linux12k8s -->08ingress nginx基于域名的网络转发资源
Posted FikL-09-19
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了linux12k8s -->08ingress nginx基于域名的网络转发资源相关的知识,希望对你有一定的参考价值。
一、 Ingress介绍
在前面课程中已经提到,Service对集群之外暴露服务的主要方式有两种:NotePort和LoadBalancer,但是这两种方式,都有一定的缺点:
# NodePort方式的缺点是会占用很多集群机器的端口,那么当集群服务变多的时候,这个缺点就愈发明显
# LB方式的缺点是每个service需要一个LB,浪费、麻烦,并且需要kubernetes之外设备的支持
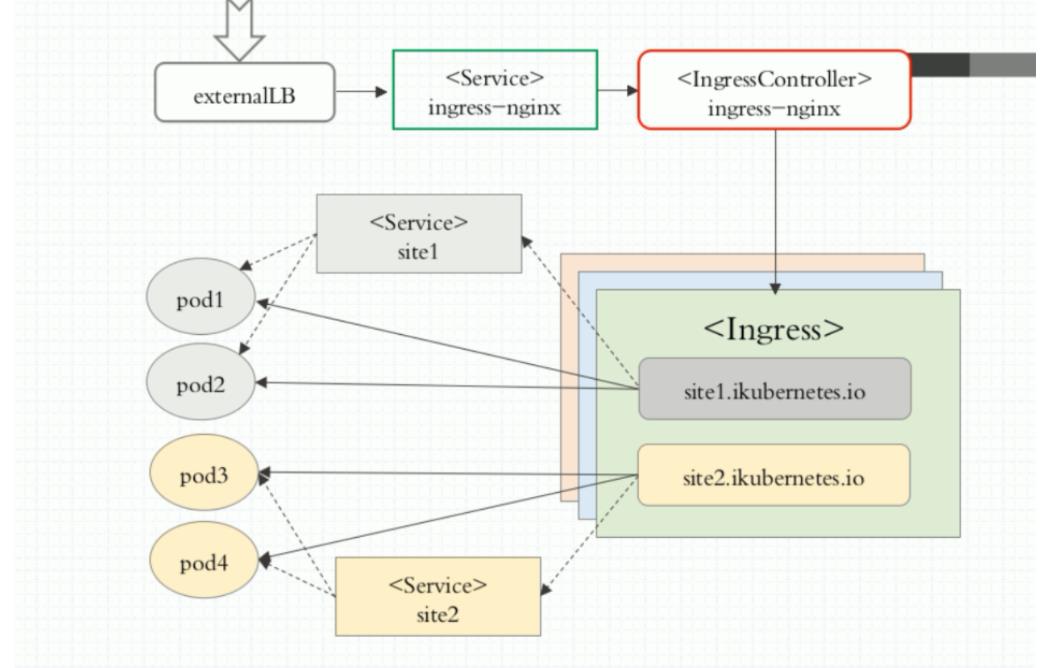
基于这种现状,kubernetes提供了Ingress资源对象,Ingress只需要一个NodePort或者一个LB就可以满足暴露多个Service的需求。工作机制大致如下图表示:
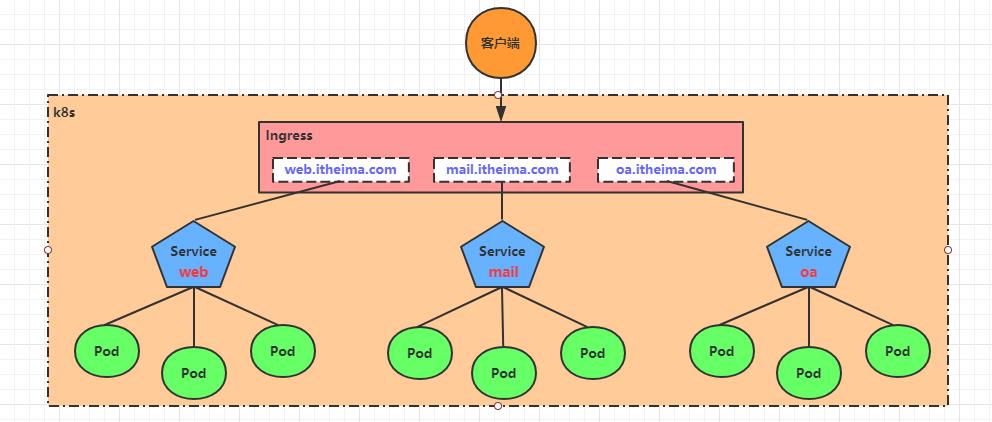
实际上,Ingress相当于一个7层的负载均衡器,是kubernetes对反向代理的一个抽象,它的工作原理类似于nginx,可以理解成在Ingress里建立诸多映射规则,Ingress Controller通过监听这些配置规则并转化成Nginx的反向代理配置 , 然后对外部提供服务。
1、两个核心概念:
# ingress:
kubernetes中的一个对象,作用是定义请求如何转发到service的规则
# ingress controller:
具体实现反向代理及负载均衡的程序,对ingress定义的规则进行解析,根据配置的规则来实现请求转发,实现方式有很多,比如Nginx, Contour, Haproxy等等
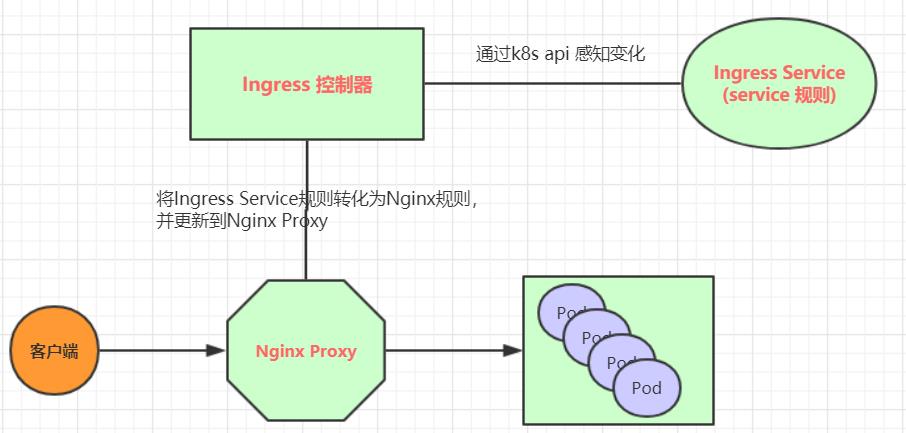
2、Ingress(以Nginx为例)的工作原理如下:
1. 用户编写Ingress规则,说明哪个域名对应kubernetes集群中的哪个Service
2. Ingress控制器动态感知Ingress服务规则的变化,然后生成一段对应的Nginx反向代理配置
3. Ingress控制器会将生成的Nginx配置写入到一个运行着的Nginx服务中,并动态更新
4. 到此为止,其实真正在工作的就是一个Nginx了,内部配置了用户定义的请求转发规则
二、 nginx Ingress (基于域名的网络转发资源)
nginx ingress : 性能强
traefik :原生支持k8s
istio : 服务网格,服务流量的治理
Ingress为Kubernetes集群中的服务提供了入口,可以提供负载均衡、SSL终止和基于名称的虚拟主机,在生产环境中常用的Ingress有Treafik(原生支持k8s)、Nginx(性能强)、HAProxy、Istio(服务网络,服务流量的治理)等。在Kubernetesv 1.1版中添加的Ingress用于从集群外部到集群内部Service的HTTP和HTTPS路由,流量从Internet到Ingress再到Services最后到Pod上,通常情况下,Ingress部署在所有的Node节点上。Ingress可以配置提供服务外部访问的URL、负载均衡、终止SSL,并提供基于域名的虚拟主机。但Ingress不会暴露任意端口或协议。
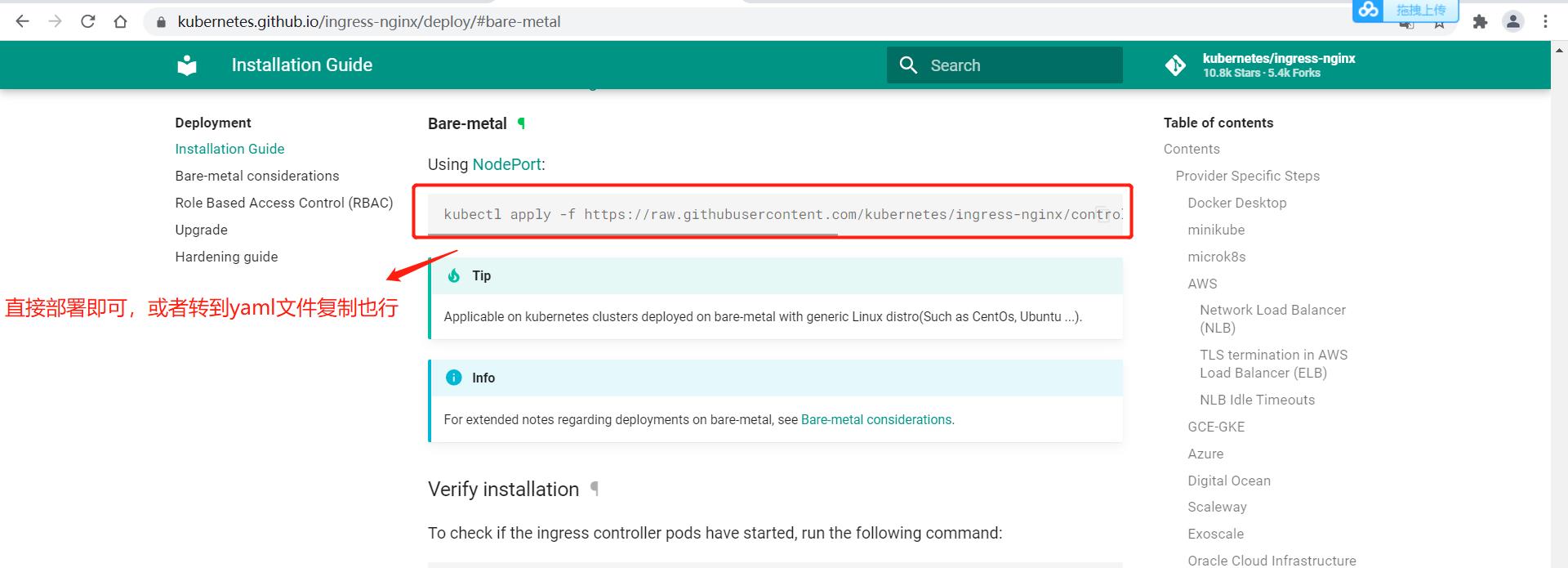
1、部署ingress访问nginx(使用一个域名)
# 1.下载ingress nginx(属于外部网络资源,不是集群内部资源,所以需要安装)
[root@k8s-m-01 ingress]# wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v0.48.1/deploy/static/provider/baremetal/deploy.yaml
# 2、修改镜像
[root@k8s-m-01 ~]# sed -i 's#k8s.gcr.io/ingress-nginx/controller:v0.48.1@sha256:e9fb216ace49dfa4a5983b183067e97496e7a8b307d2093f4278cd550c303899#registry.cn-hangzhou.aliyuncs.com/k8sos/ingress-controller:v0.48.1#g' deploy.yaml
# 3、开始部署并查看
# 扩展:查看是否部署ingress nginx成功
[root@k8s-m-01 ~]# kubectl apply -f deploy.yaml
[root@k8s-m-01 ingress]# kubectl get pod -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-admission-create-bd2tq 0/1 Completed 0 48s #状态为完成是正常的,因为是定时任务
ingress-nginx-admission-patch-x4frt 0/1 Completed 0 48s #显示正在运行就证明部署成功
ingress-nginx-controller-796fb56fb5-7464n 1/1 Running 0 49s # 出现running成功
#4.开始编辑ingress配置清单并部署
[root@k8s-m-01 ~]# vim ingress1.yaml
kind: Deployment
apiVersion: apps/v1
metadata:
name: test-svc
spec:
selector:
matchLabels:
app: test-svc
template:
metadata:
labels:
app: test-svc
spec:
containers:
- name: nginx
imagePullPolicy: IfNotPresent
image: nginx
---
kind: Service
apiVersion: v1
metadata:
name: test-svc
spec:
ports:
- port: 80
targetPort: 80
#nodePort: 38080
name: http
selector:
app: test-svc
type: NodePort
---
apiVersion: networking.k8s.io/v1
kind: Ingress #使用nginx反向代理ingress,可更换成Treafik或Istio
metadata:
name: test-svc-ingress
spec:
rules:
- host: "www.test.com"
http:
paths:
- backend:
service:
name: test-svc
port:
number: 80
path: "/"
pathType: Prefix
[root@k8s-m-01 ~]# kubectl apply -f ingress1.yaml
#5.查看ingress
[root@k8s-m-01 ingress]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
test-svc-ingress <none> www.test.com 192.168.15.112 80 36s
#6.修改主机host文件解析
192.168.15.112 www.test.com
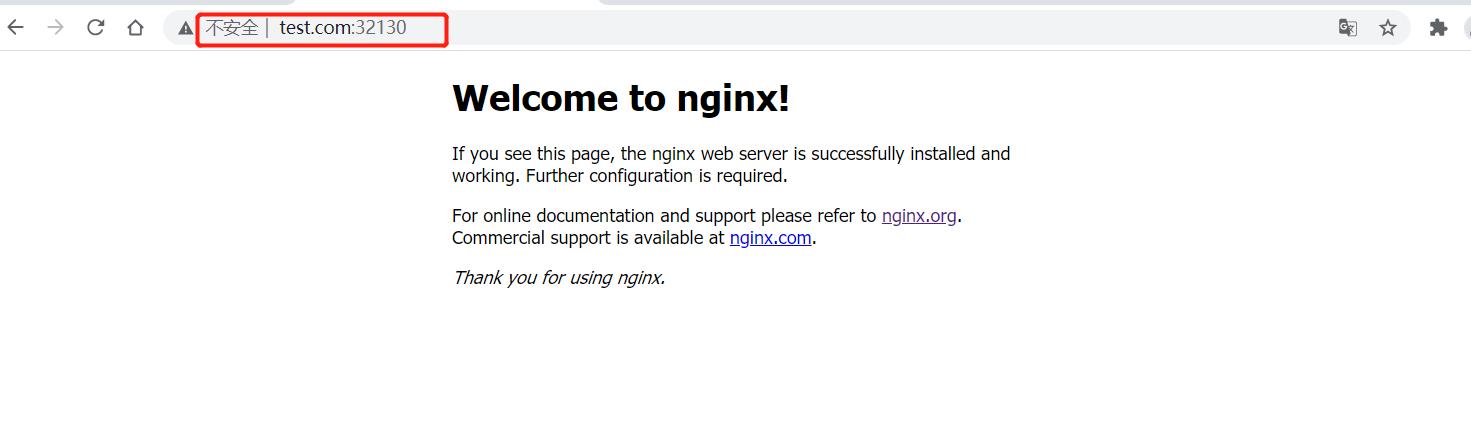
#7.浏览器测试使用域名访问www.test.com:32130
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx #查看端口号32130
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.102.90.34 <none> 80:32130/TCP,443:30236/TCP 25m
ingress-nginx-controller-admission ClusterIP 10.111.226.153 <none> 443/TCP 26m
# 8、IP访问
www.test.com:32130
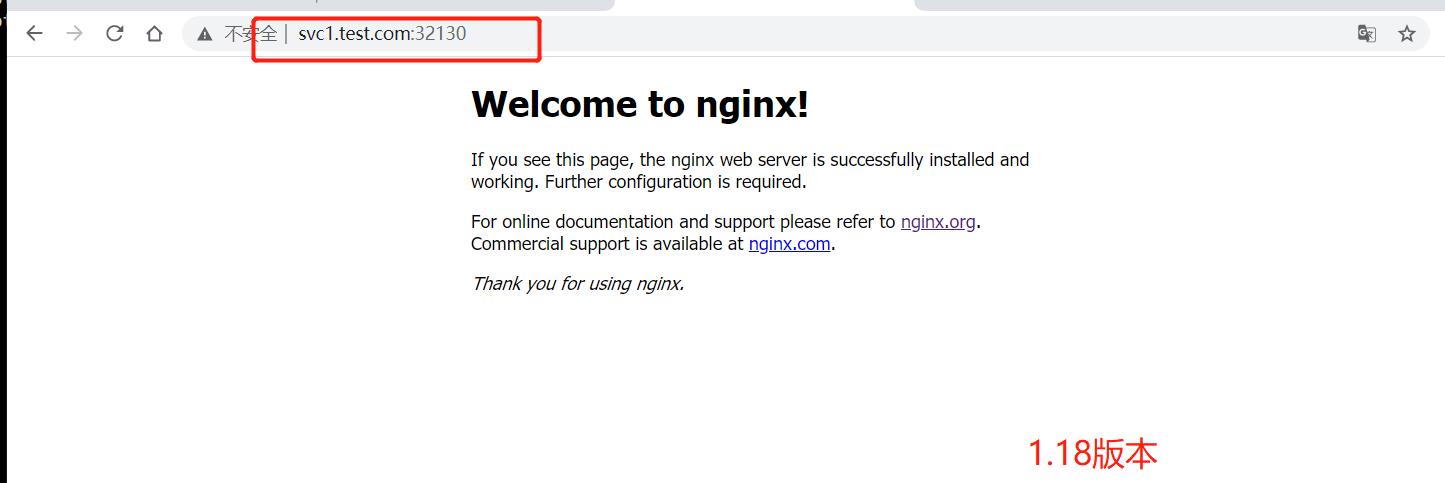
2、部署ingress访问nginx(使用两个不同域名相同的端口号)
使用两个域名指向同一个服务nginx
#1.编辑ingress2.yaml 文件
[root@k8s-m-01 ingress]# vim ingress2.yaml
kind: Deployment
apiVersion: apps/v1
metadata:
name: test-svc-01
spec:
selector:
matchLabels:
app: test-svc-01
template:
metadata:
labels:
app: test-svc-01
spec:
containers:
- name: nginx
imagePullPolicy: IfNotPresent
image: nginx:1.18
---
kind: Service
apiVersion: v1
metadata:
name: test-svc-01
spec:
ports:
- port: 80
targetPort: 80
#nodePort: 38081
selector:
app: test-svc-01
type: NodePort
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: test-svc-ingress-01
spec:
rules:
- host: "svc1.test.com"
http:
paths:
- backend:
service:
name: test-svc-01
port:
number: 80
path: "/"
pathType: Prefix
# 2.部署ingress
[root@k8s-m-01 ingress]# kubectl applf -f ingress2.yaml
#3.查看ingress(此时已有两个域名)
[root@k8s-m-01 ingress]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
test-svc-ingress <none> www.test.com 192.168.15.112 80 15m
test-svc-ingress-01 <none> svc1.test.com 80 16s
# 4.查看 ingress-nginx
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.102.90.34 <none> 80:32130/TCP,443:30236/TCP 42m
ingress-nginx-controller-admission ClusterIP 10.111.226.153 <none> 443/TCP 42m
[root@k8s-m-01 ingress]#
#5.修改主机host文件,浏览器通过域名访问(实现不同域名通过相同的端口号访问nginx)
192.168.15.111 www.test.com svc1.test.com
3、ingress nginx工作原理
实时将ingress转换成nginx配置,并使其生效,从而使nginx代理pod
# 1.部署完ingress配置清单,会实时生成nginx配置
进入nginx容器
[root@k8s-m-01 ingress]# kubectl get pod -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-admission-create-xf7jd 0/1 Completed 0 50m
ingress-nginx-admission-patch-qtl5b 0/1 Completed 0 50m
ingress-nginx-controller-6b86f68f4d-55l8g 1/1 Running 0 50m
[root@k8s-m-01 ingress]# kubectl exec -it -n ingress-nginx ingress-nginx-controller-6b86f68f4d-55l8g -- bash
bash-5.1$ cd /etc/nginx/ #切换到配置文件
bash-5.1$ ls -l
-rw-r--r-- 1 www-data www-data 21420 Apr 2 11:47 nginx.conf
bash-5.1$ vi nginx.conf #查看配置文件内容
## start server www.test.com
server {
server_name www.test.com ; #ingress自动实时生成nginx配置文件
listen 80 ;
listen 443 ssl http2 ;
set $proxy_upstream_name "-";
ssl_certificate_by_lua_block {
certificate.call()
}
location / {
set $namespace "default"; #以下都是通过变量定义
set $ingress_name "ingress-ingress";
set $service_name "service";
set $service_port "80";
set $location_path "/";
set $global_rate_limit_exceeding n;
rewrite_by_lua_block {
lua_ingress.rewrite({
force_ssl_redirect = false,
ssl_redirect = true,
# 2.nginx ingress通过headless service(因为不需要提供集群内部IP,所以选择无头service)对外提供端口服务连接到后端的pod
# 3.相当于通过nginx反向代理到后端pod,因为nginx ingress也是部署在集群内部的,只需要给nginx开一个端口,其他集群服务就不需要端口,让nginx对外提供端口,内部反向代理到后端pod即可
# 3、修改ingress-nginx 端口
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.102.90.34 <none> 80:32130/TCP,443:30236/TCP 53m
ingress-nginx-controller-admission ClusterIP 10.111.226.153 <none> 443/TCP 53m
[root@k8s-m-01 ingress]# kubectl edit svc -n ingress-nginx
nodePort: 32130 #端口可以修改
port: 80
protocol: TCP
targetPort: http
- name: https
nodePort: 30236 #端口可以修改
1、从ingress到pod的流程
ingress ---> endprints(HeadLess Service) ---> pod
2、控制器、service以及ingress管理pod的方式是什么?
控制器 ---> 通过标签
Service ---> endPoints
ingress ---> endpoints
三、Ingress使用
1、配置清单wordpress (了解)
- 部署服务(Deployment + Service)
- 编写ingress配置清单(见下文)
- 命名空间、域名不同,需重新部署证书
# 1、创建文件夹
[root@k8s-master01 ~]# mkdir ingress-controller
[root@k8s-master01 ~]# cd ingress-controller/
# 2、获取ingress-nginx,本次案例使用的是0.30版本
[root@k8s-master01 ingress-controller]# wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.30.0/deploy/static/mandatory.yaml
[root@k8s-master01 ingress-controller]# wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.30.0/deploy/static/provider/baremetal/service-nodeport.yaml
# 3、修改mandatory.yaml文件中的仓库
# 修改quay.io/kubernetes-ingress-controller/nginx-ingress-controller:0.30.0
# 为quay-mirror.qiniu.com/kubernetes-ingress-controller/nginx-ingress-controller:0.30.0
# 4、创建ingress-nginx
[root@k8s-master01 ingress-controller]# kubectl apply -f ./
# 5、查看ingress-nginx
[root@k8s-master01 ingress-controller]# kubectl get pod -n ingress-nginx
NAME READY STATUS RESTARTS AGE
pod/nginx-ingress-controller-fbf967dd5-4qpbp 1/1 Running 0 12h
# 6、查看service
[root@k8s-master01 ingress-controller]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx NodePort 10.98.75.163 <none> 80:32240/TCP,443:31335/TCP 11h
2、准备service和pod
为了后面的实验比较方便,创建如下图所示的模型
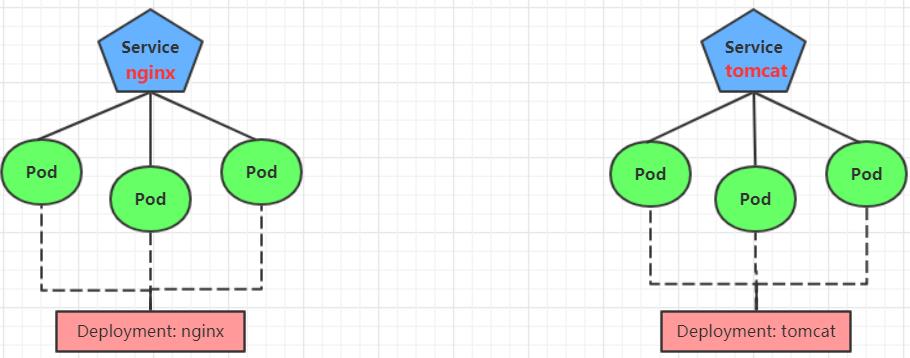
创建tomcat-nginx.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
namespace: dev
spec:
replicas: 3
selector:
matchLabels:
app: nginx-pod
template:
metadata:
labels:
app: nginx-pod
spec:
containers:
- name: nginx
image: nginx
ports:
- containerPort: 80
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: tomcat-deployment
namespace: dev
spec:
replicas: 3
selector:
matchLabels:
app: tomcat-pod
template:
metadata:
labels:
app: tomcat-pod
spec:
containers:
- name: tomcat
image: tomcat:8.5-jre10-slim
ports:
- containerPort: 8080
---
apiVersion: v1
kind: Service
metadata:
name: nginx-service
namespace: dev
spec:
selector:
app: nginx-pod
clusterIP: None
type: ClusterIP
ports:
- port: 80
targetPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: tomcat-service
namespace: dev
spec:
selector:
app: tomcat-pod
clusterIP: None
type: ClusterIP
ports:
- port: 8080
targetPort: 8080
# 1、创建
[root@k8s-m-01 ~]# kubectl create -f tomcat-nginx.yaml
# 2、查看
[root@k8s-m-01 ~]# kubectl get svc -n dev
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
nginx-service ClusterIP None <none> 80/TCP 48s
tomcat-service ClusterIP None <none> 8080/TCP 48s
3、Http代理
创建ingress-http.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-http
namespace: dev
spec:
rules:
- host: nginx.itheima.com
http:
paths:
- path: /
backend:
serviceName: nginx-service
servicePort: 80
- host: tomcat.itheima.com
http:
paths:
- path: /
backend:
serviceName: tomcat-service
servicePort: 8080
# 1、创建
[root@k8s-m-01 ~]# kubectl create -f ingress-http.yaml
ingress.extensions/ingress-http created
# 2、查看
[root@k8s-m-01 ~]# kubectl get ing ingress-http -n dev
NAME HOSTS ADDRESS PORTS AGE
ingress-http nginx.itheima.com,tomcat.itheima.com 80 22s
# 3、查看详情
[root@k8s-m-01 ~]# kubectl describe ing ingress-http -n dev
...
Rules:
Host Path Backends
---- ---- --------
nginx.itheima.com / nginx-service:80 (10.244.1.96:80,10.244.1.97:80,10.244.2.112:80)
tomcat.itheima.com / tomcat-service:8080(10.244.1.94:8080,10.244.1.95:8080,10.244.2.111:8080)
...
[root@k8s-m-01 ingress-controller]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx NodePort 10.101.84.61 <none> 80:32240/TCP,443:30007/TCP 23m
# 接下来,在本地电脑上配置host文件,解析上面的两个域名到192.168.109.100(master)上
# 然后,就可以分别访问tomcat.itheima.com:32240 和 nginx.itheima.com:32240 查看效果了
4、Https代理
创建证书
# 1、生成证书
openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/C=CN/ST=BJ/L=BJ/O=nginx/CN=itheima.com"
# 2、创建密钥
kubectl create secret tls tls-secret --key tls.key --cert tls.crt
创建ingress-https.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-https
namespace: dev
spec:
tls:
- hosts:
- nginx.itheima.com
- tomcat.itheima.com
secretName: tls-secret # 指定秘钥
rules:
- host: nginx.itheima.com
http:
paths:
- path: /
backend:
serviceName: nginx-service
servicePort: 80
- host: tomcat.itheima.com
http:
paths:
- path: /
backend:
serviceName: tomcat-service
servicePort: 8080
# 1、创建
[root@k8s-m-01 ~]# kubectl create -f ingress-https.yaml
ingress.extensions/ingress-https created
# 2、查看
[root@k8s-m-01 ~]# kubectl get ing ingress-https -n dev
NAME HOSTS ADDRESS PORTS AGE
ingress-https nginx.itheima.com,tomcat.itheima.com 10.104.184.38 80, 443 2m42s
# 3、查看详情
[root@k8s-m-01 ~]# kubectl describe ing ingress-https -n dev
...
TLS:
tls-secret terminates nginx.itheima.com,tomcat.itheima.com
Rules:
Host Path Backends
---- ---- --------
nginx.itheima.com / nginx-service:80 (10.244.1.97:80,10.244.1.98:80,10.244.2.119:80)
tomcat.itheima.com / tomcat-service:8080(10.244.1.99:8080,10.244.2.117:8080,10.244.2.120:8080)
...
# 下面可以通过浏览器访问https://nginx.itheima.com:31335 和 https://tomcat.itheima.com:31335来查看了
四、ingress常用用法
# 官网 https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/#service-upstream
有两种方式:
1、注解: 当前ingress生效
2、configMap: 全局ingress生效
所有部署都i是基于此代码
[root@k8s-m-01 ingress]# vim ingress1.yaml
kind: Deployment
apiVersion: apps/v1
metadata:
name: test-svc
spec:
selector:
matchLabels:
app: test-svc
template:
metadata:
labels:
app: test-svc
spec:
containers:
- name: nginx
imagePullPolicy: IfNotPresent
image: nginx
---
kind: Service
apiVersion: v1
metadata:
name: test-svc
spec:
ports:
- port: 80
targetPort: 80
#nodePort: 38080
name: http
selector:
app: test-svc
type: NodePort
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: test-svc-ingress
# annotations:
# nginx.ingress.kubernetes.io/auth-type: basic
# nginx.ingress.kubernetes.io/auth-secret: basic-auth
# nginx.ingress.kubernetes.io/auth-realm: "在线发牌!"
spec:
rules:
- host: "www.test.com"
http:
paths:
- backend:
service:
name: test-svc
port:
number: 80
path: "/"
pathType: Prefix
0.编写注解,使用auth功能
# 1、下载软件
[root@k8s-m-01 ingress]# yum -y install httpd-tools
# 2、生成密码
[root@k8s-m-01 ingress]# htpasswd -c auth mm
New password:
Re-type new password:
Adding password for user mm
# 3、创建secret,把密码文件放置于集群中
[root@k8s-m-01 ingress]# kubectl create secret generic basic-auth --from-file=auth
# 4、编写注解,使用auth功能
[root@k8s-m-01 ingress]# vim ingress1.yaml
kind: Deployment
apiVersion: apps/v1
metadata:
name: test-svc
spec:
selector:
matchLabels:
app: test-svc
template:
metadata:
labels:
app: test-svc
spec:
containers:
- name: nginx
imagePullPolicy: IfNotPresent
image: nginx
---
kind: Service
apiVersion: v1
metadata:
name: test-svc
spec:
ports:
- port: 80
targetPort: 80
#nodePort: 38080
name: http
selector:
app: test-svc
type: NodePort
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: test-svc-ingress
annotations: #这行注释必须有这
nginx.ingress.kubernetes.io/auth-type: basic #使用kubernetes模块
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: "在线发牌!"
spec:
rules:
- host: "www.test.com"
http:
paths:
- backend:
service:
name: test-svc
port:
number: 80
path: "/"
pathType: Prefix
#5.部署ingress
[root@k8s-m-01 ~]# kubectl apply -f ingress.yaml
#6.查看端口(32130)
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.102.90.34 <none> 80:32130/TCP,443:30236/TCP 4h44m
ingress-nginx-controller-admission ClusterIP 10.111.226.153 <none> 443/TCP 443/TCP
#7.查看域名
[root@k8s-m-01 ingress]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
test-svc-ingress <none> www.test.com 192.168.15.112 80 11m
#8.配置主机host文件并访问
192.168.15.111 www.test-nginx.com
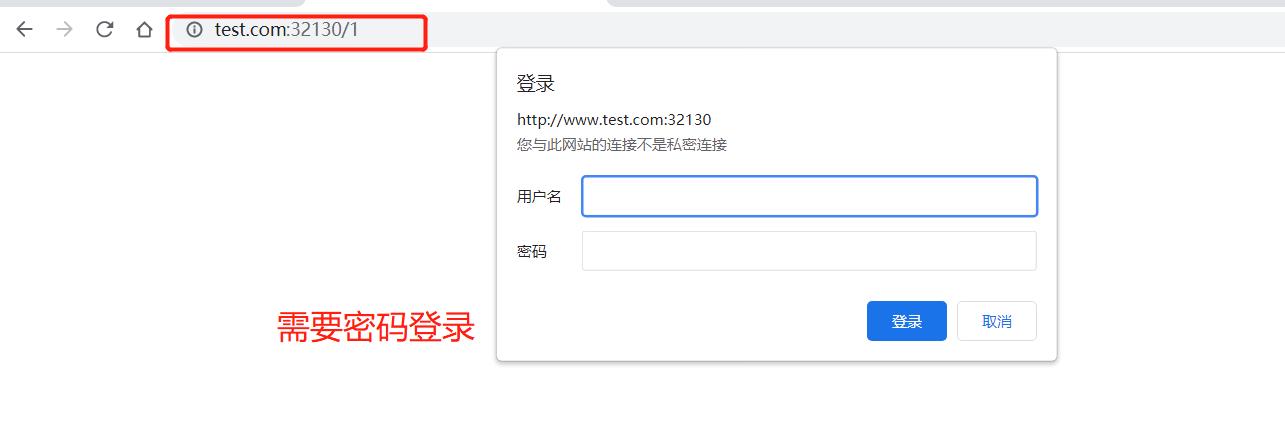
1.域名重定向(不能重定向到 /)
#1.修改配置清单(以nginx为例)
[root@k8s-m-01 ingress]# vim ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-ingress
namespace: default
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/rewrite-target: https://www.baidu.com/s?wd=nginx #指定重定向的域名(百度网址)
spec:
rules:
- host: www.test-nginx.com
http:
paths:
- path: /
backend:
serviceName: test-svc
servicePort: 80
#2.部署ingress
[root@k8s-m-01 ingress]# kubectl apply -f ingress.yaml
#3.查看端口(32708)
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.96.60.88 <none> 80:32708/TCP,443:32731/TCP 16h
ingress-nginx-controller-admission ClusterIP 10.106.141.57 <none> 443/TCP 16h
#4.查看域名
[root@k8s-m-01 ingress]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress-ingress <none> www.test-nginx.com 80 14s
#5.配置主机host文件并访问
192.168.12.11 www.test-nginx.com
访问:www.test-nginx.com:32708 自动重定向到百度
2.限速设置
后面的数字必须加引号
定义连接和传输速率的限制用于减轻DDoS攻击 (在配置清单里 kubernetes.io/ingress.class: "nginx"下边一行齐头写入)
# 1.nginx.ingress.kubernetes.io/limit-connections:'1'
允许从单个IP地址进行并发连接的数量。超过此限制时返回 503 错误。
# 2.nginx.ingress.kubernetes.io/limit-rps:'2'
每秒接受来自给定 IP 的请求数量。爆破限制设置为此限制乘以爆破乘数,默认乘数为 5。当客户超过此限制时,将返回限制-重新q-状态代码:503。
# 3.nginx.ingress.kubernetes.io/limit-rpm: '2'
每分钟接受来自给定 IP 的请求数量。爆破限制设置为此限制乘以爆破乘数,默认乘数为 5。当客户超过此限制时,将返回限制-重新q-状态代码:503。
# 4.nginx.ingress.kubernetes.io/limit-burst-multiplier: '2'
爆裂大小限制速率的乘数。默认爆破乘数为 5,此注释覆盖默认乘数。当客户超过此限制时,将返回限制-重新q-状态代码:503。
# 5.nginx.ingress.kubernetes.io/limit-rate-after:
初始千字节数,之后对给定连接的进一步响应传输将受到率限制。此功能必须与启用代理缓冲一起使用。
# 6.nginx.ingress.kubernetes.io/limit-rate:
允许发送到给定连接的每秒千字节数。零值禁用率限制。此功能必须与启用代理缓冲一起使用。
# 7.nginx.ingress.kubernetes.io/limit-whitelist:
客户端 IP 源范围将排除在费率限制之外。该值是CIDR的逗号分离列表。
如果您在单个入口规则中指定多个注释,则在顺序中应用限制,limit-connectionslimit-rpmlimit-rps
# 配置
[root@k8s-m-01 ingress]# cat ingress1.yaml
annotations:
nginx.ingress.kubernetes.io/limit-connections: '1'
#可以使用ab工具测试
nginx.ingress.kubernetes.io/limit-rps: '2'
#每秒访问频率,超过2次报503,见下图
nginx.ingress.kubernetes.io/limit-rpm: '2'
#每分钟访问频率,超过2次报503,见下图
nginx.ingress.kubernetes.io/limit-burst-multiplier:'2'
# 爆裂大小限制速率的乘数
nginx.ingress.kubernetes.io/limit-rate-after:'2'
# 初始千字节数(类似于百度网盘每分钟下载数 -- 1m/s)
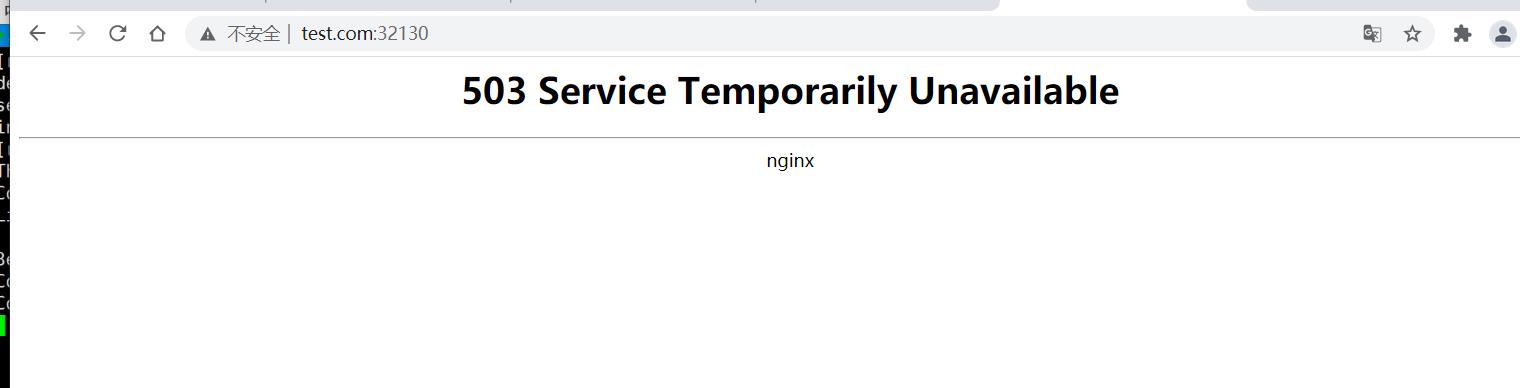
3.设置ingress白名单
通过注释指定允许的客户端 IP 源范围 (多个IP用逗号隔开)
#1.修改配置清单
[root@k8s-m-01 ~]# vim ingress1.yaml
...
annotations:
nginx.ingress.kubernetes.io/whitelist-source-range:
192.168.15.111,192.168.15.112 #白名单内没有指定192.168.15.113允许访问
spec:
rules:
- host: "www.test.com"
http:
paths:
- backend:
service:
name: test-svc
port:
number: 80
...
#2.部署ingress
[root@k8s-m-01 ~]# kubectl apply -f ingress.yaml
#3.查看端口(32130)
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.102.90.34 <none> 80:32130/TCP,443:30236/TCP 5h28m
ingress-nginx-controller-admission ClusterIP 10.111.226.153 <none> 443/TCP
#4.查看域名
[root@k8s-m-01 ingress]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
test-svc-ingress <none> www.test.com 192.168.15.112 80 56m
#5.配置主机host文件并访问
192.168.15.112 www.test.com
#6.允许访问的IP是日志里面的ip
[root@k8s-m-01 ingress]# kubectl get pod -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-admission-create-xf7jd 0/1 Completed 0 5h31m
ingress-nginx-controller-6b86f68f4d-55l8g 1/1 Running 0 5h31m
[root@k8s-m-01 ingress]# kubectl logs -n ingress-nginx ingress-nginx-controller-6b86f68f4d-55l8g
10.244.1.1 - - [12/Aug/2021:12:42:55 +0000] "GET / HTTP/1.1" 304 0 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (Khtml, like Gecko) Chrome/92.0.4515.107 Safari/537.36" 544 0.001 [default-test-svc-80] [] 10.244.1.27:80 0 0.001 304 a022eca80abad37c3fa2280bf3accc1b
访问:www.test.com:32130 被拒绝===》因为被ingress白名单拦截
在主机的是可以ping通的
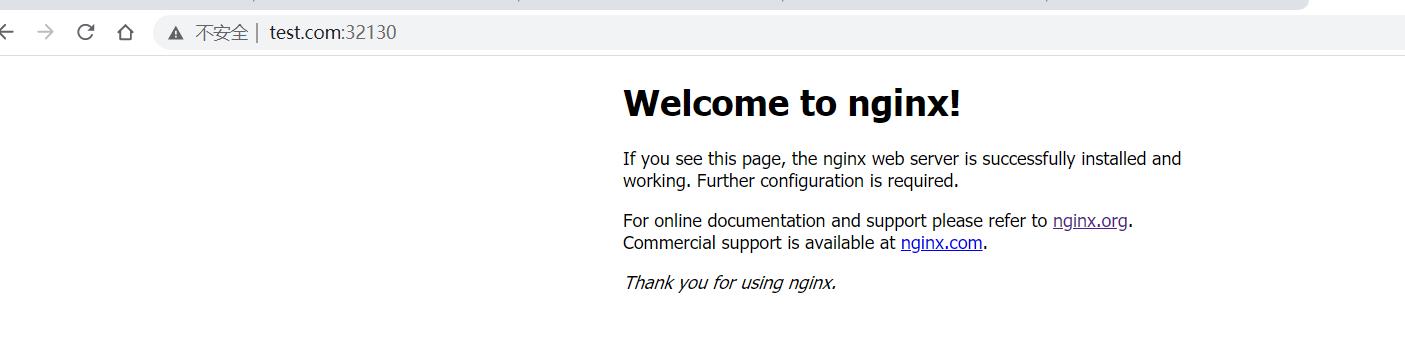
4.永久重定向
允许返回永久重定向(返回代码 301),而不是向上游发送数据。
例如,将所有内容重定向到 Google。nginx.ingress.kubernetes.io/permanent-redirect: https://www.google.com
#1.修改配置清单(以nginx为例)
[root@k8s-m-01 ~]# vim ingress.yaml
...
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: test-svc-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: https://www.baidu.com #重定向到百度
spec
...
#2.部署ingress
[root@k8s-m-01 ~]# kubectl apply -f ingress.yaml
#3.查看端口(32130)
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.102.90.34 <none> 80:32130/TCP,443:30236/TCP 4h44m
ingress-nginx-controller-admission ClusterIP 10.111.226.153 <none> 443/TCP 443/TCP
#4.查看域名
[root@k8s-m-01 ingress]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
test-svc-ingress <none> www.test.com 192.168.15.112 80 11m
#5.配置主机host文件并访问
192.168.15.111 www.test-nginx.com
访问:www.test.com:32130 自动重定向到百度
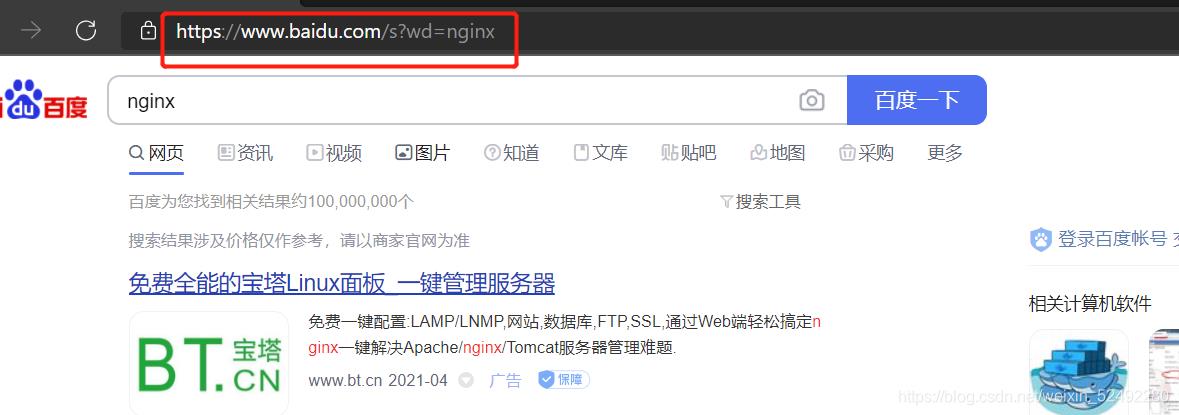
5.永久重定向码
允许您修改用于永久重定向的状态代码。例如,将返回您的永久重定向与308。nginx.ingress.kubernetes.io/permanent-redirect-code: '308'
#1.修改配置清单(以nginx为例)
[root@k8s-m-01 ~]# vim ingress.yaml
...
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: test-svc-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: https://www.baidu.com #重定向到百度
nginx.ingress.kubernetes.io/permanent-redirect-code: '308' #重定向状态码
spec
...
#2.部署ingress
[root@k8s-m-01 ~]# kubectl apply -f ingress.yaml
#3.查看端口(32130)
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.102.90.34 <none> 80:32130/TCP,443:30236/TCP 4h44m
ingress-nginx-controller-admission ClusterIP 10.111.226.153 <none> 443/TCP 443/TCP
#4.查看域名
[root@k8s-m-01 ingress]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
test-svc-ingress <none> www.test.com 192.168.15.112 80 11m
#5.配置主机host文件并访问
192.168.15.111 www.test.com
访问:www.test.com:32130 自动重定向到百度
# 6、容器里面查看
[root@k8s-m-01 ingress]# kubectl get pod -n ingress-nginx
NAME READY STATUS RESTARTS AGE
ingress-nginx-admission-create-xf7jd 0/1 Completed 0 5h
ingress-nginx-controller-6b86f68f4d-55l8g 1/1 Running 0 5h
[root@k8s-m-01 ingress]# kubectl exec -it -n ingress-nginx ingress-nginx-controller-6b86f68f4d-55l8g -- bash
bash-5.1$ cd /etc/nginx/
bash-5.1$ vi nginx.conf
http_redirect_code = 308,
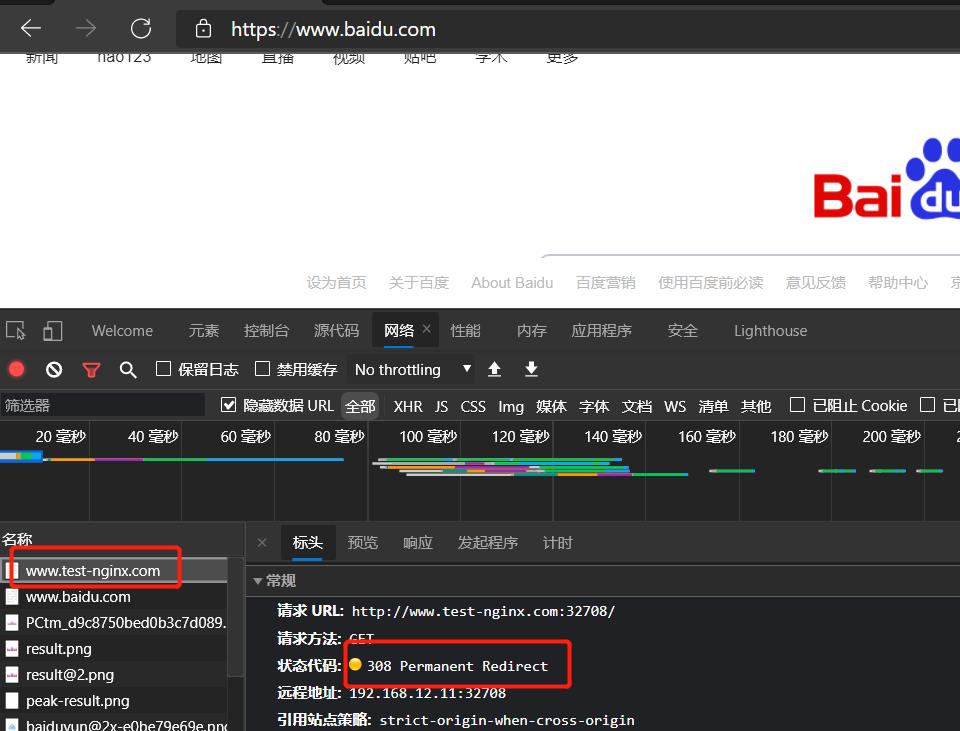
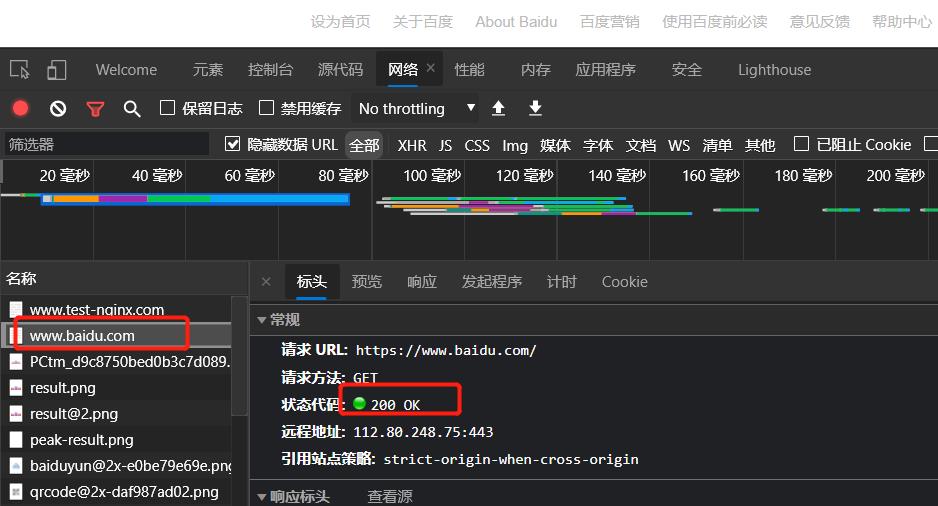
6.代理HTTP版本
设置 Nginx 反向代理用于与后端通信的proxy_http_version。 默认情况下,此设置为"1.1"。
annotations:
nginx.ingress.kubernetes.io/proxy-http-version: "1.0"
7.启用访问日志
默认情况下启用了访问日志,但在某些情况下,可能需要禁用给定入口的访问日志。
#1. 默认情况下启用了访问日志,但在某些情况下,可能需要禁用给定入口的访问日志。
nginx.ingress.kubernetes.io/enable-access-log: "true" #启用访问日志
#2.默认情况下未启用重写日志。在某些情况下,可能需要启用 NGINX 重写日志。请注意,重写日志将发送到通知级别的error_log文件。
nginx.ingress.kubernetes.io/enable-rewrite-log: "true" #启用重写日志
#3.开启跟踪可以通过 ConfigMap 在全球范围内启用或禁用,但有时需要将其覆盖才能启用或禁用特定入口(例如关闭外部健康检查端点的跟踪)
nginx.ingress.kubernetes.io/enable-opentracing: "true" #启用开放跟踪
#4.要将非标准标题添加到具有字符串值的上游请求中,可以使用以下注释:X-Forwarded-Prefix
nginx.ingress.kubernetes.io/x-forwarded-prefix: "/path" #X转发前缀标题
8.SSL密码
#1.使用此注释将在服务器级别设置指令。此配置对主机中的所有路径都是活跃的。ssl_ciphers
nginx.ingress.kubernetes.io/ssl-ciphers: "ALL:!aNULL:!EXPORT56:RC4+RSA:+HIGH:+MEDIUM:+LOW:+SSLv2:+EXP" #启用ssl密码
#2.以下注释将在服务器级别设置指令。此配置指定在使用 SSLv3 和 TLS 协议时,服务器密码应优先于客户端密码。ssl_prefer_server_ciphers
nginx.ingress.kubernetes.io/ssl-prefer-server-ciphers: "true" #启用ssl密码
9.使用正则的方式匹配(支持的正则比较少)
#1.修改配置清单
kind: Ingress
apiVersion: extensions/v1beta1
metadata:
name: ingress-ingress-nginx-tls
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/rewrite-target: https://www.baidu.com/s?wd=$1 #增加变量
spec:
rules:
- host: www.test-nginx.com
http:
paths:
- path: /search/(.+) #匹配所有
backend:
serviceName: wordpress-nginx
servicePort: 80
#2.部署步骤与上文同步此处省略
#3.配置主机host测试访问
192.168.15.111 www.test-nginx.com
访问:www.test-nginx.com:32708/search/kubernetes
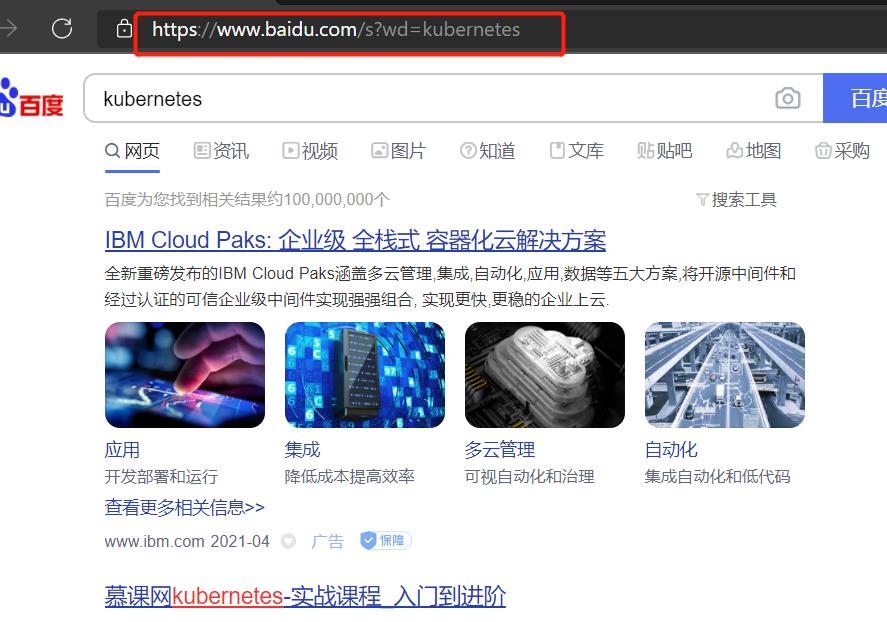
#1.定义以下入口
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: test-ingress-3
annotations:
nginx.ingress.kubernetes.io/use-regex: "true" #开启正则
spec:
rules:
- host: test.com
http:
paths:
- path: /foo/bar/bar
backend:
serviceName: test
servicePort: 80
- path: /foo/bar/[A-Z0-9]{3}
backend:
serviceName: test
servicePort: 80
#2.入口控制器将在服务器的 NGINX 模板中定义以下位置块(按此顺序):test.com
location ~ "^/foo/bar/[A-Z0-9]{3}" {
...
}
location ~ "^/foo/bar/bar" {
...
}
10.nginx登录
apiVersion: extensions/v1beta1
metadata:
name: ingress-ingress-nginx-tls
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
# nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - foo'
spec:
rules:
- host: www.test-nginx.com
http:
paths:
- path: /
backend:
serviceName: wordpress-nginx
servicePort: 80
11.HTTPS
# 1、创建HTTPS证书
[root@k8s-m-01 ingress]# openssl genrsa -out tls.key 2048
[root@k8s-m-01 ingress]# openssl req -new -x509 -key tls.key -out tls.crt -subj /C=CN/ST=ShangHai/L=ShangHai/O=Ingress/CN=www.test.com
# 2、将证书加入Secret
[root@k8s-m-01 ingress]# kubectl create secret tls ingress-tls --cert=tls.crt --key=tls.key
# 3、编辑配置文件
[root@k8s-m-01 ingress]# vim ingress1.yaml
kind: Deployment
apiVersion: apps/v1
metadata:
name: test-svc
spec:
selector:
matchLabels:
app: test-svc
template:
metadata:
labels:
app: test-svc
spec:
containers:
- name: nginx
imagePullPolicy: IfNotPresent
image: nginx
---
kind: Service
apiVersion: v1
metadata:
name: test-svc
spec:
ports:
- port: 80
targetPort: 80
#nodePort: 38080
name: http
selector:
app: test-svc
type: NodePort
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: test-svc-ingress
annotations:
nginx.ingress.kubernetes.io/whitelist-source-range: 10.244.1.1
spec:
tls: #证书
- secretName: ingress-tls # secret名字
hosts:
- "www.test.com"
rules:
- host: "www.test.com"
http:
paths:
- backend:
service:
name: test-svc
port:
number: 80
path: "/"
pathType: Prefix
# 4、查看ingress暴露的443端口
[root@k8s-m-01 ingress]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.102.90.34 <none> 80:32130/TCP,443:30236/TCP 5h54m
ingress-nginx-controller-admission ClusterIP 10.111.226.153 <none> 443/TCP
# 5、浏览器访问
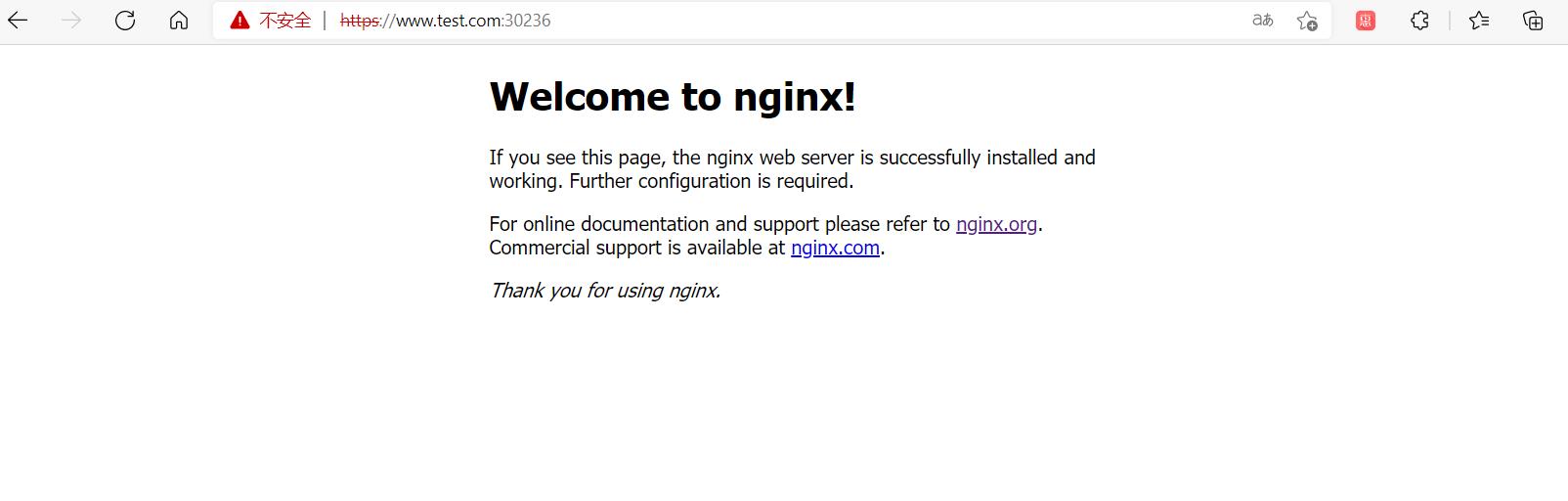
https://www.test.com:30236
以上是关于linux12k8s -->08ingress nginx基于域名的网络转发资源的主要内容,如果未能解决你的问题,请参考以下文章