Ansible如何管理你的云:AWSOpenstack?你的运维也可以很帅!
Posted 大魏分享
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Ansible如何管理你的云:AWSOpenstack?你的运维也可以很帅!相关的知识,希望对你有一定的参考价值。
一、云时代的运维
本文是我和李尧老师一起实验。李尧是红帽高级培训讲师,目前负责红帽中国区员工内部技术培训与认证。
物理机时代的运维,由于设备数量较少,运维人员的压力不大,工作之余还能喝点小酒,状态是这样的:
上了虚拟机后,操作系统数量增加十倍,运维人员严阵以待,但仍能抵挡,状态是这样的:

上了Openstack后,操作系统数量再度增加,并且需要做异构环境维护,运维人员有点蒙圈,状态是这样的:

公有云开始使用,员需要对物理机、虚拟机、Openstack、公有云的一体化运维,运维人员的状态彻底崩溃,状态是这样的:

那么,有没有一种运维手段和工具,帮助客户解决这个问题呢?请看本文如何通过Ansible管理公有云。
二、Ansible都能管什么云?
Ansible都能管什么云?不是一个两个,很是很多很多,但最有名的几个是:
AWS、Azure、Google、Openstack、VMware(虚拟化)
(http://docs.ansible.com/ansible/latest/modules/list_of_cloud_modules.html)
事实上,Anisble的管理功能是全栈的:从底层硬件到顶层云租户中的应用。
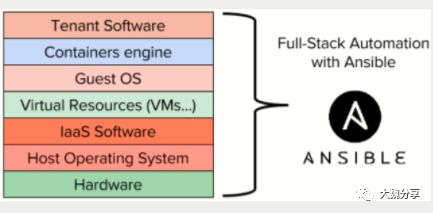
三、Ansible如何连接云
Ansible连接虚拟机中的OS,可以通过ssh、winRM。但如果想对云做配置管理,则需要对应的连接代理,对应连接代理名称:
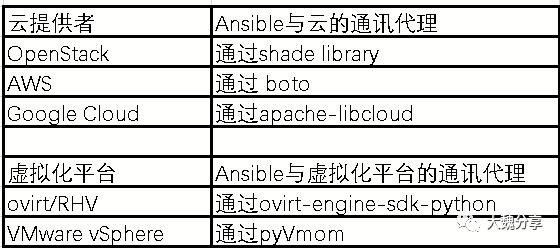
Ansible管理Openstack,用的是shade方式(https://pypi.org/project/shade/)
简单而言,shade是一种客户端连接Openstack的方式,它调用的是Openstack的API。
在Ansible Server上,如果要配置对Openstack的连接,则需要配置(~/.config/openstack下)clouds.yaml文件,具体内容在后面实验会详细解释。
Ansible管理AWS,用的boto的代理连接AWS的IAM组件。
在一个Ansible server上,如果要配置对AWS的连接,需要配置两个文件:
/etc/boto.cfg
~/.aws/credentials
~/.boto
需要配置的变量如下:
AWS_ACCESS_KEY_ID
AWS_SECRET_ACCESS_KEY
AWS_SECURITY_TOKEN
AWS_PROFILE
四、Ansible连上云可以可以调用的组件
云平台提供给Anible的可以调用的模块,先看一下AWS的,内容很丰富:
aws_acm_facts - Retrieve certificate facts from AWS Certificate Manager service
aws_api_gateway - Manage AWS API Gateway APIs
aws_application_scaling_policy - Manage Application Auto Scaling Scaling Policies
aws_az_facts - Gather facts about availability zones in AWS.
aws_batch_compute_environment - Manage AWS Batch Compute Environments
aws_batch_job_definition - Manage AWS Batch Job Definitions
aws_batch_job_queue - Manage AWS Batch Job Queues
aws_direct_connect_connection - Creates, deletes, modifies a DirectConnect connection
aws_direct_connect_gateway - Manage AWS Direct Connect Gateway.
aws_direct_connect_link_aggregation_group - Manage Direct Connect LAG bundles.
aws_direct_connect_virtual_interface - Manage Direct Connect virtual interfaces.
aws_elasticbeanstalk_app - create, update, and delete an elastic beanstalk application
aws_kms - Perform various KMS management tasks.
aws_kms_facts - Gather facts about AWS KMS keys
aws_region_facts - Gather facts about AWS regions.
aws_s3 - manage objects in S3.
aws_s3_bucket_facts - Lists S3 buckets in AWS
aws_s3_cors - Manage CORS for S3 buckets in AWS
aws_ses_identity - Manages SES email and domain identity
aws_ssm_parameter_store - Manage key-value pairs in aws parameter store.
aws_waf_condition - create and delete WAF Conditions
aws_waf_facts - Retrieve facts for WAF ACLs, Rule , Conditions and Filters.
aws_waf_rule - create and delete WAF Rules
aws_waf_web_acl - create and delete WAF Web ACLs
cloudformation - Create or delete an AWS CloudFormation stack
cloudformation_facts - Obtain facts about an AWS CloudFormation stack
cloudfront_distribution - create, update and delete aws cloudfront distributions.
cloudfront_facts - Obtain facts about an AWS CloudFront distribution
cloudfront_invalidation - create invalidations for aws cloudfront distributions
cloudfront_origin_access_identity - create, update and delete origin access identities for a cloudfront distribution.
cloudtrail - manage CloudTrail create, delete, update
cloudwatchevent_rule - Manage CloudWatch Event rules and targets
cloudwatchlogs_log_group - create or delete log_group in CloudWatchLogs
cloudwatchlogs_log_group_facts - get facts about log_group in CloudWatchLogs
data_pipeline - Create and manage AWS Datapipelines
dynamodb_table - Create, update or delete AWS Dynamo DB tables.
dynamodb_ttl - set TTL for a given DynamoDB table.
ec2 - create, terminate, start or stop an instance in ec2
ec2_ami - create or destroy an image in ec2
ec2_ami_copy - copies AMI between AWS regions, return new image id
ec2_ami_facts - Gather facts about ec2 AMIs
ec2_ami_find - Searches for AMIs to obtain the AMI ID and other information (D)
ec2_ami_search - Retrieve AWS AMI information for a given operating system. (D)
ec2_asg - Create or delete AWS Autoscaling Groups
ec2_asg_facts - Gather facts about ec2 Auto Scaling Groups (ASGs) in AWS
ec2_asg_lifecycle_hook - Create, delete or update AWS ASG Lifecycle Hooks.
ec2_customer_gateway - Manage an AWS customer gateway
ec2_customer_gateway_facts - Gather facts about customer gateways in AWS
ec2_eip - manages EC2 elastic IP (EIP) addresses.
ec2_elb - De-registers or registers instances from EC2 ELBs
ec2_elb_facts - Gather facts about EC2 Elastic Load Balancers in AWS
ec2_elb_lb - Creates or destroys Amazon ELB.
ec2_eni - Create and optionally attach an Elastic Network Interface (ENI) to an instance
ec2_eni_facts - Gather facts about ec2 ENI interfaces in AWS
ec2_group - maintain an ec2 VPC security group.
ec2_group_facts - Gather facts about ec2 security groups in AWS.
ec2_instance - Create & manage EC2 instances
ec2_instance_facts - Gather facts about ec2 instances in AWS
ec2_key - create or delete an ec2 key pair
ec2_lc - Create or delete AWS Autoscaling Launch Configurations
ec2_lc_facts - Gather facts about AWS Autoscaling Launch Configurations
ec2_lc_find - Find AWS Autoscaling Launch Configurations
ec2_metadata_facts - Gathers facts (instance metadata) about remote hosts within ec2
ec2_metric_alarm - Create/update or delete AWS Cloudwatch ‘metric alarms’
ec2_placement_group - Create or delete an EC2 Placement Group
ec2_placement_group_facts - List EC2 Placement Group(s) details
ec2_remote_facts - Gather facts about ec2 instances in AWS (D)
ec2_scaling_policy - Create or delete AWS scaling policies for Autoscaling groups
ec2_snapshot - creates a snapshot from an existing volume
ec2_snapshot_copy - copies an EC2 snapshot and returns the new Snapshot ID.
ec2_snapshot_facts - Gather facts about ec2 volume snapshots in AWS
ec2_tag - create and remove tag(s) to ec2 resources.
ec2_vol - create and attach a volume, return volume id and device map
ec2_vol_facts - Gather facts about ec2 volumes in AWS
ec2_vpc - configure AWS virtual private clouds (D)
ec2_vpc_dhcp_option - Manages DHCP Options, and can ensure the DHCP options for the given VPC match what’s requested
ec2_vpc_dhcp_option_facts - Gather facts about dhcp options sets in AWS
ec2_vpc_egress_igw - Manage an AWS VPC Egress Only Internet gateway
ec2_vpc_endpoint - Create and delete AWS VPC Endpoints.
ec2_vpc_endpoint_facts - Retrieves AWS VPC endpoints details using AWS methods.
ec2_vpc_igw - Manage an AWS VPC Internet gateway
ec2_vpc_igw_facts - Gather facts about internet gateways in AWS
ec2_vpc_nacl - create and delete Network ACLs.
ec2_vpc_nacl_facts - Gather facts about Network ACLs in an AWS VPC
ec2_vpc_nat_gateway - Manage AWS VPC NAT Gateways.
ec2_vpc_nat_gateway_facts - Retrieves AWS VPC Managed Nat Gateway details using AWS methods.
ec2_vpc_net - Configure AWS virtual private clouds
ec2_vpc_net_facts - Gather facts about ec2 VPCs in AWS
ec2_vpc_peer - create, delete, accept, and reject VPC peering connections between two VPCs.
ec2_vpc_peering_facts - Retrieves AWS VPC Peering details using AWS methods.
ec2_vpc_route_table - Manage route tables for AWS virtual private clouds
ec2_vpc_route_table_facts - Gather facts about ec2 VPC route tables in AWS
ec2_vpc_subnet - Manage subnets in AWS virtual private clouds
ec2_vpc_subnet_facts - Gather facts about ec2 VPC subnets in AWS
ec2_vpc_vgw - Create and delete AWS VPN Virtual Gateways.
ec2_vpc_vgw_facts - Gather facts about virtual gateways in AWS
ec2_vpc_vpn - Create, modify, and delete EC2 VPN connections.
ec2_win_password - gets the default administrator password for ec2 windows instances
ecs_attribute - manage ecs attributes
ecs_cluster - create or terminate ecs clusters
ecs_ecr - Manage Elastic Container Registry repositories
ecs_service - create, terminate, start or stop a service in ecs
ecs_service_facts - list or describe services in ecs
ecs_task - run, start or stop a task in ecs
ecs_taskdefinition - register a task definition in ecs
ecs_taskdefinition_facts - describe a task definition in ecs
efs - create and maintain EFS file systems
efs_facts - Get information about Amazon EFS file systems
elasticache - Manage cache clusters in Amazon Elasticache.
elasticache_facts - Retrieve facts for AWS Elasticache clusters
elasticache_parameter_group - Manage cache security groups in Amazon Elasticache.
elasticache_snapshot - Manage cache snapshots in Amazon Elasticache.
elasticache_subnet_group - manage Elasticache subnet groups
elb_application_lb - Manage an Application load balancer
elb_application_lb_facts - Gather facts about application ELBs in AWS
elb_classic_lb - Creates or destroys Amazon ELB.
elb_classic_lb_facts - Gather facts about EC2 Elastic Load Balancers in AWS
elb_instance - De-registers or registers instances from EC2 ELBs
elb_target - Manage a target in a target group
elb_target_group - Manage a target group for an Application or Network load balancer
elb_target_group_facts - Gather facts about ELB target groups in AWS
execute_lambda - Execute an AWS Lambda function
iam - Manage IAM users, groups, roles and keys
iam_cert - Manage server certificates for use on ELBs and CloudFront
iam_group - Manage AWS IAM groups
iam_managed_policy - Manage User Managed IAM policies
iam_mfa_device_facts - List the MFA (Multi-Factor Authentication) devices registered for a user
iam_policy - Manage IAM policies for users, groups, and roles
iam_role - Manage AWS IAM roles
iam_role_facts - Gather information on IAM roles
iam_server_certificate_facts - Retrieve the facts of a server certificate
iam_user - Manage AWS IAM users
kinesis_stream - Manage a Kinesis Stream.
lambda - Manage AWS Lambda functions
lambda_alias - Creates, updates or deletes AWS Lambda function aliases.
lambda_event - Creates, updates or deletes AWS Lambda function event mappings.
lambda_facts - Gathers AWS Lambda function details as Ansible facts
lambda_policy - Creates, updates or deletes AWS Lambda policy statements.
lightsail - Create or delete a virtual machine instance in AWS Lightsail
rds - create, delete, or modify an Amazon rds instance
rds_param_group - manage RDS parameter groups
rds_subnet_group - manage RDS database subnet groups
redshift - create, delete, or modify an Amazon Redshift instance
redshift_facts - Gather facts about Redshift cluster(s)
redshift_subnet_group - manage Redshift cluster subnet groups
route53 - add or delete entries in Amazons Route53 DNS service
route53_facts - Retrieves route53 details using AWS methods
route53_health_check - add or delete health-checks in Amazons Route53 DNS service
route53_zone - add or delete Route53 zones
s3_bucket - Manage S3 buckets in AWS, Ceph, Walrus and FakeS3
s3_lifecycle - Manage s3 bucket lifecycle rules in AWS
s3_logging - Manage logging facility of an s3 bucket in AWS
s3_sync - Efficiently upload multiple files to S3
s3_website - Configure an s3 bucket as a website
sns - Send Amazon Simple Notification Service (SNS) messages
sns_topic - Manages AWS SNS topics and subscriptions
sqs_queue - Creates or deletes AWS SQS queues.
sts_assume_role - Assume a role using AWS Security Token Service and obtain temporary credentials
sts_session_token - Obtain a session token from the AWS Security Token Service
管理Openstack的模块:
os_auth - Retrieve an auth token
os_client_config - Get OpenStack Client config
os_flavor_facts - Retrieve facts about one or more flavors
os_floating_ip - Add/Remove floating IP from an instance
os_group - Manage OpenStack Identity Groups
os_image - Add/Delete images from OpenStack Cloud
os_image_facts - Retrieve facts about an image within OpenStack.
os_ironic - Create/Delete Bare Metal Resources from OpenStack
os_ironic_inspect - Explicitly triggers baremetal node introspection in ironic.
os_ironic_node - Activate/Deactivate Bare Metal Resources from OpenStack
os_keypair - Add/Delete a keypair from OpenStack
os_keystone_domain - Manage OpenStack Identity Domains
os_keystone_domain_facts - Retrieve facts about one or more OpenStack domains
os_keystone_endpoint - Manage OpenStack Identity service endpoints
os_keystone_role - Manage OpenStack Identity Roles
os_keystone_service - Manage OpenStack Identity services
os_network - Creates/removes networks from OpenStack
os_networks_facts - Retrieve facts about one or more OpenStack networks.
os_nova_flavor - Manage OpenStack compute flavors
os_nova_host_aggregate - Manage OpenStack host aggregates
os_object - Create or Delete objects and containers from OpenStack
os_port - Add/Update/Delete ports from an OpenStack cloud.
os_port_facts - Retrieve facts about ports within OpenStack.
os_project - Manage OpenStack Projects
os_project_access - Manage OpenStack compute flavors acceess
os_project_facts - Retrieve facts about one or more OpenStack projects
os_quota - Manage OpenStack Quotas
os_recordset - Manage OpenStack DNS recordsets
os_router - Create or delete routers from OpenStack
os_security_group - Add/Delete security groups from an OpenStack cloud.
os_security_group_rule - Add/Delete rule from an existing security group
os_server - Create/Delete Compute Instances from OpenStack
os_server_action - Perform actions on Compute Instances from OpenStack
os_server_facts - Retrieve facts about one or more compute instances
os_server_group - Manage OpenStack server groups
os_server_volume - Attach/Detach Volumes from OpenStack VM’s
os_stack - Add/Remove Heat Stack
os_subnet - Add/Remove subnet to an OpenStack network
os_subnets_facts - Retrieve facts about one or more OpenStack subnets.
os_user - Manage OpenStack Identity Users
os_user_facts - Retrieve facts about one or more OpenStack users
os_user_group - Associate OpenStack Identity users and groups
os_user_role - Associate OpenStack Identity users and roles
os_volume - Create/Delete Cinder Volumes
os_zone - Manage OpenStack DNS zones
五、Ansible如何获取云主机的inventory
Inventory即清单。记录的是Ansible要执行任务的主机列表。
在物理机环境中,主机IP比较少,可以放到静态配置文件中:
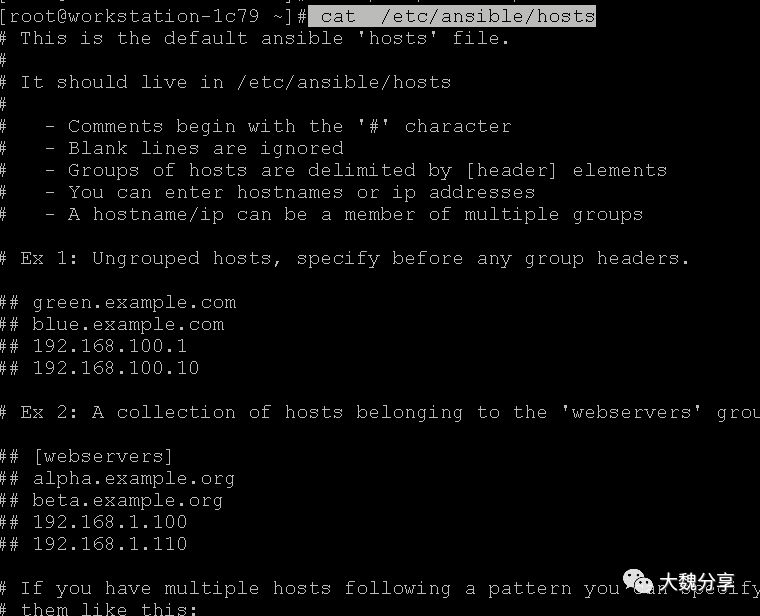
然后在执行playbook的时候,通过-i参数指定inventory文件。
获取动态清单有两种方法:
1.通过python编写动态清单脚本
2.通过ansible的gather_facts和add_host获取。
第一种方法
我们需要针对不同的云,编写不同的动态inventory脚本。
很难???有点。
还好,在github上有大量的范例可供参考和修改。记住,这就是开源的好处!
(https://github.com/ansible/ansible/tree/devel/contrib/inventory)
我们以aws举例。相关的两个文件是:ec2.ini和ec2.py。
ec2.ini是配置文件,定义了你要aws环境的配置变量,如:
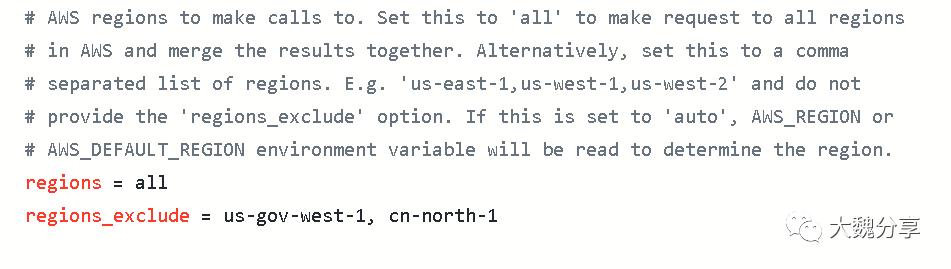
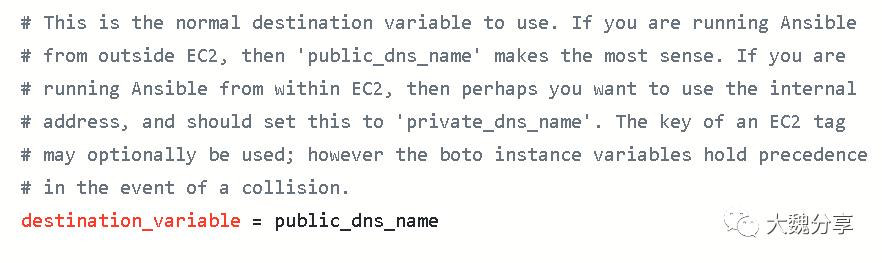

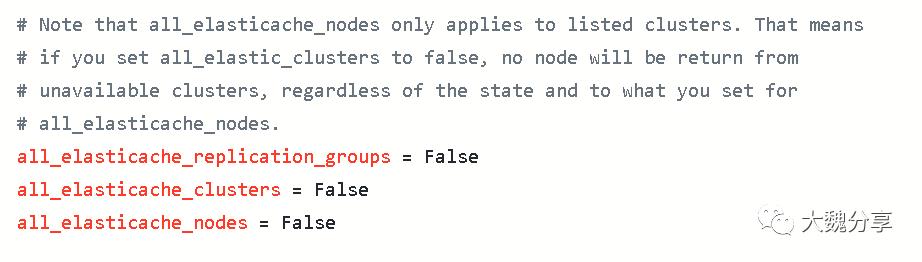
而ec2.py是获取动态信息的执行脚本。我们看其中一段内容,它表示执行这个脚本,从aws上获取如下信息并返回:
When run against a specific host, this script returns the following variables:
- ec2_ami_launch_index
- ec2_architecture
- ec2_association
- ec2_attachTime
- ec2_attachment
- ec2_attachmentId
- ec2_block_devices
- ec2_client_token
- ec2_deleteOnTermination
- ec2_description
- ec2_deviceIndex
- ec2_dns_name
- ec2_eventsSet
- ec2_group_name
- ec2_hypervisor
- ec2_id
- ec2_image_id
- ec2_instanceState
- ec2_instance_type
- ec2_ipOwnerId
- ec2_ip_address
- ec2_item
- ec2_kernel
- ec2_key_name
- ec2_launch_time
- ec2_monitored
- ec2_monitoring
- ec2_networkInterfaceId
- ec2_ownerId
- ec2_persistent
- ec2_placement
- ec2_platform
- ec2_previous_state
- ec2_private_dns_name
- ec2_private_ip_address
- ec2_publicIp
- ec2_public_dns_name
- ec2_ramdisk
- ec2_reason
- ec2_region
- ec2_requester_id
- ec2_root_device_name
- ec2_root_device_type
- ec2_security_group_ids
- ec2_security_group_names
- ec2_shutdown_state
- ec2_sourceDestCheck
- ec2_spot_instance_request_id
- ec2_state
- ec2_state_code
- ec2_state_reason
- ec2_status
- ec2_subnet_id
- ec2_tenancy
- ec2_virtualization_type
- ec2_vpc_id
而通过动态清单的方式获取的信息,不仅可以被inventory使用,还可以被module使用。
第二种方法
1.信息收集(本地方式是gather_facts,openstack通过os_server_facts模块实现)
2.add_hosts将收集到的信息推送到内存清单;add_hosts是ansible的一个模块。
(http://docs.ansible.com/ansible/latest/modules/add_host_module.html?highlight=add_host)
add_hosts的作用:add a host (and alternatively a group) to the ansible-playbook in-memory inventory.
社区有对应的用例:
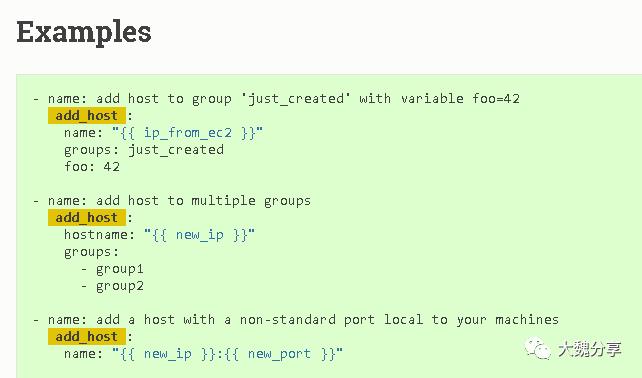
信息收集和add_hosts需要一起用,才能在内存中添加动态清单。
我们举个例子:
在这个playbook中,先通过gather_facts收集信息。然后add_host获取ipv4.address:
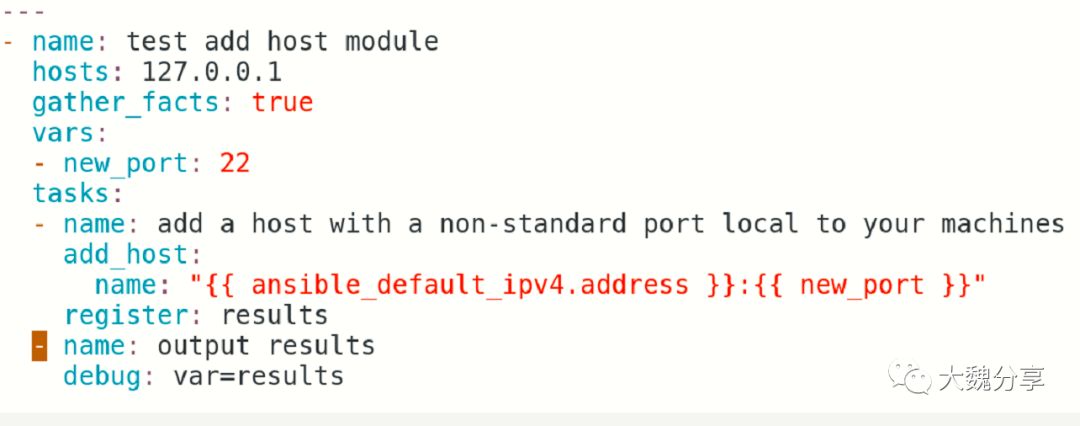
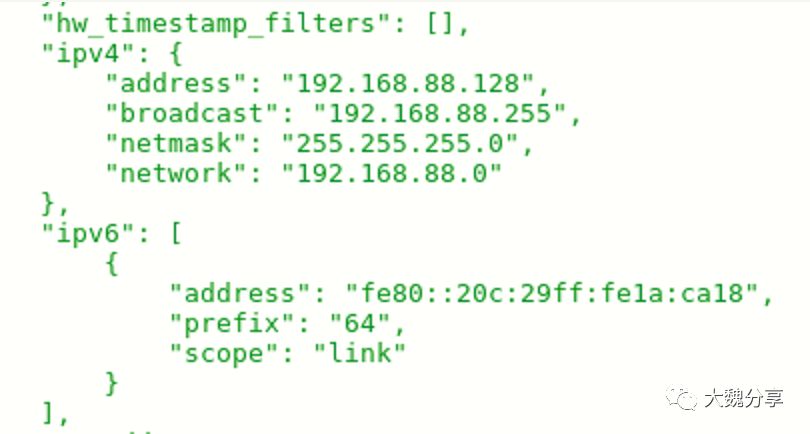
而这个playbook获取到的信息(我在实验中通过ansible setup输出),要获取的信息就是192.168.88.128的IP信息,它的key是
ansible_default_ipv4.address,层级目录可以在下图中看到:
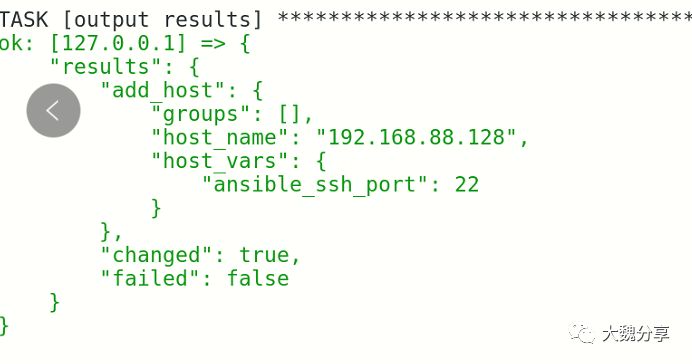
我们看一下playbook的执行结果,和预期相同:
至于在云中获取动态清单的方法选择,AWS中建议使用python方式(因为ansible的模块可以调用aws的tag);在Openstack中,建议使用gather_facts和add_hosts,ansible很难简单调用openstack的tag。
八、实验展示Ansible对Openstack的管理
Ansible管理的Openstack环境拓扑如下:
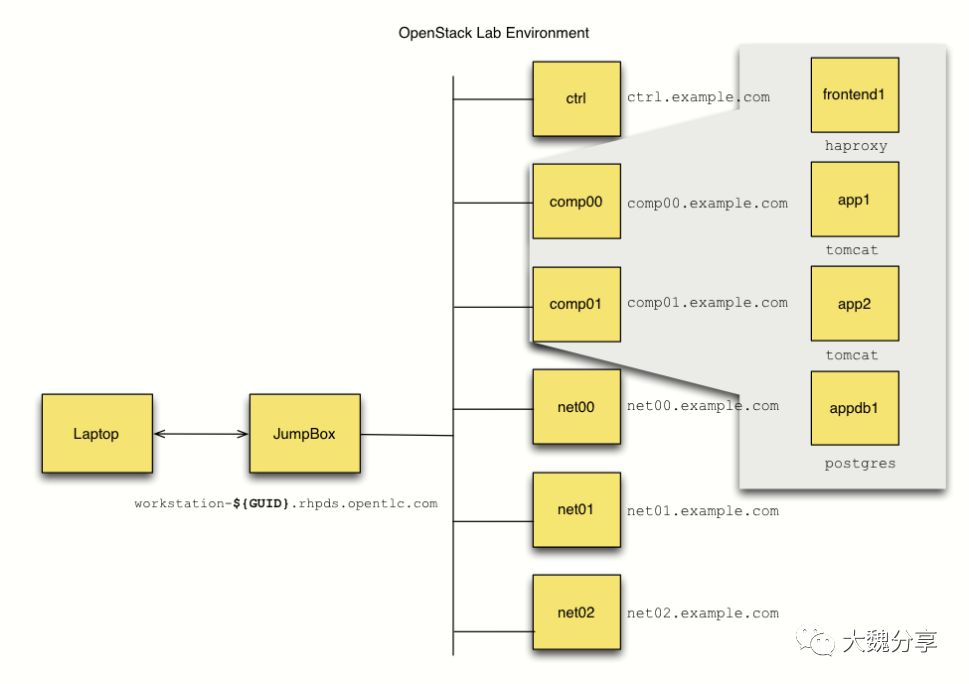
在上图中,laptop是自己的笔记本电脑,JumpBox是堡垒机,用于管理Openstack,上面将会被部署Openstack client和Ansible等。
从笔记本到堡垒机,堡垒机到Openstack实例的通讯如下图:
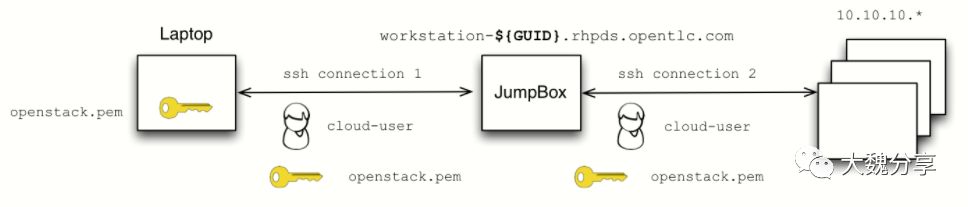
Openstack的节点:
控制节点:
OpenStack controller host: ctrl.example.com
计算节点:
OpenStack infrastructure:
Compute node 00: comp00.example.com
Compute node 01: comp01.example.com
网络节点
Network node 00: net00.example.com
Network node 01: net01.example.com
Network node 02: net02.example.com
堡垒机上安装openstack的client:
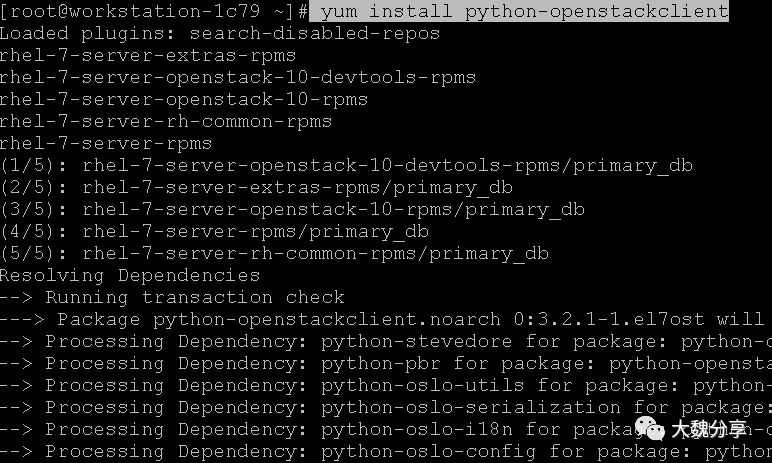
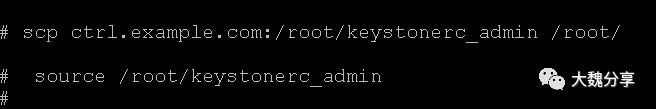
将keystonerc_admin从管理节点拷贝。
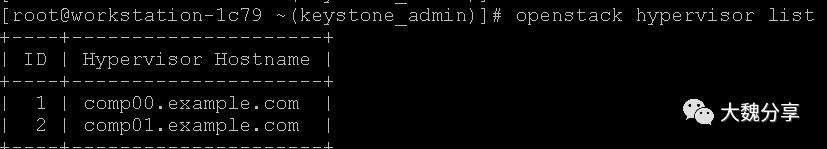
查看计算节点:
九、配置堡垒机
在堡垒机上获取openstack的公钥,然后倒入本地认证:
在堡垒机上安装必要的软件:
安装shade:
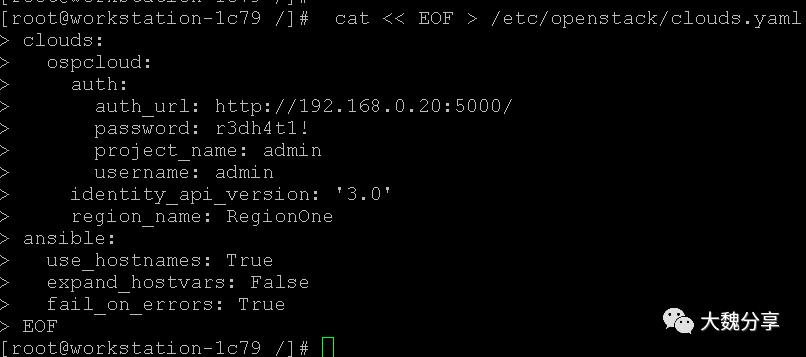
配置堡垒机的clouds.yaml文件,以便堡垒机可以通过shade library与Openstack连接:
接下来,编写 rhel-guest镜像加载的playbook,这个后面会用到执行playbook:
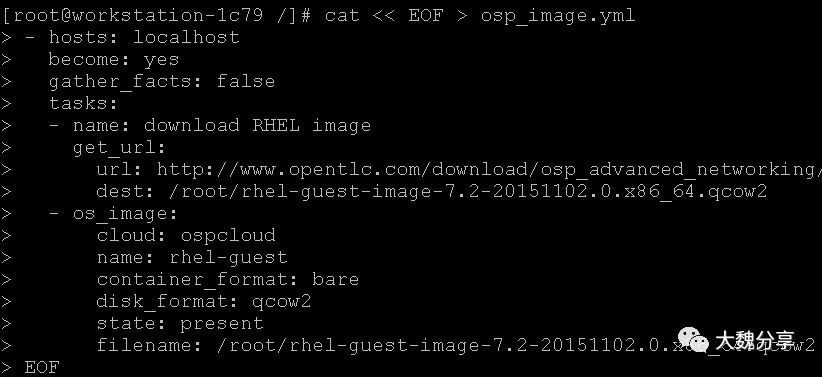
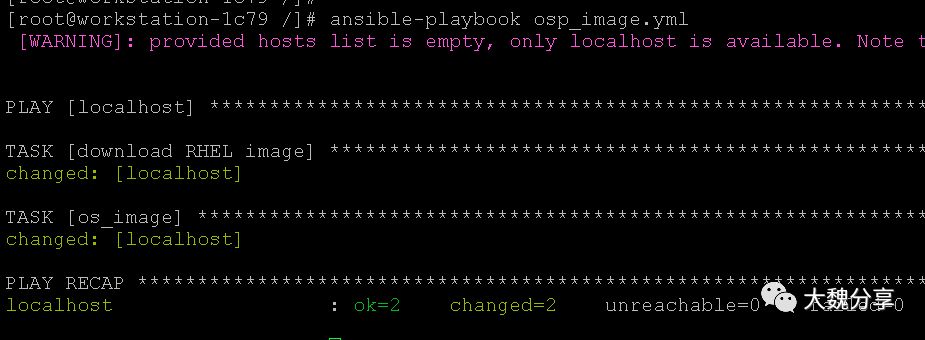
执行playbook:
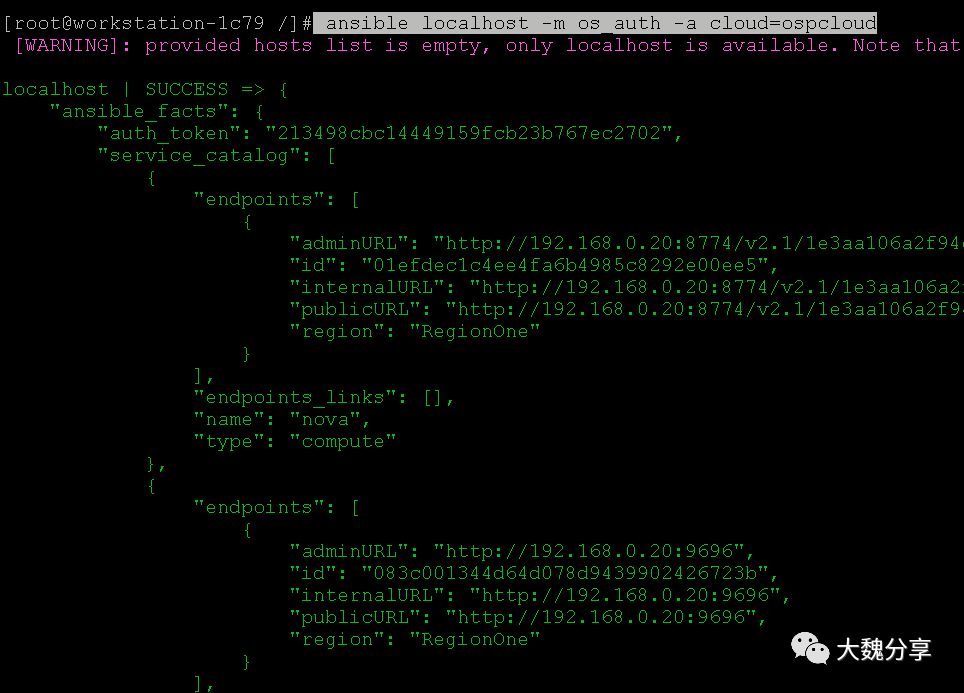
验证是否可以获取openstack的token:
验证是否可以获取openstack的用户列表:
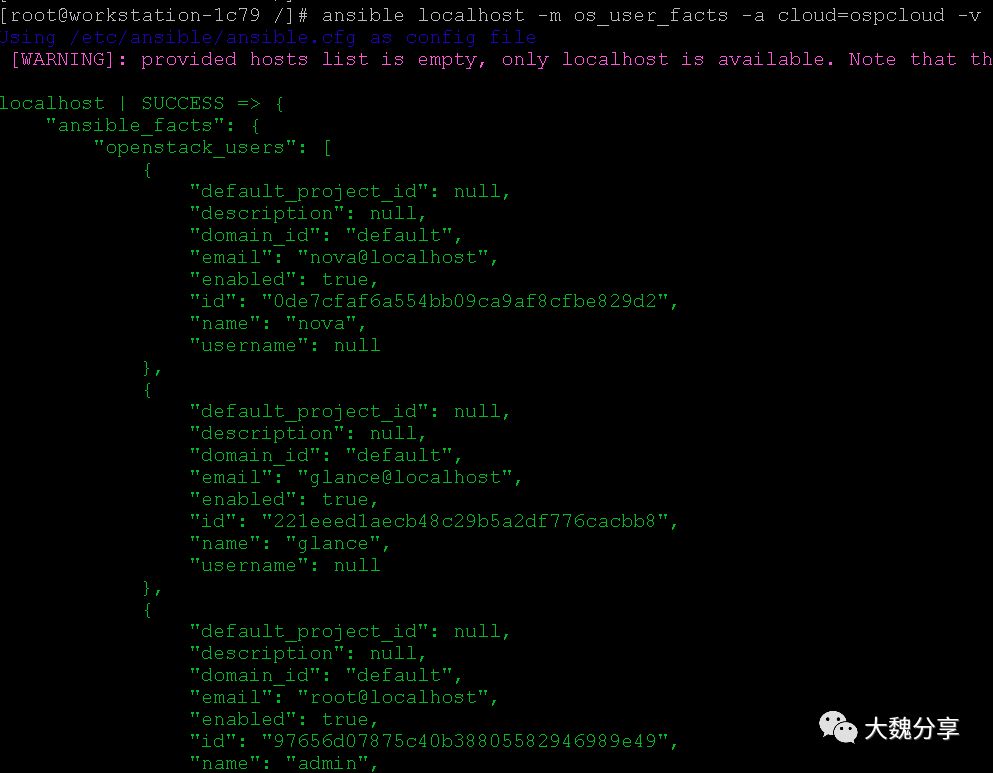
截至到目前,堡垒机与Openstack的通讯没有问题。
九、通过Ansible为Openstack一键部署多实例应用
在本实验中,我们将通过一个大的playbook,进行Openstack的多个配置,配置内容如下:
1.网络配置
public network和一个private network,以及rivate network 和internal physical network之间的路由器。
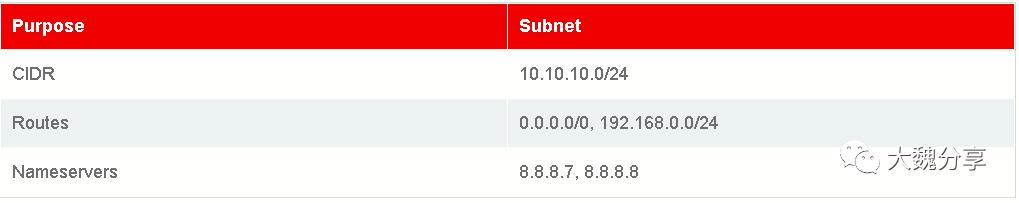
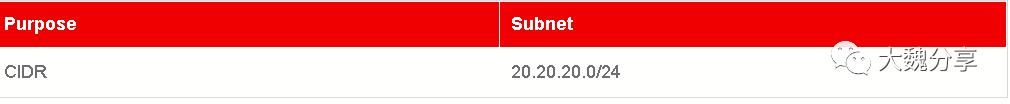
2.创建Key Pairs
3.创建 customer flavor
4.创建四个应用(四个虚拟机实例上)Application 1、Application 2、Database、Front End
5.ocp——facts role收集信息
git clone https://github.com/prakhar1985/good_example
我们看这个playbook的主任务:
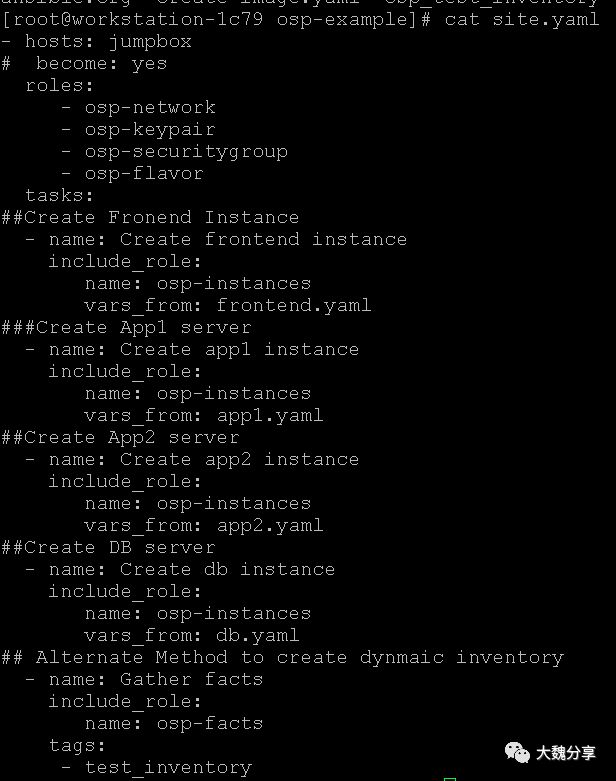
在上图中,我们可以很清楚地看到,playbook做的事情是在堡垒机上执行playbook,调用9个role,先调用4个roles做如下组件的配置:
osp-network、osp-keypair、osp-security group、osp-flavor
由于篇幅有限,我们只看osp-network的role:
[root@workstation-1c79 tasks]# cat main.yml
- os_network:
cloud: ospcloud
state: present
name: ext_network
external: true
- os_subnet:
cloud: ospcloud
state: present
network_name: ext_network
name: external_subnet
cidr: 10.10.10.0/24
dns_nameservers:
- 8.8.8.7
- 8.8.8.8
host_routes:
- destination: 0.0.0.0/0
nexthop: 10.10.10.0
- destination: 192.168.0.0/24
nexthop: 192.168.0.0
- os_network:
cloud: ospcloud
state: present
name: int_network
external: false
register: internal
tags:
- tested
- os_subnet:
cloud: ospcloud
state: present
network_name: int_network
name: int_subnet
cidr: 20.20.20.0/24
dns_nameservers:
- 8.8.8.7
- 8.8.8.8
host_routes:
- destination: 0.0.0.0/0
nexthop: 192.168.0.0
- destination: 192.168.0.0/24
nexthop: 192.168.0.0
- os_router:
cloud: ospcloud
state: present
name: router1
network: ext_network
external_fixed_ips:
- subnet: external_subnet
interfaces:
- int_subnet
上面的role就是按照之前我们的定义,创建两个openstack网络和一个router。
执行完四个role以后,就完成了对Openstack如下组件的配置:osp-network、osp-keypair、osp-security group、osp-flavor。
然后site.yml再调用另外几个role做: Create frontend instance、Create App1 server、Create App2 server、Create DB server的操作。
我们执行site.yaml,查看输出结果。
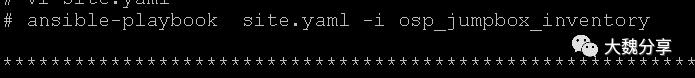
首先,playbook会按照对role的调用,依次创建网络、创建key pair、创建安全组
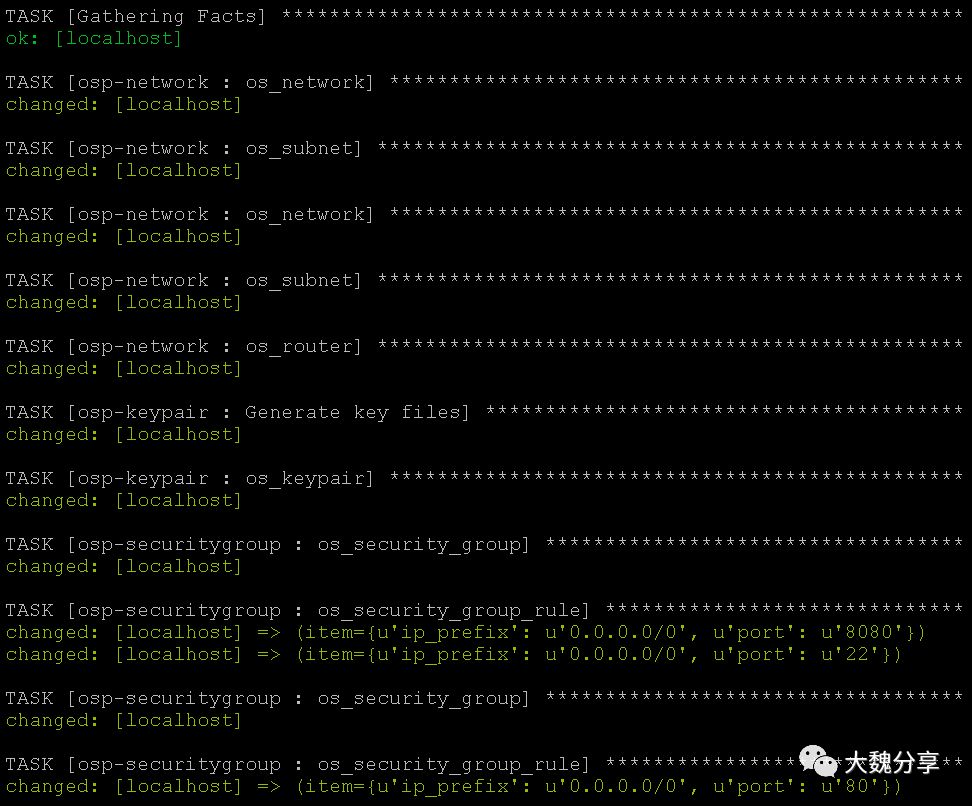
接下来,创建flavor:
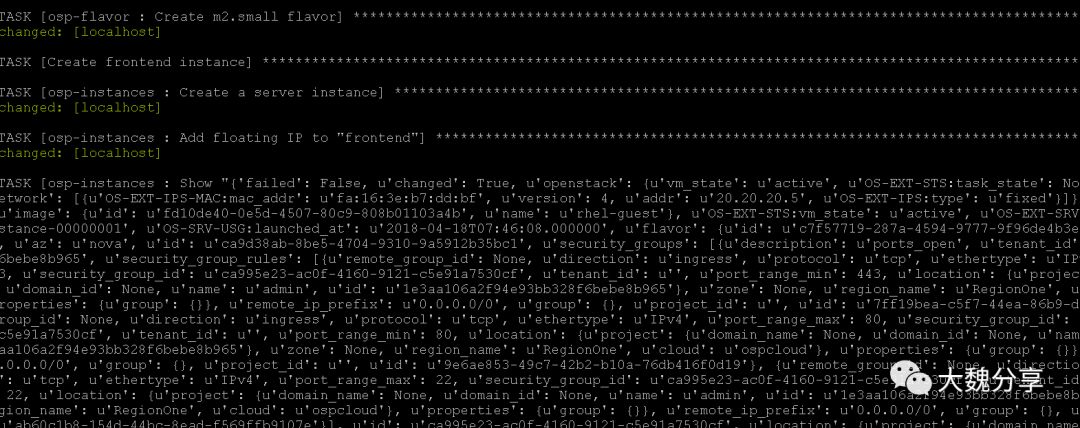
至此,基本配置的四个role已经执行完毕。
接下来,部署前端应用。
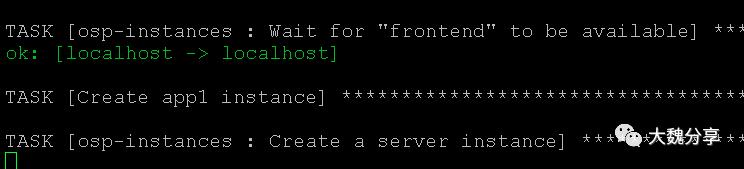
部署app1实例:
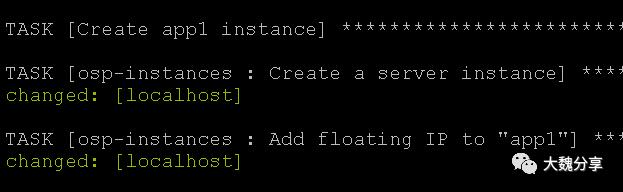
给app1实例增加浮动IP:
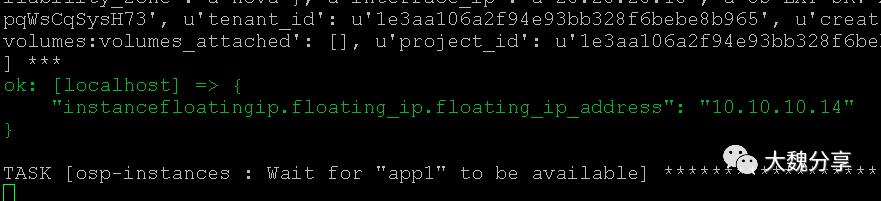
创建app2实例:
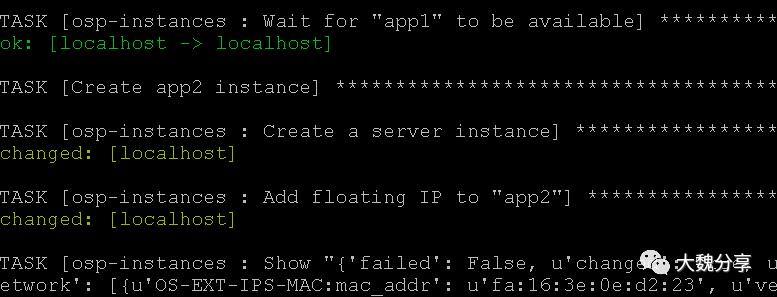
给app2实例增加浮动IP
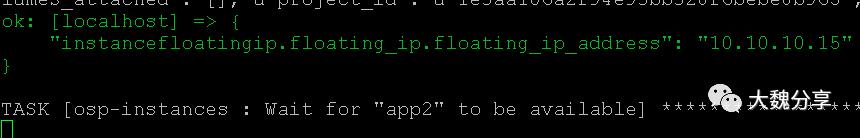
创建db实例:
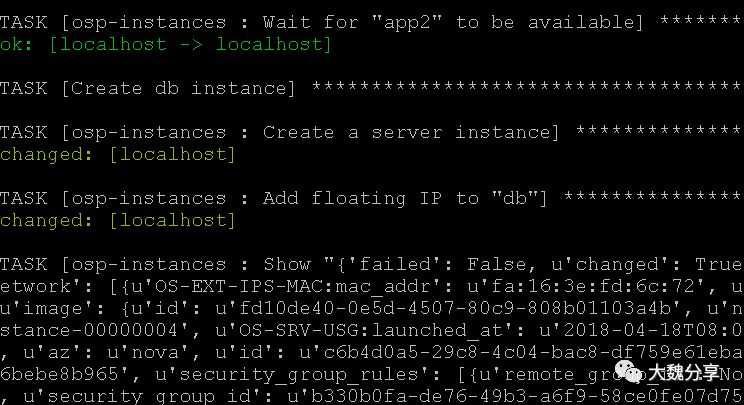
给db实例增加浮动IP:
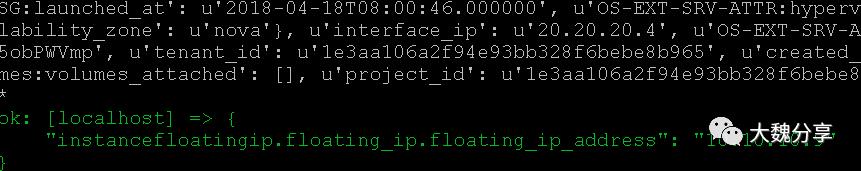
最后,通过add host收集清单,添加到动态清单中:
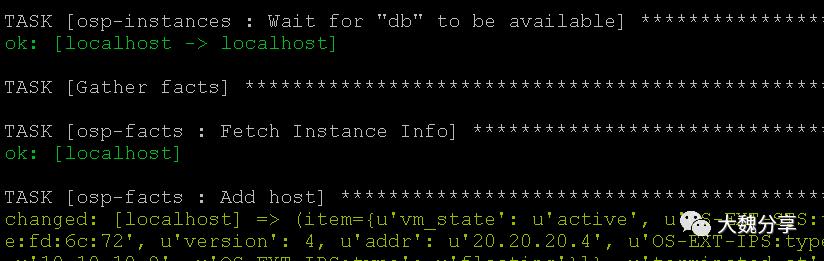
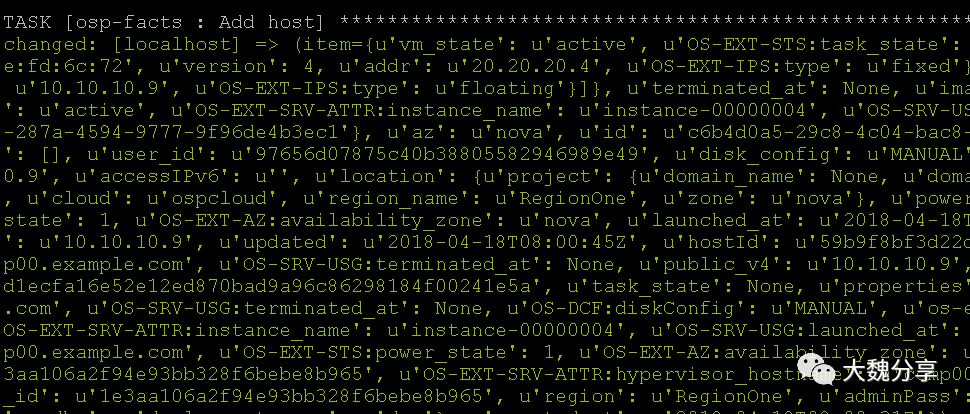
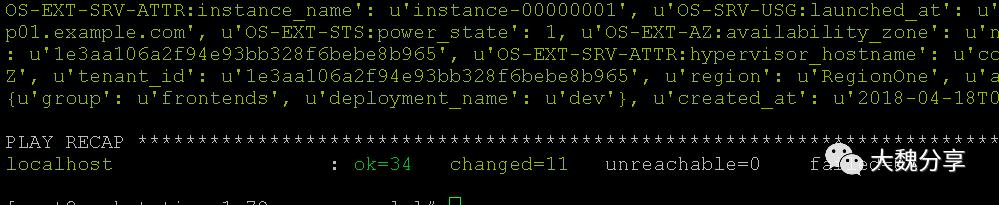
最终playbook执行成功:
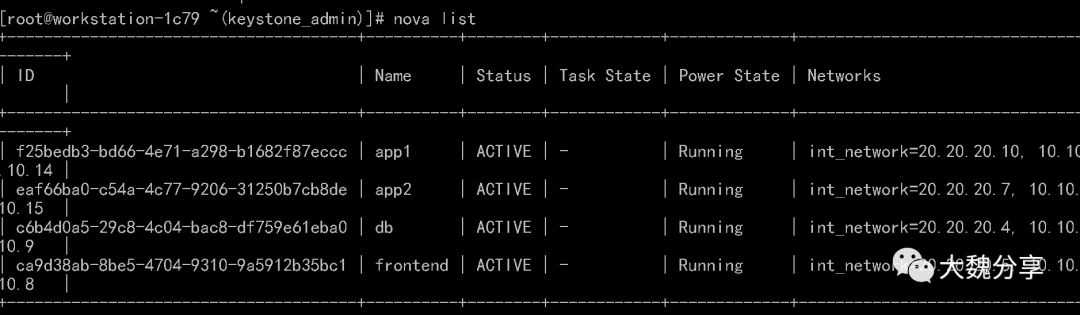
登录Openstack,查看部署好的实例:
九、通过Ansible在Openstack利用动态清单部署三层应用
(https://github.com/tonykay/good-ansible)
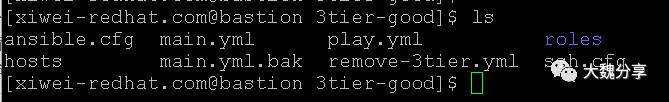
这个playbook的目录结构如下:
我们看一下主任务:main.yml
| --- | |
| - hosts: jumpbox | |
| gather_facts: false | |
| roles: | |
| - {name: osp-facts, when: ansible_product_name == 'OpenStack Compute'} | |
| # Setup front-end load balancer tier | |
| - name: setup load-balancer tier | |
| hosts: frontends | |
| become: yes | |
| roles: | |
| - {name: base-config, tags: base-config} | |
| - {name: lb-tier, tags: [lbs, haproxy]} | |
| # Setup application servers tier | |
| - name: setup app tier | |
| hosts: apps | |
| become: yes | |
| gather_facts: false | |
| roles: | |
| - {name: base-config, tags: base-config} | |
| - {name: app-tier, tags: [apps, tomcat]} | |
| # Setup database tier | |
| - name: setup database tier | |
| become: yes | |
| hosts: appdbs | |
| roles: | |
| - {name: base-config, tags: base-config} | |
| - {name: geerlingguy.postgresql, tags: [dbs, postgres]} |
这个yaml做的事情,第一步,调用osp-facts这个role获取动态清单。我们查看一下这个role:
这个role是使用os_server_facts和Add host获取动态清单(如果没有收集动态清单,则使用静态清单的变量定义)。
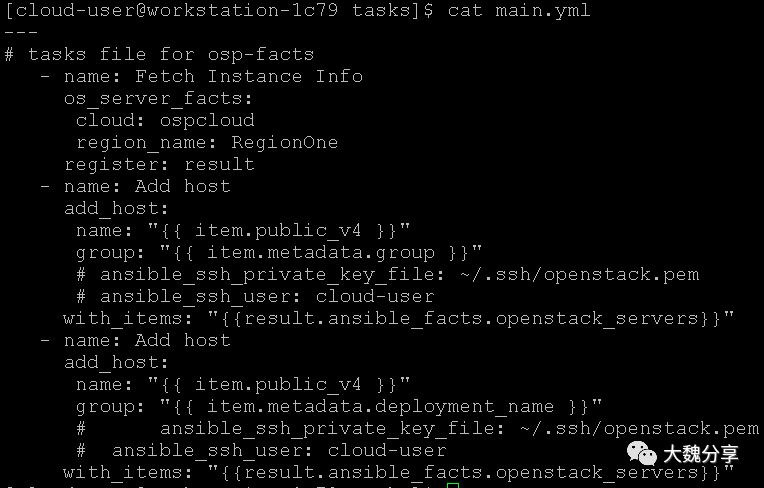
获取变量的key是:public_v4、metadata.group、metadata.deployment_name,而result.ansible_facts.openstack_servers是循环前缀。
获取完动态心以后,继续执行roles:配置load-balancer tier、app tier、 database tier。然后,这三个大的任务,分别调用写好的roles。
执行playbook:
$ ansible-playbook main.yml -i inventory/hosts --ask-vault-pass
执行playbook后,第一步是调用role osp-facts收集信息,然后以变量方式注入到roles变量中:
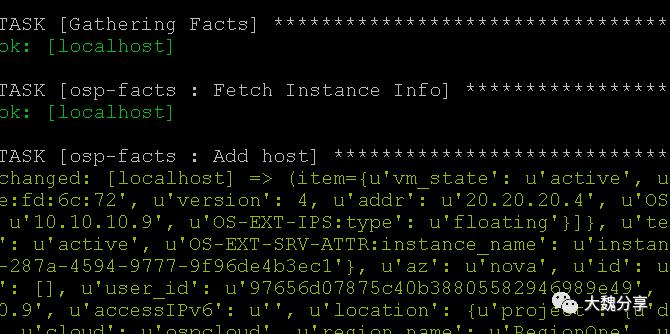
例如public_v4信息:
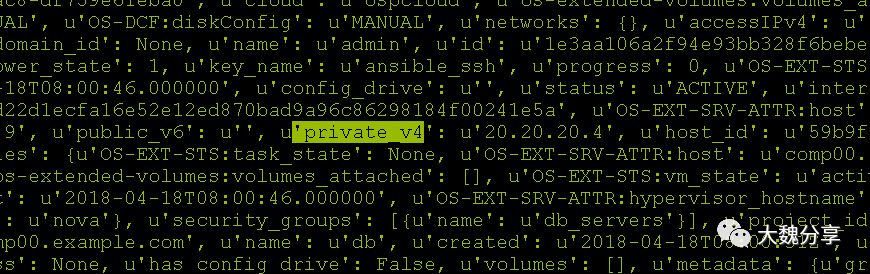
具体的安装步骤较长,这里不再赘述。实际上就是将几个组件安装到Openstack实例中。
十、有了Ansible,你的运维也可以很帅
通过Ansible对物理机、虚拟机、私有云、公有云的一体化运维,运维人员的压力不仅可以减小,还可以很拉风,状态是这样的:

而不再是这样的:

魏新宇
"大魏分享"运营者、红帽资深解决方案架构师
专注开源云计算、容器及自动化运维在金融行业的推广
拥有红帽RHCE/RHCA、VMware VCP-DCV、VCP-DT、VCP-Network、VCP-Cloud、ITIL V3、Cobit5、C-STAR、AIX、HPUX等相关认证。
文章打赏随意(转发和赞赏都是对作者原创的鼓励):
更多精彩内容,欢迎继续关注大魏分享:
以上是关于Ansible如何管理你的云:AWSOpenstack?你的运维也可以很帅!的主要内容,如果未能解决你的问题,请参考以下文章
Ansible 学习总结—— Ansible 状态管理相关知识总结