k8sgress部署加密认证重写
Posted dezasseis
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了k8sgress部署加密认证重写相关的知识,希望对你有一定的参考价值。
一、Ingress简介
-
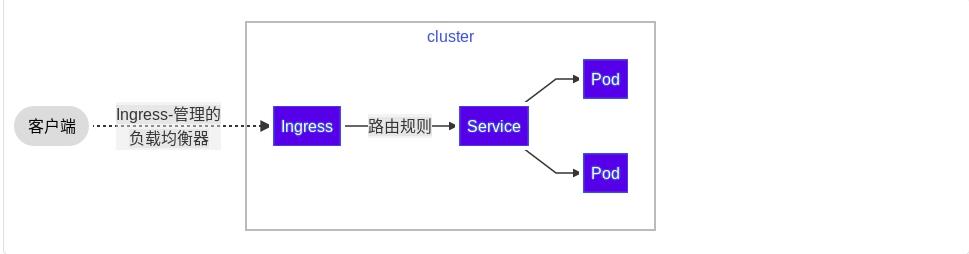
Ingress 公开了从集群外部到集群内服务的 HTTP 和 HTTPS 路由。 流量路由由 Ingress 资源上定义的规则控制。
-
可以将 Ingress 配置为服务提供外部可访问的 URL、负载均衡流量、终止 SSL/TLS,以及提供基于名称的虚拟主机等能力。Ingress 控制器 通常负责通过负载均衡器来实现 Ingress,尽管它也可以配置边缘路由器或其他前端来帮助处理流量。
-
Ingress 不会公开任意端口或协议。 将 HTTP 和 HTTPS 以外的服务公开到 Internet 时,通常使用
Service.Type=NodePort 或 Service.Type=LoadBalancer 类型的服务。
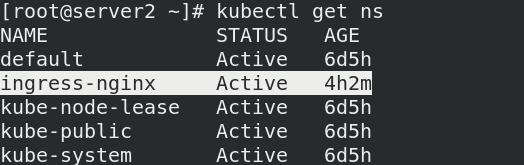
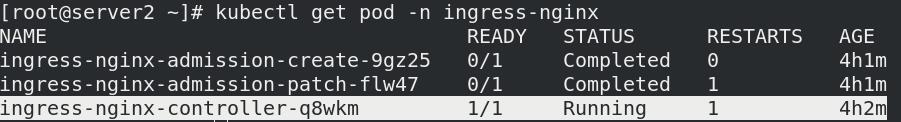
二、部署Ingress
- 为避免与上述实验冲突,需做以下注释
vim demo.yml
#clusterIP: None
#type: LoadBalancer
#externalIPs:
#- 192.168.100.200
kubectl apply -f demo.yml
- demploy.yml 文件
/root/ingress/deploy.yml
官方的文档 deploy.yml
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v0.44.0/deploy/static/provider/cloud/deploy.yaml
- 镜像
镜像1:nginx-ingress-controller:0.33.0
镜像2:kube-webhook-certgen:v1.2.0)
- 部署
kubectl apply -f ingress/deploy.yaml
三、创建Ingress
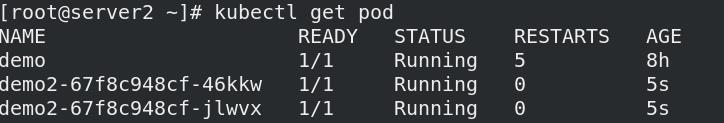
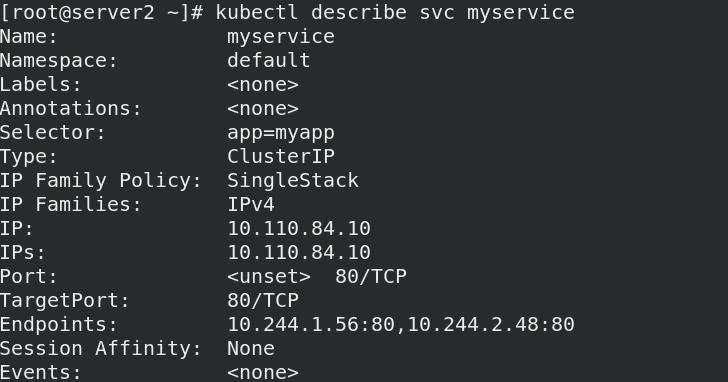
- 创建两个服务:myservice与nginx-svc
vim demo.yml
---
apiVersion: v1
kind: Service
metadata:
name: myservice
spec:
selector:
app: myapp
ports:
- protocol: TCP
port: 80
targetPort: 80
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: demo2
spec:
replicas: 2
selector:
matchLabels:
app: myapp
template:
metadata:
labels:
app: myapp
spec:
containers:
- name: myapp
image: myapp:v2
vim nginx-svc
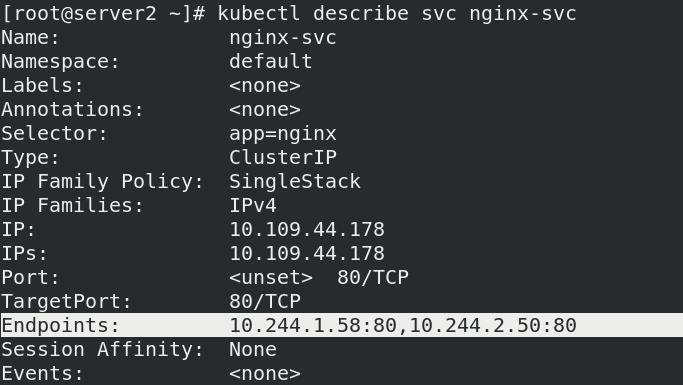
---
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
selector:
app: nginx
ports:
- protocol: TCP
port: 80
targetPort: 80
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: deployment
spec:
replicas: 2
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: myapp
image: myapp:v1
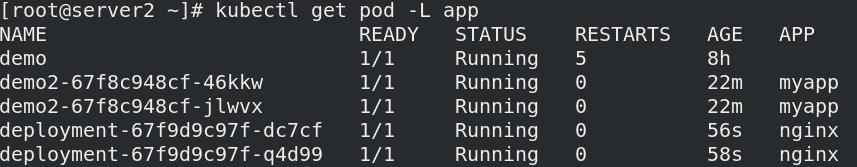
01_创建
vim ingress/nginx.yml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-demo
spec:
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: myservice
servicePort: 80
- host: www2.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
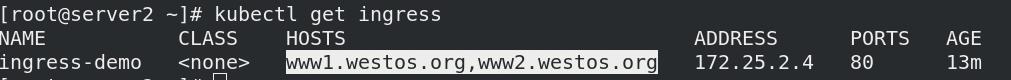
kubectl apply -f ingress/nginx.yml
- 宿主机作解析
vim /etc/hosts
172.25.2.4 server4 www1.westos.org www2.westos.org
- 负载均衡
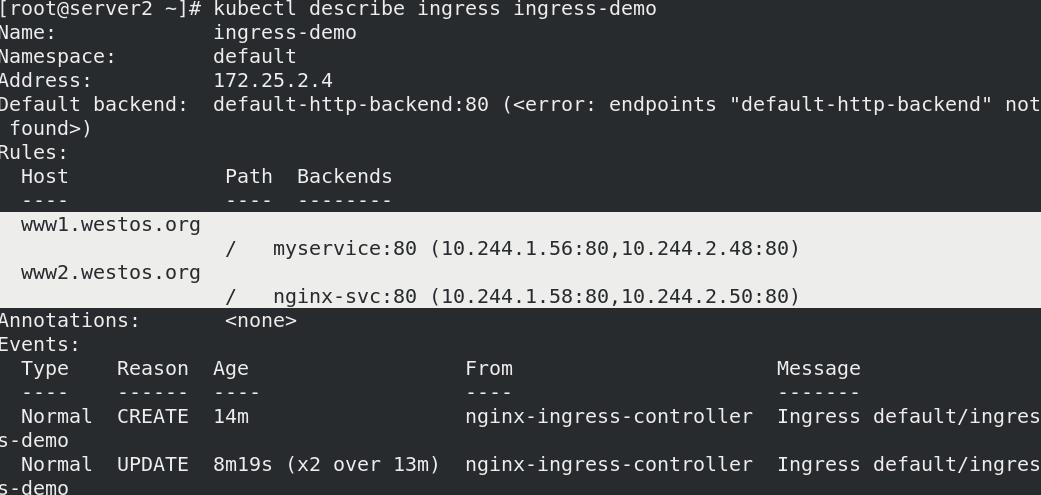
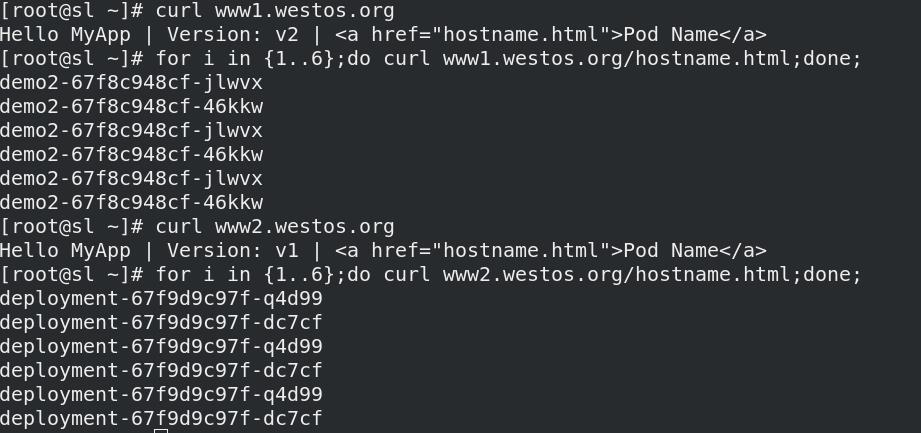
02_加密
cd ingress/openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=nginxsvc/O=nginxsvc"生成tls密钥和tls证书并签名kubectl create secret tls tls-secret --key tls.key --cert tls.crt创建一个tls secret,命名为:tls-secret
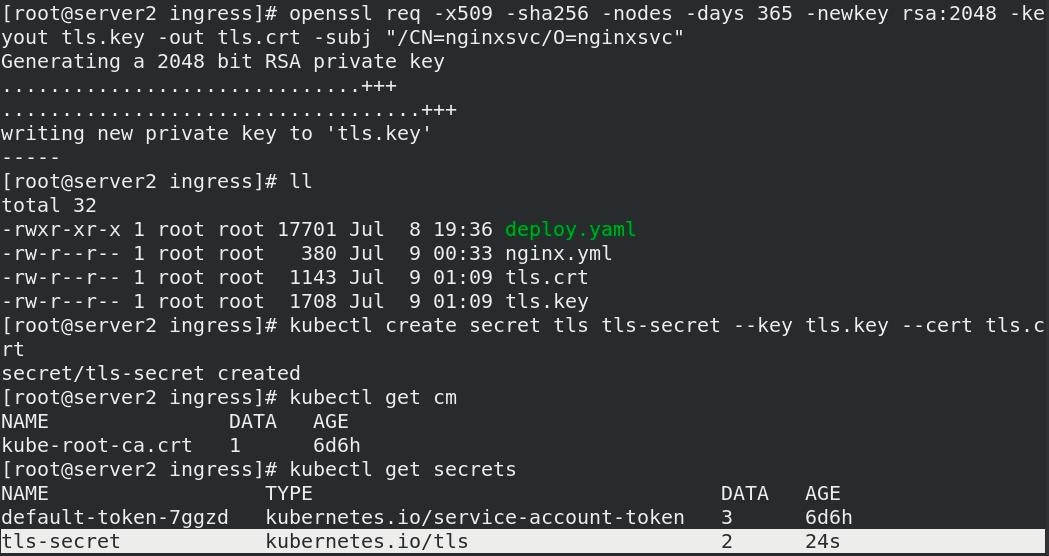
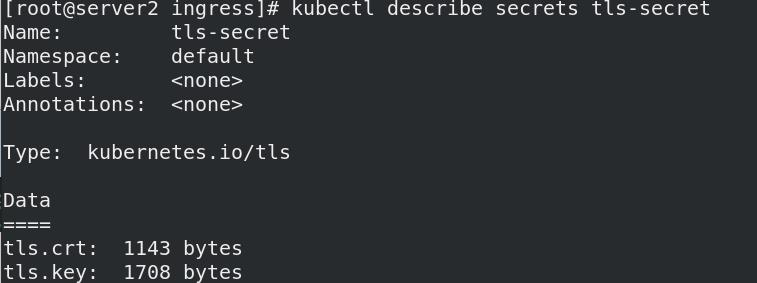
- 创建加密Ingress: www1加密,www2不加密
vim nginx.yml
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-demo
spec:
tls:
- hosts: #加密列表主机
- www1.westos.org
secretName: tls-secret #secret名字
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: myservice
servicePort: 80
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-demo2
spec:
rules:
- host: www2.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
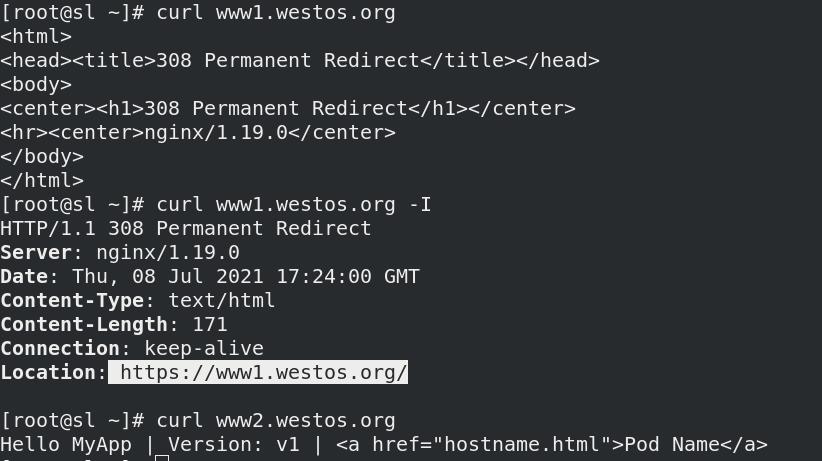
- www1加密
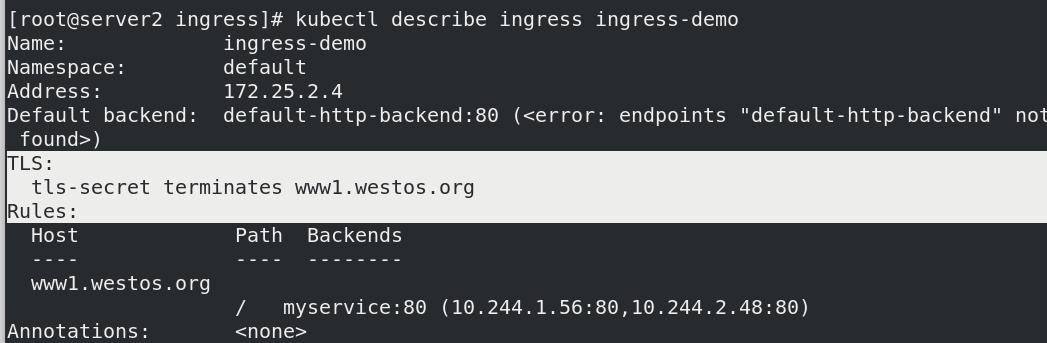
- www2不加密,无TLS
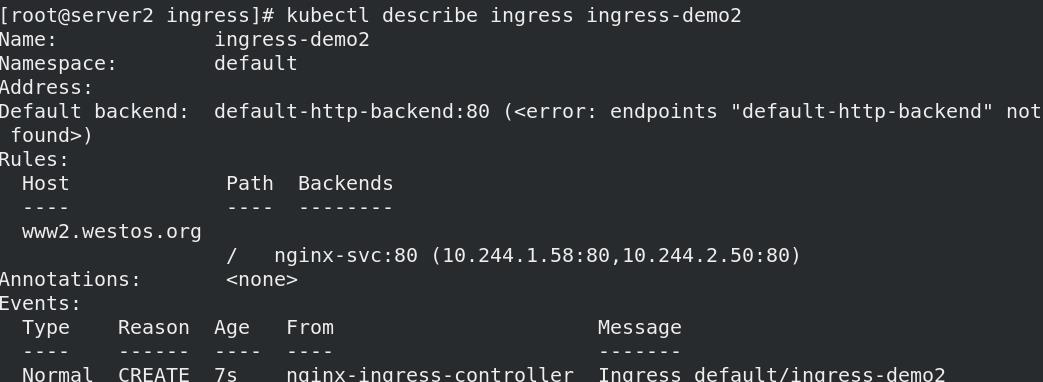
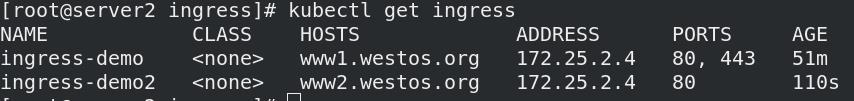
测试:
03_认证
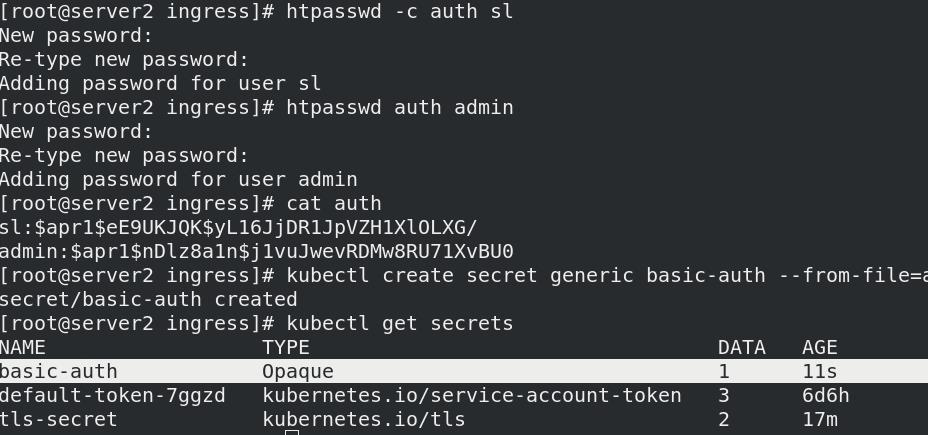
yum install -y httpd-tools安装httpd-tools- 添加身份验证: sl与admin
htpasswd -c auth sl:首次添加要使用-c
htpasswd auth admin- 创建基本验证: 命名为 basic-auth
kubectl create secret generic basic-auth --from-file=auth
- 创建需验证的Ingress: 设置www1验证用户sl,www2无需验证
vim nginx.yml
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-demo
annotations:
#认证类型
nginx.ingress.kubernetes.io/auth-type: basic
#包含用户/密码定义的验证名称:创建时定义的是basic-auth
nginx.ingress.kubernetes.io/auth-secret: basic-auth
#可验证的用户
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - sdsnzy'
spec:
tls:
- hosts:
- www1.westos.org
secretName: tls-secret
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: myservice
servicePort: 80
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-demo2
spec:
rules:
- host: www2.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
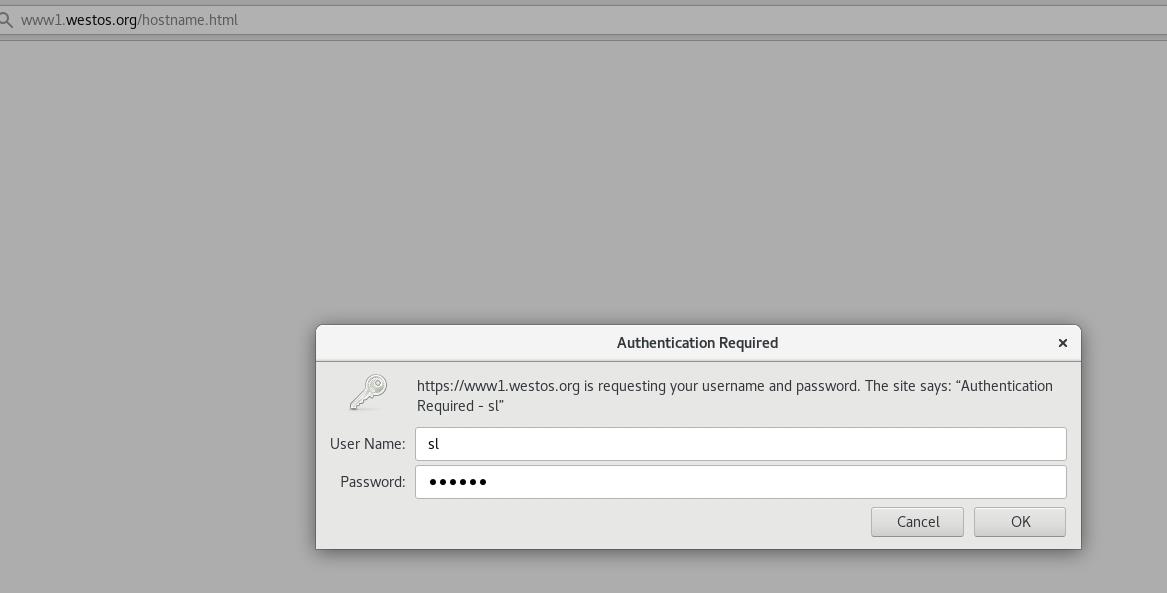
- 测试: 访问: www1.westos.org,需要验证通过才能访问
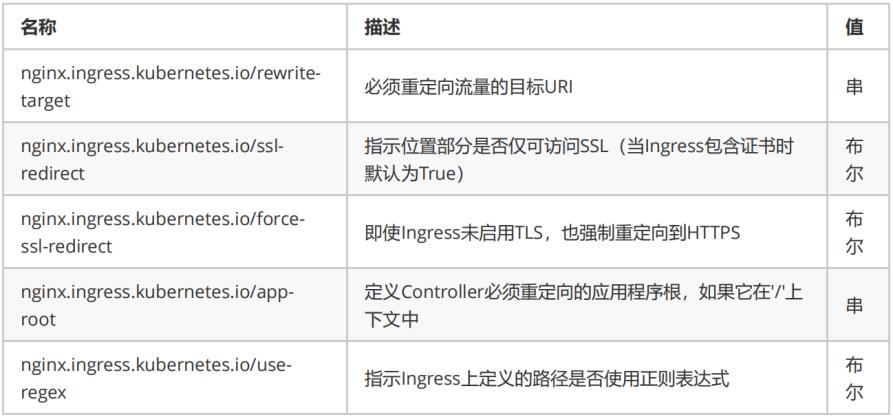
04_重写(rewrite-target)
annotations参数
- 创建重写URL规则的Ingress
vim nginx.yml
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-demo
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - sl'
spec:
tls:
- hosts:
- www1.westos.org
secretName: tls-secret
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: myservice
servicePort: 80
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-demo2
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /hostname.html
spec:
rules:
- host: www2.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
- 测试: 现在访问 www2.westos.org 相当于访问 www2.westos.org/hostname.html
未重定向访问
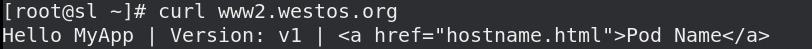
重定向访问
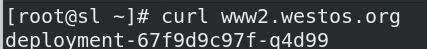
05_重写(app root)
创建app root规则的Ingress: 捕获的任何字符(.*)都将分配给占位符$2,然后将其用作rewrite-target注释中的参数。(本例设置为/westos)
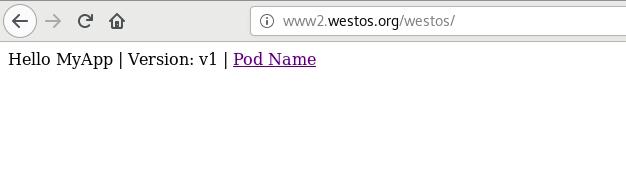
- 访问www2.westos.org/westos 重写为 www2.westos.org/
- 访问www2.westos.org/westos/ 重写为 www2.westos.org/
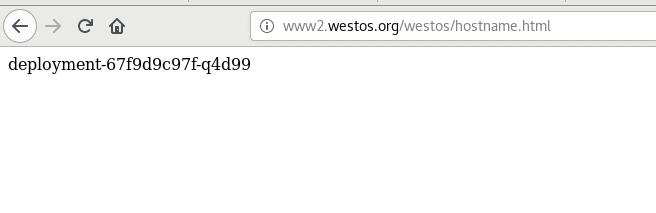
- 访问www2.westos.org/westos/XXX 重写为 www2.westos.org/XXX
vim nginx.html
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-demo
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - sl'
spec:
tls:
- hosts:
- www1.westos.org
secretName: tls-secret
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: myservice
servicePort: 80
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-demo2
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /$2
spec:
rules:
- host: www2.westos.org
http:
paths:
- backend:
serviceName: nginx-svc
servicePort: 80
path: /westos(/|$)(.*)
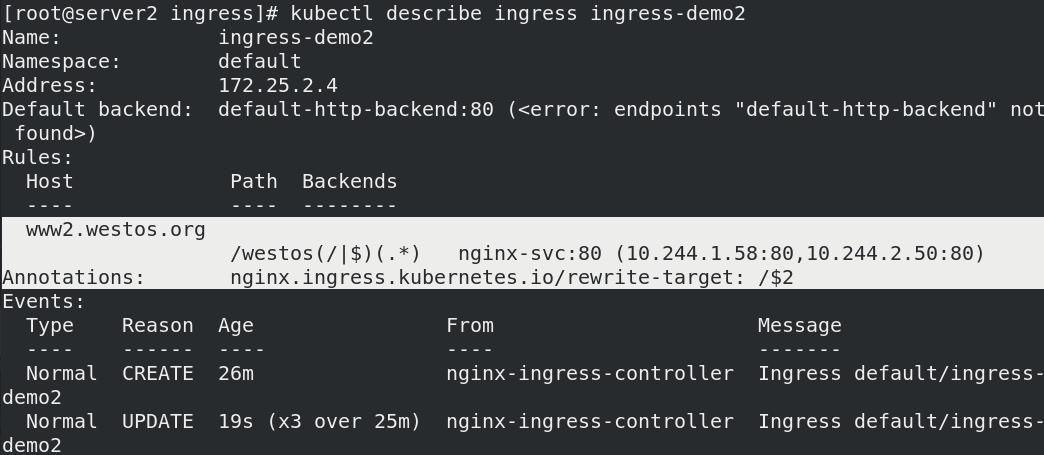
测试:
以上是关于k8sgress部署加密认证重写的主要内容,如果未能解决你的问题,请参考以下文章