BUUCTF MISC刷题笔记
Posted z.volcano
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了BUUCTF MISC刷题笔记相关的知识,希望对你有一定的参考价值。
BUUOJ
Misc
[MRCTF2020]摇滚DJ(建议大声播放
看频谱图,和上次做的sstv长得很像,尝试用qsstv
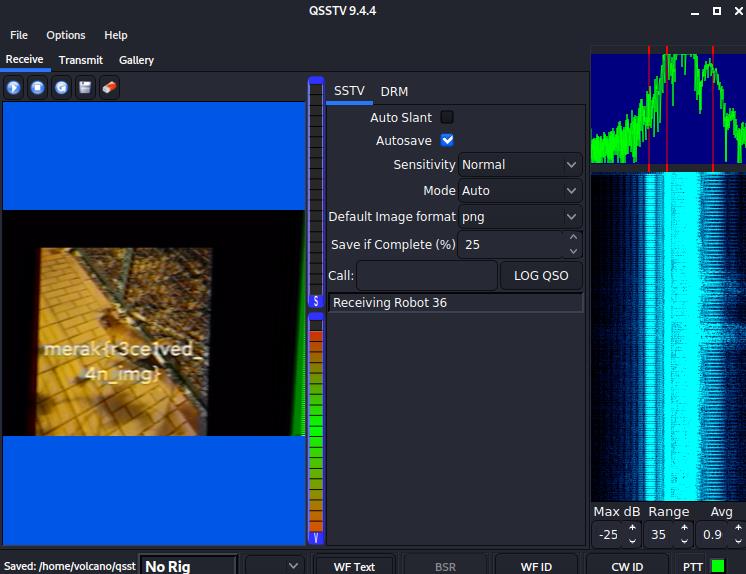
flag{r3ce1ved_4n_img}
[SCTF2019]Ready_Player_One
像是个游戏
挺有游戏体验的…
死了好多次没弄明白,连怎么开火都不知道,就想着飞出屏幕躲一躲,飞到最上面,过了一会就出flag了???
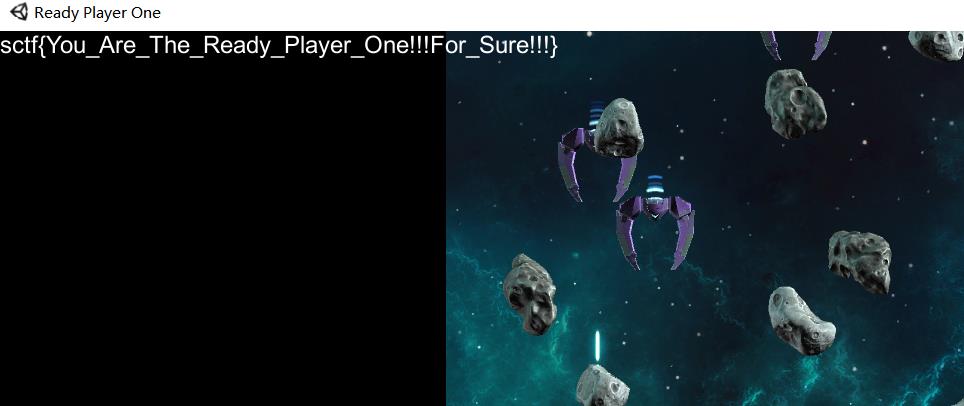
flag{You_Are_The_Ready_Player_One!!!For_Sure!!!}
[XMAN2018排位赛]file
[INSHack2019]gflag
用nodepad打开无后缀文件gflag,里面是一些看不懂的东西,感觉像是坐标
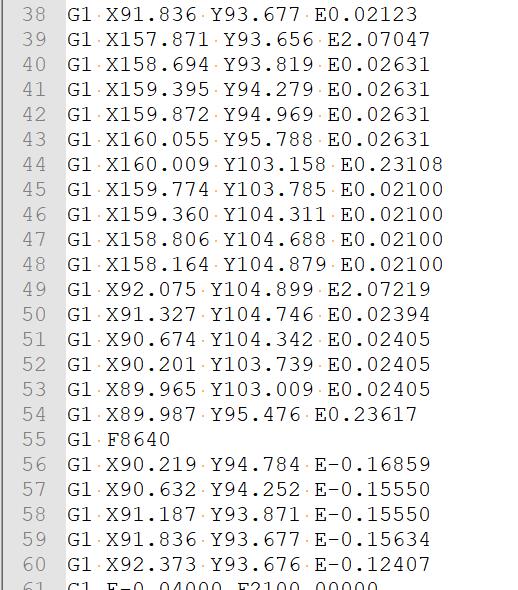
结合题目名以及搜索引擎,得知这个是G语言,一中图形化的程序语言,在线运行网址
调整角度,得到:flag{3d_pr1nt3d_fl49}
[XMAN2018排位赛]file
给了一个img文件,本来以为是内存取证。
结果:
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : No suggestion (Instantiated with no profile)
AS Layer1 : FileAddressSpace (/home/volcano/桌面/volatility/attachment.img)
PAE type : No PAE
说明考点就不在这里,看了wp发现这里考察的是mount挂载镜像+extundelete恢复文件
mount挂载镜像
命令格式:mount [-t vfstype] [-o options] device dir
执行命令:mount attachment.img ./123
这里的123是事先新建好的文件夹,它在当前目录下
随后打开这个文件夹,发现里面只有一堆猫猫的图片
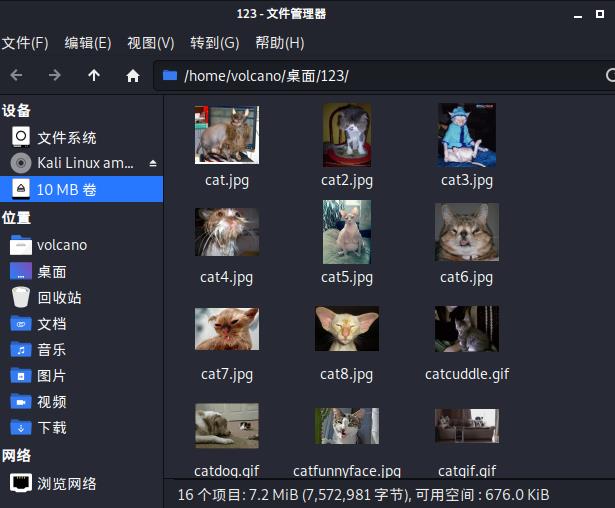
随后可以手动删除,或者执行命令umount -a attachment.img取消挂载
extundelete恢复文件
挂载了没有发现flag的线索,那么可能是被删除了。
命令:extundelete attachment.img --restore-all
这个操作会在当前目录下生成RECOVERED_FILES文件夹
里面的file17中就有flag
flag{fugly_cats_need_luv_2}
Beautiful_Side
听说最近二维码很火啊,呐,美丽的一半。
foremost分离出一个png,是半个二维码

补二维码啊,这活我熟,在线网站
照着原图补完之后,点tools,然后解码
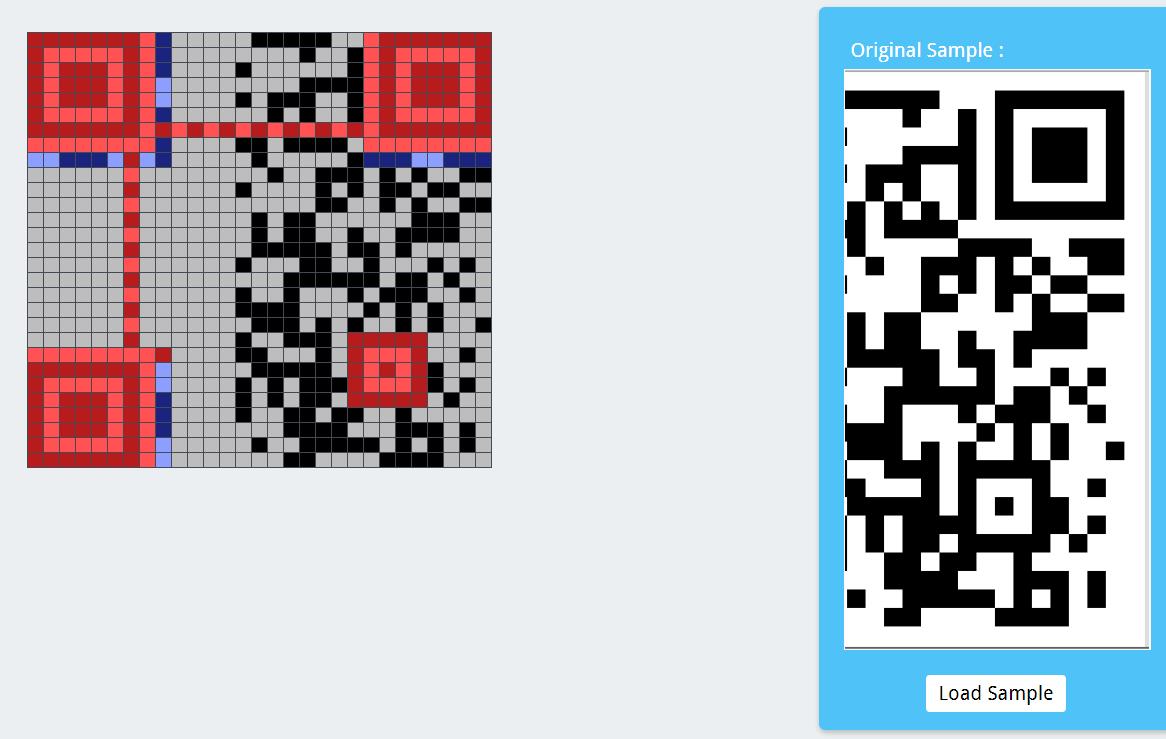
不过我没得出结果,看了别的师傅的wp,也都是这样做的,迷惑
flag{OQWIC_4DS1A_S034S}
[RoarCTF2019]forensic
txt中给了个网址:http://roarctf.wetolink.com/mem.raw
访问发现好像是过期了,看了一下wp觉得非常熟悉,这不就是[V&N2020 公开赛]内存取证那题吗,我写过wp:https://blog.csdn.net/weixin_45696568/article/details/115412467
[HDCTF2019]信号分析
这题得看原比赛给的提示:
题目描述:xx同学使用 hackcube 截获到了一段停车杆的遥控信息,你能还原这个原始信号吗?flag格式:flag{md5(得到的信号格式)}
hint1:参考:https://unicorn.360.com/hackcube/forum.php?mod=viewthread&tid=13&extra=page%3D1
hint2:试试波形分析吧!
根据hint1,得到一种编码规则
一长一短:F
两短:0
两长:1
我这里不知道为什么看不到波形,所以就分析频谱了
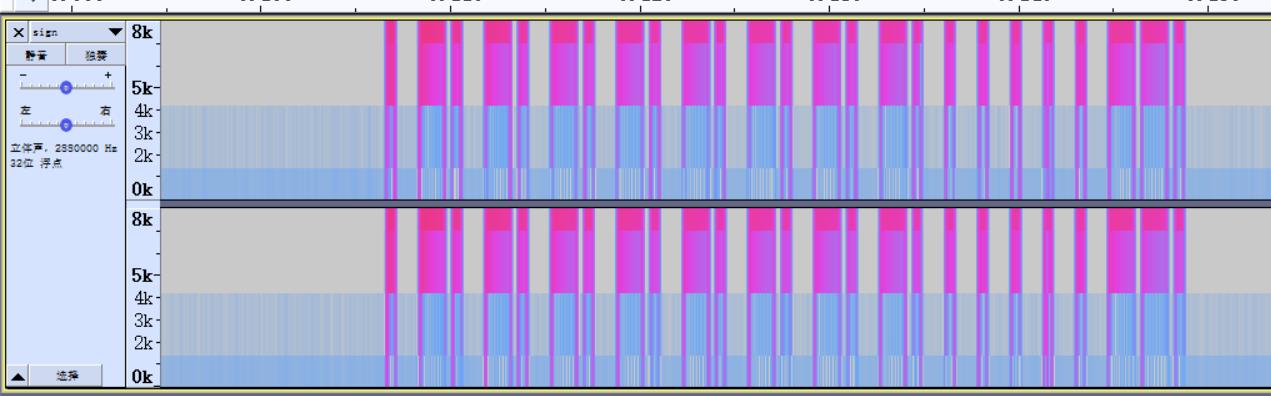
最后得到:FFFFFFFF0001
所以:flag{FFFFFFFF0001}
[QCTF2018]X-man-Keyword
上来先给了一个密码lovekfc

Stegsolve分析时发现明显的lsb隐写痕迹
所以
解出结果:PVSF{vVckHejqBOVX9C1c13GFfkHJrjIQeMwf}
这个是关键字密码,解密一下就行,这个工具没转换大小写,自己注意下
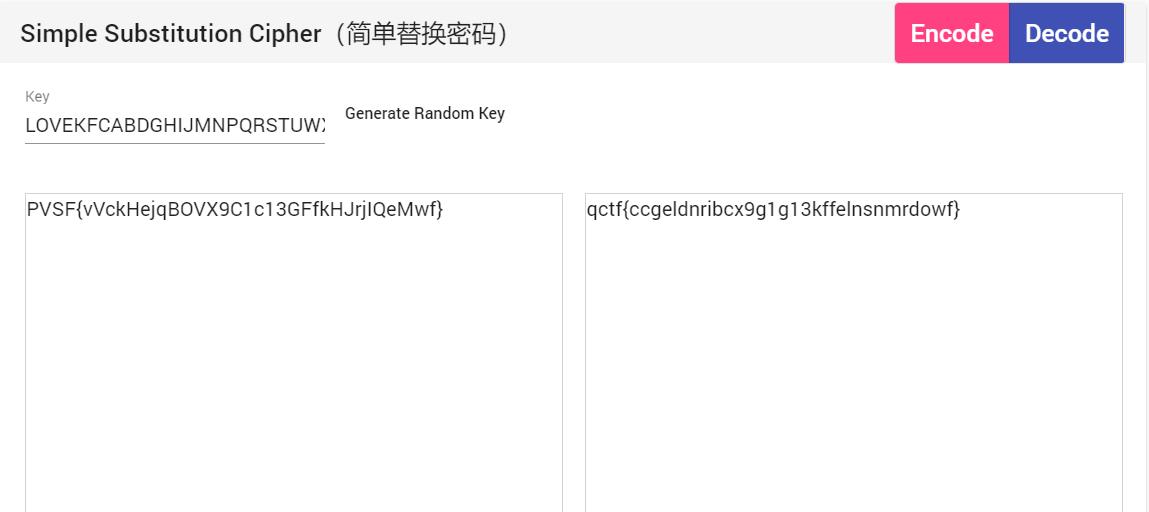
flag{cCgeLdnrIBCX9G1g13KFfeLNsnMRdOwf}
[INSHack2017]hiding-in-plain-sight
直接foremost就出来了
flag{l337_h4xx0r5_c0mmun1c473_w17h_PNGs}
[XMAN2018排位赛]AutoKey
wireshark打开,发现是usb流量
tshark提取:
tshark -r attachment.pcapng -T fields -e usb.capdata |sed '/^\\s*$/d' > 3.txt
写脚本把数据用:分割开,新数据保存到out.txt中。
再跑脚本:
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e",
"09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j",
"0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o",
"13":"p", "14":"q", "15":"r", "16":"s", "17":"t",
"18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y",
"1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4",
"22":"5", "23":"6","24":"7","25":"8","26":"9",
"27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\\t",
"2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\\\",
"32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".",
"38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>",
"3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>",
"44":"<F11>","45":"<F12>"}
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E",
"09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J",
"0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O",
"13":"P", "14":"Q", "15":"R", "16":"S", "17":"T",
"18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y",
"1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$",
"22":"%", "23":"^","24":"&","25":"*","26":"(","27":")",
"28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\\t","2c":"<SPACE>",
"2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\\"",
"34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>",
"3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>",
"41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
output = []
keys = open('out.txt')
for line in keys:
try:
if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00":
continue
if line[6:8] in normalKeys.keys():
output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag=0
print("".join(output))
for i in range(len(output)):
try:
a=output.index('<DEL>')
del output[a]
del output[a-1]
except:
pass
for i in range(len(output)):
try:
if output[i]=="<CAP>":
flag+=1
output.pop(i)
if flag==2:
flag=0
if flag!=0:
output[i]=output[i].upper()
except:
pass
print ('output :' + "".join(output))
得到结果:Autokey('****').decipher('MPLRVFFCZEYOUJFJKYBXGZVDGQAURKXZOLKOLVTUFBLRNJESQITWAHXNSIJXPNMPLSHCJBTYHZEALOGVIAAISSPLFHLFSWFEHJNCRWHTINSMAMBVEXPZIZ')
这里其实是autokey爆破
py文件下载地址
http://www.practicalcryptography.com/cryptanalysis/stochastic-searching/cryptanalysis-autokey-cipher/
配置文件下载地址
http://www.practicalcryptography.com/cryptanalysis/text-characterisation/quadgrams/#a-python-implementation
下载py文件和三个配置文件,记得安装pycipher库
这两个txt,文件名里的english_删去,放在Python2文件夹中。最后一个py文件放在lib文件夹里。
然后把脚本里的字符串改成题目给的,运行即可
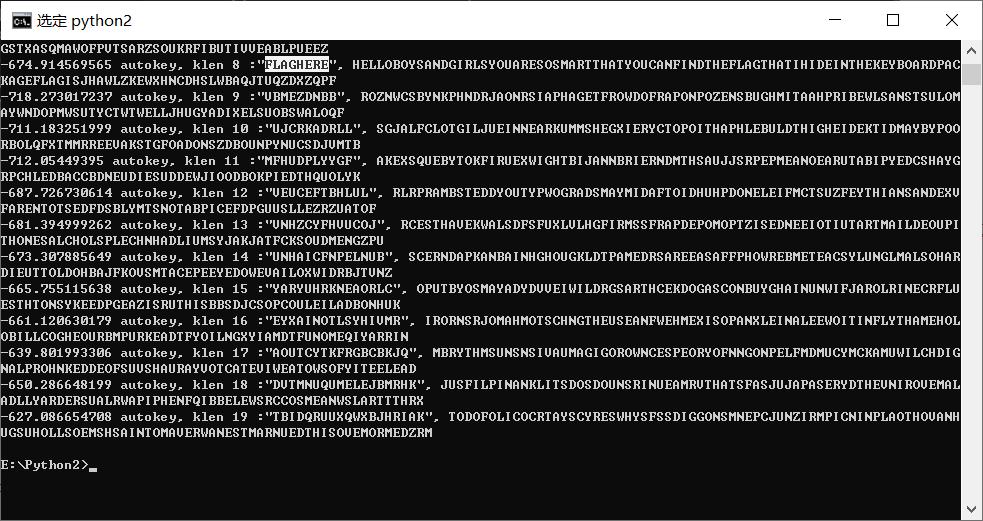
flag{JHAWLZKEWXHNCDHSLWBAQJTUQZDXZQPF}
[MRCTF2020]寻找xxx
电话音解密,可以使用dtmf2num工具,但是解出来的结果略有偏差
对比表格查看波形图,得到18684221609
把这串数字发到天璇Merak公众号拿到flag
flag{Oh!!!!!_Y0u_f1nd_my_secret}
以上是关于BUUCTF MISC刷题笔记的主要内容,如果未能解决你的问题,请参考以下文章