Chromium(Chrome) Sandbox Details
Posted 两只小蚂蚁
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Chromium(Chrome) Sandbox Details相关的知识,希望对你有一定的参考价值。
What Sandbox Do?
Sandbox leverages the OS-provided security to allow code execution that cannot make persistent changes to the computer or access information that is confidential.
What the Sandbox\'s structure is?
Sandbox operates at process-level granularity. Anything that needs to be sandboxed needs to live on a separate process.
The minimal sandbox configuration has two processes: one that is a privileged controller known as the broker, and one or more sandboxed processes known as the target.
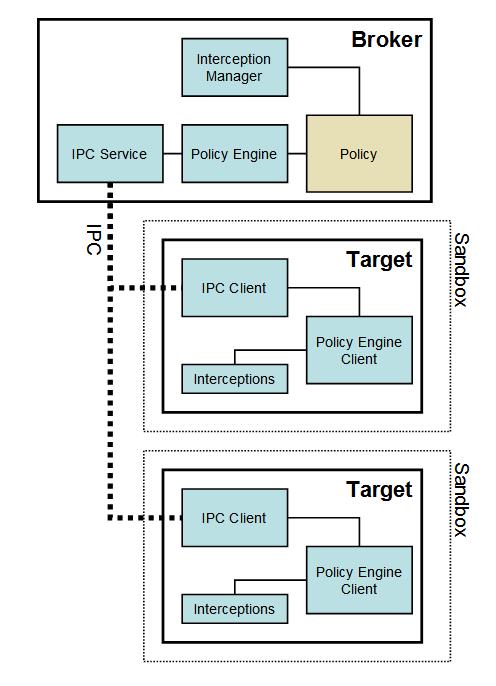
Broker
Browser process(Chromium):
- Specify the policy for each target process
- Spawn the target processes
- Host the sandbox policy engine service
- Host the sandbox interception manager
- Host the sandbox IPC service (to the target processes)
- Perform the policy-allowed actions on behalf of the target process
Target
Renderers process, hosts all the code that is going to run inside the sandbox:
- All code to be sandboxed
- The sandbox IPC client
- The sandbox policy engine client
- The sandbox interceptions
Target process restrictions:
-
- Forbid per-use system-wide changes using
SystemParametersInfo(), which can be used to swap the mouse buttons or set the screen saver timeout - Forbid the creation or switch of Desktops
- Forbid changes to the per-user display configuration such as resolution and primary display
- No read or write to the clipboard
- Forbid Windows message broadcasts
- Forbid setting global Windows hooks (using
SetWindowsHookEx()) - Forbid access to the global atoms table
- Forbid access to USER handles created outside the Job object
- One active process limit (disallows creating child processes)
- Forbid per-use system-wide changes using
Allowed resource access:
-
- Read access to most files
- Write access to
%USER PROFILE%\\AppData\\LocalLow - Read access to most of the registry
- Write access to
HKEY_CURRENT_USER\\Software\\AppDataLow - Clipboard (copy and paste for certain formats)
- Remote procedure call (RPC)
- TCP/IP Sockets
- Window messages exposed via
ChangeWindowMessageFilter - Shared memory exposed via LI (low integrity) labels
- COM interfaces with LI (low integrity) launch activation rights
- Named pipes exposed via LI (low integrity) labels
refers:
https://chromium.googlesource.com/chromium/src/+/master/docs/design/sandbox.md
以上是关于Chromium(Chrome) Sandbox Details的主要内容,如果未能解决你的问题,请参考以下文章
Chrome/Chromium的实验性功能+扩展推荐,让你的Chrome/Chromium起飞!
如何在 chrome 或 chromium 中禁用 HTTP/2?