Ethical Hacking - GAINING ACCESS(18)
Posted 一蓑烟雨
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Ethical Hacking - GAINING ACCESS(18)相关的知识,希望对你有一定的参考价值。
CLIENT SIDE ATTACKS
Backdooring ANY file
- Combine backdoor with any file - Generic solution.
- Users are more likely to run a pdf, image or audio file than an executable.
- Works well with social engineering.
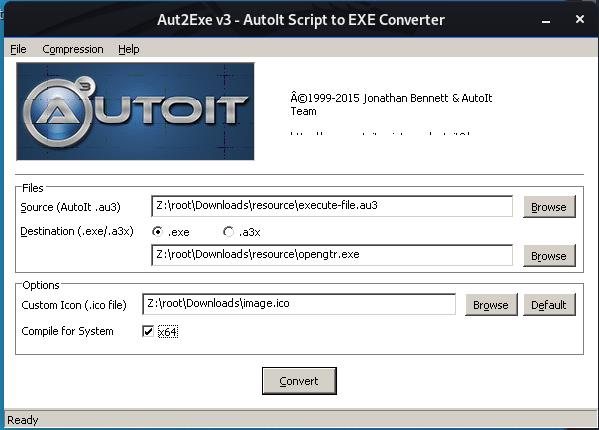
To convert the original(pdf, jpg, mp3) file to an exe, then combine it with a backdoor using veil.
Step 1:
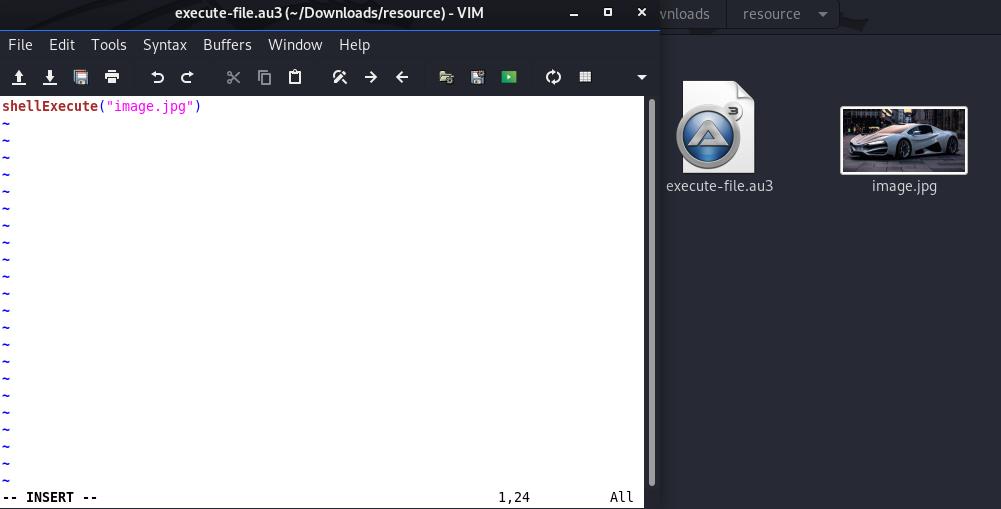
Step 2:
以上是关于Ethical Hacking - GAINING ACCESS(18)的主要内容,如果未能解决你的问题,请参考以下文章