[GKCTF2021]复现wp
Posted huamanggg
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了[GKCTF2021]复现wp相关的知识,希望对你有一定的参考价值。
签到
打开流量包,分析http流

用python转成字符串
import binascii
s = '64306c455357644251306c6e51554e4a5a3046355355737764306c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154576c44546d39525241707154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7162314645616b46445357644251306c6e51554e4a5a32644554545a46524530325157704e5a3046365458524e524531305257704e436e5177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d644442705130354e65556c7154586c4a616b31355357704e65556b4b4e6b467154576442656b31305455524e644556715458644a616b38775a566f324d6d56774e557377643074795556645a64315a485a48593152556c3051576c4e4d5546355a4777316255733254545a7162475a7763573579555552304d464e4d64444254544170304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d537a42425357526159585a764e7a567462485a735130354e564530325255524e436e6f77655531334d464e4e6555467154545a524e327877596a647362584a5252484a7a5131706f516c68614d446c745647637751306c355655524a4d315a74596e4676656d3951567974736357563151303477553078304d464e4d64444254544851775530774b63336858576d786b4d5659354d544e6c4e325179576d684752324a7a576d31615a7a427363446c7064573569567974585a7a427363446c7064573569567974585a7a427363446c706457356956797458537a423354586876564531336230524e6555464454517045546a4252524534775555527356324636546c684e65444258596d593562464a48556b524f5245347759584a6b4d464a6d4f565a6162444658596e644252456c6b556d46746345524c61577832526b6c6b556d46746345524c61577832566b747754544a5a436a303955556c6f545442525245347755516f3d'
s = binascii.a2b_hex(s)
print(s)
base64解码一次

每行逆转再base64解一次
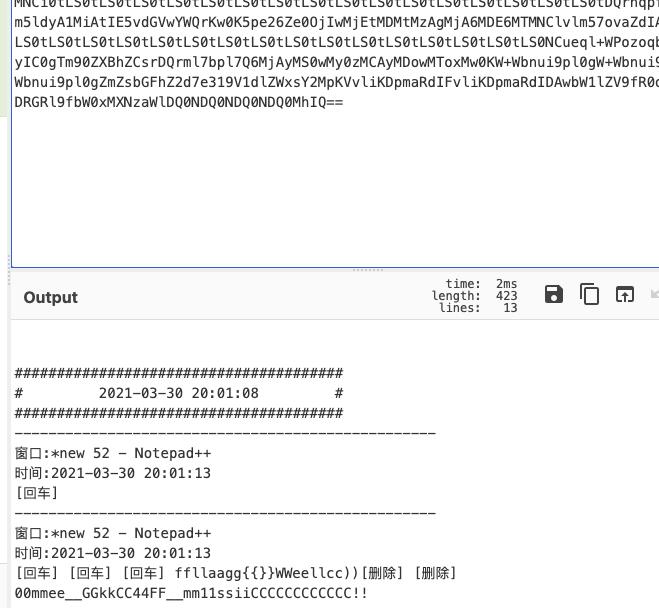
ffllaagg{{}}WWeellcc00mmee__GGkkCC44FF__mm11ssiiCCCCCCCCCCCC!!
栅栏加密
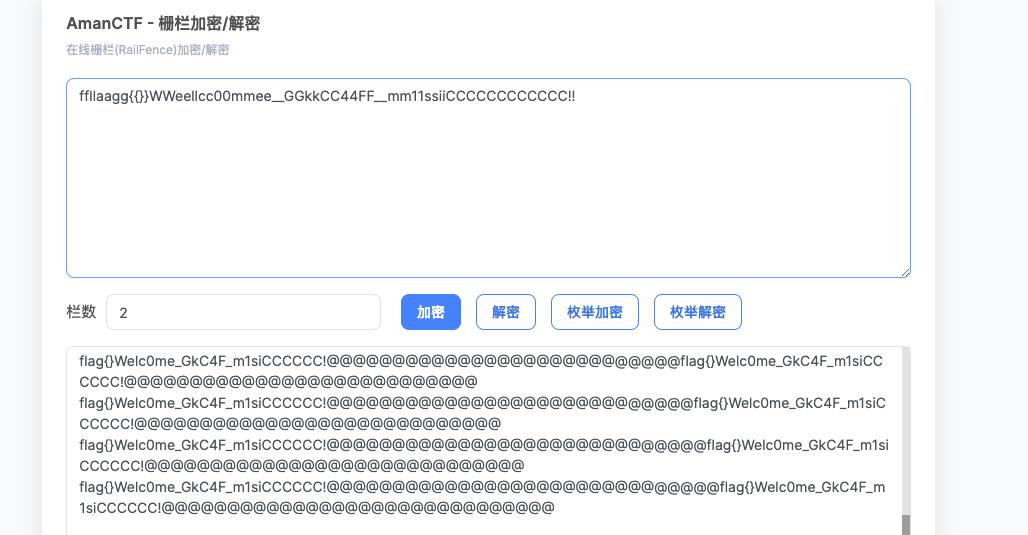
[GKCTF 2021]excel 骚操作
看起来是全白,其实里面有数据
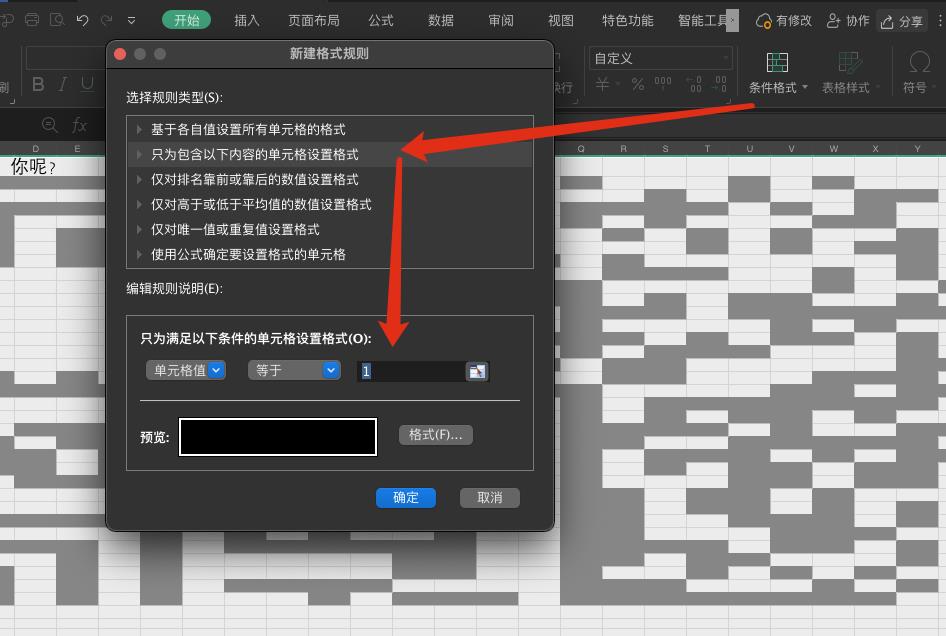
改一下列宽,差不多弄成正方形
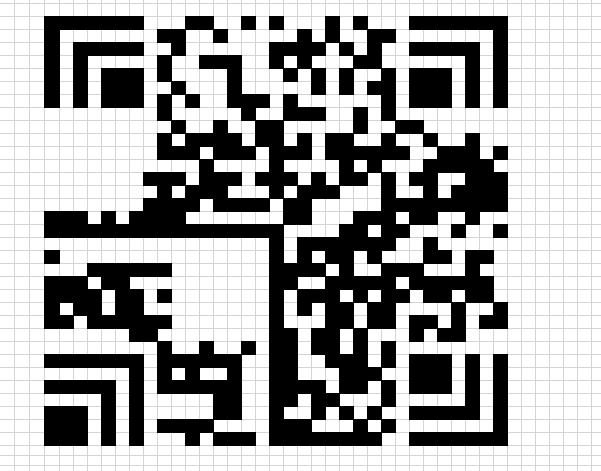
扫个汉信码就出来了
smsto:13511100000:flag{9ee0cb62-f443-4a72-e9a3-43c0b910757e}
[GKCTF 2021]easycms
弱口令进了后台admin/12345
这个后台可以导出模版,发现他导出模版的url看起来就很弱
admin.php?m=ui&f=downloadtheme&theme=L3Zhci93d3cvaHRtbC9zeXN0ZW0vdG1wL3RoZW1lL2RlZmF1bHQvMi56aXA=
base64解码一下
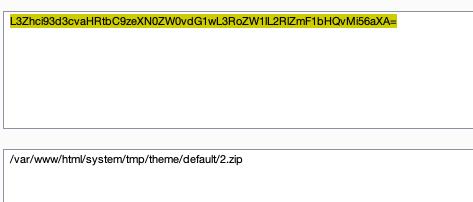
这不纯纯乱杀嘛,直接换成/flag的base64

还有一个解法
设计中最后一栏可以直接修改源码,但是需要在tmp目录下有一个baol.txt
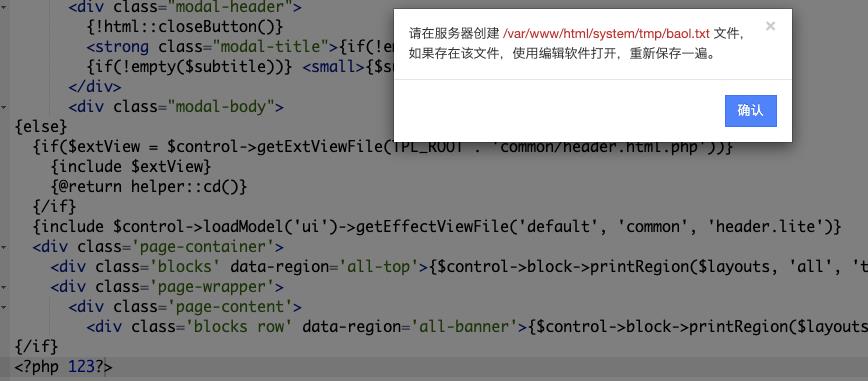
在微信服务这里,原始ID改一下
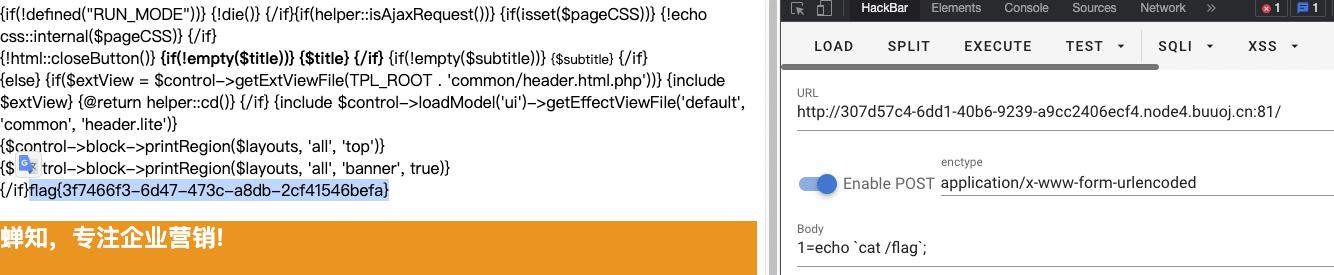
../../../system/tmp/xxxx.txt/0
然后就可以编辑php了
直接执行命令即可
以上是关于[GKCTF2021]复现wp的主要内容,如果未能解决你的问题,请参考以下文章