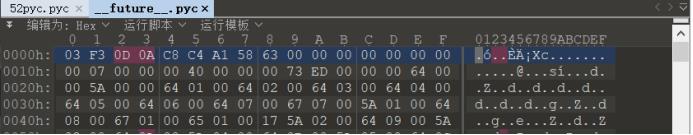
果然少了8个字节的magic文件头,Python3的magic文件头则是12字节
我们给52pyc.pyc文件加上8字节的magic文件头:
此时52pyc.pyc已经作为二进制文件可以直接运行了:

之后,再将52pyc.pyc反编译成python代码
安装uncompyle6反编译:
uncompyle6 -o 52python.py 52pyc.pyc
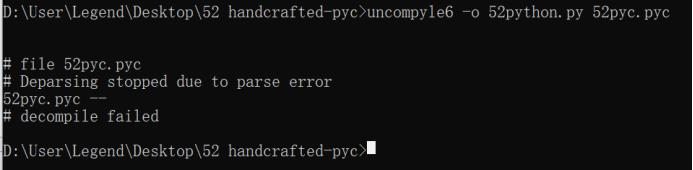
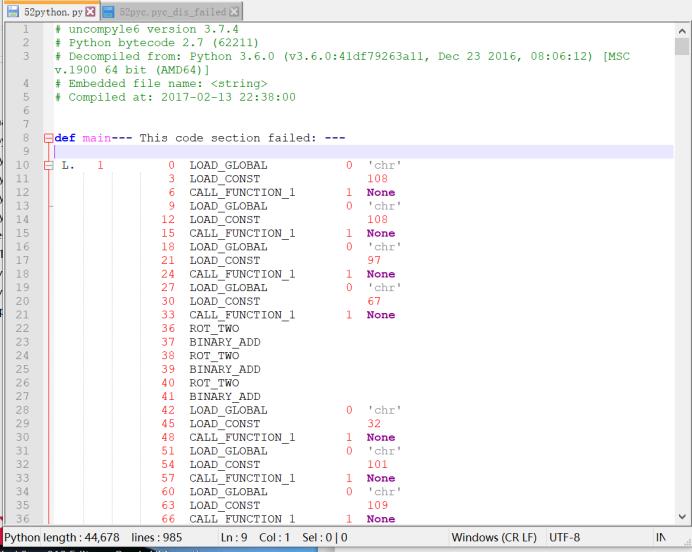
提示反编译失败,但是Python字节码是成功反编译出来了
安装Easy Python Decompiler

提示非法文件,但是也反编译出来了:
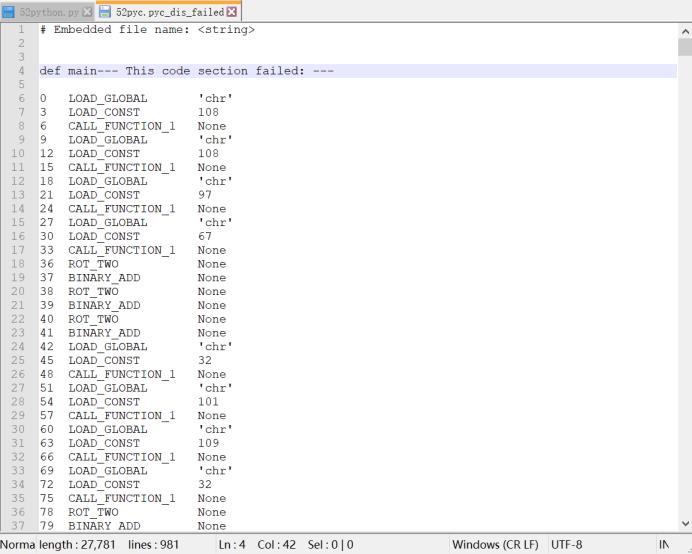
源代码:
# uncompyle6 version 3.7.4
# Python bytecode 2.7 (62211)
# Decompiled from: Python 3.6.0 (v3.6.0:41df79263a11, Dec 23 2016, 08:06:12) [MSC v.1900 64 bit (AMD64)]
# Embedded file name: <string>
# Compiled at: 2017-02-13 22:38:00
def main--- This code section failed: ---
L. 1 0 LOAD_GLOBAL 0 'chr'
3 LOAD_CONST 108
6 CALL_FUNCTION_1 1 None
9 LOAD_GLOBAL 0 'chr'
12 LOAD_CONST 108
15 CALL_FUNCTION_1 1 None
18 LOAD_GLOBAL 0 'chr'
21 LOAD_CONST 97
24 CALL_FUNCTION_1 1 None
27 LOAD_GLOBAL 0 'chr'
30 LOAD_CONST 67
33 CALL_FUNCTION_1 1 None
36 ROT_TWO
37 BINARY_ADD
38 ROT_TWO
39 BINARY_ADD
40 ROT_TWO
41 BINARY_ADD
42 LOAD_GLOBAL 0 'chr'
45 LOAD_CONST 32
48 CALL_FUNCTION_1 1 None
51 LOAD_GLOBAL 0 'chr'
54 LOAD_CONST 101
57 CALL_FUNCTION_1 1 None
60 LOAD_GLOBAL 0 'chr'
63 LOAD_CONST 109
66 CALL_FUNCTION_1 1 None
69 LOAD_GLOBAL 0 'chr'
72 LOAD_CONST 32
75 CALL_FUNCTION_1 1 None
78 ROT_TWO
79 BINARY_ADD
80 ROT_TWO
81 BINARY_ADD
82 ROT_TWO
83 BINARY_ADD
84 BINARY_ADD
85 LOAD_GLOBAL 0 'chr'
88 LOAD_CONST 121
91 CALL_FUNCTION_1 1 None
94 LOAD_GLOBAL 0 'chr'
97 LOAD_CONST 80
100 CALL_FUNCTION_1 1 None
103 LOAD_GLOBAL 0 'chr'
106 LOAD_CONST 32
109 CALL_FUNCTION_1 1 None
112 LOAD_GLOBAL 0 'chr'
115 LOAD_CONST 97
118 CALL_FUNCTION_1 1 None
121 ROT_TWO
122 BINARY_ADD
123 ROT_TWO
124 BINARY_ADD
125 ROT_TWO
126 BINARY_ADD
127 LOAD_GLOBAL 0 'chr'
130 LOAD_CONST 104
133 CALL_FUNCTION_1 1 None
136 LOAD_GLOBAL 0 'chr'
139 LOAD_CONST 116
142 CALL_FUNCTION_1 1 None
145 ROT_TWO
146 BINARY_ADD
147 LOAD_GLOBAL 0 'chr'
150 LOAD_CONST 32
153 CALL_FUNCTION_1 1 None
156 LOAD_GLOBAL 0 'chr'
159 LOAD_CONST 110
162 CALL_FUNCTION_1 1 None
165 LOAD_GLOBAL 0 'chr'
168 LOAD_CONST 111
171 CALL_FUNCTION_1 1 None
174 ROT_TWO
175 BINARY_ADD
176 ROT_TWO
177 BINARY_ADD
178 BINARY_ADD
179 BINARY_ADD
180 BINARY_ADD
181 LOAD_GLOBAL 0 'chr'
184 LOAD_CONST 116
187 CALL_FUNCTION_1 1 None
190 LOAD_GLOBAL 0 'chr'
193 LOAD_CONST 114
196 CALL_FUNCTION_1 1 None
199 LOAD_GLOBAL 0 'chr'
202 LOAD_CONST 105
205 CALL_FUNCTION_1 1 None
208 LOAD_GLOBAL 0 'chr'
211 LOAD_CONST 118
214 CALL_FUNCTION_1 1 None
217 ROT_TWO
218 BINARY_ADD
219 ROT_TWO
220 BINARY_ADD
221 ROT_TWO
222 BINARY_ADD
223 LOAD_GLOBAL 0 'chr'
226 LOAD_CONST 32
229 CALL_FUNCTION_1 1 None
232 LOAD_GLOBAL 0 'chr'
235 LOAD_CONST 108
238 CALL_FUNCTION_1 1 None
241 LOAD_GLOBAL 0 'chr'
244 LOAD_CONST 97
247 CALL_FUNCTION_1 1 None
250 LOAD_GLOBAL 0 'chr'
253 LOAD_CONST 117
256 CALL_FUNCTION_1 1 None
259 ROT_TWO
260 BINARY_ADD
261 ROT_TWO
262 BINARY_ADD
263 ROT_TWO
264 BINARY_ADD
265 BINARY_ADD
266 LOAD_GLOBAL 0 'chr'
269 LOAD_CONST 104
272 CALL_FUNCTION_1 1 None
275 LOAD_GLOBAL 0 'chr'
278 LOAD_CONST 99
281 CALL_FUNCTION_1 1 None
284 LOAD_GLOBAL 0 'chr'
287 LOAD_CONST 97
290 CALL_FUNCTION_1 1 None
293 LOAD_GLOBAL 0 'chr'
296 LOAD_CONST 109
299 CALL_FUNCTION_1 1 None
302 ROT_TWO
303 BINARY_ADD
304 ROT_TWO
305 BINARY_ADD
306 ROT_TWO
307 BINARY_ADD
308 LOAD_GLOBAL 0 'chr'
311 LOAD_CONST 110
314 CALL_FUNCTION_1 1 None
317 LOAD_GLOBAL 0 'chr'
320 LOAD_CONST 105
323 CALL_FUNCTION_1 1 None
326 ROT_TWO
327 BINARY_ADD
328 LOAD_GLOBAL 0 'chr'
331 LOAD_CONST 32
334 CALL_FUNCTION_1 1 None
337 LOAD_GLOBAL 0 'chr'
340 LOAD_CONST 33
343 CALL_FUNCTION_1 1 None
346 LOAD_GLOBAL 0 'chr'
349 LOAD_CONST 101
352 CALL_FUNCTION_1 1 None
355 ROT_TWO
356 BINARY_ADD
357 ROT_TWO
358 BINARY_ADD
359 BINARY_ADD
360 BINARY_ADD
361 BINARY_ADD
362 BINARY_ADD
363 LOAD_GLOBAL 0 'chr'
366 LOAD_CONST 97
369 CALL_FUNCTION_1 1 None
372 LOAD_GLOBAL 0 'chr'
375 LOAD_CONST 99
378 CALL_FUNCTION_1 1 None
381 LOAD_GLOBAL 0 'chr'
384 LOAD_CONST 32
387 CALL_FUNCTION_1 1 None
390 LOAD_GLOBAL 0 'chr'
393 LOAD_CONST 73
396 CALL_FUNCTION_1 1 None
399 ROT_TWO
400 BINARY_ADD
401 ROT_TWO
402 BINARY_ADD
403 ROT_TWO
404 BINARY_ADD
405 LOAD_GLOBAL 0 'chr'
408 LOAD_CONST 110
411 CALL_FUNCTION_1 1 None
414 LOAD_GLOBAL 0 'chr'
417 LOAD_CONST 105
420 CALL_FUNCTION_1 1 None
423 LOAD_GLOBAL 0 'chr'
426 LOAD_CONST 32
429 CALL_FUNCTION_1 1 None
432 LOAD_GLOBAL 0 'chr'
435 LOAD_CONST 110
438 CALL_FUNCTION_1 1 None
441 ROT_TWO
442 BINARY_ADD
443 ROT_TWO
444 BINARY_ADD
445 ROT_TWO
446 BINARY_ADD
447 BINARY_ADD
448 LOAD_GLOBAL 0 'chr'
451 LOAD_CONST 112
454 CALL_FUNCTION_1 1 None
457 LOAD_GLOBAL 0 'chr'
460 LOAD_CONST 114
463 CALL_FUNCTION_1 1 None
466 LOAD_GLOBAL 0 'chr'
469 LOAD_CONST 101
472 CALL_FUNCTION_1 1 None
475 LOAD_GLOBAL 0 'chr'
478 LOAD_CONST 116
481 CALL_FUNCTION_1 1 None
484 ROT_TWO
485 BINARY_ADD
486 ROT_TWO
487 BINARY_ADD
488 ROT_TWO
489 BINARY_ADD
490 LOAD_GLOBAL 0 'chr'
493 LOAD_CONST 101
496 CALL_FUNCTION_1 1 None
499 LOAD_GLOBAL 0 'chr'
502 LOAD_CONST 114
505 CALL_FUNCTION_1 1 None
508 ROT_TWO
509 BINARY_ADD
510 LOAD_GLOBAL 0 'chr'
513 LOAD_CONST 80
516 CALL_FUNCTION_1 1 None
519 LOAD_GLOBAL 0 'chr'
522 LOAD_CONST 32
525 CALL_FUNCTION_1 1 None
528 LOAD_GLOBAL 0 'chr'
531 LOAD_CONST 116
534 CALL_FUNCTION_1 1 None
537 ROT_TWO
538 BINARY_ADD
539 ROT_TWO
540 BINARY_ADD
541 BINARY_ADD
542 BINARY_ADD
543 BINARY_ADD
544 LOAD_GLOBAL 0 'chr'
547 LOAD_CONST 111
550 CALL_FUNCTION_1 1 None
553 LOAD_GLOBAL 0 'chr'
556 LOAD_CONST 104
559 CALL_FUNCTION_1 1 None
562 LOAD_GLOBAL 0 'chr'
565 LOAD_CONST 116
568 CALL_FUNCTION_1 1 None
571 LOAD_GLOBAL 0 'chr'
574 LOAD_CONST 121
577 CALL_FUNCTION_1 1 None
580 ROT_TWO
581 BINARY_ADD
582 ROT_TWO
583 BINARY_ADD
584 ROT_TWO
585 BINARY_ADD
586 LOAD_GLOBAL 0 'chr'
589 LOAD_CONST 32
592 CALL_FUNCTION_1 1 None
595 LOAD_GLOBAL 0 'chr'
598 LOAD_CONST 110
601 CALL_FUNCTION_1 1 None
604 ROT_TWO
605 BINARY_ADD
606 LOAD_GLOBAL 0 'chr'
609 LOAD_CONST 116
612 CALL_FUNCTION_1 1 None
615 LOAD_GLOBAL 0 'chr'
618 LOAD_CONST 121
621 CALL_FUNCTION_1 1 None
624 LOAD_GLOBAL 0 'chr'
627 LOAD_CONST 98
630 CALL_FUNCTION_1 1 None
633 ROT_TWO
634 BINARY_ADD
635 ROT_TWO
636 BINARY_ADD
637 BINARY_ADD
638 BINARY_ADD
639 LOAD_GLOBAL 0 'chr'
642 LOAD_CONST 100
645 CALL_FUNCTION_1 1 None
648 LOAD_GLOBAL 0 'chr'
651 LOAD_CONST 111
654 CALL_FUNCTION_1 1 None
657 LOAD_GLOBAL 0 'chr'
660 LOAD_CONST 99
663 CALL_FUNCTION_1 1 None
666 LOAD_GLOBAL 0 'chr'
669 LOAD_CONST 101
672 CALL_FUNCTION_1 1 None
675 ROT_TWO
676 BINARY_ADD
677 ROT_TWO
678 BINARY_ADD
679 ROT_TWO
680 BINARY_ADD
681 LOAD_GLOBAL 0 'chr'
684 LOAD_CONST 115
687 CALL_FUNCTION_1 1 None
690 LOAD_GLOBAL 0 'chr'
693 LOAD_CONST 101
696 CALL_FUNCTION_1 1 None
699 ROT_TWO
700 BINARY_ADD
701 LOAD_GLOBAL 0 'chr'
704 LOAD_CONST 33
707 CALL_FUNCTION_1 1 None
710 LOAD_GLOBAL 0 'chr'
713 LOAD_CONST 33
716 CALL_FUNCTION_1 1 None
719 LOAD_GLOBAL 0 'chr'
722 LOAD_CONST 33
725 CALL_FUNCTION_1 1 None
728 ROT_TWO
729 BINARY_ADD
730 ROT_TWO
731 BINARY_ADD
732 BINARY_ADD
733 BINARY_ADD
734 BINARY_ADD
735 BINARY_ADD
736 BINARY_ADD
737 LOAD_CONST None
740 NOP
741 JUMP_ABSOLUTE 759 'to 759'
744 LOAD_GLOBAL 1 'raw_input'
747 JUMP_ABSOLUTE 1480 'to 1480'
750 LOAD_FAST 0 'password'
753 COMPARE_OP 2 ==
756 JUMP_ABSOLUTE 767 'to 767'
759 ROT_TWO
760 STORE_FAST 0 'password'
763 POP_TOP
764 JUMP_BACK 744 'to 744'
767 POP_JUMP_IF_FALSE 1591 'to 1591'
770 LOAD_GLOBAL 0 'chr'
773 LOAD_CONST 99
776 CALL_FUNCTION_1 1 None
779 LOAD_GLOBAL 0 'chr'
782 LOAD_CONST 116
785 CALL_FUNCTION_1 1 None
788 LOAD_GLOBAL 0 'chr'
791 LOAD_CONST 105
794 CALL_FUNCTION_1 1 None
797 LOAD_GLOBAL 0 'chr'
800 LOAD_CONST 104
803 CALL_FUNCTION_1 1 None
806 ROT_TWO
807 BINARY_ADD
808 ROT_TWO
809 BINARY_ADD
810 ROT_TWO
811 BINARY_ADD
812 LOAD_GLOBAL 0 'chr'
815 LOAD_CONST 78
818 CALL_FUNCTION_1 1 None
821 LOAD_GLOBAL 0 'chr'
824 LOAD_CONST 123
827 CALL_FUNCTION_1 1 None
830 LOAD_GLOBAL 0 'chr'
833 LOAD_CONST 110
836 CALL_FUNCTION_1 1 None
839 LOAD_GLOBAL 0 'chr'
842 LOAD_CONST 111
845 CALL_FUNCTION_1 1 None
848 ROT_TWO
849 BINARY_ADD
850 ROT_TWO
851 BINARY_ADD
852 ROT_TWO
853 BINARY_ADD
854 BINARY_ADD
855 LOAD_GLOBAL 0 'chr'
858 LOAD_CONST 121
861 CALL_FUNCTION_1 1 None
864 LOAD_GLOBAL 0 'chr'
867 LOAD_CONST 32
870 CALL_FUNCTION_1 1 None
873 LOAD_GLOBAL 0 'chr'
876 LOAD_CONST 119
879 CALL_FUNCTION_1 1 None
882 LOAD_GLOBAL 0 'chr'
885 LOAD_CONST 111
888 CALL_FUNCTION_1 1 None
891 ROT_TWO
892 BINARY_ADD
893 ROT_TWO
894 BINARY_ADD
895 ROT_TWO
896 BINARY_ADD
897 LOAD_GLOBAL 0 'chr'
900 LOAD_CONST 99
903 CALL_FUNCTION_1 1 None
906 LOAD_GLOBAL 0 'chr'
909 LOAD_CONST 32
912 CALL_FUNCTION_1 1 None
915 LOAD_GLOBAL 0 'chr'
918 LOAD_CONST 117
921 CALL_FUNCTION_1 1 None
924 LOAD_GLOBAL 0 'chr'
927 LOAD_CONST 111
930 CALL_FUNCTION_1 1 None
933 ROT_TWO
934 BINARY_ADD
935 ROT_TWO
936 BINARY_ADD
937 ROT_TWO
938 BINARY_ADD
939 BINARY_ADD
940 BINARY_ADD
941 LOAD_GLOBAL 0 'chr'
944 LOAD_CONST 99
947 CALL_FUNCTION_1 1 None
950 LOAD_GLOBAL 0 'chr'
953 LOAD_CONST 32
956 CALL_FUNCTION_1 1 None
959 LOAD_GLOBAL 0 'chr'
962 LOAD_CONST 110
965 CALL_FUNCTION_1 1 None
968 LOAD_GLOBAL 0 'chr'
971 LOAD_CONST 97
974 CALL_FUNCTION_1 1 None
977 ROT_TWO
978 BINARY_ADD
979 ROT_TWO
980 BINARY_ADD
981 ROT_TWO
982 BINARY_ADD
983 LOAD_GLOBAL 0 'chr'
986 LOAD_CONST 105
989 CALL_FUNCTION_1 1 None
992 LOAD_GLOBAL 0 'chr'
995 LOAD_CONST 112
998 CALL_FUNCTION_1 1 None
1001 LOAD_GLOBAL 0 'chr'
1004 LOAD_CONST 109
1007 CALL_FUNCTION_1 1 None
1010 LOAD_GLOBAL 0 'chr'
1013 LOAD_CONST 111
1016 CALL_FUNCTION_1 1 None
1019 ROT_TWO
1020 BINARY_ADD
1021 ROT_TWO
1022 BINARY_ADD
1023 ROT_TWO
1024 BINARY_ADD
1025 BINARY_ADD
1026 LOAD_GLOBAL 0 'chr'
1029 LOAD_CONST 97
1032 CALL_FUNCTION_1 1 None
1035 LOAD_GLOBAL 0 'chr'
1038 LOAD_CONST 32
1041 CALL_FUNCTION_1 1 None
1044 LOAD_GLOBAL 0 'chr'
1047 LOAD_CONST 101
1050 CALL_FUNCTION_1 1 None
1053 LOAD_GLOBAL 0 'chr'
1056 LOAD_CONST 108
1059 CALL_FUNCTION_1 1 None
1062 ROT_TWO
1063 BINARY_ADD
1064 ROT_TWO
1065 BINARY_ADD
1066 ROT_TWO
1067 BINARY_ADD
1068 LOAD_GLOBAL 0 'chr'
1071 LOAD_CONST 100
1074 CALL_FUNCTION_1 1 None
1077 LOAD_GLOBAL 0 'chr'
1080 LOAD_CONST 110
1083 CALL_FUNCTION_1 1 None
1086 ROT_TWO
1087 BINARY_ADD
1088 LOAD_GLOBAL 0 'chr'
1091 LOAD_CONST 117
1094 CALL_FUNCTION_1 1 None
1097 LOAD_GLOBAL 0 'chr'
1100 LOAD_CONST 114
1103 CALL_FUNCTION_1 1 以上是关于XCTF-攻防世界CTF平台-Reverse逆向类——52handcrafted-pyc的主要内容,如果未能解决你的问题,请参考以下文章