云桥连接器(CloudBridge Connector)功能测试
云桥连接器简介
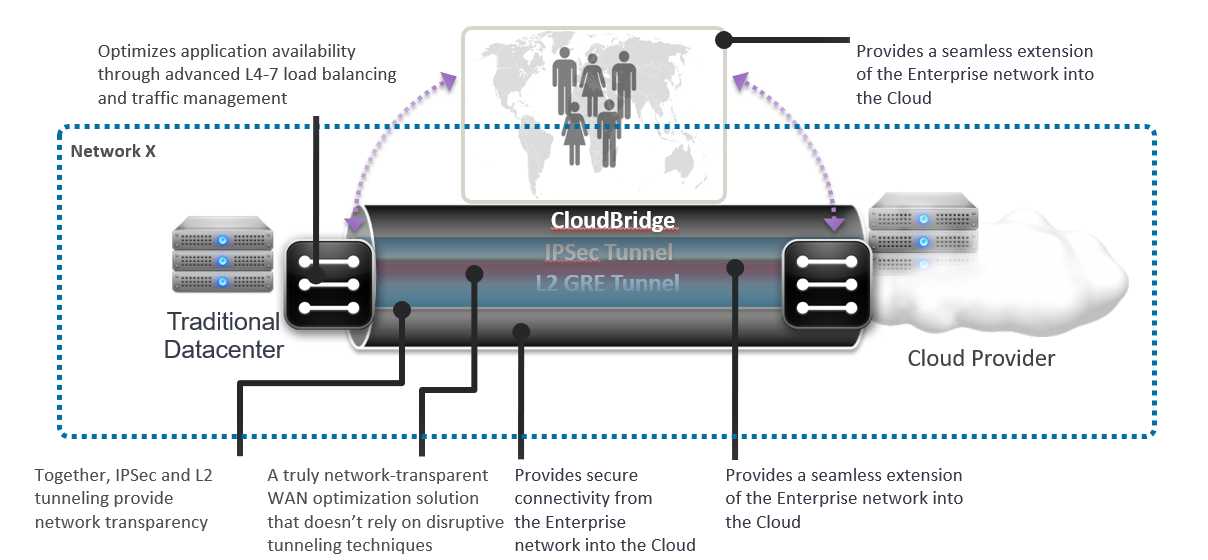
云桥连接器基本使用样例:
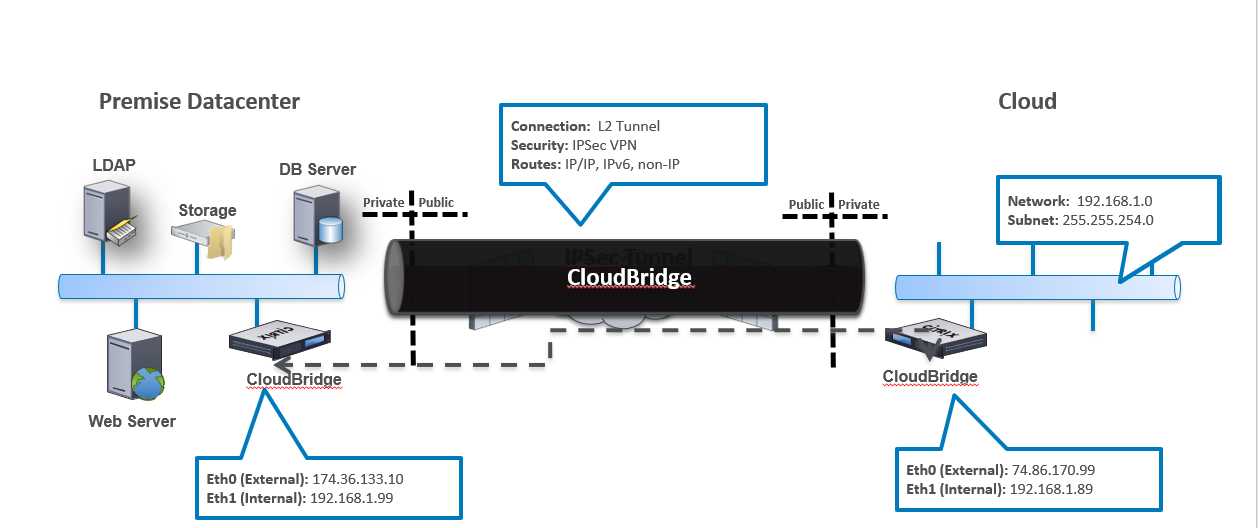
设备ans-ha1(ANSIP: 192.168.11.11)的初始配置:
> show hostName
Hostname: ans-ha1
Done
> show ip
Ipaddress TD Type Mode Arp Icmp Vserver State
--------- -- ---- ---- --- ---- ------- ------
1) 192.168.11.11 0 HGANS IP Active Enabled Enabled NA Enabled
2) 192.168.11.1 0 SNIP|ADNS Active Enabled Enabled NA Enabled
3) 192.168.10.41 0 SNIP Active Enabled Enabled NA Enabled
Done
> show route
Network Netmask Gateway/OwnedIP State TD Type
------- ------- --------------- ----- -- ----
1) 0.0.0.0 0.0.0.0 192.168.10.1 UP 0 STATIC
2) 127.0.0.0 255.0.0.0 127.0.0.1 UP 0 PERMANENT
3) 192.168.10.0 255.255.255.0 192.168.10.41 UP 0 DIRECT
4) 192.168.11.0 255.255.255.0 192.168.11.11 UP 0 DIRECT
Done
> show acl
Done
> show pbr
Done
>
设备ans-one(ANSIP: 192.168.21.11)的初始配置:
> show hostName
Hostname: ans-one
Done
> show ip
Ipaddress TD Type Mode Arp Icmp Vserver State
--------- -- ---- ---- --- ---- ------- ------
1) 192.168.21.11 0 HGANS IP Active Enabled Enabled NA Enabled
2) 192.168.20.41 0 SNIP Active Enabled Enabled NA Enabled
3) 192.168.21.1 0 SNIP|ADNS Active Enabled Enabled NA Enabled
Done
> show route
Network Netmask Gateway/OwnedIP State TD Type
------- ------- --------------- ----- -- ----
1) 0.0.0.0 0.0.0.0 192.168.20.1 UP 0 STATIC
2) 127.0.0.0 255.0.0.0 127.0.0.1 UP 0 PERMANENT
3) 192.168.20.0 255.255.255.0 192.168.20.41 UP 0 DIRECT
4) 192.168.21.0 255.255.255.0 192.168.21.11 UP 0 DIRECT
Done
> show acl
Done
> show pbr
Done
>
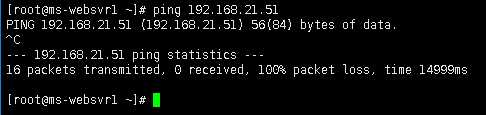
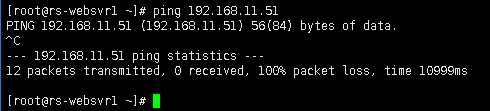
验证ms-websvr1(192.168.11.51)是否可以和rs-websvr1(192.168.21.51)网络互通
测试预期结果: 不能网络互通,100%数据包丢失。
在设备ans-ha1(ANSIP: 192.168.11.11)上进行如下配置:
> add ans ip 192.168.10.101 255.255.255.0 -type VIP
Done
> enable ans mode L3
Done
> add ipsec profile RemoteSite -encAlgo AES -psk "123456"
Done
> add ipTunnel RemoteSite 192.168.20.101 255.255.255.255 192.168.10.101 -protocol IPSEC -ipsecProfileName RemoteSite
Done
> add ans pbr RemoteSite ALLOW -td 0 -srcIP = 192.168.11.51 -destIP = 192.168.21.51 -ipTunnel RemoteSite
Done
> apply pbrs
Done
> show ipTunnel
1) Domain.......: 0
Name.........: RemoteSite
Remote.......: 192.168.20.101 Mask......: 255.255.255.255
Local........: 192.168.10.101 Encap.....: 192.168.10.101
Protocol.....: IPSEC Type......: C
IPSec Profile Name.......: RemoteSite
IPSec Tunnel Status......: DOWN
IPSec Tunnel PBR name....: RemoteSite
Done
> show pbr RemoteSite
1) Name: RemoteSite
Action: ALLOW Hits: 0
srcIP = 192.168.11.51
destIP = 192.168.21.51
srcMac: Protocol:
Vlan: Interface:
Active Status: ENABLED Applied Status: APPLIED
Priority: 10
IpTunnel: RemoteSite
Done
在设备ans-one(ANSIP: 192.168.21.11)上进行如下配置:
> add ans ip 192.168.20.101 255.255.255.0 -type VIP
Done
> enable ans mode L3
Done
> add ipsec profile RemoteSite -encAlgo AES -psk "123456"
Done
> add ipTunnel RemoteSite 192.168.10.101 255.255.255.255 192.168.20.101 -protocol IPSEC -ipsecProfileName RemoteSite
Done
> add ans pbr RemoteSite ALLOW -td 0 -srcIP = 192.168.21.51 -destIP = 192.168.11.51 -ipTunnel RemoteSite
Done
> apply pbrs
Done
> show ipTunnel
1) Domain.......: 0
Name.........: RemoteSite
Remote.......: 192.168.10.101 Mask......: 255.255.255.255
Local........: 192.168.20.101 Encap.....: 192.168.20.101
Protocol.....: IPSEC Type......: C
IPSec Profile Name.......: RemoteSite
IPSec Tunnel Status......: DOWN
IPSec Tunnel PBR name....: RemoteSite
Done
> show pbr RemoteSite
1) Name: RemoteSite
Action: ALLOW Hits: 0
srcIP = 192.168.21.51
destIP = 192.168.11.51
srcMac: Protocol:
Vlan: Interface:
Active Status: ENABLED Applied Status: APPLIED
Priority: 10
IpTunnel: RemoteSite
Done
验证ms-websvr1(192.168.11.51)是否可以和rs-websvr1(192.168.21.51)网络互通
测试预期结果: 可以网络互通,0%数据包丢失。
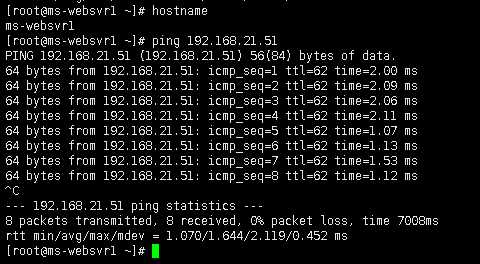
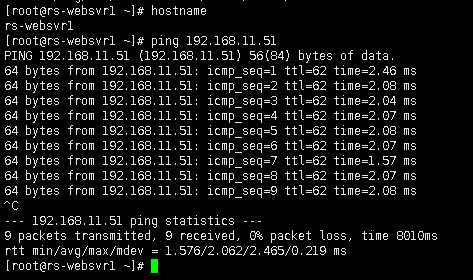
在设备ans-one(ANSIP: 192.168.21.11)上查看统计信息:
> show pbr RemoteSite
1) Name: RemoteSite
Action: ALLOW Hits: 121
srcIP = 192.168.11.51
destIP = 192.168.21.51
srcMac: Protocol:
Vlan: Interface:
Active Status: ENABLED Applied Status: APPLIED
Priority: 10
IpTunnel: RemoteSite
Done
> stat pbr
PBR Statistics
Rate (/s) Total
Allow PBR hits 0 200
Deny PBR hits 0 0
PBR hits 0 200
PBR misses 1 1818
Done
> stat ipsec counters
Secure tunnel(s) summary
Rate (/s) Total
Bytes Received 0 4704
Bytes Sent 0 7992
Packets Received 0 49
Packets Sent 0 74
Done
在设备ans-one(ANSIP: 192.168.21.11)上查看统计信息:
> show pbr RemoteSite
1) Name: RemoteSite
Action: ALLOW Hits: 94
srcIP = 192.168.21.51
destIP = 192.168.11.51
srcMac: Protocol:
Vlan: Interface:
Active Status: ENABLED Applied Status: APPLIED
Priority: 10
IpTunnel: RemoteSite
Done
> stat pbr
PBR Statistics
Rate (/s) Total
Allow PBR hits 0 110
Deny PBR hits 0 0
PBR hits 0 110
PBR misses 1 1108
Done
> stat ipsec counters
Secure tunnel(s) summary
Rate (/s) Total
Bytes Received 0 7104
Bytes Sent 0 5292
Packets Received 0 74
Packets Sent 0 49
Done
设备ipTunnel 功能支持的协议有三种:IPIP , GRE , IPSEC .
IPIP(IP over IP) : 第三层隧道协议- OSI模型的网络层
用于连接两个一般情况下无法直接通讯的IPv4网络。
GRE(Generic Routing Encapsulation): 第三层隧道协议- OSI模型的网络层
通用路由封装(GRE:Generic Routing Encapsulation)在RFC1701/RFC1702中定义,它规定了怎样用一种网络层协议去封装另一种网络层协议的方法。GRE的隧道由两端的源IP地址和目的IP地址来定义,它允许用户使用IP封装IP、IPX、AppleTalk,并支持全部的路由协议,如RIP、OSPF、IGRP、EIGRP。通过GRE,用户可以利用公用IP网络连接IPX网络和AppleTalk网络,还可以使用保留地址进行网络互联,或对公网隐藏企业网的IP地址。
GRE的包头包含了协议类型(用于标明乘客协议的类型);校验和包括了GRE的包头和完整的乘客协议与数据;密钥(用于接收端验证接收的数据);序列号(用于接收端数据包的排序和差错控制)和路由信息(用于本数据包的路由)。
GRE只提供了数据包的封装,它没有防止网络侦听和攻击的加密功能。所以在实际环境中它常和IPsec一起使用,由IPsec为用户数据的加密,给用户提供更好的安全服务。
IPSEC(Internet Protocol Security): 第三层隧道协议- OSI模型的网络层
IP安全协议(IPSec:IP Security)实际上是一套协议包而不是一个独立的协议,这一点对于我们认识IPSec是很重要的。从1995年开始IPSec的研究以来,IETF IPSec工作组在它的主页上发布了几十个Internet草案文献和12个RFC文件。其中,比较重要的有RFC2409 IKE(互连网密钥交换)、RFC2401 IPSec协议、RFC2402 AH验证包头、RFC2406 ESP加密数据等文件。
IPSec安全体系包括3个基本协议:AH协议为IP包提供信息源验证和完整性保证;ESP协议提供加密机制;密钥管理协议(ISAKMP)提供双方交流时的共享安全信息。ESP和AH协议都有相关的一系列支持文件,规定了加密和认证的算法。最后,解释域(DOI)通过一系列命令、算法、属性和参数连接所有的IPSec组文件。
测试存在的问题:
1: GRE协议的ip隧道,不能指定grepayload属性为ETHERNETwithDOT1Q。
所以在该设备系统上GRE协议目前不支持封装 dot1Q vlan id
由于GRE协议不支持封装 dot1Q vlan id,导致设置PBR规则只能进行点对点(目标IP和源IP均为1个,无法使用范围)的连接。