modSecurity规则学习——防止SQL注入
Posted 897807300
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了modSecurity规则学习——防止SQL注入相关的知识,希望对你有一定的参考价值。
1、数字型SQL注入

/opt/waf/owasp-modsecurity-crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "17"] [id "942100"]
被LibInjection Check
2、字符型SQL注入
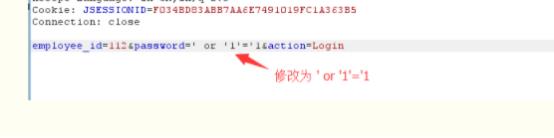
同上
3、数据库后门
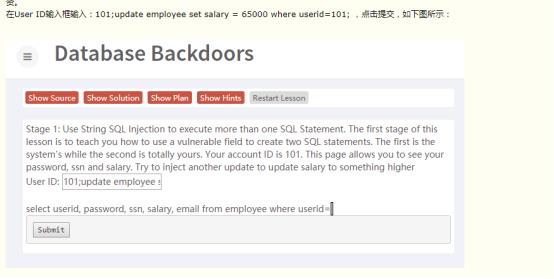
match1:LibInjection Check
match2: 94235
SecRule REQUEST_COOKIES|!REQUEST_COOKIES:/__utm/|REQUEST_COOKIES_NAMES|ARGS_NAMES|ARGS|XML:/* "(?i:(?:create\\s+function\\s+.+\\s+returns)|(?:;\\s*?(?:select|create|rename|truncate|load|alter|delete|update|insert|desc)\\s*?[\\[(]?\\w{2,}))" \\
高危
match3:REQUEST_COOKIES|!REQUEST_COOKIES:/__utm/|REQUEST_COOKIES_NAMES|ARGS_NAMES|ARGS|XML:/* "(?i:(?:[\\d\\W]\\s+as\\s*?[\\"\'`\\w]+\\s*?from)|(?:^[\\W\\d]+\\s*?(?:union|select|create|rename|truncate|load|alter|delete|update|insert|desc)\\b)|(?:(?:select|create|rename|truncate|load|alter|delete|update|insert|desc)\\s+(?:(?:group_)concat|char|load_file)\\s?\\(?)|(?:end\\s*?\\);)|([\\"\'`]\\s+regexp\\W)|(?:[\\s(]load_file\\s*?\\())" \\
sql正则汇总:
|
级别 |
描述 |
方法/正则 |
|
高危 |
SQL Injection Attack Detected via libinjection |
@detectSQLi libinjection参考 https://github.com/client9/libinjection |
|
高危 |
SQL Injection Attack: Common DB Names Detected |
(?i:\\b(?:m(?:s(?:ysaccessobjects|ysaces|ysobjects|ysqueries|ysrelationships|ysaccessstorage|ysaccessxml|ysmodules|ysmodules2|db)|aster\\.\\.sysdatabases|ysql\\.db)\\b|s(?:ys(?:\\.database_name|aux)\\b|chema(?:\\W*\\(|_name\\b)|qlite(_temp)?_master\\b)|d(?:atabas|b_nam)e\\W*\\(|information_schema\\b|pg_(catalog|toast)\\b|northwind\\b|tempdb\\b))" \\
|
|
高危 |
Detects blind sqli tests using sleep() or benchmark() |
"(?i:(sleep\\((\\s*?)(\\d*?)(\\s*?)\\)|benchmark\\((.*?)\\,(.*?)\\)))" \\ |
|
高危 |
Detects MSSQL code execution and information gathering attempts |
"(?i:(?:\\s*?(?:exec|execute).*?(?:\\W)xp_cmdshell)|(?:[\\"\'`]\\s*?!\\s*?[\\"\'`\\w])|(?:from\\W+information_schema\\W)|(?:(?:(?:current_)?user|database|schema|connection_id)\\s*?\\([^\\)]*?)|(?:[\\"\'`];?\\s*?(?:select|union|having)\\b\\s*?[^\\s])|(?:\\wiif\\s*?\\()|(?:(?:exec|execute)\\s+master\\.)|(?:union select @)|(?:union[\\w(\\s]*?select)|(?:select.*?\\w?user\\()|(?:into[\\s+]+(?:dump|out)file\\s*?[\\"\'`]))" \\ |
|
高危 |
Looking for integer overflow attacks, these are taken from skipfish, except 3.0.00738585072007e-308 is the \\"magic number\\" crash\', |
(?i:(?:^(-0000023456|4294967295|4294967296|2147483648|2147483647|0000012345|-2147483648|-2147483649|0000023456|3.0.00738585072007e-308|1e309)$))" \\ |
|
高危 |
Detects mysql charset switch and MSSQL DoS attempts |
"(?i:(?:alter\\s*?\\w+.*?(?:character|char)\\s+set\\s+\\w+)|([\\"\'`];*?\\s*?waitfor\\s+(?:time|delay)\\s+[\\"\'`])|(?:[\\"\'`];.*?:\\s*?goto))" \\ |
|
高危 |
Detects MATCH AGAINST, MERGE and EXECUTE IMMEDIATE injections |
(?i:(?:merge.*?using\\s*?\\()|(execute\\s*?immediate\\s*?[\\"\'`])|(?:match\\s*?[\\w(),+-]+\\s*?against\\s*?\\()) |
|
高危 |
Looking for basic sql injection. Common attack string for mysql, oracle and others. |
(?i:(?:(union(.*?)select(.*?)from)))" \\ |
|
高危 |
Detects Postgres pg_sleep injection, waitfor delay attacks and database shutdown attempts |
"(?i:(?:select\\s*?pg_sleep)|(?:waitfor\\s*?delay\\s?[\\"\'`]+\\s?\\d)|(?:;\\s*?shutdown\\s*?(?:;|--|#|\\/\\*|{)))" |
|
高危 |
Finds basic MongoDB SQL injection attempts |
(?i:(?:\\[\\$(?:ne|eq|lte?|gte?|n?in|mod|all|size|exists|type|slice|x?or|div|like|between|and)\\])) |
|
高危 |
Detects MySQL and PostgreSQL stored procedure/function injections |
(?i:(?:procedure\\s+analyse\\s*?\\()|(?:;\\s*?(declare|open)\\s+[\\w-]+)|(?:create\\s+(procedure|function)\\s*?\\w+\\s*?\\(\\s*?\\)\\s*?-)|(?:declare[^\\w]+[@#]\\s*?\\w+)|(exec\\s*?\\(\\s*?@))" \\ |
|
高危 |
Detects MySQL UDF injection and other data/structure manipulation attempts |
(?i:(?:create\\s+function\\s+.+\\s+returns)|(?:;\\s*?(?:select|create|rename|truncate|load|alter|delete|update|insert|desc)\\s*?[\\[(]?\\w{2,})) |
|
高危 |
Detects concatenated basic SQL injection and SQLLFI attempts |
(?i:(?:[\\d\\W]\\s+as\\s*?[\\"\'`\\w]+\\s*?from)|(?:^[\\W\\d]+\\s*?(?:union|select|create|rename|truncate|load|alter|delete|update|insert|desc)\\b)|(?:(?:select|create|rename|truncate|load|alter|delete|update|insert|desc)\\s+(?:(?:group_)concat|char|load_file)\\s?\\(?)|(?:end\\s*?\\);)|([\\"\'`]\\s+regexp\\W)|(?:[\\s(]load_file\\s*?\\()) |
|
警告 |
SQL Injection Attack: Common Injection Testing Detected |
(^[\\"\'`;]+|[\\"\'`]+$) |
|
高危 |
SQL Injection Attack: SQL Operator Detected |
(?i:(\\!\\=|\\&\\&|\\|\\||>>|<<|>=|<=|<>|<=>|\\bxor\\b|\\brlike\\b|\\bregexp\\b|\\bisnull\\b)|(?:not\\s+between\\s+0\\s+and)|(?:is\\s+null)|(like\\s+null)|(?:(?:^|\\W)in[+\\s]*\\([\\s\\d\\"]+[^()]*\\))|(?:\\bxor\\b|<>|rlike(?:\\s+binary)?)|(?:regexp\\s+binary)) |
|
高危 |
SQL Injection Attack: SQL Tautology Detected. |
(?i:([\\s\'\\"`\\(\\)]*?)([\\d\\w]++)([\\s\'\\"`\\(\\)]*?)(?:(?:=|<=>|r?like|sounds\\s+like|regexp)([\\s\'\\"`\\(\\)]*?)\\2|(?:!=|<=|>=|<>|<|>|\\^|is\\s+not|not\\s+like|not\\s+regexp)([\\s\'\\"`\\(\\)]*?)(?!\\2)([\\d\\w]+))) |
|
高危 |
Detects basic SQL authentication bypass attempts 1/3 |
(?i:(?i:\\d[\\"\'`]\\s+[\\"\'`]\\s+\\d)|(?:^admin\\s*?[\\"\'`]|(\\/\\*)+[\\"\'`]+\\s?(?:--|#|\\/\\*|{)?)|(?:[\\"\'`]\\s*?(x?or|div|like|between|and)[\\w\\s-]+\\s*?[+<>=(),-]\\s*?[\\d\\"\'`])|(?:[\\"\'`]\\s*?[^\\w\\s]?=\\s*?[\\"\'`])|(?:[\\"\'`]\\W*?[+=]+\\W*?[\\"\'`])|(?:[\\"\'`]\\s*?[!=|][\\d\\s!=+-]+.*?[\\"\'`(].*?$)|(?:[\\"\'`]\\s*?[!=|][\\d\\s!=]+.*?\\d+$)|(?:[\\"\'`]\\s*?like\\W+[\\w\\"\'`(])|(?:\\sis\\s*?0\\W)|(?:where\\s[\\s\\w\\.,-]+\\s=)|(?:[\\"\'`][<>~]+[\\"\'`])) |
|
高危 |
Detects MySQL comment-/space-obfuscated injections and backtick termination |
(?i:(?:,.*?[)\\da-f\\"\'`][\\"\'`](?:[\\"\'`].*?[\\"\'`]|\\Z|[^\\"\'`]+))|(?:\\Wselect.+\\W*?from)|((?:select|create|rename|truncate|load|alter|delete|update|insert|desc)\\s*?\\(\\s*?space\\s*?\\()) |
|
高危 |
Detects chained SQL injection attempts 1/2 |
(?i:(?:@.+=\\s*?\\(\\s*?select)|(?:\\d+\\s*?(x?or|div|like|between|and)\\s*?\\d+\\s*?[\\-+])|(?:\\/\\w+;?\\s+(?:having|and|x?or|div|like|between|and|select)\\W)|(?:\\d\\s+group\\s+by.+\\()|(?:(?:;|#|--)\\s*?(?:drop|alter))|(?:(?:;|#|--)\\s*?(?:update|insert)\\s*?\\w{2,})|(?:[^\\w]SET\\s*?@\\w+)|(?:(?:n?and|x?x?or|div|like|between|and|not|\\|\\||\\&\\&)[\\s(]+\\w+[\\s)]*?[!=+]+[\\s\\d]*?[\\"\'`=()])) |
|
高危 |
Detects basic SQL authentication bypass attempts 2/3 |
(?i:(?:union\\s*?(?:all|distinct|[(!@]*?)?\\s*?[([]*?\\s*?select\\s+)|(?:\\w+\\s+like\\s+[\\"\'`])|(?:like\\s*?[\\"\'`]\\%)|(?:[\\"\'`]\\s*?like\\W*?[\\"\'`\\d])|(?:[\\"\'`]\\s*?(?:n?and|x?x?or|div|like|between|and|not|\\|\\||\\&\\&)\\s+[\\s\\w]+=\\s*?\\w+\\s*?having\\s+)|(?:[\\"\'`]\\s*?\\*\\s*?\\w+\\W+[\\"\'`])|(?:[\\"\'`]\\s*?[^?\\w\\s=.,;)(]+\\s*?[(@\\"\'`]*?\\s*?\\w+\\W+\\w)|(?:select\\s+?[\\[\\]()\\s\\w\\.,\\"\'`-]+from\\s+)|(?:find_in_set\\s*?\\()) |
|
高危 |
Detects MySQL comments, conditions and ch(a)r injections |
(?i:(?:\\)\\s*?when\\s*?\\d+\\s*?then)|(?:[\\"\'`]\\s*?(?:#|--|{))|(?:\\/\\*!\\s?\\d+)|(?:ch(?:a)?r\\s*?\\(\\s*?\\d)|(?:(?:(n?and|x?x?or|div|like|between|and|not)\\s+|\\|\\||\\&\\&)\\s*?\\w+\\()) |
|
高危 |
Detects chained SQL injection attempts 2/2 |
(?i:(?:[\\"\'`]\\s+and\\s*?=\\W)|(?:\\(\\s*?select\\s*?\\w+\\s*?\\()|(?:\\*\\/from)|(?:\\+\\s*?\\d+\\s*?\\+\\s*?@)|(?:\\w[\\"\'`]\\s*?(?:(?:[-+=|@]+\\s+?)+|[-+=|@]+)[\\d(])|(?:coalesce\\s*?\\(|@@\\w+\\s*?[^\\w\\s])|(?:\\W!+[\\"\'`]\\w)|(?:[\\"\'`];\\s*?(?:if|while|begin))|(?:[\\"\'`][\\s\\d]+=\\s*?\\d)|(?:order\\s+by\\s+if\\w*?\\s*?\\()|(?:[\\s(]+case\\d*?\\W.+[tw]hen[\\s(])) |
|
高危 |
Detects classic SQL injection probings 1/2 |
(?i:(?:[\\"\'`]\\s*?(x?or|div|like|between|and)\\s*?[\\"\'`]?\\d)|(?:\\\\\\\\x(?:23|27|3d))|(?:^.?[\\"\'`]$)|(?:(?:^[\\"\'`\\\\\\\\]*?(?:[\\d\\"\'`]+|[^\\"\'`]+[\\"\'`]))+\\s*?(?:n?and|x?x?or|div|like|between|and|not|\\|\\||\\&\\&)\\s*?[\\w\\"\'`][+&!@(),.-])|(?:[^\\w\\s]\\w+\\s*?[|-]\\s*?[\\"\'`]\\s*?\\w)|(?:@\\w+\\s+(and|x?or|div|like|between|and)\\s*?[\\"\'`\\d]+)|(?:@[\\w-]+\\s(and|x?or|div|like|between|and)\\s*?[^\\w\\s])|(?:[^\\w\\s:]\\s*?\\d\\W+[^\\w\\s]\\s*?[\\"\'`].)|(?:\\Winformation_schema|table_name\\W)) |
|
高危 |
Detects basic SQL authentication bypass attempts 3/3 |
(?i:(?:in\\s*?\\(+\\s*?select)|(?:(?:n?and|x?x?or|div|like|between|and|not|\\|\\||\\&\\&)\\s+[\\s\\w+]+(?:regexp\\s*?\\(|sounds\\s+like\\s*?[\\"\'`]|[=\\d]+x))|([\\"\'`]\\s*?\\d\\s*?(?:--|#))|(?:[\\"\'`][\\%&<>^=]+\\d\\s*?(=|x?or|div|like|between|and))|(?:[\\"\'`]\\W+[\\w+-]+\\s*?=\\s*?\\d\\W+[\\"\'`])|(?:[\\"\'`]\\s*?is\\s*?\\d.+[\\"\'`]?\\w)|(?:[\\"\'`]\\|?[\\w-]{3,}[^\\w\\s.,]+[\\"\'`])|(?:[\\"\'`]\\s*?is\\s*?[\\d.]+\\s*?\\W.*?[\\"\'`])) |
|
高危 |
Detects classic SQL injection probings 2/2 |
(?i:(?:[\\"\'`]\\s*?\\*.+(?:x?or|div|like|between|and|id)\\W*?[\\"\'`]\\d)|(?:\\^[\\"\'`])|(?:^[\\w\\s\\"\'`-]+(?<=and\\s)(?<=or|xor|div|like|between|and\\s)(?<=xor\\s)(?<=nand\\s)(?<=not\\s)(?<=\\|\\|)(?<=\\&\\&)\\w+\\()|(?:[\\"\'`][\\s\\d]*?[^\\w\\s]+\\W*?\\d\\W*?.*?[\\"\'`\\d])|(?:[\\"\'`]\\s*?[^\\w\\s?]+\\s*?[^\\w\\s]+\\s*?[\\"\'`])|(?:[\\"\'`]\\s*?[^\\w\\s]+\\s*?[\\W\\d].*?(?:#|--))|(?:[\\"\'`].*?\\*\\s*?\\d)|(?:[\\"\'`]\\s*?(x?or|div|like|between|and)\\s[^\\d]+[\\w-]+.*?\\d)|(?:[()\\*<>%+-][\\w-]+[^\\w\\s]+[\\"\'`][^,])) |
|
高危 |
SQL Injection Attack |
\\b(?i:having)\\b\\s+(\\d{1,10}|\'[^=]{1,10}\')\\s*?[=<>]|(?i:\\bexecute(\\s{1,5}[\\w\\.$]{1,5}\\s{0,3})?\\()|\\bhaving\\b ?(?:\\d{1,10}|[\\\'\\"][^=]{1,10}[\\\'\\"]) ?[=<>]+|(?i:\\bcreate\\s+?table.{0,20}?\\()|(?i:\\blike\\W*?char\\W*?\\()|(?i:(?:(select(.*?)case|from(.*?)limit|order\\sby)))|exists\\s(\\sselect|select\\Sif(null)?\\s\\(|select\\Stop|select\\Sconcat|system\\s\\(|\\b(?i:having)\\b\\s+(\\d{1,10})|\'[^=]{1,10}\') |
|
高危 |
SQL Injection Attack |
(?i:\\bor\\b ?(?:\\d{1,10}|[\\\'\\"][^=]{1,10}[\\\'\\"]) ?[=<>]+|(?i:\'\\s+x?or\\s+.{1,20}[+\\-!<>=])|\\b(?i:x?or)\\b\\s+(\\d{1,10}|\'[^=]{1,10}\')|\\b(?i:x?or)\\b\\s+(\\d{1,10}|\'[^=]{1,10}\')\\s*?[=<>]) |
|
高危 |
SQL Injection Attack |
(?i)\\b(?i:and)\\b\\s+(\\d{1,10}|\'[^=]{1,10}\')\\s*?[=]|\\b(?i:and)\\b\\s+(\\d{1,10}|\'[^=]{1,10}\')\\s*?[<>]|\\band\\b ?(?:\\d{1,10}|[\\\'\\"][^=]{1,10}[\\\'\\"]) ?[=<>]+|\\b(?i:and)\\b\\s+(\\d{1,10}|\'[^=]{1,10}\') |
|
高危 |
SQL Injection Attack |
(?i:(?:(?:s(?:t(?:d(?:dev(_pop|_samp)?)?|r(?:_to_date|cmp))|u(?:b(?:str(?:ing(_index)?)?|(?:dat|tim)e)|m)|e(?:c(?:_to_time|ond)|ssion_user)|ys(?:tem_user|date)|ha(1|2)?|oundex|chema|ig?n|pace|qrt)|i(?:s(null|_(free_lock|ipv4_compat|ipv4_mapped|ipv4|ipv6|not_null|not|null|used_lock))?|n(?:et6?_(aton|ntoa)|s(?:ert|tr)|terval)?|f(null)?)|u(?:n(?:compress(?:ed_length)?|ix_timestamp|hex)|tc_(date|time|timestamp)|p(?:datexml|per)|uid(_short)?|case|ser)|l(?:o(?:ca(?:l(timestamp)?|te)|g(2|10)?|ad_file|wer)|ast(_day|_insert_id)?|e(?:(?:as|f)t|ngth)|case|trim|pad|n)|t(?:ime(stamp|stampadd|stampdiff|diff|_format|_to_sec)?|o_(base64|days|seconds|n?char)|r(?:uncate|im)|an)|m(?:a(?:ke(?:_set|date)|ster_pos_wait|x)|i(?:(?:crosecon)?d|n(?:ute)?)|o(?:nth(name)?|d)|d5)|r(?:e(?:p(?:lace|eat)|lease_lock|verse)|o(?:w_count|und)|a(?:dians|nd)|ight|trim|pad)|f(?:i(?:eld(_in_set)?|nd_in_set)|rom_(base64|days|unixtime)|o(?:und_rows|rmat)|loor)|a(?:es_(?:de|en)crypt|s(?:cii(str)?|in)|dd(?:dat|tim)e|(?:co|b)s|tan2?|vg)|p(?:o(?:sition|w(er)?)|eriod_(add|diff)|rocedure_analyse|assword|i)|b(?:i(?:t_(?:length|count|x?or|and)|n(_to_num)?)|enchmark)|e(?:x(?:p(?:ort_set)?|tract(value)?)|nc(?:rypt|ode)|lt)|v(?:a(?:r(?:_(?:sam|po)p|iance)|lues)|ersion)|g(?:r(?:oup_conca|eates)t|et_(format|lock))|o(?:(?:ld_passwo)?rd|ct(et_length)?)|we(?:ek(day|ofyear)?|ight_string)|n(?:o(?:t_in|w)|ame_const|ullif)|(rawton?)?hex(toraw)?|qu(?:arter|ote)|(pg_)?sleep|year(week)?|d?count|xmltype|hour)\\W*?\\(|\\b(?:(?:s(?:elect\\b(?:.{1,100}?\\b(?:(?:length|count|top)\\b.{1,100}?\\bfrom|from\\b.{1,100}?\\bwhere)|.*?\\b(?:d(?:ump\\b.*?\\bfrom|ata_type)|(?:to_(?:numbe|cha)|inst)r))|p_(?:sqlexec|replwritetovarbin|help|addextendedproc|is_srvrolemember|prepare|password|execute(?:sql)?|makewebtask|oacreate)|ql_(?:longvarchar|variant))|xp_(?:reg(?:re(?:movemultistring|ad)|delete(?:value|key)|enum(?:value|key)s|addmultistring|write)|terminate|servicecontrol|ntsec_enumdomains|terminate_process|e(?:xecresultset|numdsn)|availablemedia|loginconfig|cmdshell|filelist|dirtree|makecab|ntsec)|u(?:nion\\b.{1,100}?\\bselect|tl_(?:file|http))|d(?:b(?:a_users|ms_java)|elete\\b\\W*?\\bfrom)|group\\b.*?\\bby\\b.{1,100}?\\bhaving|open(?:rowset|owa_util|query)|load\\b\\W*?\\bdata\\b.*?\\binfile|(?:n?varcha|tbcreato)r|autonomous_transaction)\\b|i(?:n(?:to\\b\\W*?\\b(?:dump|out)file|sert\\b\\W*?\\binto|ner\\b\\W*?\\bjoin)\\b|(?:f(?:\\b\\W*?\\(\\W*?\\bbenchmark|null\\b)|snull\\b)\\W*?\\()|print\\b\\W*?\\@\\@|cast\\b\\W*?\\()|c(?:(?:ur(?:rent_(?:time(?:stamp)?|date|user)|(?:dat|tim)e)|h(?:ar(?:(?:acter)?_length|set)?|r)|iel(?:ing)?|ast|r32)\\W*?\\(|o(?:(?:n(?:v(?:ert(?:_tz)?)?|cat(?:_ws)?|nection_id)|(?:mpres)?s|ercibility|alesce|t)\\W*?\\(|llation\\W*?\\(a))|d(?:(?:a(?:t(?:e(?:(_(add|format|sub))?|diff)|abase)|y(name|ofmonth|ofweek|ofyear)?)|e(?:(?:s_(de|en)cryp|faul)t|grees|code)|ump)\\W*?\\(|bms_\\w+\\.\\b)|(?:;\\W*?\\b(?:shutdown|drop)|\\@\\@version)\\b|\\butl_inaddr\\b|\\bsys_context\\b|\'(?:s(?:qloledb|a)|msdasql|dbo)\'))" |
|
警告 |
Restricted SQL Character Anomaly Detection (args): # of special characters exceeded (12) |
((?:[\\~\\!\\@\\#\\$\\%\\^\\&\\*\\(\\)\\-\\+\\=\\{\\}\\[\\]\\|\\:\\;\\"\\\'\\麓\\鈥橽鈥榎`\\<\\>][^\\~\\!\\@\\#\\$\\%\\^\\&\\*\\(\\)\\-\\+\\=\\{\\}\\[\\]\\|\\:\\;\\"\\\'\\麓\\鈥橽鈥榎`\\<\\>]*?){12}) |
|
高危 |
SQL Comment Sequence Detected. |
(/\\*!?|\\*/|[\';]--|--[\\s\\r\\n\\v\\f]|(?:--[^-]*?-)|([^\\-&])#.*?[\\s\\r\\n\\v\\f]|;?\\\\x00) |
|
高危 |
SQL Hex Encoding Identified |
(?i:(?:\\A|[^\\d])0x[a-f\\d]{3,}[a-f\\d]*)+ |
|
高危 |
Detects HAVING injections |
(?i)\\W+\\d*?\\s*?having\\s*?[^\\s\\-] |
|
警告 |
Restricted SQL Character Anomaly Detection (cookies): # of special characters exceeded (8) |
((?:[\\~\\!\\@\\#\\$\\%\\^\\&\\*\\(\\)\\-\\+\\=\\{\\}\\[\\]\\|\\:\\;\\"\\\'\\麓\\鈥橽鈥榎`\\<\\>][^\\~\\!\\@\\#\\$\\%\\^\\&\\*\\(\\)\\-\\+\\=\\{\\}\\[\\]\\|\\:\\;\\"\\\'\\麓\\鈥橽鈥榎`\\<\\>]*?){8}) |
|
警告 |
Restricted SQL Character Anomaly Detection (args): # of special characters exceeded (6) |
((?:[\\~\\!\\@\\#\\$\\%\\^\\&\\*\\(\\)\\-\\+\\=\\{\\}\\[\\]\\|\\:\\;\\"\\\'\\麓\\鈥橽鈥榎`\\<\\>][^\\~\\!\\@\\#\\$\\%\\^\\&\\*\\(\\)\\-\\+\\=\\{\\}\\[\\]\\|\\:\\;\\"\\\'\\麓\\鈥橽鈥榎`\\<\\>]*?){6}) |
|
警告 |
Restricted SQL Character Anomaly Detection (cookies): # of special characters exceeded (3) |
((?:[\\~\\!\\@\\#\\$\\%\\^\\&\\*\\(\\)\\-\\+\\=\\{\\}\\[\\]\\|\\:\\;\\"\\\'\\麓\\鈥橽鈥榎`\\<\\>][^\\~\\!\\@\\#\\$\\%\\^\\&\\*\\(\\)\\-\\+\\=\\{\\}\\[\\]\\|\\:\\;\\"\\\'\\麓\\鈥橽鈥榎`\\<\\>]*?){3}) |
|
警告 |
Restricted SQL Character Anomaly Detection (args): # of special characters exceeded (2) |
((?:[\\~\\!\\@\\#\\$\\%\\^\\&\\*\\(\\)\\-\\+\\=\\{\\}\\[\\]\\|\\:\\;\\"\\\'\\麓\\鈥橽鈥榎`\\<\\>][^\\~\\!\\@\\#\\$\\%\\^\\&\\*\\(\\)\\-\\+\\=\\{\\}\\[\\]\\|\\:\\;\\"\\\'\\麓\\鈥橽鈥榎`\\<\\>]*?){2}) |
以上是关于modSecurity规则学习——防止SQL注入的主要内容,如果未能解决你的问题,请参考以下文章