字节二面被问到CTF真题?我立马就是一套A接W接外圈刮震射全场!
Posted 李志宽
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了字节二面被问到CTF真题?我立马就是一套A接W接外圈刮震射全场!相关的知识,希望对你有一定的参考价值。

目录
MISC部分
BlueTeaming
列举缓存在内存的注册表
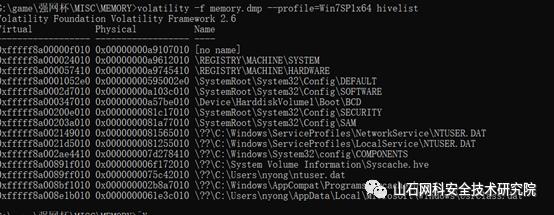
将所有注册表一一导出
volatility -f memory.dmp--profile=Win7SP1x64 dumpregistry 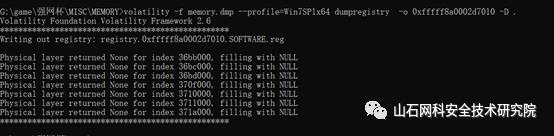
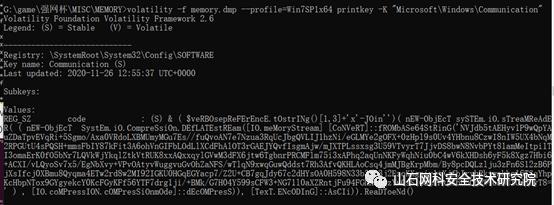
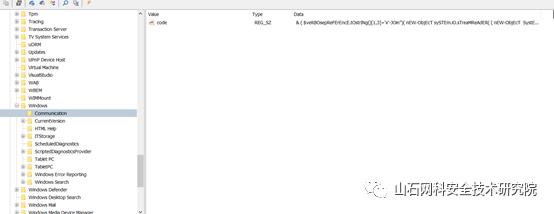
使用windows registry recovery查看注册表信息,手动找到路径。
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCommunication,此路径即为flag
ISO1995
用UItralSO将所有iso1995.iso的所有flag文件提取出来,并将这1024个文件里面的内容提取,得到一个1024的字符串
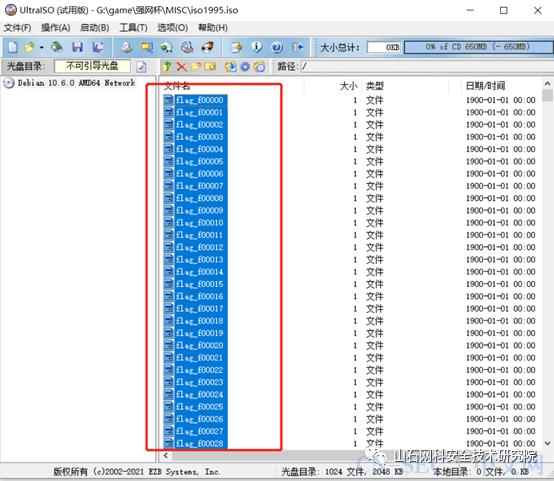
将iso 1995.iso里面所有的4个ff后面的2字节提取出来,转换为10字节,将数值对应flag文件数里的内容拿出来,组成一个字符串,里面就包含flag
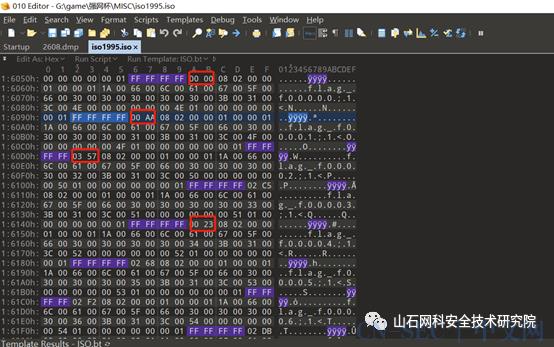
f = open("iso1995.iso",'rb+')
#输出读取到的数据
s=f.read()
s1=r'''!=gF~B.@YB01.%DYzb^-1}jH&@,K[7t/LOi*5b)L'<pW'amW4LH@toGKE1{"oDW0qf2{l{W_0V-m:af8AO4^iCT_+ $W3cz(LO)L_-s8'_<Ic/KFP9vrr~6ni{~#g5cs#7z2s++Y1BbYQV'iSl=DZ__|3T1QxWEwX}NJ@_3SdKK]91b?s-rS6gQwBs@4#5IGxW#&ArDw~_x"!_I^O`x5o'.s5)+c9RU'/%_b[rjiOP0y!&/)WjKR#IjWh0,Dr!@PH^Nf%,YoWEJ(2wXj/u~Y@gh%&_Gz5U`A=0pAV$E/ >1Kg:@4tS:V4ZB`1_x*.17B&:<xn0rW|2TY_DSN<zvbKCj7+6w'r}Lo8':fYC@FvJ02VbO)noQlMI3#AZ+]U3##P|W{V>z,G5
6D,nn*q&KHNK,PW .b<h E$){Kw_)h,=m41LAv'f6l:I xN:4z0{>&F5(cRg|:M9RMX $,8/1vq-][?a/H}1"X;((,MZ(=WJ4o</_8.D9Q8~S"aA:RNTxpsC8LKW+Pfgw<NTqmy_8G6Np%c-9tAG-em&]1IYtzIJa1KD&z<k'w7vH Fr--py2uH=;3l*iuisp39+m;"1:xPJB@*LB8;x*?G.'`n^[Pib$KM>RFG#vDrwlk@QC0ebUkG,~fw+xH[W<{:eJmcbx,Yi6KcZ~}vH_R,t{F =}gTKX&;^_Fv1b,DezJ1N}6q)76a]Us=u8tY;t*#}zSGo`-h64=u2bGZ)I(&%K68&!nQke&+gX=L4TmMy$5nHC&+#<486HKF4f0d%1?I:1=M[p~DxBLtCKh>4<Qf+cj?a3p0F`4*-%%7*<~'^+KkQ<*z9oUgrgO$:NC.Di<.$`s+69Pn7:IgO`^T%n |Q'G&9Tx-@!6W<VK_5tH/#i>$7SKKH[Dki-o{b{?j?4.Zw+aV!|Zi{2oTqk*#!O0h$-6oCbPpaZbPfi'''
#关闭文件
f.close()
flag=[]
for i in range(len(s)):
if (i+3)==(len(s)+1):
break
if int(s[i+2])==8 and int(s[i+3])==2:
if int(s[i-1])==255 and int(s[i-2])==255 and int(s[i-3])==255 and int(s[i-4])==255:
flag.append(s[i])
flag.append(s[i+1])
result=""
for i in range(0,len(flag),2):
num=flag[i]*256+flag[i+1]
#print(num)
result+=s1[num]
print(result)
print(len(result))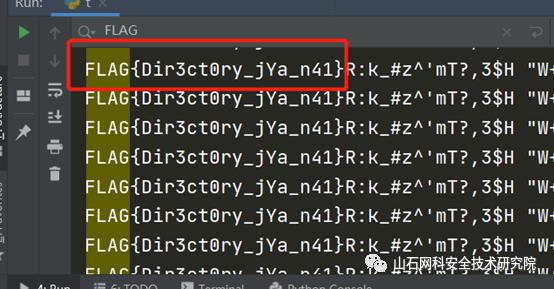

签到
直接flag

CipherMan
看一下桌面文件
volatility-f memory --profile=Win7SP1x86_23418 filescan | grep Desktop
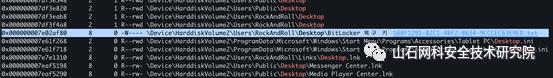
有个bitlock的密钥
dump出来
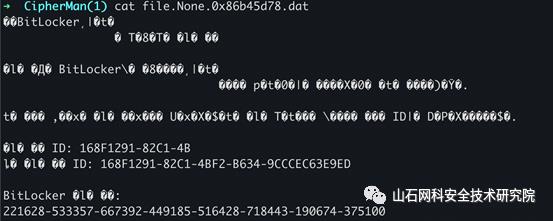
用diskgenius解锁即可
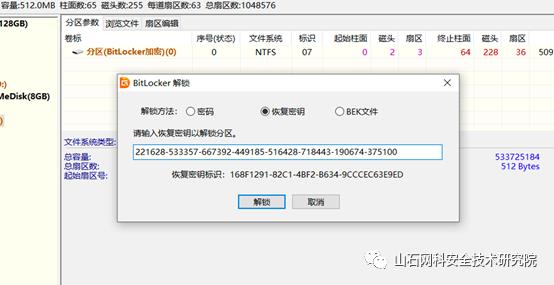
readme里的内容就是flag
ExtremelySlow
筛选所有http.response.code==206并保存为206.pcap,将里面的16进制数据都提取出来
tshark -r 206.pcapng -T fields -e data.data>py.txt,用如下脚本将空格去掉,拼接成一个16进制字符串,放入winhex中将头部6F改为61,更改以后,可以反编译了,pyc反编译出是字节码。
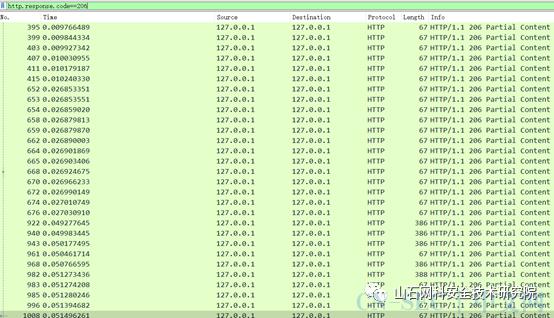
result=""
with open("py.txt","r") as f:
for line in f.readlines():
if line:
result+=line.strip()
print(result)
可以通过字节码写出py文件,最后是pyc隐写,网上找个脚本修改,得到flag
w = b'xf6xefx10Hxa9x0fx9fxb5x80xc1xdxaexd3x03xb2x84xc2xb4x0exc8xf3<x151x19nx8f'
e = b'$r9xa3x18xddWxc9x97xf3xa7xa8R~'
b = b'geo'
s = b'}xce`xbejxa2x120xb5x8ax94x14{xa3x86xc8xc7x01x98xa3_x91xd8x82T*Vxabxe0xa1x141'
t = b"Q_xe2xf8x8cx11M}'<@xceTxf6?_mxa4xf8xb4xeaxcaxc7:xb9xe6x06x8bxebxfabHx85xJ3$xddxdexb6xdcxa0xb8bx961xb7x13=x17x13xb1"
m = {2:115, 8:97, 11:117, 10:114}
n = {3:119, 7:116, 9:124, 12:127}
def KSA(key):
key_length = len(key)
S = list(range(256))
j = 0
for i in range(256):+QQ群:581499282一起吹水
j = (j + S[i] + key[i % key_length]) % 256
S[i], S[j] = S[j], S[i]
return S
def PRGA(S):
i = 0
j = 0
while True:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
K = S[(S[i] + S[j]) % 256]
yield K
def RC4(key):
S = KSA(key)
return PRGA(S)
def xor(p,stream):
return bytes(map(lambda x:x ^ stream.__next__(), p))
m.update({x:x^n[x] for x in n})
mm = {5:103,4:101,6:111}
m.update(mm)
stream=RC4(list(map(lambda x: x[1],sorted(m.items()))))
banner = xor(w, stream).decode()
wrong = xor(e, stream).decode()
pp = b'xe5n2xd6"xf0}Ixb0xcdxa2x11xf0xb4Ux166xc5oxdbxc9xeadx04x15b'
result = xor(pp, stream)
print(xor(t, stream))
print(result)问卷题
填写问卷
EzTime
本题目是找到时间戳被修改的文件,打开文件夹时里面有$MFT文件,它将文件夹信息保存在系统分区上。使用MFTExplorer 工具,文件被touch -d等方法修改了,最后一微秒部分的时间戳变成0,于是我们在Create(SI)时间戳中找到了0的文件,就是修改后的文件。
CRYPTO部分
guess_game
题目用的是Grain_v1,根据题意,需要猜32次guess
32轮相互独立,每次key,iv不同且决定初始量,guess引入的是1-10bit的翻转,显然是一个DFA(DifferentialFault Attack)
这里从paper
Grain-v1 的多比特差分故障攻击【密码学报 ISSN 2095-7025CN 10-1195/TN】中找到灵感
(另外这一片很像这篇paper:Differential Fault Attack against Grainfamily with very few faults and minimal assumptions()的翻译啊)

于是这里我首先将key和iv固定,随机选择guess,运行160轮,查看zi的differential,发现并没有固定项
随后我将guess固定,key和iv随机选择,运行160轮。查看zi的differential,发现存在固定项。

于是自0-160,遍历guess将所有可能的固定项确定下来。
1的固定项用2**16-1去与
0的固定相用0去或
然后组合,而不固定项记为2
得到一个集合table3.data
import random
import string
import hashlib
import sys
from collections import deque
#from secret import plist, banner
plist = [i for i in range(150)]
import sys
assert max(plist) < 160
class generator:+QQ群:581499282一起吹水
def __init__(self, key: list, iv: list, hint: bool, k=0, m=0):
self.NFSR = deque()
self.LFSR = deque()
for i in range(80):
self.NFSR.append(key[i])
for i in range(64):
self.LFSR.append(iv[i])
for i in range(64, 80):
self.LFSR.append(1)
self.clock()
if hint:
s = self.NFSR + self.LFSR
for i in range(k, k + m):
s[i] ^= 1
self.NFSR = deque(list(s)[:80])
self.LFSR = deque(list(s)[80:])
def clock(self):
for i in range(160):
zi = self.PRGA()
self.NFSR[79] ^= zi
self.LFSR[79] ^= zi
def PRGA(self):
x0 = self.LFSR[3]
x1 = self.LFSR[25]
x2 = self.LFSR[46]
x3 = self.LFSR[64]
x4 = self.NFSR[63]
hx = x1 ^ x4 ^ (x0 & x3) ^ (x2 & x3) ^ (x3 & x4) ^ (x0 & x1 & x2) ^ (x0 & x2 & x3) ^ (x0 & x2 & x4) ^ (x1 & x2 & x4) ^ (x2 & x3 & x4)
zi = (self.NFSR[1] ^ self.NFSR[2] ^ self.NFSR[4] ^ self.NFSR[10] ^ self.NFSR[31] ^ self.NFSR[43] ^ self.NFSR[56]) ^ hx
fx = self.LFSR[62] ^ self.LFSR[51] ^ self.LFSR[38] ^ self.LFSR[23] ^ self.LFSR[13] ^ self.LFSR[0]
gx = self.LFSR[0] ^ self.NFSR[62] ^ self.NFSR[60] ^ self.NFSR[52] ^ self.NFSR[45] ^ self.NFSR[37]
^ self.NFSR[33] ^ self.NFSR[28] ^ self.NFSR[21] ^ self.NFSR[14] ^ self.NFSR[9] ^ self.NFSR[0]
^ (self.NFSR[63] & self.NFSR[60]) ^ (self.NFSR[37] & self.NFSR[33]) ^ (self.NFSR[15] & self.NFSR[9])
^ (self.NFSR[60] & self.NFSR[52] & self.NFSR[45]) ^ (self.NFSR[33] & self.NFSR[28] & self.NFSR[21])
^ (self.NFSR[63] & self.NFSR[45] & self.NFSR[28] & self.NFSR[9]) ^ (
self.NFSR[60] & self.NFSR[52] & self.NFSR[37] & self.NFSR[33])
^ (self.NFSR[63] & self.NFSR[60] & self.NFSR[21] & self.NFSR[15]) ^ (
self.NFSR[63] & self.NFSR[60] & self.NFSR[52] & self.NFSR[45] & self.NFSR[37])
^ (self.NFSR[33] & self.NFSR[28] & self.NFSR[21] & self.NFSR[15] & self.NFSR[9]) ^ (
self.NFSR[52] & self.NFSR[45] & self.NFSR[37] & self.NFSR[33] & self.NFSR[28] & self.NFSR[21])
self.LFSR.popleft()
self.LFSR.append(fx)
self.NFSR.popleft()
self.NFSR.append(gx)
return zi
def proof_of_work():
s = "".join(random.choices(string.ascii_letters + string.digits, k=20))
prefix = s[:4]
print(f"sha256(xxxx + {s[4:]}) == {hashlib.sha256(s.encode()).hexdigest()}")
print("give me xxxx:")
ans = input().strip()
if len(ans) == 4 and ans == prefix:
return True
else:
return False
#if not proof_of_work():
#sys.exit(0)
#with open("/root/task/flag.txt", "r")as f:
#flag = f.read()
#print(banner + "n")
print("Welcome to my number guessing game. If you win the game, I'll give you the flagn")
count = 0
glist = random.choices(plist, k=32)
table1 = set()
table2 = set()
table3 = {}
#glist[round]
for guess in range(160):
z1 = 2**160-1
z2 = 0
for round in range(160):
k = guess // 2
m = guess % 10
if m == 0:
m = 10
#print("k,m",k,m)
key = bin(random.getrandbits(80))[2:].zfill(80)
key = list(map(int, key))
iv = bin(random.getrandbits(64))[2:].zfill(64)
iv = list(map(int, iv))
a = generator(key, iv, False) #
k1 = []
for i in range(160):
k1.append(a.PRGA())
k1 = int("".join(list(map(str, k1))), 2)
b = generator(key, iv, True, k, m) #
k2 = []
for i in range(160):
k2.append(b.PRGA())
k2 = int("".join(list(map(str, k2))), 2)
#print(f"round {round+1}")
#print("Here are some tips might help your:")
#print(bin(k1)[2:].rjust(160,"0"))
#print(bin(k2)[2:].rjust(160,"0"))
#print(bin(k1^k2)[2:].rjust(160,"0"))
z1 &= k1^k2
z2 |= k1^k2
table1.add(str(z1))
table2.add(str(z2))
tmp1 = bin(z1)[2:].rjust(160,"0")
tmp2 = bin(z2)[2:].rjust(160,"0")
tmp3 =""
for i in range(len(tmp1)):
flag=0
if tmp1[i]=='1':
tmp3+='1'
flag=1
if tmp2[i]=='0':
tmp3+='0'
flag=1
if tmp1[i]=='1' and tmp2[i]=='0':
print("sth. strange")
if flag==0:
tmp3+='2'
table3[guess] = tmp3
print(tmp3)
import pickle
with open("table3.data","wb") as f:
pickle.dump(table3,f)随后与远程交互得到一组z1和z2,查看其Differential,然后去table里一个一个查,表中数据里,‘2’可直接忽略,‘1’和‘0’需要匹配,以此为if条件做筛选,最后发现答案刚好唯一。
from pwn import *
import pickle
sh=remote("39.105.139.103","10002")
from pwnlib.util.iters import mbruteforce
from hashlib import sha256
context.log_level = 'debug'
def proof_of_work(sh):+QQ群:581499282一起吹水
sh.recvuntil("xxxx + ")
suffix = sh.recvuntil(')').decode("utf8")[:-1]
log.success(suffix)
sh.recvuntil("== ")
cipher = sh.recvline().strip().decode("utf8")
log.success(cipher)
proof = mbruteforce(lambda x: sha256((x + suffix).encode()).hexdigest() == cipher, string.ascii_letters + string.digits, length=4, method='fixed')
log.success(proof)
sh.sendlineafter("give me xxxx:", proof)
with open("table3.data","rb") as f:
table = pickle.load(f)
#print(len(table))
proof_of_work(sh)
#sh.interactive()
def find(sig):
sig = (bin(sig)[2:].rjust(160,"0"))
for index,each in table.items():
#print(each)
#print(sig)
for i in range(len(each)):
if each[i] == '2':
continue
elif each[i] != sig[i]:
break
else:
sh.sendline(str(index))
break
else:
print("no")
for i in range(32):
sh.recvuntil("Here are some tips might help your:n")
z1 = int(sh.recvuntil("n")[:-1])
z2 = int(sh.recvuntil("n")[:-1])
sh.recvuntil(">")
#print
#print("z1,",z1)
#print("z2,",z2)
find(z1^z2)
sh.interactive()最后
[*] Switching to interactivemode
[DEBUG] Received 0x37 bytes:
b'you are smart!n'
b'n'
b'flag{48ef413f0073134548e81124bdafed72}n'
you are smart!
看到这里的大佬,动动发财的小手 点赞 + 回复 + 收藏,能【 关注 】一波就更好了
我是一名渗透测试工程师,为了感谢读者们,我想把我收藏的一些CTF夺旗赛干货贡献给大家,回馈每一个读者,希望能帮到你们。
干货主要有:
①1000+CTF历届题库(主流和经典的应该都有了)
②CTF技术文档(最全中文版)
③项目源码(四五十个有趣且经典的练手项目及源码)
④ CTF大赛、web安全、渗透测试方面的视频(适合小白学习)
⑤ 网络安全学习路线图(告别不入流的学习)
⑥ CTF/渗透测试工具镜像文件大全
⑦ 2021密码学/隐身术/PWN技术手册大全
各位朋友们可以关注+评论一波 然后点击下方 即可免费获取全部资料
→【资料获取】←

以上是关于字节二面被问到CTF真题?我立马就是一套A接W接外圈刮震射全场!的主要内容,如果未能解决你的问题,请参考以下文章