IPV6大型网络配置实战
Posted 新网工李白
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了IPV6大型网络配置实战相关的知识,希望对你有一定的参考价值。
📢CSDN主页:新网工李白
📢路由交换专栏 : HCIE Routing&Switching

🍭问题描述
目前属于IPV6过渡阶段,NAT64是一种实现IPV4和IPV6之间网络互访的技术。NAT64可以用于IPV4主动访问IPV6,也可以用于IPV6主动访问IPV4。
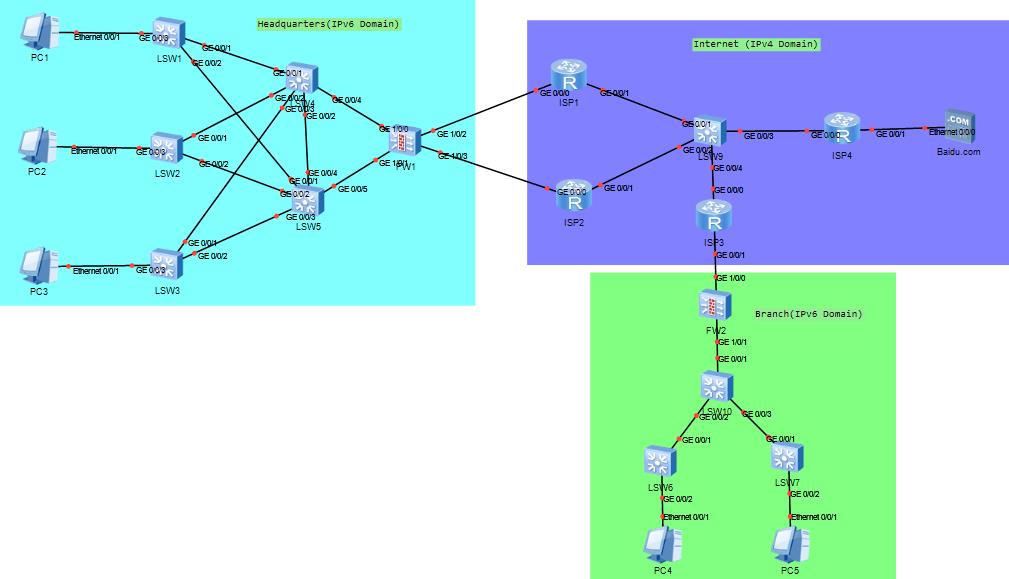
🍭实验环境
本次集训营实验拓扑一共有三部分组成,其中总部的内网是双层架构,边界设备是一台防火墙;分支的内部架构相对而言简单一点,边界和总部一样,布置一台防火墙。不管是总部还是分部,内网都使用IPv6,第三个部分是运营商部分,因为一些原因运营商网络没有迁移到IPv6,内网全部都是IPv4。
🍭实验需求
1️⃣要求总部、分部的IPv6主机可以访问运营商的IPv4服务器。
2️⃣要求总部内部的IPv6主机和分支内部的IPv6主机通过整个公网来互相访问。
🍭具体配置
一、总部
📝LSW1
vlan batch 14 15 100
int g0/0/3
port link-type access
port default vlan 100
stp edged-port enable
quit
int g0/0/1
port link-type access
port default vlan 14
quit
int g0/0/2
port link-type access
port default vlan 15
quit
ipv6
int vlan 100
ipv6 enable
ipv6 address 2001:0:0:100::1 64
quit
int vlan 14
ipv6 enable
ipv6 address 2001:0:0:14::1 64
quit
int vlan 15
ipv6 enable
ipv6 address 2001:0:0:15::1 64
quit
undo stp enable
📝LSW2
vlan batch 24 25 200
int g0/0/3
port link-type access
port default vlan 200
stp edged-port enable
quit
int g0/0/1
port link-type access
port default vlan 24
quit
int g0/0/2
port link-type access
port default vlan 25
quit
ipv6
int vlan 200
ipv6 enable
ipv6 address 2001:0:0:200::2 64
quit
int vlan 24
ipv6 enable
ipv6 address 2001:0:0:24::2 64
quit
int vlan 25
ipv6 enable
ipv6 address 2001:0:0:25::2 64
quit
undo stp enable
📝LSW3
vlan batch 34 35 300
int g0/0/3
port link-type access
port default vlan 300
stp edged-port enable
quit
int g0/0/1
port link-type access
port default vlan 34
quit
int g0/0/2
port link-type access
port default vlan 35
quit
ipv6
int vlan 300
ipv6 enable
ipv6 address 2001:0:0:300::3 64
quit
int vlan 34
ipv6 enable
ipv6 address 2001:0:0:34::3 64
quit
int vlan 35
ipv6 enable
ipv6 address 2001:0:0:35::3 64
quit
undo stp enable
📝LSW4
vlan batch 14 24 34 41 45
ipv6
int g0/0/3
port link-type access
port default vlan 34
quit
int g0/0/1
port link-type access
port default vlan 14
quit
int g0/0/2
port link-type access
port default vlan 24
quit
int g0/0/4
port link-type access
port default vlan 41
quit
int g0/0/24
port link-type access
port default vlan 45
quit
int vlan 14
ipv6 enable
ipv6 address 2001:0:0:14::4 64
quit
int vlan 24
ipv6 enable
ipv6 address 2001:0:0:24::4 64
quit
int vlan 34
ipv6 enable
ipv6 address 2001:0:0:34::4 64
quit
int vlan 41
ipv6 enable
ipv6 address 2001:0:0:41::4 64
quit
int vlan 45
ipv6 enable
ipv6 address 2001:0:0:45::4 64
quit
undo stp enable
📝LSW5
vlan batch 15 25 35 45 51
ipv6
int g0/0/3
port link-type access
port default vlan 35
quit
int g0/0/1
port link-type access
port default vlan 15
quit
int g0/0/2
port link-type access
port default vlan 25
quit
int g0/0/24
port link-type access
port default vlan 45
quit
int g0/0/5
port link-type access
port default vlan 51
quit
int vlan 15
ipv6 enable
ipv6 address 2001:0:0:15::5 64
quit
int vlan 25
ipv6 enable
ipv6 address 2001:0:0:25::5 64
quit
int vlan 35
ipv6 enable
ipv6 address 2001:0:0:35::5 64
quit
int vlan 45
ipv6 enable
ipv6 address 2001:0:0:45::5 64
quit
int vlan 51
ipv6 enable
ipv6 address 2001:0:0:51::5 64
quit
undo stp enable
接下来我们做一下防火墙的配置
📝FW1:(默认用户名:admin 密码: Admin123)
ipv6
int g1/0/0
ipv6 enable
ipv6 add 2001:0:0:41::1 64
quit
int g1/0/1
ipv6 enable
ipv6 add 2001:0:0:51::1 64
quit
int g1/0/2
ip add 100.1.11.1 24
quit
int g1/0/3
ip add 100.1.12.1 24
quit
firewall zone trust
add interface g1/0/0
add interface g1/0/1
quit
firewall zone untrust
add interface g1/0/2
add interface g1/0/3
quit
security-policy
default action permit
Warning:Setting the default packet filtering to permit poses security risks. You are advised to configure the security policy based on the actual data flows. Are you sure you want to continue?[Y/N] y //这里为警告提示我们输入y(yes)即可.
quit
int g1/0/0
service-manage ping permit
quit
int g1/0/1
service-manage ping permit
quit
int g1/0/2
service-manage ping permit
quit
int g1/0/3
service-manage ping permit
quit
ospfv3 10
router-id 100.100.100.100
quit
int g1/0/0
ospfv3 10 area 0
int g1/0/1
ospfv3 10 area 0
quit
ospfv3 10
default-route-advertise always
下一步我们来运行ospf
📝LSW1
ospfv3 10
router-id 1.1.1.1
quit
int vlan 100
ospfv3 10 area 0
int vlan 14
ospfv3 10 area 0
int vlan 15
ospfv3 10 area 0
quit
📝LSW2
ospfv3 10
router-id 2.2.2.2
quit
int vlan 200
ospfv3 10 area 0
int vlan 24
ospfv3 10 area 0
int vlan 25
ospfv3 10 area 0
📝LSW3
ospfv3 10
router-id 3.3.3.3
quit
int vlan 300
ospfv3 10 area 0
int vlan 34
ospfv3 10 area 0
int vlan 35
ospfv3 10 area 0
quit
📝LSW4
ospfv3 10
router-id 4.4.4.4
quit
int vlan 14
ospfv3 10 area 0
int vlan 24
ospfv3 10 area 0
int vlan 34
ospfv3 10 area 0
int vlan 45
ospfv3 10 area 0
int vlan 41
ospfv3 10 area 0
quit
📝LSW5
ospfv3 10
router-id 5.5.5.5
quit
int vlan 15
ospfv3 10 area 0
int vlan 25
ospfv3 10 area 0
int vlan 35
ospfv3 10 area 0
int vlan 45
ospfv3 10 area 0
int vlan 51
ospfv3 10 area 0
quit
二、运营商
📝ISP1
int g0/0/0
ip add 100.1.11.2 24
quit
int g0/0/1
ip add 100.1.100.1 24
quit
ospf 10 router-id 1.1.1.1
area 0
net 100.1.11.2 0.0.0.0
net 100.1.100.1 0.0.0.0
quit
silent-interface g0/0/0
quit
📝ISP2
int g0/0/0
ip add 100.1.12.2 24
quit
int g0/0/1
ip add 100.1.100.2 24
quit
ospf 10 router-id 2.2.2.2
area 0
net 100.1.12.2 0.0.0.0
net 100.1.100.2 0.0.0.0
quit
silent-interface g0/0/0
quit
📝ISP3
int g0/0/0
ip add 100.1.100.3 24
quit
int g0/0/1
ip add 100.1.23.3 24
quit
ospf 10 router-id 3.3.3.3
area 0
net 100.1.23.3 0.0.0.0
net 100.1.100.3 0.0.0.0
quit
silent-interface g0/0/1
quit
📝ISP4
int g0/0/0
ip add 100.1.100.4 24
quit
int g0/0/1
ip add 100.1.200.4 24
quit
ospf 10 router-id 4.4.4.4
area 0
net 100.1.200.4 0.0.0.0
net 100.1.100.4 0.0.0.0
quit
silent-interface g0/0/1
quit
📝FW1
nat64 enable
nat64 prefix 3001:0:0:100:: 96
nat address-group 1
mode pat
section 1 100.1.11.100 100.1.11.110
nat address-group 2
mode pat
section 1 100.1.12.100 100.1.12.110
quit
nat-policy
rule name Nat64-1
source-zone trust
egress-interface g1/0/2
nat-type nat64
action source-nat address-group 1
quit
rule name Nat64-2
source-zone trust
egress-interface g1/0/3
nat-type nat64
action source-nat address-group 2
quit
quit
ip route-static 0.0.0.0 0 g1/0/2 100.1.11.2
ip route-static 0.0.0.0 0 g1/0/3 100.1.12.2
int g1/0/0
nat64 enable
int g1/0/1
nat64 enable
分部
📝FW2
ipv6
int g1/0/0
ip add 100.1.23.2 24
service-manage ping permit
quit
int g1/0/1
ipv6 enable
ipv6 address 2001:0:0:500::2 64
service-manage ping permit
quit
firewall zone trust
add interface g1/0/1
firewall zone trust
add interface g1/0/1
firewall zone untrust
add interface g1/0/0
quit
security-policy
default action permit
quit
ip route-static 0.0.0.0 0 g1/0/0 100.1.23.3
📝SW6
undo stp enable
以上是关于IPV6大型网络配置实战的主要内容,如果未能解决你的问题,请参考以下文章
云原生安全实战 | 银行如何基于 IPv6 完成 CDN 内置安全能力建设
solr分布式索引实战分片配置读取:工具类configUtil.java,读取配置代码片段,配置实例