Xerror 全自动渗透测试工具 漏洞扫描+报告生成
Posted 刹客网络科技资讯
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Xerror 全自动渗透测试工具 漏洞扫描+报告生成相关的知识,希望对你有一定的参考价值。
Xerror简介
Xerror是一种自动渗透工具,它将帮助安全专业人员和非专业人员自动执行其渗透测试任务。
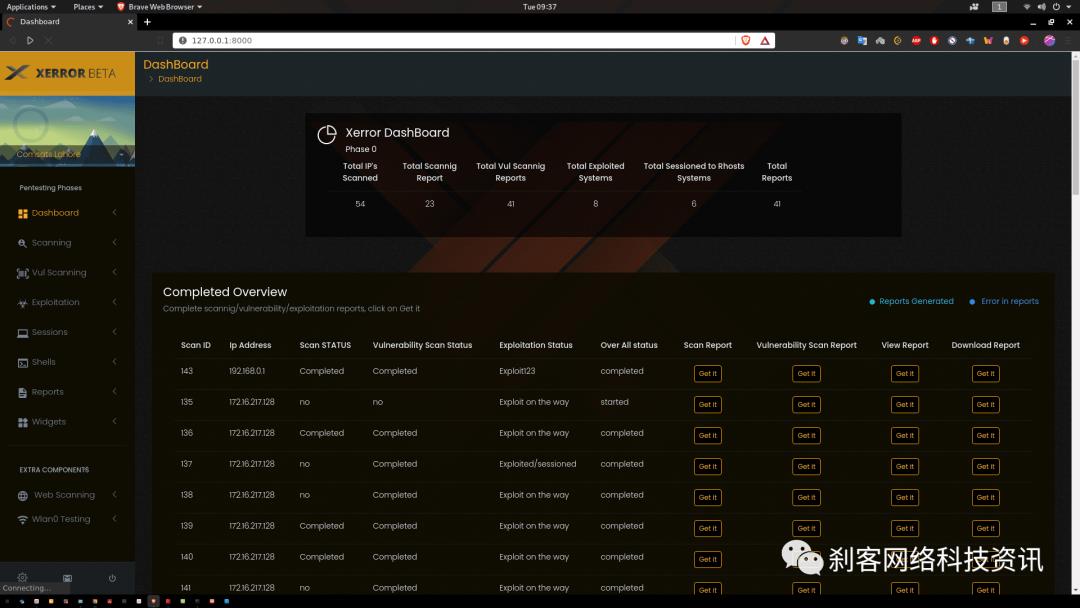
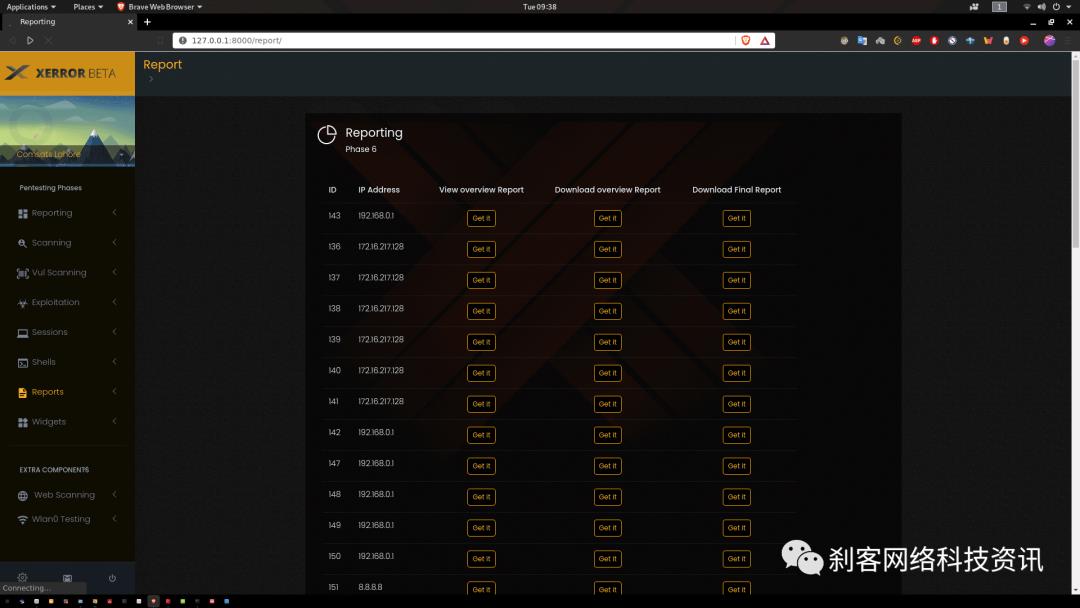
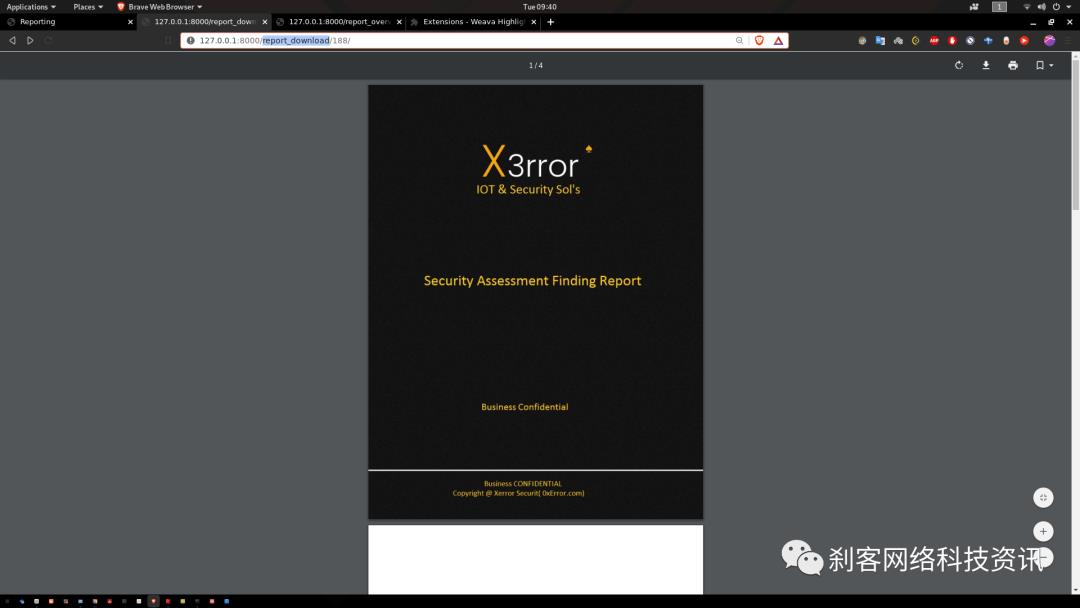
Xerror将执行所有测试,最后为主管和分析师生成两个报告。
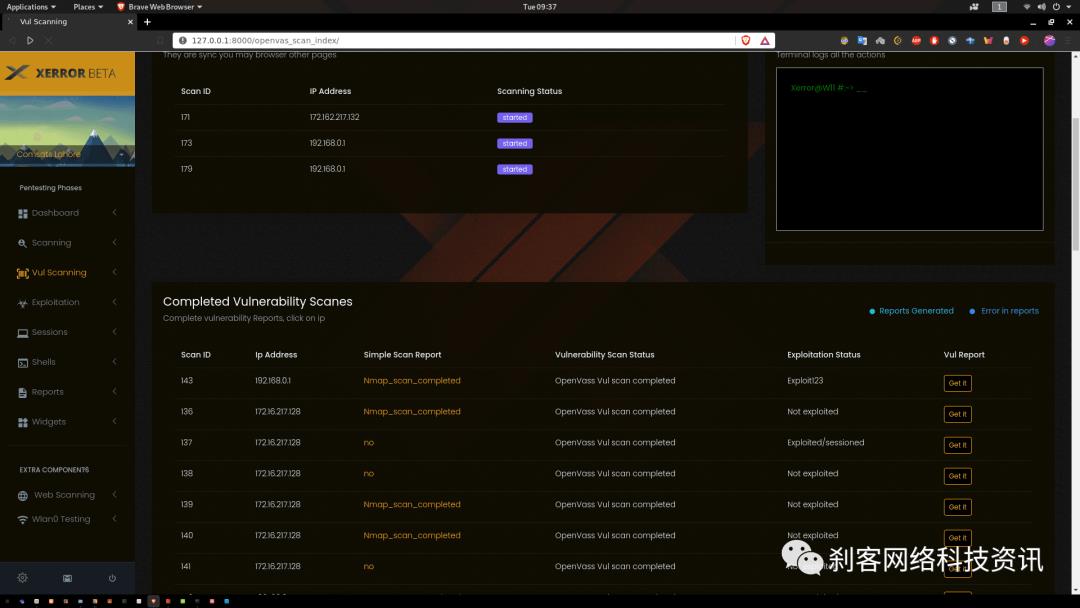
Xerror提供了易于使用的GUI菜单驱动选项,内部支持openVas进行漏洞扫描,支持Metasploit进行漏洞利用,并在成功利用后提供基于GUI的选项,例如Meterpreter sessoins。
以python为主要构建。
Xerror以python2为主要语言,以Django2为网络框架,以及celery服务器和Redis srver上的websockets(django通道)构建以实现异步。它支持Djanog默认模板enging语言,即jinga2和jquery。
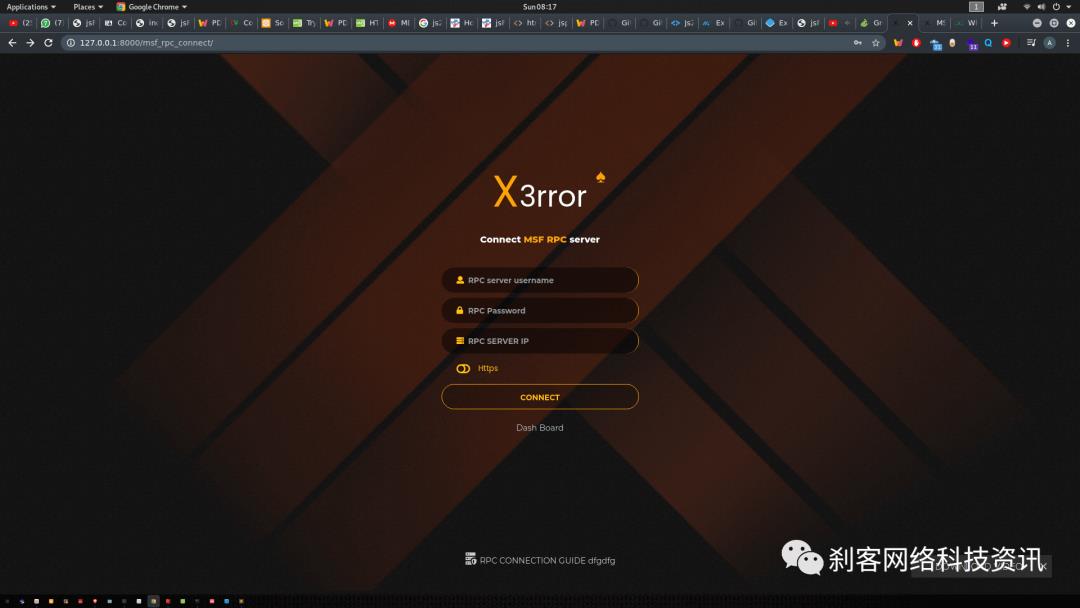
Xerror项目地址
GitHub: https://github.com/Chudry/Xerror
安装条件
amqp==1.4.9
anyjson==0.3.3
asgi-redis==0.14.0
asgiref==0.14.0
autobahn==0.15.0
billiard==3.3.0.23
celery==3.1.23
channels==0.17.0
daphne==0.14.2
Django==1.11.29
kombu==3.0.35
msgpack-python==0.4.7
pytz==2016.6.1
redis==2.10.5
six==1.10.0
txaio==2.5.1
zope.interface==4.2.0
gunicorn==19.7.1
openvas_lib
pymetasploit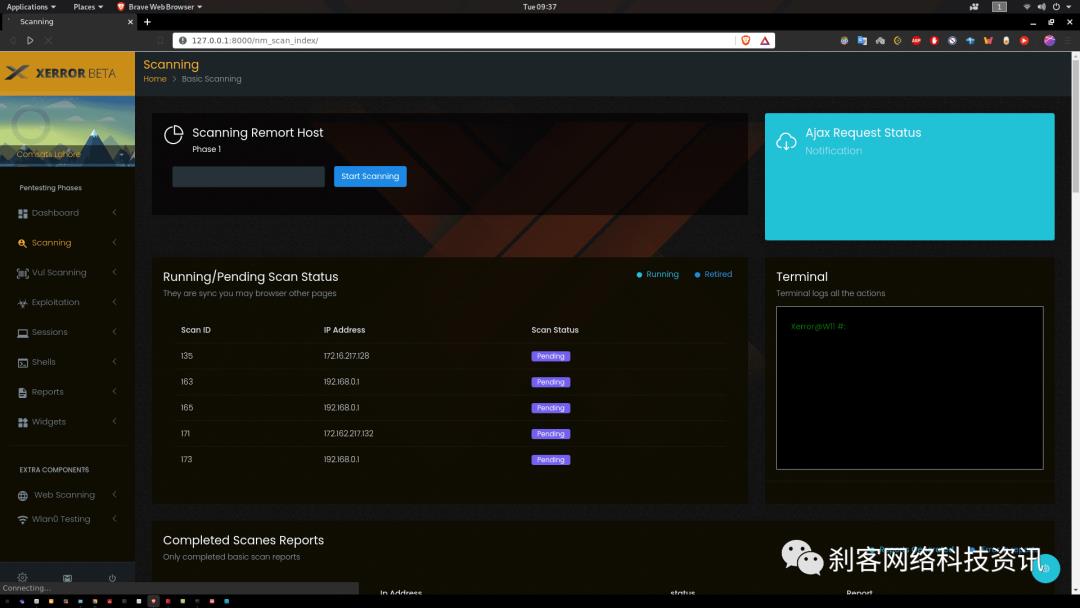
Xerror下载地址
①迅雷网盘:https://pan.xunlei.com/s/VMMsGyB9t5OO4UyLk8IHRxuZA1提取码: kZOG
②蓝奏云: https://waf.lanzoui.com/imGreipobzi
③GitHub: github.com/Chudry/Xerror
Xerror使用方法
①使用如下命令激活虚拟环境
souce env/bin/activate②启动redis服务器
service redis-server start③启动python服务
cd xerror
python mana.py runserver④启动celery服务器
cd xerror
celery -A xerror worker -l info⑤启动msfrpc服务 (metasploit 远程调用服务)
msfrpcd -P 123 -S -a 127.0.0.1⑥启动openvas服务器以将OMP服务器凭据默认设置为admin@admin 127.0.0.1:9392
这是xerror 测试版本,很快将上传完整版本,并提供完整解释和每个步骤的详细信息…
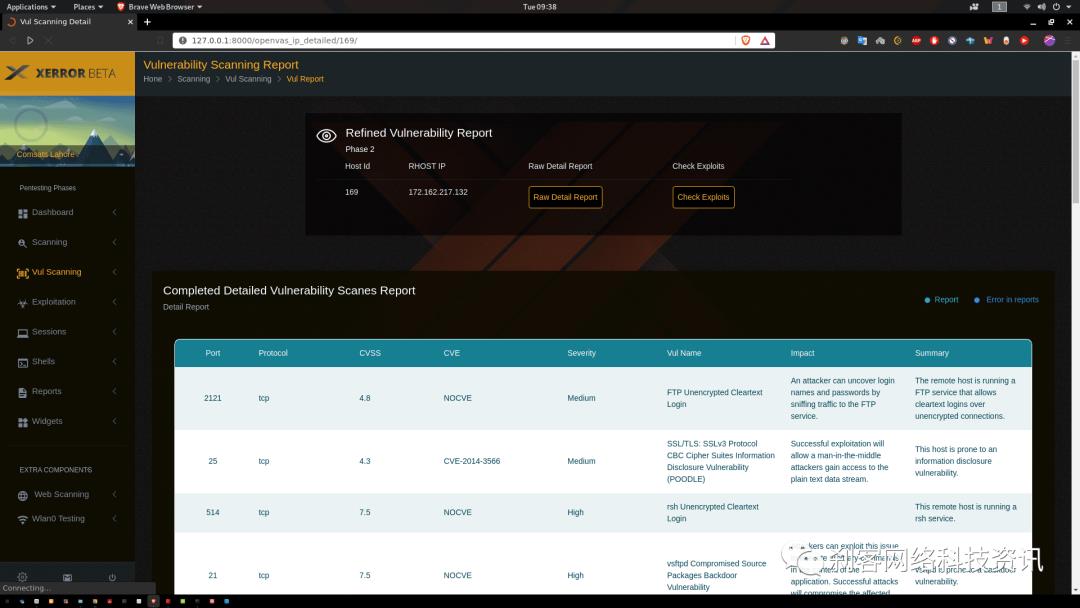
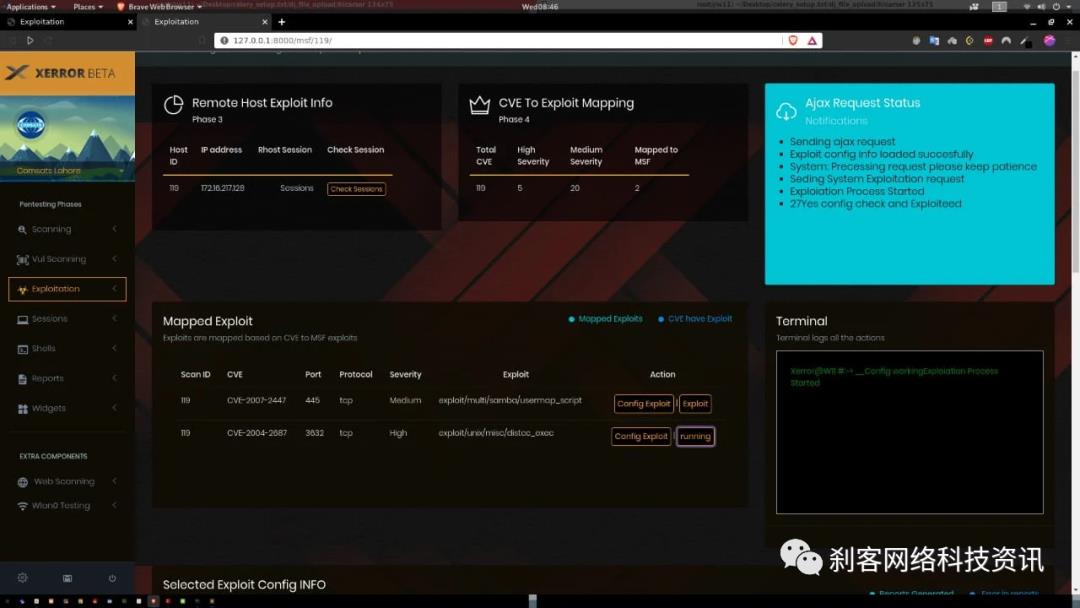
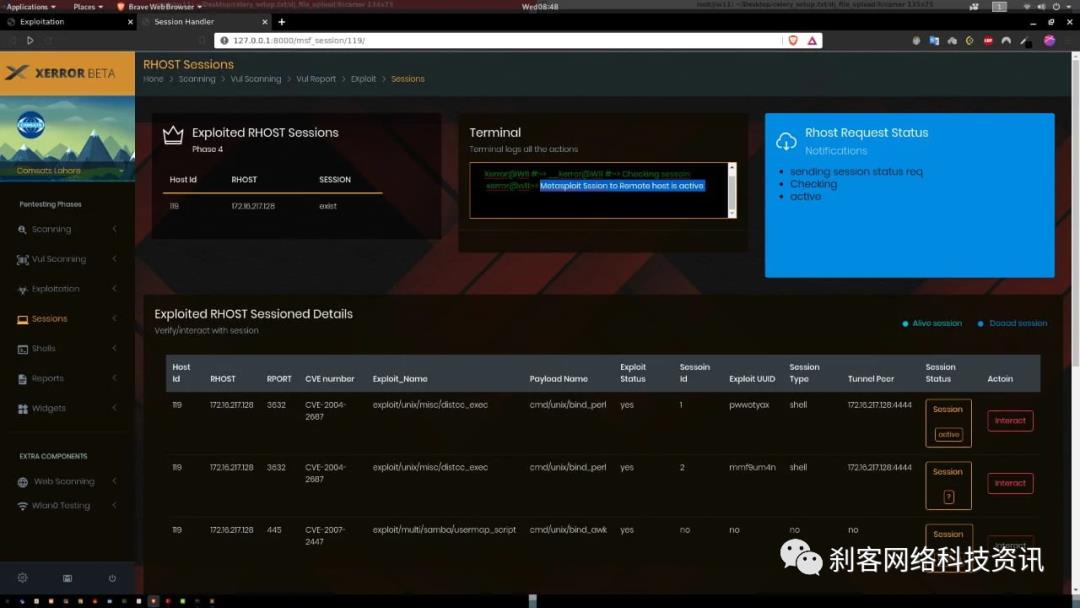
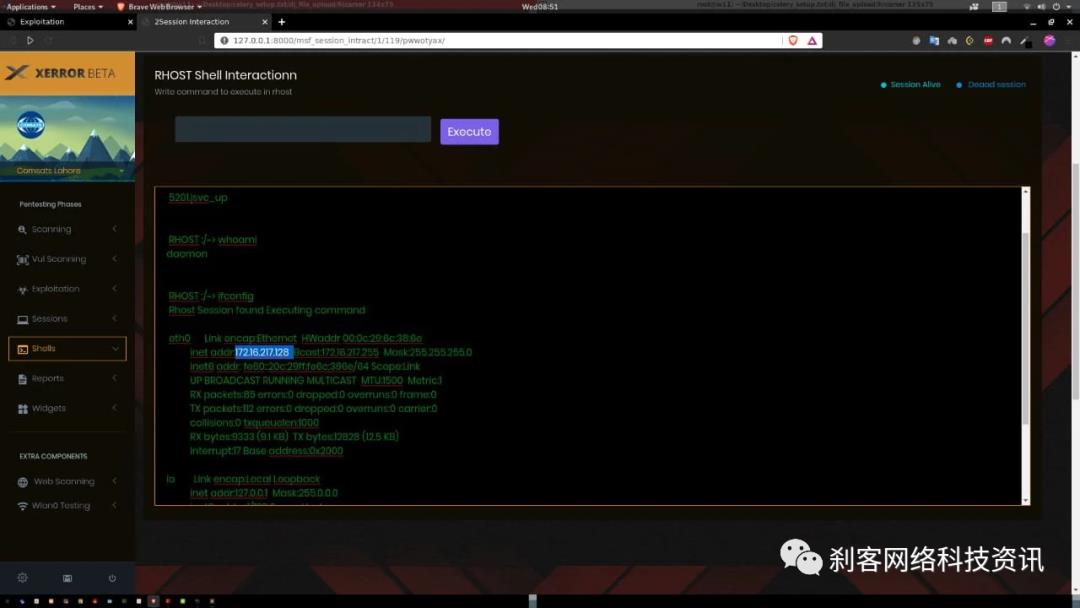
该版本具有的metasploit模块列表
Module References
Module Reference
------ ---------
auxiliary/admin/2wire/xslt_password_reset CVE-2007-4387
auxiliary/admin/android/google_play_store_uxss_xframe_rce CVE-2014-6041
auxiliary/admin/backupexec/dump CVE-2005-2611
auxiliary/admin/backupexec/registry CVE-2005-0771
auxiliary/admin/cisco/cisco_asa_extrabacon CVE-2016-6366
auxiliary/admin/cisco/cisco_dcnm_download CVE-2019-1619
auxiliary/admin/cisco/cisco_dcnm_download CVE-2019-1621
auxiliary/admin/cisco/cisco_secure_acs_bypass CVE-2011-0951
auxiliary/admin/cisco/vpn_3000_ftp_bypass CVE-2006-4313
auxiliary/admin/db2/db2rcmd CVE-2004-0795
auxiliary/admin/edirectory/edirectory_dhost_cookie CVE-2009-4655
auxiliary/admin/edirectory/edirectory_edirutil CVE-2008-0926
auxiliary/admin/emc/alphastor_devicemanager_exec CVE-2008-2157
auxiliary/admin/emc/alphastor_librarymanager_exec CVE-2008-2157
auxiliary/admin/hp/hp_data_protector_cmd CVE-2011-0923
auxiliary/admin/hp/hp_ilo_create_admin_account CVE-2017-12542
auxiliary/admin/hp/hp_imc_som_create_account CVE-2013-4824
auxiliary/admin/http/allegro_rompager_auth_bypass CVE-2014-9222
auxiliary/admin/http/arris_motorola_surfboard_backdoor_xss CVE-2015-0964
auxiliary/admin/http/arris_motorola_surfboard_backdoor_xss CVE-2015-0965
auxiliary/admin/http/arris_motorola_surfboard_backdoor_xss CVE-2015-0966
auxiliary/admin/http/axigen_file_access CVE-2012-4940
auxiliary/admin/http/cfme_manageiq_evm_pass_reset CVE-2013-2050
auxiliary/admin/http/cnpilot_r_cmd_exec CVE-2017-5259
auxiliary/admin/http/cnpilot_r_fpt CVE-2017-5261
auxiliary/admin/http/foreman_openstack_satellite_priv_esc CVE-2013-2113
auxiliary/admin/http/gitstack_rest CVE-2018-5955
auxiliary/admin/http/iis_auth_bypass CVE-2010-2731
auxiliary/admin/http/intersil_pass_reset CVE-2007-4915
auxiliary/admin/http/iomega_storcenterpro_sessionid CVE-2009-2367
auxiliary/admin/http/jboss_bshdeployer CVE-2010-0738
auxiliary/admin/http/jboss_deploymentfilerepository CVE-2010-0738
auxiliary/admin/http/jboss_seam_exec CVE-2010-1871
auxiliary/admin/http/joomla_registration_privesc CVE-2016-8869
auxiliary/admin/http/joomla_registration_privesc CVE-2016-8870
auxiliary/admin/http/kaseya_master_admin CVE-2015-6922
auxiliary/admin/http/katello_satellite_priv_esc CVE-2013-2143
auxiliary/admin/http/manage_engine_dc_create_admin CVE-2014-7862
auxiliary/admin/http/manageengine_dir_listing CVE-2014-7863
auxiliary/admin/http/manageengine_file_download CVE-2014-7863
auxiliary/admin/http/manageengine_pmp_privesc CVE-2014-8499
auxiliary/admin/http/mantisbt_password_reset CVE-2017-7615
auxiliary/admin/http/mutiny_frontend_read_delete CVE-2013-0136
auxiliary/admin/http/netflow_file_download CVE-2014-5445
auxiliary/admin/http/netgear_auth_download CVE-2016-1524
auxiliary/admin/http/netgear_wnr2000_pass_recovery CVE-2016-10175
auxiliary/admin/http/netgear_wnr2000_pass_recovery CVE-2016-10176
auxiliary/admin/http/novell_file_reporter_filedelete CVE-2011-2750
auxiliary/admin/http/nuuo_nvrmini_reset CVE-2016-5676
auxiliary/admin/http/openbravo_xxe CVE-2013-3617
auxiliary/admin/http/pfadmin_set_protected_alias CVE-2017-5930
auxiliary/admin/http/rails_devise_pass_reset CVE-2013-0233
auxiliary/admin/http/scrutinizer_add_user CVE-2012-2626
auxiliary/admin/http/sophos_wpa_traversal CVE-2013-2641
auxiliary/admin/http/supra_smart_cloud_tv_rfi CVE-2019-12477
auxiliary/admin/http/sysaid_admin_acct CVE-2015-2993
auxiliary/admin/http/sysaid_file_download CVE-2015-2996
auxiliary/admin/http/sysaid_file_download CVE-2015-2997
auxiliary/admin/http/sysaid_sql_creds CVE-2015-2996
auxiliary/admin/http/sysaid_sql_creds CVE-2015-2998
auxiliary/admin/http/tomcat_utf8_traversal CVE-2008-2938
auxiliary/admin/http/trendmicro_dlp_traversal CVE-2008-2938
auxiliary/admin/http/typo3_news_module_sqli CVE-2017-7581
auxiliary/admin/http/typo3_sa_2009_001 CVE-2009-0255
auxiliary/admin/http/typo3_sa_2009_002 CVE-2009-0815
auxiliary/admin/http/typo3_sa_2010_020 CVE-2010-3714
auxiliary/admin/http/ulterius_file_download CVE-2017-16806
auxiliary/admin/http/vbulletin_upgrade_admin CVE-2013-6129
auxiliary/admin/http/webnms_cred_disclosure CVE-2016-6601
auxiliary/admin/http/webnms_cred_disclosure CVE-2016-6602
auxiliary/admin/http/webnms_file_download CVE-2016-6601
auxiliary/admin/http/wp_easycart_privilege_escalation CVE-2015-2673
auxiliary/admin/http/wp_gdpr_compliance_privesc CVE-2018-19207
auxiliary/admin/http/wp_google_maps_sqli CVE-2019-10692
auxiliary/admin/http/wp_symposium_sql_injection CVE-2015-6522
auxiliary/admin/kerberos/ms14_068_kerberos_checksum CVE-2014-6324
auxiliary/admin/maxdb/maxdb_cons_exec CVE-2008-0244
auxiliary/admin/motorola/wr850g_cred CVE-2004-1550
auxiliary/admin/ms/ms08_059_his2006 CVE-2008-3466
auxiliary/admin/officescan/tmlisten_traversal CVE-2008-2439
auxiliary/admin/oracle/osb_execqr CVE-2008-5448
auxiliary/admin/oracle/osb_execqr2 CVE-2009-1977
auxiliary/admin/oracle/osb_execqr2 CVE-2009-1978
auxiliary/admin/oracle/osb_execqr3 CVE-2010-0904
auxiliary/admin/scada/advantech_webaccess_dbvisitor_sqli CVE-2014-0763
auxiliary/admin/scada/ge_proficy_substitute_traversal CVE-2013-0653
auxiliary/admin/scada/moxa_credentials_recovery CVE-2016-9361
auxiliary/admin/scada/phoenix_command CVE-2014-9195
auxiliary/admin/scada/yokogawa_bkbcopyd_client CVE-2014-5208
auxiliary/admin/serverprotect/file CVE-2007-6507
auxiliary/admin/smb/ms17_010_command CVE-2017-0143
auxiliary/admin/smb/ms17_010_command CVE-2017-0146
auxiliary/admin/smb/ms17_010_command CVE-2017-0147
auxiliary/admin/smb/psexec_command CVE-1999-0504
auxiliary/admin/smb/samba_symlink_traversal CVE-2010-0926
auxiliary/admin/smb/webexec_command CVE-2018-15442
auxiliary/admin/sunrpc/solaris_kcms_readfile CVE-2003-0027
auxiliary/admin/tikiwiki/tikidblib CVE-2006-5702
auxiliary/admin/vnc/realvnc_41_bypass CVE-2006-2369
auxiliary/admin/webmin/edit_html_fileaccess CVE-2012-2983
auxiliary/admin/webmin/file_disclosure CVE-2006-3392
auxiliary/dos/android/android_stock_browser_iframe CVE-2012-6301
auxiliary/dos/cisco/ios_http_percentpercent CVE-2000-0380
auxiliary/dos/cisco/ios_telnet_rocem CVE-2017-3881
auxiliary/dos/dhcp/isc_dhcpd_clientid CVE-2010-2156
auxiliary/dos/dns/bind_tkey CVE-2015-5477
auxiliary/dos/dns/bind_tsig CVE-2016-2776
auxiliary/dos/freebsd/nfsd/nfsd_mount CVE-2006-0900
auxiliary/dos/hp/data_protector_rds CVE-2011-0514
auxiliary/dos/http/3com_superstack_switch CVE-2004-2691
auxiliary/dos/http/apache_commons_fileupload_dos CVE-2014-0050
auxiliary/dos/http/apache_mod_isapi CVE-2010-0425
auxiliary/dos/http/apache_range_dos CVE-2011-3192
auxiliary/dos/http/apache_tomcat_transfer_encoding CVE-2010-2227
auxiliary/dos/http/brother_debut_dos CVE-2017-16249
auxiliary/dos/http/cable_haunt_websocket_dos CVE-2019-19494
auxiliary/dos/http/canon_wireless_printer CVE-2013-4615
auxiliary/dos/http/dell_openmanage_post CVE-2004-0331
auxiliary/dos/http/flexense_http_server_dos CVE-2018-8065
auxiliary/dos/http/hashcollision_dos CVE-2011-5034
auxiliary/dos/http/hashcollision_dos CVE-2011-5035
auxiliary/dos/http/hashcollision_dos CVE-2011-4885
auxiliary/dos/http/hashcollision_dos CVE-2011-4858
auxiliary/dos/http/ibm_lotus_notes CVE-2017-1129
auxiliary/dos/http/ibm_lotus_notes2 CVE-2017-1130
auxiliary/dos/http/metasploit_httphandler_dos CVE-2019-5645
auxiliary/dos/http/monkey_headers CVE-2013-3843
auxiliary/dos/http/ms15_034_ulonglongadd CVE-2015-1635
auxiliary/dos/http/nodejs_pipelining CVE-2013-4450
auxiliary/dos/http/novell_file_reporter_heap_bof CVE-2012-4956
auxiliary/dos/http/rails_action_view CVE-2013-6414
auxiliary/dos/http/rails_json_float_dos CVE-2013-4164
auxiliary/dos/http/tautulli_shutdown_exec CVE-2019-19833
auxiliary/dos/http/ua_parser_js_redos CVE-2017-16086
auxiliary/dos/http/webkitplus CVE-2018-11646
auxiliary/dos/http/webrick_regex CVE-2008-3656
auxiliary/dos/http/wordpress_directory_traversal_dos CVE-2016-6897
auxiliary/dos/http/wordpress_long_password_dos CVE-2014-9016
auxiliary/dos/http/wordpress_xmlrpc_dos CVE-2014-5266
auxiliary/dos/mdns/avahi_portzero CVE-2008-5081
auxiliary/dos/misc/dopewars CVE-2009-3591
auxiliary/dos/misc/ibm_sametime_webplayer_dos CVE-2013-3986
auxiliary/dos/misc/memcached CVE-2011-4971
auxiliary/dos/ntp/ntpd_reserved_dos CVE-2009-3563
auxiliary/dos/pptp/ms02_063_pptp_dos CVE-2002-1214
auxiliary/dos/rpc/rpcbomb CVE-2017-8779
auxiliary/dos/samba/lsa_addprivs_heap CVE-2007-2446
auxiliary/dos/samba/lsa_transnames_heap CVE-2007-2446
auxiliary/dos/samba/read_nttrans_ea_list CVE-2013-4124
auxiliary/dos/scada/allen_bradley_pccc CVE-2017-7924
auxiliary/dos/scada/beckhoff_twincat CVE-2011-3486
auxiliary/dos/scada/igss9_dataserver CVE-2011-4050
auxiliary/dos/scada/yokogawa_logsvr CVE-2014-0781
auxiliary/dos/smtp/sendmail_prescan CVE-2003-0694
auxiliary/dos/solaris/lpd/cascade_delete CVE-2005-4797
auxiliary/dos/ssl/dtls_changecipherspec CVE-2009-1386
auxiliary/dos/ssl/dtls_fragment_overflow CVE-2014-0195
auxiliary/dos/ssl/openssl_aesni CVE-2012-2686
auxiliary/dos/syslog/rsyslog_long_tag CVE-2011-3200
auxiliary/dos/upnp/miniupnpd_dos CVE-2013-0229
auxiliary/dos/windows/appian/appian_bpm CVE-2007-6509
auxiliary/dos/windows/browser/ms09_065_eot_integer CVE-2009-2514
auxiliary/dos/windows/ftp/filezilla_admin_user CVE-2005-3589
auxiliary/dos/windows/ftp/filezilla_server_port CVE-2006-6565
auxiliary/dos/windows/ftp/guildftp_cwdlist CVE-2008-4572
auxiliary/dos/windows/ftp/iis75_ftpd_iac_bof CVE-2010-3972
auxiliary/dos/windows/ftp/iis_list_exhaustion CVE-2009-2521
auxiliary/dos/windows/ftp/titan626_site CVE-2008-6082
auxiliary/dos/windows/ftp/vicftps50_list CVE-2008-2031
auxiliary/dos/windows/ftp/vicftps50_list CVE-2008-6829
auxiliary/dos/windows/ftp/winftp230_nlst CVE-2008-5666
auxiliary/dos/windows/ftp/xmeasy560_nlst CVE-2008-5626
auxiliary/dos/windows/ftp/xmeasy570_nlst CVE-2008-5626
auxiliary/dos/windows/http/ms10_065_ii6_asp_dos CVE-2010-1899
auxiliary/dos/windows/http/pi3web_isapi CVE-2008-6938
auxiliary/dos/windows/llmnr/ms11_030_dnsapi CVE-2011-0657
auxiliary/dos/windows/nat/nat_helper CVE-2006-5614
auxiliary/dos/windows/rdp/ms12_020_maxchannelids CVE-2012-0002
auxiliary/dos/windows/smb/ms05_047_pnp CVE-2005-2120
auxiliary/dos/windows/smb/ms06_035_mailslot CVE-2006-3942
auxiliary/dos/windows/smb/ms06_063_trans CVE-2006-3942
auxiliary/dos/windows/smb/ms09_001_write CVE-2008-4114
auxiliary/dos/windows/smb/ms09_050_smb2_negotiate_pidhigh CVE-2009-3103
auxiliary/dos/windows/smb/ms09_050_smb2_session_logoff CVE-2009-3103
auxiliary/dos/windows/smb/ms10_006_negotiate_response_loop CVE-2010-0017
auxiliary/dos/windows/smb/ms10_054_queryfs_pool_overflow CVE-2010-2550
auxiliary/dos/windows/smb/ms11_019_electbowser CVE-2011-0654
auxiliary/dos/windows/smtp/ms06_019_exchange CVE-2006-0027
auxiliary/dos/windows/tftp/pt360_write CVE-2008-1311
auxiliary/dos/windows/tftp/solarwinds CVE-2010-2115
auxiliary/dos/wireshark/capwap CVE-2013-4074
auxiliary/dos/wireshark/chunked CVE-2007-3389
auxiliary/dos/wireshark/cldap CVE-2011-1140
auxiliary/dos/wireshark/ldap CVE-2008-1562
auxiliary/fileformat/badpdf CVE-2018-4993
auxiliary/fileformat/odt_badodt CVE-2018-10583
auxiliary/gather/advantech_webaccess_creds CVE-2016-5810
auxiliary/gather/alienvault_newpolicyform_sqli CVE-2014-5383
auxiliary/gather/android_htmlfileprovider CVE-2010-4804
auxiliary/gather/android_stock_browser_uxss CVE-2014-6041
auxiliary/gather/apache_rave_creds CVE-2013-1814
auxiliary/gather/apple_safari_ftp_url_cookie_theft CVE-2015-1126
auxiliary/gather/browser_lanipleak CVE-2018-6849
auxiliary/gather/cisco_rv320_config CVE-2019-1653
auxiliary/gather/coldfusion_pwd_props CVE-2013-3336
auxiliary/gather/d20pass CVE-2012-6663
auxiliary/gather/dolibarr_creds_sqli CVE-2018-10094
auxiliary/gather/drupal_openid_xxe CVE-2012-4554
auxiliary/gather/emc_cta_xxe CVE-2014-0644
auxiliary/gather/enum_dns CVE-1999-0532
auxiliary/gather/eventlog_cred_disclosure CVE-2014-6038
auxiliary/gather/eventlog_cred_disclosure CVE-2014-6039
auxiliary/gather/firefox_pdfjs_file_theft CVE-2015-4495
auxiliary/gather/flash_rosetta_jsonp_url_disclosure CVE-2014-4671
auxiliary/gather/huawei_wifi_info CVE-2013-6031
auxiliary/gather/ibm_bigfix_sites_packages_enum CVE-2019-4061
auxiliary/gather/ibm_sametime_enumerate_users CVE-2013-3975
auxiliary/gather/ibm_sametime_room_brute CVE-2013-3977
auxiliary/gather/ibm_sametime_version CVE-2013-3982
auxiliary/gather/ie_sandbox_findfiles CVE-2016-3321
auxiliary/gather/ie_uxss_injection CVE-2015-0072
auxiliary/gather/joomla_contenthistory_sqli CVE-2015-7297
auxiliary/gather/mantisbt_admin_sqli CVE-2014-2238
auxiliary/gather/mcafee_epo_xxe CVE-2015-0921
auxiliary/gather/mcafee_epo_xxe CVE-2015-0922
auxiliary/gather/ms14_052_xmldom CVE-2013-7331
auxiliary/gather/netgear_password_disclosure CVE-2017-5521
auxiliary/gather/nuuo_cms_bruteforce CVE-2018-17888
auxiliary/gather/nuuo_cms_file_download CVE-2018-17934
auxiliary/gather/oats_downloadservlet_traversal CVE-2019-2557
auxiliary/gather/opennms_xxe CVE-2015-0975
auxiliary/gather/pimcore_creds_sqli CVE-2018-14058
auxiliary/gather/pulse_secure_file_disclosure CVE-2019-11510
auxiliary/gather/rails_doubletap_file_read CVE-2019-5418
auxiliary/gather/safari_file_url_navigation CVE-2015-1155
auxiliary/gather/samsung_browser_sop_bypass CVE-2017-17692
auxiliary/gather/solarwinds_orion_sqli CVE-2014-9566
auxiliary/gather/trackit_sql_domain_creds CVE-2014-4872
auxiliary/gather/vbulletin_vote_sqli CVE-2013-3522
auxiliary/gather/xymon_info CVE-2016-2055
auxiliary/gather/zabbix_toggleids_sqli CVE-2016-10134
auxiliary/pdf/foxit/authbypass CVE-2009-0836
auxiliary/scanner/acpp/login CVE-2003-0270
auxiliary/scanner/backdoor/energizer_duo_detect CVE-2010-0103
auxiliary/scanner/chargen/chargen_probe CVE-1999-0103
auxiliary/scanner/couchdb/couchdb_enum CVE-2017-12635
auxiliary/scanner/db2/db2_auth CVE-1999-0502
auxiliary/scanner/dlsw/dlsw_leak_capture CVE-2014-7992
auxiliary/scanner/dns/dns_amp CVE-2006-0987
auxiliary/scanner/dns/dns_amp CVE-2006-0988
auxiliary/scanner/ftp/bison_ftp_traversal CVE-2015-7602
auxiliary/scanner/ftp/easy_file_sharing_ftp CVE-2017-6510
auxiliary/scanner/ftp/ftp_login CVE-1999-0502
auxiliary/scanner/ftp/konica_ftp_traversal CVE-2015-7603
auxiliary/scanner/ftp/pcman_ftp_traversal CVE-2015-7601
auxiliary/scanner/ftp/titanftp_xcrc_traversal CVE-2010-2426
auxiliary/scanner/http/accellion_fta_statecode_file_read CVE-2015-2856
auxiliary/scanner/http/adobe_xml_inject CVE-2009-3960
auxiliary/scanner/http/allegro_rompager_misfortune_cookie CVE-2014-9222
auxiliary/scanner/http/apache_activemq_source_disclosure CVE-2010-1587
auxiliary/scanner/http/apache_mod_cgi_bash_env CVE-2014-6271
auxiliary/scanner/http/apache_mod_cgi_bash_env CVE-2014-6278
auxiliary/scanner/http/apache_optionsbleed CVE-2017-9798
auxiliary/scanner/http/apache_userdir_enum CVE-2001-1013
auxiliary/scanner/http/atlassian_crowd_fileaccess CVE-2012-2926
auxiliary/scanner/http/axis_login CVE-2010-0219
auxiliary/scanner/http/bitweaver_overlay_type_traversal CVE-2012-5192
auxiliary/scanner/http/bmc_trackit_passwd_reset CVE-2014-8270
auxiliary/scanner/http/canon_wireless CVE-2013-4614
auxiliary/scanner/http/cgit_traversal CVE-2018-14912
auxiliary/scanner/http/cisco_device_manager CVE-2000-0945
auxiliary/scanner/http/cisco_directory_traversal CVE-2018-0296
auxiliary/scanner/http/cisco_firepower_download CVE-2016-6435
auxiliary/scanner/http/cisco_ios_auth_bypass CVE-2001-0537
auxiliary/scanner/http/cisco_nac_manager_traversal CVE-2011-3305
auxiliary/scanner/http/cisco_ssl_vpn_priv_esc CVE-2014-2127
auxiliary/scanner/http/citrix_dir_traversal CVE-2019-19781
auxiliary/scanner/http/cnpilot_r_web_login_loot CVE-2017-5260
auxiliary/scanner/http/coldfusion_locale_traversal CVE-2010-2861
auxiliary/scanner/http/dell_idrac CVE-1999-0502
auxiliary/scanner/http/dir_webdav_unicode_bypass CVE-2009-1535
auxiliary/scanner/http/dir_webdav_unicode_bypass CVE-2009-1122
auxiliary/scanner/http/dlink_dir_300_615_http_login CVE-1999-0502
auxiliary/scanner/http/dlink_dir_615h_http_login CVE-1999-0502
auxiliary/scanner/http/dlink_dir_session_cgi_http_login CVE-1999-0502
auxiliary/scanner/http/dnalims_file_retrieve CVE-2017-6527
auxiliary/scanner/http/elasticsearch_traversal CVE-2015-5531
auxiliary/scanner/http/epmp1000_get_chart_cmd_exec CVE-2017-5255
auxiliary/scanner/http/epmp1000_reset_pass CVE-2017-5254
auxiliary/scanner/http/es_file_explorer_open_port CVE-2019-6447
auxiliary/scanner/http/exchange_web_server_pushsubscription CVE-2019-0724
auxiliary/scanner/http/glassfish_login CVE-2011-0807
auxiliary/scanner/http/glassfish_traversal CVE-2017-1000028
auxiliary/scanner/http/goahead_traversal CVE-2014-9707
auxiliary/scanner/http/groupwise_agents_http_traversal CVE-2012-0419
auxiliary/scanner/http/host_header_injection CVE-2016-10073
auxiliary/scanner/http/hp_imc_bims_downloadservlet_traversal CVE-2013-4823
auxiliary/scanner/http/hp_imc_faultdownloadservlet_traversal CVE-2012-5202
auxiliary/scanner/http/hp_imc_ictdownloadservlet_traversal CVE-2012-5204
auxiliary/scanner/http/hp_imc_reportimgservlt_traversal CVE-2012-5203
auxiliary/scanner/http/hp_imc_som_file_download CVE-2013-4826
auxiliary/scanner/http/http_login CVE-1999-0502
auxiliary/scanner/http/http_sickrage_password_leak CVE-2018-9160
auxiliary/scanner/http/iis_internal_ip CVE-2000-0649
auxiliary/scanner/http/intel_amt_digest_bypass CVE-2017-5689
auxiliary/scanner/http/jboss_status CVE-2008-3273
auxiliary/scanner/http/jboss_status CVE-2010-1429
auxiliary/scanner/http/jboss_vulnscan CVE-2008-3273
auxiliary/scanner/http/jboss_vulnscan CVE-2010-1429
auxiliary/scanner/http/jboss_vulnscan CVE-2010-0738
auxiliary/scanner/http/jboss_vulnscan CVE-2010-1428
auxiliary/scanner/http/jboss_vulnscan CVE-2017-12149
auxiliary/scanner/http/jenkins_command CVE-2015-8103
auxiliary/scanner/http/joomla_bruteforce_login CVE-1999-0502
auxiliary/scanner/http/joomla_ecommercewd_sqli_scanner CVE-2015-2562
auxiliary/scanner/http/kodi_traversal CVE-2017-5982
auxiliary/scanner/http/limesurvey_zip_traversals CVE-2020-11455
auxiliary/scanner/http/limesurvey_zip_traversals CVE-2019-9960
auxiliary/scanner/http/litespeed_source_disclosure CVE-2010-2333
auxiliary/scanner/http/majordomo2_directory_traversal CVE-2011-0049
auxiliary/scanner/http/majordomo2_directory_traversal CVE-2011-0063
auxiliary/scanner/http/manageengine_deviceexpert_user_creds CVE-2014-5377
auxiliary/scanner/http/meteocontrol_weblog_extractadmin CVE-2016-2296
auxiliary/scanner/http/meteocontrol_weblog_extractadmin CVE-2016-2298
auxiliary/scanner/http/ms09_020_webdav_unicode_bypass CVE-2009-1535
auxiliary/scanner/http/ms09_020_webdav_unicode_bypass CVE-2009-1122
auxiliary/scanner/http/ms15_034_http_sys_memory_dump CVE-2015-1635
auxiliary/scanner/http/netdecision_traversal CVE-2012-1465
auxiliary/scanner/http/nginx_source_disclosure CVE-2010-2263
auxiliary/scanner/http/novell_file_reporter_fsfui_fileaccess CVE-2012-4958
auxiliary/scanner/http/novell_file_reporter_srs_fileaccess CVE-2012-4957
auxiliary/scanner/http/novell_mdm_creds CVE-2013-1081
auxiliary/scanner/http/options CVE-2005-3398
auxiliary/scanner/http/options CVE-2005-3498
auxiliary/scanner/http/oracle_demantra_database_credentials_leak CVE-2013-5795
auxiliary/scanner/http/oracle_demantra_database_credentials_leak CVE-2013-5880
auxiliary/scanner/http/oracle_demantra_file_retrieval CVE-2013-5877
auxiliary/scanner/http/oracle_demantra_file_retrieval CVE-2013-5880
auxiliary/scanner/http/rails_json_yaml_scanner CVE-2013-0333
auxiliary/scanner/http/rails_xml_yaml_scanner CVE-2013-0156
auxiliary/scanner/http/rewrite_proxy_bypass CVE-2011-3368
auxiliary/scanner/http/simple_webserver_traversal CVE-2002-1864
auxiliary/scanner/http/smt_ipmi_cgi_scanner CVE-2013-3621
auxiliary/scanner/http/smt_ipmi_cgi_scanner CVE-2013-3623
auxiliary/scanner/http/smt_ipmi_static_cert_scanner CVE-2013-3619
auxiliary/scanner/http/springcloud_traversal CVE-2019-3799
auxiliary/scanner/http/ssl_version CVE-2014-3566
auxiliary/scanner/http/support_center_plus_directory_traversal CVE-2014-100002
auxiliary/scanner/http/sybase_easerver_traversal CVE-2011-2474
auxiliary/scanner/http/symantec_brightmail_ldapcreds CVE-2016-2203
auxiliary/scanner/http/symantec_brightmail_logfile CVE-2012-4347
auxiliary/scanner/http/thinvnc_traversal CVE-2019-17662
auxiliary/scanner/http/titan_ftp_admin_pwd CVE-2013-1625
auxiliary/scanner/http/tomcat_enum CVE-2009-0580
auxiliary/scanner/http/tomcat_mgr_login CVE-2009-3843
auxiliary/scanner/http/tomcat_mgr_login CVE-2009-4189
auxiliary/scanner/http/tomcat_mgr_login CVE-2009-4188
auxiliary/scanner/http/tomcat_mgr_login CVE-2010-0557
auxiliary/scanner/http/tomcat_mgr_login CVE-2010-4094
auxiliary/scanner/http/tomcat_mgr_login CVE-2009-3548
auxiliary/scanner/http/tomcat_mgr_login CVE-1999-0502
auxiliary/scanner/http/totaljs_traversal CVE-2019-8903
auxiliary/scanner/http/tplink_traversal_noauth CVE-2012-5687
auxiliary/scanner/http/trace CVE-2005-3398
auxiliary/scanner/http/tvt_nvms_traversal CVE-2019-20085
auxiliary/scanner/http/wangkongbao_traversal CVE-2012-4031
auxiliary/scanner/http/webdav_internal_ip CVE-2002-0422
auxiliary/scanner/http/wildfly_traversal CVE-2014-7816
auxiliary/scanner/http/wordpress_content_injection CVE-2017-1001000
auxiliary/scanner/http/wordpress_cp_calendar_sqli CVE-2014-8586
auxiliary/scanner/http/wordpress_ghost_scanner CVE-2015-0235
auxiliary/scanner/http/wordpress_login_enum CVE-2009-2335
auxiliary/scanner/http/wordpress_pingback_access CVE-2013-0235
auxiliary/scanner/http/wordpress_xmlrpc_login CVE-1999-0502
auxiliary/scanner/http/wp_contus_video_gallery_sqli CVE-2015-2065
auxiliary/scanner/http/wp_dukapress_file_read CVE-2014-8799
auxiliary/scanner/http/wp_mobile_pack_info_disclosure CVE-2014-5337
auxiliary/scanner/http/yaws_traversal CVE-2011-4350
auxiliary/scanner/http/zenworks_assetmanagement_fileaccess CVE-2012-4933
auxiliary/scanner/http/zenworks_assetmanagement_getconfig CVE-2012-4933
auxiliary/scanner/ike/cisco_ike_benigncertain CVE-2016-6415
auxiliary/scanner/ipmi/ipmi_cipher_zero CVE-2013-4782
auxiliary/scanner/ipmi/ipmi_dumphashes CVE-2013-4786
auxiliary/scanner/lotus/lotus_domino_hashes CVE-2007-0977
auxiliary/scanner/memcached/memcached_amp CVE-2018-1000115
auxiliary/scanner/misc/dahua_dvr_auth_bypass CVE-2013-6117
auxiliary/scanner/misc/dvr_config_disclosure CVE-2013-1391
auxiliary/scanner/misc/java_jmx_server CVE-2015-2342
auxiliary/scanner/misc/java_rmi_server CVE-2011-3556
auxiliary/scanner/misc/sercomm_backdoor_scanner CVE-2014-0659
auxiliary/scanner/misc/zenworks_preboot_fileaccess CVE-2012-2215
auxiliary/scanner/mssql/mssql_login CVE-1999-0506
auxiliary/scanner/mysql/mysql_authbypass_hashdump CVE-2012-2122
auxiliary/scanner/mysql/mysql_login CVE-1999-0502
auxiliary/scanner/nfs/nfsmount CVE-1999-0170
auxiliary/scanner/nntp/nntp_login CVE-1999-0502
auxiliary/scanner/ntp/ntp_monlist CVE-2013-5211
auxiliary/scanner/ntp/ntp_nak_to_the_future CVE-2015-7871
auxiliary/scanner/ntp/ntp_peer_list_dos CVE-2013-5211
auxiliary/scanner/ntp/ntp_peer_list_sum_dos CVE-2013-5211
auxiliary/scanner/ntp/ntp_readvar CVE-2013-5211
auxiliary/scanner/ntp/ntp_req_nonce_dos CVE-2013-5211
auxiliary/scanner/ntp/ntp_reslist_dos CVE-2013-5211
auxiliary/scanner/ntp/ntp_unsettrap_dos CVE-2013-5211
auxiliary/scanner/oracle/oracle_login CVE-1999-0502
auxiliary/scanner/oracle/tnspoison_checker CVE-2012-1675
auxiliary/scanner/pcanywhere/pcanywhere_login CVE-1999-0502
auxiliary/scanner/portmap/portmap_amp CVE-2013-5211
auxiliary/scanner/postgres/postgres_dbname_flag_injection CVE-2013-1899
auxiliary/scanner/postgres/postgres_login CVE-1999-0502
auxiliary/scanner/rdp/cve_2019_0708_bluekeep CVE-2019-0708
auxiliary/scanner/rdp/ms12_020_check CVE-2012-0002
auxiliary/scanner/rservices/rexec_login CVE-1999-0651
auxiliary/scanner/rservices/rexec_login CVE-1999-0502
auxiliary/scanner/rservices/rlogin_login CVE-1999-0651
auxiliary/scanner/rservices/rlogin_login CVE-1999-0502
auxiliary/scanner/rservices/rsh_login CVE-1999-0651
auxiliary/scanner/rservices/rsh_login CVE-1999-0502
auxiliary/scanner/sap/sap_hostctrl_getcomputersystem CVE-2013-3319
auxiliary/scanner/sap/sap_icm_urlscan CVE-2010-0738
auxiliary/scanner/sap/sap_soap_rfc_system_info CVE-2006-6010
auxiliary/scanner/scada/indusoft_ntwebserver_fileaccess CVE-2011-1900
auxiliary/scanner/scada/moxa_discover CVE-2016-9361
auxiliary/scanner/scada/sielco_winlog_fileaccess CVE-2012-4356
auxiliary/scanner/smb/psexec_loggedin_users CVE-1999-0504
auxiliary/scanner/smb/smb_login CVE-1999-0506
auxiliary/scanner/smb/smb_ms17_010 CVE-2017-0143
auxiliary/scanner/smb/smb_ms17_010 CVE-2017-0144
auxiliary/scanner/smb/smb_ms17_010 CVE-2017-0145
auxiliary/scanner/smb/smb_ms17_010 CVE-2017-0146
auxiliary/scanner/smb/smb_ms17_010 CVE-2017-0147
auxiliary/scanner/smb/smb_ms17_010 CVE-2017-0148
auxiliary/scanner/smb/smb_uninit_cred CVE-2015-0240
auxiliary/scanner/smtp/smtp_enum CVE-1999-0531
auxiliary/scanner/snmp/arris_dg950 CVE-2014-4863
auxiliary/scanner/snmp/cnpilot_r_snmp_loot CVE-2017-5262
auxiliary/scanner/snmp/epmp1000_snmp_loot CVE-2017-7918
auxiliary/scanner/snmp/epmp1000_snmp_loot CVE-2017-7922
auxiliary/scanner/snmp/snmp_login CVE-1999-0508
auxiliary/scanner/ssh/eaton_xpert_backdoor CVE-2018-16158
auxiliary/scanner/ssh/fortinet_backdoor CVE-2016-1909
auxiliary/scanner/ssh/juniper_backdoor CVE-2015-7755
auxiliary/scanner/ssh/libssh_auth_bypass CVE-2018-10933
auxiliary/scanner/ssh/ssh_enumusers CVE-2003-0190
auxiliary/scanner/ssh/ssh_enumusers CVE-2006-5229
auxiliary/scanner/ssh/ssh_enumusers CVE-2016-6210
auxiliary/scanner/ssh/ssh_enumusers CVE-2018-15473
auxiliary/scanner/ssh/ssh_login CVE-1999-0502
auxiliary/scanner/ssl/bleichenbacher_oracle CVE-2017-6168
auxiliary/scanner/ssl/bleichenbacher_oracle CVE-2017-17382
auxiliary/scanner/ssl/bleichenbacher_oracle CVE-2017-17427
auxiliary/scanner/ssl/bleichenbacher_oracle CVE-2017-17428
auxiliary/scanner/ssl/bleichenbacher_oracle CVE-2017-12373
auxiliary/scanner/ssl/bleichenbacher_oracle CVE-2017-13098
auxiliary/scanner/ssl/bleichenbacher_oracle CVE-2017-1000385
auxiliary/scanner/ssl/bleichenbacher_oracle CVE-2017-13099
auxiliary/scanner/ssl/bleichenbacher_oracle CVE-2016-6883
auxiliary/scanner/ssl/bleichenbacher_oracle CVE-2012-5081
auxiliary/scanner/ssl/openssl_ccs CVE-2014-0224
auxiliary/scanner/ssl/openssl_heartbleed CVE-2014-0160
auxiliary/scanner/telnet/brocade_enable_login CVE-1999-0502
auxiliary/scanner/telnet/satel_cmd_exec CVE-2017-6048
auxiliary/scanner/telnet/telnet_encrypt_overflow CVE-2011-4862
auxiliary/scanner/telnet/telnet_login CVE-1999-0502
auxiliary/scanner/telnet/telnet_ruggedcom CVE-2012-1803
auxiliary/scanner/tftp/ipswitch_whatsupgold_tftp CVE-2011-4722
auxiliary/scanner/tftp/netdecision_tftp CVE-2009-1730
auxiliary/scanner/udp/udp_amplification CVE-2013-5211
auxiliary/scanner/upnp/ssdp_amp CVE-2013-5211
auxiliary/scanner/upnp/ssdp_msearch CVE-2012-5958
auxiliary/scanner/upnp/ssdp_msearch CVE-2012-5959
auxiliary/scanner/upnp/ssdp_msearch CVE-2013-0230
auxiliary/scanner/upnp/ssdp_msearch CVE-2013-0229
auxiliary/scanner/varnish/varnish_cli_file_read CVE-2009-2936
auxiliary/scanner/varnish/varnish_cli_login CVE-2009-2936
auxiliary/scanner/vmware/vmauthd_login CVE-1999-0502
auxiliary/scanner/vmware/vmware_http_login CVE-1999-0502
auxiliary/scanner/vmware/vmware_server_dir_trav CVE-2009-3733
auxiliary/scanner/vmware/vmware_update_manager_traversal CVE-2011-4404
auxiliary/scanner/vnc/ard_root_pw CVE-2017-13872
auxiliary/scanner/vnc/vnc_login CVE-1999-0506
auxiliary/scanner/vnc/vnc_none_auth CVE-2006-2369
auxiliary/scanner/vxworks/urgent11_check CVE-2019-12258
auxiliary/scanner/winrm/winrm_login CVE-1999-0502
auxiliary/scanner/wproxy/att_open_proxy CVE-2017-14117
auxiliary/scanner/x11/open_x11 CVE-1999-0526
auxiliary/server/dhclient_bash_env CVE-2014-6271
auxiliary/server/jsse_skiptls_mitm_proxy CVE-2014-6593
auxiliary/server/ms15_134_mcl_leak CVE-2015-6127
auxiliary/server/netbios_spoof_nat CVE-2016-3213
auxiliary/server/netbios_spoof_nat CVE-2016-3236
auxiliary/server/openssl_altchainsforgery_mitm_proxy CVE-2015-1793
auxiliary/server/openssl_heartbeat_client_memory CVE-2014-0160
auxiliary/server/webkit_xslt_dropper CVE-2011-1774
auxiliary/server/wget_symlink_file_write CVE-2014-4877
auxiliary/spoof/arp/arp_poisoning CVE-1999-0667
auxiliary/spoof/dns/bailiwicked_domain CVE-2008-1447
auxiliary/spoof/dns/bailiwicked_host CVE-2008-1447
auxiliary/sqli/openemr/openemr_sqli_dump CVE-2018-17179
auxiliary/sqli/oracle/dbms_cdc_ipublish CVE-2008-3996
auxiliary/sqli/oracle/dbms_cdc_publish CVE-2008-3995
auxiliary/sqli/oracle/dbms_cdc_publish2 CVE-2010-0870
auxiliary/sqli/oracle/dbms_cdc_publish3 CVE-2010-2415
auxiliary/sqli/oracle/dbms_cdc_subscribe_activate_subscription CVE-2005-4832
auxiliary/sqli/oracle/dbms_export_extension CVE-2006-2081
auxiliary/sqli/oracle/droptable_trigger CVE-2008-3979
auxiliary/sqli/oracle/jvm_os_code_10g CVE-2010-0866
auxiliary/sqli/oracle/jvm_os_code_11g CVE-2010-0866
auxiliary/sqli/oracle/lt_compressworkspace CVE-2008-3982
auxiliary/sqli/oracle/lt_findricset_cursor CVE-2007-5511
auxiliary/sqli/oracle/lt_mergeworkspace CVE-2008-3983
auxiliary/sqli/oracle/lt_removeworkspace CVE-2008-3984
auxiliary/sqli/oracle/lt_rollbackworkspace CVE-2009-0978
auxiliary/voip/cisco_cucdm_call_forward CVE-2014-3300
auxiliary/voip/cisco_cucdm_speed_dials CVE-2014-3300
exploit/aix/local/ibstat_path CVE-2013-4011
exploit/aix/local/xorg_x11_server CVE-2018-14665
exploit/aix/rpc_cmsd_opcode21 CVE-2009-3699
exploit/aix/rpc_ttdbserverd_realpath CVE-2009-2727
exploit/android/browser/stagefright_mp4_tx3g_64bit CVE-2015-3864
exploit/android/browser/webview_addjavascriptinterface CVE-2012-6636
exploit/android/browser/webview_addjavascriptinterface CVE-2013-4710
exploit/android/fileformat/adobe_reader_pdf_js_interface CVE-2014-0514
exploit/android/local/binder_uaf CVE-2019-2215
exploit/android/local/futex_requeue CVE-2014-3153
exploit/android/local/janus CVE-2017-13156
exploit/android/local/put_user_vroot CVE-2013-6282
exploit/apple_ios/browser/safari_libtiff CVE-2006-3459
exploit/apple_ios/browser/webkit_createthis CVE-2018-4233
exploit/apple_ios/browser/webkit_createthis CVE-2017-13861
exploit/apple_ios/browser/webkit_trident CVE-2016-4655
exploit/apple_ios/browser/webkit_trident CVE-2016-4656
exploit/apple_ios/browser/webkit_trident CVE-2016-4657
exploit/apple_ios/email/mobilemail_libtiff CVE-2006-3459
exploit/bsdi/softcart/mercantec_softcart CVE-2004-2221
exploit/dialup/multi/login/manyargs CVE-2001-0797
exploit/freebsd/ftp/proftp_telnet_iac CVE-2010-4221
exploit/freebsd/http/watchguard_cmd_exec CVE-2015-5453
exploit/freebsd/local/intel_sysret_priv_esc CVE-2012-0217
exploit/freebsd/local/mmap CVE-2013-2171
exploit/freebsd/local/rtld_execl_priv_esc CVE-2009-4146
exploit/freebsd/local/rtld_execl_priv_esc CVE-2009-4147
exploit/freebsd/samba/trans2open CVE-2003-0201
exploit/freebsd/tacacs/xtacacsd_report CVE-2008-7232
exploit/freebsd/telnet/telnet_encrypt_keyid CVE-2011-4862
exploit/hpux/lpd/cleanup_exec CVE-2002-1473
exploit/irix/lpd/tagprinter_exec CVE-2001-0800
exploit/linux/browser/adobe_flashplayer_aslaunch CVE-2008-5499
exploit/linux/ftp/proftp_sreplace CVE-2006-5815
exploit/linux/ftp/proftp_telnet_iac CVE-2010-4221
exploit/linux/games/ut2004_secure CVE-2004-0608
exploit/linux/http/accellion_fta_getstatus_oauth CVE-2015-2857
exploit/linux/http/advantech_switch_bash_env_exec CVE-2014-6271
exploit/linux/http/airties_login_cgi_bof CVE-2015-2797
exploit/linux/http/alcatel_omnipcx_mastercgi_exec CVE-2007-3010
exploit/linux/http/alienvault_exec CVE-2016-8582
exploit/linux/http/alienvault_sqli_exec CVE-2016-8581
exploit/linux/http/apache_couchdb_cmd_exec CVE-2017-12636
exploit/linux/http/apache_couchdb_cmd_exec CVE-2017-12635
exploit/linux/http/asuswrt_lan_rce CVE-2018-5999
exploit/linux/http/asuswrt_lan_rce CVE-2018-6000
exploit/linux/http/axis_srv_parhand_rce CVE-2018-10660
exploit/linux/http/axis_srv_parhand_rce CVE-2018-10661
exploit/linux/http/axis_srv_parhand_rce CVE-2018-10662
exploit/linux/http/belkin_login_bof CVE-2014-1635
exploit/linux/http/bludit_upload_images_exec CVE-2019-16113
exploit/linux/http/centreon_sqli_exec CVE-2014-3828
exploit/linux/http/centreon_sqli_exec CVE-2014-3829
exploit/linux/http/cfme_manageiq_evm_upload_exec CVE-2013-2068
exploit/linux/http/cisco_firepower_useradd CVE-2016-6433
exploit/linux/http/cisco_prime_inf_rce CVE-2018-15379
exploit/linux/http/cisco_rv32x_rce CVE-2019-1653
exploit/linux/http/cisco_rv32x_rce CVE-2019-1652
exploit/linux/http/cisco_ucs_rce CVE-2019-1937
exploit/linux/http/cisco_ucs_rce CVE-2019-1936
exploit/linux/http/citrix_dir_traversal_rce CVE-2019-19781
exploit/linux/http/cpi_tararchive_upload CVE-2019-1821
exploit/linux/http/cve_2019_1663_cisco_rmi_rce CVE-2019-1663
exploit/linux/http/ddwrt_cgibin_exec CVE-2009-2765
exploit/linux/http/denyall_waf_exec CVE-2017-14706
exploit/linux/http/dlink_dcs931l_upload CVE-2015-2049
exploit/linux/http/dlink_diagnostic_exec_noauth CVE-2014-100005
exploit/linux/http/dlink_dwl_2600_command_injection CVE-2019-20499
exploit/linux/http/dlink_hnap_bof CVE-2014-3936
exploit/linux/http/dlink_hnap_login_bof CVE-2016-6563
exploit/linux/http/dlink_upnp_exec_noauth CVE-2014-8361
exploit/linux/http/dnalims_admin_exec CVE-2017-6526
exploit/linux/http/efw_chpasswd_exec CVE-2015-5082
exploit/linux/http/eyesofnetwork_autodiscovery_rce CVE-2020-8654
exploit/linux/http/eyesofnetwork_autodiscovery_rce CVE-2020-8655
exploit/linux/http/eyesofnetwork_autodiscovery_rce CVE-2020-8656
exploit/linux/http/eyesofnetwork_autodiscovery_rce CVE-2020-8657
exploit/linux/http/f5_icall_cmd CVE-2015-3628
exploit/linux/http/f5_icontrol_exec CVE-2014-2928
exploit/linux/http/foreman_openstack_satellite_code_exec CVE-2013-2121
exploit/linux/http/fritzbox_echo_exec CVE-2014-9727
exploit/linux/http/gitlist_exec CVE-2014-4511
exploit/linux/http/goahead_ldpreload CVE-2017-17562
exploit/linux/http/goautodial_3_rce_command_injection CVE-2015-2843
exploit/linux/http/goautodial_3_rce_command_injection CVE-2015-2845
exploit/linux/http/gpsd_format_string CVE-2004-1388
exploit/linux/http/groundwork_monarch_cmd_exec CVE-2013-3502
exploit/linux/http/ibm_qradar_unauth_rce CVE-2016-9722
exploit/linux/http/ibm_qradar_unauth_rce CVE-2018-1418
exploit/linux/http/ibm_qradar_unauth_rce CVE-2018-1612
exploit/linux/http/ipfire_bashbug_exec CVE-2014-6271
exploit/linux/http/ipfire_oinkcode_exec CVE-2017-9757
exploit/linux/http/kaltura_unserialize_cookie_rce CVE-2017-14143
exploit/linux/http/librenms_addhost_cmd_inject CVE-2018-20434
exploit/linux/http/librenms_collectd_cmd_inject CVE-2019-10669
exploit/linux/http/linksys_apply_cgi CVE-2005-2799
exploit/linux/http/linksys_wrt110_cmd_exec CVE-2013-3568
exploit/linux/http/linksys_wrt54gl_apply_exec CVE-2005-2799
exploit/linux/http/linksys_wvbr0_user_agent_exec_noauth CVE-2017-17411
exploit/linux/http/mailcleaner_exec CVE-2018-20323
exploit/linux/http/microfocus_secure_messaging_gateway CVE-2018-12464
exploit/linux/http/microfocus_secure_messaging_gateway CVE-2018-12465
exploit/linux/http/multi_ncc_ping_exec CVE-2015-1187
exploit/linux/http/mutiny_frontend_upload CVE-2013-0136
exploit/linux/http/nagios_xi_authenticated_rce CVE-2019-15949
exploit/linux/http/nagios_xi_chained_rce_2_electric_boogaloo CVE-2018-8733
exploit/linux/http/nagios_xi_chained_rce_2_electric_boogaloo CVE-2018-8734
exploit/linux/http/nagios_xi_chained_rce_2_electric_boogaloo CVE-2018-8735
exploit/linux/http/nagios_xi_chained_rce_2_electric_boogaloo CVE-2018-8736
exploit/linux/http/nagios_xi_magpie_debug CVE-2018-15708
exploit/linux/http/nagios_xi_magpie_debug CVE-2018-15710
exploit/linux/http/netgear_dnslookup_cmd_exec CVE-2017-6334
exploit/linux/http/netgear_r7000_cgibin_exec CVE-2016-6277
exploit/linux/http/netgear_readynas_exec CVE-2013-2751
exploit/linux/http/netgear_unauth_exec CVE-2016-1555
exploit/linux/http/netgear_wnr2000_rce CVE-2016-10174
exploit/linux/http/nexus_repo_manager_el_injection CVE-2020-10199
exploit/linux/http/nginx_chunked_size CVE-2013-2028
exploit/linux/http/nuuo_nvrmini_auth_rce CVE-2016-5675
exploit/linux/http/nuuo_nvrmini_unauth_rce CVE-2016-5674
exploit/linux/http/panos_readsessionvars CVE-2017-15944
exploit/linux/http/peercast_url CVE-2006-1148
exploit/linux/http/php_imap_open_rce CVE-2018-19518
exploit/linux/http/php_imap_open_rce CVE-2018-1000859
exploit/linux/http/pineapp_test_li_conn_exec CVE-2013-6829
exploit/linux/http/pineapple_bypass_cmdinject CVE-2015-4624
exploit/linux/http/pineapple_preconfig_cmdinject CVE-2015-4624
exploit/linux/http/piranha_passwd_exec CVE-2000-0248
exploit/linux/http/piranha_passwd_exec CVE-2000-0322
exploit/linux/http/pulse_secure_cmd_exec CVE-2019-11539
exploit/linux/http/qnap_qcenter_change_passwd_exec CVE-2018-0706
exploit/linux/http/qnap_qcenter_change_passwd_exec CVE-2018-0707
exploit/linux/http/railo_cfml_rfi CVE-2014-5468
exploit/linux/http/rconfig_ajaxarchivefiles_rce CVE-2019-19509
exploit/linux/http/rconfig_ajaxarchivefiles_rce CVE-2020-10220
exploit/linux/http/realtek_miniigd_upnp_exec_noauth CVE-2014-8361
exploit/linux/http/samsung_srv_1670d_upload_exec CVE-2017-16524
exploit/linux/http/samsung_srv_1670d_upload_exec CVE-2015-8279
exploit/linux/http/seagate_nas_php_exec_noauth CVE-2014-8684
exploit/linux/http/seagate_nas_php_exec_noauth CVE-2014-8686
exploit/linux/http/seagate_nas_php_exec_noauth CVE-2014-8687
exploit/linux/http/smt_ipmi_close_window_bof CVE-2013-3623
exploit/linux/http/sophos_wpa_iface_exec CVE-2014-2849
exploit/linux/http/sophos_wpa_iface_exec CVE-2014-2850
exploit/linux/http/sophos_wpa_sblistpack_exec CVE-2013-4983
exploit/linux/http/spark_unauth_rce CVE-2018-11770
exploit/linux/http/supervisor_xmlrpc_exec CVE-2017-11610
exploit/linux/http/symantec_messaging_gateway_exec CVE-2017-6326
exploit/linux/http/symantec_web_gateway_exec CVE-2012-0297
exploit/linux/http/symantec_web_gateway_file_upload CVE-2012-0299
exploit/linux/http/symantec_web_gateway_lfi CVE-2012-0297
exploit/linux/http/symantec_web_gateway_pbcontrol CVE-2012-2953
exploit/linux/http/symantec_web_gateway_restore CVE-2014-7285
exploit/linux/http/synology_dsm_sliceupload_exec_noauth CVE-2013-6955
exploit/linux/http/tp_link_sc2020n_authenticated_telnet_injection CVE-2013-2578
exploit/linux/http/tr064_ntpserver_cmdinject CVE-2016-10372
exploit/linux/http/trend_micro_imsva_exec CVE-2017-6398
exploit/linux/http/trendmicro_sps_exec CVE-2016-6267
exploit/linux/http/trueonline_billion_5200w_rce CVE-2017-18369
exploit/linux/http/trueonline_billion_5200w_rce CVE-2017-18372
exploit/linux/http/trueonline_p660hn_v1_rce CVE-2017-18368
exploit/linux/http/trueonline_p660hn_v2_rce CVE-2017-18370
exploit/linux/http/trueonline_p660hn_v2_rce CVE-2017-18371
exploit/linux/http/ueb_api_rce CVE-2017-12478
exploit/linux/http/ueb_api_rce CVE-2018-6328
exploit/linux/http/vap2500_tools_command_exec CVE-2014-8423
exploit/linux/http/vap2500_tools_command_exec CVE-2014-8424
exploit/linux/http/vcms_upload CVE-2011-4828
exploit/linux/http/vestacp_exec CVE-2020-10808
exploit/linux/http/wd_mycloud_multiupload_upload CVE-2017-17560
exploit/linux/http/webcalendar_settings_exec CVE-2012-1495
exploit/linux/http/webmin_backdoor CVE-2019-15107
exploit/linux/http/webmin_packageup_rce CVE-2019-12840
exploit/linux/http/wepresent_cmd_injection CVE-2019-3929
exploit/linux/http/xplico_exec CVE-2017-16666
exploit/linux/http/zabbix_sqli CVE-2013-5743
exploit/linux/http/zimbra_xxe_rce CVE-2019-9670
exploit/linux/http/zimbra_xxe_rce CVE-2019-9621
exploit/linux/ids/alienvault_centerd_soap_exec CVE-2014-3804
exploit/linux/ids/snortbopre CVE-2005-3252
exploit/linux/imap/imap_uw_lsub CVE-2000-0284
exploit/linux/local/abrt_raceabrt_priv_esc CVE-2015-3315
exploit/linux/local/abrt_sosreport_priv_esc CVE-2015-5287
exploit/linux/local/af_packet_chocobo_root_priv_esc CVE-2016-8655
exploit/linux/local/af_packet_packet_set_ring_priv_esc CVE-2017-7308
exploit/linux/local/apport_abrt_chroot_priv_esc CVE-2015-1318
exploit/linux/local/blueman_set_dhcp_handler_dbus_priv_esc CVE-2015-8612
exploit/linux/local/bpf_priv_esc CVE-2016-4557
exploit/linux/local/bpf_sign_extension_priv_esc CVE-2017-16995
exploit/linux/local/exim4_deliver_message_priv_esc CVE-2019-10149
exploit/linux/local/glibc_ld_audit_dso_load_priv_esc CVE-2010-3847
exploit/linux/local/glibc_ld_audit_dso_load_priv_esc CVE-2010-3856
exploit/linux/local/glibc_origin_expansion_priv_esc CVE-2010-3847
exploit/linux/local/glibc_realpath_priv_esc CVE-2018-1000001
exploit/linux/local/juju_run_agent_priv_esc CVE-2017-9232
exploit/linux/local/ktsuss_suid_priv_esc CVE-2011-2921
exploit/linux/local/libuser_roothelper_priv_esc CVE-2015-3245
exploit/linux/local/libuser_roothelper_priv_esc CVE-2015-3246
exploit/linux/local/nested_namespace_idmap_limit_priv_esc CVE-2018-18955
exploit/linux/local/netfilter_priv_esc_ipv4 CVE-2016-4997
exploit/linux/local/netfilter_priv_esc_ipv4 CVE-2016-4998
exploit/linux/local/network_manager_vpnc_username_priv_esc CVE-2018-10900
exploit/linux/local/ntfs3g_priv_esc CVE-2017-0358
exploit/linux/local/omniresolve_suid_priv_esc CVE-2019-11660
exploit/linux/local/overlayfs_priv_esc CVE-2015-1328
exploit/linux/local/overlayfs_priv_esc CVE-2015-8660
exploit/linux/local/pkexec CVE-2011-1485
exploit/linux/local/ptrace_traceme_pkexec_helper CVE-2019-13272
exploit/linux/local/rds_atomic_free_op_null_pointer_deref_priv_esc CVE-2018-5333
exploit/linux/local/rds_atomic_free_op_null_pointer_deref_priv_esc CVE-2019-9213
exploit/linux/local/rds_rds_page_copy_user_priv_esc CVE-2010-3904
exploit/linux/local/recvmmsg_priv_esc CVE-2014-0038
exploit/linux/local/servu_ftp_server_prepareinstallation_priv_esc CVE-2019-12181
exploit/linux/local/sock_sendpage CVE-2009-2692
exploit/linux/local/sophos_wpa_clear_keys CVE-2013-4984
exploit/linux/local/systemtap_modprobe_options_priv_esc CVE-2010-4170
exploit/linux/local/udev_netlink CVE-2009-1185
exploit/linux/local/ueb_bpserverd_privesc CVE-2018-6329
exploit/linux/local/ufo_privilege_escalation CVE-2017-1000112
exploit/linux/local/vmware_alsa_config CVE-2017-4915
exploit/linux/local/vmware_mount CVE-2013-1662
exploit/linux/misc/asus_infosvr_auth_bypass_exec CVE-2014-9583
exploit/linux/misc/gld_postfix CVE-2005-1099
exploit/linux/misc/hikvision_rtsp_bof CVE-2014-4880
exploit/linux/misc/hp_data_protector_cmd_exec CVE-2011-0923
exploit/linux/misc/hp_jetdirect_path_traversal CVE-2017-2741
exploit/linux/misc/hp_nnmi_pmd_bof CVE-2014-2624
exploit/linux/misc/hp_vsa_login_bof CVE-2013-2343
exploit/linux/misc/hplip_hpssd_exec CVE-2007-5208
exploit/linux/misc/ib_inet_connect CVE-2007-5243
exploit/linux/misc/ib_jrd8_create_database CVE-2007-5243
exploit/linux/misc/ib_open_marker_file CVE-2007-5244
exploit/linux/misc/ib_pwd_db_aliased CVE-2007-5243
exploit/linux/misc/jenkins_java_deserialize CVE-2015-8103
exploit/linux/misc/jenkins_ldap_deserialize CVE-2016-9299
exploit/linux/misc/lprng_format_string CVE-2000-0917
exploit/linux/misc/mongod_native_helper CVE-2013-1892
exploit/linux/misc/nagios_nrpe_arguments CVE-2013-1362
exploit/linux/misc/netsupport_manager_agent CVE-2011-0404
exploit/linux/misc/novell_edirectory_ncp_bof CVE-2012-0432
exploit/linux/misc/opennms_java_serialize CVE-2015-8103
exploit/linux/misc/qnap_transcode_server CVE-2017-13067
exploit/linux/misc/quest_pmmasterd_bof CVE-2017-6553
exploit/linux/misc/tplink_archer_a7_c7_lan_rce CVE-2020-10882
exploit/linux/misc/tplink_archer_a7_c7_lan_rce CVE-2020-10883
exploit/linux/misc/tplink_archer_a7_c7_lan_rce CVE-2020-10884
exploit/linux/misc/ueb9_bpserverd CVE-2017-12477
exploit/linux/misc/zabbix_server_exec CVE-2009-4498
exploit/linux/mysql/mysql_yassl_getname CVE-2009-4484
exploit/linux/mysql/mysql_yassl_hello CVE-2008-0226
exploit/linux/pop3/cyrus_pop3d_popsubfolders CVE-2006-2502
exploit/linux/postgres/postgres_payload CVE-2007-3280
exploit/linux/pptp/poptop_negative_read CVE-2003-0213
exploit/linux/proxy/squid_ntlm_authenticate CVE-2004-0541
exploit/linux/samba/chain_reply CVE-2010-2063
exploit/linux/samba/is_known_pipename CVE-2017-7494
exploit/linux/samba/lsa_transnames_heap CVE-2007-2446
exploit/linux/samba/setinfopolicy_heap CVE-2012-1182
exploit/linux/samba/trans2open CVE-2003-0201
exploit/linux/smtp/apache_james_exec CVE-2015-7611
exploit/linux/smtp/exim_gethostbyname_bof CVE-2015-0235
exploit/linux/snmp/awind_snmp_exec CVE-2017-16709
exploit/linux/ssh/ceragon_fibeair_known_privkey CVE-2015-0936
exploit/linux/ssh/cisco_ucs_scpuser CVE-2019-1935
exploit/linux/ssh/exagrid_known_privkey CVE-2016-1560
exploit/linux/ssh/exagrid_known_privkey CVE-2016-1561
exploit/linux/ssh/f5_bigip_known_privkey CVE-2012-1493
exploit/linux/ssh/mercurial_ssh_exec CVE-2017-9462
exploit/linux/ssh/solarwinds_lem_exec CVE-2017-7722
exploit/linux/ssh/symantec_smg_ssh CVE-2012-3579
exploit/linux/ssh/vmware_vdp_known_privkey CVE-2016-7456
exploit/linux/telnet/telnet_encrypt_keyid CVE-2011-4862
exploit/linux/upnp/dlink_dir859_exec_ssdpcgi CVE-2019-20215
exploit/linux/upnp/dlink_dir859_subscribe_exec CVE-2019-17621
exploit/linux/upnp/miniupnpd_soap_bof CVE-2013-0230
exploit/multi/browser/adobe_flash_hacking_team_uaf CVE-2015-5119
exploit/multi/browser/adobe_flash_nellymoser_bof CVE-2015-3043
exploit/multi/browser/adobe_flash_nellymoser_bof CVE-2015-3113
exploit/multi/browser/adobe_flash_net_connection_confusion CVE-2015-0336
exploit/multi/browser/adobe_flash_opaque_background_uaf CVE-2015-5122
exploit/multi/browser/adobe_flash_pixel_bender_bof CVE-2014-0515
exploit/multi/browser/adobe_flash_shader_drawing_fill CVE-2015-3105
exploit/multi/browser/adobe_flash_shader_job_overflow CVE-2015-3090
exploit/multi/browser/adobe_flash_uncompress_zlib_uaf CVE-2015-0311
exploit/multi/browser/chrome_array_map CVE-2019-5825
exploit/multi/browser/chrome_jscreate_sideeffect CVE-2020-6418
exploit/multi/browser/chrome_object_create CVE-2018-17463
exploit/multi/browser/firefox_escape_retval CVE-2009-2477
exploit/multi/browser/firefox_pdfjs_privilege_escalation CVE-2015-0816
exploit/multi/browser/firefox_pdfjs_privilege_escalation CVE-2015-0802
exploit/multi/browser/firefox_proto_crmfrequest CVE-2012-3993
exploit/multi/browser/firefox_proto_crmfrequest CVE-2013-1710
exploit/multi/browser/firefox_proxy_prototype CVE-2014-8636
exploit/multi/browser/firefox_proxy_prototype CVE-2015-0802
exploit/multi/browser/firefox_queryinterface CVE-2006-0295
exploit/multi/browser/firefox_svg_plugin CVE-2013-0758
exploit/multi/browser/firefox_svg_plugin CVE-2013-0757
exploit/multi/browser/firefox_tostring_console_injection CVE-2013-1710
exploit/multi/browser/firefox_webidl_injection CVE-2014-1510
exploit/multi/browser/firefox_webidl_injection CVE-2014-1511
exploit/multi/browser/itms_overflow CVE-2009-0950
exploit/multi/browser/java_atomicreferencearray CVE-2012-0507
exploit/multi/browser/java_calendar_deserialize CVE-2008-5353
exploit/multi/browser/java_getsoundbank_bof CVE-2009-3867
exploit/multi/browser/java_jre17_driver_manager CVE-2013-1488
exploit/multi/browser/java_jre17_exec CVE-2012-4681
exploit/multi/browser/java_jre17_glassfish_averagerangestatisticimpl CVE-2012-5076
exploit/multi/browser/java_jre17_jaxws CVE-2012-5076
exploit/multi/browser/java_jre17_jmxbean CVE-2013-0422
exploit/multi/browser/java_jre17_jmxbean_2 CVE-2013-0431
exploit/multi/browser/java_jre17_method_handle CVE-2012-5088
exploit/multi/browser/java_jre17_provider_skeleton CVE-2013-2460
exploit/multi/browser/java_jre17_reflection_types CVE-2013-2423
exploit/multi/browser/java_rhino CVE-2011-3544
exploit/multi/browser/java_rmi_connection_impl CVE-2010-0094
exploit/multi/browser/java_setdifficm_bof CVE-2009-3869
exploit/multi/browser/java_storeimagearray CVE-2013-2465
exploit/multi/browser/java_trusted_chain CVE-2010-0840
exploit/multi/browser/java_verifier_field_access CVE-2012-1723
exploit/multi/browser/mozilla_compareto CVE-2005-2265
exploit/multi/browser/mozilla_navigatorjava CVE-2006-3677
exploit/multi/browser/opera_historysearch CVE-2008-4696
exploit/multi/browser/qtjava_pointer CVE-2007-2175
exploit/multi/elasticsearch/script_mvel_rce CVE-2014-3120
exploit/multi/elasticsearch/search_groovy_script CVE-2015-1427
exploit/multi/fileformat/adobe_u3d_meshcont CVE-2009-2990
exploit/multi/fileformat/evince_cbt_cmd_injection CVE-2017-1000083
exploit/multi/fileformat/ghostscript_failed_restore CVE-2018-16509
exploit/multi/fileformat/libreoffice_logo_exec CVE-2019-9851
exploit/multi/fileformat/libreoffice_macro_exec CVE-2018-16858
exploit/multi/fileformat/nodejs_js_yaml_load_code_exec CVE-2013-4660
exploit/multi/fileformat/peazip_command_injection CVE-2009-2261
exploit/multi/fileformat/swagger_param_inject CVE-2016-5641
exploit/multi/ftp/pureftpd_bash_env_exec CVE-2014-6271
exploit/multi/ftp/wuftpd_site_exec_format CVE-2000-0573
exploit/multi/http/activecollab_chat CVE-2012-6554
exploit/multi/http/apache_activemq_upload_jsp CVE-2016-3088
exploit/multi/http/apache_jetspeed_file_upload CVE-2016-0710
exploit/multi/http/apache_jetspeed_file_upload CVE-2016-0709
exploit/multi/http/apache_mod_cgi_bash_env_exec CVE-2014-6271
exploit/multi/http/apache_mod_cgi_bash_env_exec CVE-2014-6278
exploit/multi/http/apache_roller_ognl_injection CVE-2013-4212
exploit/multi/http/apprain_upload_exec CVE-2012-1153
exploit/multi/http/atutor_sqli CVE-2016-2555
exploit/multi/http/axis2_deployer CVE-2010-0219
exploit/multi/http/bassmaster_js_injection CVE-2014-7205
exploit/multi/http/bolt_file_upload CVE-2015-7309
exploit/multi/http/cisco_dcnm_upload CVE-2013-5486
exploit/multi/http/cisco_dcnm_upload_2019 CVE-2019-1619
exploit/multi/http/cisco_dcnm_upload_2019 CVE-2019-1620
exploit/multi/http/cisco_dcnm_upload_2019 CVE-2019-1622
exploit/multi/http/clipbucket_fileupload_exec CVE-2018-7665
exploit/multi/http/cmsms_object_injection_rce CVE-2019-9055
exploit/multi/http/cmsms_showtime2_rce CVE-2019-9692
exploit/multi/http/cmsms_upload_rename_rce CVE-2018-1000094
exploit/multi/http/coldfusion_ckeditor_file_upload CVE-2018-15961
exploit/multi/http/coldfusion_rds_auth_bypass CVE-2013-0632
exploit/multi/http/confluence_widget_connector CVE-2019-3396
exploit/multi/http/cups_bash_env_exec CVE-2014-6271
exploit/multi/http/cups_bash_env_exec CVE-2014-6278
exploit/multi/http/drupal_drupageddon CVE-2014-3704
exploit/multi/http/eventlog_file_upload CVE-2014-6037
exploit/multi/http/familycms_less_exec CVE-2011-5130
exploit/multi/http/getsimplecms_unauth_code_exec CVE-2019-11231
exploit/multi/http/git_client_command_exec CVE-2014-9390
exploit/multi/http/git_submodule_command_exec CVE-2017-1000117
exploit/multi/http/git_submodule_url_exec CVE-2018-17456
exploit/multi/http/gitlab_shell_exec CVE-2013-4490
exploit/multi/http/gitlist_arg_injection CVE-2018-1000533
exploit/multi/http/glassfish_deployer CVE-2011-0807
exploit/multi/http/glpi_install_rce CVE-2013-5696
exploit/multi/http/horde_csv_rce CVE-2020-8518
exploit/multi/http/horde_form_file_upload CVE-2019-9858
exploit/multi/http/horde_href_backdoor CVE-2012-0209
exploit/multi/http/hp_sitescope_issuesiebelcmd CVE-2013-4835
exploit/multi/http/hp_sitescope_uploadfileshandler CVE-2012-3260
exploit/multi/http/hp_sitescope_uploadfileshandler CVE-2012-3261
exploit/multi/http/hp_sys_mgmt_exec CVE-2013-3576
exploit/multi/http/ibm_openadmin_tool_soap_welcomeserver_exec CVE-2017-1092
exploit/multi/http/ispconfig_php_exec CVE-2013-3629
exploit/multi/http/jboss_bshdeployer CVE-2010-0738
exploit/multi/http/jboss_deploymentfilerepository CVE-2010-0738
exploit/multi/http/jboss_invoke_deploy CVE-2007-1036
exploit/multi/http/jboss_maindeployer CVE-2007-1036
exploit/multi/http/jboss_maindeployer CVE-2010-0738
exploit/multi/http/jboss_seam_upload_exec CVE-2010-1871
exploit/multi/http/jenkins_metaprogramming CVE-2018-1000861
exploit/multi/http/jenkins_metaprogramming CVE-2019-1003000
exploit/multi/http/jenkins_metaprogramming CVE-2019-1003001
exploit/multi/http/jenkins_metaprogramming CVE-2019-1003002
exploit/multi/http/jenkins_metaprogramming CVE-2019-1003005
exploit/multi/http/jenkins_metaprogramming CVE-2019-1003029
exploit/multi/http/jenkins_xstream_deserialize CVE-2016-0792
exploit/multi/http/jira_hipchat_template CVE-2015-5603
exploit/multi/http/joomla_http_header_rce CVE-2015-8562
exploit/multi/http/lcms_php_exec CVE-2011-0518
exploit/multi/http/liferay_java_unmarshalling CVE-2020-7961
exploit/multi/http/log1cms_ajax_create_folder CVE-2011-4825
exploit/multi/http/magento_unserialize CVE-2016-4010
exploit/multi/http/manage_engine_dc_pmp_sqli CVE-2014-3996
exploit/multi/http/manageengine_auth_upload CVE-2014-5301
exploit/multi/http/mantisbt_manage_proj_page_rce CVE-2008-4687
exploit/multi/http/mantisbt_php_exec CVE-2014-7146
exploit/multi/http/mantisbt_php_exec CVE-2014-8598
exploit/multi/http/mediawiki_syntaxhighlight CVE-2017-0372
exploit/multi/http/mediawiki_thumb CVE-2014-1610
exploit/multi/http/monstra_fileupload_exec CVE-2017-18048
exploit/multi/http/moodle_cmd_exec CVE-2013-3630
exploit/multi/http/movabletype_upgrade_exec CVE-2012-6315
exploit/multi/http/movabletype_upgrade_exec CVE-2013-0209
exploit/multi/http/mutiny_subnetmask_exec CVE-2012-3001
exploit/multi/http/nas4free_php_exec CVE-2013-3631
exploit/multi/http/navigate_cms_rce CVE-2018-17552
exploit/multi/http/navigate_cms_rce CVE-2018-17553
exploit/multi/http/nibbleblog_file_upload CVE-2015-6967
exploit/multi/http/nostromo_code_exec CVE-2019-16278
exploit/multi/http/novell_servicedesk_rce CVE-2016-1593
exploit/multi/http/nuuo_nvrmini_upgrade_rce CVE-2018-14933
exploit/multi/http/october_upload_bypass_exec CVE-2017-1000119
exploit/multi/http/op5_license CVE-2012-0261
exploit/multi/http/op5_welcome CVE-2012-0262
exploit/multi/http/openfire_auth_bypass CVE-2008-6508
exploit/multi/http/openmediavault_cmd_exec CVE-2013-3632
exploit/multi/http/openmrs_deserialization CVE-2018-19276
exploit/multi/http/openx_backdoor_php CVE-2013-4211
exploit/multi/http/opmanager_socialit_file_upload CVE-2014-6034
exploit/multi/http/oracle_ats_file_upload CVE-2016-0492
exploit/multi/http/oracle_ats_file_upload CVE-2016-0491
exploit/multi/http/oracle_reports_rce CVE-2012-3152
exploit/multi/http/oracle_reports_rce CVE-2012-3153
exploit/multi/http/oracle_weblogic_wsat_deserialization_rce CVE-2017-10271
exploit/multi/http/orientdb_exec CVE-2017-11467
exploit/multi/http/pandora_upload_exec CVE-2010-4279
exploit/multi/http/php_cgi_arg_injection CVE-2012-1823
exploit/multi/http/php_fpm_rce CVE-2019-11043
exploit/multi/http/phpfilemanager_rce CVE-2015-5958
exploit/multi/http/phpldapadmin_query_engine CVE-2011-4075
exploit/multi/http/phpmailer_arg_injection CVE-2016-10033
exploit/multi/http/phpmailer_arg_injection CVE-2016-10045
exploit/multi/http/phpmoadmin_exec CVE-2015-2208
exploit/multi/http/phpmyadmin_3522_backdoor CVE-2012-5159
exploit/multi/http/phpmyadmin_lfi_rce CVE-2018-12613
exploit/multi/http/phpmyadmin_null_termination_exec CVE-2016-5734
exploit/multi/http/phpmyadmin_preg_replace CVE-2013-3238
exploit/multi/http/phpscheduleit_start_date CVE-2008-6132
exploit/multi/http/phpwiki_ploticus_exec CVE-2014-5519
exploit/multi/http/pimcore_unserialize_rce CVE-2019-10867
exploit/multi/http/playsms_filename_exec CVE-2017-9080
exploit/multi/http/playsms_template_injection CVE-2020-8644
exploit/multi/http/playsms_uploadcsv_exec CVE-2017-9101
exploit/multi/http/plone_popen2 CVE-2011-3587
exploit/multi/http/pmwiki_pagelist CVE-2011-4453
exploit/multi/http/polarcms_upload_exec CVE-2013-0803
exploit/multi/http/rails_actionpack_inline_exec CVE-2016-2098
exploit/multi/http/rails_double_tap CVE-2019-5420
exploit/multi/http/rails_dynamic_render_code_exec CVE-2016-0752
exploit/multi/http/rails_json_yaml_code_exec CVE-2013-0333
exploit/multi/http/rails_secret_deserialization CVE-2013-0156
exploit/multi/http/rails_web_console_v2_code_exec CVE-2015-3224
exploit/multi/http/rails_xml_yaml_code_exec CVE-2013-0156
exploit/multi/http/rocket_servergraph_file_requestor_rce CVE-2014-3914
exploit/multi/http/shopware_createinstancefromnamedarguments_rce CVE-2019-12799
exploit/multi/http/shopware_createinstancefromnamedarguments_rce CVE-2017-18357
exploit/multi/http/sit_file_upload CVE-2011-3829
exploit/multi/http/sit_file_upload CVE-2011-3833
exploit/multi/http/solarwinds_store_manager_auth_filter CVE-2015-5371
exploit/multi/http/solr_velocity_rce CVE-2019-17558
exploit/multi/http/sonicwall_gms_upload CVE-2013-1359
exploit/multi/http/sonicwall_scrutinizer_methoddetail_sqli CVE-2014-4977
exploit/multi/http/splunk_mappy_exec CVE-2011-4642
exploit/multi/http/struts2_code_exec_showcase CVE-2017-9791
exploit/multi/http/struts2_content_type_ognl CVE-2017-5638
exploit/multi/http/struts2_namespace_ognl CVE-2018-11776
exploit/multi/http/struts2_rest_xstream CVE-2017-9805
exploit/multi/http/struts_code_exec CVE-2010-1870
exploit/multi/http/struts_code_exec_classloader CVE-2014-0094
exploit/multi/http/struts_code_exec_classloader CVE-2014-0112
exploit/multi/http/struts_code_exec_classloader CVE-2014-0114
exploit/multi/http/struts_code_exec_exception_delegator CVE-2012-0391
exploit/multi/http/struts_code_exec_parameters CVE-2011-3923
exploit/multi/http/struts_default_action_mapper CVE-2013-2251
exploit/multi/http/struts_dev_mode CVE-2012-0394
exploit/multi/http/struts_dmi_exec CVE-2016-3081
exploit/multi/http/struts_dmi_rest_exec CVE-2016-3087
exploit/multi/http/struts_include_params CVE-2013-2115
exploit/multi/http/struts_include_params CVE-2013-1966
exploit/multi/http/sun_jsws_dav_options CVE-2010-0361
exploit/multi/http/sysaid_auth_file_upload CVE-2015-2994
exploit/multi/http/sysaid_rdslogs_file_upload CVE-2015-2995
exploit/multi/http/testlink_upload_exec CVE-2012-0938
exploit/multi/http/tomcat_jsp_upload_bypass CVE-2017-12617
exploit/multi/http/tomcat_mgr_deploy CVE-2009-3843
exploit/multi/http/tomcat_mgr_deploy CVE-2009-4189
exploit/multi/http/tomcat_mgr_deploy CVE-2009-4188
exploit/multi/http/tomcat_mgr_deploy CVE-2010-0557
exploit/multi/http/tomcat_mgr_deploy CVE-2010-4094
exploit/multi/http/tomcat_mgr_deploy CVE-2009-3548
exploit/multi/http/tomcat_mgr_upload CVE-2009-3843
exploit/multi/http/tomcat_mgr_upload CVE-2009-4189
exploit/multi/http/tomcat_mgr_upload CVE-2009-4188
exploit/multi/http/tomcat_mgr_upload CVE-2010-0557
exploit/multi/http/tomcat_mgr_upload CVE-2010-4094
exploit/multi/http/tomcat_mgr_upload CVE-2009-3548
exploit/multi/http/totaljs_cms_widget_exec CVE-2019-15954
exploit/multi/http/trendmicro_threat_discovery_admin_sys_time_cmdi CVE-2016-7552
exploit/multi/http/trendmicro_threat_discovery_admin_sys_time_cmdi CVE-2016-7547
exploit/multi/http/vbseo_proc_deutf CVE-2012-5223
exploit/multi/http/vbulletin_unserialize CVE-2015-7808
exploit/multi/http/vbulletin_widgetconfig_rce CVE-2019-16759
exploit/multi/http/visual_mining_netcharts_upload CVE-2014-8516
exploit/multi/http/vtiger_install_rce CVE-2014-2268
exploit/multi/http/vtiger_logo_upload_exec CVE-2015-6000
exploit/multi/http/vtiger_logo_upload_exec CVE-2016-1713
exploit/multi/http/vtiger_php_exec CVE-2013-3591
exploit/multi/http/vtiger_soap_upload CVE-2013-3214
exploit/multi/http/vtiger_soap_upload CVE-2013-3215
exploit/multi/http/webnms_file_upload CVE-2016-6600
exploit/multi/http/wikka_spam_exec CVE-2011-4451
exploit/multi/http/wp_crop_rce CVE-2019-8942
exploit/multi/http/wp_crop_rce CVE-2019-8943
exploit/multi/http/wp_ninja_forms_unauthenticated_file_upload CVE-2016-1209
exploit/multi/http/x7chat2_php_exec CVE-2014-8998
exploit/multi/http/zabbix_script_exec CVE-2013-3628
exploit/multi/http/zenworks_configuration_management_upload CVE-2015-0779
exploit/multi/http/zenworks_control_center_upload CVE-2013-1080
exploit/multi/ids/snort_dce_rpc CVE-2006-5276
exploit/multi/local/allwinner_backdoor CVE-2016-10225
exploit/multi/local/magnicomp_sysinfo_mcsiwrapper_priv_esc CVE-2017-6516
exploit/multi/local/xorg_x11_suid_server CVE-2018-14665
exploit/multi/local/xorg_x11_suid_server_modulepath CVE-2018-14665
exploit/multi/misc/arkeia_agent_exec CVE-2015-7709
exploit/multi/misc/bmc_patrol_cmd_exec CVE-2018-20735
exploit/multi/misc/bmc_server_automation_rscd_nsh_rce CVE-2016-1542
exploit/multi/misc/bmc_server_automation_rscd_nsh_rce CVE-2016-1543
exploit/multi/misc/claymore_dual_miner_remote_manager_rce CVE-2018-1000049
exploit/multi/misc/hp_vsa_exec CVE-2012-4361
exploit/multi/misc/ibm_tm1_unauth_rce CVE-2019-4716
exploit/multi/misc/java_jmx_server CVE-2015-2342
exploit/multi/misc/java_rmi_server CVE-2011-3556
exploit/multi/misc/openview_omniback_exec CVE-2001-0311
exploit/multi/misc/persistent_hpca_radexec_exec CVE-2015-1497
exploit/multi/misc/veritas_netbackup_cmdexec CVE-2004-1389
exploit/multi/misc/weblogic_deserialize CVE-2018-2628
exploit/multi/misc/weblogic_deserialize_asyncresponseservice CVE-2017-10271
exploit/multi/misc/weblogic_deserialize_marshalledobject CVE-2016-3510
exploit/multi/misc/weblogic_deserialize_rawobject CVE-2015-4852
exploit/multi/misc/weblogic_deserialize_unicastref CVE-2017-3248
exploit/multi/misc/wireshark_lwres_getaddrbyname CVE-2010-0304
exploit/multi/misc/wireshark_lwres_getaddrbyname_loop CVE-2010-0304
exploit/multi/ntp/ntp_overflow CVE-2001-0414
exploit/multi/php/php_unserialize_zval_cookie CVE-2007-1286
exploit/multi/php/wp_duplicator_code_inject CVE-2018-17207
exploit/multi/postgres/postgres_copy_from_program_cmd_exec CVE-2019-9193
exploit/multi/realserver/describe CVE-2002-1643
exploit/multi/samba/nttrans CVE-2002-1318
exploit/multi/samba/usermap_script CVE-2007-2447
exploit/multi/ssh/sshexec CVE-1999-0502
exploit/multi/svn/svnserve_date CVE-2004-0397
exploit/multi/upnp/libupnp_ssdp_overflow CVE-2012-5958
exploit/multi/vpn/tincd_bof CVE-2013-1428
exploit/multi/wyse/hagent_untrusted_hsdata CVE-2009-0695
exploit/netware/smb/lsass_cifs CVE-2005-2852
exploit/openbsd/local/dynamic_loader_chpass_privesc CVE-2019-19726
exploit/osx/afp/loginext CVE-2004-0430
exploit/osx/arkeia/type77 CVE-2005-0491
exploit/osx/browser/adobe_flash_delete_range_tl_op CVE-2016-4117
exploit/osx/browser/mozilla_mchannel CVE-2011-0065
exploit/osx/browser/safari_file_policy CVE-2011-3230
exploit/osx/browser/safari_metadata_archive CVE-2006-0848
exploit/osx/browser/safari_proxy_object_type_confusion CVE-2018-4233
exploit/osx/browser/safari_proxy_object_type_confusion CVE-2018-4404
exploit/osx/browser/safari_user_assisted_applescript_exec CVE-2015-7007
exploit/osx/browser/software_update CVE-2007-5863
exploit/osx/email/mailapp_image_exec CVE-2006-0395
exploit/osx/email/mailapp_image_exec CVE-2007-6165
exploit/osx/ftp/webstar_ftp_user CVE-2004-0695
exploit/osx/http/evocam_webserver CVE-2010-2309
exploit/osx/local/dyld_print_to_file_root CVE-2015-3760
exploit/osx/local/feedback_assistant_root CVE-2019-8565
exploit/osx/local/iokit_keyboard_root CVE-2014-4404
exploit/osx/local/libxpc_mitm_ssudo CVE-2018-4237
exploit/osx/local/root_no_password CVE-2017-13872
exploit/osx/local/rootpipe CVE-2015-1130
exploit/osx/local/rootpipe_entitlements CVE-2015-3673
exploit/osx/local/rsh_libmalloc CVE-2015-5889
exploit/osx/local/setuid_tunnelblick CVE-2012-3485
exploit/osx/local/setuid_viscosity CVE-2012-4284
exploit/osx/local/sudo_password_bypass CVE-2013-1775
exploit/osx/local/timemachine_cmd_injection CVE-2019-8513
exploit/osx/local/vmware_bash_function_root CVE-2014-6271
exploit/osx/local/vmware_fusion_lpe CVE-2020-3950
exploit/osx/mdns/upnp_location CVE-2007-2386
exploit/osx/rtsp/quicktime_rtsp_content_type CVE-2007-6166
exploit/osx/samba/lsa_transnames_heap CVE-2007-2446
exploit/osx/samba/trans2open CVE-2003-0201
exploit/qnx/local/ifwatchd_priv_esc CVE-2014-2533
exploit/solaris/dtspcd/heap_noir CVE-2001-0803
exploit/solaris/local/extremeparr_dtappgather_priv_esc CVE-2017-3622
exploit/solaris/local/libnspr_nspr_log_file_priv_esc CVE-2006-4842
exploit/solaris/local/rsh_stack_clash_priv_esc CVE-2017-1000364
exploit/solaris/local/rsh_stack_clash_priv_esc CVE-2017-3629
exploit/solaris/local/rsh_stack_clash_priv_esc CVE-2017-3630
exploit/solaris/local/rsh_stack_clash_priv_esc CVE-2017-3631
exploit/solaris/local/xscreensaver_log_priv_esc CVE-2019-3010
exploit/solaris/lpd/sendmail_exec CVE-2001-1583
exploit/solaris/samba/lsa_transnames_heap CVE-2007-2446
exploit/solaris/samba/trans2open CVE-2003-0201
exploit/solaris/sunrpc/sadmind_adm_build_path CVE-2008-4556
exploit/solaris/sunrpc/sadmind_exec CVE-2003-0722
exploit/solaris/sunrpc/ypupdated_exec CVE-1999-0209
exploit/solaris/telnet/fuser CVE-2007-0882
exploit/solaris/telnet/ttyprompt CVE-2001-0797
exploit/unix/dhcp/bash_environment CVE-2014-6271
exploit/unix/dhcp/rhel_dhcp_client_command_injection CVE-2018-1111
exploit/unix/fileformat/ghostscript_type_confusion CVE-2017-8291
exploit/unix/fileformat/imagemagick_delegate CVE-2016-3714
exploit/unix/fileformat/imagemagick_delegate CVE-2016-7976
exploit/unix/ftp/proftpd_modcopy_exec CVE-2015-3306
exploit/unix/http/ctek_skyrouter CVE-2011-5010
exploit/unix/http/epmp1000_get_chart_cmd_shell CVE-2017-5255
exploit/unix/http/epmp1000_ping_cmd_shell CVE-2017-5255
exploit/unix/http/freepbx_callmenum CVE-2012-4869
exploit/unix/http/laravel_token_unserialize_exec CVE-2018-15133
exploit/unix/http/laravel_token_unserialize_exec CVE-2017-16894
exploit/unix/http/lifesize_room CVE-2011-2763
exploit/unix/http/pfsense_clickjacking CVE-2017-1000479
exploit/unix/http/pfsense_graph_injection_exec CVE-2016-10709
exploit/unix/http/quest_kace_systems_management_rce CVE-2018-11138
exploit/unix/http/schneider_electric_net55xx_encoder CVE-2019-6814
exploit/unix/http/tnftp_savefile CVE-2014-8517
exploit/unix/http/twiki_debug_plugins CVE-2014-7236
exploit/unix/http/vmturbo_vmtadmin_exec_noauth CVE-2014-5073
exploit/unix/irc/unreal_ircd_3281_backdoor CVE-2010-2075
exploit/unix/local/chkrootkit CVE-2014-0476
exploit/unix/local/exim_perl_startup CVE-2016-1531
exploit/unix/local/netbsd_mail_local CVE-2016-6253
exploit/unix/local/opensmtpd_oob_read_lpe CVE-2020-8794
exploit/unix/misc/distcc_exec CVE-2004-2687
exploit/unix/misc/spamassassin_exec CVE-2006-2447
exploit/unix/misc/zabbix_agent_exec CVE-2009-4502
exploit/unix/smtp/clamav_milter_blackhole CVE-2007-4560
exploit/unix/smtp/exim4_string_format CVE-2010-4344
exploit/unix/smtp/exim4_string_format CVE-2010-4345
exploit/unix/smtp/opensmtpd_mail_from_rce CVE-2020-7247
exploit/unix/smtp/qmail_bash_env_exec CVE-2014-6271
exploit/unix/ssh/tectia_passwd_changereq CVE-2012-5975
exploit/unix/webapp/actualanalyzer_ant_cookie_exec CVE-2014-5470
exploit/unix/webapp/awstats_configdir_exec CVE-2005-0116
exploit/unix/webapp/awstats_migrate_exec CVE-2006-2237
exploit/unix/webapp/awstatstotals_multisort CVE-2008-3922
exploit/unix/webapp/barracuda_img_exec CVE-2005-2847
exploit/unix/webapp/base_qry_common CVE-2006-2685
exploit/unix/webapp/basilic_diff_exec CVE-2012-3399
exploit/unix/webapp/cakephp_cache_corruption CVE-2010-4335
exploit/unix/webapp/citrix_access_gateway_exec CVE-2010-4566
exploit/unix/webapp/coppermine_piceditor CVE-2008-0506
exploit/unix/webapp/datalife_preview_exec CVE-2013-1412
exploit/unix/webapp/drupal_drupalgeddon2 CVE-2018-7600
exploit/unix/webapp/drupal_restws_unserialize CVE-2019-6340
exploit/unix/webapp/elfinder_php_connector_exiftran_cmd_injection CVE-2019-9194
exploit/unix/webapp/foswiki_maketext CVE-2012-6329
exploit/unix/webapp/freepbx_config_exec CVE-2014-1903
exploit/unix/webapp/fusionpbx_operator_panel_exec_cmd_exec CVE-2019-11409
exploit/unix/webapp/google_proxystylesheet_exec CVE-2005-3757
exploit/unix/webapp/graphite_pickle_exec CVE-2013-5093
exploit/unix/webapp/guestbook_ssi_exec CVE-1999-1053
exploit/unix/webapp/hastymail_exec CVE-2011-4542
exploit/unix/webapp/horde_unserialize_exec CVE-2014-1691
exploit/unix/webapp/invision_pboard_unserialize_exec CVE-2012-5692
exploit/unix/webapp/joomla_akeeba_unserialize CVE-2014-7228
exploit/unix/webapp/joomla_comfields_sqli_rce CVE-2017-8917
exploit/unix/webapp/joomla_contenthistory_sqli_rce CVE-2015-7857
exploit/unix/webapp/joomla_contenthistory_sqli_rce CVE-2015-7297
exploit/unix/webapp/joomla_contenthistory_sqli_rce CVE-2015-7857
exploit/unix/webapp/joomla_contenthistory_sqli_rce CVE-2015-7858
exploit/unix/webapp/joomla_media_upload_exec CVE-2013-5576
exploit/unix/webapp/joomla_tinybrowser CVE-2011-4908
exploit/unix/webapp/jquery_file_upload CVE-2018-9206
exploit/unix/webapp/maarch_letterbox_file_upload CVE-2015-1587
exploit/unix/webapp/mambo_cache_lite CVE-2008-2905
exploit/unix/webapp/moinmoin_twikidraw CVE-2012-6081
exploit/unix/webapp/nagios3_history_cgi CVE-2012-6096
exploit/unix/webapp/nagios3_statuswml_ping CVE-2009-2288
exploit/unix/webapp/open_flash_chart_upload_exec CVE-2009-4140
exploit/unix/webapp/openemr_upload_exec CVE-2009-4140
exploit/unix/webapp/opensis_modname_exec CVE-2013-1349
exploit/unix/webapp/openview_connectednodes_exec CVE-2005-2773
exploit/unix/webapp/openx_banner_edit CVE-2009-4098
exploit/unix/webapp/oracle_vm_agent_utl CVE-2010-3585
exploit/unix/webapp/pajax_remote_exec CVE-2006-1551
exploit/unix/webapp/php_vbulletin_template CVE-2005-0511
exploit/unix/webapp/php_xmlrpc_eval CVE-2005-1921
exploit/unix/webapp/phpbb_highlight CVE-2005-2086
exploit/unix/webapp/phpbb_highlight CVE-2004-1315
exploit/unix/webapp/phpcollab_upload_exec CVE-2017-6090
exploit/unix/webapp/phpmyadmin_config CVE-2009-1151
exploit/unix/webapp/qtss_parse_xml_exec CVE-2003-0050
exploit/unix/webapp/rconfig_install_cmd_exec CVE-2019-16662
exploit/unix/webapp/redmine_scm_exec CVE-2011-4929
exploit/unix/webapp/seportal_sqli_exec CVE-2008-5191
exploit/unix/webapp/sixapart_movabletype_storable_exec CVE-2015-1592
exploit/unix/webapp/skybluecanvas_exec CVE-2014-1683
exploit/unix/webapp/sphpblog_file_upload CVE-2005-2733
exploit/unix/webapp/squash_yaml_exec CVE-2013-5036
exploit/unix/webapp/squirrelmail_pgp_plugin CVE-2003-0990
exploit/unix/webapp/sugarcrm_unserialize_exec CVE-2012-0694
exploit/unix/webapp/thinkphp_rce CVE-2018-20062
exploit/unix/webapp/thinkphp_rce CVE-2019-9082
exploit/unix/webapp/tikiwiki_graph_formula_exec CVE-2007-5423
exploit/unix/webapp/tikiwiki_jhot_exec CVE-2006-4602
exploit/unix/webapp/tikiwiki_unserialize_exec CVE-2012-0911
exploit/unix/webapp/trixbox_langchoice CVE-2008-6825
exploit/unix/webapp/tuleap_rest_unserialize_exec CVE-2017-7411
exploit/unix/webapp/tuleap_unserialize_exec CVE-2014-8791
exploit/unix/webapp/twiki_history CVE-2005-2877
exploit/unix/webapp/twiki_maketext CVE-2012-6329
exploit/unix/webapp/twiki_search CVE-2004-1037
exploit/unix/webapp/vbulletin_vote_sqli_exec CVE-2013-3522
exploit/unix/webapp/vicidial_manager_send_cmd_exec CVE-2013-4467
exploit/unix/webapp/vicidial_manager_send_cmd_exec CVE-2013-4468
exploit/unix/webapp/webmin_show_cgi_exec CVE-2012-2982
exploit/unix/webapp/webmin_upload_exec CVE-2019-9624
exploit/unix/webapp/wp_easycart_unrestricted_file_upload CVE-2014-9308
exploit/unix/webapp/wp_google_document_embedder_exec CVE-2012-4915
exploit/unix/webapp/wp_holding_pattern_file_upload CVE-2015-1172
exploit/unix/webapp/wp_infusionsoft_upload CVE-2014-6446
exploit/unix/webapp/wp_lastpost_exec CVE-2005-2612
exploit/unix/webapp/wp_optimizepress_upload CVE-2013-7102
exploit/unix/webapp/wp_photo_gallery_unrestricted_file_upload CVE-2014-9312
exploit/unix/webapp/wp_phpmailer_host_header CVE-2016-10033
exploit/unix/webapp/wp_pixabay_images_upload CVE-2015-1376
exploit/unix/webapp/wp_plainview_activity_monitor_rce CVE-2018-15877
exploit/unix/webapp/wp_reflexgallery_file_upload CVE-2015-4133
exploit/unix/webapp/wp_revslider_upload_execute CVE-2014-9735
exploit/unix/webapp/wp_slideshowgallery_upload CVE-2014-5460
exploit/unix/webapp/wp_total_cache_exec CVE-2013-2010
exploit/unix/webapp/xymon_useradm_cmd_exec CVE-2016-2056
exploit/unix/webapp/zeroshell_exec CVE-2009-0545
exploit/unix/webapp/zimbra_lfi CVE-2013-7091
exploit/unix/webapp/zoneminder_packagecontrol_exec CVE-2013-0232
exploit/windows/antivirus/ams_hndlrsvc CVE-2010-0111
exploit/windows/antivirus/ams_xfr CVE-2009-1429
exploit/windows/antivirus/symantec_endpoint_manager_rce CVE-2013-5014
exploit/windows/antivirus/symantec_endpoint_manager_rce CVE-2013-5015
exploit/windows/antivirus/symantec_iao CVE-2009-1430
exploit/windows/antivirus/symantec_rtvscan CVE-2006-2630
exploit/windows/antivirus/symantec_workspace_streaming_exec CVE-2014-1649
exploit/windows/antivirus/trendmicro_serverprotect CVE-2007-1070
exploit/windows/antivirus/trendmicro_serverprotect_createbinding CVE-2007-2508
exploit/windows/antivirus/trendmicro_serverprotect_earthagent CVE-2007-2508
exploit/windows/arkeia/type77 CVE-2005-0491
exploit/windows/backdoor/energizer_duo_payload CVE-2010-0103
exploit/windows/backupexec/name_service CVE-2004-1172
exploit/windows/backupexec/remote_agent CVE-2005-0773
exploit/windows/backupexec/ssl_uaf CVE-2017-8895
exploit/windows/brightstor/ca_arcserve_342 CVE-2008-4397
exploit/windows/brightstor/discovery_tcp CVE-2005-2535
exploit/windows/brightstor/discovery_udp CVE-2005-0260
exploit/windows/brightstor/etrust_itm_alert CVE-2007-4620
exploit/windows/brightstor/hsmserver CVE-2007-5082
exploit/windows/brightstor/lgserver CVE-2007-0449
exploit/windows/brightstor/lgserver_multi CVE-2007-3216
exploit/windows/brightstor/lgserver_rxrlogin CVE-2007-5003
exploit/windows/brightstor/lgserver_rxssetdatagrowthscheduleandfilter CVE-2007-3216
exploit/windows/brightstor/lgserver_rxsuselicenseini CVE-2007-3216
exploit/windows/brightstor/license_gcr CVE-2005-0581
exploit/windows/brightstor/mediasrv_sunrpc CVE-2007-2139
exploit/windows/brightstor/message_engine CVE-2007-0169
exploit/windows/brightstor/message_engine_heap CVE-2006-5143
exploit/windows/brightstor/sql_agent CVE-2005-1272
exploit/windows/brightstor/tape_engine CVE-2006-6076
exploit/windows/brightstor/universal_agent CVE-2005-1018
exploit/windows/browser/adobe_cooltype_sing CVE-2010-2883
exploit/windows/browser/adobe_flash_avm2 CVE-2014-0497
exploit/windows/browser/adobe_flash_casi32_int_overflow CVE-2014-0569
exploit/windows/browser/adobe_flash_copy_pixels_to_byte_array CVE-2014-0556
exploit/windows/browser/adobe_flash_domain_memory_uaf CVE-2015-0359
exploit/windows/browser/adobe_flash_filters_type_confusion CVE-2013-5331
exploit/windows/browser/adobe_flash_mp4_cprt CVE-2012-0754
exploit/windows/browser/adobe_flash_otf_font CVE-2012-1535
exploit/windows/browser/adobe_flash_pcre CVE-2015-0318
exploit/windows/browser/adobe_flash_regex_value CVE-2013-0634
exploit/windows/browser/adobe_flash_rtmp CVE-2012-0779
exploit/windows/browser/adobe_flash_sps CVE-2011-2140
exploit/windows/browser/adobe_flash_uncompress_zlib_uninitialized CVE-2014-8440
exploit/windows/browser/adobe_flash_worker_byte_array_uaf CVE-2015-0313
exploit/windows/browser/adobe_flashplayer_arrayindexing CVE-2011-2110
exploit/windows/browser/adobe_flashplayer_avm CVE-2011-0609
exploit/windows/browser/adobe_flashplayer_flash10o CVE-2011-0611
exploit/windows/browser/adobe_flashplayer_newfunction CVE-2010-1297
exploit/windows/browser/adobe_flatedecode_predictor02 CVE-2009-3459
exploit/windows/browser/adobe_geticon CVE-2009-0927
exploit/windows/browser/adobe_jbig2decode CVE-2009-0658
exploit/windows/browser/adobe_media_newplayer CVE-2009-4324
exploit/windows/browser/adobe_shockwave_rcsl_corruption CVE-2010-3653
exploit/windows/browser/adobe_toolbutton CVE-2013-3346
exploit/windows/browser/adobe_utilprintf CVE-2008-2992
exploit/windows/browser/advantech_webaccess_dvs_getcolor CVE-2014-2364
exploit/windows/browser/aim_goaway CVE-2004-0636
exploit/windows/browser/amaya_bdo CVE-2009-0323
exploit/windows/browser/aol_icq_downloadagent CVE-2006-5650
exploit/windows/browser/apple_itunes_playlist CVE-2005-0043
exploit/windows/browser/apple_quicktime_marshaled_punk CVE-2010-1818
exploit/windows/browser/apple_quicktime_mime_type CVE-2012-3753
exploit/windows/browser/apple_quicktime_rdrf CVE-2013-1017
exploit/windows/browser/apple_quicktime_rtsp CVE-2007-0015
exploit/windows/browser/apple_quicktime_smil_debug CVE-2010-1799
exploit/windows/browser/apple_quicktime_texml_font_table CVE-2012-3752
exploit/windows/browser/ask_shortformat CVE-2007-5107
exploit/windows/browser/asus_net4switch_ipswcom CVE-2012-4924
exploit/windows/browser/awingsoft_web3d_bof CVE-2009-4588
exploit/windows/browser/awingsoft_winds3d_sceneurl CVE-2009-4850
exploit/windows/browser/baofeng_storm_onbeforevideodownload CVE-2009-1612
exploit/windows/browser/barcode_ax49 CVE-2007-3435
exploit/windows/browser/blackice_downloadimagefileurl CVE-2008-2683
exploit/windows/browser/c6_messenger_downloaderactivex CVE-2008-2551
exploit/windows/browser/ca_brightstor_addcolumn CVE-2008-1472
exploit/windows/browser/chilkat_crypt_writefile CVE-2008-5002
exploit/windows/browser/chrome_filereader_uaf CVE-2019-5786
exploit/windows/browser/cisco_anyconnect_exec CVE-2011-2039
exploit/windows/browser/cisco_playerpt_setsource CVE-2012-0284
exploit/windows/browser/cisco_playerpt_setsource_surl CVE-2012-0284
exploit/windows/browser/cisco_webex_ext CVE-2017-3823
exploit/windows/browser/citrix_gateway_actx CVE-2011-2882
exploit/windows/browser/clear_quest_cqole CVE-2012-0708
exploit/windows/browser/creative_software_cachefolder CVE-2008-0955
exploit/windows/browser/crystal_reports_printcontrol CVE-2010-2590
exploit/windows/browser/dxstudio_player_exec CVE-2009-2011
exploit/windows/browser/ea_checkrequirements CVE-2007-4466
exploit/windows/browser/ebook_flipviewer_fviewerloading CVE-2007-2919
exploit/windows/browser/enjoysapgui_comp_download CVE-2008-4830
exploit/windows/browser/enjoysapgui_preparetoposthtml CVE-2007-3605
exploit/windows/browser/exodus CVE-2018-1000006
exploit/windows/browser/facebook_extractiptc CVE-2008-5711
exploit/windows/browser/firefox_smil_uaf CVE-2016-9079
exploit/windows/browser/getgodm_http_response_bof CVE-2014-2206
exploit/windows/browser/gom_openurl CVE-2007-5779
exploit/windows/browser/honeywell_hscremotedeploy_exec CVE-2013-0108
exploit/windows/browser/hp_easy_printer_care_xmlcachemgr CVE-2011-4786
exploit/windows/browser/hp_easy_printer_care_xmlsimpleaccessor CVE-2011-2404
exploit/windows/browser/hp_loadrunner_addfile CVE-2008-0492
exploit/windows/browser/hp_loadrunner_addfolder CVE-2007-6530
exploit/windows/browser/hp_loadrunner_writefilebinary CVE-2013-2370
exploit/windows/browser/hp_loadrunner_writefilestring CVE-2013-4798
exploit/windows/browser/hpmqc_progcolor CVE-2007-1819
exploit/windows/browser/hyleos_chemviewx_activex CVE-2010-0679
exploit/windows/browser/ibm_spss_c1sizer CVE-2012-5946
exploit/windows/browser/ibm_tivoli_pme_activex_bof CVE-2012-0198
exploit/windows/browser/ibmegath_getxmlvalue CVE-2009-0215
exploit/windows/browser/ibmlotusdomino_dwa_uploadmodule CVE-2007-4474
exploit/windows/browser/ie_cbutton_uaf CVE-2012-4792
exploit/windows/browser/ie_cgenericelement_uaf CVE-2013-1347
exploit/windows/browser/ie_createobject CVE-2006-0003
exploit/windows/browser/ie_createobject CVE-2006-4704
exploit/windows/browser/ie_execcommand_uaf CVE-2012-4969
exploit/windows/browser/ie_iscomponentinstalled CVE-2006-1016
exploit/windows/browser/ie_setmousecapture_uaf CVE-2013-3893
exploit/windows/browser/imgeviewer_tifmergemultifiles CVE-2010-5193
exploit/windows/browser/indusoft_issymbol_internationalseparator CVE-2011-0340
exploit/windows/browser/inotes_dwa85w_bof CVE-2012-2175
exploit/windows/browser/intrust_annotatex_add CVE-2012-5896
exploit/windows/browser/java_basicservice_impl CVE-2010-3563
exploit/windows/browser/java_cmm CVE-2013-1493
exploit/windows/browser/java_codebase_trust CVE-2010-4452
exploit/windows/browser/java_docbase_bof CVE-2010-3552
exploit/windows/browser/java_mixer_sequencer CVE-2010-0842
exploit/windows/browser/java_ws_arginject_altjvm CVE-2010-0886
exploit/windows/browser/java_ws_arginject_altjvm CVE-2010-1423
exploit/windows/browser/java_ws_double_quote CVE-2012-1533
exploit/windows/browser/java_ws_vmargs CVE-2012-0500
exploit/windows/browser/juniper_sslvpn_ive_setupdll CVE-2006-2086
exploit/windows/browser/kazaa_altnet_heap CVE-2007-5217
exploit/windows/browser/keyhelp_launchtripane_exec CVE-2012-2516
exploit/windows/browser/logitechvideocall_start CVE-2007-2918
exploit/windows/browser/lpviewer_url CVE-2008-4384
exploit/windows/browser/macrovision_downloadandexecute CVE-2007-5660
exploit/windows/browser/macrovision_unsafe CVE-2007-5660
exploit/windows/browser/malwarebytes_update_exec CVE-2014-4936
exploit/windows/browser/mcafee_mcsubmgr_vsprintf CVE-2006-3961
exploit/windows/browser/mcafee_mvt_exec CVE-2012-4598
exploit/windows/browser/mcafeevisualtrace_tracetarget CVE-2006-6707
exploit/windows/browser/mirc_irc_url CVE-2003-1336
exploit/windows/browser/mozilla_attribchildremoved CVE-2011-3659
exploit/windows/browser/mozilla_firefox_onreadystatechange CVE-2013-1690
exploit/windows/browser/mozilla_firefox_xmlserializer CVE-2013-0753
exploit/windows/browser/mozilla_interleaved_write CVE-2010-3765
exploit/windows/browser/mozilla_mchannel CVE-2011-0065
exploit/windows/browser/mozilla_nssvgvalue CVE-2011-3658
exploit/windows/browser/mozilla_nstreerange CVE-2011-0073
exploit/windows/browser/mozilla_reduceright CVE-2011-2371
exploit/windows/browser/ms03_020_ie_objecttype CVE-2003-0344
exploit/windows/browser/ms05_054_onload CVE-2005-1790
exploit/windows/browser/ms06_001_wmf_setabortproc CVE-2005-4560
exploit/windows/browser/ms06_013_createtextrange CVE-2006-1359
exploit/windows/browser/ms06_055_vml_method CVE-2006-4868
exploit/windows/browser/ms06_057_webview_setslice CVE-2006-3730
exploit/windows/browser/ms06_067_keyframe CVE-2006-4777
exploit/windows/browser/ms06_071_xml_core CVE-2006-5745
exploit/windows/browser/ms07_017_ani_loadimage_chunksize CVE-2007-0038
exploit/windows/browser/ms08_041_snapshotviewer CVE-2008-2463
exploit/windows/browser/ms08_053_mediaencoder CVE-2008-3008
exploit/windows/browser/ms08_070_visual_studio_msmask CVE-2008-3704
exploit/windows/browser/ms08_078_xml_corruption CVE-2008-4844
exploit/windows/browser/ms09_002_memory_corruption CVE-2009-0075
exploit/windows/browser/ms09_043_owc_htmlurl CVE-2009-1534
exploit/windows/browser/ms09_043_owc_msdso CVE-2009-1136
exploit/windows/browser/ms09_072_style_object CVE-2009-3672
exploit/windows/browser/ms10_002_aurora CVE-2010-0249
exploit/windows/browser/ms10_002_ie_object CVE-2010-0248
exploit/windows/browser/ms10_018_ie_behaviors CVE-2010-0806
exploit/windows/browser/ms10_018_ie_tabular_activex CVE-2010-0805
exploit/windows/browser/ms10_022_ie_vbscript_winhlp32 CVE-2010-0483
exploit/windows/browser/ms10_026_avi_nsamplespersec CVE-2010-0480
exploit/windows/browser/ms10_042_helpctr_xss_cmd_exec CVE-2010-1885
exploit/windows/browser/ms10_046_shortcut_icon_dllloader CVE-2010-2568
exploit/windows/browser/ms10_090_ie_css_clip CVE-2010-3962
exploit/windows/browser/ms11_003_ie_css_import CVE-2010-3971
exploit/windows/browser/ms11_050_mshtml_cobjectelement CVE-2011-1260
exploit/windows/browser/ms11_081_option CVE-2011-1996
exploit/windows/browser/ms11_093_ole32 CVE-2011-3400
exploit/windows/browser/ms12_004_midi CVE-2012-0003
exploit/windows/browser/ms12_037_ie_colspan CVE-2012-1876
exploit/windows/browser/ms12_037_same_id CVE-2012-1875
exploit/windows/browser/ms13_009_ie_slayoutrun_uaf CVE-2013-0025
exploit/windows/browser/ms13_022_silverlight_script_object CVE-2013-0074
exploit/windows/browser/ms13_022_silverlight_script_object CVE-2013-3896
exploit/windows/browser/ms13_037_svg_dashstyle CVE-2013-2551
exploit/windows/browser/ms13_055_canchor CVE-2013-3163
exploit/windows/browser/ms13_059_cflatmarkuppointer CVE-2013-3184
exploit/windows/browser/ms13_069_caret CVE-2013-3205
exploit/windows/browser/ms13_080_cdisplaypointer CVE-2013-3897
exploit/windows/browser/ms13_090_cardspacesigninhelper CVE-2013-3918
exploit/windows/browser/ms14_012_cmarkup_uaf CVE-2014-0322
exploit/windows/browser/ms14_012_textrange CVE-2014-0307
exploit/windows/browser/ms14_064_ole_code_execution CVE-2014-6332
exploit/windows/browser/ms16_051_vbscript CVE-2016-0189
exploit/windows/browser/msvidctl_mpeg2 CVE-2008-0015
exploit/windows/browser/mswhale_checkforupdates CVE-2007-2238
exploit/windows/browser/msxml_get_definition_code_exec CVE-2012-1889
exploit/windows/browser/nctaudiofile2_setformatlikesample CVE-2007-0018
exploit/windows/browser/nis2004_antispam CVE-2004-0363
exploit/windows/browser/nis2004_get CVE-2007-1689
exploit/windows/browser/notes_handler_cmdinject CVE-2012-2174
exploit/windows/browser/novell_groupwise_gwcls1_actvx CVE-2012-0439
exploit/windows/browser/novelliprint_callbackurl CVE-2010-1527
exploit/windows/browser/novelliprint_datetime CVE-2009-1569
exploit/windows/browser/novelliprint_executerequest CVE-2008-0935
exploit/windows/browser/novelliprint_executerequest_dbg CVE-2010-3106
exploit/windows/browser/novelliprint_getdriversettings CVE-2008-2908
exploit/windows/browser/novelliprint_getdriversettings_2 CVE-2010-4321
exploit/windows/browser/novelliprint_target_frame CVE-2009-1568
exploit/windows/browser/ntr_activex_check_bof CVE-2012-0266
exploit/windows/browser/ntr_activex_stopmodule CVE-2012-0267
exploit/windows/browser/oracle_autovue_setmarkupmode CVE-2012-0549
exploit/windows/browser/oracle_dc_submittoexpress CVE-2007-4607
exploit/windows/browser/oracle_webcenter_checkoutandopen CVE-2013-1559
exploit/windows/browser/orbit_connecting CVE-2009-0187
exploit/windows/browser/ovftool_format_string CVE-2012-3569
exploit/windows/browser/pcvue_func CVE-2011-4044
exploit/windows/browser/persits_xupload_traversal CVE-2009-3693
exploit/windows/browser/quickr_qp2_bof CVE-2012-2176
exploit/windows/browser/realplayer_cdda_uri CVE-2010-3747
exploit/windows/browser/realplayer_console CVE-2008-1309
exploit/windows/browser/realplayer_import CVE-2007-5601
exploit/windows/browser/realplayer_qcp CVE-2011-2950
exploit/windows/browser/realplayer_smil CVE-2005-0455
exploit/windows/browser/roxio_cineplayer CVE-2007-1559
exploit/windows/browser/safari_xslt_output CVE-2011-1774
exploit/windows/browser/samsung_neti_wiewer_backuptoavi_bof CVE-2012-4333
exploit/windows/browser/sapgui_saveviewtosessionfile CVE-2007-4475
exploit/windows/browser/softartisans_getdrivename CVE-2007-1682
exploit/windows/browser/sonicwall_addrouteentry CVE-2007-5603
exploit/windows/browser/symantec_altirisdeployment_downloadandinstall CVE-2009-3028
exploit/windows/browser/symantec_altirisdeployment_runcmd CVE-2009-3033
exploit/windows/browser/symantec_appstream_unsafe CVE-2008-4388
exploit/windows/browser/symantec_backupexec_pvcalendar CVE-2007-6016
exploit/windows/browser/symantec_consoleutilities_browseandsavefile CVE-2009-3031
exploit/windows/browser/systemrequirementslab_unsafe CVE-2008-4385
exploit/windows/browser/tom_sawyer_tsgetx71ex552 CVE-2011-2217
exploit/windows/browser/trendmicro_extsetowner CVE-2010-3189
exploit/windows/browser/trendmicro_officescan CVE-2007-0325
exploit/windows/browser/tumbleweed_filetransfer CVE-2008-1724
exploit/windows/browser/ubisoft_uplay_cmd_exec CVE-2012-4177
exploit/windows/browser/ultramjcam_openfiledig_bof CVE-2012-4876
exploit/windows/browser/ultraoffice_httpupload CVE-2008-3878
exploit/windows/browser/verypdf_pdfview CVE-2008-5492
exploit/windows/browser/viscom_movieplayer_drawtext CVE-2010-0356
exploit/windows/browser/vlc_amv CVE-2010-3275
exploit/windows/browser/vlc_mms_bof CVE-2012-1775
exploit/windows/browser/webex_ucf_newobject CVE-2008-3558
exploit/windows/browser/wellintech_kingscada_kxclientdownload CVE-2013-2827
exploit/windows/browser/winamp_playlist_unc CVE-2006-0476
exploit/windows/browser/winamp_ultravox CVE-2008-0065
exploit/windows/browser/windvd7_applicationtype CVE-2007-0348
exploit/windows/browser/winzip_fileview CVE-2006-5198
exploit/windows/browser/wmi_admintools CVE-2010-3973
exploit/windows/browser/xmplay_asx CVE-2006-6063
exploit/windows/browser/yahoomessenger_fvcom CVE-2007-4515
exploit/windows/browser/yahoomessenger_server CVE-2007-3147
exploit/windows/browser/zenturiprogramchecker_unsafe CVE-2007-2987
exploit/windows/browser/zenworks_helplauncher_exec CVE-2011-2657
exploit/windows/dcerpc/ms03_026_dcom CVE-2003-0352
exploit/windows/dcerpc/ms05_017_msmq CVE-2005-0059
exploit/windows/dcerpc/ms07_029_msdns_zonename CVE-2007-1748
exploit/windows/dcerpc/ms07_065_msmq CVE-2007-3039
exploit/windows/email/ms07_017_ani_loadimage_chunksize CVE-2007-0038
exploit/windows/email/ms07_017_ani_loadimage_chunksize CVE-2007-1765
exploit/windows/email/ms10_045_outlook_ref_only CVE-2010-0266
exploit/windows/email/ms10_045_outlook_ref_resolve CVE-2010-0266
exploit/windows/emc/alphastor_agent CVE-2008-2158
exploit/windows/emc/alphastor_device_manager_exec CVE-2013-0928
exploit/windows/emc/networker_format_string CVE-2012-2288
exploit/windows/emc/replication_manager_exec CVE-2011-0647
exploit/windows/fileformat/acdsee_fotoslate_string CVE-2011-2595
exploit/windows/fileformat/acdsee_xpm CVE-2007-2193
exploit/windows/fileformat/adobe_collectemailinfo CVE-2007-5659
exploit/windows/fileformat/adobe_cooltype_sing CVE-2010-2883
exploit/windows/fileformat/adobe_flashplayer_button CVE-2010-3654
exploit/windows/fileformat/adobe_flashplayer_newfunction CVE-2010-1297
exploit/windows/fileformat/adobe_flatedecode_predictor02 CVE-2009-3459
exploit/windows/fileformat/adobe_geticon CVE-2009-0927
exploit/windows/fileformat/adobe_illustrator_v14_eps CVE-2009-4195
exploit/windows/fileformat/adobe_jbig2decode CVE-2009-0658
exploit/windows/fileformat/adobe_libtiff CVE-2010-0188
exploit/windows/fileformat/adobe_media_newplayer CVE-2009-4324
exploit/windows/fileformat/adobe_pdf_embedded_exe CVE-2010-1240
exploit/windows/fileformat/adobe_pdf_embedded_exe_nojs CVE-2010-1240
exploit/windows/fileformat/adobe_reader_u3d CVE-2011-2462
exploit/windows/fileformat/adobe_toolbutton CVE-2013-3346
exploit/windows/fileformat/adobe_u3d_meshdecl CVE-2009-3953
exploit/windows/fileformat/adobe_utilprintf CVE-2008-2992
exploit/windows/fileformat/allplayer_m3u_bof CVE-2013-7409
exploit/windows/fileformat/altap_salamander_pdb CVE-2007-3314
exploit/windows/fileformat/apple_quicktime_pnsize CVE-2011-0257
exploit/windows/fileformat/apple_quicktime_rdrf CVE-2013-1017
exploit/windows/fileformat/apple_quicktime_texml CVE-2012-0663
exploit/windows/fileformat/audio_coder_m3u CVE-2017-8870
exploit/windows/fileformat/audio_wkstn_pls CVE-2009-0476
exploit/windows/fileformat/audiotran_pls CVE-2009-0476
exploit/windows/fileformat/bacnet_csv CVE-2010-4740
exploit/windows/fileformat/blazedvd_plf CVE-2006-6199
exploit/windows/fileformat/boxoft_wav_to_mp3 CVE-2015-7243
exploit/windows/fileformat/bpftp_client_bps_bof CVE-2014-2973
exploit/windows/fileformat/ca_cab CVE-2007-2864
exploit/windows/fileformat/cain_abel_4918_rdp CVE-2008-5405
exploit/windows/fileformat/ccmplayer_m3u_bof CVE-2011-5170
exploit/windows/fileformat/chasys_draw_ies_bmp_bof CVE-2013-3928
exploit/windows/fileformat/coolpdf_image_stream_bof CVE-2012-4914
exploit/windows/fileformat/corelpdf_fusion_bof CVE-2013-3248
exploit/windows/fileformat/csound_getnum_bof CVE-2012-0270
exploit/windows/fileformat/cve_2017_8464_lnk_rce CVE-2017-8464
exploit/windows/fileformat/cyberlink_lpp_bof CVE-2017-14627
exploit/windows/fileformat/cyberlink_p2g_bof CVE-2011-5171
exploit/windows/fileformat/deepburner_path CVE-2006-6665
exploit/windows/fileformat/destinymediaplayer16 CVE-2009-3429
exploit/windows/fileformat/djstudio_pls_bof CVE-2009-4656
exploit/windows/fileformat/djvu_imageurl CVE-2008-4922
exploit/windows/fileformat/dupscout_xml CVE-2017-7310
exploit/windows/fileformat/dvdx_plf_bof CVE-2007-3068
exploit/windows/fileformat/easycdda_pls_bof CVE-2010-2343
exploit/windows/fileformat/emc_appextender_keyworks CVE-2012-2515
exploit/windows/fileformat/erdas_er_viewer_bof CVE-2013-0726
exploit/windows/fileformat/erdas_er_viewer_rf_report_error CVE-2013-3482
exploit/windows/fileformat/esignal_styletemplate_bof CVE-2011-3494
exploit/windows/fileformat/etrust_pestscan CVE-2009-4225
exploit/windows/fileformat/ezip_wizard_bof CVE-2009-1028
exploit/windows/fileformat/fatplayer_wav CVE-2009-4962
exploit/windows/fileformat/fdm_torrent CVE-2009-0184
exploit/windows/fileformat/feeddemon_opml CVE-2009-0546
exploit/windows/fileformat/foxit_reader_launch CVE-2009-0837
exploit/windows/fileformat/foxit_reader_uaf CVE-2018-9948
exploit/windows/fileformat/foxit_reader_uaf CVE-2018-9958
exploit/windows/fileformat/free_mp3_ripper_wav CVE-2011-5165
exploit/windows/fileformat/gsm_sim CVE-2015-1171
exploit/windows/fileformat/hhw_hhp_compiledfile_bof CVE-2006-0564
exploit/windows/fileformat/hhw_hhp_contentfile_bof CVE-2006-0564
exploit/windows/fileformat/hhw_hhp_indexfile_bof CVE-2009-0133
exploit/windows/fileformat/ht_mp3player_ht3_bof CVE-2009-2485
exploit/windows/fileformat/ibm_forms_viewer_fontname CVE-2013-5447
exploit/windows/fileformat/ibm_pcm_ws CVE-2012-0201
exploit/windows/fileformat/icofx_bof CVE-2013-4988
exploit/windows/fileformat/ideal_migration_ipj CVE-2009-4265
exploit/windows/fileformat/irfanview_jpeg2000_bof CVE-2012-0897
exploit/windows/fileformat/kingview_kingmess_kvl CVE-2012-4711
exploit/windows/fileformat/lattice_pac_bof CVE-2012-2915
exploit/windows/fileformat/lotusnotes_lzh CVE-2011-1213
exploit/windows/fileformat/mediacoder_m3u CVE-2017-8869
exploit/windows/fileformat/mediajukebox CVE-2009-2650
exploit/windows/fileformat/microp_mppl CVE-2010-5299
exploit/windows/fileformat/mini_stream_pls_bof CVE-2010-5081
exploit/windows/fileformat/moxa_mediadbplayback CVE-2010-4742
exploit/windows/fileformat/ms09_067_excel_featheader CVE-2009-3129
exploit/windows/fileformat/ms10_004_textbytesatom CVE-2010-0033
exploit/windows/fileformat/ms10_038_excel_obj_bof CVE-2010-0822
exploit/windows/fileformat/ms10_087_rtf_pfragments_bof CVE-2010-3333
exploit/windows/fileformat/ms11_006_createsizeddibsection CVE-2010-3970
exploit/windows/fileformat/ms11_021_xlb_bof CVE-2011-0105
exploit/windows/fileformat/ms12_005 CVE-2012-0013
exploit/windows/fileformat/ms12_027_mscomctl_bof CVE-2012-0158
exploit/windows/fileformat/ms13_071_theme CVE-2013-0810
exploit/windows/fileformat/ms14_017_rtf CVE-2014-1761
exploit/windows/fileformat/ms14_060_sandworm CVE-2014-4114
exploit/windows/fileformat/ms14_064_packager_python CVE-2014-6352
exploit/windows/fileformat/ms14_064_packager_run_as_admin CVE-2014-6352
exploit/windows/fileformat/ms15_020_shortcut_icon_dllloader CVE-2015-0096
exploit/windows/fileformat/ms15_100_mcl_exe CVE-2015-2509
exploit/windows/fileformat/ms_visual_basic_vbp CVE-2007-4776
exploit/windows/fileformat/mswin_tiff_overflow CVE-2013-3906
exploit/windows/fileformat/msworks_wkspictureinterface CVE-2008-1898
exploit/windows/fileformat/nitro_reader_jsapi CVE-2017-7442
exploit/windows/fileformat/office_ms17_11882 CVE-2017-11882
exploit/windows/fileformat/office_ole_multiple_dll_hijack CVE-2015-6132
exploit/windows/fileformat/office_ole_multiple_dll_hijack CVE-2015-6128
exploit/windows/fileformat/office_ole_multiple_dll_hijack CVE-2015-6133
exploit/windows/fileformat/office_ole_multiple_dll_hijack CVE-2016-0041
exploit/windows/fileformat/office_ole_multiple_dll_hijack CVE-2016-0100
exploit/windows/fileformat/office_ole_multiple_dll_hijack CVE-2016-3235
exploit/windows/fileformat/office_word_hta CVE-2017-0199
exploit/windows/fileformat/openoffice_ole CVE-2008-0320
exploit/windows/fileformat/orbit_download_failed_bof CVE-2008-1602
exploit/windows/fileformat/orbital_viewer_orb CVE-2010-0688
exploit/windows/fileformat/ovf_format_string CVE-2012-3569
exploit/windows/fileformat/proshow_cellimage_bof CVE-2009-3214
exploit/windows/fileformat/publishit_pui CVE-2014-0980
exploit/windows/fileformat/real_player_url_property_bof CVE-2012-5691
exploit/windows/fileformat/realplayer_ver_attribute_bof CVE-2013-7260
exploit/windows/fileformat/safenet_softremote_groupname CVE-2009-3861
exploit/windows/fileformat/sascam_get CVE-2008-6898
exploit/windows/fileformat/scadaphone_zip CVE-2011-4535
exploit/windows/fileformat/shadow_stream_recorder_bof CVE-2009-1641
exploit/windows/fileformat/syncbreeze_xml CVE-2017-7310
exploit/windows/fileformat/tfm_mmplayer_m3u_ppl_bof CVE-2009-2566
exploit/windows/fileformat/tugzip CVE-2008-4779
exploit/windows/fileformat/ultraiso_ccd CVE-2009-1260
exploit/windows/fileformat/ultraiso_cue CVE-2007-2888
exploit/windows/fileformat/ursoft_w32dasm CVE-2005-0308
exploit/windows/fileformat/videolan_tivo CVE-2008-4654
exploit/windows/fileformat/videospirit_visprj CVE-2011-0499
exploit/windows/fileformat/videospirit_visprj CVE-2011-0500
exploit/windows/fileformat/visio_dxf_bof CVE-2010-1681
exploit/windows/fileformat/visiwave_vwr_type CVE-2011-2386
exploit/windows/fileformat/vlc_mkv CVE-2018-11529
exploit/windows/fileformat/vlc_modplug_s3m CVE-2011-1574
exploit/windows/fileformat/vlc_realtext CVE-2008-5036
exploit/windows/fileformat/vlc_smb_uri CVE-2009-2484
exploit/windows/fileformat/vlc_webm CVE-2011-0531
exploit/windows/fileformat/vuplayer_m3u CVE-2006-6251
exploit/windows/fileformat/watermark_master CVE-2013-6935
exploit/windows/fileformat/winamp_maki_bof CVE-2009-1831
exploit/windows/fileformat/winrar_ace CVE-2018-20250
exploit/windows/fileformat/wireshark_mpeg_overflow CVE-2014-2299
exploit/windows/fileformat/wireshark_packet_dect CVE-2011-1591
exploit/windows/fileformat/xradio_xrl_sehbof CVE-2008-2789
exploit/windows/fileformat/zahir_enterprise_plus_csv CVE-2018-17408
exploit/windows/fileformat/zinfaudioplayer221_pls CVE-2004-0964
exploit/windows/firewall/blackice_pam_icq CVE-2004-0362
exploit/windows/firewall/kerio_auth CVE-2003-0220
exploit/windows/ftp/3cdaemon_ftp_user CVE-2005-0277
exploit/windows/ftp/ability_server_stor CVE-2004-1626
exploit/windows/ftp/absolute_ftp_list_bof CVE-2011-5164
exploit/windows/ftp/ayukov_nftp CVE-2017-15222
exploit/windows/ftp/bison_ftp_bof CVE-1999-1510
exploit/windows/ftp/cesarftp_mkd CVE-2006-2961
exploit/windows/ftp/dreamftp_format CVE-2004-2074
exploit/windows/ftp/easyfilesharing_pass CVE-2006-3952
exploit/windows/ftp/filecopa_list_overflow CVE-2006-3726
exploit/windows/ftp/freeftpd_user CVE-2005-3683
exploit/windows/ftp/ftpshell_cli_bof CVE-2018-7573
exploit/windows/ftp/globalscapeftp_input CVE-2005-1415
exploit/windows/ftp/goldenftp_pass_bof CVE-2006-6576
exploit/windows/ftp/httpdx_tolog_format CVE-2009-4769
exploit/windows/ftp/kmftp_utility_cwd CVE-2015-7768
exploit/windows/ftp/labf_nfsaxe CVE-2017-18047
exploit/windows/ftp/leapftp_pasv_reply CVE-2003-0558
exploit/windows/ftp/ms09_053_ftpd_nlst CVE-2009-3023
exploit/windows/ftp/netterm_netftpd_user CVE-2005-1323
exploit/windows/ftp/open_ftpd_wbem CVE-2010-2620
exploit/windows/ftp/oracle9i_xdb_ftp_pass CVE-2003-0727
exploit/windows/ftp/oracle9i_xdb_ftp_unlock CVE-2003-0727
exploit/windows/ftp/pcman_put CVE-2013-4730
exploit/windows/ftp/pcman_stor CVE-2013-4730
exploit/windows/ftp/proftp_banner CVE-2009-3976
exploit/windows/ftp/ricoh_dl_bof CVE-2012-5002
exploit/windows/ftp/sami_ftpd_user CVE-2006-0441
exploit/windows/ftp/sami_ftpd_user CVE-2006-2212
exploit/windows/ftp/scriptftp_list CVE-2011-3976
exploit/windows/ftp/servu_chmod CVE-2004-2111
exploit/windows/ftp/servu_mdtm CVE-2004-0330
exploit/windows/ftp/slimftpd_list_concat CVE-2005-2373
exploit/windows/ftp/trellian_client_pasv CVE-2010-1465
exploit/windows/ftp/warftpd_165_pass CVE-1999-0256
exploit/windows/ftp/warftpd_165_user CVE-1999-0256
exploit/windows/ftp/wftpd_size CVE-2006-4318
exploit/windows/ftp/wsftp_server_503_mkd CVE-2004-1135
exploit/windows/ftp/wsftp_server_505_xmd5 CVE-2006-4847
exploit/windows/ftp/xlink_client CVE-2006-5792
exploit/windows/ftp/xlink_server CVE-2006-5792
exploit/windows/games/mohaa_getinfo CVE-2004-0735
exploit/windows/games/racer_503beta5 CVE-2007-4370
exploit/windows/games/ut2004_secure CVE-2004-0608
exploit/windows/http/adobe_robohelper_authbypass CVE-2009-3068
exploit/windows/http/altn_securitygateway CVE-2008-4193
exploit/windows/http/altn_webadmin CVE-2003-0471
exploit/windows/http/apache_activemq_traversal_upload CVE-2015-1830
exploit/windows/http/apache_chunked CVE-2002-0392
exploit/windows/http/apache_mod_rewrite_ldap CVE-2006-3747
exploit/windows/http/apache_modjk_overflow CVE-2007-0774
exploit/windows/http/apache_tika_jp2_jscript CVE-2018-1335
exploit/windows/http/avaya_ccr_imageupload_exec CVE-2012-3811
exploit/windows/http/badblue_ext_overflow CVE-2005-0595
exploit/windows/http/badblue_passthru CVE-2007-6377
exploit/windows/http/bea_weblogic_jsessionid CVE-2008-5457
exploit/windows/http/bea_weblogic_post_bof CVE-2008-3257
exploit/windows/http/bea_weblogic_transfer_encoding CVE-2008-4008
exploit/windows/http/ca_arcserve_rpc_authbypass CVE-2011-3011
exploit/windows/http/ca_igateway_debug CVE-2005-3190
exploit/windows/http/ca_totaldefense_regeneratereports CVE-2011-1653
exploit/windows/http/cogent_datahub_command CVE-2014-3789
exploit/windows/http/cogent_datahub_request_headers_bof CVE-2013-0680
exploit/windows/http/coldfusion_fckeditor CVE-2009-2265
exploit/windows/http/desktopcentral_deserialization CVE-2020-10189
exploit/windows/http/desktopcentral_file_upload CVE-2013-7390
exploit/windows/http/desktopcentral_statusupdate_upload CVE-2014-5005
exploit/windows/http/disksavvy_get_bof CVE-2017-6187
exploit/windows/http/disksorter_bof CVE-2017-7230
exploit/windows/http/dnn_cookie_deserialization_rce CVE-2017-9822
exploit/windows/http/dnn_cookie_deserialization_rce CVE-2018-15811
exploit/windows/http/dnn_cookie_deserialization_rce CVE-2018-15812
exploit/windows/http/dnn_cookie_deserialization_rce CVE-2018-18325
exploit/windows/http/dnn_cookie_deserialization_rce CVE-2018-18326
exploit/windows/http/dup_scout_enterprise_login_bof CVE-2017-13696
exploit/windows/http/edirectory_host CVE-2006-5478
exploit/windows/http/edirectory_imonitor CVE-2005-2551
exploit/windows/http/efs_easychatserver_username CVE-2004-2466
exploit/windows/http/efs_fmws_userid_bof CVE-2014-3791
exploit/windows/http/ektron_xslt_exec CVE-2012-5357
exploit/windows/http/ektron_xslt_exec_ws CVE-2015-0923
exploit/windows/http/ericom_access_now_bof CVE-2014-3913
exploit/windows/http/exchange_ecp_viewstate CVE-2020-0688
exploit/windows/http/fdm_auth_header CVE-2009-0183
exploit/windows/http/file_sharing_wizard_seh CVE-2019-16724
exploit/windows/http/geutebrueck_gcore_x64_rce_bo CVE-2017-11517
exploit/windows/http/gitstack_rce CVE-2018-5955
exploit/windows/http/hp_autopass_license_traversal CVE-2013-6221
exploit/windows/http/hp_imc_bims_upload CVE-2013-4822
exploit/windows/http/hp_imc_java_deserialize CVE-2017-12557
exploit/windows/http/hp_imc_mibfileupload CVE-2012-5201
exploit/windows/http/hp_loadrunner_copyfiletoserver CVE-2013-4837
exploit/windows/http/hp_mpa_job_acct CVE-2011-4166
exploit/windows/http/hp_nnm_getnnmdata_hostname CVE-2010-1555
exploit/windows/http/hp_nnm_getnnmdata_icount CVE-2010-1554
exploit/windows/http/hp_nnm_getnnmdata_maxage CVE-2010-1553
exploit/windows/http/hp_nnm_nnmrptconfig_nameparams CVE-2011-0266
exploit/windows/http/hp_nnm_nnmrptconfig_schdparams CVE-2011-0267
exploit/windows/http/hp_nnm_openview5 CVE-2007-6204
exploit/windows/http/hp_nnm_ovalarm_lang CVE-2009-4179
exploit/windows/http/hp_nnm_ovas CVE-2008-1697
exploit/windows/http/hp_nnm_ovbuildpath_textfile CVE-2011-3167
exploit/windows/http/hp_nnm_ovwebhelp CVE-2009-4178
exploit/windows/http/hp_nnm_ovwebsnmpsrv_main CVE-2010-1964
exploit/windows/http/hp_nnm_ovwebsnmpsrv_ovutil CVE-2010-1961
exploit/windows/http/hp_nnm_ovwebsnmpsrv_uro CVE-2010-1960
exploit/windows/http/hp_nnm_snmp CVE-2009-3849
exploit/windows/http/hp_nnm_snmpviewer_actapp CVE-2010-1552
exploit/windows/http/hp_nnm_toolbar_01 CVE-2008-0067
exploit/windows/http/hp_nnm_toolbar_02 CVE-2009-0920
exploit/windows/http/hp_nnm_webappmon_execvp CVE-2010-2703
exploit/windows/http/hp_nnm_webappmon_ovjavalocale CVE-2010-2709
exploit/windows/http/hp_openview_insight_backdoor CVE-2011-0276
exploit/windows/http/hp_pcm_snac_update_certificates CVE-2013-4812
exploit/windows/http/hp_pcm_snac_update_domain CVE-2013-4811
exploit/windows/http/hp_power_manager_filename CVE-2009-3999
exploit/windows/http/hp_power_manager_login CVE-2009-2685
exploit/windows/http/hp_sitescope_runomagentcommand CVE-2013-2367
exploit/windows/http/httpdx_handlepeer CVE-2009-3711
exploit/windows/http/httpdx_tolog_format CVE-2009-4769
exploit/windows/http/ia_webmail CVE-2003-1192
exploit/windows/http/ibm_tivoli_endpoint_bof CVE-2011-1220
exploit/windows/http/ibm_tpmfosd_overflow CVE-2007-1868
exploit/windows/http/ibm_tsm_cad_header CVE-2007-4880
exploit/windows/http/icecast_header CVE-2004-1561
exploit/windows/http/ipswitch_wug_maincfgret CVE-2004-0798
exploit/windows/http/jira_collector_traversal CVE-2014-2314
exploit/windows/http/kaseya_uploader CVE-2015-6922
exploit/windows/http/kolibri_http CVE-2002-2268
exploit/windows/http/landesk_thinkmanagement_upload_asp CVE-2012-1195
exploit/windows/http/landesk_thinkmanagement_upload_asp CVE-2012-1196
exploit/windows/http/lexmark_markvision_gfd_upload CVE-2014-8741
exploit/windows/http/mailenable_auth_header CVE-2005-1348
exploit/windows/http/manage_engine_opmanager_rce CVE-2015-7765
exploit/windows/http/manage_engine_opmanager_rce CVE-2015-7766
exploit/windows/http/manageengine_appmanager_exec CVE-2018-7890
exploit/windows/http/manageengine_connectionid_write CVE-2015-8249
exploit/windows/http/maxdb_webdbm_database CVE-2006-4305
exploit/windows/http/maxdb_webdbm_get_overflow CVE-2005-0684
exploit/windows/http/mcafee_epolicy_source CVE-2006-5156
exploit/windows/http/mdaemon_worldclient_form2raw CVE-2003-1200
exploit/windows/http/minishare_get_overflow CVE-2004-2271
exploit/windows/http/navicopa_get_overflow CVE-2006-5112
exploit/windows/http/netdecision_http_bof CVE-2012-1465
exploit/windows/http/netgear_nms_rce CVE-2016-1525
exploit/windows/http/novell_mdm_lfi CVE-2013-1081
exploit/windows/http/novell_messenger_acceptlang CVE-2006-0992
exploit/windows/http/nowsms CVE-2008-0871
exploit/windows/http/oracle9i_xdb_pass CVE-2003-0727
exploit/windows/http/oracle_beehive_evaluation CVE-2010-4417
exploit/windows/http/oracle_endeca_exec CVE-2013-3763
exploit/windows/http/oracle_event_processing_upload CVE-2014-2424
exploit/windows/http/osb_uname_jlist CVE-2010-0904
exploit/windows/http/peercast_url CVE-2006-1148
exploit/windows/http/php_apache_request_headers_bof CVE-2012-2329
exploit/windows/http/privatewire_gateway CVE-2006-3252
exploit/windows/http/psoproxy91_overflow CVE-2004-0313
exploit/windows/http/rejetto_hfs_exec CVE-2014-6287
exploit/windows/http/sambar6_search_results CVE-2004-2086
exploit/windows/http/sapdb_webtools CVE-2007-3614
exploit/windows/http/savant_31_overflow CVE-2002-1120
exploit/windows/http/sepm_auth_bypass_rce CVE-2015-1486
exploit/windows/http/sepm_auth_bypass_rce CVE-2015-1487
exploit/windows/http/sepm_auth_bypass_rce CVE-2015-1489
exploit/windows/http/servu_session_cookie CVE-2009-4006
exploit/windows/http/sharepoint_workflows_xoml CVE-2020-0646
exploit/windows/http/shoutcast_format CVE-2004-1373
exploit/windows/http/shttpd_post CVE-2006-5216
exploit/windows/http/solarwinds_fsm_userlogin CVE-2015-2284
exploit/windows/http/sonicwall_scrutinizer_sqli CVE-2012-2962
exploit/windows/http/ssrs_navcorrector_viewstate CVE-2020-0618
exploit/windows/http/steamcast_useragent CVE-2008-0550
exploit/windows/http/sybase_easerver CVE-2005-2297
exploit/windows/http/syncbreeze_bof CVE-2017-14980
exploit/windows/http/sysax_create_folder CVE-2012-6530
exploit/windows/http/tomcat_cgi_cmdlineargs CVE-2019-0232
exploit/windows/http/trackercam_phparg_overflow CVE-2005-0478
exploit/windows/http/trackit_file_upload CVE-2014-4872
exploit/windows/http/trendmicro_officescan CVE-2008-1365
exploit/windows/http/trendmicro_officescan_widget_exec CVE-2017-11394
exploit/windows/http/ultraminihttp_bof CVE-2013-5019
exploit/windows/http/vmware_vcenter_chargeback_upload CVE-2013-3520
exploit/windows/http/webster_http CVE-2002-2268
exploit/windows/http/xitami_if_mod_since CVE-2007-5067
exploit/windows/http/zenworks_assetmgmt_uploadservlet CVE-2011-2653
exploit/windows/http/zenworks_uploadservlet CVE-2010-5324
exploit/windows/ibm/ibm_was_dmgr_java_deserialization_rce CVE-2019-4279
exploit/windows/iis/iis_webdav_scstoragepathfromurl CVE-2017-7269
exploit/windows/iis/ms01_023_printer CVE-2001-0241
exploit/windows/iis/ms01_026_dbldecode CVE-2001-0333
exploit/windows/iis/ms01_033_idq CVE-2001-0500
exploit/windows/iis/ms02_018_htr CVE-1999-0874
exploit/windows/iis/ms02_065_msadc CVE-2002-1142
exploit/windows/iis/ms03_007_ntdll_webdav CVE-2003-0109
exploit/windows/iis/msadc CVE-1999-1011
exploit/windows/imap/eudora_list CVE-2005-4267
exploit/windows/imap/imail_delete CVE-2004-1520
exploit/windows/imap/ipswitch_search CVE-2007-3925
exploit/windows/imap/mailenable_login CVE-2006-6423
exploit/windows/imap/mailenable_status CVE-2005-2278
exploit/windows/imap/mailenable_w3c_select CVE-2005-3155
exploit/windows/imap/mdaemon_cram_md5 CVE-2004-1520
exploit/windows/imap/mdaemon_fetch CVE-2008-1358
exploit/windows/imap/mercur_imap_select_overflow CVE-2006-1255
exploit/windows/imap/mercur_login CVE-2006-1255
exploit/windows/imap/mercury_login CVE-2007-1373
exploit/windows/imap/mercury_rename CVE-2004-1211
exploit/windows/imap/novell_netmail_append CVE-2006-6425
exploit/windows/imap/novell_netmail_status CVE-2005-3314
exploit/windows/imap/novell_netmail_subscribe CVE-2006-6761
exploit/windows/isapi/ms00_094_pbserver CVE-2000-1089
exploit/windows/isapi/ms03_022_nsiislog_post CVE-2003-0349
exploit/windows/isapi/ms03_051_fp30reg_chunked CVE-2003-0822
exploit/windows/isapi/rsa_webagent_redirect CVE-2005-4734
exploit/windows/isapi/w3who_query CVE-2004-1134
exploit/windows/ldap/imail_thc CVE-2004-0297
exploit/windows/ldap/pgp_keyserver7 CVE-2001-1320
exploit/windows/license/calicclnt_getconfig CVE-2005-0581
exploit/windows/license/calicserv_getconfig CVE-2005-0581
exploit/windows/license/sentinel_lm7_udp CVE-2005-0353
exploit/windows/local/adobe_sandbox_adobecollabsync CVE-2013-2730
exploit/windows/local/alpc_taskscheduler CVE-2018-8440
exploit/windows/local/appxsvc_hard_link_privesc CVE-2019-0841
exploit/windows/local/bthpan CVE-2014-4971
exploit/windows/local/comahawk CVE-2019-1322
exploit/windows/local/comahawk CVE-2019-1405
exploit/windows/local/current_user_psexec CVE-1999-0504
exploit/windows/local/cve_2017_8464_lnk_lpe CVE-2017-8464
exploit/windows/local/cve_2018_8453_win32k_priv_esc CVE-2018-8453
exploit/windows/local/cve_2020_0796_smbghost CVE-2020-0796
exploit/windows/local/ipass_launch_app CVE-2015-0925
exploit/windows/local/lenovo_systemupdate CVE-2015-2219
exploit/windows/local/mov_ss CVE-2018-8897
exploit/windows/local/mqac_write CVE-2014-4971
exploit/windows/local/ms10_015_kitrap0d CVE-2010-0232
exploit/windows/local/ms10_092_schelevator CVE-2010-3338
exploit/windows/local/ms11_080_afdjoinleaf CVE-2011-2005
exploit/windows/local/ms13_005_hwnd_broadcast CVE-2013-0008
exploit/windows/local/ms13_053_schlamperei CVE-2013-1300
exploit/windows/local/ms13_081_track_popup_menu CVE-2013-3881
exploit/windows/local/ms13_097_ie_registry_symlink CVE-2013-5045
exploit/windows/local/ms14_009_ie_dfsvc CVE-2014-0257
exploit/windows/local/ms14_058_track_popup_menu CVE-2014-4113
exploit/windows/local/ms14_070_tcpip_ioctl CVE-2014-4076
exploit/windows/local/ms15_004_tswbproxy CVE-2015-0016
exploit/windows/local/ms15_051_client_copy_image CVE-2015-1701
exploit/windows/local/ms15_078_atmfd_bof CVE-2015-2426
exploit/windows/local/ms15_078_atmfd_bof CVE-2015-2433
exploit/windows/local/ms16_014_wmi_recv_notif CVE-2016-0040
exploit/windows/local/ms16_016_webdav CVE-2016-0051
exploit/windows/local/ms16_032_secondary_logon_handle_privesc CVE-2016-0099
exploit/windows/local/ms16_075_reflection CVE-2016-3225
exploit/windows/local/ms16_075_reflection_juicy CVE-2016-3225
exploit/windows/local/ms18_8120_win32k_privesc CVE-2018-8120
exploit/windows/local/ms_ndproxy CVE-2013-5065
exploit/windows/local/novell_client_nicm CVE-2013-3956
exploit/windows/local/novell_client_nwfs CVE-2008-3158
exploit/windows/local/ntapphelpcachecontrol CVE-2015-0002
exploit/windows/local/nvidia_nvsvc CVE-2013-0109
exploit/windows/local/plantronics_hub_spokesupdateservice_privesc CVE-2019-15742
exploit/windows/local/powershell_remoting CVE-1999-0504
exploit/windows/local/ppr_flatten_rec CVE-2013-3660
exploit/windows/local/razer_zwopenprocess CVE-2017-9769
exploit/windows/local/ricoh_driver_privesc CVE-2019-19363
exploit/windows/local/virtual_box_guest_additions CVE-2014-2477
exploit/windows/local/virtual_box_opengl_escape CVE-2014-0983
exploit/windows/local/webexec CVE-2018-15442
exploit/windows/local/windscribe_windscribeservice_priv_esc CVE-2018-11479
exploit/windows/local/wmi CVE-1999-0504
exploit/windows/lotus/domino_http_accept_language CVE-2008-2240
exploit/windows/lotus/domino_icalendar_organizer CVE-2010-3407
exploit/windows/lotus/domino_sametime_stmux CVE-2008-2499
exploit/windows/lotus/lotusnotes_lzh CVE-2011-1213
exploit/windows/lpd/hummingbird_exceed CVE-2005-1815
exploit/windows/lpd/niprint CVE-2003-1141
exploit/windows/lpd/saplpd CVE-2008-0621
exploit/windows/lpd/wincomlpd_admin CVE-2008-5159
exploit/windows/misc/agentxpp_receive_agentx CVE-2010-1318
exploit/windows/misc/ahsay_backup_fileupload CVE-2019-10267
exploit/windows/misc/ais_esel_server_rce CVE-2019-10123
exploit/windows/misc/allmediaserver_bof CVE-2017-17932
exploit/windows/misc/altiris_ds_sqli CVE-2008-2286
exploit/windows/misc/apple_quicktime_rtsp_response CVE-2007-6166
exploit/windows/misc/asus_dpcproxy_overflow CVE-2008-1491
exploit/windows/misc/avidphoneticindexer CVE-2011-5003
exploit/windows/misc/bakbone_netvault_heap CVE-2005-1009
exploit/windows/misc/bcaaa_bof CVE-2011-5124
exploit/windows/misc/bigant_server CVE-2008-1914
exploit/windows/misc/bigant_server_250 CVE-2008-1914
exploit/windows/misc/bigant_server_dupf_upload CVE-2012-6274
exploit/windows/misc/bigant_server_sch_dupf_bof CVE-2012-6275
exploit/windows/misc/bigant_server_usv CVE-2009-4660
exploit/windows/misc/bomberclone_overflow CVE-2006-0460
exploit/windows/misc/bopup_comm CVE-2009-2227
exploit/windows/misc/borland_interbase CVE-2007-3566
exploit/windows/misc/borland_starteam CVE-2008-0311
exploit/windows/misc/cloudme_sync CVE-2018-6892
exploit/windows/misc/commvault_cmd_exec CVE-2017-18044
exploit/windows/misc/crosschex_device_bof CVE-2019-12518
exploit/windows/misc/doubletake CVE-2008-1661
exploit/windows/misc/eiqnetworks_esa CVE-2006-3838
exploit/windows/misc/eiqnetworks_esa_topology CVE-2006-3838
exploit/windows/misc/enterasys_netsight_syslog_bof CVE-2011-5227
exploit/windows/misc/eureka_mail_err CVE-2009-3837
exploit/windows/misc/fb_cnct_group CVE-2013-2492
exploit/windows/misc/fb_isc_attach_database CVE-2007-5243
exploit/windows/misc/fb_isc_create_database CVE-2007-5243
exploit/windows/misc/fb_svc_attach CVE-2007-5243
exploit/windows/misc/gimp_script_fu CVE-2012-2763
exploit/windows/misc/hp_dataprotector_cmd_exec CVE-2014-2623
exploit/windows/misc/hp_dataprotector_crs CVE-2013-2333
exploit/windows/misc/hp_dataprotector_dtbclslogin CVE-2010-3007
exploit/windows/misc/hp_dataprotector_encrypted_comms CVE-2016-2004
exploit/windows/misc/hp_dataprotector_exec_bar CVE-2013-2347
exploit/windows/misc/hp_dataprotector_install_service CVE-2011-0922
exploit/windows/misc/hp_dataprotector_new_folder CVE-2012-0124
exploit/windows/misc/hp_dataprotector_traversal CVE-2013-6194
exploit/windows/misc/hp_imc_dbman_restartdb_unauth_rce CVE-2017-5816
exploit/windows/misc/hp_imc_dbman_restoredbase_unauth_rce CVE-2017-5817
exploit/windows/misc/hp_imc_uam CVE-2012-3274
exploit/windows/misc/hp_loadrunner_magentproc CVE-2013-4800
exploit/windows/misc/hp_loadrunner_magentproc_cmdexec CVE-2010-1549
exploit/windows/misc/hp_magentservice CVE-2011-4789
exploit/windows/misc/hp_omniinet_1 CVE-2007-2280
exploit/windows/misc/hp_omniinet_2 CVE-2009-3844
exploit/windows/misc/hp_omniinet_3 CVE-2011-1865
exploit/windows/misc/hp_omniinet_4 CVE-2011-1865
exploit/windows/misc/hp_operations_agent_coda_34 CVE-2012-2019
exploit/windows/misc/hp_operations_agent_coda_8c CVE-2012-2020
exploit/windows/misc/hp_ovtrace CVE-2007-3872
exploit/windows/misc/ib_isc_attach_database CVE-2007-5243
exploit/windows/misc/ib_isc_create_database CVE-2007-5243
exploit/windows/misc/ib_svc_attach CVE-2007-5243
exploit/windows/misc/ibm_cognos_tm1admsd_bof CVE-2012-0202
exploit/windows/misc/ibm_director_cim_dllinject CVE-2009-0880
exploit/windows/misc/ibm_tsm_cad_ping CVE-2009-3853
exploit/windows/misc/ibm_tsm_rca_dicugetidentify CVE-2008-4828
exploit/windows/misc/ibm_websphere_java_deserialize CVE-2015-7450
exploit/windows/misc/landesk_aolnsrvr CVE-2007-1674
exploit/windows/misc/lianja_db_net CVE-2013-3563
exploit/windows/misc/manageengine_eventlog_analyzer_rce CVE-2015-7387
exploit/windows/misc/mercury_phonebook CVE-2005-4411
exploit/windows/misc/mini_stream CVE-2009-5109
exploit/windows/misc/mirc_privmsg_server CVE-2008-4449
exploit/windows/misc/ms07_064_sami CVE-2007-3901
exploit/windows/misc/ms10_104_sharepoint CVE-2010-3964
exploit/windows/misc/netcat110_nt CVE-2004-1317
exploit/windows/misc/nettransport CVE-2017-17968
exploit/windows/misc/poppeeper_date CVE-2009-1029
exploit/windows/misc/poppeeper_uidl CVE-2009-1029
exploit/windows/misc/realtek_playlist CVE-2008-5664
exploit/windows/misc/sap_2005_license CVE-2009-4988
exploit/windows/misc/sap_netweaver_dispatcher CVE-2012-2611
exploit/windows/misc/shixxnote_font CVE-2004-1595
exploit/windows/misc/solidworks_workgroup_pdmwservice_file_write CVE-2014-100015
exploit/windows/misc/stream_down_bof CVE-2011-5052
exploit/windows/misc/tiny_identd_overflow CVE-2007-2711
exploit/windows/misc/trendmicro_cmdprocessor_addtask CVE-2011-5001
exploit/windows/misc/vmhgfs_webdav_dll_sideload CVE-2016-5330
exploit/windows/misc/windows_rsh CVE-2007-4006
exploit/windows/misc/wireshark_lua CVE-2011-3360
exploit/windows/misc/wireshark_packet_dect CVE-2011-1591
exploit/windows/mmsp/ms10_025_wmss_connect_funnel CVE-2010-0478
exploit/windows/motorola/timbuktu_fileupload CVE-2008-1117
exploit/windows/mssql/lyris_listmanager_weak_pass CVE-2005-4145
exploit/windows/mssql/ms02_039_slammer CVE-2002-0649
exploit/windows/mssql/ms02_056_hello CVE-2002-1123
exploit/windows/mssql/ms09_004_sp_replwritetovarbin CVE-2008-5416
exploit/windows/mssql/ms09_004_sp_replwritetovarbin_sqli CVE-2008-5416
exploit/windows/mssql/mssql_payload CVE-2000-0402
exploit/windows/mssql/mssql_payload CVE-2000-1209
exploit/windows/mssql/mssql_payload_sqli CVE-2000-0402
exploit/windows/mssql/mssql_payload_sqli CVE-2000-1209
exploit/windows/mysql/mysql_mof CVE-2012-5613
exploit/windows/mysql/mysql_start_up CVE-2012-5613
exploit/windows/mysql/mysql_yassl_hello CVE-2008-0226
exploit/windows/mysql/scrutinizer_upload_exec CVE-2012-3951
exploit/windows/nfs/xlink_nfsd CVE-2006-5780
exploit/windows/nntp/ms05_030_nntp CVE-2005-1213
exploit/windows/novell/file_reporter_fsfui_upload CVE-2012-4959
exploit/windows/novell/groupwisemessenger_client CVE-2008-2703
exploit/windows/novell/netiq_pum_eval CVE-2012-5932
exploit/windows/novell/nmap_stor CVE-2006-6424
exploit/windows/novell/zenworks_desktop_agent CVE-2005-1543
exploit/windows/novell/zenworks_preboot_op21_bof CVE-2012-2215
exploit/windows/novell/zenworks_preboot_op4c_bof CVE-2011-3176
exploit/windows/novell/zenworks_preboot_op6c_bof CVE-2011-3175
exploit/windows/nuuo/nuuo_cms_fu CVE-2018-17936
exploit/windows/nuuo/nuuo_cms_sqli CVE-2018-18982
exploit/windows/oracle/client_system_analyzer_upload CVE-2010-3600
exploit/windows/oracle/osb_ndmp_auth CVE-2008-5444
exploit/windows/oracle/tns_arguments CVE-2001-0499
exploit/windows/oracle/tns_auth_sesskey CVE-2009-1979
exploit/windows/oracle/tns_service_name CVE-2002-0965
exploit/windows/pop3/seattlelab_pass CVE-2003-0264
exploit/windows/proxy/bluecoat_winproxy_host CVE-2005-4085
exploit/windows/proxy/ccproxy_telnet_ping CVE-2004-2416
exploit/windows/proxy/proxypro_http_get CVE-2004-0326
exploit/windows/proxy/qbik_wingate_wwwproxy CVE-2006-2926
exploit/windows/rdp/cve_2019_0708_bluekeep_rce CVE-2019-0708
exploit/windows/scada/advantech_webaccess_dashboard_file_upload CVE-2016-0854
exploit/windows/scada/advantech_webaccess_webvrpcs_bof CVE-2017-14016
exploit/windows/scada/citect_scada_odbc CVE-2008-2639
exploit/windows/scada/codesys_gateway_server_traversal CVE-2012-4705
exploit/windows/scada/codesys_web_server CVE-2011-5007
exploit/windows/scada/daq_factory_bof CVE-2011-3492
exploit/windows/scada/delta_ia_commgr_bof CVE-2018-10594
exploit/windows/scada/ge_proficy_cimplicity_gefebt CVE-2014-0750
exploit/windows/scada/iconics_webhmi_setactivexguid CVE-2011-2089
exploit/windows/scada/igss9_igssdataserver_listall CVE-2011-1567
exploit/windows/scada/igss9_igssdataserver_rename CVE-2011-1567
exploit/windows/scada/igss9_misc CVE-2011-1565
exploit/windows/scada/igss9_misc CVE-2011-1566
exploit/windows/scada/igss_exec_17 CVE-2011-1566
exploit/windows/scada/indusoft_webstudio_exec CVE-2011-4051
exploit/windows/scada/moxa_mdmtool CVE-2010-4741
exploit/windows/scada/procyon_core_server CVE-2011-3322
exploit/windows/scada/realwin CVE-2008-4322
exploit/windows/scada/realwin_on_fc_binfile_a CVE-2011-1563
exploit/windows/scada/realwin_on_fcs_login CVE-2011-1563
exploit/windows/scada/realwin_scpc_initialize CVE-2010-4142
exploit/windows/scada/realwin_scpc_initialize_rf CVE-2010-4142
exploit/windows/scada/realwin_scpc_txtevent CVE-2010-4142
exploit/windows/scada/scadapro_cmdexe CVE-2011-3497
exploit/windows/scada/winlog_runtime CVE-2011-0517
exploit/windows/scada/winlog_runtime_2 CVE-2012-3815
exploit/windows/scada/yokogawa_bkbcopyd_bof CVE-2014-0784
exploit/windows/scada/yokogawa_bkesimmgr_bof CVE-2014-0782
exploit/windows/scada/yokogawa_bkfsim_vhfd CVE-2014-3888
exploit/windows/scada/yokogawa_bkhodeq_bof CVE-2014-0783
exploit/windows/sip/aim_triton_cseq CVE-2006-3524
exploit/windows/sip/sipxezphone_cseq CVE-2006-3524
exploit/windows/sip/sipxphone_cseq CVE-2006-3524
exploit/windows/smb/ipass_pipe_exec CVE-2015-0925
exploit/windows/smb/ms03_049_netapi CVE-2003-0812
exploit/windows/smb/ms04_007_killbill CVE-2003-0818
exploit/windows/smb/ms04_011_lsass CVE-2003-0533
exploit/windows/smb/ms04_031_netdde CVE-2004-0206
exploit/windows/smb/ms05_039_pnp CVE-2005-1983
exploit/windows/smb/ms06_025_rasmans_reg CVE-2006-2370
exploit/windows/smb/ms06_025_rras CVE-2006-2370
exploit/windows/smb/ms06_040_netapi CVE-2006-3439
exploit/windows/smb/ms06_066_nwapi CVE-2006-4688
exploit/windows/smb/ms06_066_nwwks CVE-2006-4688
exploit/windows/smb/ms06_070_wkssvc CVE-2006-4691
exploit/windows/smb/ms07_029_msdns_zonename CVE-2007-1748
exploit/windows/smb/ms08_067_netapi CVE-2008-4250
exploit/windows/smb/ms09_050_smb2_negotiate_func_index CVE-2009-3103
exploit/windows/smb/ms10_046_shortcut_icon_dllloader CVE-2010-2568
exploit/windows/smb/ms10_061_spoolss CVE-2010-2729
exploit/windows/smb/ms15_020_shortcut_icon_dllloader CVE-2015-0096
exploit/windows/smb/ms17_010_eternalblue CVE-2017-0143
exploit/windows/smb/ms17_010_eternalblue CVE-2017-0144
exploit/windows/smb/ms17_010_eternalblue CVE-2017-0145
exploit/windows/smb/ms17_010_eternalblue CVE-2017-0146
exploit/windows/smb/ms17_010_eternalblue CVE-2017-0147
exploit/windows/smb/ms17_010_eternalblue CVE-2017-0148
exploit/windows/smb/ms17_010_psexec CVE-2017-0143
exploit/windows/smb/ms17_010_psexec CVE-2017-0146
exploit/windows/smb/ms17_010_psexec CVE-2017-0147
exploit/windows/smb/netidentity_xtierrpcpipe CVE-2009-1350
exploit/windows/smb/psexec CVE-1999-0504
exploit/windows/smb/psexec_psh CVE-1999-0504
exploit/windows/smb/smb_doublepulsar_rce CVE-2017-0143
exploit/windows/smb/smb_doublepulsar_rce CVE-2017-0144
exploit/windows/smb/smb_doublepulsar_rce CVE-2017-0145
exploit/windows/smb/smb_doublepulsar_rce CVE-2017-0146
exploit/windows/smb/smb_doublepulsar_rce CVE-2017-0147
exploit/windows/smb/smb_doublepulsar_rce CVE-2017-0148
exploit/windows/smb/smb_relay CVE-2008-4037
exploit/windows/smb/timbuktu_plughntcommand_bof CVE-2009-1394
exploit/windows/smb/webexec CVE-2018-15442
exploit/windows/smtp/mailcarrier_smtp_ehlo CVE-2004-1638
exploit/windows/smtp/mercury_cram_md5 CVE-2007-4440
exploit/windows/smtp/ms03_046_exchange2000_xexch50 CVE-2003-0714
exploit/windows/smtp/njstar_smtp_bof CVE-2011-4040
exploit/windows/smtp/sysgauge_client_bof CVE-2017-6416
exploit/windows/smtp/wmailserver CVE-2005-2287
exploit/windows/smtp/ypops_overflow1 CVE-2004-1558
exploit/windows/ssh/freeftpd_key_exchange CVE-2006-2407
exploit/windows/ssh/freesshd_authbypass CVE-2012-6066
exploit/windows/ssh/freesshd_key_exchange CVE-2006-2407
exploit/windows/ssh/putty_msg_debug CVE-2002-1359
exploit/windows/ssh/securecrt_ssh1 CVE-2002-1059
exploit/windows/ssl/ms04_011_pct CVE-2003-0719
exploit/windows/telnet/gamsoft_telsrv_username CVE-2000-0665
exploit/windows/telnet/goodtech_telnet CVE-2005-0768
exploit/windows/tftp/attftp_long_filename CVE-2006-6184
exploit/windows/tftp/distinct_tftp_traversal CVE-2012-6664
exploit/windows/tftp/dlink_long_filename CVE-2007-1435
exploit/windows/tftp/futuresoft_transfermode CVE-2005-1812
exploit/windows/tftp/netdecision_tftp_traversal CVE-2009-1730
exploit/windows/tftp/opentftp_error_code CVE-2008-2161
exploit/windows/tftp/quick_tftp_pro_mode CVE-2008-1610
exploit/windows/tftp/tftpd32_long_filename CVE-2002-2226
exploit/windows/tftp/tftpdwin_long_filename CVE-2006-4948
exploit/windows/tftp/tftpserver_wrq_bof CVE-2008-1611
exploit/windows/tftp/threectftpsvc_long_mode CVE-2006-6183
exploit/windows/unicenter/cam_log_security CVE-2005-2668
exploit/windows/vnc/realvnc_client CVE-2001-0167
exploit/windows/vnc/ultravnc_client CVE-2006-1652
exploit/windows/vnc/ultravnc_viewer_bof CVE-2008-0610
exploit/windows/vnc/winvnc_http_get CVE-2001-0168
exploit/windows/vpn/safenet_ike_11 CVE-2009-1943
exploit/windows/wins/ms04_045_wins CVE-2004-1080
post/android/manage/remove_lock CVE-2013-6271
post/hardware/automotive/pdt CVE-2017-14937
post/linux/dos/xen_420_dos CVE-2012-5525
post/multi/escalate/cups_root_file_read CVE-2012-5519
post/solaris/escalate/srsexec_readline CVE-2007-2617
post/windows/escalate/ms10_073_kbdlayout CVE-2010-2743
post/windows/escalate/unmarshal_cmd_exec CVE-2018-0824
post/windows/gather/credentials/dynazip_log CVE-2001-0152
post/windows/gather/credentials/teamviewer_passwords CVE-2019-18988
post/windows/gather/forensics/duqu_check CVE-2011-3402

点分享

点收藏
点点赞
点在看
以上是关于Xerror 全自动渗透测试工具 漏洞扫描+报告生成的主要内容,如果未能解决你的问题,请参考以下文章