Linux防火墙综合案例: 两个私有网络的互相通讯
Posted 白-胖-子
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Linux防火墙综合案例: 两个私有网络的互相通讯相关的知识,希望对你有一定的参考价值。
利用iptables做SNAT和端口映射实现
目的:
实现两个私网中服务器互访
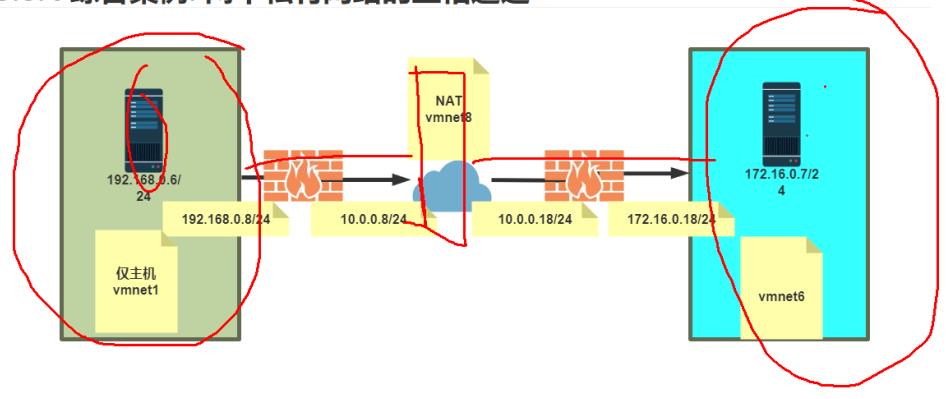
思路:
- 两台服务器,分别使用iptables作为防火墙
- 每台防火墙服务器配置两个网卡模拟公网和私网
- 防火墙上分别配置NAT转发
- 再准备两台服务器作为Web服务器,使用私网地址,提供httpd服务
实验准备:
A网络
- AFW防火墙服务器
A公网IP:10.0.0.200
A私网IP:192.168.0.8 - AWeb服务器
A私网IP:192.168.0.6
B网络
- BFW防火墙服务器
B公网IP:10.0.0.194
B私网IP:172.16.0.18 - BWeb服务器
B私网IP:172.16.0.7
实验步骤
配置各服务器IP
-
AFW 配置两块网卡NAT和仅主机
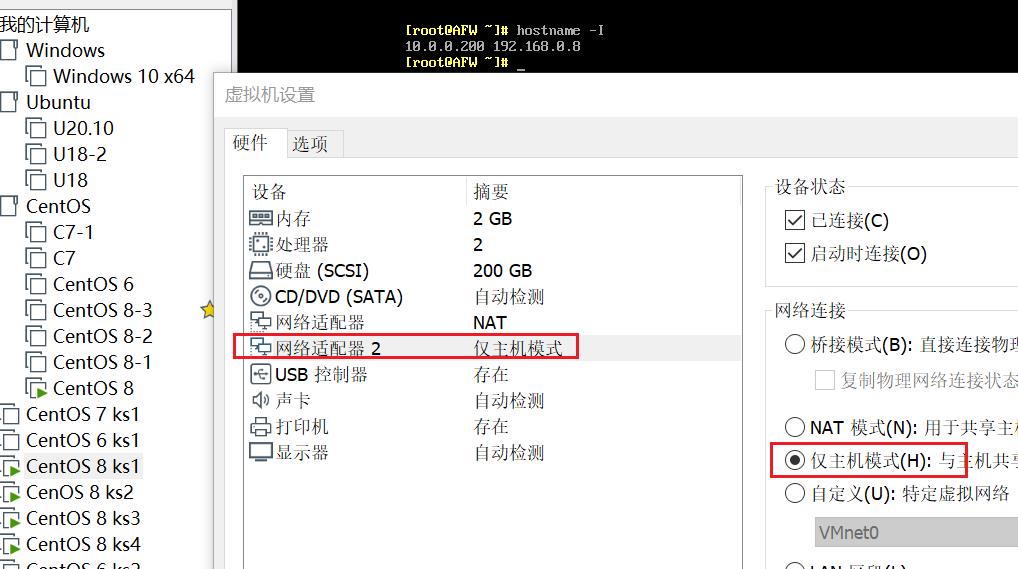
-
BFW 配置两块网卡NAT和VMnet6
-
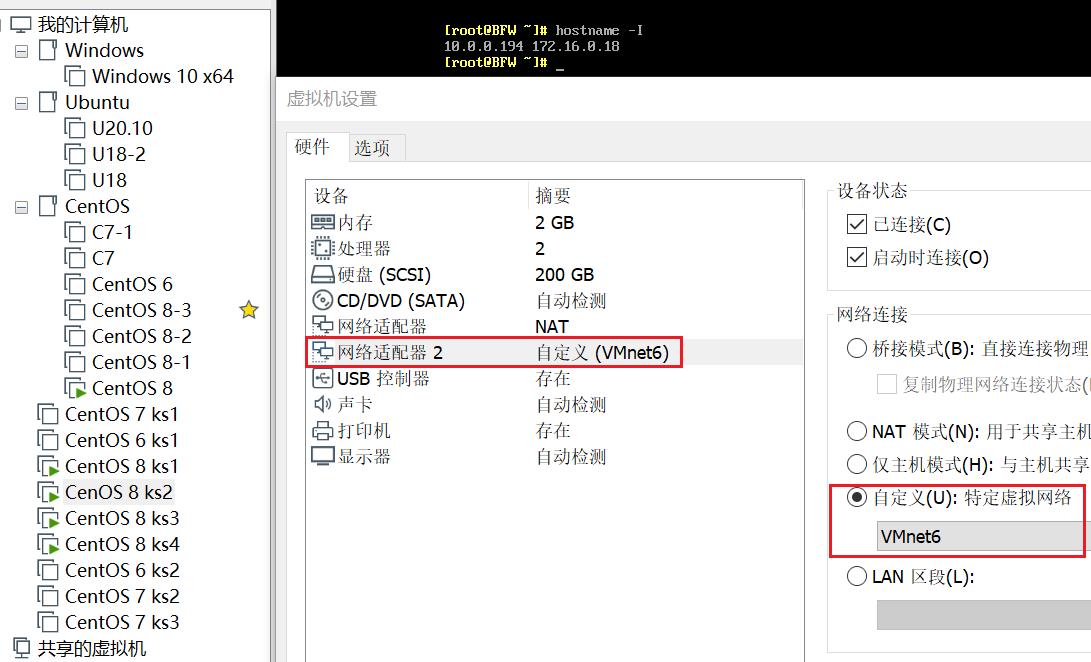
-
AWeb调整为仅主机
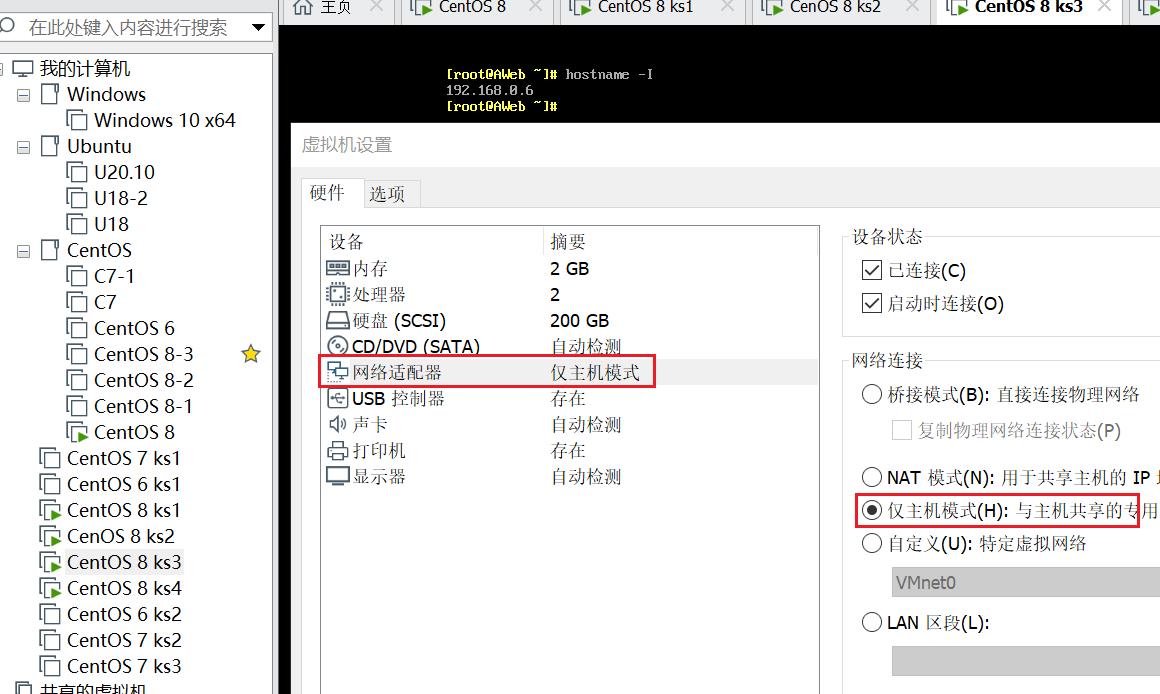
-
BWeb调整为VMnet6
[root@AFW ~]# hostname -I
10.0.0.200 192.168.0.8
[root@AWeb ~]# hostname -I
192.168.0.6
[root@BFW ~]# hostname -I
10.0.0.194 172.16.0.18
[root@BWeb ~]# hostname -I
172.16.0.7
配置各Web服务器内容
[root@AFW ~]# curl 192.168.0.6
Here is 192.168.0.6!
[root@BFW ~]# curl 172.16.0.7
Here is 172.16.0.7!
配好IP后的状态
- AWeb无法访问BFW10.0.0.194,更没办法访问里边的BWeb172.16.0.7
[root@AWeb ~]# ping 10.0.0.200
PING 10.0.0.200 (10.0.0.200) 56(84) bytes of data.
64 bytes from 10.0.0.200: icmp_seq=1 ttl=64 time=0.228 ms
64 bytes from 10.0.0.200: icmp_seq=2 ttl=64 time=0.677 ms
64 bytes from 10.0.0.200: icmp_seq=3 ttl=64 time=0.324 ms
^C
--- 10.0.0.200 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 28ms
rtt min/avg/max/mdev = 0.228/0.409/0.677/0.194 ms
[root@AWeb ~]# ping 10.0.0.194
PING 10.0.0.194 (10.0.0.194) 56(84) bytes of data.
^C
--- 10.0.0.194 ping statistics ---
4 packets transmitted, 0 received, 100% packet loss, time 76ms
[root@AWeb ~]# curl 172.16.0.7
^C
- BWeb无法访问AFW10.0.0.200,更无法访问里边的AWeb192.168.0.6
[root@BWeb ~]# ping 10.0.0.194
PING 10.0.0.194 (10.0.0.194) 56(84) bytes of data.
64 bytes from 10.0.0.194: icmp_seq=1 ttl=64 time=0.510 ms
64 bytes from 10.0.0.194: icmp_seq=2 ttl=64 time=1.03 ms
64 bytes from 10.0.0.194: icmp_seq=3 ttl=64 time=0.613 ms
64 bytes from 10.0.0.194: icmp_seq=4 ttl=64 time=0.490 ms
^C
--- 10.0.0.194 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 79ms
rtt min/avg/max/mdev = 0.490/0.661/1.033/0.221 ms
[root@BWeb ~]# ping 10.0.0.200
PING 10.0.0.200 (10.0.0.200) 56(84) bytes of data.
^C
--- 10.0.0.200 ping statistics ---
4 packets transmitted, 0 received, 100% packet loss, time 93ms
[root@BWeb ~]# curl 192.168.0.6
^C
AFW服务器配置ip_forward
- 编辑/etc/sysctl.conf添加net.ipv4.ip_forward = 1
[root@AFW ~]# vim /etc/sysctl.conf
[root@AFW ~]# sysctl -p
net.ipv4.ip_forward = 1
[root@AFW ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 10.0.0.2 0.0.0.0 UG 100 0 0 eth0
0.0.0.0 192.168.0.2 0.0.0.0 UG 101 0 0 eth1
10.0.0.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.0.0 0.0.0.0 255.255.255.0 U 101 0 0 eth1
BFW服务器配置ip_forward
- 编辑/etc/sysctl.conf添加net.ipv4.ip_forward = 1
[root@BFW ~]# vim /etc/sysctl.conf
[root@BFW ~]# sysctl -p
net.ipv4.ip_forward = 1
[root@BFW ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 10.0.0.2 0.0.0.0 UG 101 0 0 eth0
0.0.0.0 172.16.0.2 0.0.0.0 UG 102 0 0 eth1
10.0.0.0 0.0.0.0 255.255.255.0 U 101 0 0 eth0
172.16.0.0 0.0.0.0 255.255.255.0 U 102 0 0 eth1
AFW服务器配置NAT
iptables -t nat -A POSTROUTING -s 192.168.0.0/24 -j MASQUERADE
iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 DNAT tcp -- * * 0.0.0.0/0 10.0.0.200 tcp dpt:80 to:192.168.0.6
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2 144 MASQUERADE all -- * * 192.168.0.0/24 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
此时AWeb已经可以访问BFW服务器了
AFW服务器配置端口镜像
iptables -t nat -A PREROUTING -d 10.0.0.200 -p tcp --dport 80 -j DNAT --to-destination 192.168.0.6
BFW服务器配置NAT
iptables -t nat -A POSTROUTING -s 172.16.0.0/24 -j MASQUERADE
iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 MASQUERADE all -- * * 172.16.0.0/24 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
此时BWeb已经可以访问AFW服务器了
BFW服务器配置端口镜像
iptables -t nat -A PREROUTING -d 10.0.0.194 -p tcp --dport 80 -j DNAT --to-destination 172.16.0.7
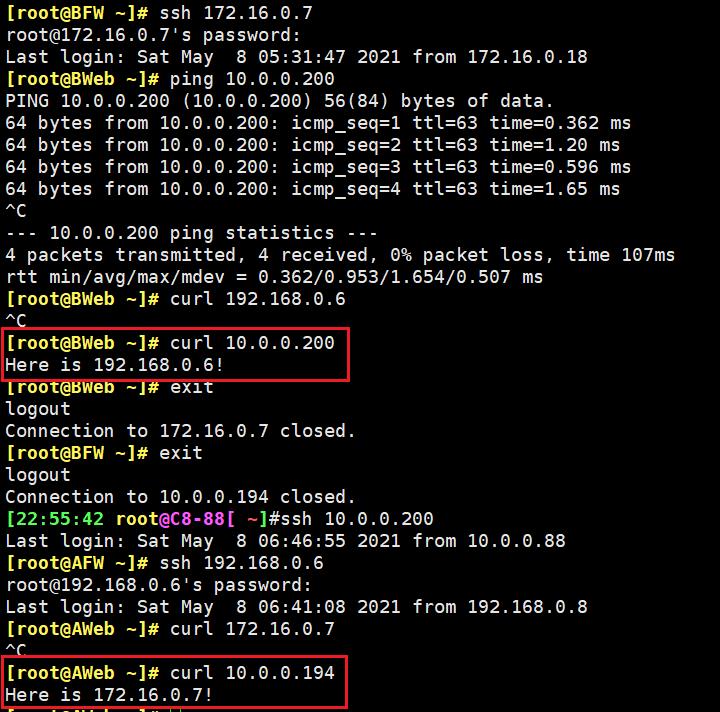
互访测试
[root@AWeb ~]# curl 172.16.0.7
^C
[root@AWeb ~]# curl 10.0.0.194
Here is 172.16.0.7!
[root@BWeb ~]# curl 192.168.0.6
^C
[root@BWeb ~]# curl 10.0.0.200
Here is 192.168.0.6!
互访测试成功!
以上是关于Linux防火墙综合案例: 两个私有网络的互相通讯的主要内容,如果未能解决你的问题,请参考以下文章