Linux CA认证-http ssl实现
Posted 笨小孩@GF 知行合一
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Linux CA认证-http ssl实现相关的知识,希望对你有一定的参考价值。

- CA 概述:Certificate Authority 的缩写,通常翻译成认证权威或者认证中心,主要用途是为用户发放数字证书。
- CA 认证的流程和公安局派出所颁发身份证的流程大致一致
- 认证中心(CA)的功能有:证书发放、证书更新、证书撤销和证书验证。
- CA 证书作用:身份认证,实现数据的不可否认性。
- 回顾一下身份证的办理过程:
- 带上户口本(证明你合法)-》当地派出所(认证机构)-》签发证书(审核有效信息)-》去领证书
- 接下来回顾数字证书认证过程如下图:
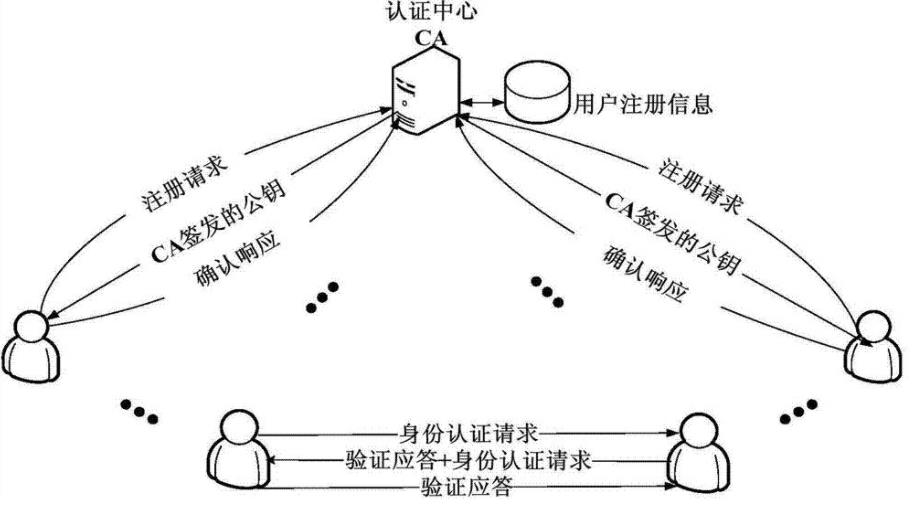
- 证书请求文件:CSR 是 Cerificate Signing Request 的英文缩写,即证书请求文件,也就是证书申请者在申请数字证书时由 CSP(加密服务提供者)在生成私钥的同时也生成证书请求文件,证书申请者只要把 CSR 文件提交给证书颁发机构后,证书颁发机构使用其根证书的私钥签名就生成了证书文件,也就是颁发给用户的证书。
- 总结:证书签名过程
1、 生成请求文件
2、 CA 确认申请者的身份真实性
3、 CA 使用根证书的私钥加密请求文件,生成证书
4、 把证书传给申请者 - 用户使用 CA 证书确认服务器身份过程
- 1、请求文件发给 CA 认证中心
2、CA 认证 (用 CA 的私钥加密请求文件), 得到加密后的文件,这个文件就是证书 ),CA 认证中心颁发加密后的数字证书
3、用户访问网站并向该网站索要数字证书
4、用户拿到数字证书后,用浏览器中 CA 的公钥解密证书,解开后得到公钥和标识(主机名,国家,省,组织等信息),从而确认身份。 - 申请收费证书
- https://buy.wosign.com
-
搭建 CA 认证中心
- 安装 CA 认证软件包中心:
- # rpm -qf `which openssl `

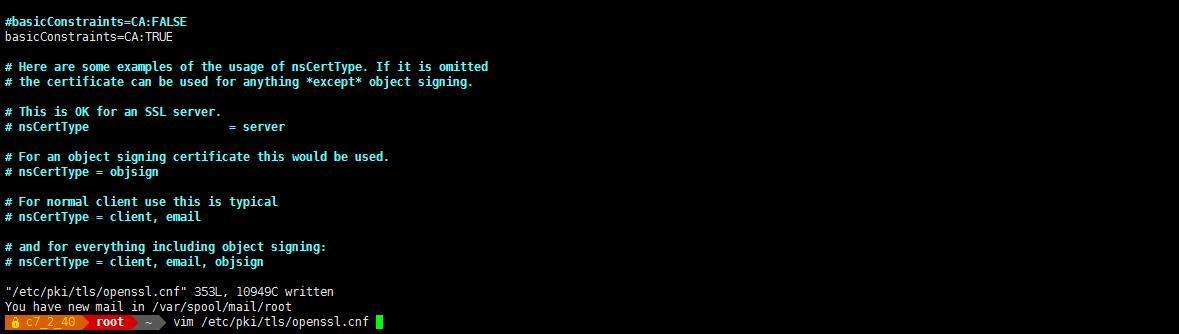
- 配置一个自己的 CA 认证中心。生成 CA 的根证书和私钥。 根证书中包括:CA 的公钥
# vim /etc/pki/tls/openssl.cnf
改:basicConstraints=CA:FALSE
为:basicConstraints=CA:TRUE #让自己成为 CA 认证中心
- 生成 CA 的公钥证书和私钥
- # /etc/pki/tls/misc/CA -h #查看帮助
usage: /etc/pki/tls/misc/CA -newcert|-newreq|-newreq-nodes|-newca|-sign|-verify
选项 :
-newcert 新证书
-newreq 新请求
-newreq-nodes 新请求节点
-newca 新的 CA 证书
-sign 签证
-verify 验证 - 1
-
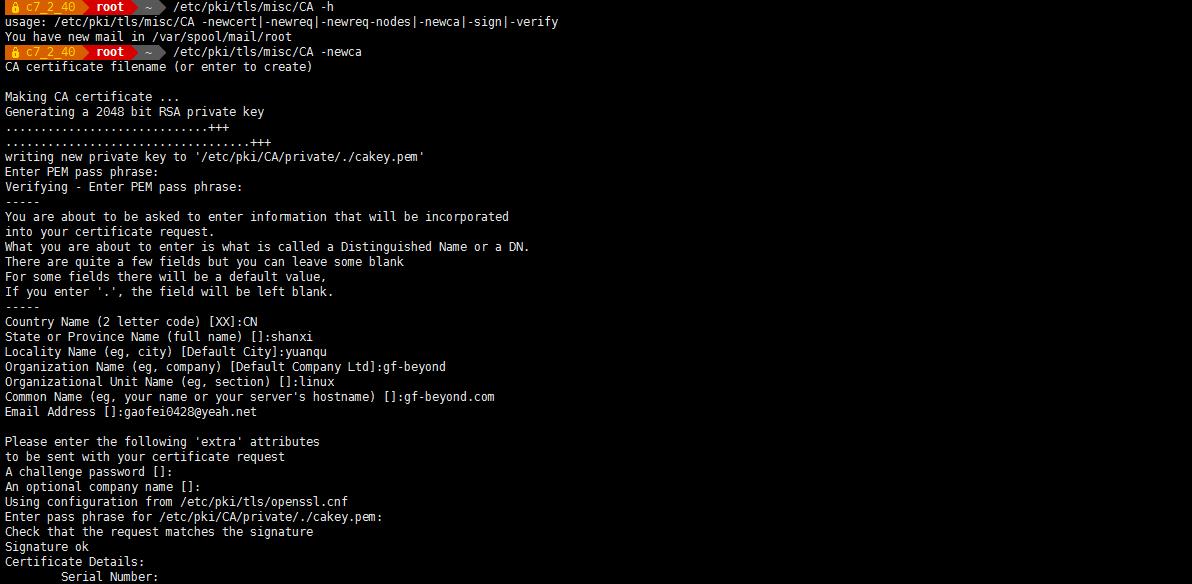
/etc/pki/tls/misc/CA -newca
CA certificate filename (or enter to create) #直接回车Making CA certificate ...
Generating a 2048 bit RSA private key
.............................+++
...................................+++
writing new private key to '/etc/pki/CA/private/./cakey.pem'
Enter PEM pass phrase: #输入密码,保护私钥。
Verifying - Enter PEM pass phrase: #确认密码
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:shanxi
Locality Name (eg, city) [Default City]:yuanqu
Organization Name (eg, company) [Default Company Ltd]:gf-beyond
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:gf-beyond.com #普通名称(例如,您的姓名或您的服务器的主机名),随便写. 指定 CA 认证中心服务器的名字
Email Address []:gaofei0428@yeah.netPlease enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []: #直接回车
An optional company name []: #直接回车
Using configuration from /etc/pki/tls/openssl.cnf # CA 服务器的配置文件。上面修改的内容会添加到这个配置文件中
Enter pass phrase for /etc/pki/CA/private/./cakey.pem: #输入刚才保护 CA私钥的密码
Check that the request matches the signature
Signature ok
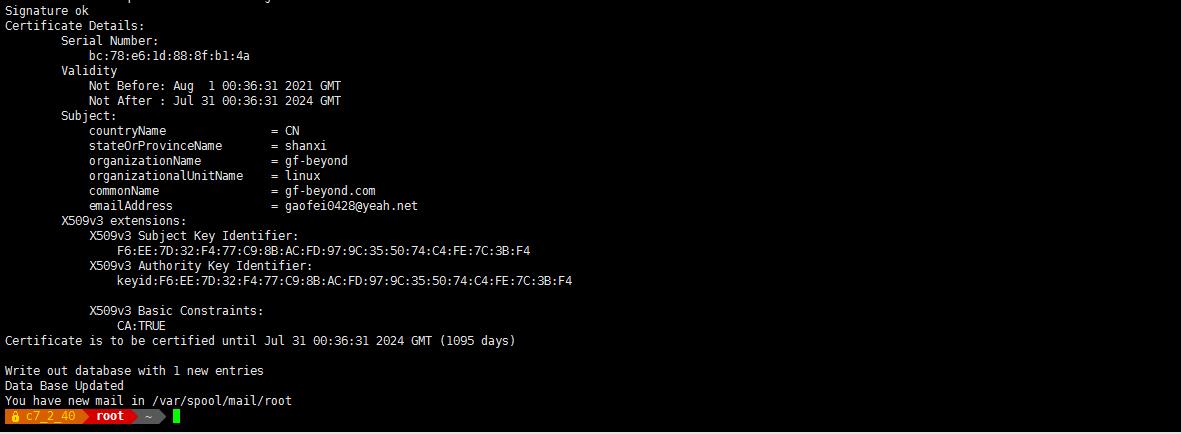
Certificate Details:
Serial Number:
bc:78:e6:1d:88:8f:b1:4a
Validity
Not Before: Aug 1 00:36:31 2021 GMT
Not After : Jul 31 00:36:31 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = shanxi
organizationName = gf-beyond
organizationalUnitName = linux
commonName = gf-beyond.com
emailAddress = gaofei0428@yeah.net
X509v3 extensions:
X509v3 Subject Key Identifier:
F6:EE:7D:32:F4:77:C9:8B:AC:FD:97:9C:35:50:74:C4:FE:7C:3B:F4
X509v3 Authority Key Identifier:
keyid:F6:EE:7D:32:F4:77:C9:8B:AC:FD:97:9C:35:50:74:C4:FE:7C:3B:F4X509v3 Basic Constraints:
CA:TRUE
Certificate is to be certified until Jul 31 00:36:31 2024 GMT (1095 days)Write out database with 1 new entries
Data Base Updated -
到此 CA 认证中心就搭建好了。
-
查看生成的 CA 根证书,根证书中包括 CA 公钥
-
cat /etc/pki/CA/cacert.pem
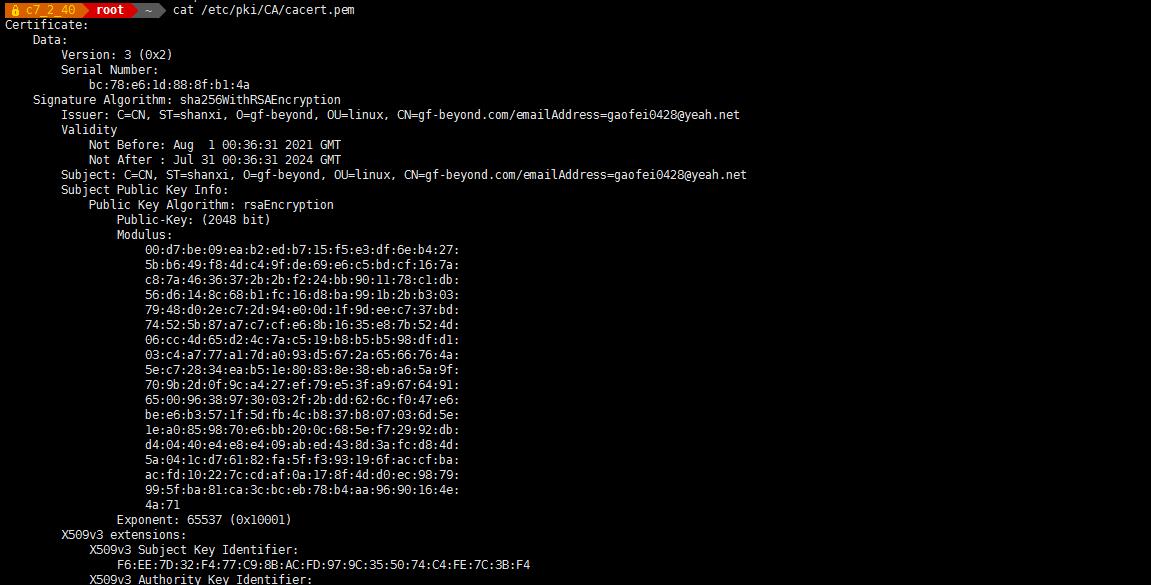
- cat /etc/pki/CA/cacert.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
bc:78:e6:1d:88:8f:b1:4a
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=shanxi, O=gf-beyond, OU=linux, CN=gf-beyond.com/emailAddress=gaofei0428@yeah.net #CA 机构信息
Validity
Not Before: Aug 1 00:36:31 2021 GMT
Not After : Jul 31 00:36:31 2024 GMT
Subject: C=CN, ST=shanxi, O=gf-beyond, OU=linux, CN=gf-beyond.com/emailAddress=gaofei0428@yeah.net
Subject Public Key Info: #CA 认证中心公钥信息
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit) - 查看根证书的私钥
# cat /etc/pki/CA/private/cakey.pem
- 在 Apache 上搭建 https
1、基于 apache 搭建 https 的整体流程如下:
(1)、在 192.168.2.41 上安装 httpd
(2)、192.168.2.41 生成证书请求文件,发给 192.168.2.40 CA 认证中心进行签名,192.168.2.40 下发证书给 192.168.2.41
(3)、把证书和 httpd 相结合,实现 https
(4)、测试 https 认证效果 -
在 192.168.2.41 上安装:httpd web 服务器
- # yum install httpd -y
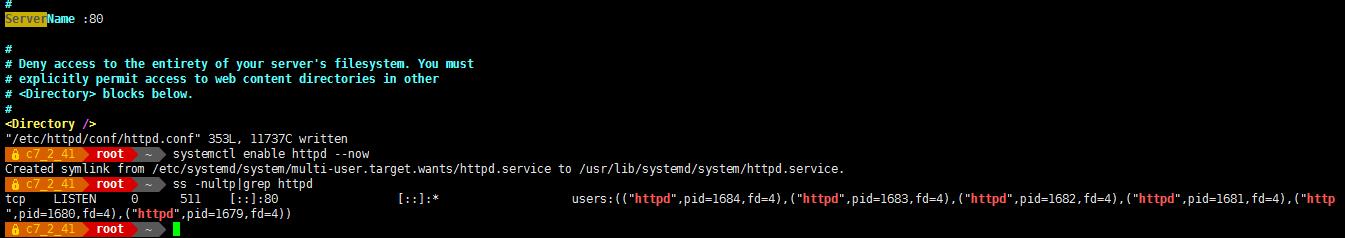
# vim /etc/httpd/conf/httpd.conf
改:95 #ServerName www.example.com:80 #指定 ServerName
为:95 ServerName :80
# systemctl start httpd
- 生成证书请求文件,获取证书
- 首先生成一个私钥密钥(此时还没有生成公钥):
# openssl genrsa -des3 -out /etc/httpd/conf.d/server.key
参数:-des3 encrypt the generated key with DES in ede cbc mode (168 bit key) #加密一下私钥
Generating RSA private key, 512 bit long modulus
.....++++++++++++
..............................++++++++++++
e is 65537 (0x10001)
Enter pass phrase for /etc/httpd/conf.d/server.key:123456 #输入保护私钥的密码,保护私 钥时,使用的加密算法是 -des3
Verifying - Enter pass phrase for /etc/httpd/conf.d/server.key: 123456 - 注: 有私钥可以推出来公钥,但是公钥不可以推出私钥。公钥由私钥生成
- 使用私钥生成证书请求文件
# openssl req -new -key /etc/httpd/conf.d/server.key -out /etc/httpd/conf.d/server.csrEnter pass phrase for /etc/httpd/conf.d/server.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:shanxi
Locality Name (eg, city) [Default City]:yuanqu
Organization Name (eg, company) [Default Company Ltd]:gf-beyond
Organizational Unit Name (eg, section) []:linux
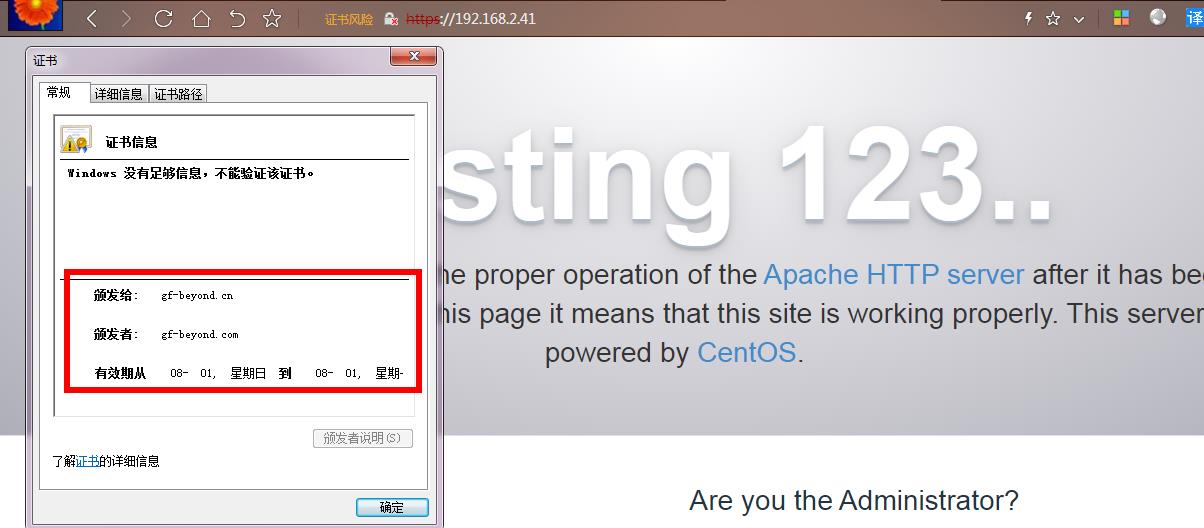
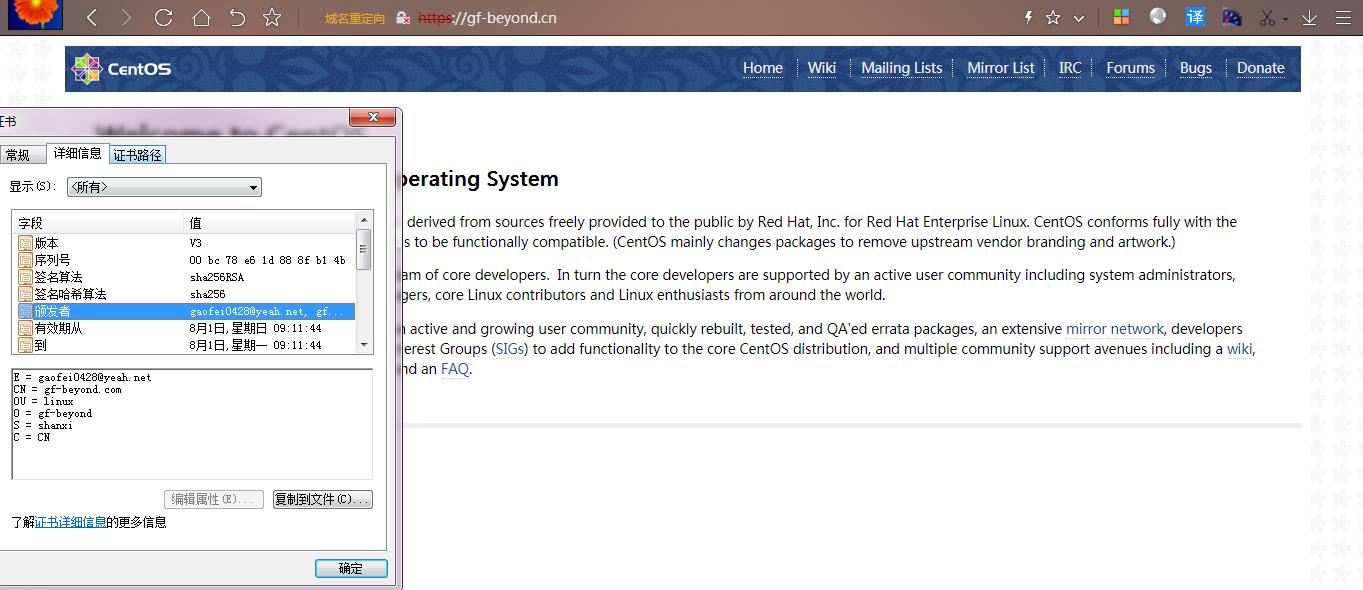
Common Name (eg, your name or your server's hostname) []:gf-beyond.cn #这里要求输入的 CommonName 必须与通过浏览器访问您网站的 URL 完全相同,否则用户会发现您服务器证书的通用名与站点的名字不匹配,用户就会怀疑您的证书的真实性。可以使域名也可以使用IP地址。
Email Address []:gaofei0428@yeah.netPlease enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []: - 将证书请求文件发给 CA 服务器:
- scp /etc/httpd/conf.d/server.csr root@192.168.2.40:/tmp/
-
在 192.168.2.40 上 CA 签名
-
# openssl ca -keyfile /etc/pki/CA/private/cakey.pem -cert /etc/pki/CA/cacert.pem -in /tmp/server.csr -out /opt/ca/server.crt
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for /etc/pki/CA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
bc:78:e6:1d:88:8f:b1:4b
Validity
Not Before: Aug 1 01:11:44 2021 GMT
Not After : Aug 1 01:11:44 2022 GMT
Subject:
countryName = CN
stateOrProvinceName = shanxi
organizationName = gf-beyond
organizationalUnitName = linux
commonName = gf-beyond.cn
emailAddress = gaofei0428@yeah.net
X509v3 extensions:
X509v3 Basic Constraints:
CA:TRUE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
68:9E:67:34:24:88:2B:68:F0:EC:19:73:4C:AC:0A:35:93:60:80:F9
X509v3 Authority Key Identifier:
keyid:F6:EE:7D:32:F4:77:C9:8B:AC:FD:97:9C:35:50:74:C4:FE:7C:3B:F4Certificate is to be certified until Aug 1 01:11:44 2022 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated -
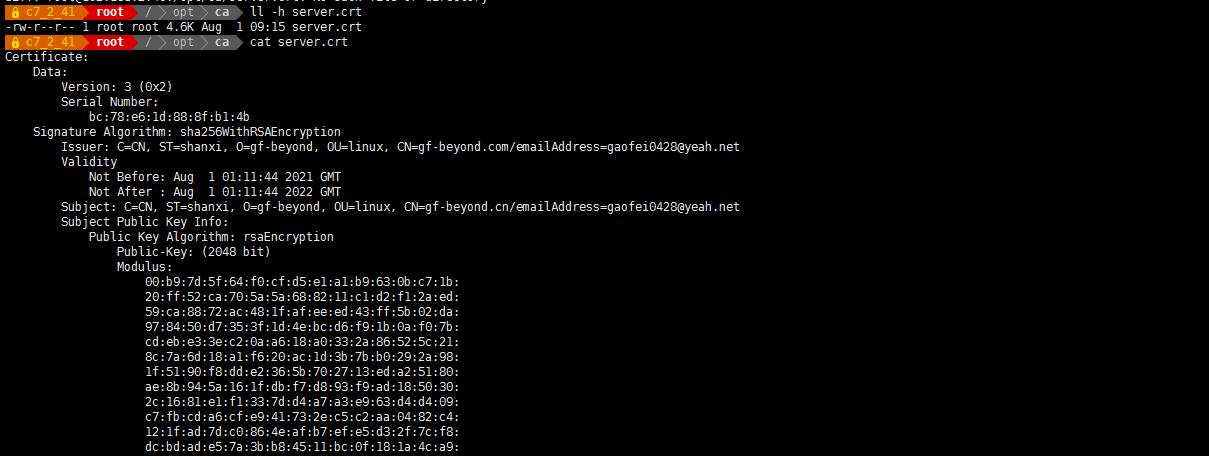
cat server.crt
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
bc:78:e6:1d:88:8f:b1:4b
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=shanxi, O=gf-beyond, OU=linux, CN=gf-beyond.com/emailAddress=gaofei0428@yeah.net
Validity
Not Before: Aug 1 01:11:44 2021 GMT
Not After : Aug 1 01:11:44 2022 GMT
Subject: C=CN, ST=shanxi, O=gf-beyond, OU=linux, CN=gf-beyond.cn/emailAddress=gaofei0428@yeah.net
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b9:7d:5f:64:f0:cf:d5:e1:a1:b9:63:0b:c7:1b:
20:ff:52:ca:70:5a:5a:68:82:11:c1:d2:f1:2a:ed:
59:ca:88:72:ac:48:1f:af:ee:ed:43:ff:5b:02:da:
97:84:50:d7:35:3f:1d:4e:bc:d6:f9:1b:0a:f0:7b:
cd:eb:e3:3e:c2:0a:a6:18:a0:33:2a:86:52:5c:21:
8c:7a:6d:18:a1:f6:20:ac:1d:3b:7b:b0:29:2a:98:
1f:51:90:f8:dd:e2:36:5b:70:27:13:ed:a2:51:80:
ae:8b:94:5a:16:1f:db:f7:d8:93:f9:ad:18:50:30:
2c:16:81:e1:f1:33:7d:d4:a7:a3:e9:63:d4:d4:09:
c7:fb:cd:a6:cf:e9:41:73:2e:c5:c2:aa:04:82:c4:
12:1f:ad:7d:c0:86:4e:af:b7:ef:e5:d3:2f:7c:f8:
dc:bd:ad:e5:7a:3b:b8:45:11:bc:0f:18:1a:4c:a9:
c0:82:62:03:9f:9c:ae:9e:5e:b6:b7:57:ec:3d:03:
66:19:71:53:93:7a:2e:c8:f7:db:88:6f:04:bd:30:
74:de:fe:17:79:33:22:a6:29:18:7a:07:68:f7:3d:
e7:87:31:06:29:ee:d2:6e:f9:bd:7a:e3:9e:5c:93:
ad:9f:fd:2c:e2:c3:93:8f:b3:fe:cb:bb:ca:49:56:
79:db
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:TRUE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
68:9E:67:34:24:88:2B:68:F0:EC:19:73:4C:AC:0A:35:93:60:80:F9
X509v3 Authority Key Identifier:
keyid:F6:EE:7D:32:F4:77:C9:8B:AC:FD:97:9C:35:50:74:C4:FE:7C:3B:F4Signature Algorithm: sha256WithRSAEncryption
9b:25:55:2f:33:c3:9c:a9:1d:53:d4:c3:38:04:ee:7c:8a:e1:
29:4c:b3:e3:f3:f8:73:a1:f6:60:58:3b:c5:d7:be:68:7c:80:
e8:64:97:e4:2c:e0:21:88:18:ce:8f:4e:c9:d2:0f:8c:fc:f5:
4a:48:b2:0e:51:c9:51:a5:73:92:09:21:8a:40:18:64:39:36:
3e:65:3f:92:78:7a:da:d1:4b:14:09:ab:5d:c8:31:91:a9:34:
b7:2b:1a:84:78:36:2b:5a:89:da:c3:12:a2:d2:e8:4c:88:a6:
03:f5:d0:81:bd:b4:76:4a:6b:f1:07:0a:68:9c:cb:6a:ec:c9:
9f:37:d1:7f:1e:27:67:11:e0:89:18:3b:c4:9d:df:ad:df:21:
21:52:01:48:2a:37:d3:a9:ec:c0:b0:e7:5e:22:8a:2c:17:06:
ea:5e:40:c8:36:e9:87:09:1e:f9:dc:2f:fd:82:2f:95:40:59:
6b:44:9d:23:ae:04:d3:7b:a8:71:92:a1:1c:8c:eb:ff:4f:78:
68:3f:33:f6:38:f6:c3:06:45:72:20:2a:41:4f:8e:97:51:bc:
f6:0a:33:c2:72:a0:0c:66:a9:c1:57:80:d5:25:2f:fb:fb:33:
fc:d0:b8:cd:56:54:c2:ba:98:aa:42:17:1d:44:dc:23:a9:6c:
55:37:cd:59
-----BEGIN CERTIFICATE-----
MIID/DCCAuSgAwIBAgIJALx45h2Ij7FLMA0GCSqGSIb3DQEBCwUAMH4xCzAJBgNV
BAYTAkNOMQ8wDQYDVQQIDAZzaGFueGkxEjAQBgNVBAoMCWdmLWJleW9uZDEOMAwG
A1UECwwFbGludXgxFjAUBgNVBAMMDWdmLWJleW9uZC5jb20xIjAgBgkqhkiG9w0B
CQEWE2dhb2ZlaTA0MjhAeWVhaC5uZXQwHhcNMjEwODAxMDExMTQ0WhcNMjIwODAx
MDExMTQ0WjB9MQswCQYDVQQGEwJDTjEPMA0GA1UECAwGc2hhbnhpMRIwEAYDVQQK
DAlnZi1iZXlvbmQxDjAMBgNVBAsMBWxpbnV4MRUwEwYDVQQDDAxnZi1iZXlvbmQu
Y24xIjAgBgkqhkiG9w0BCQEWE2dhb2ZlaTA0MjhAeWVhaC5uZXQwggEiMA0GCSqG
SIb3DQEBAQUAA4IBDwAwggEKAoIBAQC5fV9k8M/V4aG5YwvHGyD/UspwWlpoghHB
0vEq7VnKiHKsSB+v7u1D/1sC2peEUNc1Px1OvNb5Gwrwe83r4z7CCqYYoDMqhlJc
IYx6bRih9iCsHTt7sCkqmB9RkPjd4jZbcCcT7aJRgK6LlFoWH9v32JP5rRhQMCwW
geHxM33Up6PpY9TUCcf7zabP6UFzLsXCqgSCxBIfrX3Ahk6vt+/l0y98+Ny9reV6
O7hFEbwPGBpMqcCCYgOfnK6eXra3V+w9A2YZcVOTei7I99uIbwS9MHTe/hd5MyKm
KRh6B2j3PeeHMQYp7tJu+b16455ck62f/Sziw5OPs/7Lu8pJVnnbAgMBAAGjfjB8
MAwGA1UdEwQFMAMBAf8wLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVk
IENlcnRpZmljYXRlMB0GA1UdDgQWBBRonmc0JIgraPDsGXNMrAo1k2CA+TAfBgNV
HSMEGDAWgBT27n0y9HfJi6z9l5w1UHTE/nw79DANBgkqhkiG9w0BAQsFAAOCAQEA
myVVLzPDnKkdU9TDOATufIrhKUyz4/P4c6H2YFg7xde+aHyA6GSX5CzgIYgYzo9O
ydIPjPz1SkiyDlHJUaVzkgkhikAYZDk2PmU/knh62tFLFAmrXcgxkak0tysahHg2
K1qJ2sMSotLoTIimA/XQgb20dkpr8QcKaJzLauzJnzfRfx4nZxHgiRg7xJ3frd8h
IVIBSCo306nswLDnXiKKLBcG6l5AyDbphwke+dwv/YIvlUBZa0SdI64E03uocZKh
HIzr/094aD8z9jj2wwZFciAqQU+Ol1G89gozwnKgDGapwVeA1SUv+/sz/NC4zVZU
wrqYqkIXHUTcI6lsVTfNWQ==
-----END CERTIFICATE----- -
将证书复制到 192.168.2.41
-
scp server.crt root@192.168.2.41:/opt/ca
- 使用证书实现 https
- SSL 四次握手实现安全传输数据
- SSL 概述:(Secure Socket Layer)安全套接字层,通过一种机制在互联网上提供密钥传输。
其主要目标是保证两个应用间通信数据的保密性和可靠性,可在服务器端和用户端同时支持的一种加密算法。目前主流版本 SSLV2、SSLV3(常用)。
注:SSL作用,可以让你在一个不安全的公网环境中,安全传输你的密钥。 - SSL 应用情景:
- 存在安全隐患: 客户端和服务器之间传输数据时,如果何保证数据的安全? 加密!
问题:这个密码如何在不安全的公网环境中,安全的传输给你? - SSL 四次握手安全传输流程如下:
C(client 客户端) ------------------------------> S(server 服务端)
(1)、 客户端请求一个安全的会话,协商加密算法
C <------------------------------------------------- S
(2)、服务端将自己的证书传给客户端
C -------------------------------------------------> S
(3)、客户端用浏览中存放CA的根证书检测192.168.2.41证书,确认是要访问的网站。
客户端使用CA根证书中的公钥解密192.168.2.41的证书,从而得到192.168.2.41的公钥;
然后客户端生成一把对称的加密密钥,用192.168.2.41的公钥加密这个对称加密的密钥发给192.168.2.41。 后期使用对称密钥加密数据
C <------------------------------------------------> S
(4)、192.168.2.41使用私钥解密,得到对称加密的密钥。从而,使用对称加密密钥来进行安全快速传输数据。这里使用对称加密数据,是因为对称加密和解密速度快 - 总结 SSL 四次握手流程整体分两个过程:
过程 1: 确认身份;过程 2:生成一把对称加密密钥,传输数据。 - 在 192.168.2.41上配置 HTTPS web 服务器
安装 SSL 模块 - yum install mod_ssl -y
- 配置 apache 加载证书文件
- 查看私钥

- vim /etc/httpd/conf.d/ssl.conf
改:100 SSLCertificateFile /etc/pki/tls/certs/localhost.crt
为:100 SSLCertificateFile /etc/httpd/conf.d/server.crt
改:107 SSLCertificateKeyFile /etc/pki/tls/private/localhost.key
为:107 SSLCertificateKeyFile /etc/httpd/conf.d/server.key
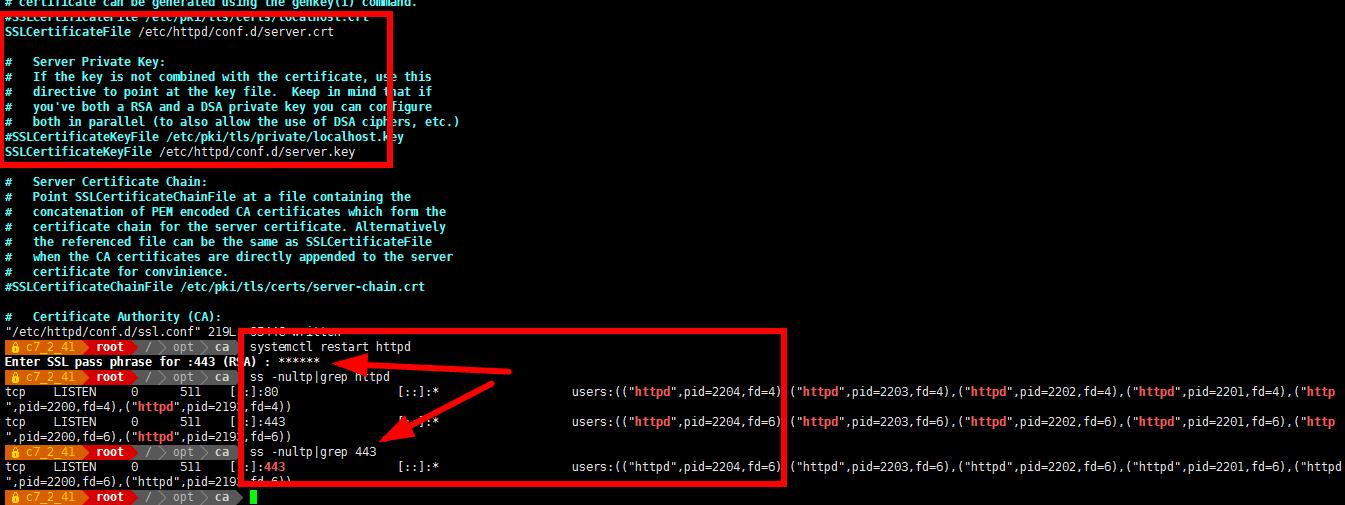
- systemctl restart httpd
Enter SSL pass phrase for :443 (RSA) : ****** #httpd 私钥密码 - 查看 443 端口
- ss -nultp|grep 443
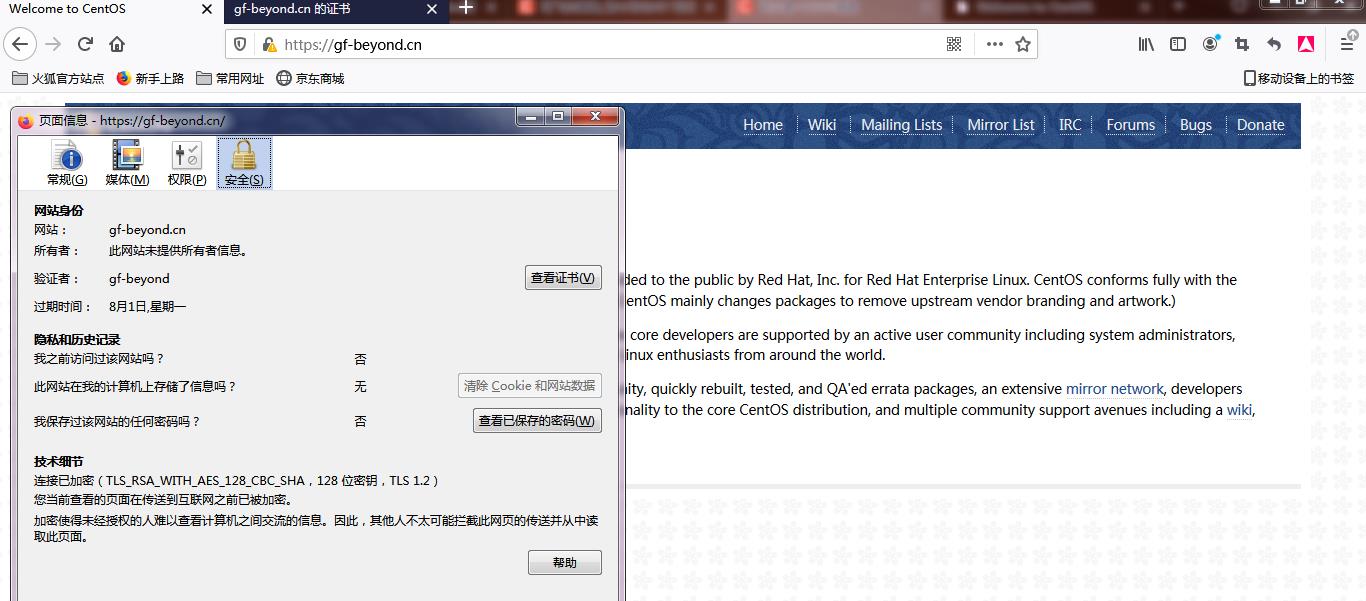
tcp LISTEN 0 511 [::]:443 [::]:* users:(("httpd",pid=2204,fd=6),("httpd",pid=2203,fd=6),("httpd",pid=2202,fd=6),("httpd",pid=2201,fd=6),("httpd",pid=2200,fd=6),("httpd",pid=2193,fd=6)) - 打开浏览器访问 https://192.168.2.41
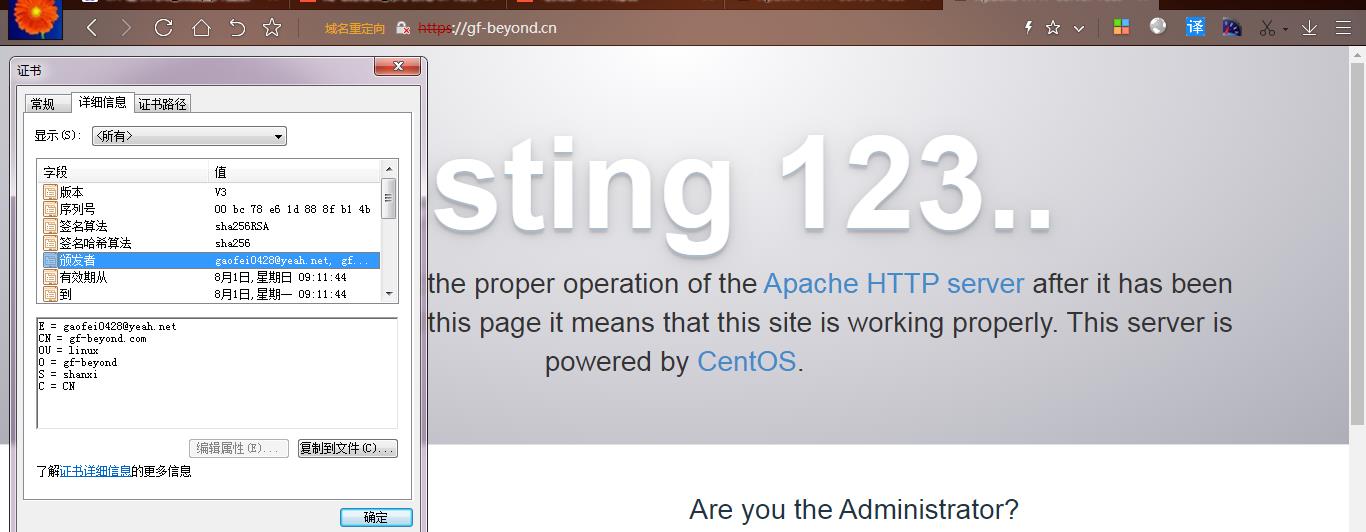
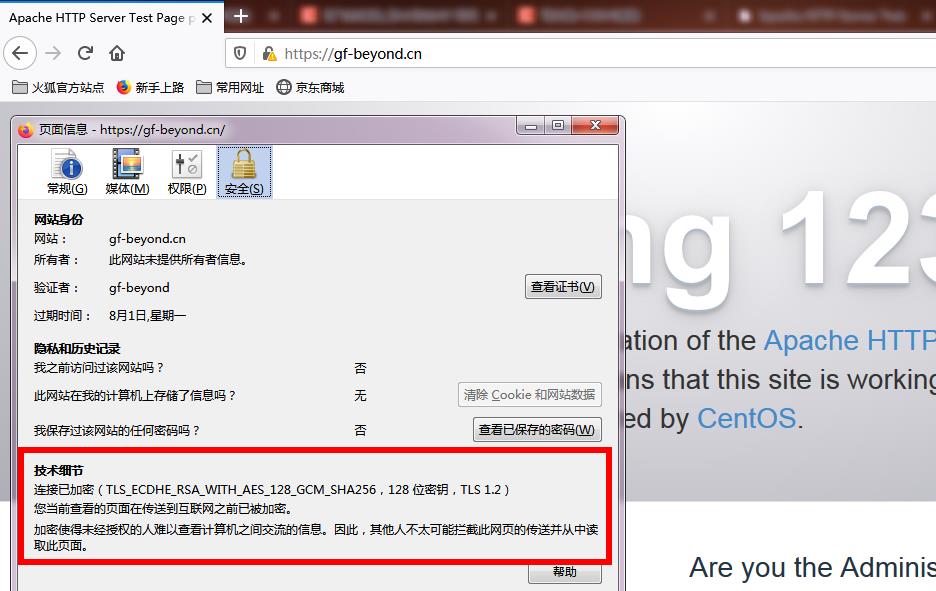
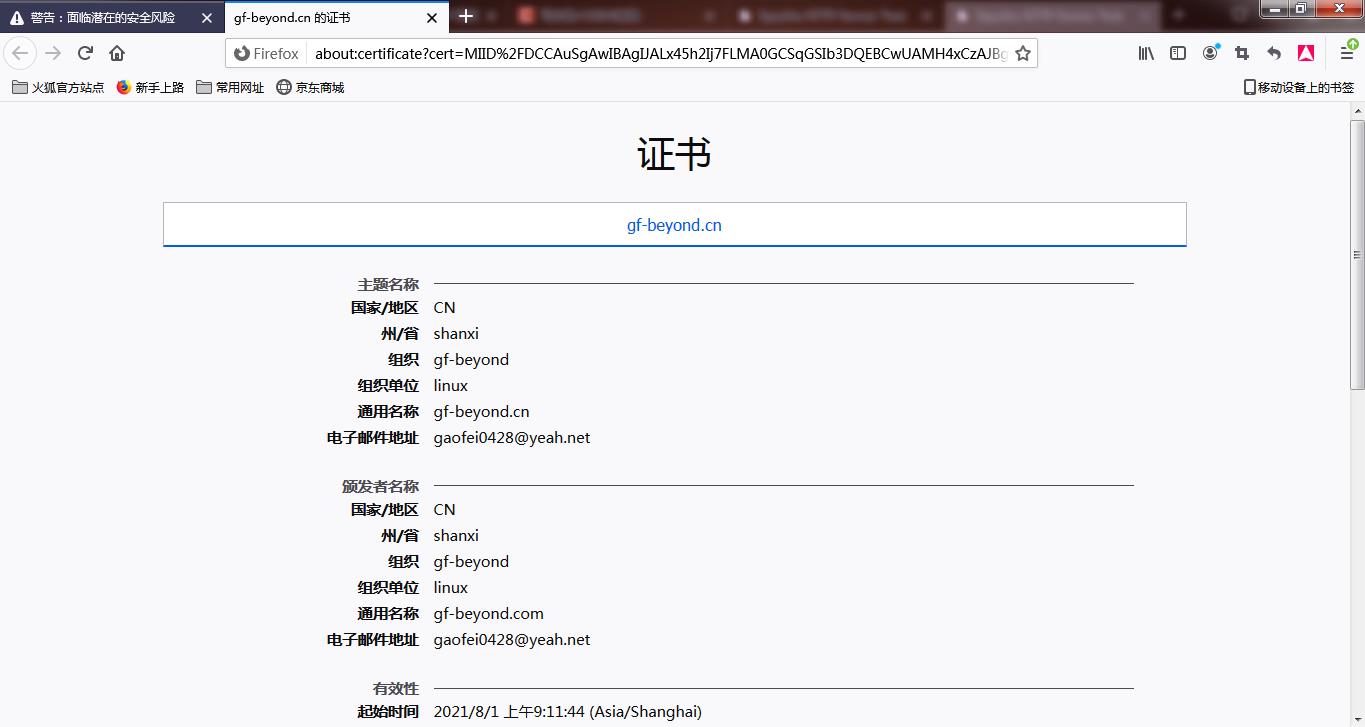
-
使用 nginx 实现 https
- 在 192.168.2.41 上安装启动 nginx
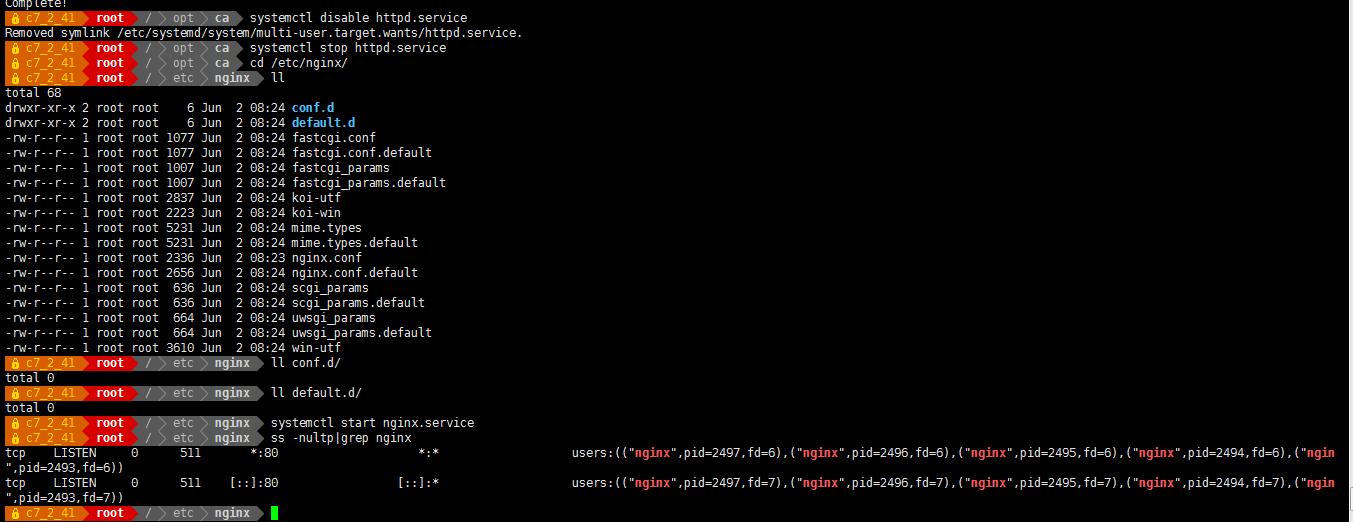
- 配置 Nginx 实现 https
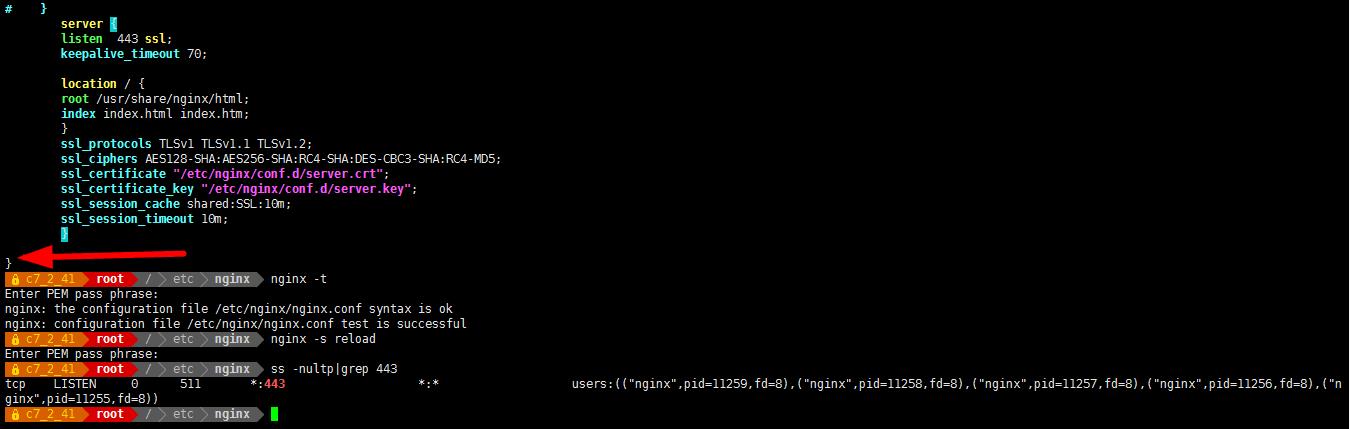
- vim /etc/nginx/nginx.conf #在最后 } 前添加上以下内容
................
server {
listen 443 ssl;
keepalive_timeout 70;
location / {
root /usr/share/nginx/html;
index index.html index.htm;
}
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers AES128-SHA:AES256-SHA:RC4-SHA:DES-CBC3-SHA:RC4-MD5;
ssl_certificate /etc/nginx/conf.d/server.crt;
ssl_certificate_key /etc/nginx/conf.d/server.key;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
}
} - \\cp /etc/httpd/conf.d/server.* /etc/nginx/conf.d/
- nginx -t
Enter PEM pass phrase:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
nginx -s reload
以上是关于Linux CA认证-http ssl实现的主要内容,如果未能解决你的问题,请参考以下文章